IT Infrastructure Security: Recommendations and Upgrades Report
VerifiedAdded on 2022/12/26
|13
|591
|20
Report
AI Summary
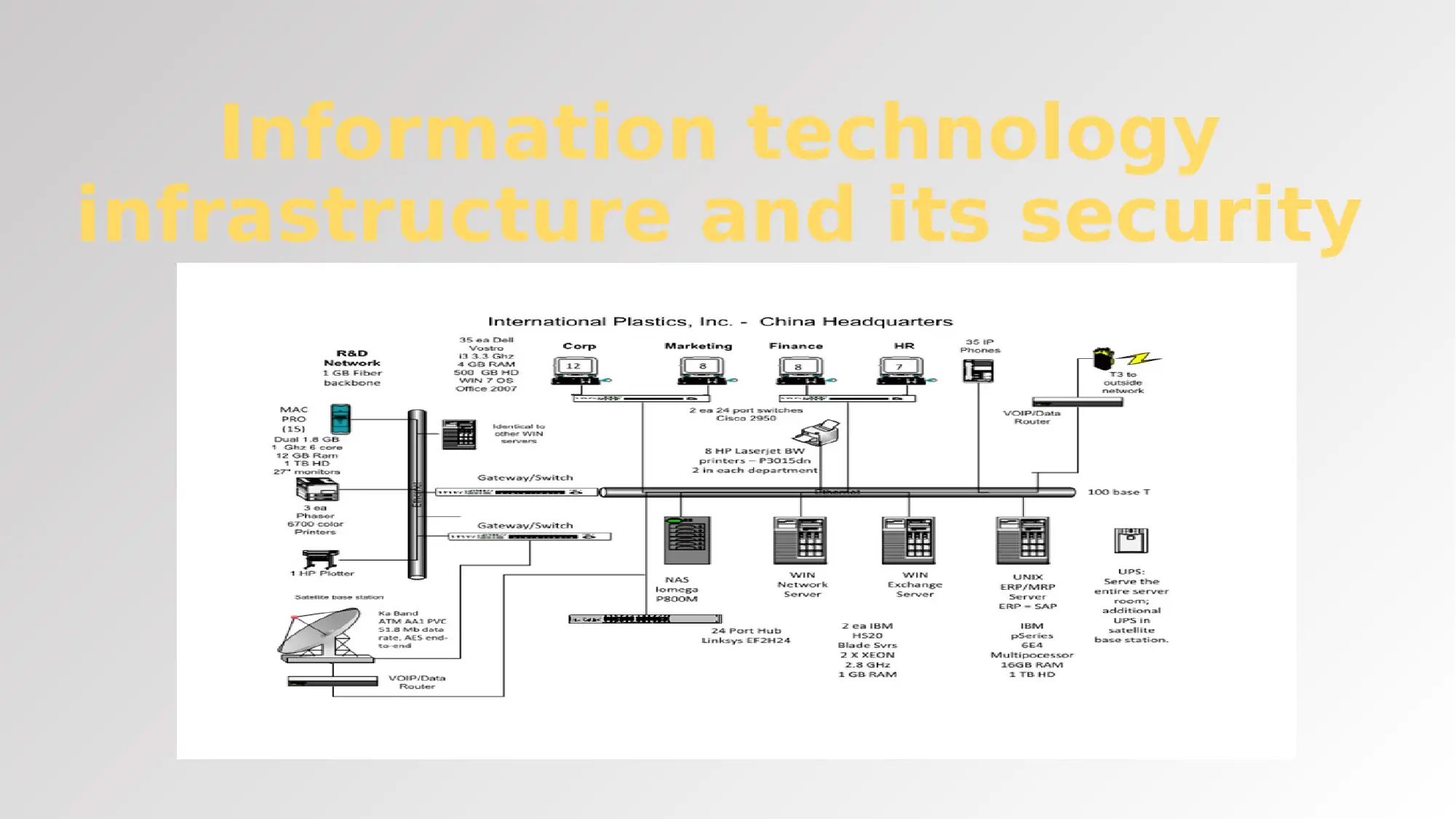
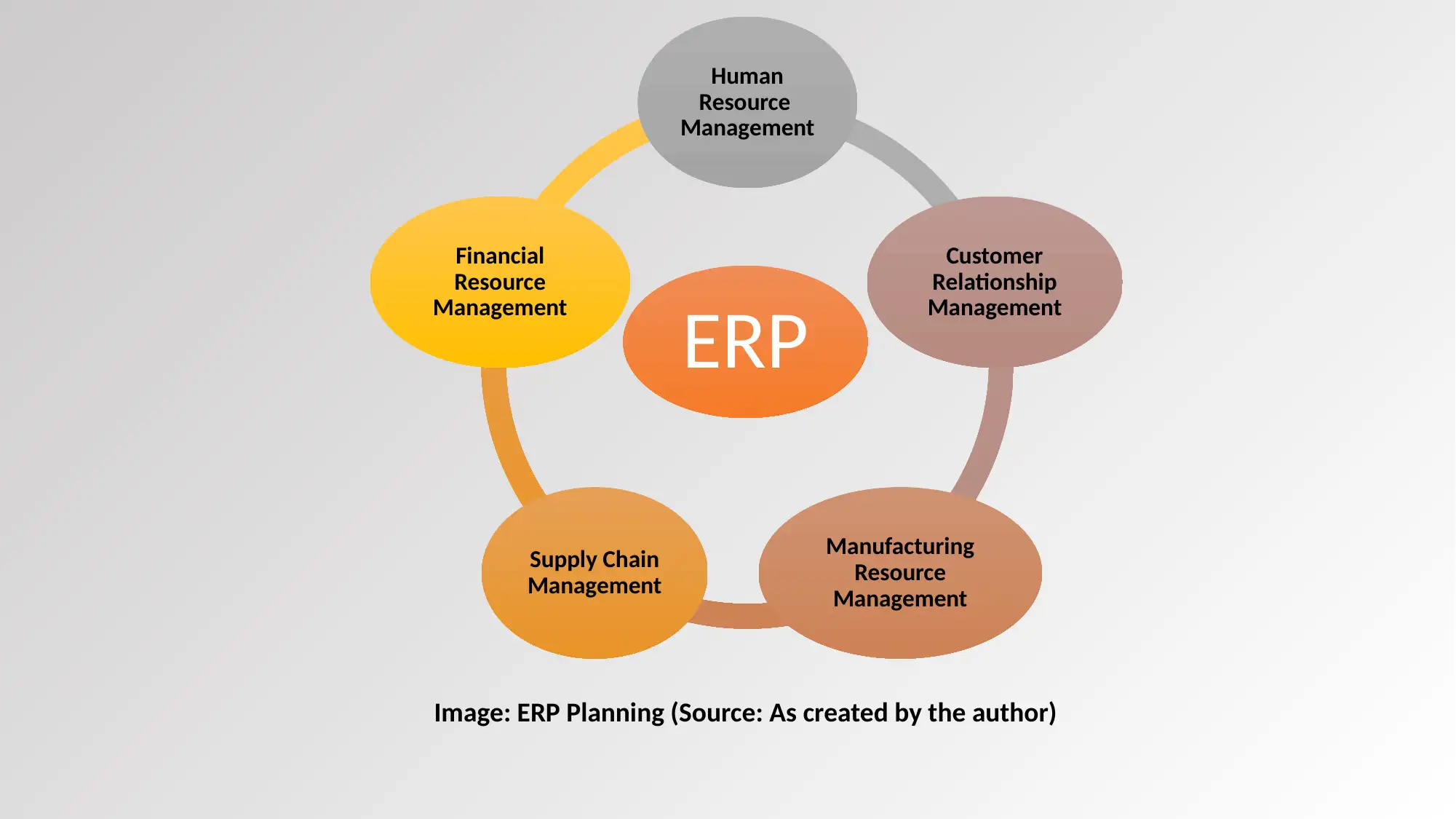
This report focuses on the current IT infrastructure and its security, providing recommendations for improvements and upgrades. It examines the existing infrastructure, identifies vulnerabilities, and suggests solutions such as implementing hardware firewalls, enhancing data protection through encryption and authentication, and upgrading network diagrams. The report also addresses e-commerce strategies, suggesting the implementation of filtering systems. Moreover, it emphasizes the importance of both hardware and software security measures, including the use of strong encryption, separate networks for guests, and the implementation of anti-virus software. The report also highlights the need for employee training and the utilization of data masking and encryption technologies. The report concludes by referencing several sources that support its recommendations.
1 out of 13














![[object Object]](/_next/static/media/star-bottom.7253800d.svg)