Comprehensive Report: IS Security and Risk Management for Atlassian
VerifiedAdded on 2021/06/18
|14
|2580
|335
Report
AI Summary
This report provides a comprehensive analysis of IS security and risk management within the context of Atlassian, an enterprise software company. It begins by identifying common malware threats such as adware, bots, spyware, worms, and Trojan horses, and then discusses the required networking devices including NICs, hubs, bridges, brouters, and gateways. The report assesses methods for ensuring the availability and reliability of web services, as well as the integrity and confidentiality of staff emails, covering topics such as access controls, file permissions, and version control. It prioritizes and discusses threats related to web servers and webmails, including data leakage, malware, and DoS attacks. Furthermore, the report explores two approaches to developing the availability of email and web servers: utilizing cloud services and employing search engines. The impact of organizational issues and human factors on risk management and IS-related securities is also examined, followed by illustrations of security problems and risk management challenges at Atlassian. The report includes an analysis of audit log reports and proposes network security devices such as anti-malware software, mobile device management, network access controls, and next-generation firewalls. The report concludes with recommendations for enhancing Atlassian's security posture, such as installing antivirus software, patching software, and securing Wi-Fi connections.

Running head: IS SECURITY AND RISK MANAGEMENT
IS Security and Risk Management
(Atlassian)
Name of the student:
Name of the university:
Author Note
IS Security and Risk Management
(Atlassian)
Name of the student:
Name of the university:
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1IS SECURITY AND RISK MANAGEMENT
Executive summary
Atlassian is one of the most popular enterprise software organization located in Australia. Here the
report aims to recognize various common malware and threads against information of the company.
Next, it analyzes multiple networking devices, reliability and availability of different web-services.
Apart from this, it assesses methods ensuring confidentiality and integrity of various employee
emails. Lastly, different malware and security problems concerning webmails and web servers are
analyzed here.
Executive summary
Atlassian is one of the most popular enterprise software organization located in Australia. Here the
report aims to recognize various common malware and threads against information of the company.
Next, it analyzes multiple networking devices, reliability and availability of different web-services.
Apart from this, it assesses methods ensuring confidentiality and integrity of various employee
emails. Lastly, different malware and security problems concerning webmails and web servers are
analyzed here.

2IS SECURITY AND RISK MANAGEMENT
Table of Contents
1. Introduction:......................................................................................................................................3
2. Common malware and threads against Information systems of Atlassian:.......................................3
3. Required networking devices for Atlassian:......................................................................................4
4. Assuring availability and reliability of web services:........................................................................4
5. Methods to assure integrity and confidentiality of staff emails:........................................................5
5.1. Confidentiality:...............................................................................................................5
5.2. Integrity:.........................................................................................................................5
6. Prioritization and discussion of threats and possible kinds of security and malware related to a
web server and web-mails:....................................................................................................................6
7. Two approaches to developing availability of email and web servers:.............................................6
8. Effect of organizational issues and human factors on risk management and IS-related securities:. .8
8.1. The organizational issues:...............................................................................................8
8.2. Human factors:................................................................................................................9
9. Various illustrations of security and problems at managing risks at Atlassian:................................9
10. Audit log reports:.............................................................................................................................9
11. Proposal of network security devices:...........................................................................................10
12. Conclusion:....................................................................................................................................11
13. Recommendations:........................................................................................................................11
14. References:....................................................................................................................................12
Table of Contents
1. Introduction:......................................................................................................................................3
2. Common malware and threads against Information systems of Atlassian:.......................................3
3. Required networking devices for Atlassian:......................................................................................4
4. Assuring availability and reliability of web services:........................................................................4
5. Methods to assure integrity and confidentiality of staff emails:........................................................5
5.1. Confidentiality:...............................................................................................................5
5.2. Integrity:.........................................................................................................................5
6. Prioritization and discussion of threats and possible kinds of security and malware related to a
web server and web-mails:....................................................................................................................6
7. Two approaches to developing availability of email and web servers:.............................................6
8. Effect of organizational issues and human factors on risk management and IS-related securities:. .8
8.1. The organizational issues:...............................................................................................8
8.2. Human factors:................................................................................................................9
9. Various illustrations of security and problems at managing risks at Atlassian:................................9
10. Audit log reports:.............................................................................................................................9
11. Proposal of network security devices:...........................................................................................10
12. Conclusion:....................................................................................................................................11
13. Recommendations:........................................................................................................................11
14. References:....................................................................................................................................12
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3IS SECURITY AND RISK MANAGEMENT
1. Introduction:
Atlassian Corporation Plc is an enterprise software company situated in Australia. It creates
products for content management, project managers and software developers. Thus it has been
providing information systems to its customers and staffs ("Atlassian | Software Development and
Collaboration Tools", 2018).
The aim of the report is to identify common malware and various threads against Atlassian’s
information system, identification of different networking devices, availability and reliability of web
services. It also analyzes methods assuring integrity and confidentiality of staff emails and
prioritization of threats and kinds of security and malware issues related to web servers and
webmails.
2. Common malware and threads against Information systems of Atlassian:
Adware This malware delivers advertisements automatically.
Bot This threat is a software program for performing particular operations
automatically.
Spyware This functions through spying on user activities instead of any knowledge.
Worm This threat is spread around computer networks through exploiting
vulnerabilities of operating systems.
Trojan Horse This disguises as a regular program or file for tricking users to install and
download software. It provides remote access to infected computers
(DeAngelo & Stulz, 2015).
1. Introduction:
Atlassian Corporation Plc is an enterprise software company situated in Australia. It creates
products for content management, project managers and software developers. Thus it has been
providing information systems to its customers and staffs ("Atlassian | Software Development and
Collaboration Tools", 2018).
The aim of the report is to identify common malware and various threads against Atlassian’s
information system, identification of different networking devices, availability and reliability of web
services. It also analyzes methods assuring integrity and confidentiality of staff emails and
prioritization of threats and kinds of security and malware issues related to web servers and
webmails.
2. Common malware and threads against Information systems of Atlassian:
Adware This malware delivers advertisements automatically.
Bot This threat is a software program for performing particular operations
automatically.
Spyware This functions through spying on user activities instead of any knowledge.
Worm This threat is spread around computer networks through exploiting
vulnerabilities of operating systems.
Trojan Horse This disguises as a regular program or file for tricking users to install and
download software. It provides remote access to infected computers
(DeAngelo & Stulz, 2015).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4IS SECURITY AND RISK MANAGEMENT
3. Required networking devices for Atlassian:
The first one is Network Interface Card (NIC), which is very much important for networking.
This is helpful for computers for creating communications with others. The next one is a hub which
is used for connecting various computers under a single workgroup LAN network (McNeil, Frey &
Embrechts, 2015). The next one is a bridge which is used for improving performances where the
networks are divided into smaller segments. It is used for dividing huge networks into smaller
segments. The next one is the brouters which are the combination of bridges and routers. Next, the
gateways must be used effectively to forward packets needed for the remote network from various
local networks.
4. Assuring availability and reliability of web services:
Atlassian has needed a quality aspect whether Web services has existed or has been ready for
immediate usage as per as the availability is concerned. This is helpful to represent the probability
that any service has been available. The higher values have been representing that this service has
always been ready to utilize smaller values indicating unpredictability. This uncertainty is whether
the service has been available at a specific point of time (Aven, 2016).
For reliability, Atlassian must assure the quality element of the web services representing
degree being able to contain service and quality of services. Here, the number of failures every
month per year has been representing measures of the reliability of web service. Stating in other
rods, the reliability has been denoting to ordered and assured delivery of messages that are being
sent and received and to the service providers (Soomro, Shah & Ahmed, 2016).
3. Required networking devices for Atlassian:
The first one is Network Interface Card (NIC), which is very much important for networking.
This is helpful for computers for creating communications with others. The next one is a hub which
is used for connecting various computers under a single workgroup LAN network (McNeil, Frey &
Embrechts, 2015). The next one is a bridge which is used for improving performances where the
networks are divided into smaller segments. It is used for dividing huge networks into smaller
segments. The next one is the brouters which are the combination of bridges and routers. Next, the
gateways must be used effectively to forward packets needed for the remote network from various
local networks.
4. Assuring availability and reliability of web services:
Atlassian has needed a quality aspect whether Web services has existed or has been ready for
immediate usage as per as the availability is concerned. This is helpful to represent the probability
that any service has been available. The higher values have been representing that this service has
always been ready to utilize smaller values indicating unpredictability. This uncertainty is whether
the service has been available at a specific point of time (Aven, 2016).
For reliability, Atlassian must assure the quality element of the web services representing
degree being able to contain service and quality of services. Here, the number of failures every
month per year has been representing measures of the reliability of web service. Stating in other
rods, the reliability has been denoting to ordered and assured delivery of messages that are being
sent and received and to the service providers (Soomro, Shah & Ahmed, 2016).

5IS SECURITY AND RISK MANAGEMENT
5. Methods to assure integrity and confidentiality of staff emails:
5.1. Confidentiality:
For assuring confidentiality has been roughly equivalent privacy. Here the measures have
been undertaken for ensuring confidentiality has been effectively designed to prevent various
sensitive data from reaching to the wrong people. This is also helpful to assure those suitable
individuals can get access to it. Here, the access should be limited to various authorized people for
seeing the data under query (Rittinghouse & Ransome, 2016). Further, it has been common for
information to get categorized as per the amount. This has also included the kind of damage that
might be done to get fall towards unintended hands. Moreover, stringent measures can also be
implemented as per those categories.
5.2. Integrity:
This includes maintenance of trustworthiness, the accuracy and the consistency of data over
the complete life-cycle. Furthermore, here, the data should be changed according to transit and the
steps should be undertaken to assure that the information cannot be changed by different kinds of
unauthorized people like the case of confidentiality. Further, the measures have been including user
access controls and file permissions. The version controls have been sued for preventing mistaken
changes and accidental deletion of authorized individuals from becoming a problem (Webb et al.,
2014). Moreover, there has been various means that must be in place to find different changes in the
data. This can occur as the results of different types of events that are caused by non-human like
EMP or electromagnetic pulse or crashes in servers. Further, there are some data that includes
checksums and cryptographic checksums in verify integrity. Further, the redundancies or backups
should also be available. This is to restore the various affected data towards the proper state.
5. Methods to assure integrity and confidentiality of staff emails:
5.1. Confidentiality:
For assuring confidentiality has been roughly equivalent privacy. Here the measures have
been undertaken for ensuring confidentiality has been effectively designed to prevent various
sensitive data from reaching to the wrong people. This is also helpful to assure those suitable
individuals can get access to it. Here, the access should be limited to various authorized people for
seeing the data under query (Rittinghouse & Ransome, 2016). Further, it has been common for
information to get categorized as per the amount. This has also included the kind of damage that
might be done to get fall towards unintended hands. Moreover, stringent measures can also be
implemented as per those categories.
5.2. Integrity:
This includes maintenance of trustworthiness, the accuracy and the consistency of data over
the complete life-cycle. Furthermore, here, the data should be changed according to transit and the
steps should be undertaken to assure that the information cannot be changed by different kinds of
unauthorized people like the case of confidentiality. Further, the measures have been including user
access controls and file permissions. The version controls have been sued for preventing mistaken
changes and accidental deletion of authorized individuals from becoming a problem (Webb et al.,
2014). Moreover, there has been various means that must be in place to find different changes in the
data. This can occur as the results of different types of events that are caused by non-human like
EMP or electromagnetic pulse or crashes in servers. Further, there are some data that includes
checksums and cryptographic checksums in verify integrity. Further, the redundancies or backups
should also be available. This is to restore the various affected data towards the proper state.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6IS SECURITY AND RISK MANAGEMENT
6. Prioritization and discussion of threats and possible kinds of security and
malware related to a web server and web-mails:
A threat of data leakage:
Receiving personal data has been one of the primary targets of the hackers. As email is sent
through Internet, it undergoes through unprotected channels of communications. Thus messages,
usernames and passwords can be intercepted (Oppliger, 2015).
Threats of malware:
Email clients and servers are susceptible to malware. As any email servers get infected, the
stability of the entire system gets compromised. Here, privacy and integrity of personal data have
been falling under threats. The malware are spread among various email clients because of infected
attachments.
DoS threat:
Here the damages done by DoS attack have been hard to overstate. Further, it is unsent and
received emails ultimately harming the overall company.
7. Two approaches to developing availability of email and web servers:
Using cloud services:
The scaling quality of cloud servers has been effective and it has been easy and quick to
incorporate every update. This is done to cloud servers since it has been more affordable. One can
integrate various applications under one cloud. Further, it has been faster and easier to sign up for
cloud servers than running over web servers.
6. Prioritization and discussion of threats and possible kinds of security and
malware related to a web server and web-mails:
A threat of data leakage:
Receiving personal data has been one of the primary targets of the hackers. As email is sent
through Internet, it undergoes through unprotected channels of communications. Thus messages,
usernames and passwords can be intercepted (Oppliger, 2015).
Threats of malware:
Email clients and servers are susceptible to malware. As any email servers get infected, the
stability of the entire system gets compromised. Here, privacy and integrity of personal data have
been falling under threats. The malware are spread among various email clients because of infected
attachments.
DoS threat:
Here the damages done by DoS attack have been hard to overstate. Further, it is unsent and
received emails ultimately harming the overall company.
7. Two approaches to developing availability of email and web servers:
Using cloud services:
The scaling quality of cloud servers has been effective and it has been easy and quick to
incorporate every update. This is done to cloud servers since it has been more affordable. One can
integrate various applications under one cloud. Further, it has been faster and easier to sign up for
cloud servers than running over web servers.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
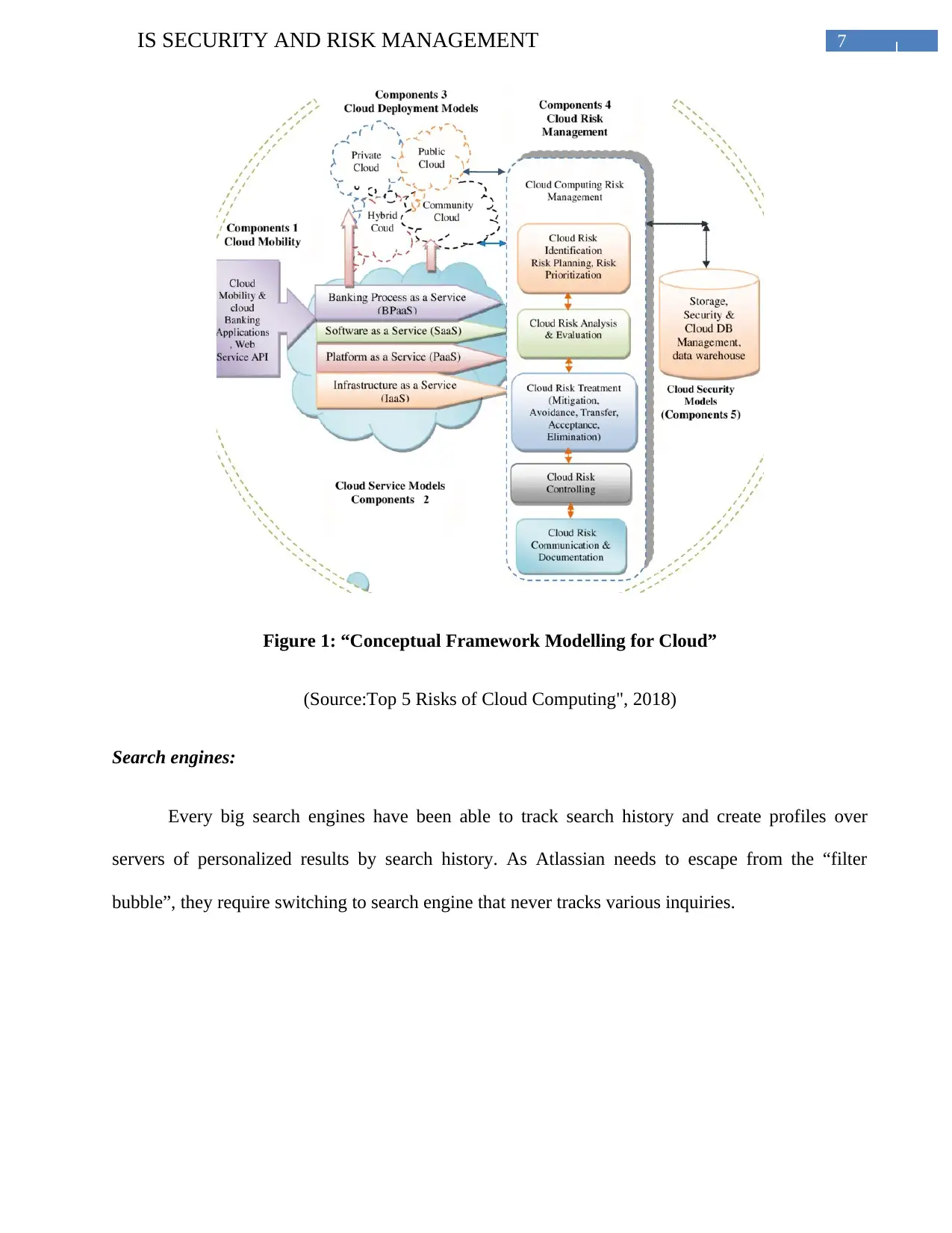
7IS SECURITY AND RISK MANAGEMENT
Figure 1: “Conceptual Framework Modelling for Cloud”
(Source:Top 5 Risks of Cloud Computing", 2018)
Search engines:
Every big search engines have been able to track search history and create profiles over
servers of personalized results by search history. As Atlassian needs to escape from the “filter
bubble”, they require switching to search engine that never tracks various inquiries.
Figure 1: “Conceptual Framework Modelling for Cloud”
(Source:Top 5 Risks of Cloud Computing", 2018)
Search engines:
Every big search engines have been able to track search history and create profiles over
servers of personalized results by search history. As Atlassian needs to escape from the “filter
bubble”, they require switching to search engine that never tracks various inquiries.
8IS SECURITY AND RISK MANAGEMENT
Figure 2: “Project risks – good and bad practice for search engines”
(Source: "Example project risks: real examples of bad & best practices", 2018 )
8. Effect of organizational issues and human factors on risk management and IS-
related securities:
8.1. The organizational issues:
There has been lack of decision making structure at Atlassian with lack of accountability
regarding risk decisions at the company.
There has been lack of needed risk analysis processes. Atlassian needs to consider risk
management that is needed to do from compliance standpoints conducting a superficial risk analysis
(Nazareth & Choi, 2015).
Figure 2: “Project risks – good and bad practice for search engines”
(Source: "Example project risks: real examples of bad & best practices", 2018 )
8. Effect of organizational issues and human factors on risk management and IS-
related securities:
8.1. The organizational issues:
There has been lack of decision making structure at Atlassian with lack of accountability
regarding risk decisions at the company.
There has been lack of needed risk analysis processes. Atlassian needs to consider risk
management that is needed to do from compliance standpoints conducting a superficial risk analysis
(Nazareth & Choi, 2015).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9IS SECURITY AND RISK MANAGEMENT
8.2. Human factors:
As Atlassian, has been addressing human factors, they mainly denote health and safety to
optimizing human performances and decreasing human failures.
9. Various illustrations of security and problems at managing risks at Atlassian:
Use of logs records:
While writing log records, the logging services verify that the logging requester gets the
sufficient authority to log and write data to a configured location. This is to complete and format
columns in log records.
Issues and securities:
The attackers have been able to use information that is not validated prior used by web
applications to reach various backend components.
Events in monitoring and analyzing:
The analyses of various risks are to be done on identified values. This required the proper
situation to deliver sufficient information regarding decision making. Here, the guidance is provided
with both through quantitative and qualitative methods (Eriksson, 2017).
10. Audit log reports:
For Atlassian, files and networks are needed to be accessed and changes must be made to
system configurations. Further, they must use system utilities and exceptions and various other
security-related events like alarms triggered. They must activate protection systems like antimalware
and detection systems. A collection of data has been assisting in access control monitoring and
8.2. Human factors:
As Atlassian, has been addressing human factors, they mainly denote health and safety to
optimizing human performances and decreasing human failures.
9. Various illustrations of security and problems at managing risks at Atlassian:
Use of logs records:
While writing log records, the logging services verify that the logging requester gets the
sufficient authority to log and write data to a configured location. This is to complete and format
columns in log records.
Issues and securities:
The attackers have been able to use information that is not validated prior used by web
applications to reach various backend components.
Events in monitoring and analyzing:
The analyses of various risks are to be done on identified values. This required the proper
situation to deliver sufficient information regarding decision making. Here, the guidance is provided
with both through quantitative and qualitative methods (Eriksson, 2017).
10. Audit log reports:
For Atlassian, files and networks are needed to be accessed and changes must be made to
system configurations. Further, they must use system utilities and exceptions and various other
security-related events like alarms triggered. They must activate protection systems like antimalware
and detection systems. A collection of data has been assisting in access control monitoring and
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10IS SECURITY AND RISK MANAGEMENT
provides audits trails while analyzing any incident. As most of the logs are covered by various kinds
of regulations, they must be kept long as the requirements have been calling for in case they are
required for investigation.
11. Proposal of network security devices:
Anti-Malware:
This network tool help administrators to remove, block and identify malware. They have
been helping IT departments for tailoring anti-malware policies for identifying different unknown
and known malware sources like surveil particular groups and users.
Mobile device management:
This software has been bolstering network securities through various distant controls and monitoring
of patch pushes, policy enforcement, controlling security configurations to different mobile devices.
Network access controls:
The NAC products have been enforcing policies of security through granting through
security policies and compliant to various devices accessing to different network resources.
Next-generation firewalls:
It provides next-generation security services, application visibility and essential web
securities.
provides audits trails while analyzing any incident. As most of the logs are covered by various kinds
of regulations, they must be kept long as the requirements have been calling for in case they are
required for investigation.
11. Proposal of network security devices:
Anti-Malware:
This network tool help administrators to remove, block and identify malware. They have
been helping IT departments for tailoring anti-malware policies for identifying different unknown
and known malware sources like surveil particular groups and users.
Mobile device management:
This software has been bolstering network securities through various distant controls and monitoring
of patch pushes, policy enforcement, controlling security configurations to different mobile devices.
Network access controls:
The NAC products have been enforcing policies of security through granting through
security policies and compliant to various devices accessing to different network resources.
Next-generation firewalls:
It provides next-generation security services, application visibility and essential web
securities.

11IS SECURITY AND RISK MANAGEMENT
Authorization and authentication:
This includes conventional directory-based services like authenticating users, active
directories and granting access by authorization rules ("How to Prevent Malware from Affecting
Network Security | White Rock Security Group", 2018).
12. Conclusion:
The above study shows that security risk management has been a vital factor and concern for
Atlassian. The research is useful for both external and internal risks. There are many IR risk options
for Atlassian that must be mitigated. Otherwise, that can lead to detrimental problems as they are
handled with proper care.
13. Recommendations:
The various recommendations for Atlassian for the present scenario are listed below.
Installing antivirus software and keeping all the software patched.
Using strong patched for all the sites and applications that are used.
Spotting social engineering attempts
Using secured Wi-Fi connections
Keeping back up of vital data
Limiting social network data
Downloading a file through legal processes
Obtaining the various areas before leaving that unattended.
Authorization and authentication:
This includes conventional directory-based services like authenticating users, active
directories and granting access by authorization rules ("How to Prevent Malware from Affecting
Network Security | White Rock Security Group", 2018).
12. Conclusion:
The above study shows that security risk management has been a vital factor and concern for
Atlassian. The research is useful for both external and internal risks. There are many IR risk options
for Atlassian that must be mitigated. Otherwise, that can lead to detrimental problems as they are
handled with proper care.
13. Recommendations:
The various recommendations for Atlassian for the present scenario are listed below.
Installing antivirus software and keeping all the software patched.
Using strong patched for all the sites and applications that are used.
Spotting social engineering attempts
Using secured Wi-Fi connections
Keeping back up of vital data
Limiting social network data
Downloading a file through legal processes
Obtaining the various areas before leaving that unattended.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 14
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.



