A New Approach For Combining IT Frameworks: A Unified Maturity Model
VerifiedAdded on 2022/10/17
|6
|3120
|199
Report
AI Summary
This paper, published in the IJCSI International Journal of Computer Science Issues, explores a new approach to combining various IT frameworks and standards, including ITIL, COBIT, PMBOK, CMMI, ISO 27001, Val IT, and eTOM. The research aims to develop a Unified Maturity Model that integrates these frameworks to provide a comprehensive assessment of an information system's maturity and improve IT services within an enterprise. The study analyzes the positioning of these frameworks within the IT value chain and conducts a comparative study of their processes and best practices, highlighting their similarities and areas of overlap. The authors propose a unified model based on eleven process areas derived from existing standards and IS concerns, allowing for a more effective and integrated approach to IT governance and service management. The paper also details the levels of IS maturity, ranging from elementary to advanced, and the corresponding processes associated with each level. The findings suggest that the combined use of these frameworks can significantly enhance the management of IT resources, improve service quality, and facilitate better alignment with business objectives.

Towards a New Approach For Combining The IT Frameworks
Samir BAHSANI1, Alami SEMMA2 and Noura SELLAM3
1 Department of Mathematics and Computer Science, Faculty of Science and Techniques,
Hassan 1 University
Settat, Morocco
2 Department of Mathematics and Computer Science, Faculty of Science and Techniques,
Hassan 1 University
Settat, Morocco
3 Department of Communication Systems, INPT
National Institute of Posts and Telecommunications
Rabat, Morocco
Abstract
There are various IT frameworks and best practices supporting
Information Systems. Each has its own strenghts but none of
them satisfies all of the IS requirements independently. In this
paper we are studying the possibilities of pooling of the most
used frameworks: ITIL, Cobit, PMbok, CMMI, ISO 27001, Val
IT and eTOM.
The result of this paper is meant to present a Unified Maturity
Model combining IS standards and IT frameworks concurrently
in order to get a greater insight on the information system’
maturity and improve the enterprise’s IT services.
Keywords: Information systems, governance, frameworks,
pooling, maturity of Information Systems.
1. Introduction
It is within such a turbulent economic environment marked
by a challenging growth [1] and perpetual change on
different business aspects that a company seeks to increase
its capacity to quickly change its strategies concerning
management, resources and market [2]. These
organizational and technological changes must be regarded
as an opportunity because they allow the company to re-
position itself effectively to ensure a continuous flow of
market insights into their business or taking part of the
competitive market by offering new products and services
These standards can be mentioned among others: ITIL
(Information Technology Infrastructure Library) for the
production and life cycle management of IT, COBIT
(Control Objectives for Information and related
Technology) for governance, IS0 27001 (International
Organization for Standardization) for security, PMP
(project Management Professional) for project
management, CMMI (Capability Maturity Model
Integration) for the evaluation of the system development,
hardware and/or software, Val IT (Value of Information
Technology) that deals with the issue of creating value by
the Information System Direction (ISD) projects that are
offering an evaluation of IT investments [4].
Whatever the adopted framework is, its implementation
should bring new management concepts regarding
processes and contribute to the improvement of product
and service development process, customer satisfaction
and economy of time and that of resources [5].
In this article we study the possibilities of pooling of
several IT standards.
2. Positioning of IT Frameworks in the Value
Chain
The Value Chain is a set of the required steps to produce a
company's added value. The Value Chain of an ISD is a set
of functional blocks involved in the creation process of the
IJCSI International Journal of Computer Science Issues, Volume 12, Issue 1, No 1, January 2015
ISSN (Print): 1694-0814 | ISSN (Online): 1694-0784
www.IJCSI.org 118
Samir BAHSANI1, Alami SEMMA2 and Noura SELLAM3
1 Department of Mathematics and Computer Science, Faculty of Science and Techniques,
Hassan 1 University
Settat, Morocco
2 Department of Mathematics and Computer Science, Faculty of Science and Techniques,
Hassan 1 University
Settat, Morocco
3 Department of Communication Systems, INPT
National Institute of Posts and Telecommunications
Rabat, Morocco
Abstract
There are various IT frameworks and best practices supporting
Information Systems. Each has its own strenghts but none of
them satisfies all of the IS requirements independently. In this
paper we are studying the possibilities of pooling of the most
used frameworks: ITIL, Cobit, PMbok, CMMI, ISO 27001, Val
IT and eTOM.
The result of this paper is meant to present a Unified Maturity
Model combining IS standards and IT frameworks concurrently
in order to get a greater insight on the information system’
maturity and improve the enterprise’s IT services.
Keywords: Information systems, governance, frameworks,
pooling, maturity of Information Systems.
1. Introduction
It is within such a turbulent economic environment marked
by a challenging growth [1] and perpetual change on
different business aspects that a company seeks to increase
its capacity to quickly change its strategies concerning
management, resources and market [2]. These
organizational and technological changes must be regarded
as an opportunity because they allow the company to re-
position itself effectively to ensure a continuous flow of
market insights into their business or taking part of the
competitive market by offering new products and services
These standards can be mentioned among others: ITIL
(Information Technology Infrastructure Library) for the
production and life cycle management of IT, COBIT
(Control Objectives for Information and related
Technology) for governance, IS0 27001 (International
Organization for Standardization) for security, PMP
(project Management Professional) for project
management, CMMI (Capability Maturity Model
Integration) for the evaluation of the system development,
hardware and/or software, Val IT (Value of Information
Technology) that deals with the issue of creating value by
the Information System Direction (ISD) projects that are
offering an evaluation of IT investments [4].
Whatever the adopted framework is, its implementation
should bring new management concepts regarding
processes and contribute to the improvement of product
and service development process, customer satisfaction
and economy of time and that of resources [5].
In this article we study the possibilities of pooling of
several IT standards.
2. Positioning of IT Frameworks in the Value
Chain
The Value Chain is a set of the required steps to produce a
company's added value. The Value Chain of an ISD is a set
of functional blocks involved in the creation process of the
IJCSI International Journal of Computer Science Issues, Volume 12, Issue 1, No 1, January 2015
ISSN (Print): 1694-0814 | ISSN (Online): 1694-0784
www.IJCSI.org 118
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
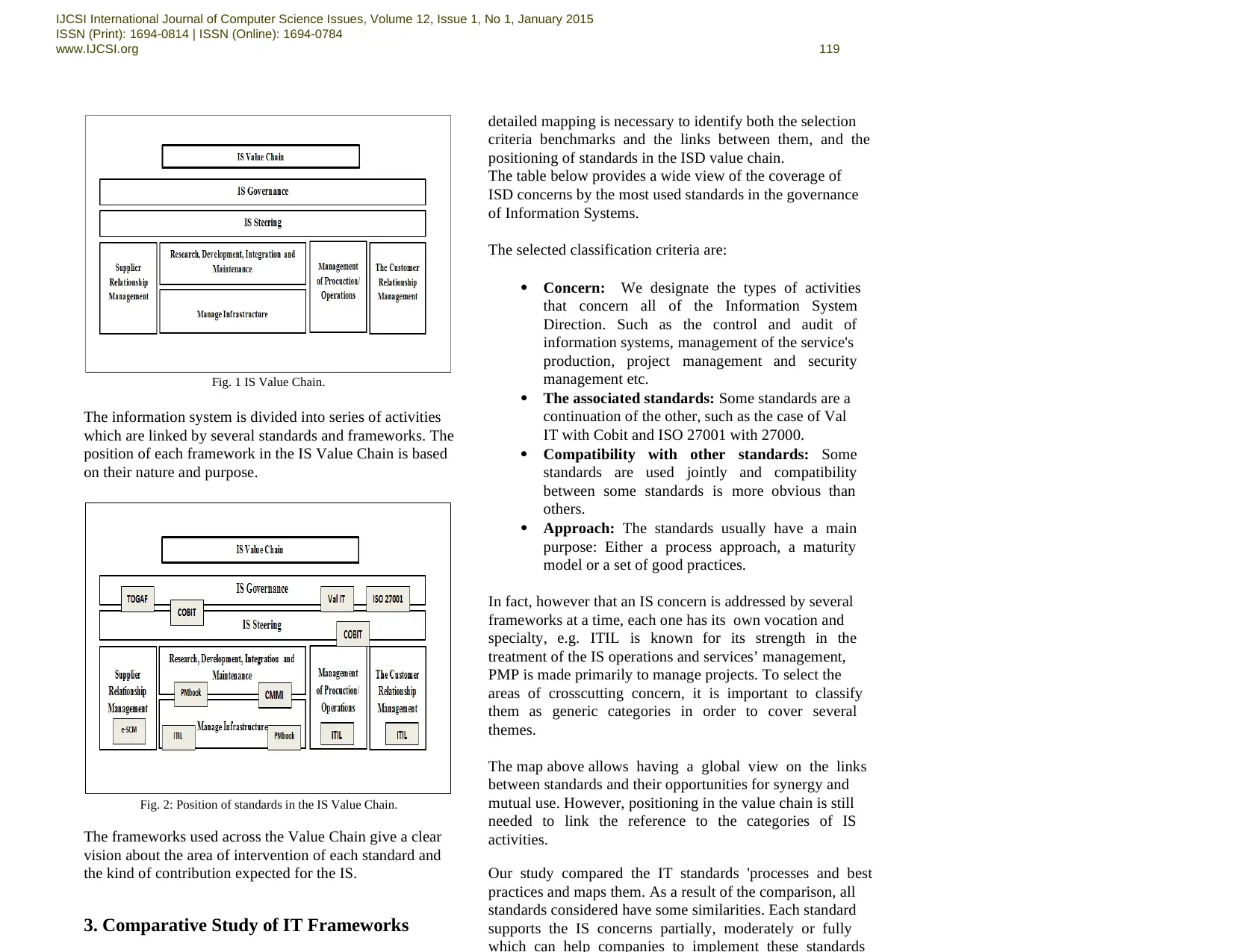
Fig. 1 IS Value Chain.
The information system is divided into series of activities
which are linked by several standards and frameworks. The
position of each framework in the IS Value Chain is based
on their nature and purpose.
Fig. 2: Position of standards in the IS Value Chain.
The frameworks used across the Value Chain give a clear
vision about the area of intervention of each standard and
the kind of contribution expected for the IS.
3. Comparative Study of IT Frameworks
detailed mapping is necessary to identify both the selection
criteria benchmarks and the links between them, and the
positioning of standards in the ISD value chain.
The table below provides a wide view of the coverage of
ISD concerns by the most used standards in the governance
of Information Systems.
The selected classification criteria are:
Concern: We designate the types of activities
that concern all of the Information System
Direction. Such as the control and audit of
information systems, management of the service's
production, project management and security
management etc.
The associated standards: Some standards are a
continuation of the other, such as the case of Val
IT with Cobit and ISO 27001 with 27000.
Compatibility with other standards: Some
standards are used jointly and compatibility
between some standards is more obvious than
others.
Approach: The standards usually have a main
purpose: Either a process approach, a maturity
model or a set of good practices.
In fact, however that an IS concern is addressed by several
frameworks at a time, each one has its own vocation and
specialty, e.g. ITIL is known for its strength in the
treatment of the IS operations and services’ management,
PMP is made primarily to manage projects. To select the
areas of crosscutting concern, it is important to classify
them as generic categories in order to cover several
themes.
The map above allows having a global view on the links
between standards and their opportunities for synergy and
mutual use. However, positioning in the value chain is still
needed to link the reference to the categories of IS
activities.
Our study compared the IT standards 'processes and best
practices and maps them. As a result of the comparison, all
standards considered have some similarities. Each standard
supports the IS concerns partially, moderately or fully
which can help companies to implement these standards
IJCSI International Journal of Computer Science Issues, Volume 12, Issue 1, No 1, January 2015
ISSN (Print): 1694-0814 | ISSN (Online): 1694-0784
www.IJCSI.org 119
The information system is divided into series of activities
which are linked by several standards and frameworks. The
position of each framework in the IS Value Chain is based
on their nature and purpose.
Fig. 2: Position of standards in the IS Value Chain.
The frameworks used across the Value Chain give a clear
vision about the area of intervention of each standard and
the kind of contribution expected for the IS.
3. Comparative Study of IT Frameworks
detailed mapping is necessary to identify both the selection
criteria benchmarks and the links between them, and the
positioning of standards in the ISD value chain.
The table below provides a wide view of the coverage of
ISD concerns by the most used standards in the governance
of Information Systems.
The selected classification criteria are:
Concern: We designate the types of activities
that concern all of the Information System
Direction. Such as the control and audit of
information systems, management of the service's
production, project management and security
management etc.
The associated standards: Some standards are a
continuation of the other, such as the case of Val
IT with Cobit and ISO 27001 with 27000.
Compatibility with other standards: Some
standards are used jointly and compatibility
between some standards is more obvious than
others.
Approach: The standards usually have a main
purpose: Either a process approach, a maturity
model or a set of good practices.
In fact, however that an IS concern is addressed by several
frameworks at a time, each one has its own vocation and
specialty, e.g. ITIL is known for its strength in the
treatment of the IS operations and services’ management,
PMP is made primarily to manage projects. To select the
areas of crosscutting concern, it is important to classify
them as generic categories in order to cover several
themes.
The map above allows having a global view on the links
between standards and their opportunities for synergy and
mutual use. However, positioning in the value chain is still
needed to link the reference to the categories of IS
activities.
Our study compared the IT standards 'processes and best
practices and maps them. As a result of the comparison, all
standards considered have some similarities. Each standard
supports the IS concerns partially, moderately or fully
which can help companies to implement these standards
IJCSI International Journal of Computer Science Issues, Volume 12, Issue 1, No 1, January 2015
ISSN (Print): 1694-0814 | ISSN (Online): 1694-0784
www.IJCSI.org 119
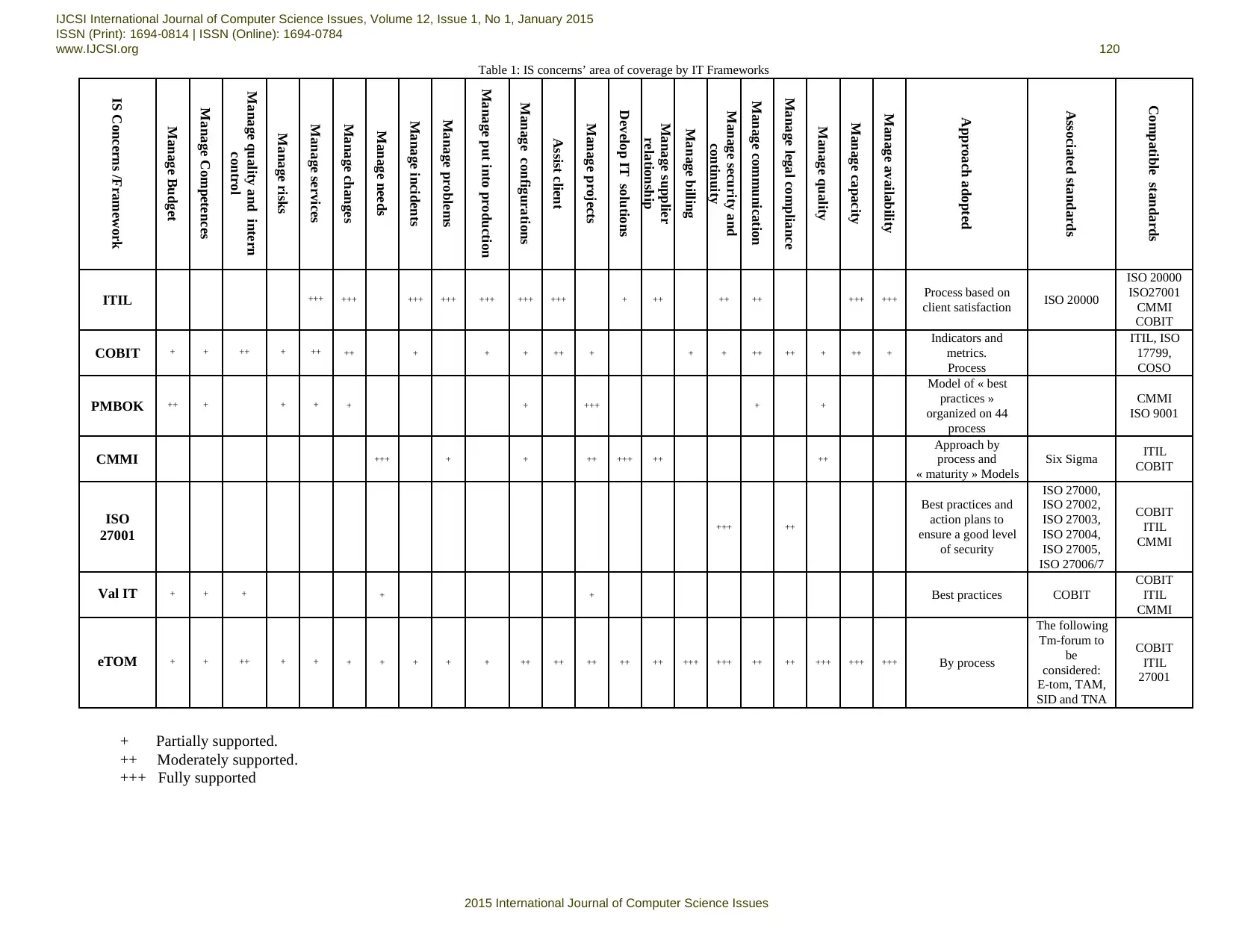
Table 1: IS concerns’ area of coverage by IT Frameworks
IS Concerns /Framework
Manage Budget
Manage Competences
Manage quality and intern
control
Manage risks
Manage services
Manage changes
Manage needs
Manage incidents
Manage problems
Manage put into production
Manage configurations
Assist client
Manage projects
Develop IT solutions
Manage supplier
relationship
Manage billing
Manage security and
continuity
Manage communication
Manage legal compliance
Manage quality
Manage capacity
Manage availability
Approach adopted
Associated standards
Compatible standards
ITIL +++ +++ +++ +++ +++ +++ +++ + ++ ++ ++ +++ +++ Process based on
client satisfaction ISO 20000
ISO 20000
ISO27001
CMMI
COBIT
COBIT + + ++ + ++ ++ + + + ++ + + + ++ ++ + ++ +
Indicators and
metrics.
Process
ITIL, ISO
17799,
COSO
PMBOK ++ + + + + + +++ + +
Model of « best
practices »
organized on 44
process
CMMI
ISO 9001
CMMI +++ + + ++ +++ ++ ++
Approach by
process and
« maturity » Models
Six Sigma ITIL
COBIT
ISO
27001 +++ ++
Best practices and
action plans to
ensure a good level
of security
ISO 27000,
ISO 27002,
ISO 27003,
ISO 27004,
ISO 27005,
ISO 27006/7
COBIT
ITIL
CMMI
Val IT + + + + + Best practices COBIT
COBIT
ITIL
CMMI
eTOM + + ++ + + + + + + + ++ ++ ++ ++ ++ +++ +++ ++ ++ +++ +++ +++ By process
The following
Tm-forum to
be
considered:
E-tom, TAM,
SID and TNA
COBIT
ITIL
27001
+ Partially supported.
++ Moderately supported.
+++ Fully supported
IJCSI International Journal of Computer Science Issues, Volume 12, Issue 1, No 1, January 2015
ISSN (Print): 1694-0814 | ISSN (Online): 1694-0784
www.IJCSI.org 120
2015 International Journal of Computer Science Issues
IS Concerns /Framework
Manage Budget
Manage Competences
Manage quality and intern
control
Manage risks
Manage services
Manage changes
Manage needs
Manage incidents
Manage problems
Manage put into production
Manage configurations
Assist client
Manage projects
Develop IT solutions
Manage supplier
relationship
Manage billing
Manage security and
continuity
Manage communication
Manage legal compliance
Manage quality
Manage capacity
Manage availability
Approach adopted
Associated standards
Compatible standards
ITIL +++ +++ +++ +++ +++ +++ +++ + ++ ++ ++ +++ +++ Process based on
client satisfaction ISO 20000
ISO 20000
ISO27001
CMMI
COBIT
COBIT + + ++ + ++ ++ + + + ++ + + + ++ ++ + ++ +
Indicators and
metrics.
Process
ITIL, ISO
17799,
COSO
PMBOK ++ + + + + + +++ + +
Model of « best
practices »
organized on 44
process
CMMI
ISO 9001
CMMI +++ + + ++ +++ ++ ++
Approach by
process and
« maturity » Models
Six Sigma ITIL
COBIT
ISO
27001 +++ ++
Best practices and
action plans to
ensure a good level
of security
ISO 27000,
ISO 27002,
ISO 27003,
ISO 27004,
ISO 27005,
ISO 27006/7
COBIT
ITIL
CMMI
Val IT + + + + + Best practices COBIT
COBIT
ITIL
CMMI
eTOM + + ++ + + + + + + + ++ ++ ++ ++ ++ +++ +++ ++ ++ +++ +++ +++ By process
The following
Tm-forum to
be
considered:
E-tom, TAM,
SID and TNA
COBIT
ITIL
27001
+ Partially supported.
++ Moderately supported.
+++ Fully supported
IJCSI International Journal of Computer Science Issues, Volume 12, Issue 1, No 1, January 2015
ISSN (Print): 1694-0814 | ISSN (Online): 1694-0784
www.IJCSI.org 120
2015 International Journal of Computer Science Issues
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
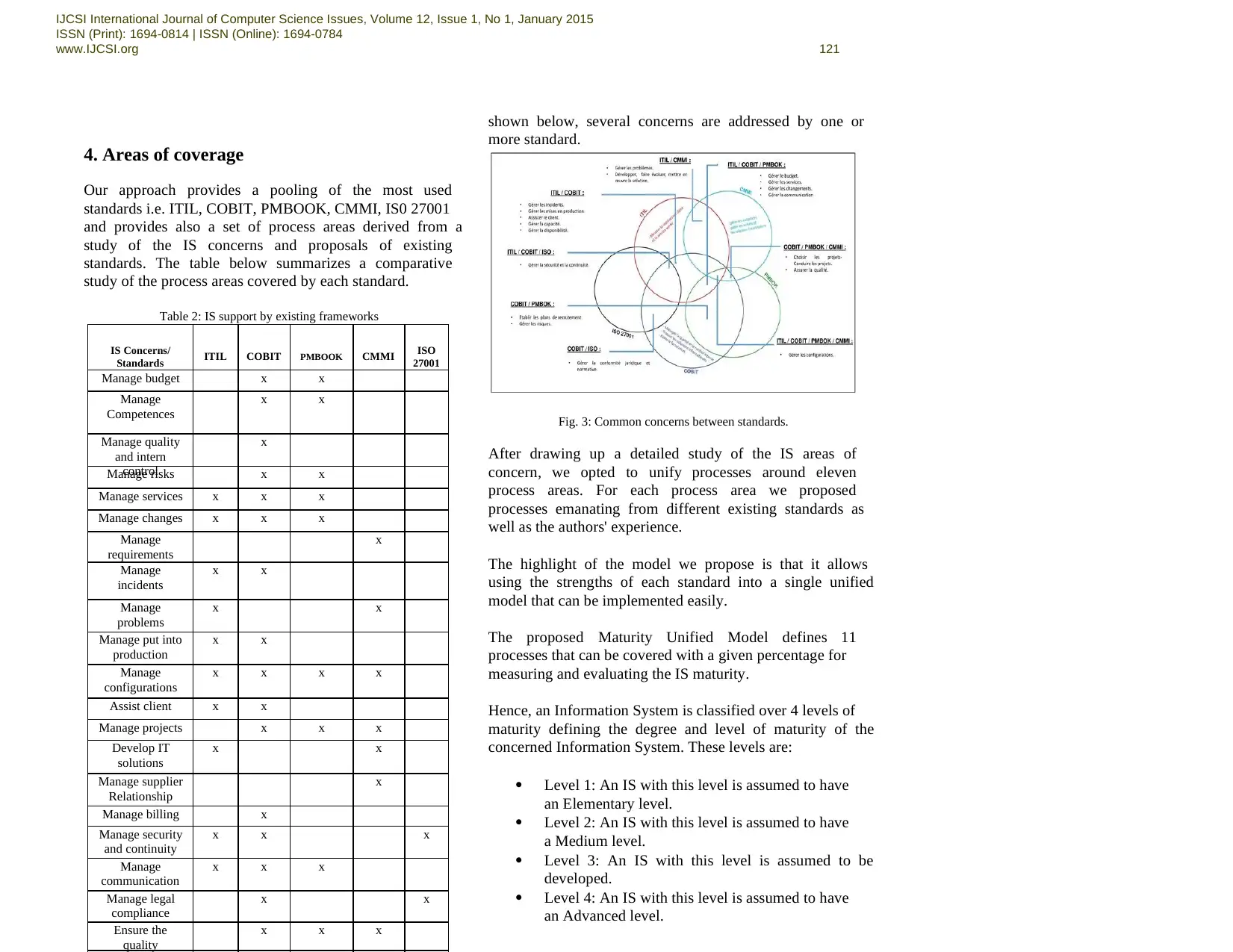
4. Areas of coverage
Our approach provides a pooling of the most used
standards i.e. ITIL, COBIT, PMBOOK, CMMI, IS0 27001
and provides also a set of process areas derived from a
study of the IS concerns and proposals of existing
standards. The table below summarizes a comparative
study of the process areas covered by each standard.
Table 2: IS support by existing frameworks
IS Concerns/
Standards ITIL COBIT PMBOOK CMMI ISO
27001
Manage budget x x
Manage
Competences
x x
Manage quality
and intern
control
x
Manage risks x x
Manage services x x x
Manage changes x x x
Manage
requirements
x
Manage
incidents
x x
Manage
problems
x x
Manage put into
production
x x
Manage
configurations
x x x x
Assist client x x
Manage projects x x x
Develop IT
solutions
x x
Manage supplier
Relationship
x
Manage billing x
Manage security
and continuity
x x x
Manage
communication
x x x
Manage legal
compliance
x x
Ensure the
quality
x x x
shown below, several concerns are addressed by one or
more standard.
Fig. 3: Common concerns between standards.
After drawing up a detailed study of the IS areas of
concern, we opted to unify processes around eleven
process areas. For each process area we proposed
processes emanating from different existing standards as
well as the authors' experience.
The highlight of the model we propose is that it allows
using the strengths of each standard into a single unified
model that can be implemented easily.
The proposed Maturity Unified Model defines 11
processes that can be covered with a given percentage for
measuring and evaluating the IS maturity.
Hence, an Information System is classified over 4 levels of
maturity defining the degree and level of maturity of the
concerned Information System. These levels are:
Level 1: An IS with this level is assumed to have
an Elementary level.
Level 2: An IS with this level is assumed to have
a Medium level.
Level 3: An IS with this level is assumed to be
developed.
Level 4: An IS with this level is assumed to have
an Advanced level.
IJCSI International Journal of Computer Science Issues, Volume 12, Issue 1, No 1, January 2015
ISSN (Print): 1694-0814 | ISSN (Online): 1694-0784
www.IJCSI.org 121
Our approach provides a pooling of the most used
standards i.e. ITIL, COBIT, PMBOOK, CMMI, IS0 27001
and provides also a set of process areas derived from a
study of the IS concerns and proposals of existing
standards. The table below summarizes a comparative
study of the process areas covered by each standard.
Table 2: IS support by existing frameworks
IS Concerns/
Standards ITIL COBIT PMBOOK CMMI ISO
27001
Manage budget x x
Manage
Competences
x x
Manage quality
and intern
control
x
Manage risks x x
Manage services x x x
Manage changes x x x
Manage
requirements
x
Manage
incidents
x x
Manage
problems
x x
Manage put into
production
x x
Manage
configurations
x x x x
Assist client x x
Manage projects x x x
Develop IT
solutions
x x
Manage supplier
Relationship
x
Manage billing x
Manage security
and continuity
x x x
Manage
communication
x x x
Manage legal
compliance
x x
Ensure the
quality
x x x
shown below, several concerns are addressed by one or
more standard.
Fig. 3: Common concerns between standards.
After drawing up a detailed study of the IS areas of
concern, we opted to unify processes around eleven
process areas. For each process area we proposed
processes emanating from different existing standards as
well as the authors' experience.
The highlight of the model we propose is that it allows
using the strengths of each standard into a single unified
model that can be implemented easily.
The proposed Maturity Unified Model defines 11
processes that can be covered with a given percentage for
measuring and evaluating the IS maturity.
Hence, an Information System is classified over 4 levels of
maturity defining the degree and level of maturity of the
concerned Information System. These levels are:
Level 1: An IS with this level is assumed to have
an Elementary level.
Level 2: An IS with this level is assumed to have
a Medium level.
Level 3: An IS with this level is assumed to be
developed.
Level 4: An IS with this level is assumed to have
an Advanced level.
IJCSI International Journal of Computer Science Issues, Volume 12, Issue 1, No 1, January 2015
ISSN (Print): 1694-0814 | ISSN (Online): 1694-0784
www.IJCSI.org 121
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
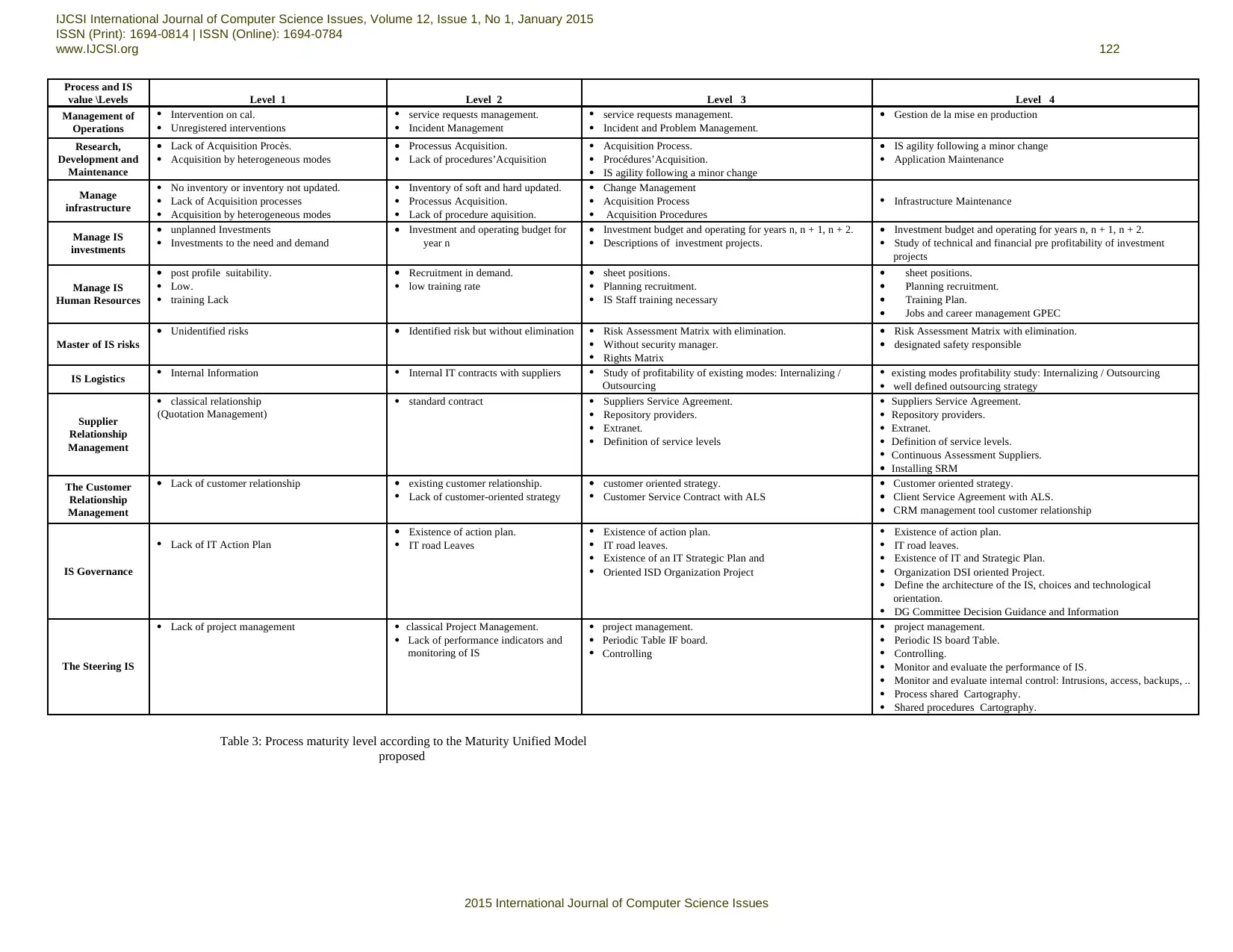
Table 3: Process maturity level according to the Maturity Unified Model
proposed
Process and IS
value \Levels Level 1 Level 2 Level 3 Level 4
Management of
Operations
Intervention on cal.
Unregistered interventions
service requests management.
Incident Management
service requests management.
Incident and Problem Management.
Gestion de la mise en production
Research,
Development and
Maintenance
Lack of Acquisition Procès.
Acquisition by heterogeneous modes
Processus Acquisition.
Lack of procedures’Acquisition
Acquisition Process.
Procédures’Acquisition.
IS agility following a minor change
IS agility following a minor change
Application Maintenance
Manage
infrastructure
No inventory or inventory not updated.
Lack of Acquisition processes
Acquisition by heterogeneous modes
Inventory of soft and hard updated.
Processus Acquisition.
Lack of procedure aquisition.
Change Management
Acquisition Process
Acquisition Procedures
Infrastructure Maintenance
Manage IS
investments
unplanned Investments
Investments to the need and demand
Investment and operating budget for
year n
Investment budget and operating for years n, n + 1, n + 2.
Descriptions of investment projects.
Investment budget and operating for years n, n + 1, n + 2.
Study of technical and financial pre profitability of investment
projects
Manage IS
Human Resources
post profile suitability.
Low.
training Lack
Recruitment in demand.
low training rate
sheet positions.
Planning recruitment.
IS Staff training necessary
sheet positions.
Planning recruitment.
Training Plan.
Jobs and career management GPEC
Master of IS risks
Unidentified risks Identified risk but without elimination Risk Assessment Matrix with elimination.
Without security manager.
Rights Matrix
Risk Assessment Matrix with elimination.
designated safety responsible
IS Logistics Internal Information Internal IT contracts with suppliers Study of profitability of existing modes: Internalizing /
Outsourcing
existing modes profitability study: Internalizing / Outsourcing
well defined outsourcing strategy
Supplier
Relationship
Management
classical relationship
(Quotation Management)
standard contract Suppliers Service Agreement.
Repository providers.
Extranet.
Definition of service levels
Suppliers Service Agreement.
Repository providers.
Extranet.
Definition of service levels.
Continuous Assessment Suppliers.
Installing SRM
The Customer
Relationship
Management
Lack of customer relationship existing customer relationship.
Lack of customer-oriented strategy
customer oriented strategy.
Customer Service Contract with ALS
Customer oriented strategy.
Client Service Agreement with ALS.
CRM management tool customer relationship
IS Governance
Lack of IT Action Plan
Existence of action plan.
IT road Leaves
Existence of action plan.
IT road leaves.
Existence of an IT Strategic Plan and
Oriented ISD Organization Project
Existence of action plan.
IT road leaves.
Existence of IT and Strategic Plan.
Organization DSI oriented Project.
Define the architecture of the IS, choices and technological
orientation.
DG Committee Decision Guidance and Information
The Steering IS
Lack of project management classical Project Management.
Lack of performance indicators and
monitoring of IS
project management.
Periodic Table IF board.
Controlling
project management.
Periodic IS board Table.
Controlling.
Monitor and evaluate the performance of IS.
Monitor and evaluate internal control: Intrusions, access, backups, ..
Process shared Cartography.
Shared procedures Cartography.
IJCSI International Journal of Computer Science Issues, Volume 12, Issue 1, No 1, January 2015
ISSN (Print): 1694-0814 | ISSN (Online): 1694-0784
www.IJCSI.org 122
2015 International Journal of Computer Science Issues
proposed
Process and IS
value \Levels Level 1 Level 2 Level 3 Level 4
Management of
Operations
Intervention on cal.
Unregistered interventions
service requests management.
Incident Management
service requests management.
Incident and Problem Management.
Gestion de la mise en production
Research,
Development and
Maintenance
Lack of Acquisition Procès.
Acquisition by heterogeneous modes
Processus Acquisition.
Lack of procedures’Acquisition
Acquisition Process.
Procédures’Acquisition.
IS agility following a minor change
IS agility following a minor change
Application Maintenance
Manage
infrastructure
No inventory or inventory not updated.
Lack of Acquisition processes
Acquisition by heterogeneous modes
Inventory of soft and hard updated.
Processus Acquisition.
Lack of procedure aquisition.
Change Management
Acquisition Process
Acquisition Procedures
Infrastructure Maintenance
Manage IS
investments
unplanned Investments
Investments to the need and demand
Investment and operating budget for
year n
Investment budget and operating for years n, n + 1, n + 2.
Descriptions of investment projects.
Investment budget and operating for years n, n + 1, n + 2.
Study of technical and financial pre profitability of investment
projects
Manage IS
Human Resources
post profile suitability.
Low.
training Lack
Recruitment in demand.
low training rate
sheet positions.
Planning recruitment.
IS Staff training necessary
sheet positions.
Planning recruitment.
Training Plan.
Jobs and career management GPEC
Master of IS risks
Unidentified risks Identified risk but without elimination Risk Assessment Matrix with elimination.
Without security manager.
Rights Matrix
Risk Assessment Matrix with elimination.
designated safety responsible
IS Logistics Internal Information Internal IT contracts with suppliers Study of profitability of existing modes: Internalizing /
Outsourcing
existing modes profitability study: Internalizing / Outsourcing
well defined outsourcing strategy
Supplier
Relationship
Management
classical relationship
(Quotation Management)
standard contract Suppliers Service Agreement.
Repository providers.
Extranet.
Definition of service levels
Suppliers Service Agreement.
Repository providers.
Extranet.
Definition of service levels.
Continuous Assessment Suppliers.
Installing SRM
The Customer
Relationship
Management
Lack of customer relationship existing customer relationship.
Lack of customer-oriented strategy
customer oriented strategy.
Customer Service Contract with ALS
Customer oriented strategy.
Client Service Agreement with ALS.
CRM management tool customer relationship
IS Governance
Lack of IT Action Plan
Existence of action plan.
IT road Leaves
Existence of action plan.
IT road leaves.
Existence of an IT Strategic Plan and
Oriented ISD Organization Project
Existence of action plan.
IT road leaves.
Existence of IT and Strategic Plan.
Organization DSI oriented Project.
Define the architecture of the IS, choices and technological
orientation.
DG Committee Decision Guidance and Information
The Steering IS
Lack of project management classical Project Management.
Lack of performance indicators and
monitoring of IS
project management.
Periodic Table IF board.
Controlling
project management.
Periodic IS board Table.
Controlling.
Monitor and evaluate the performance of IS.
Monitor and evaluate internal control: Intrusions, access, backups, ..
Process shared Cartography.
Shared procedures Cartography.
IJCSI International Journal of Computer Science Issues, Volume 12, Issue 1, No 1, January 2015
ISSN (Print): 1694-0814 | ISSN (Online): 1694-0784
www.IJCSI.org 122
2015 International Journal of Computer Science Issues

4. Conclusions
Standards of good practices have been designed to meet
the needs of structuring information systems management
processes. The diversity of standards vocations and wealth
makes their use tedious and expensive. IS Managers are
confronted to multiple standards having each own
terminology, proper processes and a separate
implementation methodology. Articles about this are
increasing, and each initiative attempts to focus on the
possibilities of "mapping" two or more standards [7] [8].
At the end of this article a model of unified standards is
proposed to solve the redundancy problem of standards.
Moreover, the effectiveness of a standard implementation
depends on the level of maturity of the various IS
management processes. It would be then necessary to
include such reference in a unified process of evaluating
capacities and global maturity of the IS.
References
[1] Kamprath, N. and Röglinger, M. (2011), Ökonomische
Planung von Prozessverbesserungsmaßnahmen – Ein
modelltheoretischer Ansatz auf Grundlage CMMI-basierter
Prozessreifegradmodelle. Internationale Tagung
Wirtschaftsinformatik (WI2011). Zürich, Switzerland.
[2] P. B. Nassar, Y. Badr, F. Biennier, K. Barbar ―Securing
Collaborative Business Processes: A Methodology for
Security Management in Service-Based Infrastructure”, IFIP
International Federation for Information Processing, Ifip
Aict 384, 2012, pp. 480–487.
[3] D. Botta, K. Muldner, K. Hawkey, K. Beznosov, “Toward
understanding distributed cognition in IT security
management: the role of cues and norms”, Cognition,
Technology & Work, Volume 13, Issue 2, June 2011,
[4] Hill P. and Turbitt K,”Combine ITIL and COBIT to
MeetBusiness Challenges”, BMC Software, 2007,
BMC_BPWP_ITIL_COBIT_06.pdf Companies by type,
(n.d.). In Wikipedia, Retrieved July 2008
[5] Tanguy Crusson. Business process management : De la
modélisation à l’exécution, positionnement par rapport aux
architectures orientées services. Intalio, 2003.
IJCSI International Journal of Computer Science Issues, Volume 12, Issue 1, No 1, January 2015
ISSN (Print): 1694-0814 | ISSN (Online): 1694-0784
www.IJCSI.org 123
Standards of good practices have been designed to meet
the needs of structuring information systems management
processes. The diversity of standards vocations and wealth
makes their use tedious and expensive. IS Managers are
confronted to multiple standards having each own
terminology, proper processes and a separate
implementation methodology. Articles about this are
increasing, and each initiative attempts to focus on the
possibilities of "mapping" two or more standards [7] [8].
At the end of this article a model of unified standards is
proposed to solve the redundancy problem of standards.
Moreover, the effectiveness of a standard implementation
depends on the level of maturity of the various IS
management processes. It would be then necessary to
include such reference in a unified process of evaluating
capacities and global maturity of the IS.
References
[1] Kamprath, N. and Röglinger, M. (2011), Ökonomische
Planung von Prozessverbesserungsmaßnahmen – Ein
modelltheoretischer Ansatz auf Grundlage CMMI-basierter
Prozessreifegradmodelle. Internationale Tagung
Wirtschaftsinformatik (WI2011). Zürich, Switzerland.
[2] P. B. Nassar, Y. Badr, F. Biennier, K. Barbar ―Securing
Collaborative Business Processes: A Methodology for
Security Management in Service-Based Infrastructure”, IFIP
International Federation for Information Processing, Ifip
Aict 384, 2012, pp. 480–487.
[3] D. Botta, K. Muldner, K. Hawkey, K. Beznosov, “Toward
understanding distributed cognition in IT security
management: the role of cues and norms”, Cognition,
Technology & Work, Volume 13, Issue 2, June 2011,
[4] Hill P. and Turbitt K,”Combine ITIL and COBIT to
MeetBusiness Challenges”, BMC Software, 2007,
BMC_BPWP_ITIL_COBIT_06.pdf Companies by type,
(n.d.). In Wikipedia, Retrieved July 2008
[5] Tanguy Crusson. Business process management : De la
modélisation à l’exécution, positionnement par rapport aux
architectures orientées services. Intalio, 2003.
IJCSI International Journal of Computer Science Issues, Volume 12, Issue 1, No 1, January 2015
ISSN (Print): 1694-0814 | ISSN (Online): 1694-0784
www.IJCSI.org 123
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 6
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.
