SBM4104: IT Infrastructure Design for E-commerce Enterprise, Sydney
VerifiedAdded on 2023/02/01
|9
|3114
|51
Project
AI Summary
This assignment details the design of an advanced IT infrastructure for an e-commerce enterprise located in Sydney. The project encompasses a geographical study, focusing on a campus area network connecting various departments. It includes logical network design, IP addressing schemes with subnetting, and a discussion on cloud computing and virtualization techniques. The design incorporates network diagrams, categorization of segments, applications, and users within a three-tier architecture. Furthermore, the assignment explores the benefits of cloud providers like Amazon Web Services and Google Cloud Platform for hosting services such as email and web hosting, considering scalability and cost-effectiveness. The project concludes with a study of scaling and its importance to the e-commerce business's success.

PART I
Introduction
IT infrastructure can be defined as the hardware, network resources, services and software required for
operation, management of business processes, and existence of a business organization. The in IT
infrastructure provides business organizations with ICT services that drive their operations making. One
can imagine a business enterprise without email service. How will communication take place? How will
the CEO communicate to everyone within the organization about the performance of the business? How
will the sales team share both the quotations and sales orders to distant customers? As that is not
enough, how does a business enterprise look like when it does not have a website to market itself to the
outside world? These two are just among the imperative IT Infrastructure services that are necessary for
a business organization to carry out its operations.
For sure, IT infrastructure comprises of services that are driving factor towards the success of a business
enterprise. The services offered can used for internal business operations and deployment of
Information technology business solutions. Below are the main components of ideal IT Infrastructure for
business processes:
a. Network – network refers to the interconnection of computing devices all over the world by the
aid of internet. Network as an IT infrastructure service for business enterprise, enables these
organizations to reached by customers who at a far distance. In fact, most of business activities
are going online due to enabled network, assured security and the firewall.
b. Hardware – hardware as a component of IT infrastructure refers to the tangible items such as
the servers, switches, routers, hubs and data centers that actualize IT infrastructure.
c. Meatware – meatware denotes to human beings that are really in need of the IT infrastructure
services so as they carry out their jobs with efficiency. Meatware also covers the developers,
network designers and the administrators.
d. Software – software entails the productivity applications, enterprise management and customer
relationship management application that are all together used with the hardware to achieve
the goal of IT infrastructure.
Garrison & Nova exclaims that the present industry market is changing so much such if your business
enterprise does not move with it the present technology it will automatically become extinct (Garrison &
Nova, 2017). The best thing is that the management of the subject e-commerce enterprise has foreseen
Introduction
IT infrastructure can be defined as the hardware, network resources, services and software required for
operation, management of business processes, and existence of a business organization. The in IT
infrastructure provides business organizations with ICT services that drive their operations making. One
can imagine a business enterprise without email service. How will communication take place? How will
the CEO communicate to everyone within the organization about the performance of the business? How
will the sales team share both the quotations and sales orders to distant customers? As that is not
enough, how does a business enterprise look like when it does not have a website to market itself to the
outside world? These two are just among the imperative IT Infrastructure services that are necessary for
a business organization to carry out its operations.
For sure, IT infrastructure comprises of services that are driving factor towards the success of a business
enterprise. The services offered can used for internal business operations and deployment of
Information technology business solutions. Below are the main components of ideal IT Infrastructure for
business processes:
a. Network – network refers to the interconnection of computing devices all over the world by the
aid of internet. Network as an IT infrastructure service for business enterprise, enables these
organizations to reached by customers who at a far distance. In fact, most of business activities
are going online due to enabled network, assured security and the firewall.
b. Hardware – hardware as a component of IT infrastructure refers to the tangible items such as
the servers, switches, routers, hubs and data centers that actualize IT infrastructure.
c. Meatware – meatware denotes to human beings that are really in need of the IT infrastructure
services so as they carry out their jobs with efficiency. Meatware also covers the developers,
network designers and the administrators.
d. Software – software entails the productivity applications, enterprise management and customer
relationship management application that are all together used with the hardware to achieve
the goal of IT infrastructure.
Garrison & Nova exclaims that the present industry market is changing so much such if your business
enterprise does not move with it the present technology it will automatically become extinct (Garrison &
Nova, 2017). The best thing is that the management of the subject e-commerce enterprise has foreseen
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

this and hence, the quest for network design that will host the IT infrastructure that will be the steering
wheel for the business enterprise processes.
In this piece of assignment, we will be designing an advanced network IT infrastructure for the subject e-
commerce enterprise in the city of Sydney. The activities performed in this task will include coming up
with appropriate network diagrams that suite the e-commerce business activities, providing the
geographic study of the business, design a logical diagram to show data flow within the organization and
IP addressing. Furthermore, we will provide a better option of hosting part of IT Infrastructure services
in the cloud due scaling advantage, we discuss the techniques that support virtualization and cloud
computing. In the final stage, we provide a study of scaling and its importance to business enterprises.
Geographical Scope
According to Sterbenz & Touch, geographic scope refers to the network coverage that computers have
within a particular geographical area. This is basically how far the network nodes along with their
networks can span geographically. Local area networks deploy dedicated data paths and entail private
branch exchanges. The local Area networks are used to interlink several computing devices. The
distribution of a Local Area Network is limited to a single building or a distance of about two hundred
meters without intervention of a repeater (Sterbenz & Touch, 2012). The LANs are mostly deployed to
interlink workstations and personal computers in an office, home factories and many other
organizational units. This implies that the users of a LAN can share equipment like printers, files and
other resources.
On the other hand, the Wide area networks deploy telecommunications paths and take in the value
added networks. Personal Area network is another example of a network geographical scope.it
comprises of computing devices (cell phones, PDAs, computers access points printers, audio devices)
that are near to the access point. Personal Area Network is usually few meters away and is typically for
personal use. These kind of geographic network can be connected together by use of wires, USB cables,
Wireless Personal Network and Bluetooth. Other geographic networks scopes include the Storage Area
network and Campus area networks. For the implementation of our e-commerce network, we deploy
campus area network scope as discussed below:
Campus Area Network (CAN)
A campus area network refers to a collection of geographically separated Local Area Networks within a
campus. By the campus we mean an institution whose buildings are geographically dispersed. A campus
wheel for the business enterprise processes.
In this piece of assignment, we will be designing an advanced network IT infrastructure for the subject e-
commerce enterprise in the city of Sydney. The activities performed in this task will include coming up
with appropriate network diagrams that suite the e-commerce business activities, providing the
geographic study of the business, design a logical diagram to show data flow within the organization and
IP addressing. Furthermore, we will provide a better option of hosting part of IT Infrastructure services
in the cloud due scaling advantage, we discuss the techniques that support virtualization and cloud
computing. In the final stage, we provide a study of scaling and its importance to business enterprises.
Geographical Scope
According to Sterbenz & Touch, geographic scope refers to the network coverage that computers have
within a particular geographical area. This is basically how far the network nodes along with their
networks can span geographically. Local area networks deploy dedicated data paths and entail private
branch exchanges. The local Area networks are used to interlink several computing devices. The
distribution of a Local Area Network is limited to a single building or a distance of about two hundred
meters without intervention of a repeater (Sterbenz & Touch, 2012). The LANs are mostly deployed to
interlink workstations and personal computers in an office, home factories and many other
organizational units. This implies that the users of a LAN can share equipment like printers, files and
other resources.
On the other hand, the Wide area networks deploy telecommunications paths and take in the value
added networks. Personal Area network is another example of a network geographical scope.it
comprises of computing devices (cell phones, PDAs, computers access points printers, audio devices)
that are near to the access point. Personal Area Network is usually few meters away and is typically for
personal use. These kind of geographic network can be connected together by use of wires, USB cables,
Wireless Personal Network and Bluetooth. Other geographic networks scopes include the Storage Area
network and Campus area networks. For the implementation of our e-commerce network, we deploy
campus area network scope as discussed below:
Campus Area Network (CAN)
A campus area network refers to a collection of geographically separated Local Area Networks within a
campus. By the campus we mean an institution whose buildings are geographically dispersed. A campus

could be a factory, a university, and government offices that belong to a similar organizational unit that
are few kilometers apart (Pradeep & Priti, 2016 ).
CAN Infrastructure
Campus Area network use similar technology together with the hardware used in the other buildings of
the same campus. Same terminologies are adhered to just like the local area network. Nevertheless,
they are connected between the buildings at a specified location. In terms of our e-commerce business
enterprise, you can imagine having a number of departments such as production, distribution, branding
and marketing departments that are located in different buildings. This departments need to
communicate to each other seamlessly as if the departments are in the area on the next door of the
other.by the term same technologies and terminologies we mean that the type of hardware such as the
routers, hubs, switches, repeaters, wireless connection, and cabling locations are similar in the buildings.
Below is the Campus Area Network within our e-commerce enterprise.
Campus Area Network and e-commerce
are few kilometers apart (Pradeep & Priti, 2016 ).
CAN Infrastructure
Campus Area network use similar technology together with the hardware used in the other buildings of
the same campus. Same terminologies are adhered to just like the local area network. Nevertheless,
they are connected between the buildings at a specified location. In terms of our e-commerce business
enterprise, you can imagine having a number of departments such as production, distribution, branding
and marketing departments that are located in different buildings. This departments need to
communicate to each other seamlessly as if the departments are in the area on the next door of the
other.by the term same technologies and terminologies we mean that the type of hardware such as the
routers, hubs, switches, repeaters, wireless connection, and cabling locations are similar in the buildings.
Below is the Campus Area Network within our e-commerce enterprise.
Campus Area Network and e-commerce
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

CAN is the best type of geographic network for e-commerce because the building blocks of
administration, sales and marketing, service workshop, show room and the conference hall are
connected with one another combining to form a Campus area network. Note that some of our
corporate buildings are connected with use of Wi-Fi. We choose wireless medium because it is
economical as compared to wired medium especially when there is a road to be crossed.
Categorization of segnments, applications and users.
Our Campus area network is categorized on the basis of three-tier architecture. This architecture comprises of access
layer which give users access to the networked environment. Access layer consists of layer 2 switches and host
computers. Distribution layer is the middle component the 3 tier network architecture. It forms the communication
point between the core tier and access layer. The layer consists of Layer 3 fast switches and routers. This tier
implements routing and switching protocols. Finally the core layer is at the topmost of the 3 tier architecture. The core
layer as known as backbone network, it provides interlinking between the distribution layers. It consists of fast routing
and switching components. It provides redundancy mechanisms to the network.
Logical network design
Logical network design refers to the techniques by which information will flow within a networked
system. This task includes an entity that may be built from many larger distinct local area networks and
it is designed in a manner that they appear a single network. Normally, logical network design used to
scale down the bigger picture of the whole network into something that can be discussed on paper. The
below diagram depicts the logical network of our subject e-commerce business enterprise (Lammle,
2015).
administration, sales and marketing, service workshop, show room and the conference hall are
connected with one another combining to form a Campus area network. Note that some of our
corporate buildings are connected with use of Wi-Fi. We choose wireless medium because it is
economical as compared to wired medium especially when there is a road to be crossed.
Categorization of segnments, applications and users.
Our Campus area network is categorized on the basis of three-tier architecture. This architecture comprises of access
layer which give users access to the networked environment. Access layer consists of layer 2 switches and host
computers. Distribution layer is the middle component the 3 tier network architecture. It forms the communication
point between the core tier and access layer. The layer consists of Layer 3 fast switches and routers. This tier
implements routing and switching protocols. Finally the core layer is at the topmost of the 3 tier architecture. The core
layer as known as backbone network, it provides interlinking between the distribution layers. It consists of fast routing
and switching components. It provides redundancy mechanisms to the network.
Logical network design
Logical network design refers to the techniques by which information will flow within a networked
system. This task includes an entity that may be built from many larger distinct local area networks and
it is designed in a manner that they appear a single network. Normally, logical network design used to
scale down the bigger picture of the whole network into something that can be discussed on paper. The
below diagram depicts the logical network of our subject e-commerce business enterprise (Lammle,
2015).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
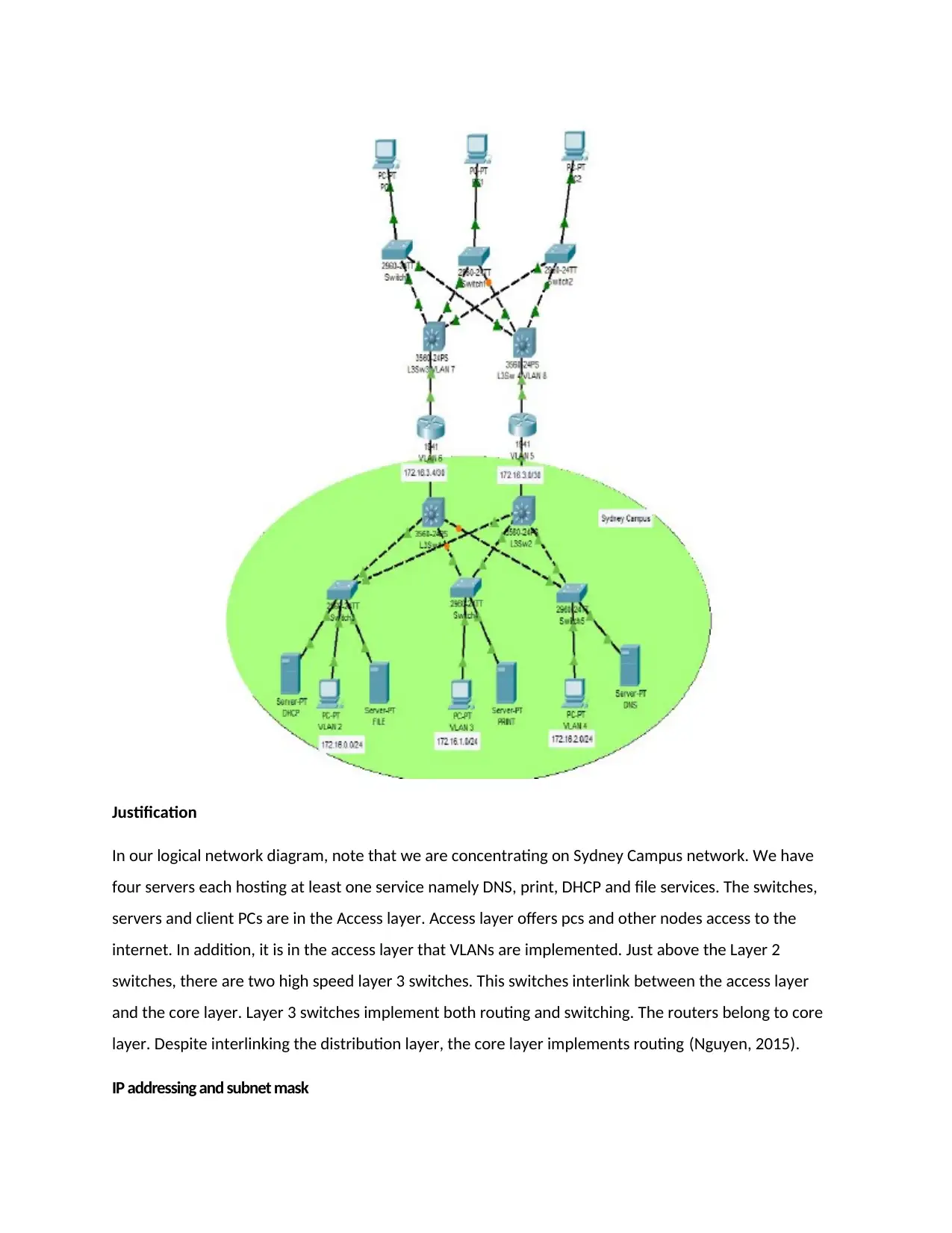
Justification
In our logical network diagram, note that we are concentrating on Sydney Campus network. We have
four servers each hosting at least one service namely DNS, print, DHCP and file services. The switches,
servers and client PCs are in the Access layer. Access layer offers pcs and other nodes access to the
internet. In addition, it is in the access layer that VLANs are implemented. Just above the Layer 2
switches, there are two high speed layer 3 switches. This switches interlink between the access layer
and the core layer. Layer 3 switches implement both routing and switching. The routers belong to core
layer. Despite interlinking the distribution layer, the core layer implements routing (Nguyen, 2015).
IP addressing and subnet mask
In our logical network diagram, note that we are concentrating on Sydney Campus network. We have
four servers each hosting at least one service namely DNS, print, DHCP and file services. The switches,
servers and client PCs are in the Access layer. Access layer offers pcs and other nodes access to the
internet. In addition, it is in the access layer that VLANs are implemented. Just above the Layer 2
switches, there are two high speed layer 3 switches. This switches interlink between the access layer
and the core layer. Layer 3 switches implement both routing and switching. The routers belong to core
layer. Despite interlinking the distribution layer, the core layer implements routing (Nguyen, 2015).
IP addressing and subnet mask
IP addressing denotes to the fact that computing devices in order for them to be identified on the
network uniquely, they will require a unique number that will be used as a sole entity to identify the
networking devices. The unique number is called an IP address. IP addressing therefore is the act of
assigning an IP address, default gateway DNS, IP address and mask to computing device. The IP
assignment process can either be static or dynamic. With dynamic IP address assignment strategy, a
DHCP server used to lease an IP address together with the other mentioned parameters for a period of
time known as lease time. This strategy of IP assignment is the most recommended as it does not
involve the systems administrator so much (Duggan, 2014).
Static IP address assignment strategy on the other hand quests for the administrator to perform manual
assignment of IP addresses to the network hosts. This strategy is so strenuous since it requires the
network administrator to be always available monitoring which device has left the network to reclaim
the IP address and which device require network connection for it to be assigned an IP address. Despite
all this, this strategy is applauded of being more secure as compared to dynamic IP address assignment.
For our e-commerce enterprise, we will use both techniques.
It should be noted that before an IP address is assigned to the host device, it is imperative to take note
of the subnet that you would want the device to operate from. This brings about the subnetting
concept. Subnetting refers to the art dividing a large network into smaller vlan/subnets/units that are
easier to troubleshoot and manage just in case there is a fault (Lammle, 2017). Assuming that we have
been offered an IP address of 172.16.97.34/19 with our service provider, our network will be subdivided
into sub networks as below table:
VLAN
Name
Hosts
Needed
Network
Address
Slash Mask Valid Hosts Broadcast Wildcard
VLAN 2 250 172.16.0.0 /24 255.255.255.0 172.16.0.1 -
172.16.0.254
172.16.0.255 0.0.0.255
VLAN 3 250 172.16.1.0 /24 255.255.255.0 172.16.1.1 -
172.16.1.254
172.16.1.255 0.0.0.255
VLAN 4 250 172.16.2.0 /24 255.255.255.0 172.16.2.1 -
172.16.2.254
172.16.2.255 0.0.0.255
VLAN 5 2 172.16.3.0 /30 255.255.255.252 172.16.3.1 -
172.16.3.2
172.16.3.3 0.0.0.3
VLAN 6 2 172.16.3.4 /30 255.255.255.252 172.16.3.5 -
172.16.3.6
172.16.3.7 0.0.0.3
(James, et al., 2016)
PART II
Cloud providers
In the recent past, cloud computing has found popularity in itself due to its distinct features as
compared to traditional webhosting. The unique characteristics are;
a. The service is fully managed by the service provider, this gives the client time to concentrate on
the business processes.
b. It is elastic, i.e. the client can be provided as more or less as per their requirements.
c. It is offered on demand, that’s, typically per minute or second.
network uniquely, they will require a unique number that will be used as a sole entity to identify the
networking devices. The unique number is called an IP address. IP addressing therefore is the act of
assigning an IP address, default gateway DNS, IP address and mask to computing device. The IP
assignment process can either be static or dynamic. With dynamic IP address assignment strategy, a
DHCP server used to lease an IP address together with the other mentioned parameters for a period of
time known as lease time. This strategy of IP assignment is the most recommended as it does not
involve the systems administrator so much (Duggan, 2014).
Static IP address assignment strategy on the other hand quests for the administrator to perform manual
assignment of IP addresses to the network hosts. This strategy is so strenuous since it requires the
network administrator to be always available monitoring which device has left the network to reclaim
the IP address and which device require network connection for it to be assigned an IP address. Despite
all this, this strategy is applauded of being more secure as compared to dynamic IP address assignment.
For our e-commerce enterprise, we will use both techniques.
It should be noted that before an IP address is assigned to the host device, it is imperative to take note
of the subnet that you would want the device to operate from. This brings about the subnetting
concept. Subnetting refers to the art dividing a large network into smaller vlan/subnets/units that are
easier to troubleshoot and manage just in case there is a fault (Lammle, 2017). Assuming that we have
been offered an IP address of 172.16.97.34/19 with our service provider, our network will be subdivided
into sub networks as below table:
VLAN
Name
Hosts
Needed
Network
Address
Slash Mask Valid Hosts Broadcast Wildcard
VLAN 2 250 172.16.0.0 /24 255.255.255.0 172.16.0.1 -
172.16.0.254
172.16.0.255 0.0.0.255
VLAN 3 250 172.16.1.0 /24 255.255.255.0 172.16.1.1 -
172.16.1.254
172.16.1.255 0.0.0.255
VLAN 4 250 172.16.2.0 /24 255.255.255.0 172.16.2.1 -
172.16.2.254
172.16.2.255 0.0.0.255
VLAN 5 2 172.16.3.0 /30 255.255.255.252 172.16.3.1 -
172.16.3.2
172.16.3.3 0.0.0.3
VLAN 6 2 172.16.3.4 /30 255.255.255.252 172.16.3.5 -
172.16.3.6
172.16.3.7 0.0.0.3
(James, et al., 2016)
PART II
Cloud providers
In the recent past, cloud computing has found popularity in itself due to its distinct features as
compared to traditional webhosting. The unique characteristics are;
a. The service is fully managed by the service provider, this gives the client time to concentrate on
the business processes.
b. It is elastic, i.e. the client can be provided as more or less as per their requirements.
c. It is offered on demand, that’s, typically per minute or second.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Cloud computing denotes to the anything that relates to provision of IT infrastructure via the internet.
The services provided in cloud computing are categorized in three groups namely: SaaS (Software-as-a-
Service), PaaS (Platform-as-a-Service) and IaaS (Infrastructure-as-a-Service) (Bhowmik, 2017 ).
Cloud computing and virtualization has experienced massive shifting by business enterprises which seek
efficient, cost effective and reliable services. Our subject e-commerce business enterprise is not an
exception from benefiting the advantages of virtualization and cloud computing. Some of the services
that our client would take to the cloud are email and web. On the basis of infrastructure and cost of
hosting these services, Amazon Web Hosting and Google Cloud Platform are our proposed choices.
Amazon Web Services
Amazon Web Service offer a lump sum of globe storage, database analytics and deployment which
enable business enterprises to lower their IT infrastructure service costs due to scaled applications by
Amazon. We recommend web hosting service to be used as our hosting service. Hosting our web with
Amazon will avail to us the enriched media content. This is the best choice for our marketing strategy.
Google Cloud Platform
Google Cloud Platform is a kind of Platform-as-a-Service which has a myriad of public virtualization and
cloud computing services. It has a suite of hosted services such application, compute, storage and
application which are run on Google hardware servers.
We suggest Google Cloud Platform for email hosting as its G-Suite hosted email offers collaboration and
productivity. Our e-commerce subject business enterprise will enjoy unlimited storage, smart search
functionality and un-wavered security. In addition, Google offers a-24/7 phone call support to their
clients.
Techniques supporting virtualization and cloud computing
Virtualization allows more than one operating system to run a single hardware computer by offering
virtualized hardware to the guest operating system (Cain, et al., 2015). There are techniques that are
adopted to support virtualization. These strategies are:
a. OS Level virtualization; this strategy of virtualization is intended to provide the needed security
and security to run programs on the same server. Such kind of separation, provision and
isolation an environment which ensures simple sharing and executing of VMs with several
applications program applications running on a distinct server.
b. Virtual machines; virtual machines mimic specific hardware requiring legal resources from the
host machine, this technique benefits system emulators that are deployed for executing the OS.
The services provided in cloud computing are categorized in three groups namely: SaaS (Software-as-a-
Service), PaaS (Platform-as-a-Service) and IaaS (Infrastructure-as-a-Service) (Bhowmik, 2017 ).
Cloud computing and virtualization has experienced massive shifting by business enterprises which seek
efficient, cost effective and reliable services. Our subject e-commerce business enterprise is not an
exception from benefiting the advantages of virtualization and cloud computing. Some of the services
that our client would take to the cloud are email and web. On the basis of infrastructure and cost of
hosting these services, Amazon Web Hosting and Google Cloud Platform are our proposed choices.
Amazon Web Services
Amazon Web Service offer a lump sum of globe storage, database analytics and deployment which
enable business enterprises to lower their IT infrastructure service costs due to scaled applications by
Amazon. We recommend web hosting service to be used as our hosting service. Hosting our web with
Amazon will avail to us the enriched media content. This is the best choice for our marketing strategy.
Google Cloud Platform
Google Cloud Platform is a kind of Platform-as-a-Service which has a myriad of public virtualization and
cloud computing services. It has a suite of hosted services such application, compute, storage and
application which are run on Google hardware servers.
We suggest Google Cloud Platform for email hosting as its G-Suite hosted email offers collaboration and
productivity. Our e-commerce subject business enterprise will enjoy unlimited storage, smart search
functionality and un-wavered security. In addition, Google offers a-24/7 phone call support to their
clients.
Techniques supporting virtualization and cloud computing
Virtualization allows more than one operating system to run a single hardware computer by offering
virtualized hardware to the guest operating system (Cain, et al., 2015). There are techniques that are
adopted to support virtualization. These strategies are:
a. OS Level virtualization; this strategy of virtualization is intended to provide the needed security
and security to run programs on the same server. Such kind of separation, provision and
isolation an environment which ensures simple sharing and executing of VMs with several
applications program applications running on a distinct server.
b. Virtual machines; virtual machines mimic specific hardware requiring legal resources from the
host machine, this technique benefits system emulators that are deployed for executing the OS.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

c. Full virtualization; full virtualization strategy virtualizes the whole main server to enable it
support software program applications to work in same way as on a physical area. Such
virtualization strategy develops an environment which appear as it is on a distinct server.
Dynamic scaling using Cloud computing
Dynamic scaling refers to a cloud computing feature that permits nodes to scale automatically cloud
services. A good example is when a virtual machine server lowers down service delivery when a system
is not in use and rise up the service where there are very many activities taking place. This kind of
dynamic scaling ensures that fresh instances are seamlessly minimized as the demand slows down.
Similarly, the service will be raised up when there increased demand (Aljawarneh, 2012).
Such scaling technique implemented by Google’s G-suite will benefit our e-commerce business as the
scaling minimizes the cost while giving best performance and reliability.
Summary
In summary, we note that dynamism in the current world market necessitates that business enterprises
to change their tactic of operation lest they become distinct. IT Infrastructure has been the primary
game changer in how business activities are carried. Each day, new technology that is efficiently best
performing evolves, business enterprises which own it before the saturation they normally have a lion’s
share of gain.
IT infrastructure services such as mailing, messaging, web, file sharing and storage, DHCP, DNS, Internet,
and security services are the major factors that determine the success or derail of IT solutions to an
organization. Therefore, the appropriate design and implementation will make a business enterprise to
survive in the existing competitive market.
support software program applications to work in same way as on a physical area. Such
virtualization strategy develops an environment which appear as it is on a distinct server.
Dynamic scaling using Cloud computing
Dynamic scaling refers to a cloud computing feature that permits nodes to scale automatically cloud
services. A good example is when a virtual machine server lowers down service delivery when a system
is not in use and rise up the service where there are very many activities taking place. This kind of
dynamic scaling ensures that fresh instances are seamlessly minimized as the demand slows down.
Similarly, the service will be raised up when there increased demand (Aljawarneh, 2012).
Such scaling technique implemented by Google’s G-suite will benefit our e-commerce business as the
scaling minimizes the cost while giving best performance and reliability.
Summary
In summary, we note that dynamism in the current world market necessitates that business enterprises
to change their tactic of operation lest they become distinct. IT Infrastructure has been the primary
game changer in how business activities are carried. Each day, new technology that is efficiently best
performing evolves, business enterprises which own it before the saturation they normally have a lion’s
share of gain.
IT infrastructure services such as mailing, messaging, web, file sharing and storage, DHCP, DNS, Internet,
and security services are the major factors that determine the success or derail of IT solutions to an
organization. Therefore, the appropriate design and implementation will make a business enterprise to
survive in the existing competitive market.

References
Aljawarneh, S., 2012. Cloud Computing Advancements in Design, Implementation, and Technologies. 3rd
ed. Hershey: IGI Global.
Bhowmik, S., 2017 . Cloud Computing. 5th ed. Cambridge: Cambridge University Press.
Cain, N., Luescher, . & Flynn, ., 2015. Logical networks. In: Microsoft System Center Building a Virtualized
Network Solution. Carmel, Indiana: Sams Publishing, pp. 67-77.
Duggan, M., 2014. Cisco CCIE Routing and Switching v5.0 Configuration and Troubleshooting. In: Cisco
CCIE Routing and Switching. Indianapolis: Cisco Press, pp. 321-3330.
Garrison, J. & Nova, ., 2017. Cloud Native Infrastructure: Patterns for Scalable Infrastructure. 2nd ed.
Sebastopol, California: O'Reilly Media, Inc..
James, P., Jeffrey, C. & Tittel, ., 2016. Guide to TCP/IP: IPv6 and IPv4. Boston: Cengage Learning.
Lammle, T., 2015. CompTIA Network+ Study Guide, (Exam: N10-006). 4th ed. New York City: John Wiley
& Sons..
Lammle, T., 2017. Subnetting. Hoboken: Wiley.
Lammle, T. & Swartz, J., 2013. CCNA Data Center - Introducing Cisco Data Center Networking Study
Guide. 6th ed. Hoboken, New Jersey: John Wiley & Sons.
Nguyen, T., 2015. Understanding TCP/IP Subnetting. Musk: EnCognitive.
Pradeep, S. & Priti, ., 2016 . IInformation Technology: Theory and Practice. 2nd ed. Delhi: PHI Learning
Pvt. Ltd.
Sterbenz, J. P. G. & Touch, . D., 2012. High-Speed Networking: A Systematic Approach to High-Bandwidth
Low-Latency. 3rd ed. Hoboken: John Wiley & Sons.
Velte, T. & Velte, ., 2013. Cisco A Beginner's Guide. New York City: McGraw Hill Professional.
Aljawarneh, S., 2012. Cloud Computing Advancements in Design, Implementation, and Technologies. 3rd
ed. Hershey: IGI Global.
Bhowmik, S., 2017 . Cloud Computing. 5th ed. Cambridge: Cambridge University Press.
Cain, N., Luescher, . & Flynn, ., 2015. Logical networks. In: Microsoft System Center Building a Virtualized
Network Solution. Carmel, Indiana: Sams Publishing, pp. 67-77.
Duggan, M., 2014. Cisco CCIE Routing and Switching v5.0 Configuration and Troubleshooting. In: Cisco
CCIE Routing and Switching. Indianapolis: Cisco Press, pp. 321-3330.
Garrison, J. & Nova, ., 2017. Cloud Native Infrastructure: Patterns for Scalable Infrastructure. 2nd ed.
Sebastopol, California: O'Reilly Media, Inc..
James, P., Jeffrey, C. & Tittel, ., 2016. Guide to TCP/IP: IPv6 and IPv4. Boston: Cengage Learning.
Lammle, T., 2015. CompTIA Network+ Study Guide, (Exam: N10-006). 4th ed. New York City: John Wiley
& Sons..
Lammle, T., 2017. Subnetting. Hoboken: Wiley.
Lammle, T. & Swartz, J., 2013. CCNA Data Center - Introducing Cisco Data Center Networking Study
Guide. 6th ed. Hoboken, New Jersey: John Wiley & Sons.
Nguyen, T., 2015. Understanding TCP/IP Subnetting. Musk: EnCognitive.
Pradeep, S. & Priti, ., 2016 . IInformation Technology: Theory and Practice. 2nd ed. Delhi: PHI Learning
Pvt. Ltd.
Sterbenz, J. P. G. & Touch, . D., 2012. High-Speed Networking: A Systematic Approach to High-Bandwidth
Low-Latency. 3rd ed. Hoboken: John Wiley & Sons.
Velte, T. & Velte, ., 2013. Cisco A Beginner's Guide. New York City: McGraw Hill Professional.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 9
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





