IS Security and Risk Management Report: Health Sector Threats
VerifiedAdded on 2023/01/09
|13
|3313
|58
Report
AI Summary
This report provides a comprehensive analysis of Information Security (IS) and Risk Management within the Australian healthcare sector. It begins by identifying and categorizing various threats faced by healthcare organizations, including Advanced Persistent Threats (APT), remote access scams, wire fraud emails, SMS phishing scams, and relief payment scams. The report then details the different categories of assets within a healthcare system, such as people, procedures, data and information, software, hardware, and networking, and discusses how each asset can be vulnerable to cyberattacks. Furthermore, it prioritizes these threats based on their potential impact and explores the application of security principles with cyber security mitigation and control recommendations proposed by ACSC for health. The analysis covers Application Control, Patch Application, and other critical areas to enhance the security posture of healthcare organizations, providing valuable insights into safeguarding sensitive patient data and maintaining the integrity of healthcare systems.

IS Security and Risk Management
1
1
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Contents
INTRODUCTION...........................................................................................................................3
MAIN BODY..................................................................................................................................3
Identify and examine all types of threat facing the Australian health sector organizations and
summarise into table....................................................................................................................3
Identifying the categories assets which include the different elements of health organization’s
system..........................................................................................................................................5
Identifying and prioritizing threats..............................................................................................7
Analysis of principles with cyber security mitigation and control recommendations proposed
by ACSC for health...................................................................................................................10
CONCLUSION..............................................................................................................................12
REFERENCES..............................................................................................................................13
2
INTRODUCTION...........................................................................................................................3
MAIN BODY..................................................................................................................................3
Identify and examine all types of threat facing the Australian health sector organizations and
summarise into table....................................................................................................................3
Identifying the categories assets which include the different elements of health organization’s
system..........................................................................................................................................5
Identifying and prioritizing threats..............................................................................................7
Analysis of principles with cyber security mitigation and control recommendations proposed
by ACSC for health...................................................................................................................10
CONCLUSION..............................................................................................................................12
REFERENCES..............................................................................................................................13
2

INTRODUCTION
Information security risk management is based on the process that mainly used for managing
different risk which associated with use of information technology. Generally, it involves the
different processes such as identifying, assessing and treating the risks to maintain
confidentiality, integrity as well as availability of organizations assets. The primary goal of this
process is to perform the significant role while treating the risk in accordance with health care
organizations.
The documentation will discuss about the different type of threats facing the Australian
health sectors organizations. It will identify the different categories of assets which mainly
include the elements of organizational system. Furthermore, there are different type of threats
performed the action against the assets and impact on the overall processes. However, the
documentation will describe five different fundamental security principles to manage or control
cyber security mitigation process with health organization’s sector.
MAIN BODY
Identify and examine all types of threat facing the Australian health sector organizations and
summarise into table.
According to given case study, it has identified that virus continues impact on the health
sector across the global world. APT groups may be seeking information, data and intellectual
properly related the vaccine development, treatments. The Australian health as well as research
sector could be greater deals with the malicious APT groups (World Health Organization, 2019).
Due to increase the pressure place within healthcare sector to respond towards Covid-19
Pandemic. It is consider one of the most critical issue that increases the malicious cyber threats
and directly impact on the entire business system.
Advanced persistent threat (APT)
Advanced persistent threat is important term which given into the sophisticated and well-
resourced type of malicious cyber adversary. This is commonly associated with the nation and
seek to comprise with network to obtain policy, defence, legal and security information for
strategy advantage (Offner, Sitnikova and MacIntyre, 2020). Malicious cyber actors are actively
targeting the individuals and Australian organizations with COVID-19 related scam, phishing
3
Information security risk management is based on the process that mainly used for managing
different risk which associated with use of information technology. Generally, it involves the
different processes such as identifying, assessing and treating the risks to maintain
confidentiality, integrity as well as availability of organizations assets. The primary goal of this
process is to perform the significant role while treating the risk in accordance with health care
organizations.
The documentation will discuss about the different type of threats facing the Australian
health sectors organizations. It will identify the different categories of assets which mainly
include the elements of organizational system. Furthermore, there are different type of threats
performed the action against the assets and impact on the overall processes. However, the
documentation will describe five different fundamental security principles to manage or control
cyber security mitigation process with health organization’s sector.
MAIN BODY
Identify and examine all types of threat facing the Australian health sector organizations and
summarise into table.
According to given case study, it has identified that virus continues impact on the health
sector across the global world. APT groups may be seeking information, data and intellectual
properly related the vaccine development, treatments. The Australian health as well as research
sector could be greater deals with the malicious APT groups (World Health Organization, 2019).
Due to increase the pressure place within healthcare sector to respond towards Covid-19
Pandemic. It is consider one of the most critical issue that increases the malicious cyber threats
and directly impact on the entire business system.
Advanced persistent threat (APT)
Advanced persistent threat is important term which given into the sophisticated and well-
resourced type of malicious cyber adversary. This is commonly associated with the nation and
seek to comprise with network to obtain policy, defence, legal and security information for
strategy advantage (Offner, Sitnikova and MacIntyre, 2020). Malicious cyber actors are actively
targeting the individuals and Australian organizations with COVID-19 related scam, phishing
3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

emails. Generally, APT is mainly targeting the Australian health care organizations and system
to access the personal information or data through malicious attacks.
These are considered the incidents which likely to increase the problem or issue of
Australian health care organizations. There are different threats facing the Australian health
sector organizations.
Remote access scams: it is the most commonly threat that mainly occurred during
COVID-19, according to report, it has identified that receive large number of remote
access scams. Generally, it is targeting the people who will work from home. Many
individual health care professionals are conducted the meeting with team members so that
it has chances to attempt the remote access (Offner, Sitnikova and MacIntyre, 2020). In
this way, it can easily access the confidential information or data about medicine,
vaccine. This type of threat may be occurred to access computer or devices while
compromises the personal accounts of health officers.
Wire fraud email: It is also another threat which mainly faced by Australian health care
organizations, individuals. According to survey, it has identified that one client had
received a COVID-19 themed fraud email which include the health care organizations.
Usually, Australian health organizations are managed or comprised by manager and then
send to invoice themed mail to client. But the attacker can easily hack the details while
sending information to client (Offner, Sitnikova and MacIntyre, 2020). In this way, it is
considered as unauthorised activities performed by hackers in order to increase problem
or issue for both client and health organization in term of security or privacy.
SMS phishing scam: this type of threat will use SMS phishing messages which offering
where to get tested for COVID-19. Sometimes, SMS may appears to come from “Gov.”,
whereas it can easily identify the malicious link to get tested in local areas (Offner,
Sitnikova and MacIntyre, 2020). This is completely fraud which directly affecting on the
device and access sensitive information. ACSC always aware about the SMS scam
because this can be sender identification of my Gov.
Relief payment scam: The phishing email is mainly pretending to be from world health
organization and prompts to open the attachment for advice on safety measurement and
4
to access the personal information or data through malicious attacks.
These are considered the incidents which likely to increase the problem or issue of
Australian health care organizations. There are different threats facing the Australian health
sector organizations.
Remote access scams: it is the most commonly threat that mainly occurred during
COVID-19, according to report, it has identified that receive large number of remote
access scams. Generally, it is targeting the people who will work from home. Many
individual health care professionals are conducted the meeting with team members so that
it has chances to attempt the remote access (Offner, Sitnikova and MacIntyre, 2020). In
this way, it can easily access the confidential information or data about medicine,
vaccine. This type of threat may be occurred to access computer or devices while
compromises the personal accounts of health officers.
Wire fraud email: It is also another threat which mainly faced by Australian health care
organizations, individuals. According to survey, it has identified that one client had
received a COVID-19 themed fraud email which include the health care organizations.
Usually, Australian health organizations are managed or comprised by manager and then
send to invoice themed mail to client. But the attacker can easily hack the details while
sending information to client (Offner, Sitnikova and MacIntyre, 2020). In this way, it is
considered as unauthorised activities performed by hackers in order to increase problem
or issue for both client and health organization in term of security or privacy.
SMS phishing scam: this type of threat will use SMS phishing messages which offering
where to get tested for COVID-19. Sometimes, SMS may appears to come from “Gov.”,
whereas it can easily identify the malicious link to get tested in local areas (Offner,
Sitnikova and MacIntyre, 2020). This is completely fraud which directly affecting on the
device and access sensitive information. ACSC always aware about the SMS scam
because this can be sender identification of my Gov.
Relief payment scam: The phishing email is mainly pretending to be from world health
organization and prompts to open the attachment for advice on safety measurement and
4
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
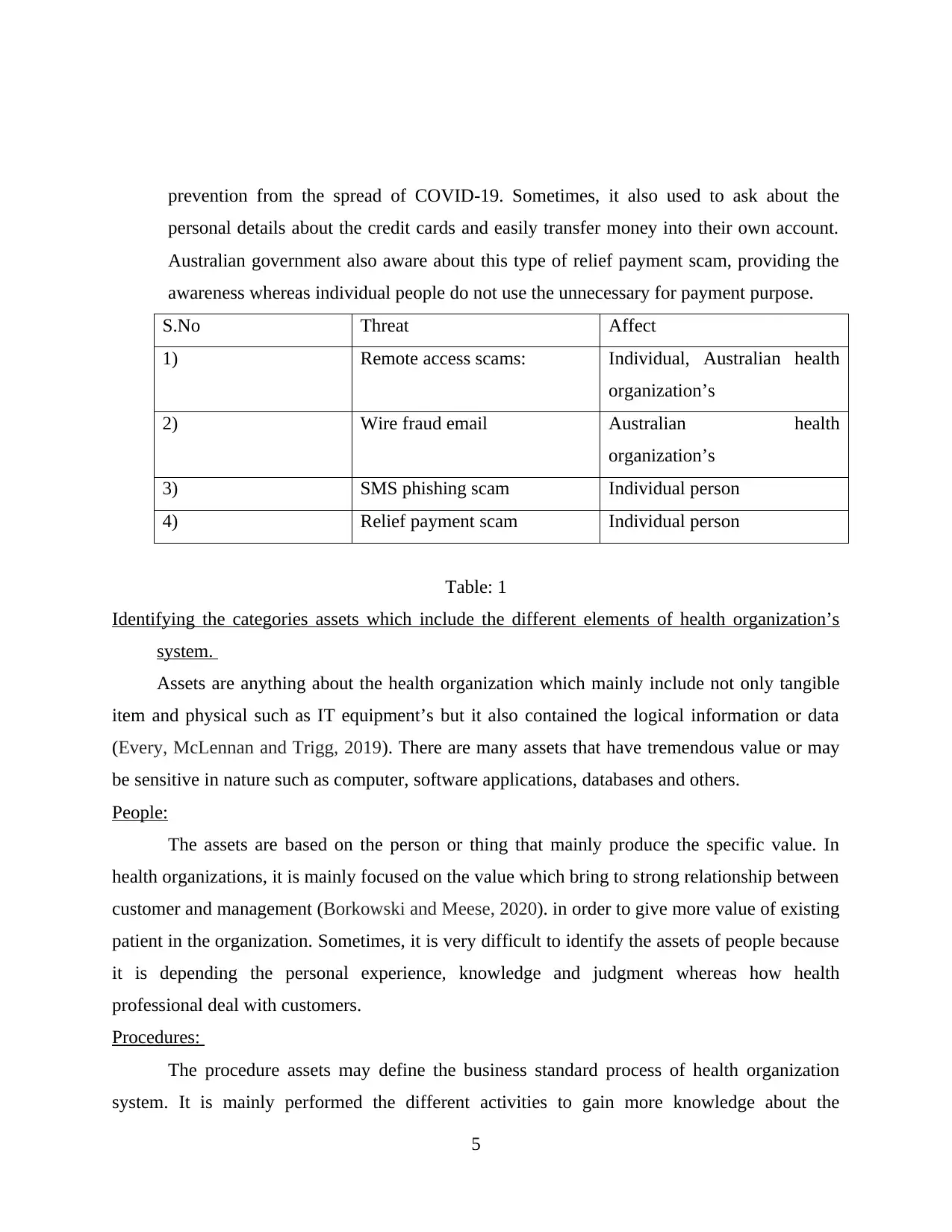
prevention from the spread of COVID-19. Sometimes, it also used to ask about the
personal details about the credit cards and easily transfer money into their own account.
Australian government also aware about this type of relief payment scam, providing the
awareness whereas individual people do not use the unnecessary for payment purpose.
S.No Threat Affect
1) Remote access scams: Individual, Australian health
organization’s
2) Wire fraud email Australian health
organization’s
3) SMS phishing scam Individual person
4) Relief payment scam Individual person
Table: 1
Identifying the categories assets which include the different elements of health organization’s
system.
Assets are anything about the health organization which mainly include not only tangible
item and physical such as IT equipment’s but it also contained the logical information or data
(Every, McLennan and Trigg, 2019). There are many assets that have tremendous value or may
be sensitive in nature such as computer, software applications, databases and others.
People:
The assets are based on the person or thing that mainly produce the specific value. In
health organizations, it is mainly focused on the value which bring to strong relationship between
customer and management (Borkowski and Meese, 2020). in order to give more value of existing
patient in the organization. Sometimes, it is very difficult to identify the assets of people because
it is depending the personal experience, knowledge and judgment whereas how health
professional deal with customers.
Procedures:
The procedure assets may define the business standard process of health organization
system. It is mainly performed the different activities to gain more knowledge about the
5
personal details about the credit cards and easily transfer money into their own account.
Australian government also aware about this type of relief payment scam, providing the
awareness whereas individual people do not use the unnecessary for payment purpose.
S.No Threat Affect
1) Remote access scams: Individual, Australian health
organization’s
2) Wire fraud email Australian health
organization’s
3) SMS phishing scam Individual person
4) Relief payment scam Individual person
Table: 1
Identifying the categories assets which include the different elements of health organization’s
system.
Assets are anything about the health organization which mainly include not only tangible
item and physical such as IT equipment’s but it also contained the logical information or data
(Every, McLennan and Trigg, 2019). There are many assets that have tremendous value or may
be sensitive in nature such as computer, software applications, databases and others.
People:
The assets are based on the person or thing that mainly produce the specific value. In
health organizations, it is mainly focused on the value which bring to strong relationship between
customer and management (Borkowski and Meese, 2020). in order to give more value of existing
patient in the organization. Sometimes, it is very difficult to identify the assets of people because
it is depending the personal experience, knowledge and judgment whereas how health
professional deal with customers.
Procedures:
The procedure assets may define the business standard process of health organization
system. It is mainly performed the different activities to gain more knowledge about the
5

inventory management, planning. Moreover, it is describing the basic purpose of business,
location about the software, hardware system. Another way, it also stored the large amount of
record so as require to update on regular basis.
Data and information:
it is mainly consider the knowledge that organised or managed as single entity. Health
organization’s always focused on the information assets in context of financial value. It may
contain large number of information about the medicine, treatment as well as patient (Every,
McLennan and Trigg, 2019). Sometimes, data may be classified, implemented to make
organization’s information assets easily identify, maintain and share to another one.
Within health organization’s system, which mainly include different assets such as
patient records, photographs, personnel information, lab results, inventories, outsourcing
contracts and research information. These are essential information that should be maintained by
different departments. In order to establish the coordination between them.
Software:
It is based on the application or program that mainly used by health organization in term
of business activities. For enterprise, it is an essential for monitoring and managing the assets. It
plays important role for using to examine the patient’s health condition. Nowadays, medical
professional have used the advanced technology to identify risk, threat. It provide the better
treatment facilities and services to improve health condition of people.
There are different software assets used by health organization’s system such as
encryption tools, clinical medical system, special medical software, financial system, HR system,
development tools (Every, McLennan and Trigg, 2019). On the other hand, different departments
have used their own running system which will provide the better facility to maintain large
amount of records in regards of patient, treatment within database system.
Hardware:
this type of components which mainly consider the assets that can be grouped into
different categories such as network, removable media, peripherals and computers. These are
considered as important which always support for performing the different activities.
6
location about the software, hardware system. Another way, it also stored the large amount of
record so as require to update on regular basis.
Data and information:
it is mainly consider the knowledge that organised or managed as single entity. Health
organization’s always focused on the information assets in context of financial value. It may
contain large number of information about the medicine, treatment as well as patient (Every,
McLennan and Trigg, 2019). Sometimes, data may be classified, implemented to make
organization’s information assets easily identify, maintain and share to another one.
Within health organization’s system, which mainly include different assets such as
patient records, photographs, personnel information, lab results, inventories, outsourcing
contracts and research information. These are essential information that should be maintained by
different departments. In order to establish the coordination between them.
Software:
It is based on the application or program that mainly used by health organization in term
of business activities. For enterprise, it is an essential for monitoring and managing the assets. It
plays important role for using to examine the patient’s health condition. Nowadays, medical
professional have used the advanced technology to identify risk, threat. It provide the better
treatment facilities and services to improve health condition of people.
There are different software assets used by health organization’s system such as
encryption tools, clinical medical system, special medical software, financial system, HR system,
development tools (Every, McLennan and Trigg, 2019). On the other hand, different departments
have used their own running system which will provide the better facility to maintain large
amount of records in regards of patient, treatment within database system.
Hardware:
this type of components which mainly consider the assets that can be grouped into
different categories such as network, removable media, peripherals and computers. These are
considered as important which always support for performing the different activities.
6
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
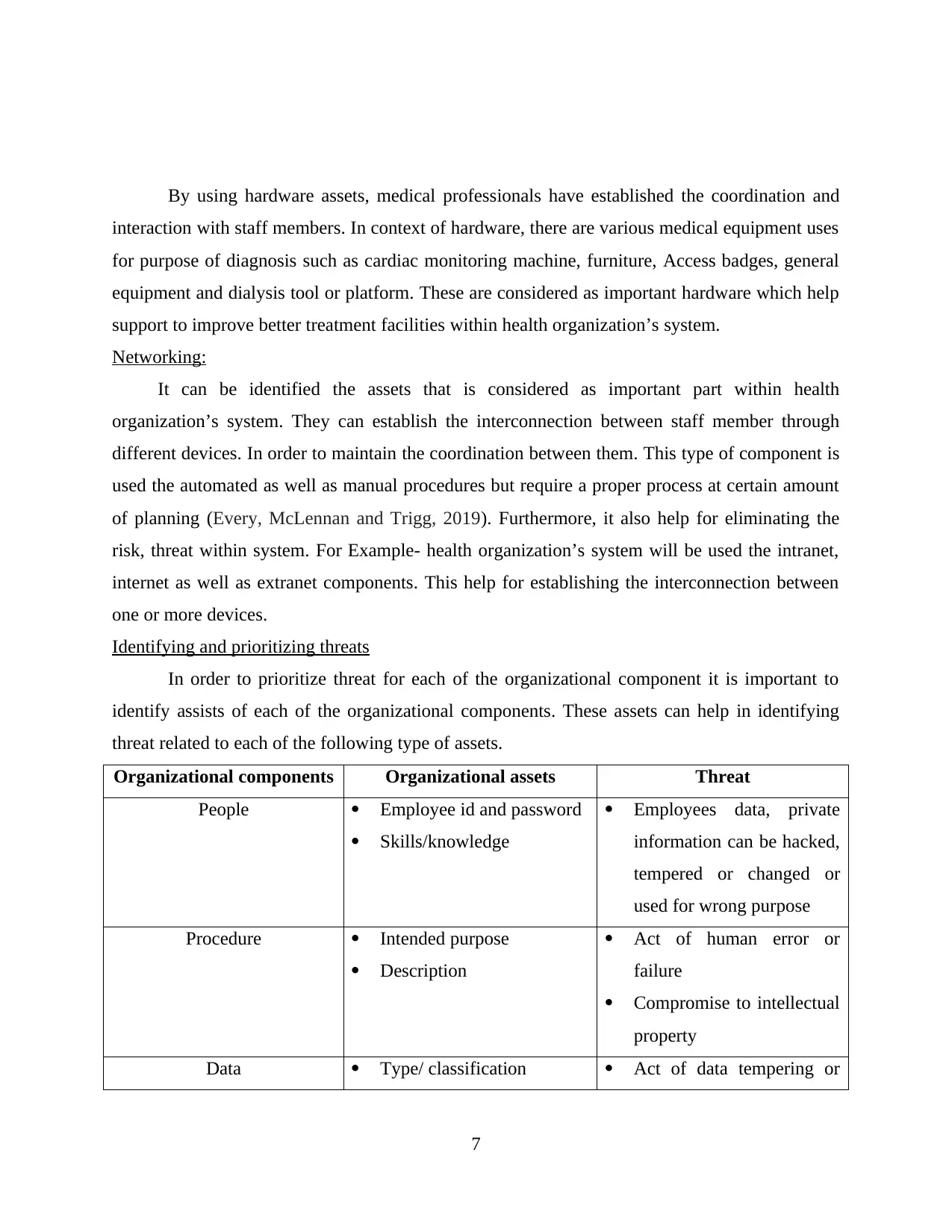
By using hardware assets, medical professionals have established the coordination and
interaction with staff members. In context of hardware, there are various medical equipment uses
for purpose of diagnosis such as cardiac monitoring machine, furniture, Access badges, general
equipment and dialysis tool or platform. These are considered as important hardware which help
support to improve better treatment facilities within health organization’s system.
Networking:
It can be identified the assets that is considered as important part within health
organization’s system. They can establish the interconnection between staff member through
different devices. In order to maintain the coordination between them. This type of component is
used the automated as well as manual procedures but require a proper process at certain amount
of planning (Every, McLennan and Trigg, 2019). Furthermore, it also help for eliminating the
risk, threat within system. For Example- health organization’s system will be used the intranet,
internet as well as extranet components. This help for establishing the interconnection between
one or more devices.
Identifying and prioritizing threats
In order to prioritize threat for each of the organizational component it is important to
identify assists of each of the organizational components. These assets can help in identifying
threat related to each of the following type of assets.
Organizational components Organizational assets Threat
People Employee id and password
Skills/knowledge
Employees data, private
information can be hacked,
tempered or changed or
used for wrong purpose
Procedure Intended purpose
Description
Act of human error or
failure
Compromise to intellectual
property
Data Type/ classification Act of data tempering or
7
interaction with staff members. In context of hardware, there are various medical equipment uses
for purpose of diagnosis such as cardiac monitoring machine, furniture, Access badges, general
equipment and dialysis tool or platform. These are considered as important hardware which help
support to improve better treatment facilities within health organization’s system.
Networking:
It can be identified the assets that is considered as important part within health
organization’s system. They can establish the interconnection between staff member through
different devices. In order to maintain the coordination between them. This type of component is
used the automated as well as manual procedures but require a proper process at certain amount
of planning (Every, McLennan and Trigg, 2019). Furthermore, it also help for eliminating the
risk, threat within system. For Example- health organization’s system will be used the intranet,
internet as well as extranet components. This help for establishing the interconnection between
one or more devices.
Identifying and prioritizing threats
In order to prioritize threat for each of the organizational component it is important to
identify assists of each of the organizational components. These assets can help in identifying
threat related to each of the following type of assets.
Organizational components Organizational assets Threat
People Employee id and password
Skills/knowledge
Employees data, private
information can be hacked,
tempered or changed or
used for wrong purpose
Procedure Intended purpose
Description
Act of human error or
failure
Compromise to intellectual
property
Data Type/ classification Act of data tempering or
7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
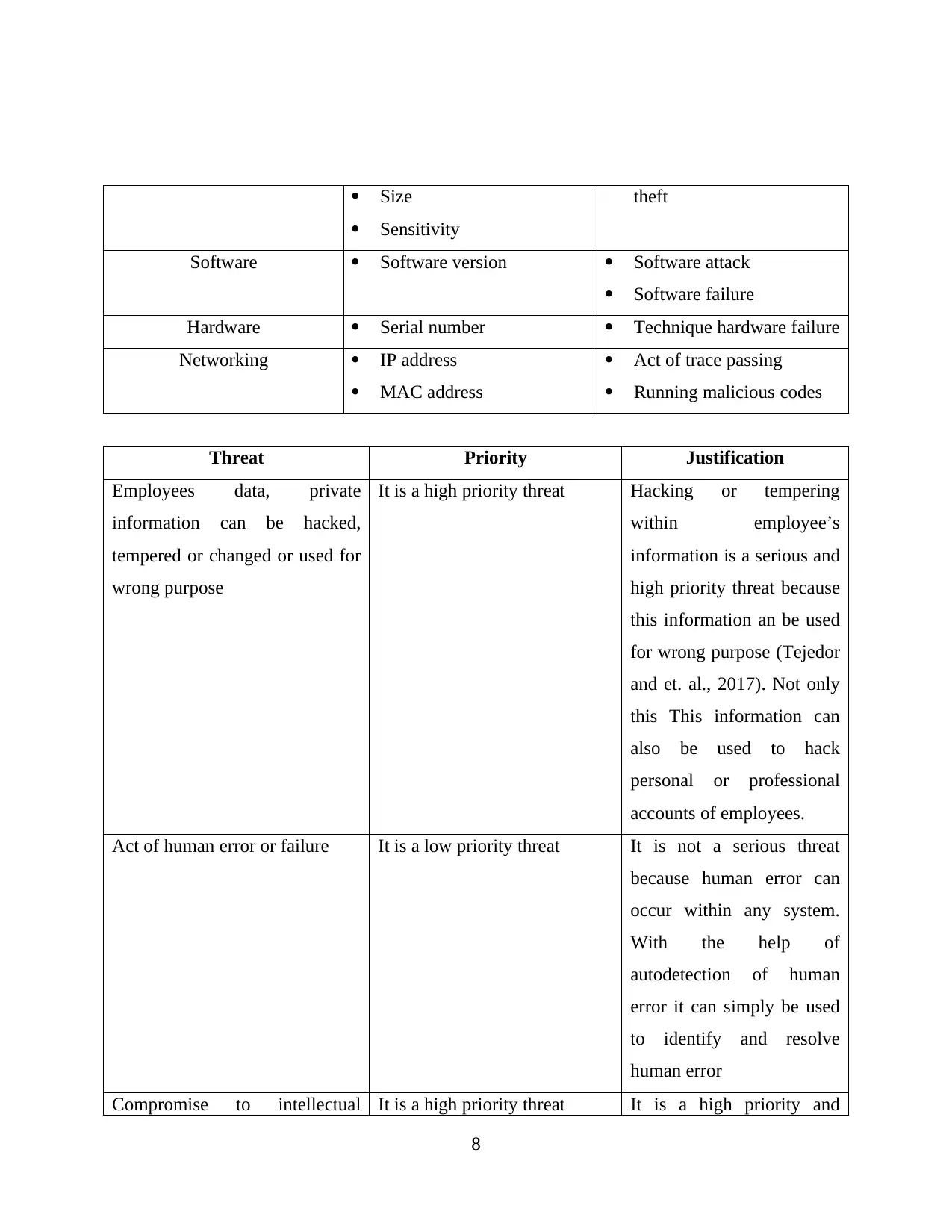
Size
Sensitivity
theft
Software Software version Software attack
Software failure
Hardware Serial number Technique hardware failure
Networking IP address
MAC address
Act of trace passing
Running malicious codes
Threat Priority Justification
Employees data, private
information can be hacked,
tempered or changed or used for
wrong purpose
It is a high priority threat Hacking or tempering
within employee’s
information is a serious and
high priority threat because
this information an be used
for wrong purpose (Tejedor
and et. al., 2017). Not only
this This information can
also be used to hack
personal or professional
accounts of employees.
Act of human error or failure It is a low priority threat It is not a serious threat
because human error can
occur within any system.
With the help of
autodetection of human
error it can simply be used
to identify and resolve
human error
Compromise to intellectual It is a high priority threat It is a high priority and
8
Sensitivity
theft
Software Software version Software attack
Software failure
Hardware Serial number Technique hardware failure
Networking IP address
MAC address
Act of trace passing
Running malicious codes
Threat Priority Justification
Employees data, private
information can be hacked,
tempered or changed or used for
wrong purpose
It is a high priority threat Hacking or tempering
within employee’s
information is a serious and
high priority threat because
this information an be used
for wrong purpose (Tejedor
and et. al., 2017). Not only
this This information can
also be used to hack
personal or professional
accounts of employees.
Act of human error or failure It is a low priority threat It is not a serious threat
because human error can
occur within any system.
With the help of
autodetection of human
error it can simply be used
to identify and resolve
human error
Compromise to intellectual It is a high priority threat It is a high priority and
8
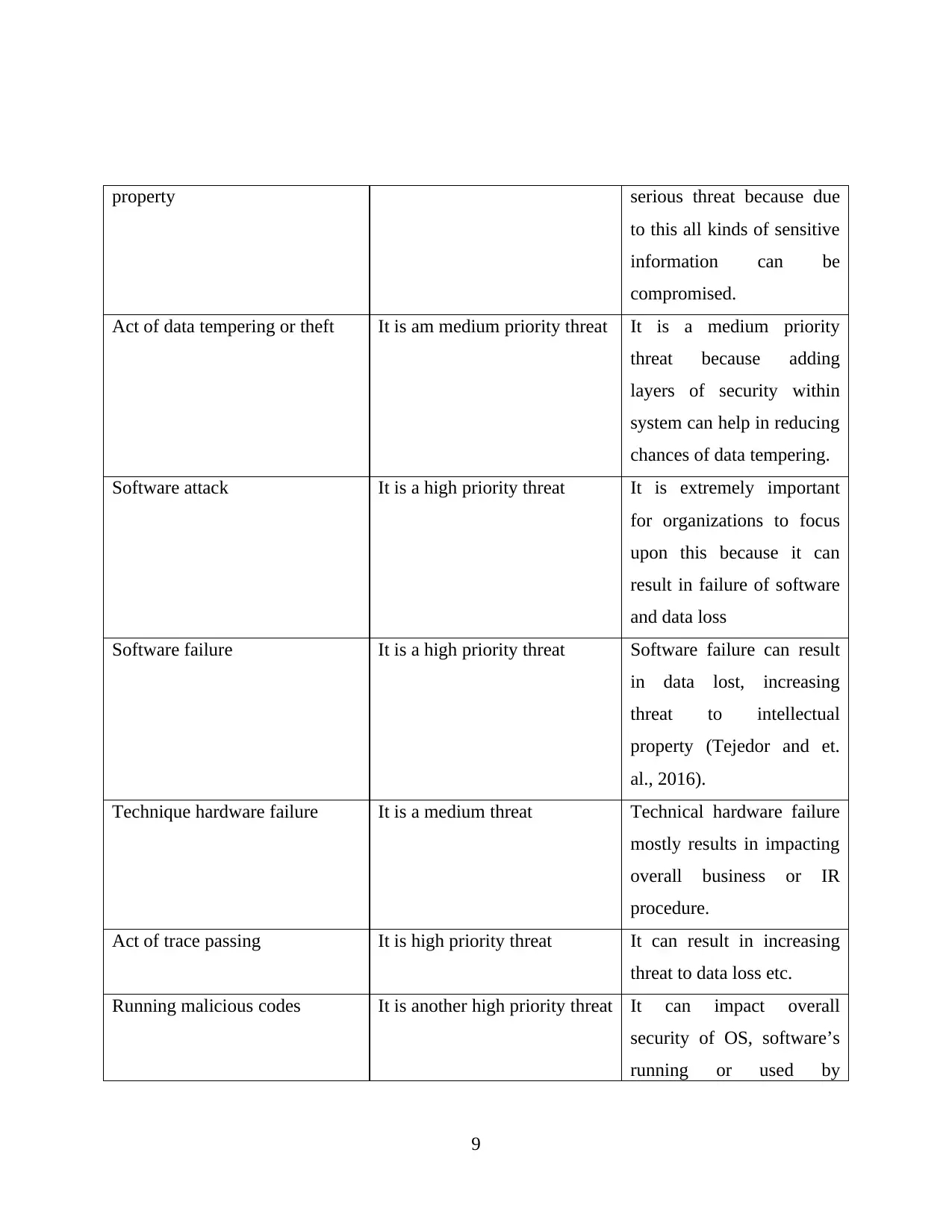
property serious threat because due
to this all kinds of sensitive
information can be
compromised.
Act of data tempering or theft It is am medium priority threat It is a medium priority
threat because adding
layers of security within
system can help in reducing
chances of data tempering.
Software attack It is a high priority threat It is extremely important
for organizations to focus
upon this because it can
result in failure of software
and data loss
Software failure It is a high priority threat Software failure can result
in data lost, increasing
threat to intellectual
property (Tejedor and et.
al., 2016).
Technique hardware failure It is a medium threat Technical hardware failure
mostly results in impacting
overall business or IR
procedure.
Act of trace passing It is high priority threat It can result in increasing
threat to data loss etc.
Running malicious codes It is another high priority threat It can impact overall
security of OS, software’s
running or used by
9
to this all kinds of sensitive
information can be
compromised.
Act of data tempering or theft It is am medium priority threat It is a medium priority
threat because adding
layers of security within
system can help in reducing
chances of data tempering.
Software attack It is a high priority threat It is extremely important
for organizations to focus
upon this because it can
result in failure of software
and data loss
Software failure It is a high priority threat Software failure can result
in data lost, increasing
threat to intellectual
property (Tejedor and et.
al., 2016).
Technique hardware failure It is a medium threat Technical hardware failure
mostly results in impacting
overall business or IR
procedure.
Act of trace passing It is high priority threat It can result in increasing
threat to data loss etc.
Running malicious codes It is another high priority threat It can impact overall
security of OS, software’s
running or used by
9
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

organization
Analysis of principles with cyber security mitigation and control recommendations proposed by
ACSC for health
ACSC has defined eight cyber security mitigation and control recommendations for
healthcare sector. Each of these eight strategies are related to or are based upon five main
fundamentals of security. All the eight strategies have been explained below:
Application Control: It helps in preventing execution of any kind of malicious or unapproved
program and installers such as: .exe, Windows Script host and many more. It is related to
limiting fundamental security principle so that unauthorized or unapproved programs can be
protected and no outsider and run any kind of malicious program upon system.
Patch Applications: These kind of applications helps in protecting computer with extreme
kinds of risk and vulnerabilities within 48 hours by using latest version of each kind of
applications such as: Java, Microsoft Office, PDF viewers (Offner and et. al., 2020). It is
used for simplicity fundamental security principle because any kind of vulnerabilities within
system can create professional security issues.
Configure Microsoft office macro settings: These kind of settings helps in blocking macros
from internet so that only vetted macros from limited sources and trusted locations can only
be allowed. It is also used to allows macros only from digitally signed trusted certificates
only. It is related to layering fundamental security principle because macro settings works as
a layer that helps in working as a protection layer by limiting or protecting malicious codes
from running on the computer.
User application hardening: It is used for configuration of web browsers in order to block
flash, java, advertisements on internet. It is also used for disabling unneeded features of
Microsoft office etc. It is related to limiting fundamental security principle as it helps in
limiting or blocking advertisements, java, flash etc. due to which malicious codes upon
system can be executed.
10
Analysis of principles with cyber security mitigation and control recommendations proposed by
ACSC for health
ACSC has defined eight cyber security mitigation and control recommendations for
healthcare sector. Each of these eight strategies are related to or are based upon five main
fundamentals of security. All the eight strategies have been explained below:
Application Control: It helps in preventing execution of any kind of malicious or unapproved
program and installers such as: .exe, Windows Script host and many more. It is related to
limiting fundamental security principle so that unauthorized or unapproved programs can be
protected and no outsider and run any kind of malicious program upon system.
Patch Applications: These kind of applications helps in protecting computer with extreme
kinds of risk and vulnerabilities within 48 hours by using latest version of each kind of
applications such as: Java, Microsoft Office, PDF viewers (Offner and et. al., 2020). It is
used for simplicity fundamental security principle because any kind of vulnerabilities within
system can create professional security issues.
Configure Microsoft office macro settings: These kind of settings helps in blocking macros
from internet so that only vetted macros from limited sources and trusted locations can only
be allowed. It is also used to allows macros only from digitally signed trusted certificates
only. It is related to layering fundamental security principle because macro settings works as
a layer that helps in working as a protection layer by limiting or protecting malicious codes
from running on the computer.
User application hardening: It is used for configuration of web browsers in order to block
flash, java, advertisements on internet. It is also used for disabling unneeded features of
Microsoft office etc. It is related to limiting fundamental security principle as it helps in
limiting or blocking advertisements, java, flash etc. due to which malicious codes upon
system can be executed.
10
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Restrict administrative privileges: It is used for Operating systems and applications that are
based upon user duties. It is also used for regularly revalidating all the all the needs of
privileges. It is recommended that privileged accounts should not be used for reading emails
and web browsers (Nagahawatta, Warren and Yeoh, 2019). It is related to limiting and
obscurity fundamental security principles because it helps in limiting number of people who
can access the system and makes it difficult for outsider to access the system and go inside it.
Patch operating systems: Computers with Patch OS with network devices are used for
eliminating extreme risk vulnerabilities. For this latest version OS should be used instead of
using unsupported version. It is majorly because vulnerabilities within OS are used for
compromising other kinds of security settings within the system. It is related to layering
fundamental security principle as using updated or latest patch operating system can help in
adding an additional layer so that protection of the system can be updated and defence layer
for protection of system can be updated.
Multi- factor authentication: It is used for making user authentication much stronger so that
sensitive information within system can be protected and secured. It is related to layering and
diversity because multifactor authentication works as a security layer due to which it
becomes difficult for attackers to use different techniques to attack the system.
Daily backups: It is used to ensure that information can be easily accessed even in terms of
cyber security incidents. This helps in ensuring that all the data is securely protected and
saved at a certain location even if IT infrastructure chances (Nagahawatta, Warren and Yeoh,
2019). It is related to diversity because daily backups of the information system is a kind of
layer though which information can be protected in a better and appropriate manner.
11
based upon user duties. It is also used for regularly revalidating all the all the needs of
privileges. It is recommended that privileged accounts should not be used for reading emails
and web browsers (Nagahawatta, Warren and Yeoh, 2019). It is related to limiting and
obscurity fundamental security principles because it helps in limiting number of people who
can access the system and makes it difficult for outsider to access the system and go inside it.
Patch operating systems: Computers with Patch OS with network devices are used for
eliminating extreme risk vulnerabilities. For this latest version OS should be used instead of
using unsupported version. It is majorly because vulnerabilities within OS are used for
compromising other kinds of security settings within the system. It is related to layering
fundamental security principle as using updated or latest patch operating system can help in
adding an additional layer so that protection of the system can be updated and defence layer
for protection of system can be updated.
Multi- factor authentication: It is used for making user authentication much stronger so that
sensitive information within system can be protected and secured. It is related to layering and
diversity because multifactor authentication works as a security layer due to which it
becomes difficult for attackers to use different techniques to attack the system.
Daily backups: It is used to ensure that information can be easily accessed even in terms of
cyber security incidents. This helps in ensuring that all the data is securely protected and
saved at a certain location even if IT infrastructure chances (Nagahawatta, Warren and Yeoh,
2019). It is related to diversity because daily backups of the information system is a kind of
layer though which information can be protected in a better and appropriate manner.
11

CONCLUSION
From above discussion, it concluded that Information security risk management is based on
the process that mainly used for managing different risk which associated with use of
information technology. It has summarised about the different types of threats facing the
Australian health sectors organizations. It can be determined the different categories of assets
which mainly include the elements of organizational system. Furthermore, it has found that
security threat may be performed the action against the assets and impact on the overall
processes. However, the documentation can be identifying the five fundamental security
principles to manage or control cyber security mitigation process with health organization’s
sector.
12
From above discussion, it concluded that Information security risk management is based on
the process that mainly used for managing different risk which associated with use of
information technology. It has summarised about the different types of threats facing the
Australian health sectors organizations. It can be determined the different categories of assets
which mainly include the elements of organizational system. Furthermore, it has found that
security threat may be performed the action against the assets and impact on the overall
processes. However, the documentation can be identifying the five fundamental security
principles to manage or control cyber security mitigation process with health organization’s
sector.
12
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 13
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





