SBM4104 IT Infrastructure: Cloud & Network Proposal for compname
VerifiedAdded on 2023/06/13
|19
|3051
|347
Report
AI Summary
This report proposes an IT infrastructure solution for compname.org.au, focusing on enhancing security, installing firewalls, and configuring DHCP servers. It outlines the objectives for developing a network diagram, including configuring DHCP and DNS servers, and using access control lists. Two network solutions are proposed: an in-house server setup and a cloud-based solution for virtualization and scalability. The report details the required IT components, such as web, DNS, and DHCP servers, and employs a three-layer hierarchical model for network design, dividing the network into core, access, and distribution layers. It also discusses scaling the organizational network, IP addressing, and the benefits of cloud services, including storage, computation, and security. The application of virtualization using dynamic application scaling is also explored, along with network simulation using Cisco Packet Tracer, and the configuration of web, DHCP, and DNS servers.

Running head: IT INFRASTRUCTURE
IT Infrastructure
Name of the Student
Name of the University
Author’s Note
IT Infrastructure
Name of the Student
Name of the University
Author’s Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
IT INFRASTRUCTURE
Table of Contents
Introduction......................................................................................................................................3
Required IT infrastructure Components..........................................................................................4
Three layer hierarchical model........................................................................................................4
Introduction..................................................................................................................................4
Current IT infrastructure Requirements.......................................................................................5
Network Geographical Diagram..................................................................................................5
Scaling of the organizational network.........................................................................................6
Service and server required.........................................................................................................6
Logical network model and Justification.....................................................................................7
IP address and mask.....................................................................................................................8
Design proposal based on Cloud.....................................................................................................8
Identification of different cloud service organization.................................................................9
List of service provided by the organization...............................................................................9
Application of virtualization using dynamic application scaling..............................................11
Network Simulation.......................................................................................................................11
Access Layer Diagram...............................................................................................................11
DHCP Configuration.................................................................................................................12
DNS and WEB server configuration.........................................................................................13
Demonstration and Explanation................................................................................................14
IT INFRASTRUCTURE
Table of Contents
Introduction......................................................................................................................................3
Required IT infrastructure Components..........................................................................................4
Three layer hierarchical model........................................................................................................4
Introduction..................................................................................................................................4
Current IT infrastructure Requirements.......................................................................................5
Network Geographical Diagram..................................................................................................5
Scaling of the organizational network.........................................................................................6
Service and server required.........................................................................................................6
Logical network model and Justification.....................................................................................7
IP address and mask.....................................................................................................................8
Design proposal based on Cloud.....................................................................................................8
Identification of different cloud service organization.................................................................9
List of service provided by the organization...............................................................................9
Application of virtualization using dynamic application scaling..............................................11
Network Simulation.......................................................................................................................11
Access Layer Diagram...............................................................................................................11
DHCP Configuration.................................................................................................................12
DNS and WEB server configuration.........................................................................................13
Demonstration and Explanation................................................................................................14

2
IT INFRASTRUCTURE
Conclusion and Recommendations................................................................................................15
Bibliography..................................................................................................................................16
IT INFRASTRUCTURE
Conclusion and Recommendations................................................................................................15
Bibliography..................................................................................................................................16
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3
IT INFRASTRUCTURE
Introduction
The main aims and objectives for preparing the network infrastructure for compname.org.au
is listed below:
To increase the security of the servers such that the sensitive information residing in the
data center and the servers cannot be access by the illegal users.
To install firewall at different location of the network for allowing or denying the data
packets to reach the destination location.
To configure the DHCP servers with the pool of address for allocating IP address to the
machines connected with the interface of the router.
To configure a main server with SMTP protocol such that the business rules are aligned
and the internal communication can be maintained with the employees can send or
receive data packets in the network.
The objectives for the development of the network diagram are given below:
Configure the DHCP and the DNS server according to the requirement for association
of the network equipment and enabling communication between them
To configure the DNS server with network address translation and using a domain
name for accessing the web server
To configure the router with access control list for blocking the unknown sources to
connect with the internal network of the company.
The report is prepared for compname.org.au by proposing two different network solution
for the organization aligning the needs of the organization. For the development of the network
solution an analysis is made on the IT components required for the development of the network
IT INFRASTRUCTURE
Introduction
The main aims and objectives for preparing the network infrastructure for compname.org.au
is listed below:
To increase the security of the servers such that the sensitive information residing in the
data center and the servers cannot be access by the illegal users.
To install firewall at different location of the network for allowing or denying the data
packets to reach the destination location.
To configure the DHCP servers with the pool of address for allocating IP address to the
machines connected with the interface of the router.
To configure a main server with SMTP protocol such that the business rules are aligned
and the internal communication can be maintained with the employees can send or
receive data packets in the network.
The objectives for the development of the network diagram are given below:
Configure the DHCP and the DNS server according to the requirement for association
of the network equipment and enabling communication between them
To configure the DNS server with network address translation and using a domain
name for accessing the web server
To configure the router with access control list for blocking the unknown sources to
connect with the internal network of the company.
The report is prepared for compname.org.au by proposing two different network solution
for the organization aligning the needs of the organization. For the development of the network
solution an analysis is made on the IT components required for the development of the network
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4
IT INFRASTRUCTURE
and a local area network is designed for connecting the network devices. A prototype of the
network is designed in cisco packet tracer and the network devices are configured for connecting
with different branches. A local area network and a cloud based solution is proposed that can be
implemented by the company for virtualizing the servers and increase the scalability of the
network. The benefits of the development of the in house servers and the cloud based design
solution are discussed in the report.
There are 2000 hosts located in different areas of the organization and that are needed to
be connected with each other for enabling communication in the network. Compname is a
software development organization and it has different teams that are located in different floors
of a three story building. There is a requirement for the management of the network and secure
the network from external users. A wireless access point is needed to be installed in each of the
floor such that the employees can connect their smart devices with the network and send and
receive data packets. A dmz zone should be created for the installation of the servers and
configure it according to the business rules for protecting the core layer of the network.
Required IT infrastructure Components
The main resources and IT components required for the development of the network
solution are:
Web Server
DNS Server
DHCP Server
Router
Switch
IT INFRASTRUCTURE
and a local area network is designed for connecting the network devices. A prototype of the
network is designed in cisco packet tracer and the network devices are configured for connecting
with different branches. A local area network and a cloud based solution is proposed that can be
implemented by the company for virtualizing the servers and increase the scalability of the
network. The benefits of the development of the in house servers and the cloud based design
solution are discussed in the report.
There are 2000 hosts located in different areas of the organization and that are needed to
be connected with each other for enabling communication in the network. Compname is a
software development organization and it has different teams that are located in different floors
of a three story building. There is a requirement for the management of the network and secure
the network from external users. A wireless access point is needed to be installed in each of the
floor such that the employees can connect their smart devices with the network and send and
receive data packets. A dmz zone should be created for the installation of the servers and
configure it according to the business rules for protecting the core layer of the network.
Required IT infrastructure Components
The main resources and IT components required for the development of the network
solution are:
Web Server
DNS Server
DHCP Server
Router
Switch

5
IT INFRASTRUCTURE
Firewall
Three layer hierarchical model
Introduction
For the development of the network solution a three layer hierarchical model is selected
because it increases the reliability of the network. The three layer hierarchical model is
developed by dividing each of the layers of the network into core, access and distribution layers
and reducing the complexity of the network. The access layer consist of the device that can be
used for controlling the workgroup and it consists of the layer 2 switch and the access point that
helps in connecting the servers and the workstations connected in the network. The distribution
layer is used for analyzing the fastest path that can be used for forwarding the request to the
servers connected in the network. The core layer is used for transferring the huge volume of data
traffic in the network and it is used for interconnecting the distribution layer and consist of high
speed network devices such as switches, routers that are connected using redundant links.
IT INFRASTRUCTURE
Firewall
Three layer hierarchical model
Introduction
For the development of the network solution a three layer hierarchical model is selected
because it increases the reliability of the network. The three layer hierarchical model is
developed by dividing each of the layers of the network into core, access and distribution layers
and reducing the complexity of the network. The access layer consist of the device that can be
used for controlling the workgroup and it consists of the layer 2 switch and the access point that
helps in connecting the servers and the workstations connected in the network. The distribution
layer is used for analyzing the fastest path that can be used for forwarding the request to the
servers connected in the network. The core layer is used for transferring the huge volume of data
traffic in the network and it is used for interconnecting the distribution layer and consist of high
speed network devices such as switches, routers that are connected using redundant links.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
6
IT INFRASTRUCTURE
Current IT infrastructure Requirements
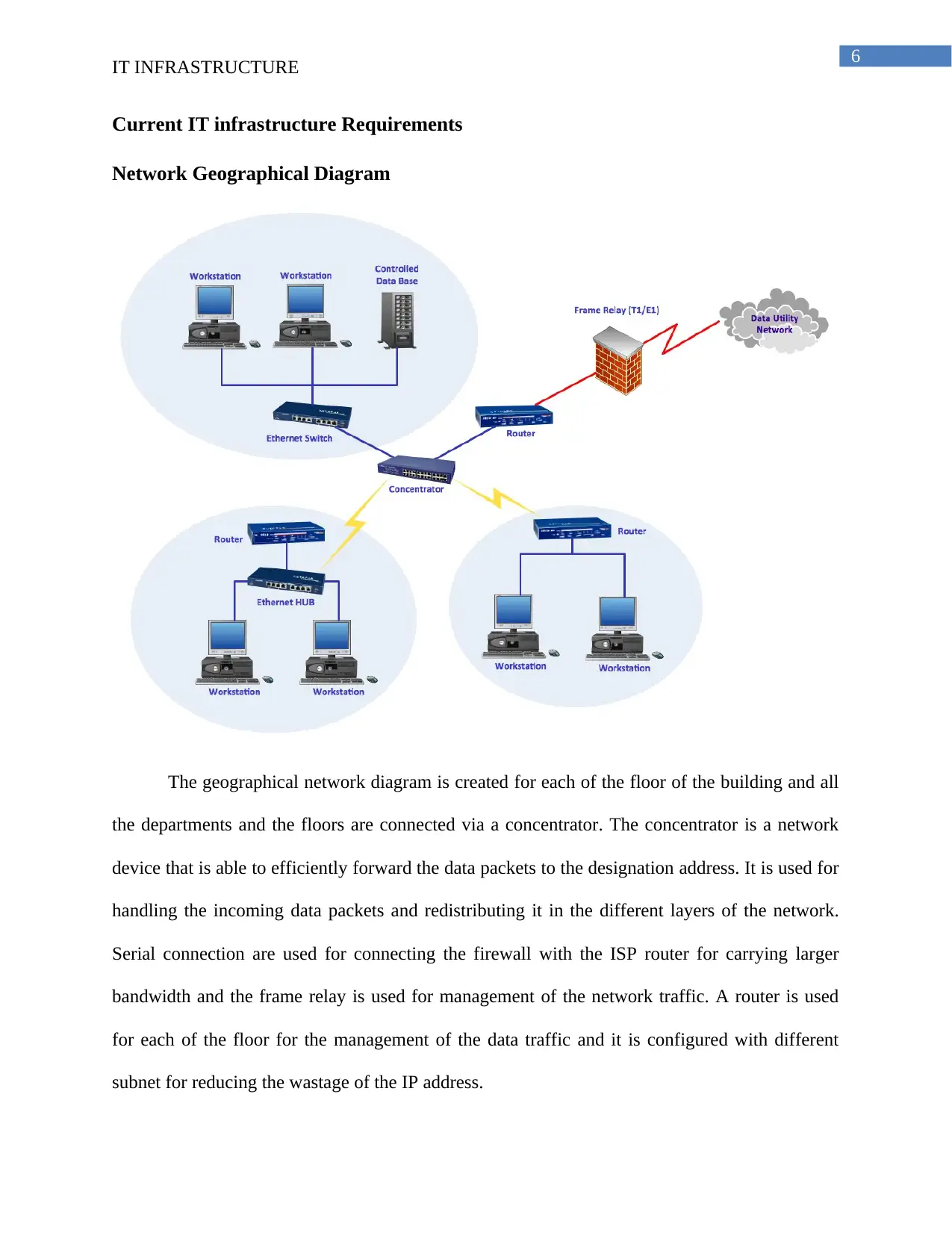
Network Geographical Diagram
The geographical network diagram is created for each of the floor of the building and all
the departments and the floors are connected via a concentrator. The concentrator is a network
device that is able to efficiently forward the data packets to the designation address. It is used for
handling the incoming data packets and redistributing it in the different layers of the network.
Serial connection are used for connecting the firewall with the ISP router for carrying larger
bandwidth and the frame relay is used for management of the network traffic. A router is used
for each of the floor for the management of the data traffic and it is configured with different
subnet for reducing the wastage of the IP address.
IT INFRASTRUCTURE
Current IT infrastructure Requirements
Network Geographical Diagram
The geographical network diagram is created for each of the floor of the building and all
the departments and the floors are connected via a concentrator. The concentrator is a network
device that is able to efficiently forward the data packets to the designation address. It is used for
handling the incoming data packets and redistributing it in the different layers of the network.
Serial connection are used for connecting the firewall with the ISP router for carrying larger
bandwidth and the frame relay is used for management of the network traffic. A router is used
for each of the floor for the management of the data traffic and it is configured with different
subnet for reducing the wastage of the IP address.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7
IT INFRASTRUCTURE
Scaling of the organizational network
The use of separate router for each of the floor increases the scalability of the network.
The network address plan is created for configuring the routers and the network device interface
according to the addressing plan. For increasing the scalability of the network solution the
network address is subdivided into different subnets and the routers and the servers are
configured with DHCP pool for automatically assign the IP address to the hosts connected with
the interface of the router.
Service and server required
The servers and the service that are required for the development of the current network
solution are given below:
DHCP service – This is required for creating a DHCP pool and connecting the end
device in the network with the IP address.
Web and DNS Service – This sis required to host a web page and created different
account for the employees to access the resources and the information from the file server.
IT INFRASTRUCTURE
Scaling of the organizational network
The use of separate router for each of the floor increases the scalability of the network.
The network address plan is created for configuring the routers and the network device interface
according to the addressing plan. For increasing the scalability of the network solution the
network address is subdivided into different subnets and the routers and the servers are
configured with DHCP pool for automatically assign the IP address to the hosts connected with
the interface of the router.
Service and server required
The servers and the service that are required for the development of the current network
solution are given below:
DHCP service – This is required for creating a DHCP pool and connecting the end
device in the network with the IP address.
Web and DNS Service – This sis required to host a web page and created different
account for the employees to access the resources and the information from the file server.
8
IT INFRASTRUCTURE
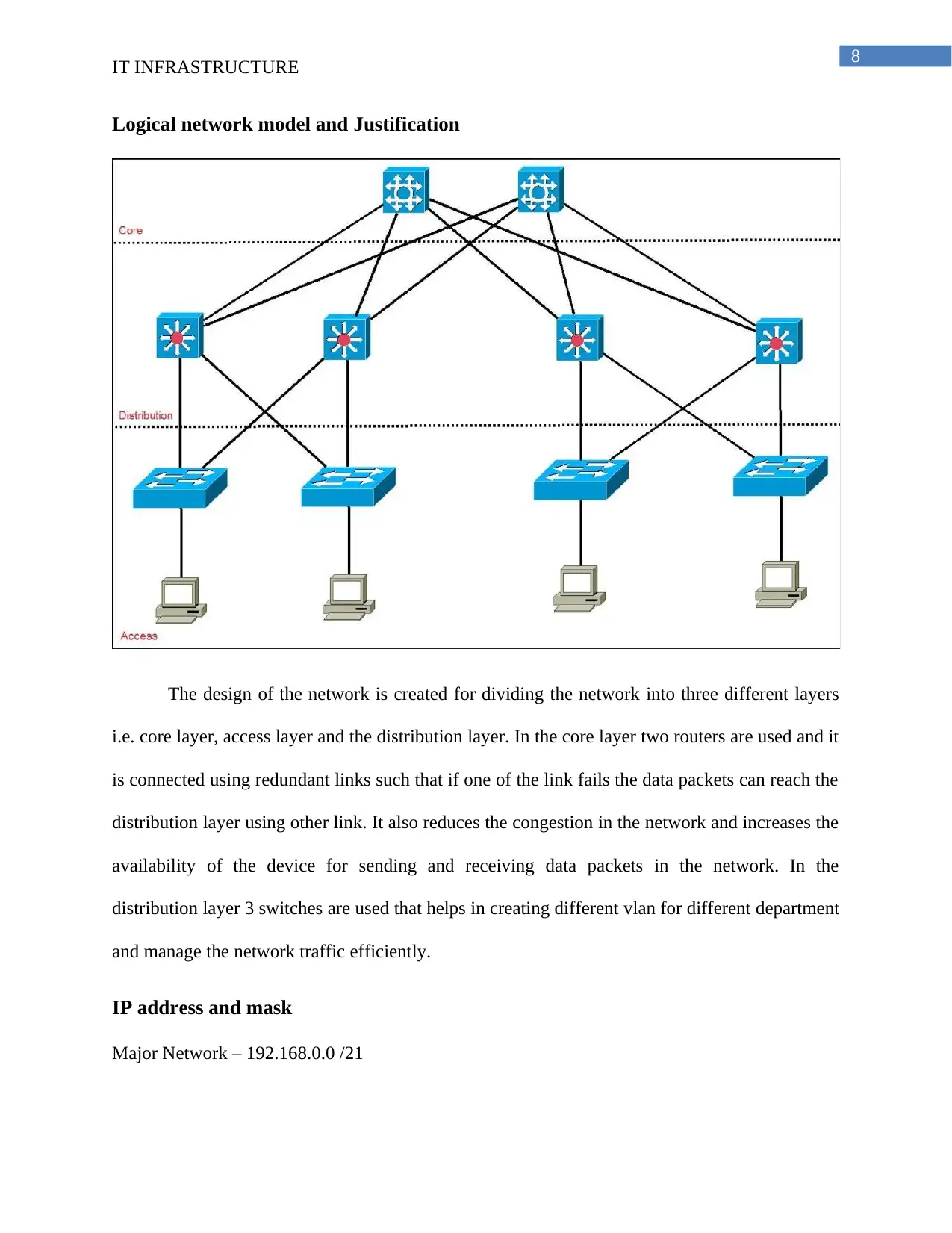
Logical network model and Justification
The design of the network is created for dividing the network into three different layers
i.e. core layer, access layer and the distribution layer. In the core layer two routers are used and it
is connected using redundant links such that if one of the link fails the data packets can reach the
distribution layer using other link. It also reduces the congestion in the network and increases the
availability of the device for sending and receiving data packets in the network. In the
distribution layer 3 switches are used that helps in creating different vlan for different department
and manage the network traffic efficiently.
IP address and mask
Major Network – 192.168.0.0 /21
IT INFRASTRUCTURE
Logical network model and Justification
The design of the network is created for dividing the network into three different layers
i.e. core layer, access layer and the distribution layer. In the core layer two routers are used and it
is connected using redundant links such that if one of the link fails the data packets can reach the
distribution layer using other link. It also reduces the congestion in the network and increases the
availability of the device for sending and receiving data packets in the network. In the
distribution layer 3 switches are used that helps in creating different vlan for different department
and manage the network traffic efficiently.
IP address and mask
Major Network – 192.168.0.0 /21
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
9
IT INFRASTRUCTURE
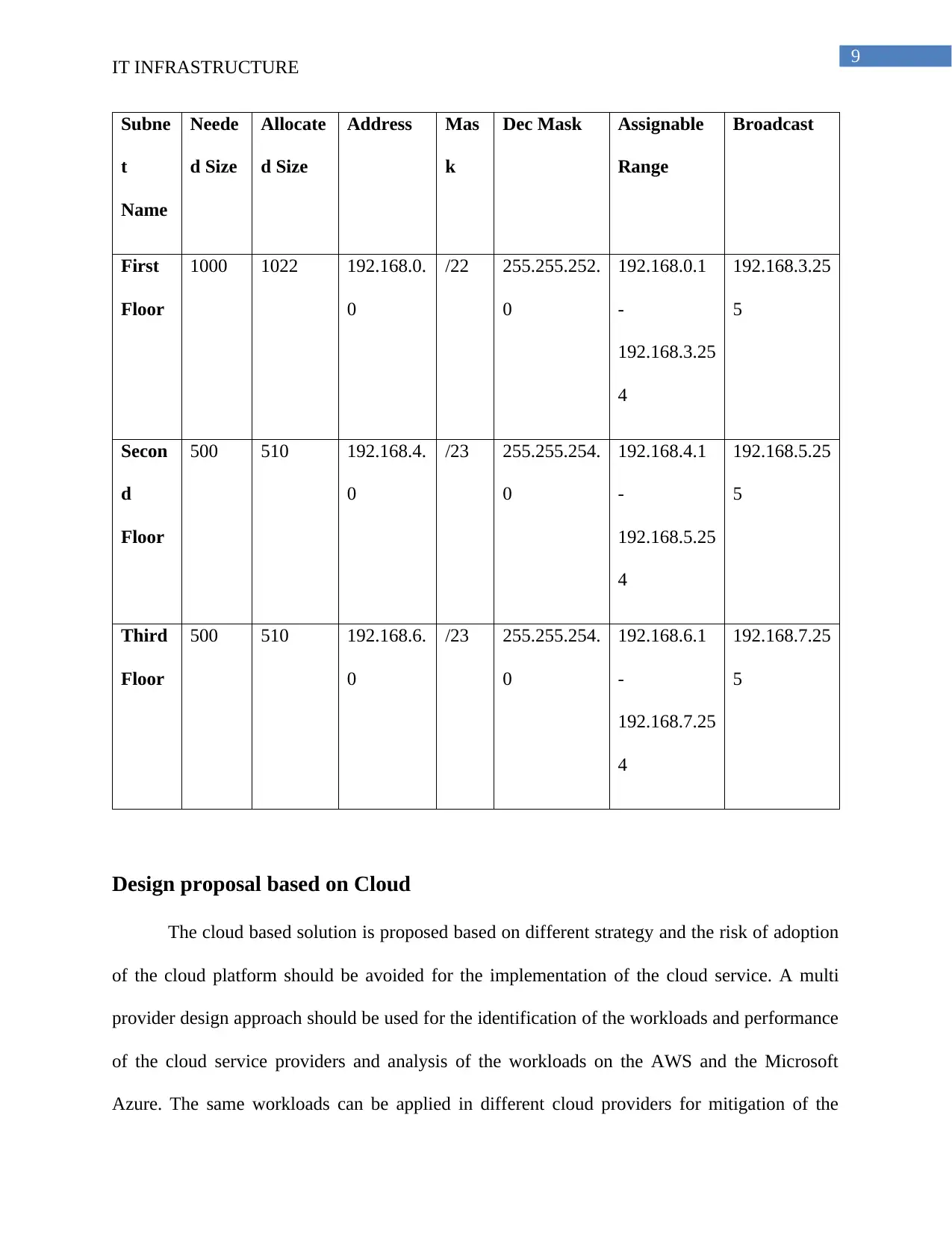
Subne
t
Name
Neede
d Size
Allocate
d Size
Address Mas
k
Dec Mask Assignable
Range
Broadcast
First
Floor
1000 1022 192.168.0.
0
/22 255.255.252.
0
192.168.0.1
-
192.168.3.25
4
192.168.3.25
5
Secon
d
Floor
500 510 192.168.4.
0
/23 255.255.254.
0
192.168.4.1
-
192.168.5.25
4
192.168.5.25
5
Third
Floor
500 510 192.168.6.
0
/23 255.255.254.
0
192.168.6.1
-
192.168.7.25
4
192.168.7.25
5
Design proposal based on Cloud
The cloud based solution is proposed based on different strategy and the risk of adoption
of the cloud platform should be avoided for the implementation of the cloud service. A multi
provider design approach should be used for the identification of the workloads and performance
of the cloud service providers and analysis of the workloads on the AWS and the Microsoft
Azure. The same workloads can be applied in different cloud providers for mitigation of the
IT INFRASTRUCTURE
Subne
t
Name
Neede
d Size
Allocate
d Size
Address Mas
k
Dec Mask Assignable
Range
Broadcast
First
Floor
1000 1022 192.168.0.
0
/22 255.255.252.
0
192.168.0.1
-
192.168.3.25
4
192.168.3.25
5
Secon
d
Floor
500 510 192.168.4.
0
/23 255.255.254.
0
192.168.4.1
-
192.168.5.25
4
192.168.5.25
5
Third
Floor
500 510 192.168.6.
0
/23 255.255.254.
0
192.168.6.1
-
192.168.7.25
4
192.168.7.25
5
Design proposal based on Cloud
The cloud based solution is proposed based on different strategy and the risk of adoption
of the cloud platform should be avoided for the implementation of the cloud service. A multi
provider design approach should be used for the identification of the workloads and performance
of the cloud service providers and analysis of the workloads on the AWS and the Microsoft
Azure. The same workloads can be applied in different cloud providers for mitigation of the
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10
IT INFRASTRUCTURE
potential outrage risk and different options should be provided such as development of the
application for working with multiple service providers, driving automation and portability and
deployment of different application and components for leveraging the micro service approach.
Identification of different cloud service organization
There are different cloud service organization that can be aligned with the business for
differentiation of the current business process and gain the leading position. Technical
innovations should be applied in the business such that business does not gets disrupted. The
implementation of the cloud service technology in the current business process would help the
organization to prioritize the cloud strategies. There are different service such as Iaas, SaaS,
PaaS that are provided by the cloud vendor and it should be selected for the implementation of
the cloud platform. There are different vendor such as AWS, Google, Microsoft Azure, etc. that
provides IaaS service in the market and an in depth analysis should be made for the adoption of
the cloud service.
List of service provided by the organization
The following are the list of service that are provided by the cloud service organization such as
Storage – the cloud service can be used for adding more storage for management of the
files and document in the cloud servers.
Computation – The computation power can be increased and with purchasing of extra
resource and reducing the needs of purchase of extra hardware for the in house server
management.
Migration – The commercial platform can be used for migration of the data platform and
the proficiency of the system can be increased.
IT INFRASTRUCTURE
potential outrage risk and different options should be provided such as development of the
application for working with multiple service providers, driving automation and portability and
deployment of different application and components for leveraging the micro service approach.
Identification of different cloud service organization
There are different cloud service organization that can be aligned with the business for
differentiation of the current business process and gain the leading position. Technical
innovations should be applied in the business such that business does not gets disrupted. The
implementation of the cloud service technology in the current business process would help the
organization to prioritize the cloud strategies. There are different service such as Iaas, SaaS,
PaaS that are provided by the cloud vendor and it should be selected for the implementation of
the cloud platform. There are different vendor such as AWS, Google, Microsoft Azure, etc. that
provides IaaS service in the market and an in depth analysis should be made for the adoption of
the cloud service.
List of service provided by the organization
The following are the list of service that are provided by the cloud service organization such as
Storage – the cloud service can be used for adding more storage for management of the
files and document in the cloud servers.
Computation – The computation power can be increased and with purchasing of extra
resource and reducing the needs of purchase of extra hardware for the in house server
management.
Migration – The commercial platform can be used for migration of the data platform and
the proficiency of the system can be increased.

11
IT INFRASTRUCTURE
Database – The database is used for recording the data generated due to daily activity
and management of the information of the organization.
Network Delivery substance – Authorization should be applied at the access level for
management of the network elements and ensuring integrity of data.
Management instruments – the assets in the organization can be managed for improving
the service framework provided by the cloud vendor.
Developer Tools – The source codes generated by the software development team can be
tested using the developer tools and it can reduce the cost of new application that are required to
be purchased and installed in the physical machine of the organization for proceeding with the
development of the software.
Security – The use of private cloud can increase the security of the sensitive data because
the public cloud platform are not secure and can be accessed by external agents causing a risk for
the organization.
IoT support – It can be used for the management of the unstructured data generated form
the IoT devices installed in the network and storing them in separate servers for the management
of the database.
Mobile Benefits – The mobile applications can be build using the cloud service and the
cost of external software and hardware can be eliminated by the application of the cloud
technology.
IT INFRASTRUCTURE
Database – The database is used for recording the data generated due to daily activity
and management of the information of the organization.
Network Delivery substance – Authorization should be applied at the access level for
management of the network elements and ensuring integrity of data.
Management instruments – the assets in the organization can be managed for improving
the service framework provided by the cloud vendor.
Developer Tools – The source codes generated by the software development team can be
tested using the developer tools and it can reduce the cost of new application that are required to
be purchased and installed in the physical machine of the organization for proceeding with the
development of the software.
Security – The use of private cloud can increase the security of the sensitive data because
the public cloud platform are not secure and can be accessed by external agents causing a risk for
the organization.
IoT support – It can be used for the management of the unstructured data generated form
the IoT devices installed in the network and storing them in separate servers for the management
of the database.
Mobile Benefits – The mobile applications can be build using the cloud service and the
cost of external software and hardware can be eliminated by the application of the cloud
technology.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 19
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





