IT Continuity Management: Developing a Disaster Recovery Plan
VerifiedAdded on 2023/04/06
|7
|797
|401
Report
AI Summary
This report provides an overview of IT continuity management, focusing on disaster recovery planning. It details plan updating authority, documentation storage, and backup strategies. The report also covers risk management, potential consequences of data breaches, and natural disasters, along with remedial actions. Emergency events and communication strategies for notifying employees, customers, and the media are outlined. The document emphasizes the importance of a well-structured disaster recovery plan for business continuity and includes relevant references.

Running head: IT MANAGEMENT
IT MANAGEMENT
Name of the Student
Name of the Organization
Author Note
IT MANAGEMENT
Name of the Student
Name of the Organization
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1IT MANAGEMENT
Table of Contents
2) Plan overview..............................................................................................................................2
Plan Updating Authority..............................................................................................................2
Plan Documentation Storage........................................................................................................2
3) Backup strategy...........................................................................................................................2
4) Risk Management........................................................................................................................3
5) Emergency Events.......................................................................................................................5
6) Communication strategy for notifying employees, customers and media..................................5
References........................................................................................................................................6
Table of Contents
2) Plan overview..............................................................................................................................2
Plan Updating Authority..............................................................................................................2
Plan Documentation Storage........................................................................................................2
3) Backup strategy...........................................................................................................................2
4) Risk Management........................................................................................................................3
5) Emergency Events.......................................................................................................................5
6) Communication strategy for notifying employees, customers and media..................................5
References........................................................................................................................................6

2IT MANAGEMENT
2) Plan overview
Plan Updating Authority
In this disaster recovery plan, the auditor is responsible for examining and assessing that the
procedures which are stated in the disaster recovery plan are consistent with a real practice. The
auditor is also responsible for assessing that officer for disaster recovery, the liaison for disaster
recovery or the disaster recovery coordinator possess all kinds of technical skills, experience and
training required for analyzing the capabilities of the members of team to complete the tasks
assigned.
Plan Documentation Storage
For maximizing the effectiveness of the auditors, disaster recovery officers or coordinators, the
plans for disaster recovery becomes most effective when they are frequently updated. The
auditor is responsible for examining records, contracts and billings for verifying all the records
which are being kept (Mohamed, 2014). Such records include a recent list of the hardware and
the software vendors of the organization. This list is periodically updated for reflecting the
changing practices of business. Several copies of it are stored both on and off site and are made
accessible to those which needs them. The auditor is responsible for testing the procedures which
are required for meeting the main objective and in determining the effectiveness.
3) Backup strategy
As a backup strategy, executives or some other leaders may plan some general testing like
operations testing based on scenario and also the testing for backup sources of power (Whitman,
Mattord & Green, 2013). In case of actual testing the information technology system for backup,
2) Plan overview
Plan Updating Authority
In this disaster recovery plan, the auditor is responsible for examining and assessing that the
procedures which are stated in the disaster recovery plan are consistent with a real practice. The
auditor is also responsible for assessing that officer for disaster recovery, the liaison for disaster
recovery or the disaster recovery coordinator possess all kinds of technical skills, experience and
training required for analyzing the capabilities of the members of team to complete the tasks
assigned.
Plan Documentation Storage
For maximizing the effectiveness of the auditors, disaster recovery officers or coordinators, the
plans for disaster recovery becomes most effective when they are frequently updated. The
auditor is responsible for examining records, contracts and billings for verifying all the records
which are being kept (Mohamed, 2014). Such records include a recent list of the hardware and
the software vendors of the organization. This list is periodically updated for reflecting the
changing practices of business. Several copies of it are stored both on and off site and are made
accessible to those which needs them. The auditor is responsible for testing the procedures which
are required for meeting the main objective and in determining the effectiveness.
3) Backup strategy
As a backup strategy, executives or some other leaders may plan some general testing like
operations testing based on scenario and also the testing for backup sources of power (Whitman,
Mattord & Green, 2013). In case of actual testing the information technology system for backup,
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
3IT MANAGEMENT
these tests are as diverse as simulating the simple data files loss or even a server as a whole by
looking at the backup processes for the OS, applications and databases or even processes which
involve testing failback or failover (Andrade et al., 2017). It is also responsible for looking for
the correct responses of IT to a range of several events.
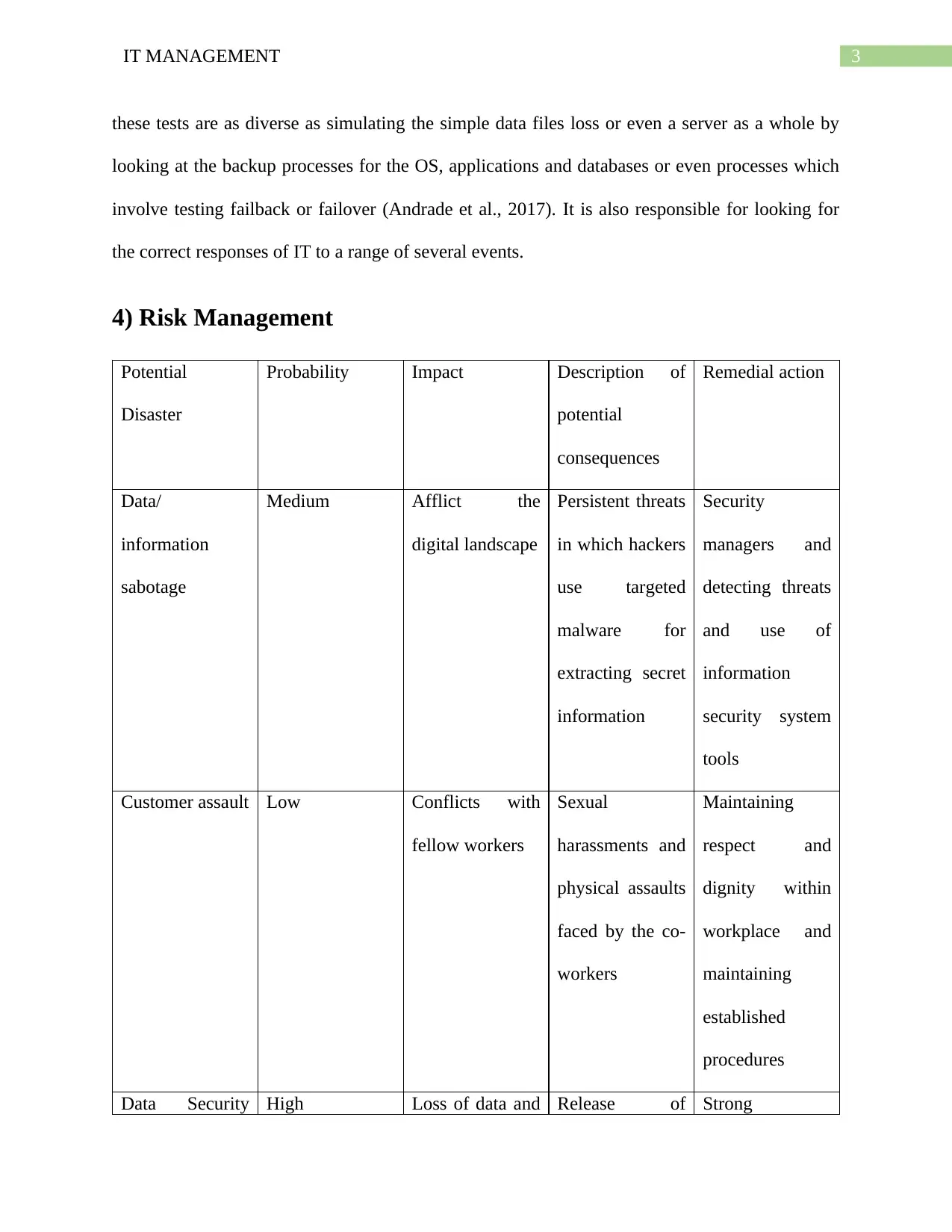
4) Risk Management
Potential
Disaster
Probability Impact Description of
potential
consequences
Remedial action
Data/
information
sabotage
Medium Afflict the
digital landscape
Persistent threats
in which hackers
use targeted
malware for
extracting secret
information
Security
managers and
detecting threats
and use of
information
security system
tools
Customer assault Low Conflicts with
fellow workers
Sexual
harassments and
physical assaults
faced by the co-
workers
Maintaining
respect and
dignity within
workplace and
maintaining
established
procedures
Data Security High Loss of data and Release of Strong
these tests are as diverse as simulating the simple data files loss or even a server as a whole by
looking at the backup processes for the OS, applications and databases or even processes which
involve testing failback or failover (Andrade et al., 2017). It is also responsible for looking for
the correct responses of IT to a range of several events.
4) Risk Management
Potential
Disaster
Probability Impact Description of
potential
consequences
Remedial action
Data/
information
sabotage
Medium Afflict the
digital landscape
Persistent threats
in which hackers
use targeted
malware for
extracting secret
information
Security
managers and
detecting threats
and use of
information
security system
tools
Customer assault Low Conflicts with
fellow workers
Sexual
harassments and
physical assaults
faced by the co-
workers
Maintaining
respect and
dignity within
workplace and
maintaining
established
procedures
Data Security High Loss of data and Release of Strong
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
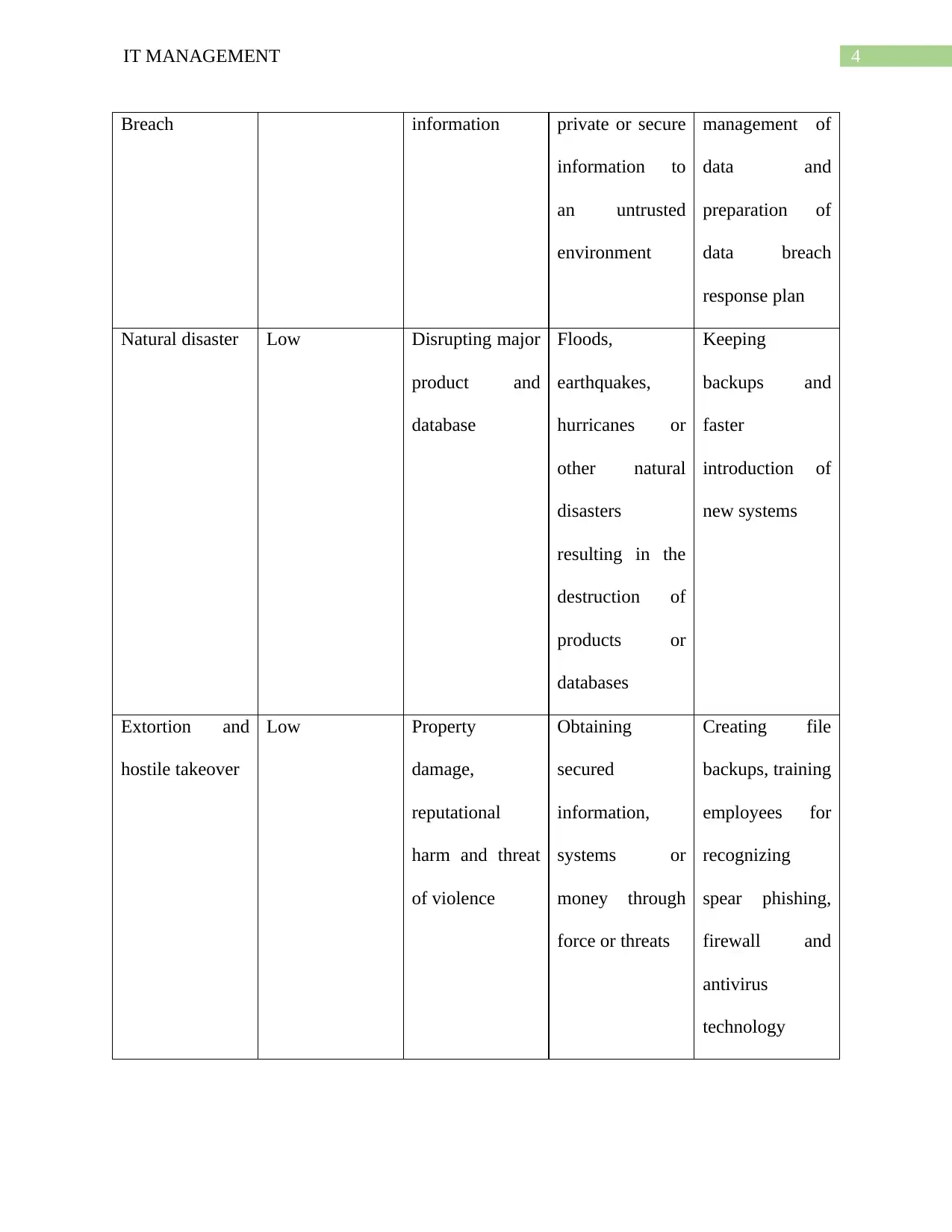
4IT MANAGEMENT
Breach information private or secure
information to
an untrusted
environment
management of
data and
preparation of
data breach
response plan
Natural disaster Low Disrupting major
product and
database
Floods,
earthquakes,
hurricanes or
other natural
disasters
resulting in the
destruction of
products or
databases
Keeping
backups and
faster
introduction of
new systems
Extortion and
hostile takeover
Low Property
damage,
reputational
harm and threat
of violence
Obtaining
secured
information,
systems or
money through
force or threats
Creating file
backups, training
employees for
recognizing
spear phishing,
firewall and
antivirus
technology
Breach information private or secure
information to
an untrusted
environment
management of
data and
preparation of
data breach
response plan
Natural disaster Low Disrupting major
product and
database
Floods,
earthquakes,
hurricanes or
other natural
disasters
resulting in the
destruction of
products or
databases
Keeping
backups and
faster
introduction of
new systems
Extortion and
hostile takeover
Low Property
damage,
reputational
harm and threat
of violence
Obtaining
secured
information,
systems or
money through
force or threats
Creating file
backups, training
employees for
recognizing
spear phishing,
firewall and
antivirus
technology

5IT MANAGEMENT
5) Emergency Events
An emergency event is basically a sudden or usually unexpected incident which requires
immediate reaction for emergency situations. Emergency events for this branch can be the
natural disasters, data breach and information sabotage.
There may be chances that natural disasters may occur suddenly and there may be a loss of huge
amount of secure information by the hackers. In case of natural disasters, a backup of files and
information are to be maintained and in case of data breaches there is a need for maintaining
proper cyber security within it.
6) Communication strategy for notifying employees, customers and
media
In case of disaster recovery plan, communication strategy is very important for notifying all the
employees, customers and media (Fearn-Banks, 2016). Emergency alerts are sent via mail and
text messages to mobile devices. Information about the situation is communicated to all the
employees, customers and also to media. Many different audiences are reached with specific
information to their needs and the business is able to respond accurately during the emergency in
the following days and hours.
5) Emergency Events
An emergency event is basically a sudden or usually unexpected incident which requires
immediate reaction for emergency situations. Emergency events for this branch can be the
natural disasters, data breach and information sabotage.
There may be chances that natural disasters may occur suddenly and there may be a loss of huge
amount of secure information by the hackers. In case of natural disasters, a backup of files and
information are to be maintained and in case of data breaches there is a need for maintaining
proper cyber security within it.
6) Communication strategy for notifying employees, customers and
media
In case of disaster recovery plan, communication strategy is very important for notifying all the
employees, customers and media (Fearn-Banks, 2016). Emergency alerts are sent via mail and
text messages to mobile devices. Information about the situation is communicated to all the
employees, customers and also to media. Many different audiences are reached with specific
information to their needs and the business is able to respond accurately during the emergency in
the following days and hours.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6IT MANAGEMENT
References
Andrade, E., Nogueira, B., Matos, R., Callou, G., & Maciel, P. (2017). Availability modeling
and analysis of a disaster-recovery-as-a-service solution. Computing, 99(10), 929-954.
Fearn-Banks, K. (2016). Crisis communications: A casebook approach. Routledge.
Mohamed, H. A. R. (2014). A proposed model for IT disaster recovery plan. International
Journal of Modern Education and Computer Science, 6(4), 57.
Whitman, M. E., Mattord, H. J., & Green, A. (2013). Principles of incident response and
disaster recovery. Cengage Learning.
References
Andrade, E., Nogueira, B., Matos, R., Callou, G., & Maciel, P. (2017). Availability modeling
and analysis of a disaster-recovery-as-a-service solution. Computing, 99(10), 929-954.
Fearn-Banks, K. (2016). Crisis communications: A casebook approach. Routledge.
Mohamed, H. A. R. (2014). A proposed model for IT disaster recovery plan. International
Journal of Modern Education and Computer Science, 6(4), 57.
Whitman, M. E., Mattord, H. J., & Green, A. (2013). Principles of incident response and
disaster recovery. Cengage Learning.
1 out of 7
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




