IT Infrastructure Report: Network Devices and Communication
VerifiedAdded on 2022/09/13
|13
|2817
|14
Report
AI Summary
This report provides a detailed analysis of the IT infrastructure of the ABC Company. It begins with an introduction to the company's IT needs, including its website, database, and employee systems across three floors. The report then identifies key network devices like firewalls, routers, and switches, explaining their functions and importance. It delves into client-server communication models, including the use of email and web browsers, and the application software used by the company. Furthermore, the report describes the process of data communication, focusing on an email sent between employees on different floors, and explains the data flow through the seven layers of the OSI model. The report concludes by summarizing the key findings and emphasizing the significance of the IT infrastructure in enabling the company to provide services to its clients.

Running head: IT INFRASTRUCTURE
IT INFRASTRUCTURE
Name of the Student
Name of the University
Author Note
IT INFRASTRUCTURE
Name of the Student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1IT INFRASTRUCTURE
Table of Contents
Introduction:...............................................................................................................................2
Identification of Network Devices.............................................................................................2
Communication Application and Software................................................................................4
Data Communication in the Company.......................................................................................5
Conclusion..................................................................................................................................7
References..................................................................................................................................8
Table of Contents
Introduction:...............................................................................................................................2
Identification of Network Devices.............................................................................................2
Communication Application and Software................................................................................4
Data Communication in the Company.......................................................................................5
Conclusion..................................................................................................................................7
References..................................................................................................................................8

2IT INFRASTRUCTURE
Introduction:
The IT infrastructure is one of the most essential parts of the ABC Company as the
major work of the company is done by the IT infrastructure. The company that is provided
here is the ABC Company. The ABC Company must provide information system services to
their clients and the employees of company including webpage, database and webpage. The
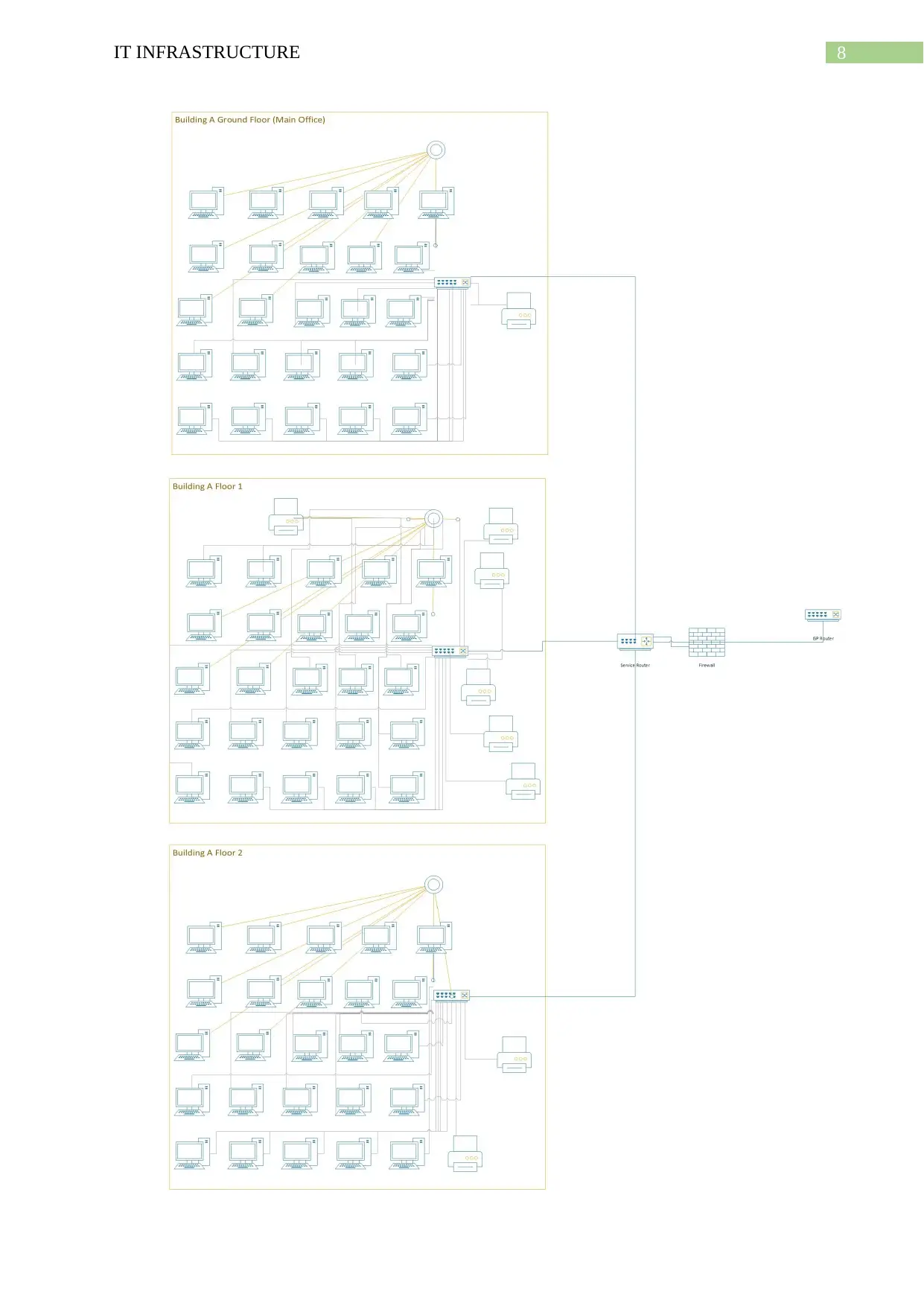
office of the ABC Company consists of three floors of which the ground floor is the main
office. The main office includes two computers and a shared printer and the other two floors
have 25 computers each and six printers those are shared in each of the floors. The ABC
Company has a website that offers the clients of the company with general information and
the clients can purchase various products and services from the website.
The report deals with the identification and the discussions about the about the
devices of network those are required in order to achieve the requirements of the
organization. The functions of the devices are discussed in the report. The report discusses
about the client sever communication software and the application software that are required
in order to accomplish the requirements of the company. The report provides an overview of
transmission of email with an appropriate diagram.
Identification of Network Devices
For the appropriate working of the company, the company requires to implement
proper devices of network in order to accomplish the requirements of the company. The
devices of network those are implemented in the company include firewalls, routers and
switches.
A firewall is a device of security of network that administers the outgoing as well the
incoming traffic of network and allows or obstructs the data packets that is based on a
sequence of regulations of security. The main aim of firewall in to develop a obstruction
Introduction:
The IT infrastructure is one of the most essential parts of the ABC Company as the
major work of the company is done by the IT infrastructure. The company that is provided
here is the ABC Company. The ABC Company must provide information system services to
their clients and the employees of company including webpage, database and webpage. The
office of the ABC Company consists of three floors of which the ground floor is the main
office. The main office includes two computers and a shared printer and the other two floors
have 25 computers each and six printers those are shared in each of the floors. The ABC
Company has a website that offers the clients of the company with general information and
the clients can purchase various products and services from the website.
The report deals with the identification and the discussions about the about the
devices of network those are required in order to achieve the requirements of the
organization. The functions of the devices are discussed in the report. The report discusses
about the client sever communication software and the application software that are required
in order to accomplish the requirements of the company. The report provides an overview of
transmission of email with an appropriate diagram.
Identification of Network Devices
For the appropriate working of the company, the company requires to implement
proper devices of network in order to accomplish the requirements of the company. The
devices of network those are implemented in the company include firewalls, routers and
switches.
A firewall is a device of security of network that administers the outgoing as well the
incoming traffic of network and allows or obstructs the data packets that is based on a
sequence of regulations of security. The main aim of firewall in to develop a obstruction
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3IT INFRASTRUCTURE
between the incoming traffic and the internal network from the sources those are external to
obstruct the damaging traffic like hackers and the viruses (Soewito and Andhika 2019). The
firewalls evaluate the traffic that is based on rules and then filter the traffic that is coming
from unsecured sources in order to stop the attacks. Firewalls safeguard the traffic at the point
of entry of the computer known as ports. The ports are where various information are shared
with the external devices. The firewall generally works at the layer 3 and layer 4 of the OSI
model. Various sophisticated firewalls work at the layer 7 of the OSI model.
A router is a virtual or a physical device that passé various information between
multiple computer networks those are packet switched (Alani 2017). A router examines
packet destination, the Internet protocol of a data and then it calculates the best possible way
for the data to reach the destination, and then it forwards the data accordingly. A router
evaluates destination IP address of a data and then compares the data against a table of
routing in order to decide the next hop of the packet. There are two types of routers used by
the organization. These include service routers and ISP routers. The routers work at the layer
3 of the OSI model that is the network layer (Kloth 2018).
A switch is a network device that is utilised in a wired network in order to connect all
the devices utilising the cables of Ethernet (Gallo and Pianese 2018). The switch permits each
device those are connected to talk to each other. The wireless networks do not utilise switches
such as the wireless adapters communicate directly with each other. The main functionality of
switch is to otain any kind of information from any of the source that is connected to it. The
switch send off information to the proper destination only. This is the difference between
hubs and switches (Nirasawa et al 2016). The switches work at the layer 2 of the OSI model.
between the incoming traffic and the internal network from the sources those are external to
obstruct the damaging traffic like hackers and the viruses (Soewito and Andhika 2019). The
firewalls evaluate the traffic that is based on rules and then filter the traffic that is coming
from unsecured sources in order to stop the attacks. Firewalls safeguard the traffic at the point
of entry of the computer known as ports. The ports are where various information are shared
with the external devices. The firewall generally works at the layer 3 and layer 4 of the OSI
model. Various sophisticated firewalls work at the layer 7 of the OSI model.
A router is a virtual or a physical device that passé various information between
multiple computer networks those are packet switched (Alani 2017). A router examines
packet destination, the Internet protocol of a data and then it calculates the best possible way
for the data to reach the destination, and then it forwards the data accordingly. A router
evaluates destination IP address of a data and then compares the data against a table of
routing in order to decide the next hop of the packet. There are two types of routers used by
the organization. These include service routers and ISP routers. The routers work at the layer
3 of the OSI model that is the network layer (Kloth 2018).
A switch is a network device that is utilised in a wired network in order to connect all
the devices utilising the cables of Ethernet (Gallo and Pianese 2018). The switch permits each
device those are connected to talk to each other. The wireless networks do not utilise switches
such as the wireless adapters communicate directly with each other. The main functionality of
switch is to otain any kind of information from any of the source that is connected to it. The
switch send off information to the proper destination only. This is the difference between
hubs and switches (Nirasawa et al 2016). The switches work at the layer 2 of the OSI model.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4IT INFRASTRUCTURE
Communication Application and Software
The communication of the ABC works by the client-server communication model. In
a client server, communication there are more than one client and a server is present. The
messages between a server and a client are exchanged request-response pattern of messaging.
First, the client dispatches a request and after that, the server returns a response (de Souza
Soares et al 2018). This example of communication is known as the inter-process
communication. The rules and language of communication are defined in the protocol of
communication. All the protocols of server and client work in the layer of application. In
order to formalize the exchange of data, the server can deploy an application-programming
interface. The API is a layer of abstraction in order to access a service. A server can receive
large number of requests from multiple clients in a very short period. A computer can only
execute restricted number of tasks at a time therefore; it depends of the system of scheduling
to accommodate the requests coming from the clients (Choi and Chang 2019). The denial of
services attacks are designed in order to utilise obligation of a server to process the request by
congesting it with excess rates of request. Encryption must be applied if any kind of sensitive
information is to be transmitted between the server and the client.
The company utilises Email in order to connect with the clients. The email is an
application of client server communication. The application software that can be used by the
ABC Company in order to accomplish the requirements is MS Outlook. Application software
is used for email (Liang 2018).
The World Wide is an example of client server communication and it is based on
hypertext documents. Therefore, any web browser such as Google Chrome, Mozilla Firefox
and many more browsers are client-server communication software that is used by the
company. The website of the company that is used by the company is also an example of
client-server communication model (De Sutter et al 2016).
Communication Application and Software
The communication of the ABC works by the client-server communication model. In
a client server, communication there are more than one client and a server is present. The
messages between a server and a client are exchanged request-response pattern of messaging.
First, the client dispatches a request and after that, the server returns a response (de Souza
Soares et al 2018). This example of communication is known as the inter-process
communication. The rules and language of communication are defined in the protocol of
communication. All the protocols of server and client work in the layer of application. In
order to formalize the exchange of data, the server can deploy an application-programming
interface. The API is a layer of abstraction in order to access a service. A server can receive
large number of requests from multiple clients in a very short period. A computer can only
execute restricted number of tasks at a time therefore; it depends of the system of scheduling
to accommodate the requests coming from the clients (Choi and Chang 2019). The denial of
services attacks are designed in order to utilise obligation of a server to process the request by
congesting it with excess rates of request. Encryption must be applied if any kind of sensitive
information is to be transmitted between the server and the client.
The company utilises Email in order to connect with the clients. The email is an
application of client server communication. The application software that can be used by the
ABC Company in order to accomplish the requirements is MS Outlook. Application software
is used for email (Liang 2018).
The World Wide is an example of client server communication and it is based on
hypertext documents. Therefore, any web browser such as Google Chrome, Mozilla Firefox
and many more browsers are client-server communication software that is used by the
company. The website of the company that is used by the company is also an example of
client-server communication model (De Sutter et al 2016).

5IT INFRASTRUCTURE
Data Communication in the Company
The office off the ABC Company has three floors. The ground floor is the main office
and consists of two computers and a shared printer. The other two floors have 25 computers
and 6 printers each. The scenario is that an employee in the ground floor sends an email to
the employee at the third floor. The email will be delivered through the seven layers of OSI
model.
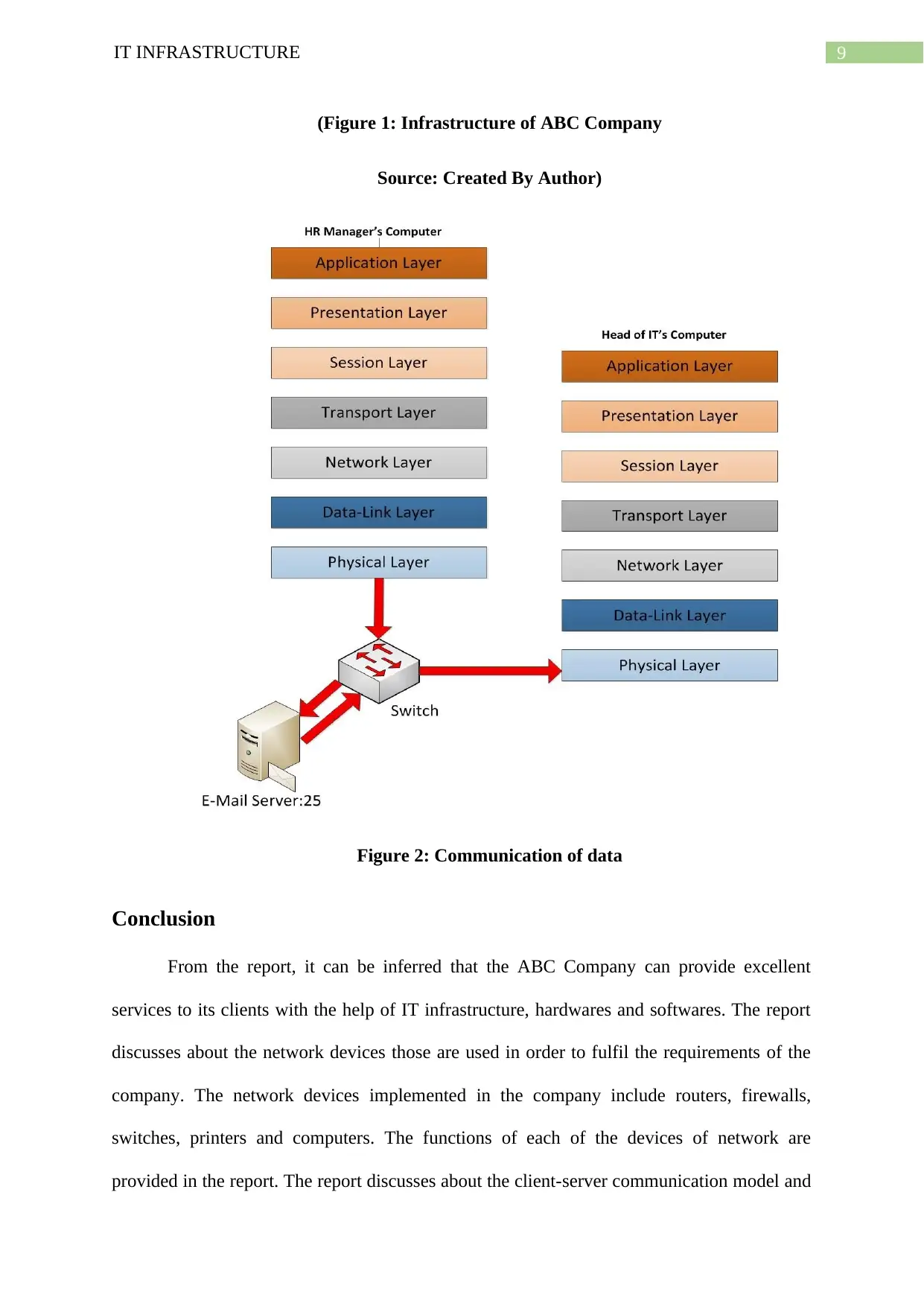
When the email is send by the employee at the ground floor, it goes in the application
layer of the model of OSI. It offers the interface for the end user in order to tell the computer
the way to handle the data (Zhao et al 2018). In this scenario, the SMTP protocol will be used
and it will command the computer a way to handle the data.
After this, the email starts operating at the transport layer of the model of OSI. The
content of email will be changed to the formats of network. The text of the email will be
changed to ASCII values and the images of the email will be converted to JPEG, PNG and
many more. The encryption and compression of data will take place in this layer. In this
layer, th secure socket layer will be used for the encryption of data.
After this, the email will start operating in the session layer of the model of OSI. The
session layer will be responsible in order to start, handle and terminate the connection. In this
scenario, the session layer is responsible in order to keep the connection with the employee at
the ground floor. The session layer develops, manages and then terminates the connection to
the host that is relevant. The session layers separates various connections utilising the ports
those are random. Without any connection, the data will not flow via the layers of OSI.
Then the email starts operating at the transport layer. The transport layer determines
reliability and flow of control. The data of the email will be broken into small fragments and
it will be transmitted in form of UDP or TCP packets. In this scenario, the email will utilise
Data Communication in the Company
The office off the ABC Company has three floors. The ground floor is the main office
and consists of two computers and a shared printer. The other two floors have 25 computers
and 6 printers each. The scenario is that an employee in the ground floor sends an email to
the employee at the third floor. The email will be delivered through the seven layers of OSI
model.
When the email is send by the employee at the ground floor, it goes in the application
layer of the model of OSI. It offers the interface for the end user in order to tell the computer
the way to handle the data (Zhao et al 2018). In this scenario, the SMTP protocol will be used
and it will command the computer a way to handle the data.
After this, the email starts operating at the transport layer of the model of OSI. The
content of email will be changed to the formats of network. The text of the email will be
changed to ASCII values and the images of the email will be converted to JPEG, PNG and
many more. The encryption and compression of data will take place in this layer. In this
layer, th secure socket layer will be used for the encryption of data.
After this, the email will start operating in the session layer of the model of OSI. The
session layer will be responsible in order to start, handle and terminate the connection. In this
scenario, the session layer is responsible in order to keep the connection with the employee at
the ground floor. The session layer develops, manages and then terminates the connection to
the host that is relevant. The session layers separates various connections utilising the ports
those are random. Without any connection, the data will not flow via the layers of OSI.
Then the email starts operating at the transport layer. The transport layer determines
reliability and flow of control. The data of the email will be broken into small fragments and
it will be transmitted in form of UDP or TCP packets. In this scenario, the email will utilise
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6IT INFRASTRUCTURE
port number 25 of TCP and it uses the protocol of SMTP. The receiver port will also be port
number 25 (Latif and Aliero 2019).
The data packets of the email flow in the network later of model of OSI. The routing
of this data packet will take place in this layer. This layer will help to find the route from the
computer of the ground floor to the computer of the second floor. It will also add the IP
address of the sender and the IP address of receiver to packets of data. Now the data packet
will know where they should go.
After this, the packets of data move to the layer of data link. The packets of data of
email will be sending over the Ethernet. The packets of data will be changed to frames of
data. The data link layer carries out the function of defining the physical address of the data
packets also known as the MAC address to the frames of data. The MAC address is a
distinctive address and two MAC address will not have the same value (Santos and Marcillo
2018). Therefore, with this MAC address it can easily recognise to which host the packet will
be delivered. The data frame in this data link layer, the MAC address of the sender will be
added and the MAC address of the receiver.
After this, the data is ready for transmission to the side of receiver. In the physical
layer, the frames of data will be prepared. The frames will be changed into bits. The frames
will be sending over the physical media that means with the help of Ethernet cable, NIC and
many more.
The data frames are now in the receiver’s physical address. After this the data frames
are received by the emails server, which then transmits the data frames to the switch. The
switch then transmits the frames of data to the physical layer. The data frames are
broadcasted to the data link layer where the frames of data will be changes to packets of data.
The packets of data will be transmitted to the network layer of the receiver’s computer. The
port number 25 of TCP and it uses the protocol of SMTP. The receiver port will also be port
number 25 (Latif and Aliero 2019).
The data packets of the email flow in the network later of model of OSI. The routing
of this data packet will take place in this layer. This layer will help to find the route from the
computer of the ground floor to the computer of the second floor. It will also add the IP
address of the sender and the IP address of receiver to packets of data. Now the data packet
will know where they should go.
After this, the packets of data move to the layer of data link. The packets of data of
email will be sending over the Ethernet. The packets of data will be changed to frames of
data. The data link layer carries out the function of defining the physical address of the data
packets also known as the MAC address to the frames of data. The MAC address is a
distinctive address and two MAC address will not have the same value (Santos and Marcillo
2018). Therefore, with this MAC address it can easily recognise to which host the packet will
be delivered. The data frame in this data link layer, the MAC address of the sender will be
added and the MAC address of the receiver.
After this, the data is ready for transmission to the side of receiver. In the physical
layer, the frames of data will be prepared. The frames will be changed into bits. The frames
will be sending over the physical media that means with the help of Ethernet cable, NIC and
many more.
The data frames are now in the receiver’s physical address. After this the data frames
are received by the emails server, which then transmits the data frames to the switch. The
switch then transmits the frames of data to the physical layer. The data frames are
broadcasted to the data link layer where the frames of data will be changes to packets of data.
The packets of data will be transmitted to the network layer of the receiver’s computer. The
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7IT INFRASTRUCTURE
routing is done here. The packets of data already know the receivers IP address. From the
network layer, the data will be broadcasted to the transport layer. In the transport layer, the
broken segments of data will be reassembled and then send to the session layer of the OSI
model. In the session layer, based on information of session, it will recognise the type of
communication that the data belongs (Howser 2020). The information of session helps to
make this connection. The data is then broadcasted to the presentation layer. The encryption
and compression of the email will be decrypted and decompressed in this layer. After that,
the email will be send to the E-mail client of the employee at the second floor.
routing is done here. The packets of data already know the receivers IP address. From the
network layer, the data will be broadcasted to the transport layer. In the transport layer, the
broken segments of data will be reassembled and then send to the session layer of the OSI
model. In the session layer, based on information of session, it will recognise the type of
communication that the data belongs (Howser 2020). The information of session helps to
make this connection. The data is then broadcasted to the presentation layer. The encryption
and compression of the email will be decrypted and decompressed in this layer. After that,
the email will be send to the E-mail client of the employee at the second floor.
8IT INFRASTRUCTURE
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
9IT INFRASTRUCTURE
(Figure 1: Infrastructure of ABC Company
Source: Created By Author)
Figure 2: Communication of data
Conclusion
From the report, it can be inferred that the ABC Company can provide excellent
services to its clients with the help of IT infrastructure, hardwares and softwares. The report
discusses about the network devices those are used in order to fulfil the requirements of the
company. The network devices implemented in the company include routers, firewalls,
switches, printers and computers. The functions of each of the devices of network are
provided in the report. The report discusses about the client-server communication model and
(Figure 1: Infrastructure of ABC Company
Source: Created By Author)
Figure 2: Communication of data
Conclusion
From the report, it can be inferred that the ABC Company can provide excellent
services to its clients with the help of IT infrastructure, hardwares and softwares. The report
discusses about the network devices those are used in order to fulfil the requirements of the
company. The network devices implemented in the company include routers, firewalls,
switches, printers and computers. The functions of each of the devices of network are
provided in the report. The report discusses about the client-server communication model and
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10IT INFRASTRUCTURE
provides an overview of the model. The report identifies client-server communication
software and application software that can be used in order to fulfil the requirements of the
ABC Company. The application software MS outlook and the communication software can
be any type of web browsers such as the Google Chrome, Mozilla Firefox and many more.
The report provides an overview of transmitting an email that is sent from ground floor to the
second floor employee. The transmission is thoroughly is discussed utilising the concepts of
OSI model.
provides an overview of the model. The report identifies client-server communication
software and application software that can be used in order to fulfil the requirements of the
ABC Company. The application software MS outlook and the communication software can
be any type of web browsers such as the Google Chrome, Mozilla Firefox and many more.
The report provides an overview of transmitting an email that is sent from ground floor to the
second floor employee. The transmission is thoroughly is discussed utilising the concepts of
OSI model.

11IT INFRASTRUCTURE
References
Alani, M.M., 2017. Domestic Router Functions Configuration. In Guide to Cisco Routers
Configuration (pp. 11-39). Springer, Cham.
Choi, K. and Chang, B.M., 2019. A theory of RPC calculi for client–server model. Journal of
Functional Programming, 29.
de Souza Soares, E.F., Thiago, R.M., Azevedo, L.G., de Bayser, M., da Silva, V.T. and
Cerqueira, R.F.D.G., 2018, March. Evaluation of Server Push Technologies for Scalable
Client-Server Communication. In 2018 IEEE Symposium on Service-Oriented System
Engineering (SOSE) (pp. 1-10). IEEE.
De Sutter, B., Falcarin, P., Wyseur, B., Basile, C., Ceccato, M., DAnnoville, J. and Zunke,
M., 2016, April. A reference architecture for software protection. In 2016 13th Working
IEEE/IFIP Conference on Software Architecture (WICSA) (pp. 291-294). IEEE.
Gallo, M. and Pianese, F., 2018, August. vNS: a modular programmable virtual network
switch. In Proceedings of the ACM SIGCOMM 2018 Conference on Posters and Demos (pp.
96-98).
Howser, G., 2020. The OSI Seven Layer Model. In Computer Networks and the Internet (pp.
7-32). Springer, Cham.
Kloth, A.K., 2018. Advanced Router Architectures. CRC Press.
Latif, M. and Aliero, M.S., 2019. Field-Programmable Gate Array Implementation on
Ethernet MAC for High Speed Secure Data Communication. International Journal of
Computing and Communication Networks, 1(1), pp.35-45.
References
Alani, M.M., 2017. Domestic Router Functions Configuration. In Guide to Cisco Routers
Configuration (pp. 11-39). Springer, Cham.
Choi, K. and Chang, B.M., 2019. A theory of RPC calculi for client–server model. Journal of
Functional Programming, 29.
de Souza Soares, E.F., Thiago, R.M., Azevedo, L.G., de Bayser, M., da Silva, V.T. and
Cerqueira, R.F.D.G., 2018, March. Evaluation of Server Push Technologies for Scalable
Client-Server Communication. In 2018 IEEE Symposium on Service-Oriented System
Engineering (SOSE) (pp. 1-10). IEEE.
De Sutter, B., Falcarin, P., Wyseur, B., Basile, C., Ceccato, M., DAnnoville, J. and Zunke,
M., 2016, April. A reference architecture for software protection. In 2016 13th Working
IEEE/IFIP Conference on Software Architecture (WICSA) (pp. 291-294). IEEE.
Gallo, M. and Pianese, F., 2018, August. vNS: a modular programmable virtual network
switch. In Proceedings of the ACM SIGCOMM 2018 Conference on Posters and Demos (pp.
96-98).
Howser, G., 2020. The OSI Seven Layer Model. In Computer Networks and the Internet (pp.
7-32). Springer, Cham.
Kloth, A.K., 2018. Advanced Router Architectures. CRC Press.
Latif, M. and Aliero, M.S., 2019. Field-Programmable Gate Array Implementation on
Ethernet MAC for High Speed Secure Data Communication. International Journal of
Computing and Communication Networks, 1(1), pp.35-45.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 13
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





