University IT Ethics Report: Spoofing Apps Ethical Issues Case Study
VerifiedAdded on 2022/12/16
|5
|1086
|242
Report
AI Summary
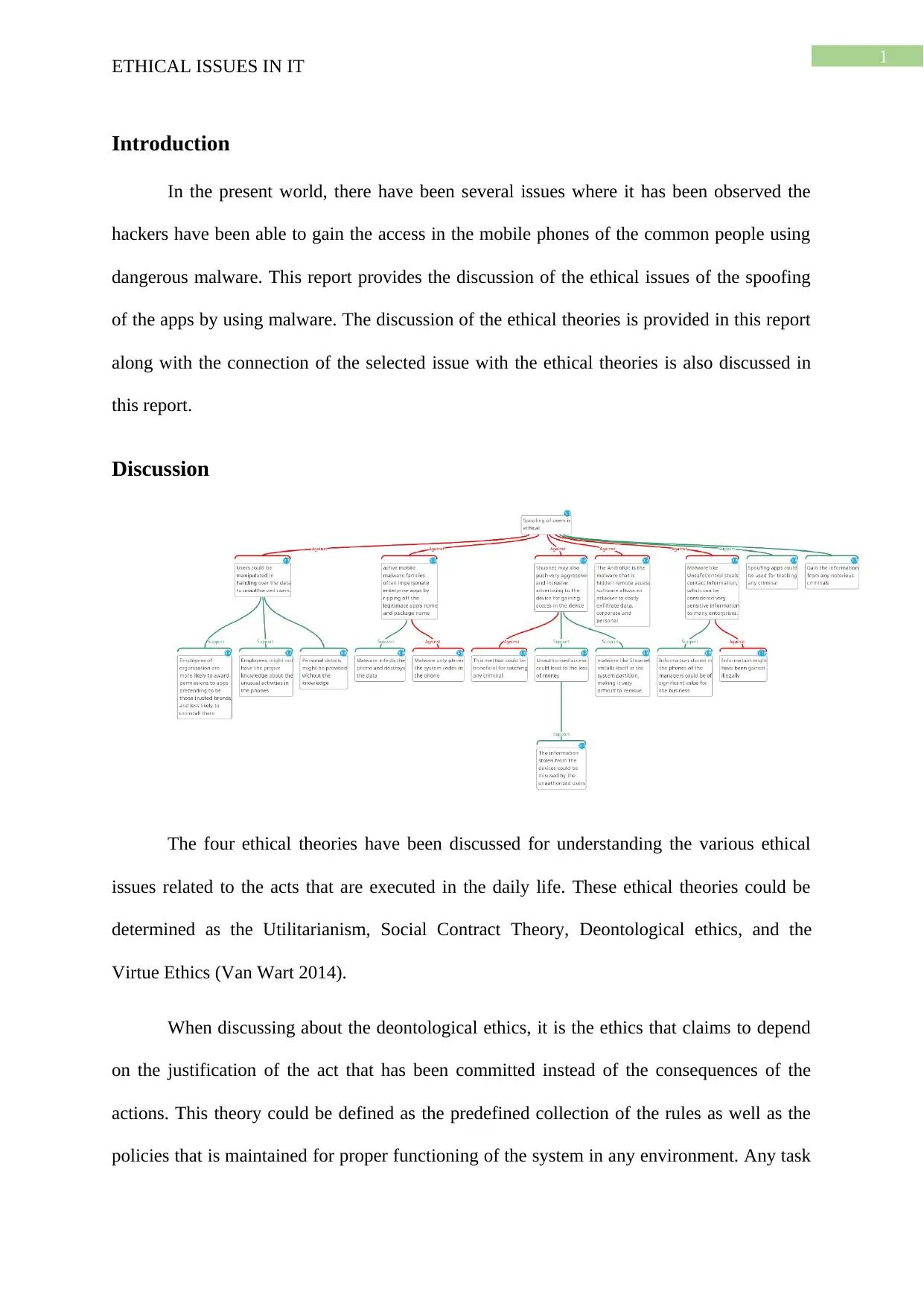
This report delves into the ethical considerations surrounding the spoofing of enterprise applications through the use of malware. It begins by outlining the problem of unauthorized access to mobile devices via malicious software. The core of the report focuses on applying four key ethical theories—Utilitarianism, Social Contract Theory, Deontological Ethics, and Virtue Ethics—to the issue of app spoofing. The discussion analyzes how app spoofing violates each ethical framework, highlighting the negative consequences for both enterprises and individuals. Specifically, the report argues that spoofing apps undermines deontological principles, fails the utilitarian test due to its harmful outcomes, breaches social contracts by disrupting moral order, and contradicts the virtues of ethical behavior. The conclusion reinforces the unethical nature of spoofing apps and emphasizes the potential for serious damage resulting from such actions. The report uses a case study approach to analyze the ethical implications, providing a framework for understanding the complexities of cybersecurity ethics.
1 out of 5










![[object Object]](/_next/static/media/star-bottom.7253800d.svg)