IT Audit and Controls: Assessment of General Computer Controls
VerifiedAdded on 2022/12/01
|5
|778
|74
Report
AI Summary
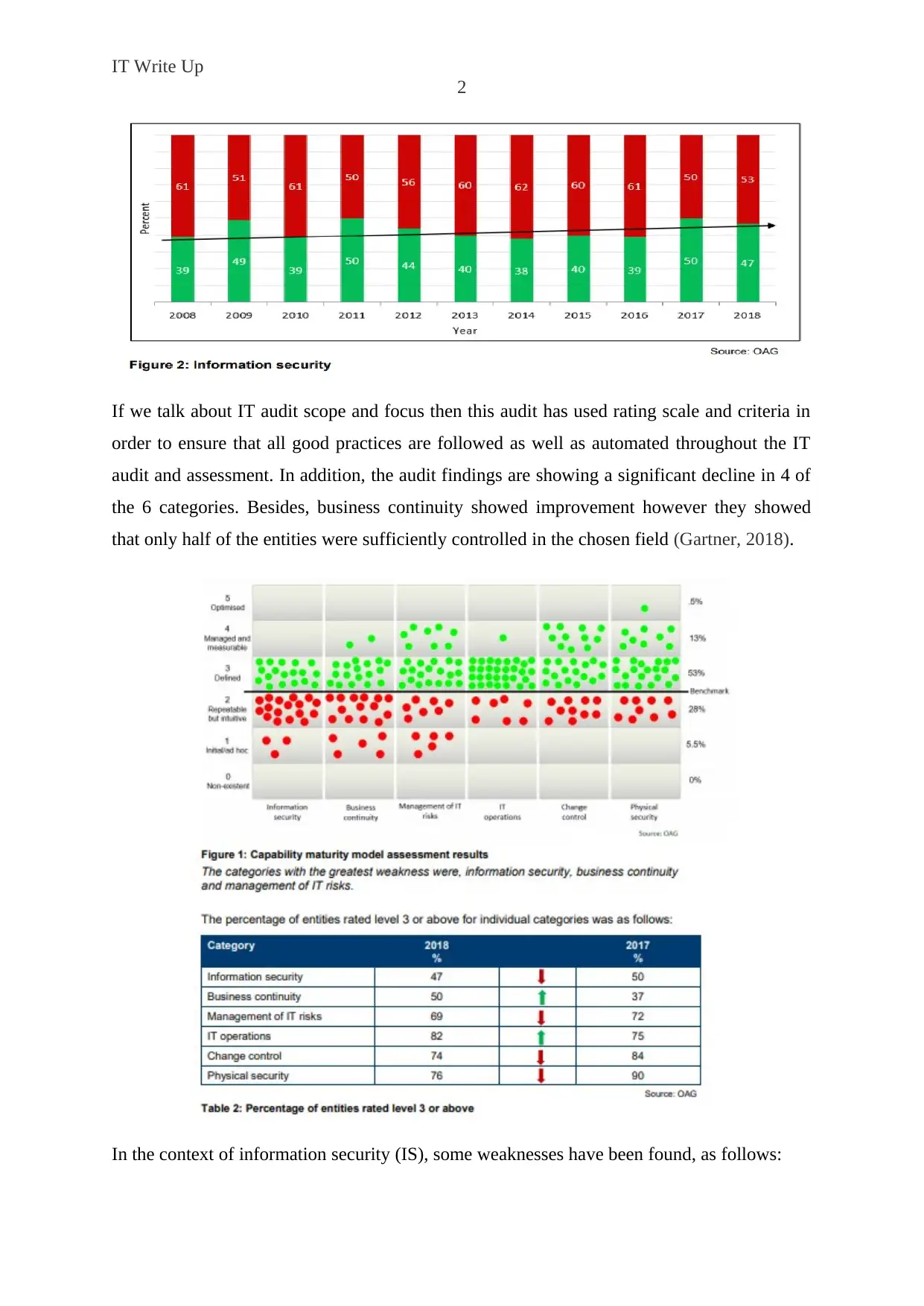
This report provides an in-depth analysis of IT audit and controls, focusing on general computer controls (GCC) within various governmental entities. The audit assesses six key control categories: physical security, business continuity, information security, IT risk management, change control, and IT operations. The findings reveal both strengths and weaknesses, highlighting areas where improvements are needed, such as enhanced information security awareness, updated business continuity plans, and better IT risk management practices. The report provides recommendations for executive managers to ensure effective system security, conduct regular reviews, and implement robust IT risk management policies and procedures. The report draws on industry best practices and compares findings from 2017 and 2018, highlighting specific issues and suggesting actionable steps for improvement across the assessed control categories. The audit also identifies weaknesses in areas like information security awareness, business continuity, and risk management procedures.
1 out of 5











![[object Object]](/_next/static/media/star-bottom.7253800d.svg)