Information Technology Ethics: ITC506 Assignment 1 Analysis
VerifiedAdded on 2021/04/21
|6
|2059
|84
Homework Assignment
AI Summary
This assignment analyzes an ethical dilemma in an Information Technology project using the Doing Ethics Technique (DET). The scenario involves a project manager under pressure from the CEO to deliver a software product early, even if it means omitting essential encryption features, as the program director, Gregg, and senior developer, Jason, are concerned about the security implications. The assignment meticulously addresses the problem by first outlining the situation and presenting relevant facts about encryption and software updates. It then identifies key issues such as the integration of encryption algorithms and the limitations of resolving security issues through software updates. The assignment further identifies stakeholders affected by the decision, including the client company, its customers, and the reputation of the software development company. The core of the analysis involves evaluating the ethical implications of compromising security for the sake of deadlines and financial gain. The assignment proposes and evaluates options to resolve the dilemma, ultimately recommending extending the project deadline to ensure the inclusion of necessary security measures, thus avoiding potential risks and maintaining ethical standards. The analysis is structured to follow the DET framework, providing a comprehensive understanding of the ethical considerations and decision-making process in the context of IT project management.

SCHOOL OF COMPUTING AND MATHS, Charles Sturt University
Information Technology Ethics
Assignment 1: Doing Ethics Technique
Your Name
Student Number
Word Count:1000
Information Technology Ethics
Assignment 1: Doing Ethics Technique
Your Name
Student Number
Word Count:1000
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Information Technology Ethics
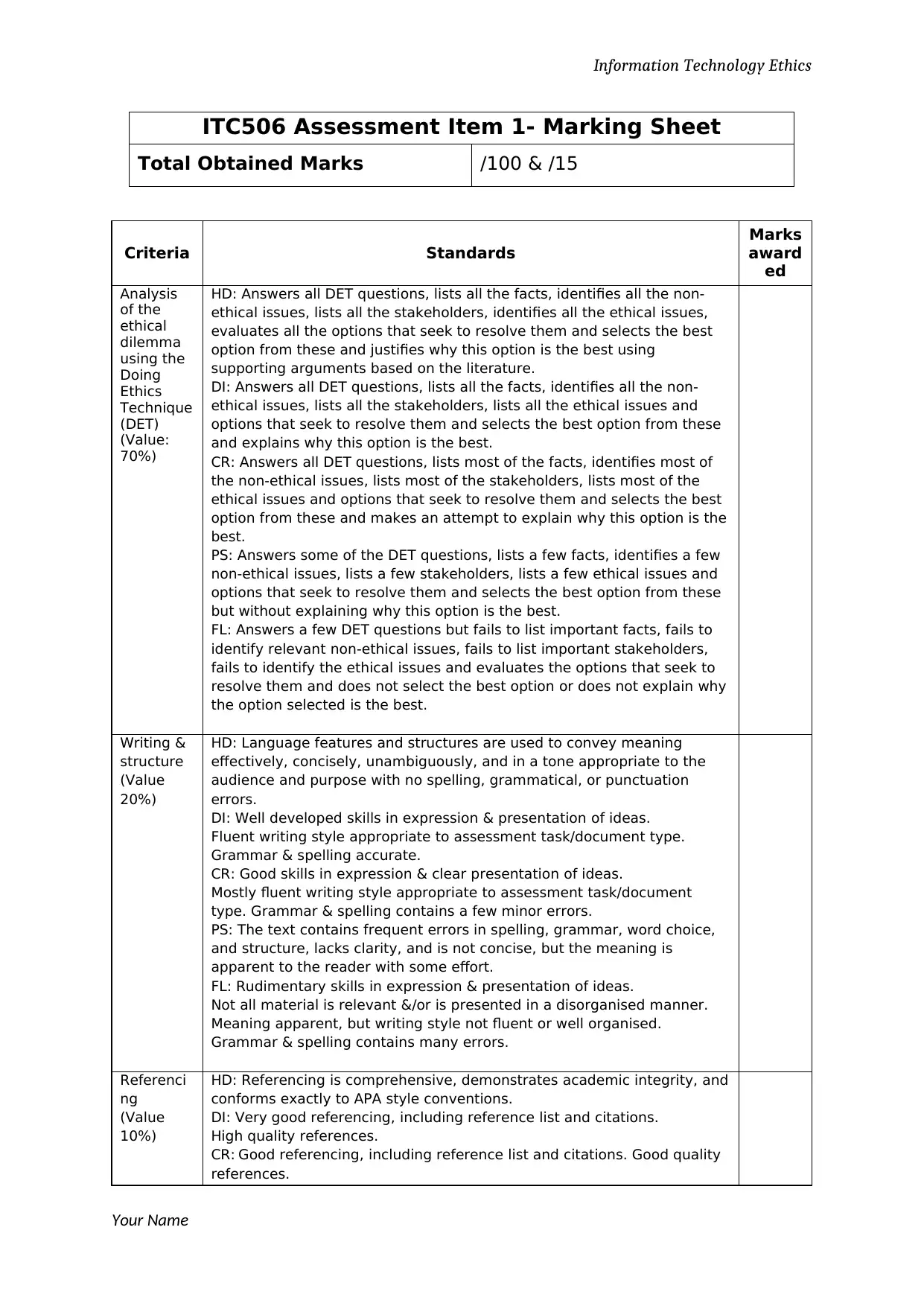
ITC506 Assessment Item 1- Marking Sheet
Total Obtained Marks /100 & /15
Criteria Standards
Marks
award
ed
Analysis
of the
ethical
dilemma
using the
Doing
Ethics
Technique
(DET)
(Value:
70%)
HD: Answers all DET questions, lists all the facts, identifies all the non-
ethical issues, lists all the stakeholders, identifies all the ethical issues,
evaluates all the options that seek to resolve them and selects the best
option from these and justifies why this option is the best using
supporting arguments based on the literature.
DI: Answers all DET questions, lists all the facts, identifies all the non-
ethical issues, lists all the stakeholders, lists all the ethical issues and
options that seek to resolve them and selects the best option from these
and explains why this option is the best.
CR: Answers all DET questions, lists most of the facts, identifies most of
the non-ethical issues, lists most of the stakeholders, lists most of the
ethical issues and options that seek to resolve them and selects the best
option from these and makes an attempt to explain why this option is the
best.
PS: Answers some of the DET questions, lists a few facts, identifies a few
non-ethical issues, lists a few stakeholders, lists a few ethical issues and
options that seek to resolve them and selects the best option from these
but without explaining why this option is the best.
FL: Answers a few DET questions but fails to list important facts, fails to
identify relevant non-ethical issues, fails to list important stakeholders,
fails to identify the ethical issues and evaluates the options that seek to
resolve them and does not select the best option or does not explain why
the option selected is the best.
Writing &
structure
(Value
20%)
HD: Language features and structures are used to convey meaning
effectively, concisely, unambiguously, and in a tone appropriate to the
audience and purpose with no spelling, grammatical, or punctuation
errors.
DI: Well developed skills in expression & presentation of ideas.
Fluent writing style appropriate to assessment task/document type.
Grammar & spelling accurate.
CR: Good skills in expression & clear presentation of ideas.
Mostly fluent writing style appropriate to assessment task/document
type. Grammar & spelling contains a few minor errors.
PS: The text contains frequent errors in spelling, grammar, word choice,
and structure, lacks clarity, and is not concise, but the meaning is
apparent to the reader with some effort.
FL: Rudimentary skills in expression & presentation of ideas.
Not all material is relevant &/or is presented in a disorganised manner.
Meaning apparent, but writing style not fluent or well organised.
Grammar & spelling contains many errors.
Referenci
ng
(Value
10%)
HD: Referencing is comprehensive, demonstrates academic integrity, and
conforms exactly to APA style conventions.
DI: Very good referencing, including reference list and citations.
High quality references.
CR: Good referencing, including reference list and citations. Good quality
references.
Your Name
ITC506 Assessment Item 1- Marking Sheet
Total Obtained Marks /100 & /15
Criteria Standards
Marks
award
ed
Analysis
of the
ethical
dilemma
using the
Doing
Ethics
Technique
(DET)
(Value:
70%)
HD: Answers all DET questions, lists all the facts, identifies all the non-
ethical issues, lists all the stakeholders, identifies all the ethical issues,
evaluates all the options that seek to resolve them and selects the best
option from these and justifies why this option is the best using
supporting arguments based on the literature.
DI: Answers all DET questions, lists all the facts, identifies all the non-
ethical issues, lists all the stakeholders, lists all the ethical issues and
options that seek to resolve them and selects the best option from these
and explains why this option is the best.
CR: Answers all DET questions, lists most of the facts, identifies most of
the non-ethical issues, lists most of the stakeholders, lists most of the
ethical issues and options that seek to resolve them and selects the best
option from these and makes an attempt to explain why this option is the
best.
PS: Answers some of the DET questions, lists a few facts, identifies a few
non-ethical issues, lists a few stakeholders, lists a few ethical issues and
options that seek to resolve them and selects the best option from these
but without explaining why this option is the best.
FL: Answers a few DET questions but fails to list important facts, fails to
identify relevant non-ethical issues, fails to list important stakeholders,
fails to identify the ethical issues and evaluates the options that seek to
resolve them and does not select the best option or does not explain why
the option selected is the best.
Writing &
structure
(Value
20%)
HD: Language features and structures are used to convey meaning
effectively, concisely, unambiguously, and in a tone appropriate to the
audience and purpose with no spelling, grammatical, or punctuation
errors.
DI: Well developed skills in expression & presentation of ideas.
Fluent writing style appropriate to assessment task/document type.
Grammar & spelling accurate.
CR: Good skills in expression & clear presentation of ideas.
Mostly fluent writing style appropriate to assessment task/document
type. Grammar & spelling contains a few minor errors.
PS: The text contains frequent errors in spelling, grammar, word choice,
and structure, lacks clarity, and is not concise, but the meaning is
apparent to the reader with some effort.
FL: Rudimentary skills in expression & presentation of ideas.
Not all material is relevant &/or is presented in a disorganised manner.
Meaning apparent, but writing style not fluent or well organised.
Grammar & spelling contains many errors.
Referenci
ng
(Value
10%)
HD: Referencing is comprehensive, demonstrates academic integrity, and
conforms exactly to APA style conventions.
DI: Very good referencing, including reference list and citations.
High quality references.
CR: Good referencing, including reference list and citations. Good quality
references.
Your Name
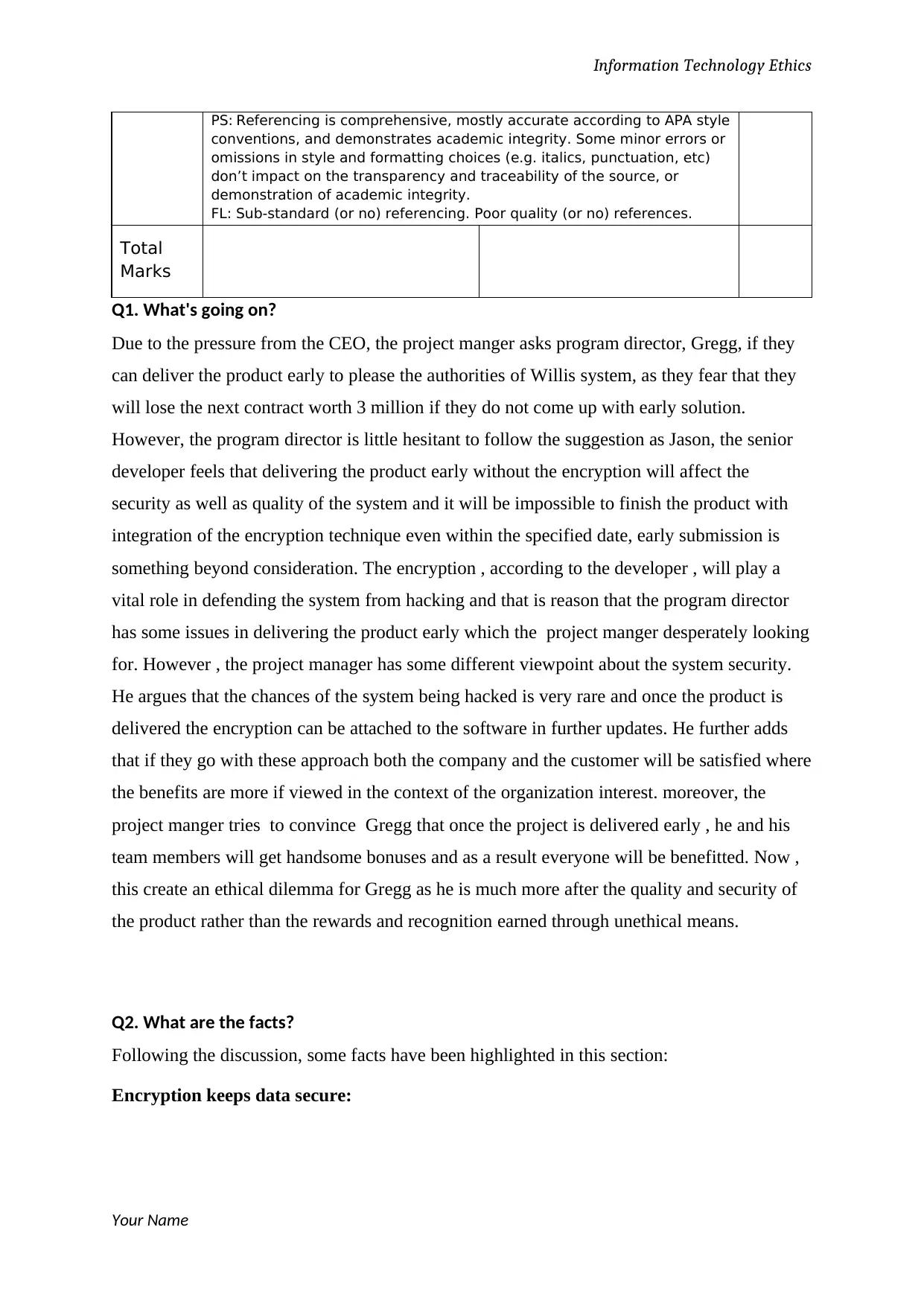
Information Technology Ethics
PS: Referencing is comprehensive, mostly accurate according to APA style
conventions, and demonstrates academic integrity. Some minor errors or
omissions in style and formatting choices (e.g. italics, punctuation, etc)
don’t impact on the transparency and traceability of the source, or
demonstration of academic integrity.
FL: Sub-standard (or no) referencing. Poor quality (or no) references.
Total
Marks
Q1. What's going on?
Due to the pressure from the CEO, the project manger asks program director, Gregg, if they
can deliver the product early to please the authorities of Willis system, as they fear that they
will lose the next contract worth 3 million if they do not come up with early solution.
However, the program director is little hesitant to follow the suggestion as Jason, the senior
developer feels that delivering the product early without the encryption will affect the
security as well as quality of the system and it will be impossible to finish the product with
integration of the encryption technique even within the specified date, early submission is
something beyond consideration. The encryption , according to the developer , will play a
vital role in defending the system from hacking and that is reason that the program director
has some issues in delivering the product early which the project manger desperately looking
for. However , the project manager has some different viewpoint about the system security.
He argues that the chances of the system being hacked is very rare and once the product is
delivered the encryption can be attached to the software in further updates. He further adds
that if they go with these approach both the company and the customer will be satisfied where
the benefits are more if viewed in the context of the organization interest. moreover, the
project manger tries to convince Gregg that once the project is delivered early , he and his
team members will get handsome bonuses and as a result everyone will be benefitted. Now ,
this create an ethical dilemma for Gregg as he is much more after the quality and security of
the product rather than the rewards and recognition earned through unethical means.
Q2. What are the facts?
Following the discussion, some facts have been highlighted in this section:
Encryption keeps data secure:
Your Name
PS: Referencing is comprehensive, mostly accurate according to APA style
conventions, and demonstrates academic integrity. Some minor errors or
omissions in style and formatting choices (e.g. italics, punctuation, etc)
don’t impact on the transparency and traceability of the source, or
demonstration of academic integrity.
FL: Sub-standard (or no) referencing. Poor quality (or no) references.
Total
Marks
Q1. What's going on?
Due to the pressure from the CEO, the project manger asks program director, Gregg, if they
can deliver the product early to please the authorities of Willis system, as they fear that they
will lose the next contract worth 3 million if they do not come up with early solution.
However, the program director is little hesitant to follow the suggestion as Jason, the senior
developer feels that delivering the product early without the encryption will affect the
security as well as quality of the system and it will be impossible to finish the product with
integration of the encryption technique even within the specified date, early submission is
something beyond consideration. The encryption , according to the developer , will play a
vital role in defending the system from hacking and that is reason that the program director
has some issues in delivering the product early which the project manger desperately looking
for. However , the project manager has some different viewpoint about the system security.
He argues that the chances of the system being hacked is very rare and once the product is
delivered the encryption can be attached to the software in further updates. He further adds
that if they go with these approach both the company and the customer will be satisfied where
the benefits are more if viewed in the context of the organization interest. moreover, the
project manger tries to convince Gregg that once the project is delivered early , he and his
team members will get handsome bonuses and as a result everyone will be benefitted. Now ,
this create an ethical dilemma for Gregg as he is much more after the quality and security of
the product rather than the rewards and recognition earned through unethical means.
Q2. What are the facts?
Following the discussion, some facts have been highlighted in this section:
Encryption keeps data secure:
Your Name
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Information Technology Ethics
Encryption plays a major role in making software more secure, reliable and robust (Han et al.,
2015). According to the authors, encryption strengthens the security by maintaining three
key aspects of data security:
1. Confidentiality – it keeps the data private
2. Integrity – it helps to keep the accuracy of the data
3. Availability – it helps to keep the web server online and always make the data
available.
Encryption makes use of the cryptographic algorithm to maintain the data security as
mentioned by the authors.
Software updates resolves security issues:
Software updates are provided to remove bugs that the software encounters during execution.
Though best efforts are given in the design, it is not possible to create software without any
issues. Eventually they software is expected to create issues in terms of execution or
performance (Fleischmann et al. , 2016). Regular updates are provided to ensure that the
software works correctly with less error.
Q3. What are the issues?
There are some issues regarding the project, which will be discussed below:
Integration of the encryption algorithm:
The consequence of not integrating the encryption technology with the software is directly
linked with the security of the software. Though it is necessary to finish the project within the
specified time and designing the encryption algorithm will delay the process further, still
delivering the product without the proper encryption technology will make the system less
secure (Wright & Cache , 2015).
Resolving security issues with software updates:
Even though software updates claims to resolves security issues, it is just some regular
updates focused more in bringing improvement in day-to-day activities that the software is
designed for. It is not an effective solution to deal with the security issues by exploring the
root cause. The best practice to deal with the security issues more effectively, it is much more
convenient to come up with solution at the designing process (Bernstein , 2014). Otherwise, it
becomes difficult to maintain the security level through software updates and it might not
produce the same level of integrity in data security as pointed out by the authors.
Q4. Who is affected?
Your Name
Encryption plays a major role in making software more secure, reliable and robust (Han et al.,
2015). According to the authors, encryption strengthens the security by maintaining three
key aspects of data security:
1. Confidentiality – it keeps the data private
2. Integrity – it helps to keep the accuracy of the data
3. Availability – it helps to keep the web server online and always make the data
available.
Encryption makes use of the cryptographic algorithm to maintain the data security as
mentioned by the authors.
Software updates resolves security issues:
Software updates are provided to remove bugs that the software encounters during execution.
Though best efforts are given in the design, it is not possible to create software without any
issues. Eventually they software is expected to create issues in terms of execution or
performance (Fleischmann et al. , 2016). Regular updates are provided to ensure that the
software works correctly with less error.
Q3. What are the issues?
There are some issues regarding the project, which will be discussed below:
Integration of the encryption algorithm:
The consequence of not integrating the encryption technology with the software is directly
linked with the security of the software. Though it is necessary to finish the project within the
specified time and designing the encryption algorithm will delay the process further, still
delivering the product without the proper encryption technology will make the system less
secure (Wright & Cache , 2015).
Resolving security issues with software updates:
Even though software updates claims to resolves security issues, it is just some regular
updates focused more in bringing improvement in day-to-day activities that the software is
designed for. It is not an effective solution to deal with the security issues by exploring the
root cause. The best practice to deal with the security issues more effectively, it is much more
convenient to come up with solution at the designing process (Bernstein , 2014). Otherwise, it
becomes difficult to maintain the security level through software updates and it might not
produce the same level of integrity in data security as pointed out by the authors.
Q4. Who is affected?
Your Name
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Information Technology Ethics
The client company will be the affected most if the software is delivered to the company
overlooking the security issues. Not only the client company, the customers associated with
the organization will be affected as well.
Additionally, if the product does not deliver the expected performance and create security
issues the reputation of the designing company will also be affected.
Q5. What are the ethical issues and their implications?
Violation of security:
Whenever an organization is involved in creating any product for the client organizations , it
is the responsibility of the company to give the highest priority to ensure that best design
methodology is followed to make the product highly secure. However , in this context the
manufacturing company is trying to overlook the security issues just because of delivering
the product early to please the authorities.
This move is highly unethical as it involves the data security of thousands of customer
associated with the client organization.
Compromising of quality over money:
To deliver the project early and to ensure that they get the next project worth millions , they
have decided to compromise the quality of the product as they think that the security issues
can be later resolved by rolling out software updates . However, according to the program
director, this method is not reliable to ensure system security and proper attention should be
given right at the time of designing the software.
From the discussion , this move can be regarded as unethical and it has the potential to affect
the client both in terms of security and reputation. Additionally, the reputation of the
manufacturing company will also be affected.
Q6. What could have been done about it?
In order to finish the project and deliver it within the specified time frame , the project should
have been started earlier and if not the speed of designing parts of the product should have
Your Name
The client company will be the affected most if the software is delivered to the company
overlooking the security issues. Not only the client company, the customers associated with
the organization will be affected as well.
Additionally, if the product does not deliver the expected performance and create security
issues the reputation of the designing company will also be affected.
Q5. What are the ethical issues and their implications?
Violation of security:
Whenever an organization is involved in creating any product for the client organizations , it
is the responsibility of the company to give the highest priority to ensure that best design
methodology is followed to make the product highly secure. However , in this context the
manufacturing company is trying to overlook the security issues just because of delivering
the product early to please the authorities.
This move is highly unethical as it involves the data security of thousands of customer
associated with the client organization.
Compromising of quality over money:
To deliver the project early and to ensure that they get the next project worth millions , they
have decided to compromise the quality of the product as they think that the security issues
can be later resolved by rolling out software updates . However, according to the program
director, this method is not reliable to ensure system security and proper attention should be
given right at the time of designing the software.
From the discussion , this move can be regarded as unethical and it has the potential to affect
the client both in terms of security and reputation. Additionally, the reputation of the
manufacturing company will also be affected.
Q6. What could have been done about it?
In order to finish the project and deliver it within the specified time frame , the project should
have been started earlier and if not the speed of designing parts of the product should have
Your Name

Information Technology Ethics
been accelerated rather than coming with some unethical plans at the later part of the project
and convincing the designing team to follow it accordingly.
Q7. What are the options?
Considering the current scenario, two options are available right now
Either the higher authorities should approach the client company for extending the date of
delivery or they should simply refuse to complete the project in the due date.
Q8. Which option is the best and why?
From the above two options , the best option is obviously to convince the company for
extending the delivery time because if they choose to refuse completing the project, it will
create a bad impression about the organization and they will lose the next project for the
company. However , if they are able to convince the client about the importance of extending
the delivery date by showing them the consequences of delivering the product within the
specified time, both ends will be benefited.
References
Bernstein, D. J. (2014). Caesar: Competition for authenticated encryption: Security,
applicability, and robustness.
Fleischmann, M., Amirpur, M., Grupp, T., Benlian, A., & Hess, T. (2016). The role of
software updates in information systems continuance—An experimental study from a
user perspective. Decision Support Systems, 83, 83-96.
Han, J., Susilo, W., Mu, Y., Zhou, J., & Au, M. H. A. (2015). Improving privacy and security
in decentralized ciphertext-policy attribute-based encryption. IEEE transactions on
information forensics and security, 10(3), 665-678.
Wright, J., & Cache, J. (2015). Hacking exposed wireless: wireless security secrets &
solutions. McGraw-Hill Education Group.
Your Name
been accelerated rather than coming with some unethical plans at the later part of the project
and convincing the designing team to follow it accordingly.
Q7. What are the options?
Considering the current scenario, two options are available right now
Either the higher authorities should approach the client company for extending the date of
delivery or they should simply refuse to complete the project in the due date.
Q8. Which option is the best and why?
From the above two options , the best option is obviously to convince the company for
extending the delivery time because if they choose to refuse completing the project, it will
create a bad impression about the organization and they will lose the next project for the
company. However , if they are able to convince the client about the importance of extending
the delivery date by showing them the consequences of delivering the product within the
specified time, both ends will be benefited.
References
Bernstein, D. J. (2014). Caesar: Competition for authenticated encryption: Security,
applicability, and robustness.
Fleischmann, M., Amirpur, M., Grupp, T., Benlian, A., & Hess, T. (2016). The role of
software updates in information systems continuance—An experimental study from a
user perspective. Decision Support Systems, 83, 83-96.
Han, J., Susilo, W., Mu, Y., Zhou, J., & Au, M. H. A. (2015). Improving privacy and security
in decentralized ciphertext-policy attribute-based encryption. IEEE transactions on
information forensics and security, 10(3), 665-678.
Wright, J., & Cache, J. (2015). Hacking exposed wireless: wireless security secrets &
solutions. McGraw-Hill Education Group.
Your Name
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 6
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





