IS Security Model, Risk and Management for UK Ministry of Defence
VerifiedAdded on 2020/07/22
|9
|2516
|33
Report
AI Summary
This report provides a detailed analysis of an IS security model designed for the UK Ministry of Defence, emphasizing the importance of information security in the defense sector. It outlines the necessity of adhering to ISO 17799 standards to effectively manage risks and secure sensitive data. The report delves into risk assessment methodologies, including contingency planning, to mitigate potential threats and vulnerabilities. Furthermore, it explores the analysis of IS threats, vulnerabilities, and the use of tools like social engineering, to identify and address security weaknesses. The study underscores the significance of establishing robust security standards and controls, along with comprehensive risk analysis and contingency planning, to protect critical information and ensure the operational integrity of the Ministry of Defence. The report emphasizes the importance of a proactive approach to security, incorporating information security policies, development plans, and frameworks to safeguard against internal and external threats. This information is crucial for organizations seeking to enhance their security posture and protect valuable assets.

SECURITY RISK
AND
MANAGEMENT
AND
MANAGEMENT
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
INTRODUCTION...........................................................................................................................1
TASK 1............................................................................................................................................1
REFERENCES................................................................................................................................7
INTRODUCTION...........................................................................................................................1
TASK 1............................................................................................................................................1
REFERENCES................................................................................................................................7

INTRODUCTION
In this documentation, this assignment defines about to an IS security model in ministry
of define in UK, which must follow the standard of ISO 17799 in order to maintain risk and
manager all risky activities in effective form. Apart from it, this study also refer to risk
assessment in the organisation and identification of them by proper contingency planning about
reducing risk in the company in efficient form. Moreover, this assignment also describe about to
the analysis of IS threats and vulnerabilities and tools including the social engineering.
TASK 1
AN IS MODEL FOR MINISTRY OF DEFENCE IN UK
In several organisations, securities issues is most vital issues in terms of operating
business function in the industry in more appropriate manner. Nowadays, defence services of the
UK has been reached to its top level in the industry and now creating more complexity in the
defence industry of the country in most appropriate manner. Ministry of defence in the UK is
making efforts for developing its functionality in more effective ways so that proper securities of
its services and factors can be utilised effectively. Securities efforts are most needed approach
for the organisation which must be taken in order to secure all relevant data and information in
the industry in more efficient form (Spears and Barki, 2010). The organisation need to utilise
safer security ways in order to recording and distribution of important information in the industry
in more effective manner. Information security must be involves as a part of the organisation's
operating processes to make sure that it is implementation in exercises of the organisation in
effective form. This is an information technology system by which the organisation can
management of information security system and personal responsible for information security
and services provision efficiently. Increment in information security system must be taken into
accounts. Security planning is the process of security measurement that follow from the
organisation's operating policies and strategies takes into targets for individuals in positions of
responsibility for the entire organisation (Poolsappasit, Dewri and Ray,2012). In case of
provisions of ICT services in the firm, they need to ensure that, they have proper performance
management in connection with performance appraisals while implementing the services of the
IS security effectively. System information protection development get calls for sufficient
management of information system within the organisation efficiently. Ministry of defence in the
UK's information technology department need to make planning of IS security implementation
1
In this documentation, this assignment defines about to an IS security model in ministry
of define in UK, which must follow the standard of ISO 17799 in order to maintain risk and
manager all risky activities in effective form. Apart from it, this study also refer to risk
assessment in the organisation and identification of them by proper contingency planning about
reducing risk in the company in efficient form. Moreover, this assignment also describe about to
the analysis of IS threats and vulnerabilities and tools including the social engineering.
TASK 1
AN IS MODEL FOR MINISTRY OF DEFENCE IN UK
In several organisations, securities issues is most vital issues in terms of operating
business function in the industry in more appropriate manner. Nowadays, defence services of the
UK has been reached to its top level in the industry and now creating more complexity in the
defence industry of the country in most appropriate manner. Ministry of defence in the UK is
making efforts for developing its functionality in more effective ways so that proper securities of
its services and factors can be utilised effectively. Securities efforts are most needed approach
for the organisation which must be taken in order to secure all relevant data and information in
the industry in more efficient form (Spears and Barki, 2010). The organisation need to utilise
safer security ways in order to recording and distribution of important information in the industry
in more effective manner. Information security must be involves as a part of the organisation's
operating processes to make sure that it is implementation in exercises of the organisation in
effective form. This is an information technology system by which the organisation can
management of information security system and personal responsible for information security
and services provision efficiently. Increment in information security system must be taken into
accounts. Security planning is the process of security measurement that follow from the
organisation's operating policies and strategies takes into targets for individuals in positions of
responsibility for the entire organisation (Poolsappasit, Dewri and Ray,2012). In case of
provisions of ICT services in the firm, they need to ensure that, they have proper performance
management in connection with performance appraisals while implementing the services of the
IS security effectively. System information protection development get calls for sufficient
management of information system within the organisation efficiently. Ministry of defence in the
UK's information technology department need to make planning of IS security implementation
1
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
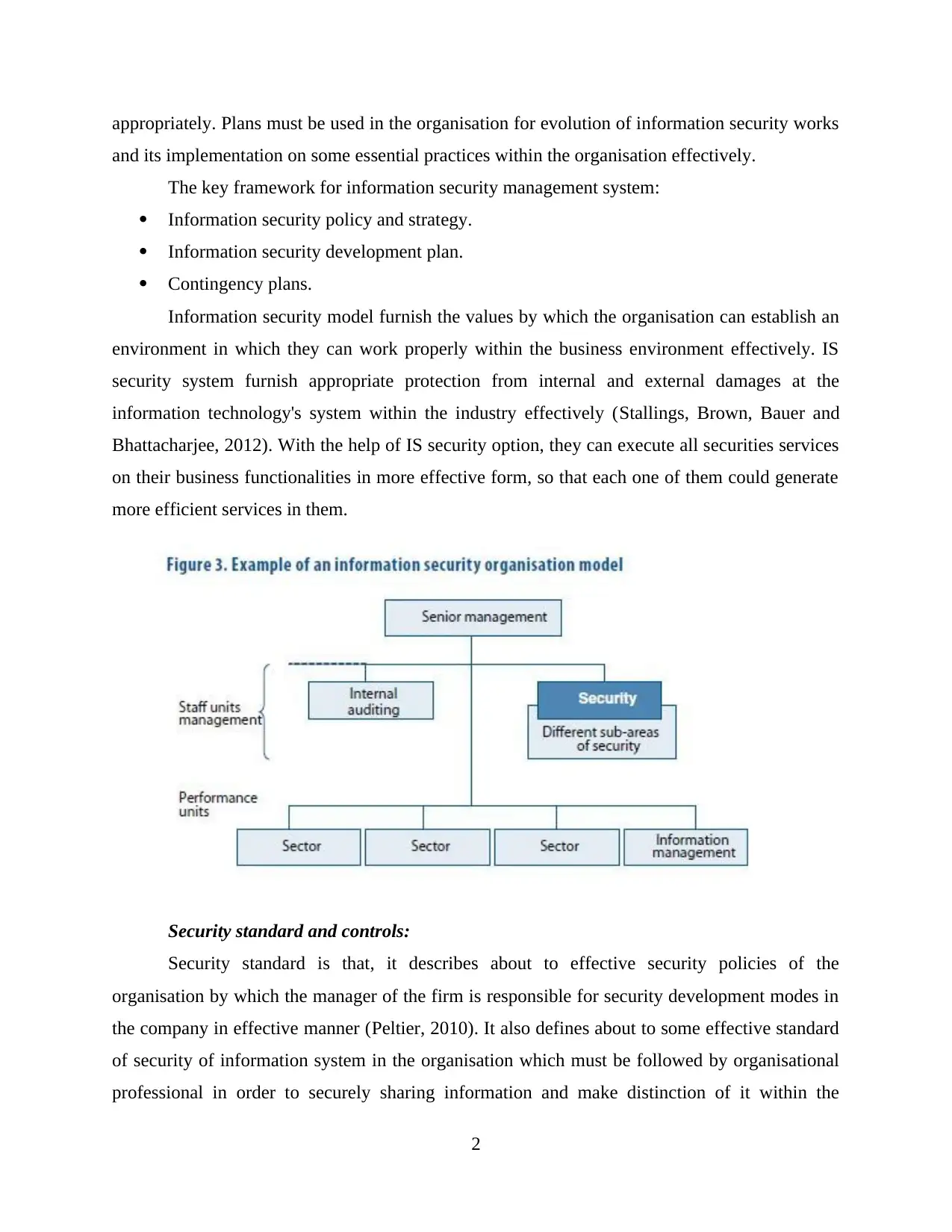
appropriately. Plans must be used in the organisation for evolution of information security works
and its implementation on some essential practices within the organisation effectively.
The key framework for information security management system:
Information security policy and strategy.
Information security development plan.
Contingency plans.
Information security model furnish the values by which the organisation can establish an
environment in which they can work properly within the business environment effectively. IS
security system furnish appropriate protection from internal and external damages at the
information technology's system within the industry effectively (Stallings, Brown, Bauer and
Bhattacharjee, 2012). With the help of IS security option, they can execute all securities services
on their business functionalities in more effective form, so that each one of them could generate
more efficient services in them.
Security standard and controls:
Security standard is that, it describes about to effective security policies of the
organisation by which the manager of the firm is responsible for security development modes in
the company in effective manner (Peltier, 2010). It also defines about to some effective standard
of security of information system in the organisation which must be followed by organisational
professional in order to securely sharing information and make distinction of it within the
2
and its implementation on some essential practices within the organisation effectively.
The key framework for information security management system:
Information security policy and strategy.
Information security development plan.
Contingency plans.
Information security model furnish the values by which the organisation can establish an
environment in which they can work properly within the business environment effectively. IS
security system furnish appropriate protection from internal and external damages at the
information technology's system within the industry effectively (Stallings, Brown, Bauer and
Bhattacharjee, 2012). With the help of IS security option, they can execute all securities services
on their business functionalities in more effective form, so that each one of them could generate
more efficient services in them.
Security standard and controls:
Security standard is that, it describes about to effective security policies of the
organisation by which the manager of the firm is responsible for security development modes in
the company in effective manner (Peltier, 2010). It also defines about to some effective standard
of security of information system in the organisation which must be followed by organisational
professional in order to securely sharing information and make distinction of it within the
2
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

business environment properly. The organisational professional needs to know that, they have
proper security system and in case of defence organisations in UK, ministry of defence in the
country need to follow all the instruction and standard of the SI security system in the country in
order to sharing their important information within the country in more effective manner.
Standard for furnishing information system has been become one of the essential in some critical
condition of the business in more effective form. Standard of information security defines that
some of security function must be followed by the organisation in efficient form. The
organisational policies must be implemented by the organisational professionals within the
defence industry in more appropriate form (Talbot and Jakeman, 2011). With the assistance of
this standard of security, they information and human resources of the company could be
efficiently managed within the organisation environment properly.
ISO:17799
This is the most appropriate security system and guideline documentation which has been
evaluated in recent years in order to aid management and the area of information security in
which the two most appraisals option is ISO 17799, which defines that primary with process
security, they need to furnishing effective services regarding to information system within the
business environment. They need to follow the common criteria of this security standard in more
appropriate manner so that each of their information system can be executed within the business
environment in effective form (Webb, Ahmad, Maynard and Shanks, 2014). They need to make
development in some areas by which they can generate more efficient form of the services in
more effective form, so that each one of them can better use of this security system in respect to
sharing information safely within the business environment effectively. They need to proceed
some code of practice for information securities management within the organisation effectively.
This could be utilised by each organisation in order to protect their comprehensive information
security management in the firm effectively. It furnishes some of security service such as the
asset classification and control services and personal; security management services within the
organisation environment in appropriate manner. They need to manage all the services in more
effective manner so that each one of them will be able to generate more effective services in
more appropriate manner. This approach also furnish relevant access control management system
in effective form.
Risk analysis and contingency planning for the organisation:
3
proper security system and in case of defence organisations in UK, ministry of defence in the
country need to follow all the instruction and standard of the SI security system in the country in
order to sharing their important information within the country in more effective manner.
Standard for furnishing information system has been become one of the essential in some critical
condition of the business in more effective form. Standard of information security defines that
some of security function must be followed by the organisation in efficient form. The
organisational policies must be implemented by the organisational professionals within the
defence industry in more appropriate form (Talbot and Jakeman, 2011). With the assistance of
this standard of security, they information and human resources of the company could be
efficiently managed within the organisation environment properly.
ISO:17799
This is the most appropriate security system and guideline documentation which has been
evaluated in recent years in order to aid management and the area of information security in
which the two most appraisals option is ISO 17799, which defines that primary with process
security, they need to furnishing effective services regarding to information system within the
business environment. They need to follow the common criteria of this security standard in more
appropriate manner so that each of their information system can be executed within the business
environment in effective form (Webb, Ahmad, Maynard and Shanks, 2014). They need to make
development in some areas by which they can generate more efficient form of the services in
more effective form, so that each one of them can better use of this security system in respect to
sharing information safely within the business environment effectively. They need to proceed
some code of practice for information securities management within the organisation effectively.
This could be utilised by each organisation in order to protect their comprehensive information
security management in the firm effectively. It furnishes some of security service such as the
asset classification and control services and personal; security management services within the
organisation environment in appropriate manner. They need to manage all the services in more
effective manner so that each one of them will be able to generate more effective services in
more appropriate manner. This approach also furnish relevant access control management system
in effective form.
Risk analysis and contingency planning for the organisation:
3

Every organisation needs for risk assessment proper planning in order to simply
purchasing liability insurance in complex manner. Risk assessment and contingency planning is
the method which determines the risks of a business which is faces by them in more appropriate
manner, they need to make development in some areas by which risk assessment can be executed
in more relevant form. In terms of risk assessment within the business organisation, they need to
prepare a proper contingency planning in respect to risk analysis in the industry effectively. This
could be beneficial for that time, in which the company is going to organise new projection in the
company in more appropriate manner (Krutz and Vines, 2010). Risk analysis helps the business
professionals appropriately in order to sustain in the market in more relevant form. Securities
issues is one of the most vital risk for ministry of defence in the UK, which need to share most of
their confidential information regarding to the country defence exercise effectively. The
organisational professionals need to recognise the level and identification of the risk in proper
manner so that each one of them can get more appropriate issues and barriers which comes in
against in the form of security in the defence industry efficiently. The business threats could find
in some essential business elements such as human resources, operational departments, technical
issues and political issues and project based organisation in the industry. There are multiple
variety of techniques are presented by which the organisational professionals can determine the
risk in the business in more relevant form these ways of risk assessment is that. They have some
issues by which they can generate more relevant manner in terms of proper development in some
areas by which they can generate more effective sort. The standard techniques of risk assessment
can be examined with the help of appropriate manner of risk analysis in the industry (Amoore,
2011). The defence industry need to identify its appropriate risk according to some effective
tools and planning of risk assessment within the industry effectively. They need to make
appropriate development in some areas by which they can get more efficient services in the
industry in more relevant form. Once the risk has been identified,, they need to examine the
criteria by which they can get more relevant manner of risk resolution in the company
effectively. The general techniques of risk reduction in the company is that, they have major part
of the issues by which they can get avoid the risk within the business environment in more
relevant form. The organisational professional need to formulate contingency planning in respect
to appropriate resolution of risk management in the company in relevant form. So it will be more
beneficial for the organisation in order to having an appropriate contingency plan for dealing
4
purchasing liability insurance in complex manner. Risk assessment and contingency planning is
the method which determines the risks of a business which is faces by them in more appropriate
manner, they need to make development in some areas by which risk assessment can be executed
in more relevant form. In terms of risk assessment within the business organisation, they need to
prepare a proper contingency planning in respect to risk analysis in the industry effectively. This
could be beneficial for that time, in which the company is going to organise new projection in the
company in more appropriate manner (Krutz and Vines, 2010). Risk analysis helps the business
professionals appropriately in order to sustain in the market in more relevant form. Securities
issues is one of the most vital risk for ministry of defence in the UK, which need to share most of
their confidential information regarding to the country defence exercise effectively. The
organisational professionals need to recognise the level and identification of the risk in proper
manner so that each one of them can get more appropriate issues and barriers which comes in
against in the form of security in the defence industry efficiently. The business threats could find
in some essential business elements such as human resources, operational departments, technical
issues and political issues and project based organisation in the industry. There are multiple
variety of techniques are presented by which the organisational professionals can determine the
risk in the business in more relevant form these ways of risk assessment is that. They have some
issues by which they can generate more relevant manner in terms of proper development in some
areas by which they can generate more effective sort. The standard techniques of risk assessment
can be examined with the help of appropriate manner of risk analysis in the industry (Amoore,
2011). The defence industry need to identify its appropriate risk according to some effective
tools and planning of risk assessment within the industry effectively. They need to make
appropriate development in some areas by which they can get more efficient services in the
industry in more relevant form. Once the risk has been identified,, they need to examine the
criteria by which they can get more relevant manner of risk resolution in the company
effectively. The general techniques of risk reduction in the company is that, they have major part
of the issues by which they can get avoid the risk within the business environment in more
relevant form. The organisational professional need to formulate contingency planning in respect
to appropriate resolution of risk management in the company in relevant form. So it will be more
beneficial for the organisation in order to having an appropriate contingency plan for dealing
4
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

better in the plan by which they can generate more effective form in the services in relevant
form. Proper contingency planning concerning about to current risk in the company can generate
more relevant services in the company in more effective form. They must need to make
communication of plan in the organisation in relevant manner so that effective outcomes can be
gained.
Analysis of IS threats and vulnerabilities and tools including social engineering
Risk management plan is threats' analysis in the company in more relevant form. They
need to know about to the relevant areas by which they can identify the relevant form of IS
threats in the industry efficiently. A threats' assessment is one of the approach in which they can
generate more relevant services in the company in effective form. These threats could be in form
of natural, criminal, terrorists and accidental etc. the assessment of the threats could be in
effective form so that each one of them can generate more relevant services within the business
environment efficiently (Calder and Watkins, 2010). Contingency approach of the firm need to
make implemented in the company in more relevant manner so that each one of them can get
more appropriate issues in he in the company. There are some of effective security threats can
be find out within the business environment in efficient form. The organisation professional need
to maintain the defence industry security standard according to IS security system provision in
the company. Potential threats can be find out within the organisation in effective form., so that
each one of them can get more relevant issues to them in appropriate form. There are varied form
of risk threats can be find out by the business professionals effectively and they need to analyse
them within the industry efficiently. The vulnerabilities' assessment is also necessary part for
each organisation within the business in more efficient form. The organisation manager need to
identify the potential impact of losses on the organisational environment and according to them
take action to manager them within the business environment efficiently. Most of the IS security
has been attracted by cyber criminals to manipulate important information of security in relevant
manner. They major damaged of information securities is that, critical information about defence
in the country might be manipulated by the organisational department in effective form. So they
can get more appropriate issues in the business environment in effective form (Turral,Burke and
Faurès, 2011). The social engineering toolkit is specifically designed for the human factors in the
industry. These could attack on online basis by which they can generate more relevant services in
effective form. They need to know that, they have some areas by which they can generate more
5
form. Proper contingency planning concerning about to current risk in the company can generate
more relevant services in the company in more effective form. They must need to make
communication of plan in the organisation in relevant manner so that effective outcomes can be
gained.
Analysis of IS threats and vulnerabilities and tools including social engineering
Risk management plan is threats' analysis in the company in more relevant form. They
need to know about to the relevant areas by which they can identify the relevant form of IS
threats in the industry efficiently. A threats' assessment is one of the approach in which they can
generate more relevant services in the company in effective form. These threats could be in form
of natural, criminal, terrorists and accidental etc. the assessment of the threats could be in
effective form so that each one of them can generate more relevant services within the business
environment efficiently (Calder and Watkins, 2010). Contingency approach of the firm need to
make implemented in the company in more relevant manner so that each one of them can get
more appropriate issues in he in the company. There are some of effective security threats can
be find out within the business environment in efficient form. The organisation professional need
to maintain the defence industry security standard according to IS security system provision in
the company. Potential threats can be find out within the organisation in effective form., so that
each one of them can get more relevant issues to them in appropriate form. There are varied form
of risk threats can be find out by the business professionals effectively and they need to analyse
them within the industry efficiently. The vulnerabilities' assessment is also necessary part for
each organisation within the business in more efficient form. The organisation manager need to
identify the potential impact of losses on the organisational environment and according to them
take action to manager them within the business environment efficiently. Most of the IS security
has been attracted by cyber criminals to manipulate important information of security in relevant
manner. They major damaged of information securities is that, critical information about defence
in the country might be manipulated by the organisational department in effective form. So they
can get more appropriate issues in the business environment in effective form (Turral,Burke and
Faurès, 2011). The social engineering toolkit is specifically designed for the human factors in the
industry. These could attack on online basis by which they can generate more relevant services in
effective form. They need to know that, they have some areas by which they can generate more
5
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

effective services in the company in effective form. The tool could be used in terms of identify
the website attack vectors effectively within the organisation environment effectively.
CONCLUSION
From the above analysis, it is concluded that, ministry of defence in the country, they
need to follow ISO 17799 standard in the organisation in relevant manner so that, the company
will be able to generate more effective services in efficient form. Moreover, it is concluded that,
the organisational professional need to follow the security standard in order to control risk in the
organisation in effective form so that effective development can be generate in efficient form.
6
the website attack vectors effectively within the organisation environment effectively.
CONCLUSION
From the above analysis, it is concluded that, ministry of defence in the country, they
need to follow ISO 17799 standard in the organisation in relevant manner so that, the company
will be able to generate more effective services in efficient form. Moreover, it is concluded that,
the organisational professional need to follow the security standard in order to control risk in the
organisation in effective form so that effective development can be generate in efficient form.
6

REFERENCES
Books and Journals
Amoore, L., 2011. Data derivatives: On the emergence of a security risk calculus for our times.
Calder, A. and Watkins, S. G., 2010. Information security risk management for
ISO27001/ISO27002. It Governance Ltd.Theory, Culture & Society. 28. 6. pp. 24-43.
Krutz, R. L. and Vines, R. D., 2010. Cloud security: A comprehensive guide to secure cloud
computing. Wiley Publishing.
Peltier, T. R., 2010. Information security risk analysis. Auerbach publications.
Poolsappasit, N., Dewri, R. and Ray, I., 2012. Dynamic security risk management using bayesian
attack graphs. IEEE Transactions on Dependable and Secure Computing. 9. 1. pp. 61-74.
Spears, J. L. and Barki, H., 2010. User participation in information systems security risk
management. MIS quarterly. pp. 503-522.
Stallings, W., Brown, L., Bauer, M. D. and Bhattacharjee, A. K., 2012. Computer security:
principles and practice (pp. 978-0). Pearson Education.
Talbot, J. and Jakeman, M., 2011. Security risk management body of knowledge (Vol. 69). John
Wiley & Sons.
Turral, H., Burke, J. J. and Faurès, J. M., 2011. Climate change, water and food security. Rome,
Italy: Food and Agriculture Organization of the United Nations.
Webb, J., Ahmad, A., Maynard, S. B. and Shanks, G., 2014. A situation awareness model for
information security risk management. Computers & security. 44. pp. 1-15.
7
Books and Journals
Amoore, L., 2011. Data derivatives: On the emergence of a security risk calculus for our times.
Calder, A. and Watkins, S. G., 2010. Information security risk management for
ISO27001/ISO27002. It Governance Ltd.Theory, Culture & Society. 28. 6. pp. 24-43.
Krutz, R. L. and Vines, R. D., 2010. Cloud security: A comprehensive guide to secure cloud
computing. Wiley Publishing.
Peltier, T. R., 2010. Information security risk analysis. Auerbach publications.
Poolsappasit, N., Dewri, R. and Ray, I., 2012. Dynamic security risk management using bayesian
attack graphs. IEEE Transactions on Dependable and Secure Computing. 9. 1. pp. 61-74.
Spears, J. L. and Barki, H., 2010. User participation in information systems security risk
management. MIS quarterly. pp. 503-522.
Stallings, W., Brown, L., Bauer, M. D. and Bhattacharjee, A. K., 2012. Computer security:
principles and practice (pp. 978-0). Pearson Education.
Talbot, J. and Jakeman, M., 2011. Security risk management body of knowledge (Vol. 69). John
Wiley & Sons.
Turral, H., Burke, J. J. and Faurès, J. M., 2011. Climate change, water and food security. Rome,
Italy: Food and Agriculture Organization of the United Nations.
Webb, J., Ahmad, A., Maynard, S. B. and Shanks, G., 2014. A situation awareness model for
information security risk management. Computers & security. 44. pp. 1-15.
7
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 9
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





