ISY2003/ISY203 Information Security Report: Policy, Threats, BOQ
VerifiedAdded on 2023/06/04
|11
|2755
|383
Report
AI Summary
This report provides a comprehensive analysis of information security within the banking sector, focusing on the Bank of Queensland. It identifies stakeholders, outlines the nature of the bank's business, and proposes a strategic security policy to protect customer data. The report details potential threats and vulnerabilities, such as data breaches and misuse, and suggests mitigation strategies including robust encryption, access control, and firewall implementation. The importance of continuous system monitoring is emphasized for early threat detection and incident response. The report concludes that data security is paramount in banking and highlights the need for ongoing vigilance and proactive measures to safeguard sensitive information.

Running head: INFORMATION SECURITY
INFORMATION SECURITY
Name of the Student
Name of the University
Author Note
INFORMATION SECURITY
Name of the Student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

2INFORMATION SECURITY
Table of Contents
Introduction......................................................................................................................................3
Name of the organization chosen....................................................................................................3
Stakeholder of the organization.......................................................................................................4
Nature of business of the organization............................................................................................5
Strategic security policy..................................................................................................................6
Potential threat and vulnerability.....................................................................................................7
Mitigation of threat and vulnerability..............................................................................................8
Conclusion.......................................................................................................................................9
References......................................................................................................................................10
Table of Contents
Introduction......................................................................................................................................3
Name of the organization chosen....................................................................................................3
Stakeholder of the organization.......................................................................................................4
Nature of business of the organization............................................................................................5
Strategic security policy..................................................................................................................6
Potential threat and vulnerability.....................................................................................................7
Mitigation of threat and vulnerability..............................................................................................8
Conclusion.......................................................................................................................................9
References......................................................................................................................................10

3INFORMATION SECURITY
Introduction
In recent times it can be stated that the different types of technology are playing a very
vital role in the sector of the involvement of the framework of the working of the technology.
The sector of implementation of each of the technological aspect can be seen in more than one
area so that there can be different types of benefit which can be achieved from the
implementation sector. In most of the times it can be stated that security of the data can be stated
to be very much important due to the factor that it directly impacts the sector of the operation
which would be included into the concept (Soomro, Shah and Ahmed 2016). The security aspect
which would be involved into the concept can be stated to be one of the factors which play a
crucial role.
The main focus point relating to the report would be to take into consideration a domain
of the project and provide a critical analysis on the sector of the working. The domain which is
taken into consideration is the sector of banking. This is majorly taken into consideration due to
the factor that it is one of the domains which can be directly be linked with the aspect of the
security of the data which is prevailing into the system.
Name of the organization chosen
The organization which is chosen in the sector of the report is the Bank of Queensland.
The bank is located in Australia (Peters and Panayi 2016). The main reason behind the selection
of the organization is that it directly involves different sector of working which is related to the
concept of the operation in the banking sector. There are different factors which can be included
into the concept of the working.
Introduction
In recent times it can be stated that the different types of technology are playing a very
vital role in the sector of the involvement of the framework of the working of the technology.
The sector of implementation of each of the technological aspect can be seen in more than one
area so that there can be different types of benefit which can be achieved from the
implementation sector. In most of the times it can be stated that security of the data can be stated
to be very much important due to the factor that it directly impacts the sector of the operation
which would be included into the concept (Soomro, Shah and Ahmed 2016). The security aspect
which would be involved into the concept can be stated to be one of the factors which play a
crucial role.
The main focus point relating to the report would be to take into consideration a domain
of the project and provide a critical analysis on the sector of the working. The domain which is
taken into consideration is the sector of banking. This is majorly taken into consideration due to
the factor that it is one of the domains which can be directly be linked with the aspect of the
security of the data which is prevailing into the system.
Name of the organization chosen
The organization which is chosen in the sector of the report is the Bank of Queensland.
The bank is located in Australia (Peters and Panayi 2016). The main reason behind the selection
of the organization is that it directly involves different sector of working which is related to the
concept of the operation in the banking sector. There are different factors which can be included
into the concept of the working.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
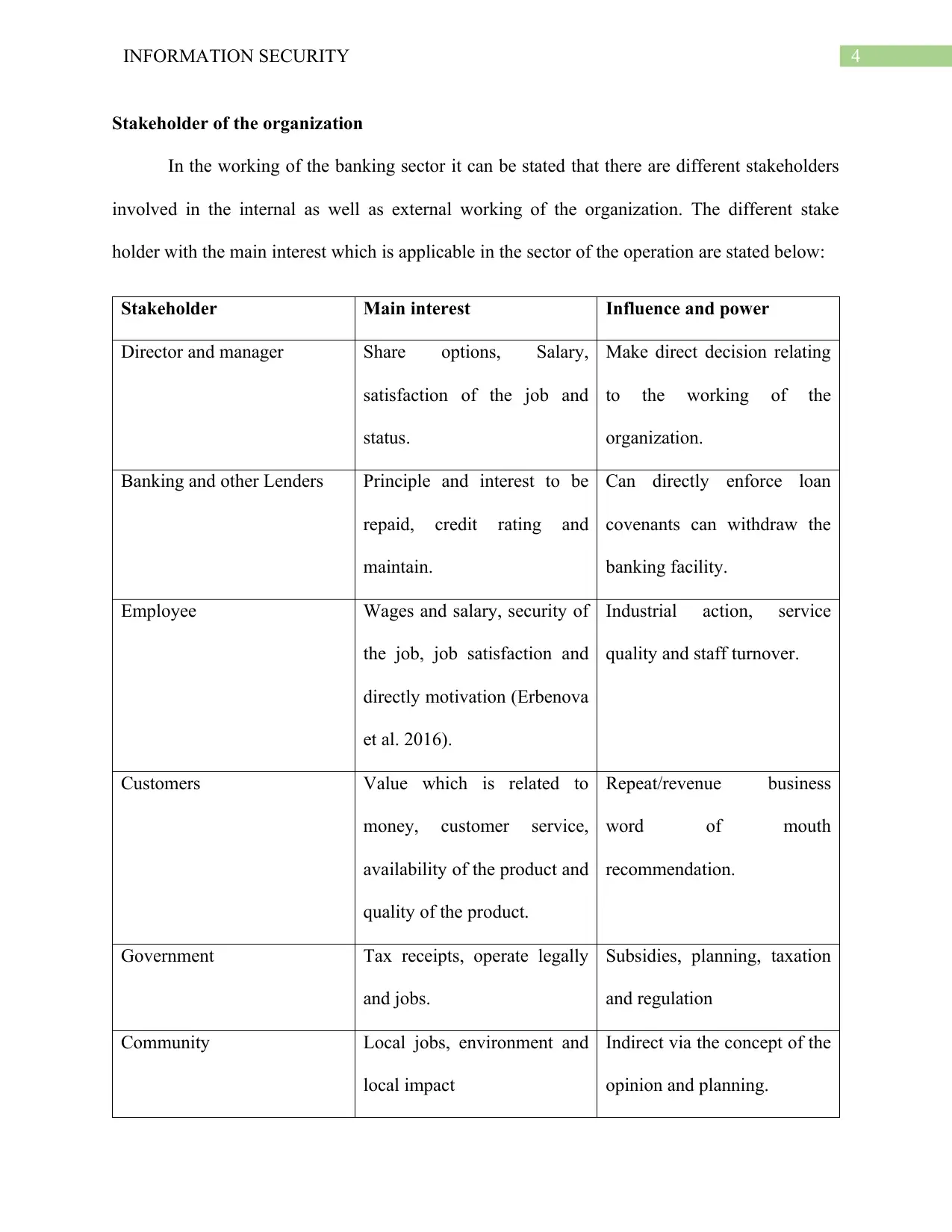
4INFORMATION SECURITY
Stakeholder of the organization
In the working of the banking sector it can be stated that there are different stakeholders
involved in the internal as well as external working of the organization. The different stake
holder with the main interest which is applicable in the sector of the operation are stated below:
Stakeholder Main interest Influence and power
Director and manager Share options, Salary,
satisfaction of the job and
status.
Make direct decision relating
to the working of the
organization.
Banking and other Lenders Principle and interest to be
repaid, credit rating and
maintain.
Can directly enforce loan
covenants can withdraw the
banking facility.
Employee Wages and salary, security of
the job, job satisfaction and
directly motivation (Erbenova
et al. 2016).
Industrial action, service
quality and staff turnover.
Customers Value which is related to
money, customer service,
availability of the product and
quality of the product.
Repeat/revenue business
word of mouth
recommendation.
Government Tax receipts, operate legally
and jobs.
Subsidies, planning, taxation
and regulation
Community Local jobs, environment and
local impact
Indirect via the concept of the
opinion and planning.
Stakeholder of the organization
In the working of the banking sector it can be stated that there are different stakeholders
involved in the internal as well as external working of the organization. The different stake
holder with the main interest which is applicable in the sector of the operation are stated below:
Stakeholder Main interest Influence and power
Director and manager Share options, Salary,
satisfaction of the job and
status.
Make direct decision relating
to the working of the
organization.
Banking and other Lenders Principle and interest to be
repaid, credit rating and
maintain.
Can directly enforce loan
covenants can withdraw the
banking facility.
Employee Wages and salary, security of
the job, job satisfaction and
directly motivation (Erbenova
et al. 2016).
Industrial action, service
quality and staff turnover.
Customers Value which is related to
money, customer service,
availability of the product and
quality of the product.
Repeat/revenue business
word of mouth
recommendation.
Government Tax receipts, operate legally
and jobs.
Subsidies, planning, taxation
and regulation
Community Local jobs, environment and
local impact
Indirect via the concept of the
opinion and planning.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

5INFORMATION SECURITY
Supplier Prompt payment, long term
contract and growth of the
purchase.
Quality, price and product
availability.
Nature of business of the organization
The nature of business which is majorly conducted by any of the banking sector and the
other non-financial institute is that the banking sector majorly provide financial service and
banking service directly to the clients. The Bank of Queensland is considered as a financial
institute which basically provides the fundamental concept of the banking service for example
providing loans and deposit. It can be stated here that there are other non-banking organization in
recent times which get engaged into the concept of the providing different types of banking
service without getting into the legal definition of the bank (Bai, Krishnamurthy and Weymuller
2018). The Bank of Queensland can be considered as a subset which is related to the financial
service industry. It can be stated that the sector of the financial intermediaries, the bank directly
plays a rule of important as institute of national finance which is every step of life deal with
human. The organization directly provides different types of options to the customer relating the
services which can be easily be adopted by an organization. In the sector of the operation it can
be stated that the working of the banking sector should be directly be intended for the point of
view of the customers so that they can easily get engaged into the concept of the working of the
technology. The nature of the business which is related to the concept can be seen in the sector of
both domestic and international (Safa and Von Solms 2016) The main aspect which should be
included into the working of the organization would be in the sector of the security of the data
which would be directly prevailing into the system.
Supplier Prompt payment, long term
contract and growth of the
purchase.
Quality, price and product
availability.
Nature of business of the organization
The nature of business which is majorly conducted by any of the banking sector and the
other non-financial institute is that the banking sector majorly provide financial service and
banking service directly to the clients. The Bank of Queensland is considered as a financial
institute which basically provides the fundamental concept of the banking service for example
providing loans and deposit. It can be stated here that there are other non-banking organization in
recent times which get engaged into the concept of the providing different types of banking
service without getting into the legal definition of the bank (Bai, Krishnamurthy and Weymuller
2018). The Bank of Queensland can be considered as a subset which is related to the financial
service industry. It can be stated that the sector of the financial intermediaries, the bank directly
plays a rule of important as institute of national finance which is every step of life deal with
human. The organization directly provides different types of options to the customer relating the
services which can be easily be adopted by an organization. In the sector of the operation it can
be stated that the working of the banking sector should be directly be intended for the point of
view of the customers so that they can easily get engaged into the concept of the working of the
technology. The nature of the business which is related to the concept can be seen in the sector of
both domestic and international (Safa and Von Solms 2016) The main aspect which should be
included into the working of the organization would be in the sector of the security of the data
which would be directly prevailing into the system.

6INFORMATION SECURITY
Strategic security policy
The security policy in the working of the banking sector can be stated as one of the
primary factor which should be taken into consideration. Some of the strategic security policy
which should be implemented within the working in the banking sector are stated below:
The data of the customer should be protected so that they can easily save their personal
data into the system of the bank (Lee et al., 2017). It can be stated that privacy aspect
should be included into the working of the bank sector due to the involvement of crucial
It should be taken into consideration that the management of the data and the sector of the
identification of data can be stated to be very much important in the sector of the
implantation of the technique.
The confidentiality of the data should be taken into consideration so that the concept of
integrity is involve into the concept of the working of the data.
Advise and assist user in the sector of the evaluation of the different factor of risk so that
they can be implementation of the sector of the choosing of the appropriate working
related to the concept.
The policy should be ensuring the aspect of the information security and the importance
of their direct involvement.
Taking into consideration the aspect of the transaction it can be stated that there are
different levels of policy which can be included into the concept (Siponen, Mahmood and
Pahnila 2014). In this case it can be stated that the concepts which is related to the approach can
be stated to be working in a predefined manner which would be directly indicating the sector of
the operation which is involved into the concept.
Strategic security policy
The security policy in the working of the banking sector can be stated as one of the
primary factor which should be taken into consideration. Some of the strategic security policy
which should be implemented within the working in the banking sector are stated below:
The data of the customer should be protected so that they can easily save their personal
data into the system of the bank (Lee et al., 2017). It can be stated that privacy aspect
should be included into the working of the bank sector due to the involvement of crucial
It should be taken into consideration that the management of the data and the sector of the
identification of data can be stated to be very much important in the sector of the
implantation of the technique.
The confidentiality of the data should be taken into consideration so that the concept of
integrity is involve into the concept of the working of the data.
Advise and assist user in the sector of the evaluation of the different factor of risk so that
they can be implementation of the sector of the choosing of the appropriate working
related to the concept.
The policy should be ensuring the aspect of the information security and the importance
of their direct involvement.
Taking into consideration the aspect of the transaction it can be stated that there are
different levels of policy which can be included into the concept (Siponen, Mahmood and
Pahnila 2014). In this case it can be stated that the concepts which is related to the approach can
be stated to be working in a predefined manner which would be directly indicating the sector of
the operation which is involved into the concept.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

7INFORMATION SECURITY
Potential threat and vulnerability
In the banking sector it can be stated that there are different types of threats and
vulnerability which can directly impact the overall performance of the banking sector. Some of
the threats which are majorly seen in the concept are stated below:
Threats to data: It can be stated here that the data which prevails in the system can be
stated to be very much crucial in the aspect of the customer. It may consist of data which are
personal including the email, user name and password (Peltier 2016). These data if goes into the
hand of intruder can be stated as very much be a problem which alter the factor of data integrity
of the data. The data would be very much secured from intruder activity due to the factor that it
directly involves the aspect of the controlling of the data.
Control access of the data: It should be a concern area to check who is directly in
control of the data. It must be taken into consideration that who has the direct access to the data
which is stored in the system. In most of the cases it can be seen that there is different person
who can directly access the data which can be related to the aspect of the removing the security
implications which are inbuilt into the sector. It should be taken into consideration that only
authorized user would be given the permission to directly access the data which is saved in the
sector.
Misuse of data: It can be stated here that the misuse of the data can be stated to be very
much important in the sector of the working of the technology. There are major functions which
can be related to the concept which should be taken into consideration. As stated in the recent
Forrester research that a great volume of data is in the sector of breach due to the factor of
involvement of the employee inadvertently misusing the direct data.
Potential threat and vulnerability
In the banking sector it can be stated that there are different types of threats and
vulnerability which can directly impact the overall performance of the banking sector. Some of
the threats which are majorly seen in the concept are stated below:
Threats to data: It can be stated here that the data which prevails in the system can be
stated to be very much crucial in the aspect of the customer. It may consist of data which are
personal including the email, user name and password (Peltier 2016). These data if goes into the
hand of intruder can be stated as very much be a problem which alter the factor of data integrity
of the data. The data would be very much secured from intruder activity due to the factor that it
directly involves the aspect of the controlling of the data.
Control access of the data: It should be a concern area to check who is directly in
control of the data. It must be taken into consideration that who has the direct access to the data
which is stored in the system. In most of the cases it can be seen that there is different person
who can directly access the data which can be related to the aspect of the removing the security
implications which are inbuilt into the sector. It should be taken into consideration that only
authorized user would be given the permission to directly access the data which is saved in the
sector.
Misuse of data: It can be stated here that the misuse of the data can be stated to be very
much important in the sector of the working of the technology. There are major functions which
can be related to the concept which should be taken into consideration. As stated in the recent
Forrester research that a great volume of data is in the sector of breach due to the factor of
involvement of the employee inadvertently misusing the direct data.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

8INFORMATION SECURITY
Mitigation of threat and vulnerability
Standard of working
The organization which is taken into consideration which is the Bank of Queensland
imposes strictest standard relating to the working. One of the factor of implementation which is
done in the sector is the 128-bit system encryption which is the highest level of security which
can be imposed. The aspect of providing a secured password can be stated to be one of the most
primary factor which is related to the working of the concept. The password should always have
a combination which cannot be retrieved by any person especially the intruders. Few of the
points which can be stated in context of the password setting are stated below:
Changing of the spelling of few words.
Join different words together which would be involving some complication in the
password.
Use of character which are not usual implemented.
Implementation of scanner
Implementation of scanner which is related to the data which is being processed should
be included into the working of the banking sector. This would be beneficial in the sector of the
restricting the entry point of the data. This majorly means that the access point which is related to
the interaction of the system with the customers so that customer can enjoy different types of
services related to financial aspect.
Implementation of Firewall
The implementation of the firewall can be stated to be another control mechanism which
can be focused which would be directly altering the data which is present in the system. The
Mitigation of threat and vulnerability
Standard of working
The organization which is taken into consideration which is the Bank of Queensland
imposes strictest standard relating to the working. One of the factor of implementation which is
done in the sector is the 128-bit system encryption which is the highest level of security which
can be imposed. The aspect of providing a secured password can be stated to be one of the most
primary factor which is related to the working of the concept. The password should always have
a combination which cannot be retrieved by any person especially the intruders. Few of the
points which can be stated in context of the password setting are stated below:
Changing of the spelling of few words.
Join different words together which would be involving some complication in the
password.
Use of character which are not usual implemented.
Implementation of scanner
Implementation of scanner which is related to the data which is being processed should
be included into the working of the banking sector. This would be beneficial in the sector of the
restricting the entry point of the data. This majorly means that the access point which is related to
the interaction of the system with the customers so that customer can enjoy different types of
services related to financial aspect.
Implementation of Firewall
The implementation of the firewall can be stated to be another control mechanism which
can be focused which would be directly altering the data which is present in the system. The

9INFORMATION SECURITY
control aspect is implemented by a manner in which the packets would be checked before it is
allowed to be saved into the concept of the technology or the sector. In most of the sector it can
be stated that the quality of data which would be existing in the system should be taken care of
so that the system would be very much safe in the sector of the operation which is involved into
the concept.
Monitoring of the system
The sector of monitoring of the system can be stated as one of the factor which can be
used in the sector of the detection of any abnormal activity in the concept of the system. The
monitoring would be beneficial in the sector of the early detection of the different threats which
can be seen in the sector (Fuller 2016). The early detection of the threat can be beneficial in the
sector of implementing a mitigation plan which is related to the concept so that it does not
impact the overall working of the system.
Conclusion
The report can be concluded on a note that in the domain of banking it can be stated that
the security of the data is one of the most important factor which should be focused upon. The
serious sector which is related to the concept can be on the sector of the mitigation of the
different issues which are seen in the sector of the working with the crucial information. There is
different standard which is related to the concept of the operation which can be included into the
concept which are widely discussed.
control aspect is implemented by a manner in which the packets would be checked before it is
allowed to be saved into the concept of the technology or the sector. In most of the sector it can
be stated that the quality of data which would be existing in the system should be taken care of
so that the system would be very much safe in the sector of the operation which is involved into
the concept.
Monitoring of the system
The sector of monitoring of the system can be stated as one of the factor which can be
used in the sector of the detection of any abnormal activity in the concept of the system. The
monitoring would be beneficial in the sector of the early detection of the different threats which
can be seen in the sector (Fuller 2016). The early detection of the threat can be beneficial in the
sector of implementing a mitigation plan which is related to the concept so that it does not
impact the overall working of the system.
Conclusion
The report can be concluded on a note that in the domain of banking it can be stated that
the security of the data is one of the most important factor which should be focused upon. The
serious sector which is related to the concept can be on the sector of the mitigation of the
different issues which are seen in the sector of the working with the crucial information. There is
different standard which is related to the concept of the operation which can be included into the
concept which are widely discussed.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

10INFORMATION SECURITY
References
Bai, J., Krishnamurthy, A. and Weymuller, C.H., 2018. Measuring liquidity mismatch in the
banking sector. The Journal of Finance, 73(1), pp.51-93.
Bauer, S. and Bernroider, E.W., 2017. From information security awareness to reasoned
compliant action: analyzing information security policy compliance in a large banking
organization. ACM SIGMIS Database: the DATABASE for Advances in Information
Systems, 48(3), pp.44-68.
Dehling, T., Gao, F., Schneider, S. and Sunyaev, A., 2015. Exploring the far side of mobile
health: information security and privacy of mobile health apps on iOS and Android. JMIR
mHealth and uHealth, 3(1).
Erbenova, M.M., Liu, M.Y., Kyriakos-Saad, M.N., Mejia, A.L., Gasha, J.G., Mathias, M.E.,
Norat, M.M., Fernando, M.F. and Almeida, M.Y., 2016. The withdrawal of correspondent
banking relationships: a case for policy action. International Monetary Fund.
Fuller, G.W., 2016. Introduction. In The Great Debt Transformation (pp. 1-24). Palgrave
Macmillan, New York.
Kudakwashe, L., Rumbidzai, I.C., Keith, C., Gift, M. and Kaseke, N., 2016. Challenges faced by
the Banking Sector in tapping the untapped Informal Sector Market in Zimbabwe. International
Journal of Marketing and Technology, 6(9), pp.21-38.
Lee, J., Yoo, B., Lee, H., Cha, G.D., Lee, H.S., Cho, Y., Kim, S.Y., Seo, H., Lee, W., Son, D.
and Kang, M., 2017. Ultra‐wideband multi‐Dye‐sensitized upconverting nanoparticles for
information security application. Advanced Materials, 29(1), p.1603169.
References
Bai, J., Krishnamurthy, A. and Weymuller, C.H., 2018. Measuring liquidity mismatch in the
banking sector. The Journal of Finance, 73(1), pp.51-93.
Bauer, S. and Bernroider, E.W., 2017. From information security awareness to reasoned
compliant action: analyzing information security policy compliance in a large banking
organization. ACM SIGMIS Database: the DATABASE for Advances in Information
Systems, 48(3), pp.44-68.
Dehling, T., Gao, F., Schneider, S. and Sunyaev, A., 2015. Exploring the far side of mobile
health: information security and privacy of mobile health apps on iOS and Android. JMIR
mHealth and uHealth, 3(1).
Erbenova, M.M., Liu, M.Y., Kyriakos-Saad, M.N., Mejia, A.L., Gasha, J.G., Mathias, M.E.,
Norat, M.M., Fernando, M.F. and Almeida, M.Y., 2016. The withdrawal of correspondent
banking relationships: a case for policy action. International Monetary Fund.
Fuller, G.W., 2016. Introduction. In The Great Debt Transformation (pp. 1-24). Palgrave
Macmillan, New York.
Kudakwashe, L., Rumbidzai, I.C., Keith, C., Gift, M. and Kaseke, N., 2016. Challenges faced by
the Banking Sector in tapping the untapped Informal Sector Market in Zimbabwe. International
Journal of Marketing and Technology, 6(9), pp.21-38.
Lee, J., Yoo, B., Lee, H., Cha, G.D., Lee, H.S., Cho, Y., Kim, S.Y., Seo, H., Lee, W., Son, D.
and Kang, M., 2017. Ultra‐wideband multi‐Dye‐sensitized upconverting nanoparticles for
information security application. Advanced Materials, 29(1), p.1603169.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

11INFORMATION SECURITY
Peltier, T.R., 2016. Information Security Policies, Procedures, and Standards: guidelines for
effective information security management. Auerbach Publications.
Peters, G.W. and Panayi, E., 2016. Understanding modern banking ledgers through blockchain
technologies: Future of transaction processing and smart contracts on the internet of money.
In Banking Beyond Banks and Money (pp. 239-278). Springer, Cham.
Safa, N.S. and Von Solms, R., 2016. An information security knowledge sharing model in
organizations. Computers in Human Behavior, 57, pp.442-451.
Scarlett, L. and Boyd, J., 2015. Ecosystem services and resource management: institutional
issues, challenges, and opportunities in the public sector. Ecological Economics, 115, pp.3-10.
Siponen, M., Mahmood, M.A. and Pahnila, S., 2014. Employees’ adherence to information
security policies: An exploratory field study. Information & management, 51(2), pp.217-224.
Soomro, Z.A., Shah, M.H. and Ahmed, J., 2016. Information security management needs more
holistic approach: A literature review. International Journal of Information Management, 36(2),
pp.215-225.
Tuna, G., Kogias, D.G., Gungor, V.C., Gezer, C., Taşkın, E. and Ayday, E., 2017. A survey on
information security threats and solutions for Machine to Machine (M2M)
communications. Journal of Parallel and Distributed Computing, 109, pp.142-154.
Peltier, T.R., 2016. Information Security Policies, Procedures, and Standards: guidelines for
effective information security management. Auerbach Publications.
Peters, G.W. and Panayi, E., 2016. Understanding modern banking ledgers through blockchain
technologies: Future of transaction processing and smart contracts on the internet of money.
In Banking Beyond Banks and Money (pp. 239-278). Springer, Cham.
Safa, N.S. and Von Solms, R., 2016. An information security knowledge sharing model in
organizations. Computers in Human Behavior, 57, pp.442-451.
Scarlett, L. and Boyd, J., 2015. Ecosystem services and resource management: institutional
issues, challenges, and opportunities in the public sector. Ecological Economics, 115, pp.3-10.
Siponen, M., Mahmood, M.A. and Pahnila, S., 2014. Employees’ adherence to information
security policies: An exploratory field study. Information & management, 51(2), pp.217-224.
Soomro, Z.A., Shah, M.H. and Ahmed, J., 2016. Information security management needs more
holistic approach: A literature review. International Journal of Information Management, 36(2),
pp.215-225.
Tuna, G., Kogias, D.G., Gungor, V.C., Gezer, C., Taşkın, E. and Ayday, E., 2017. A survey on
information security threats and solutions for Machine to Machine (M2M)
communications. Journal of Parallel and Distributed Computing, 109, pp.142-154.
1 out of 11
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




