ISYS201: Detailed IT Infrastructure and Network Proposal for AusEd Inc
VerifiedAdded on 2023/06/12
|8
|2438
|275
Report
AI Summary
This document provides an IT infrastructure proposal for AusEd Inc., a not-for-profit private education organization. As the IT Infrastructure manager, the author outlines a plan to review and enhance the existing IT infrastructure to meet the increasing demands of staff and students. The proposal includes a detailed network infrastructure diagram, highlighting the placement of servers, clients, and security features like firewalls and VPNs. The document justifies the selection of specific hardware brands, emphasizing compatibility, durability, and cost-effectiveness. The network design follows a three-layered hierarchical model (core, access, and distribution) to ensure scalability and manageability. The proposal addresses security concerns, scalability, reliability, and ease of management for troubleshooting. The analysis covers hardware components (cabling, switches, routers, transceivers, servers, security devices) and software components (operating systems, network services, protocols). The goal is to provide AusEd with a robust and secure network infrastructure to support their online education services.

Introduction.
When it comes to interact with the network infrastructure where we have been asked to perform a
certain analysis then it might be a challenge for us as we strive to get to know what we are required to
do if we don’t not have the necessary knowledge. Network can be explained to be a group of hardware
devices and the components of software’s which will be necessary when connecting the devices in an
organization to other many organizations and the specific internet used. AusEd institution is in a position
where it is in need of designing a network that is estimated to server almost 3000 hosts in the
institution. As the IT manager we are required to give sense to the management of AusEd to what we
are needed for us to achieve their needs. The understanding will be majored in two components as
explained below.
1. Hardware Components- these are the physical and tangible devices that are utilized in the
networking environment such as the routers, servers, hub, printers, switches, modem,
transceiver, cabling, network interface cards and the phone lines among many others.
2. Software Components are those components that are known for utilizing the environment of
the network services and all the needed protocols in enabling the hardware devices to
communicate and interconnect with each other.
An operating system can only be understood and installed only after the hardware have be installed and
configured as well as installing the software in the network infrastructure. The operating system is on e
of the major components used in the networking as it is used by the server in managing all the resources
that are transmitted from one device to the other. Network IT infrastructure is referred to as group of
physical hardware and the logical components which is needed in providing some features over the
network which may include the network security, the access control, network security, Routing and the
capabilities of switching.
There has been a rapid growth in the world of technology where each and every day we get new
technologies and new versions of what we were using yesterday so it should always be wise in knowing
where we belong as the future will need something else. AusEd is entitled to have us know what they
have that can be used in the proposed setup of the network design. This will be done by doing an
analysis of the whole institution so that we know how to plan for what we will need and the appropriate
flow of information from the devices in the entire network (Adato, 2015). The network to be set is
based on the needs of the organisation where we have to consider the following issues.
When it comes to interact with the network infrastructure where we have been asked to perform a
certain analysis then it might be a challenge for us as we strive to get to know what we are required to
do if we don’t not have the necessary knowledge. Network can be explained to be a group of hardware
devices and the components of software’s which will be necessary when connecting the devices in an
organization to other many organizations and the specific internet used. AusEd institution is in a position
where it is in need of designing a network that is estimated to server almost 3000 hosts in the
institution. As the IT manager we are required to give sense to the management of AusEd to what we
are needed for us to achieve their needs. The understanding will be majored in two components as
explained below.
1. Hardware Components- these are the physical and tangible devices that are utilized in the
networking environment such as the routers, servers, hub, printers, switches, modem,
transceiver, cabling, network interface cards and the phone lines among many others.
2. Software Components are those components that are known for utilizing the environment of
the network services and all the needed protocols in enabling the hardware devices to
communicate and interconnect with each other.
An operating system can only be understood and installed only after the hardware have be installed and
configured as well as installing the software in the network infrastructure. The operating system is on e
of the major components used in the networking as it is used by the server in managing all the resources
that are transmitted from one device to the other. Network IT infrastructure is referred to as group of
physical hardware and the logical components which is needed in providing some features over the
network which may include the network security, the access control, network security, Routing and the
capabilities of switching.
There has been a rapid growth in the world of technology where each and every day we get new
technologies and new versions of what we were using yesterday so it should always be wise in knowing
where we belong as the future will need something else. AusEd is entitled to have us know what they
have that can be used in the proposed setup of the network design. This will be done by doing an
analysis of the whole institution so that we know how to plan for what we will need and the appropriate
flow of information from the devices in the entire network (Adato, 2015). The network to be set is
based on the needs of the organisation where we have to consider the following issues.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1. Security issues
2. Scalability
3. Reliability and accessibility
4. Management where it must be easy when we are doing some troubleshooting in case a problem
arise.
The project is to help us give out the model to be used in designing the network. The idea will be
explained where we have to describe the project, the scope of the project, the purpose of the case
study, the assumptions that have been made, the list of the devices to be used when networking, the
system design logical diagram, justification of the applied hardware’s and the conclusion which will give
a summary of what we have analysed in the other areas.
Description of the Project
The management of AusEd is in need of a network and we will have a giant construction to the
implementation of the proposed network design. From the description we have to start the plan of the
infrastructure where we will base it on the resources available and what is needed in making the work
complete. There are some objectives that need to be achieved at the end of the day. There is already an
existing network. Their idea is to improve their relationship with their customers where they are
considering to use the Customer Relationship management software’s and the Microsoft server 2007
which will be used when we are exchanging the emails through sending and receiving. When we say we
want to do the plan it may sound easy but when we do a feasibility study and understand the following
points such as the ratio of the servers to the number of hosts (Workstations), the expected size of the IT
infrastructure, mixing the platforms, building a fast network may be a big challenge when determining
how the network will be designed.
Scope of the Problem and its Purpose
Designing the IT infrastructure of AusEd will help them in determining the strategic plan which is
classified in to two concepts where they are looking in to a future where they will be able to increase the
resources through the diversification of the sources of fund and minimizing the all cost that results ot all
the core-non activities. After understanding the strategic plan then we are required to understand the
technology plan where we will help them in developing an offline Moodle that will help the
management to help the students maintain the personal computers of the school and at the same time
access resources when they are offline but connected to the network. The other development in the
2. Scalability
3. Reliability and accessibility
4. Management where it must be easy when we are doing some troubleshooting in case a problem
arise.
The project is to help us give out the model to be used in designing the network. The idea will be
explained where we have to describe the project, the scope of the project, the purpose of the case
study, the assumptions that have been made, the list of the devices to be used when networking, the
system design logical diagram, justification of the applied hardware’s and the conclusion which will give
a summary of what we have analysed in the other areas.
Description of the Project
The management of AusEd is in need of a network and we will have a giant construction to the
implementation of the proposed network design. From the description we have to start the plan of the
infrastructure where we will base it on the resources available and what is needed in making the work
complete. There are some objectives that need to be achieved at the end of the day. There is already an
existing network. Their idea is to improve their relationship with their customers where they are
considering to use the Customer Relationship management software’s and the Microsoft server 2007
which will be used when we are exchanging the emails through sending and receiving. When we say we
want to do the plan it may sound easy but when we do a feasibility study and understand the following
points such as the ratio of the servers to the number of hosts (Workstations), the expected size of the IT
infrastructure, mixing the platforms, building a fast network may be a big challenge when determining
how the network will be designed.
Scope of the Problem and its Purpose
Designing the IT infrastructure of AusEd will help them in determining the strategic plan which is
classified in to two concepts where they are looking in to a future where they will be able to increase the
resources through the diversification of the sources of fund and minimizing the all cost that results ot all
the core-non activities. After understanding the strategic plan then we are required to understand the
technology plan where we will help them in developing an offline Moodle that will help the
management to help the students maintain the personal computers of the school and at the same time
access resources when they are offline but connected to the network. The other development in the

technology plan is coming up with a system where we have develop an add-on Moodle which will acts as
a project where the students will be able to take a Photo exam when they are on the network on their
personal computers and laptops.
The main objective of this project is understanding the network future scalability that will help in
accommodating additional devices in future (Coleman, 2012). We would also a network design that
will be easy to manage when problems arises and when there is need for troubleshooting in cases
when they arise. Also the security of the network will be a great consideration as making this
network design we will need to consider the security of the network and that is why we have told
to explain on the use of security devices and software’s such as the firewalls and the virtual
Private networks (VPNs).
Assumptions Made
When the experts in networking are doing an analysis in the feasibility study of the design of
AusEd network then we will need to do some assumptions as they are explained here below. The
first assumptions is that we expect the AusEd institution to add some devices in the future which
will in turn require us to develop a system that has scalability, flexibility and reliable hence
requiring us to use the three layered hierarchical model. Second assumptions is that we expect
the management of AusEd not to put constraints on the budget such that they will not be able to
make it hard when we ask for the money for the equipment’s hence delaying the implementation
process. Third Assumption is where we take the small logical diagram to represent the entire
system design. Lastly is that the estimate cost of the network devices is just an estimate that will
be used to provide an overview of the entire AusEd network.
a project where the students will be able to take a Photo exam when they are on the network on their
personal computers and laptops.
The main objective of this project is understanding the network future scalability that will help in
accommodating additional devices in future (Coleman, 2012). We would also a network design that
will be easy to manage when problems arises and when there is need for troubleshooting in cases
when they arise. Also the security of the network will be a great consideration as making this
network design we will need to consider the security of the network and that is why we have told
to explain on the use of security devices and software’s such as the firewalls and the virtual
Private networks (VPNs).
Assumptions Made
When the experts in networking are doing an analysis in the feasibility study of the design of
AusEd network then we will need to do some assumptions as they are explained here below. The
first assumptions is that we expect the AusEd institution to add some devices in the future which
will in turn require us to develop a system that has scalability, flexibility and reliable hence
requiring us to use the three layered hierarchical model. Second assumptions is that we expect
the management of AusEd not to put constraints on the budget such that they will not be able to
make it hard when we ask for the money for the equipment’s hence delaying the implementation
process. Third Assumption is where we take the small logical diagram to represent the entire
system design. Lastly is that the estimate cost of the network devices is just an estimate that will
be used to provide an overview of the entire AusEd network.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
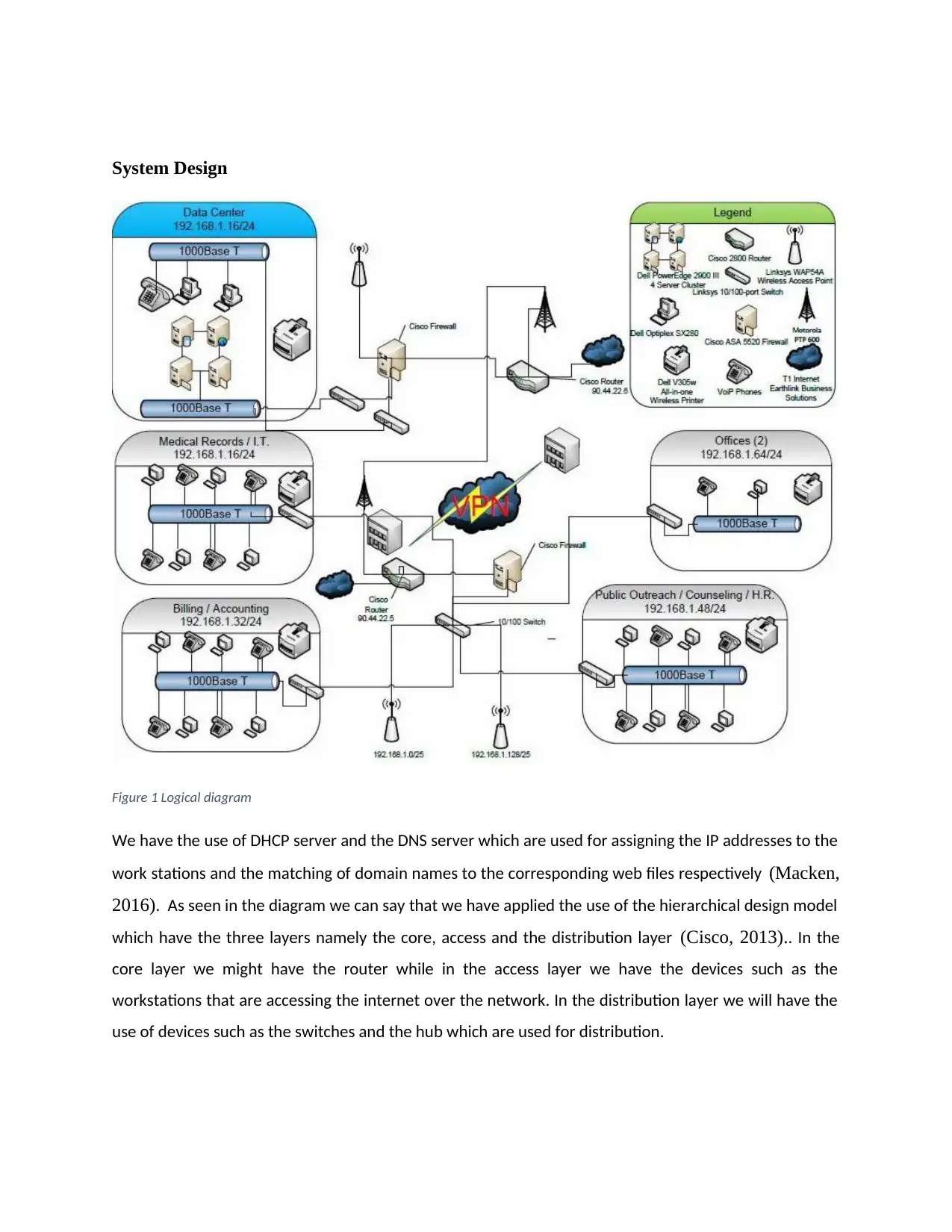
System Design
Figure 1 Logical diagram
We have the use of DHCP server and the DNS server which are used for assigning the IP addresses to the
work stations and the matching of domain names to the corresponding web files respectively (Macken,
2016). As seen in the diagram we can say that we have applied the use of the hierarchical design model
which have the three layers namely the core, access and the distribution layer (Cisco, 2013).. In the
core layer we might have the router while in the access layer we have the devices such as the
workstations that are accessing the internet over the network. In the distribution layer we will have the
use of devices such as the switches and the hub which are used for distribution.
Figure 1 Logical diagram
We have the use of DHCP server and the DNS server which are used for assigning the IP addresses to the
work stations and the matching of domain names to the corresponding web files respectively (Macken,
2016). As seen in the diagram we can say that we have applied the use of the hierarchical design model
which have the three layers namely the core, access and the distribution layer (Cisco, 2013).. In the
core layer we might have the router while in the access layer we have the devices such as the
workstations that are accessing the internet over the network. In the distribution layer we will have the
use of devices such as the switches and the hub which are used for distribution.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
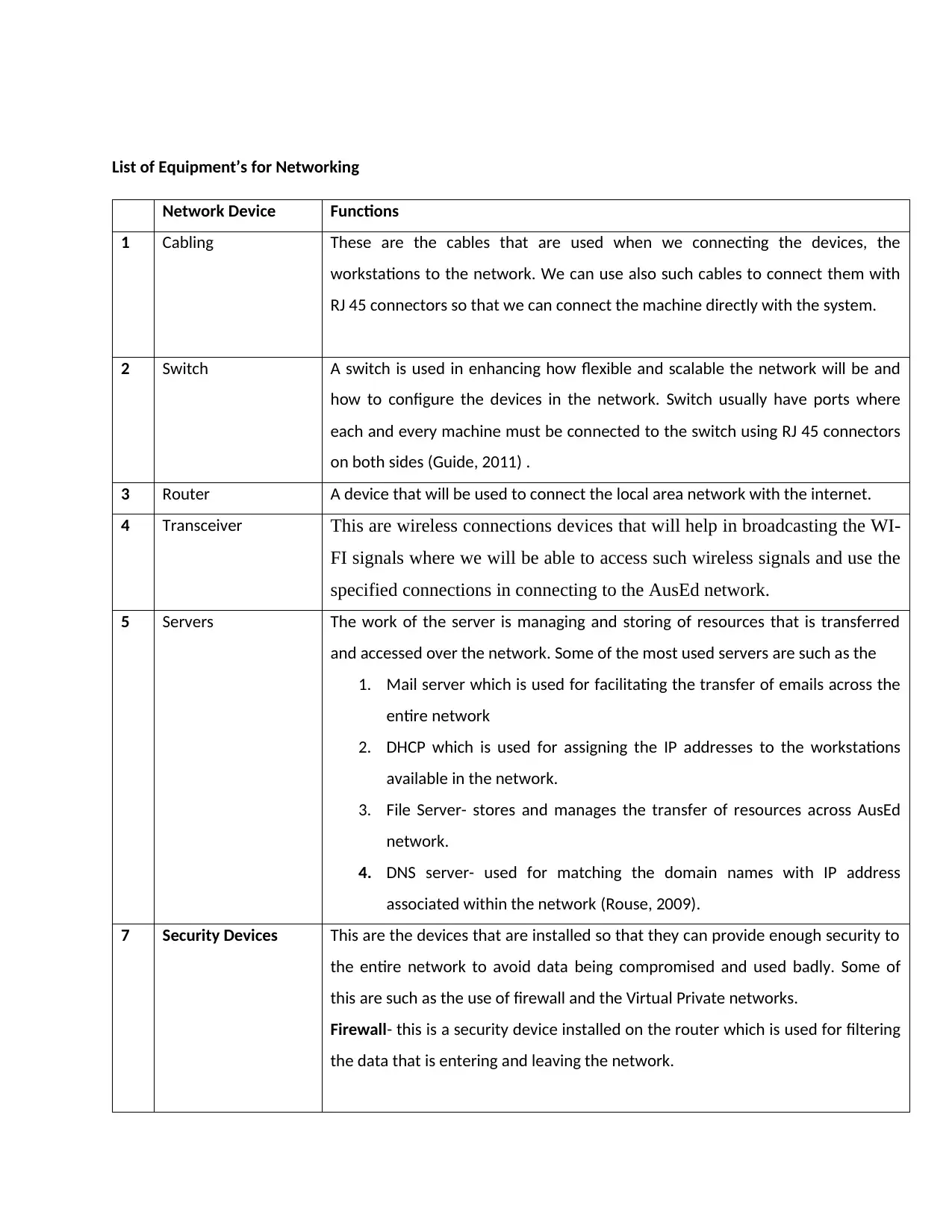
List of Equipment’s for Networking
Network Device Functions
1 Cabling These are the cables that are used when we connecting the devices, the
workstations to the network. We can use also such cables to connect them with
RJ 45 connectors so that we can connect the machine directly with the system.
2 Switch A switch is used in enhancing how flexible and scalable the network will be and
how to configure the devices in the network. Switch usually have ports where
each and every machine must be connected to the switch using RJ 45 connectors
on both sides (Guide, 2011) .
3 Router A device that will be used to connect the local area network with the internet.
4 Transceiver This are wireless connections devices that will help in broadcasting the WI-
FI signals where we will be able to access such wireless signals and use the
specified connections in connecting to the AusEd network.
5 Servers The work of the server is managing and storing of resources that is transferred
and accessed over the network. Some of the most used servers are such as the
1. Mail server which is used for facilitating the transfer of emails across the
entire network
2. DHCP which is used for assigning the IP addresses to the workstations
available in the network.
3. File Server- stores and manages the transfer of resources across AusEd
network.
4. DNS server- used for matching the domain names with IP address
associated within the network (Rouse, 2009).
7 Security Devices This are the devices that are installed so that they can provide enough security to
the entire network to avoid data being compromised and used badly. Some of
this are such as the use of firewall and the Virtual Private networks.
Firewall- this is a security device installed on the router which is used for filtering
the data that is entering and leaving the network.
Network Device Functions
1 Cabling These are the cables that are used when we connecting the devices, the
workstations to the network. We can use also such cables to connect them with
RJ 45 connectors so that we can connect the machine directly with the system.
2 Switch A switch is used in enhancing how flexible and scalable the network will be and
how to configure the devices in the network. Switch usually have ports where
each and every machine must be connected to the switch using RJ 45 connectors
on both sides (Guide, 2011) .
3 Router A device that will be used to connect the local area network with the internet.
4 Transceiver This are wireless connections devices that will help in broadcasting the WI-
FI signals where we will be able to access such wireless signals and use the
specified connections in connecting to the AusEd network.
5 Servers The work of the server is managing and storing of resources that is transferred
and accessed over the network. Some of the most used servers are such as the
1. Mail server which is used for facilitating the transfer of emails across the
entire network
2. DHCP which is used for assigning the IP addresses to the workstations
available in the network.
3. File Server- stores and manages the transfer of resources across AusEd
network.
4. DNS server- used for matching the domain names with IP address
associated within the network (Rouse, 2009).
7 Security Devices This are the devices that are installed so that they can provide enough security to
the entire network to avoid data being compromised and used badly. Some of
this are such as the use of firewall and the Virtual Private networks.
Firewall- this is a security device installed on the router which is used for filtering
the data that is entering and leaving the network.
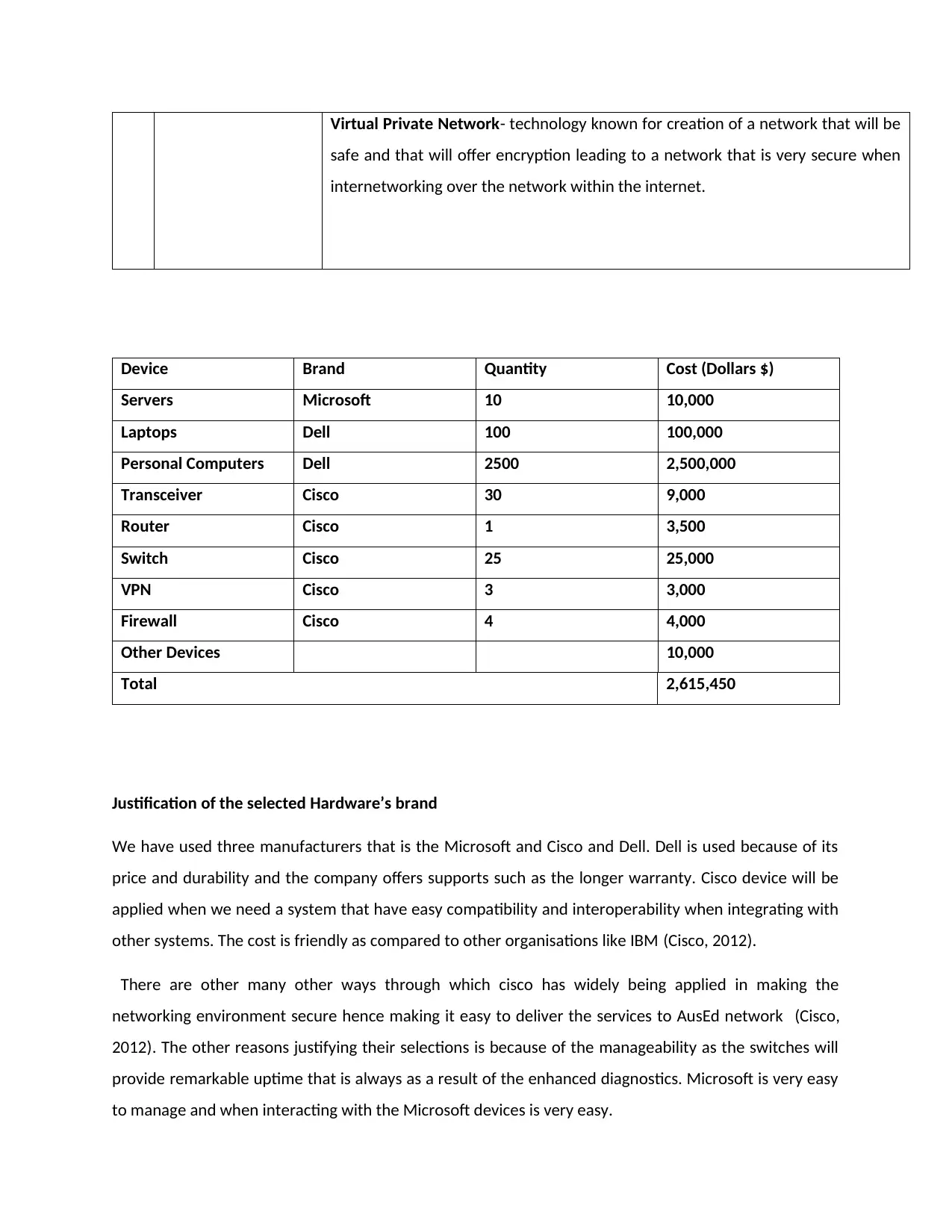
Virtual Private Network- technology known for creation of a network that will be
safe and that will offer encryption leading to a network that is very secure when
internetworking over the network within the internet.
Device Brand Quantity Cost (Dollars $)
Servers Microsoft 10 10,000
Laptops Dell 100 100,000
Personal Computers Dell 2500 2,500,000
Transceiver Cisco 30 9,000
Router Cisco 1 3,500
Switch Cisco 25 25,000
VPN Cisco 3 3,000
Firewall Cisco 4 4,000
Other Devices 10,000
Total 2,615,450
Justification of the selected Hardware’s brand
We have used three manufacturers that is the Microsoft and Cisco and Dell. Dell is used because of its
price and durability and the company offers supports such as the longer warranty. Cisco device will be
applied when we need a system that have easy compatibility and interoperability when integrating with
other systems. The cost is friendly as compared to other organisations like IBM (Cisco, 2012).
There are other many other ways through which cisco has widely being applied in making the
networking environment secure hence making it easy to deliver the services to AusEd network (Cisco,
2012). The other reasons justifying their selections is because of the manageability as the switches will
provide remarkable uptime that is always as a result of the enhanced diagnostics. Microsoft is very easy
to manage and when interacting with the Microsoft devices is very easy.
safe and that will offer encryption leading to a network that is very secure when
internetworking over the network within the internet.
Device Brand Quantity Cost (Dollars $)
Servers Microsoft 10 10,000
Laptops Dell 100 100,000
Personal Computers Dell 2500 2,500,000
Transceiver Cisco 30 9,000
Router Cisco 1 3,500
Switch Cisco 25 25,000
VPN Cisco 3 3,000
Firewall Cisco 4 4,000
Other Devices 10,000
Total 2,615,450
Justification of the selected Hardware’s brand
We have used three manufacturers that is the Microsoft and Cisco and Dell. Dell is used because of its
price and durability and the company offers supports such as the longer warranty. Cisco device will be
applied when we need a system that have easy compatibility and interoperability when integrating with
other systems. The cost is friendly as compared to other organisations like IBM (Cisco, 2012).
There are other many other ways through which cisco has widely being applied in making the
networking environment secure hence making it easy to deliver the services to AusEd network (Cisco,
2012). The other reasons justifying their selections is because of the manageability as the switches will
provide remarkable uptime that is always as a result of the enhanced diagnostics. Microsoft is very easy
to manage and when interacting with the Microsoft devices is very easy.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Conclusion
The research above has been on the analysis of the equipment’s used when delivering the analysis of
the design. The design diagram have been used to explain how the router, servers, switches and the
workstations interact with the network. We have used the Three-hierarchical layer network design in
explaining the way the devices will be arranged from the access layer to distribution layer and lastly to
the core layer. If the above information is applied by AusEd then they will be guaranteed a smooth
network implementation in all its branches.
References
Adato, L., 2015. 5 Fundamental Requirements For High-Performing Networks. A new set of network
essentials is necessary to meet the challenges of today's network administration and management, pp.
23-36.
The research above has been on the analysis of the equipment’s used when delivering the analysis of
the design. The design diagram have been used to explain how the router, servers, switches and the
workstations interact with the network. We have used the Three-hierarchical layer network design in
explaining the way the devices will be arranged from the access layer to distribution layer and lastly to
the core layer. If the above information is applied by AusEd then they will be guaranteed a smooth
network implementation in all its branches.
References
Adato, L., 2015. 5 Fundamental Requirements For High-Performing Networks. A new set of network
essentials is necessary to meet the challenges of today's network administration and management, pp.
23-36.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Anon., 2010. Subnetting. [Online]
Available at: http://www.tutorialspoint.com/ipv4/ipv4_subnetting.htm
[Accessed 10 September 2017].
Cisco, 2009. Benefits of a Hierarchical Network, s.l.: Cisco.
Cisco, 2012. Cisco Router. [Online]
Available at: http://www.router-switch.com New and Used Cisco network equipment, cisco router,cisco
switch
[Accessed 20 May 2018].
Cisco, 2013. Small Enterprise Design Profile Reference Guide, s.l.: cisco.
CISCO, 2014. Campus Design Summary, Singapore: Cisco.
Coleman, N., 2012. Happy Haven Day care network design proposal, Michigan: Network Solution Inc.
Hope, C., 2017. Router. [Online]
Available at: https://www.computerhope.com/jargon/r/router.htm
[Accessed 03 may 2018].
Hope, C., 2017. Server. [Online]
Available at: https://www.computerhope.com/jargon/s/server.htm
[Accessed 03 May 2018].
JoshWepman, 2015. techwalla. [Online]
Available at: https://www.techwalla.com/articles/what-are-the-benefits-of-hierarchical-network-design
Macken, T., 2016. Azure Resource Manager and Classic Deployment, s.l.: Microsoft.
Meena, R., 2017. How to configure DHCP , DNS, HTTP Server in Cisco packet tracer along with switches..
Technoheper24, pp. 1-9.
Mitchell, B., 2017. Internet and Network. What is Computer Networking?, pp. 1-3.
requirement, N., 2014. Network Requirements for a Small Office , s.l.: requirements network.
Tittel, E., 2016. VPN requirements and components: What do you need to set up a VPN?. [Online]
Available at: https://searchenterprisewan.techtarget.com/photostory/4500270544/The-best-VPNs-for-
enterprise-use/4/VPN-requirements-and-components-What-do-you-need-to-set-up-a-VPN
[Accessed 20 May 2018].
Available at: http://www.tutorialspoint.com/ipv4/ipv4_subnetting.htm
[Accessed 10 September 2017].
Cisco, 2009. Benefits of a Hierarchical Network, s.l.: Cisco.
Cisco, 2012. Cisco Router. [Online]
Available at: http://www.router-switch.com New and Used Cisco network equipment, cisco router,cisco
switch
[Accessed 20 May 2018].
Cisco, 2013. Small Enterprise Design Profile Reference Guide, s.l.: cisco.
CISCO, 2014. Campus Design Summary, Singapore: Cisco.
Coleman, N., 2012. Happy Haven Day care network design proposal, Michigan: Network Solution Inc.
Hope, C., 2017. Router. [Online]
Available at: https://www.computerhope.com/jargon/r/router.htm
[Accessed 03 may 2018].
Hope, C., 2017. Server. [Online]
Available at: https://www.computerhope.com/jargon/s/server.htm
[Accessed 03 May 2018].
JoshWepman, 2015. techwalla. [Online]
Available at: https://www.techwalla.com/articles/what-are-the-benefits-of-hierarchical-network-design
Macken, T., 2016. Azure Resource Manager and Classic Deployment, s.l.: Microsoft.
Meena, R., 2017. How to configure DHCP , DNS, HTTP Server in Cisco packet tracer along with switches..
Technoheper24, pp. 1-9.
Mitchell, B., 2017. Internet and Network. What is Computer Networking?, pp. 1-3.
requirement, N., 2014. Network Requirements for a Small Office , s.l.: requirements network.
Tittel, E., 2016. VPN requirements and components: What do you need to set up a VPN?. [Online]
Available at: https://searchenterprisewan.techtarget.com/photostory/4500270544/The-best-VPNs-for-
enterprise-use/4/VPN-requirements-and-components-What-do-you-need-to-set-up-a-VPN
[Accessed 20 May 2018].
1 out of 8
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





