IT Ethics Report: Ethical Analysis of Path Application Privacy
VerifiedAdded on 2022/09/23
|7
|1096
|26
Report
AI Summary
This report analyzes the ethical implications of the Path application's privacy practices, focusing on the unauthorized collection and storage of user data. The report employs four classical ethical theories: utilitarianism, deontology, virtue ethics, and rights, to evaluate the actions of the Path application. The discussion examines how each theory applies to the case, considering the benefits, obligations, character, and rights involved. The report highlights the controversies surrounding the application's data collection methods, including storing user contacts without consent and storing them in an unencrypted manner. Furthermore, the report references the company's response, including apologies, data deletion, and settlements with regulatory bodies. A mind map is used to visually represent the ethical arguments. The conclusion summarizes the findings, emphasizing the importance of ethical considerations in application development, particularly regarding user privacy and data security.

Running head: IT ETHICS
IT ETHICS
Name of the Student
Name of the University
Author Note:
IT ETHICS
Name of the Student
Name of the University
Author Note:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1IT ETHICS
Table of Contents
Introduction..........................................................................................................................2
Discussion............................................................................................................................2
Conclusion...........................................................................................................................4
References............................................................................................................................5
Appendix..............................................................................................................................6
Table of Contents
Introduction..........................................................................................................................2
Discussion............................................................................................................................2
Conclusion...........................................................................................................................4
References............................................................................................................................5
Appendix..............................................................................................................................6

2IT ETHICS
Introduction
Path is a well-known networking application which describes smart journal that helps in
sharing with life that an individual love. In the year 2010, the application was founded by Dave
Morin, ex-employee of Facebook.
In the coming pages of the report, this particular scenario has been analyzed from the
perspective of ethical theories. The report is completely based on privacy and application related
issues for path application. A visual representation has been provided with respect to the case
study using MindMup tool.
Discussion
The four ethical theories have been described below in details like
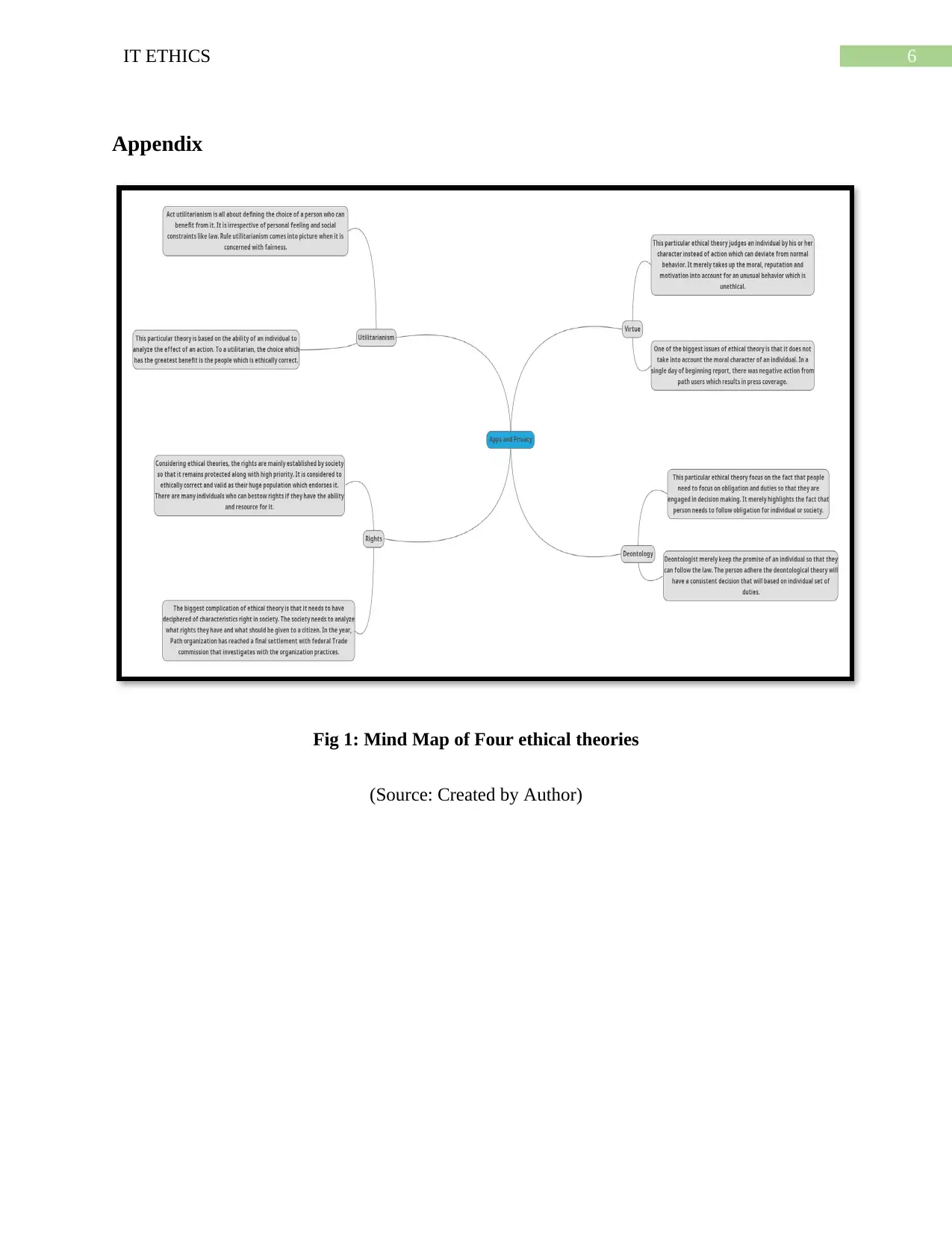
Utilitarianism: This particular theory is based on overall ability of an individual to
analyze the effect of action. To a utilitarian, the choice which has the biggest benefit is the
people which is correct in terms of ethics. Utilitarianisms are generally of two kinds that is act
utilitarianism and rule utilitarianisms (University, 2019). Act utilitarianism is all about defining
the choice of a person who can benefit from it. It is all about neglecting the personal feeling and
social constraints like law. Both act and rule utilitarianisms has certain number of drawbacks.
Uncertainty can lead easily lead to unexpected benefits which can make the decision of
utilitarian decision as an unethical one (Laczniak & Murphy, 2019). Path application encounter
certain number of privacy issues where the application collected information without any
permission from user end. The collected details of user were stored in unencrypted way in the
Path server.
Introduction
Path is a well-known networking application which describes smart journal that helps in
sharing with life that an individual love. In the year 2010, the application was founded by Dave
Morin, ex-employee of Facebook.
In the coming pages of the report, this particular scenario has been analyzed from the
perspective of ethical theories. The report is completely based on privacy and application related
issues for path application. A visual representation has been provided with respect to the case
study using MindMup tool.
Discussion
The four ethical theories have been described below in details like
Utilitarianism: This particular theory is based on overall ability of an individual to
analyze the effect of action. To a utilitarian, the choice which has the biggest benefit is the
people which is correct in terms of ethics. Utilitarianisms are generally of two kinds that is act
utilitarianism and rule utilitarianisms (University, 2019). Act utilitarianism is all about defining
the choice of a person who can benefit from it. It is all about neglecting the personal feeling and
social constraints like law. Both act and rule utilitarianisms has certain number of drawbacks.
Uncertainty can lead easily lead to unexpected benefits which can make the decision of
utilitarian decision as an unethical one (Laczniak & Murphy, 2019). Path application encounter
certain number of privacy issues where the application collected information without any
permission from user end. The collected details of user were stored in unencrypted way in the
Path server.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3IT ETHICS
Deontology: This particular ethical theory focus on the fact that people need to focus on
obligation and duties so that they are engaged in decision making. It merely highlights the fact
that person needs to follow obligation for individual or society. Deontologist merely keep the
promise of an individual so that they can obey law. The person adhere the deontological theory
will have a consistent decision which is based on certain number of duties (Baumane-Vitolina,
Cals & Sumilo, 2016). Deontology may have certain number of attributes but also a certain
number of flaws. The biggest issue is that there is no logical basis for analyzing the duties of
individual. The founder of the path application has responded to the whole scenario by stating
address book to the server. It is mainly done so that user can find and connect to friends on this
path application quickly. The organization claimed that this particular action was taken as per the
industry best practices.
Virtue: This particular ethical theory judges an individual by his or her character instead
of action much different from normal behavior. One of the biggest issues of ethical theory is that
it does not take into account the moral character of an individual (Paulraj, Chen & Blome, 2017).
In a single day of beginning report, there was negative action from path users which results in
press coverage. Chief executive and co-founder of Path posted an apology on an official blog.
The organization rapidly delete the gathered data of user along with updating the IOS
application.
Rights: Considering ethical theories, the rights are mainly established by society so that it
remains protected along with high priority. It is considered to be correct ethically and valid as
their huge population which endorses it. There are many individuals who can bestow rights if
they have the ability and resource for it (Hatfield, 2019). The biggest complication of ethical
theory is that it needs to have deciphered of characteristics right in society. The society needs to
Deontology: This particular ethical theory focus on the fact that people need to focus on
obligation and duties so that they are engaged in decision making. It merely highlights the fact
that person needs to follow obligation for individual or society. Deontologist merely keep the
promise of an individual so that they can obey law. The person adhere the deontological theory
will have a consistent decision which is based on certain number of duties (Baumane-Vitolina,
Cals & Sumilo, 2016). Deontology may have certain number of attributes but also a certain
number of flaws. The biggest issue is that there is no logical basis for analyzing the duties of
individual. The founder of the path application has responded to the whole scenario by stating
address book to the server. It is mainly done so that user can find and connect to friends on this
path application quickly. The organization claimed that this particular action was taken as per the
industry best practices.
Virtue: This particular ethical theory judges an individual by his or her character instead
of action much different from normal behavior. One of the biggest issues of ethical theory is that
it does not take into account the moral character of an individual (Paulraj, Chen & Blome, 2017).
In a single day of beginning report, there was negative action from path users which results in
press coverage. Chief executive and co-founder of Path posted an apology on an official blog.
The organization rapidly delete the gathered data of user along with updating the IOS
application.
Rights: Considering ethical theories, the rights are mainly established by society so that it
remains protected along with high priority. It is considered to be correct ethically and valid as
their huge population which endorses it. There are many individuals who can bestow rights if
they have the ability and resource for it (Hatfield, 2019). The biggest complication of ethical
theory is that it needs to have deciphered of characteristics right in society. The society needs to
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4IT ETHICS
analyze what rights they have and what should be given to a citizen. In the year, Path
organization has reached a final settlement with federal Trade commission that investigates with
the organization practices. With respect to violation of children online privacy protection act, the
organization aims to pay a fine of 800,000 dollars (Fuenmayor & Benzmüller, 2019). In addition,
it has deleted around three thousand accounts and provided a privacy audit on a yearly basis for
the next 20 years.
Conclusion
The above pages help us in concluding the point that this report is about analyzing
application and privacy ethics case study with respect to four ethical theories. Considering the
perspective of developers, path organization has the tendency of building new things. This will
come into the picture for account verification so that they can have a look. In the year 2012, path
application stands as the center of privacy controversy as it stores all the user contacts without
their permission. The collected information from user is stored in the path server where it is
stored in unencrypted way.
analyze what rights they have and what should be given to a citizen. In the year, Path
organization has reached a final settlement with federal Trade commission that investigates with
the organization practices. With respect to violation of children online privacy protection act, the
organization aims to pay a fine of 800,000 dollars (Fuenmayor & Benzmüller, 2019). In addition,
it has deleted around three thousand accounts and provided a privacy audit on a yearly basis for
the next 20 years.
Conclusion
The above pages help us in concluding the point that this report is about analyzing
application and privacy ethics case study with respect to four ethical theories. Considering the
perspective of developers, path organization has the tendency of building new things. This will
come into the picture for account verification so that they can have a look. In the year 2012, path
application stands as the center of privacy controversy as it stores all the user contacts without
their permission. The collected information from user is stored in the path server where it is
stored in unencrypted way.

5IT ETHICS
References
Baumane-Vitolina, I., Cals, I., & Sumilo, E. (2016). Is Ethics Rational? Teleological,
Deontological and Virtue Ethics Theories Reconciled in the Context of Traditional
Economic Decision Making. Procedia Economics and Finance, 39, 108-114.
Fuenmayor, D., & Benzmüller, C. (2019). Harnessing Higher-Order (Meta-) Logic to Represent
and Reason with Complex Ethical Theories. arXiv preprint arXiv:1903.09818.
Hatfield, J. M. (2019). Virtuous human hacking: The ethics of social engineering in penetration-
testing. Computers & Security, 83, 354-366.
Laczniak, G. R., & Murphy, P. E. (2019). The role of normative marketing ethics. Journal of
Business Research, 95, 401-407.
Paulraj, A., Chen, I. J., & Blome, C. (2017). Motives and performance outcomes of sustainable
supply chain management practices: A multi-theoretical perspective. Journal of Business
Ethics, 145(2), 239-258.
University, S., 2019. Apps and Privacy. [online] Scu.edu. Available at:
<https://www.scu.edu/ethics/focus-areas/internet-ethics/resources/apps-and-privacy/>
[Accessed 4 Sep. 2019].
References
Baumane-Vitolina, I., Cals, I., & Sumilo, E. (2016). Is Ethics Rational? Teleological,
Deontological and Virtue Ethics Theories Reconciled in the Context of Traditional
Economic Decision Making. Procedia Economics and Finance, 39, 108-114.
Fuenmayor, D., & Benzmüller, C. (2019). Harnessing Higher-Order (Meta-) Logic to Represent
and Reason with Complex Ethical Theories. arXiv preprint arXiv:1903.09818.
Hatfield, J. M. (2019). Virtuous human hacking: The ethics of social engineering in penetration-
testing. Computers & Security, 83, 354-366.
Laczniak, G. R., & Murphy, P. E. (2019). The role of normative marketing ethics. Journal of
Business Research, 95, 401-407.
Paulraj, A., Chen, I. J., & Blome, C. (2017). Motives and performance outcomes of sustainable
supply chain management practices: A multi-theoretical perspective. Journal of Business
Ethics, 145(2), 239-258.
University, S., 2019. Apps and Privacy. [online] Scu.edu. Available at:
<https://www.scu.edu/ethics/focus-areas/internet-ethics/resources/apps-and-privacy/>
[Accessed 4 Sep. 2019].
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
6IT ETHICS
Appendix
Fig 1: Mind Map of Four ethical theories
(Source: Created by Author)
Appendix
Fig 1: Mind Map of Four ethical theories
(Source: Created by Author)
1 out of 7
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




