IT Networking Design Report: Network Design and Implementation
VerifiedAdded on 2020/03/04
|12
|2179
|592
Report
AI Summary
This report provides a detailed IT network design for a three-floor building with a data center. It encompasses network topology, cabling plans (including LAN and fiber optic), and the implementation of Active Directory for centralized network management. The design incorporates routers, switches, and firewalls for security, including VPN configuration and access control lists (ACLs). The report identifies required servers (web, mail, file), allocates IP addresses and subnet masks, and simulates the network design using Cisco Packet Tracer. It also covers a request for proposal, equipment needs, and measures to prevent security attacks. The report concludes with a discussion of network security, scalability, and the importance of a well-planned network infrastructure. The report emphasizes the need for a secure and efficient network design, suitable for a multi-floor building with a central data center. It also details various network devices, cabling plans, and security measures to ensure a robust and reliable network environment. The report covers various aspects of network design, including cabling, security, and IP address allocation, making it a comprehensive guide to building a secure and efficient IT network.

Running head: IT NETWORKING DESIGNING
IT Networking Designing
Name of the Student
Name of the University
Author’s Note
IT Networking Designing
Name of the Student
Name of the University
Author’s Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
IT NETWORKING DESIGNING
Table of Contents
1. Introduction......................................................................................................................2
2. Designing the network.....................................................................................................2
2.1. Network cabling plan................................................................................................3
2.2. Implementation of Active Directory Service............................................................3
3. Identification of the service and the Server.....................................................................4
4. Allocation of the IP address and subnet masking............................................................5
5. Simulation of the network design using cisco packet tracer............................................6
6. Request for proposal and the equipment’s.......................................................................7
7. Measures for prevention of security attacks....................................................................8
8. Summary and conclusion.................................................................................................8
Bibliography......................................................................................................................10
IT NETWORKING DESIGNING
Table of Contents
1. Introduction......................................................................................................................2
2. Designing the network.....................................................................................................2
2.1. Network cabling plan................................................................................................3
2.2. Implementation of Active Directory Service............................................................3
3. Identification of the service and the Server.....................................................................4
4. Allocation of the IP address and subnet masking............................................................5
5. Simulation of the network design using cisco packet tracer............................................6
6. Request for proposal and the equipment’s.......................................................................7
7. Measures for prevention of security attacks....................................................................8
8. Summary and conclusion.................................................................................................8
Bibliography......................................................................................................................10

2
IT NETWORKING DESIGNING
1. Introduction
The report is prepared for the development of network design for a building having 3
floors and the data center is located at the 3rd floor of the building. Each of the floor of the
building have desktops and servers and are connected with the data center. The network topology
and the cabling plan used for interconnecting the servers, PCs and the data centers are analyzed
and the network design is created. The need for creation of the Virtual private network and the
security measures that are required to be applied for securing the network from external access is
documented in the report.
2. Designing the network
The network design is created including all the necessary networking devices and the
diagram illustrates the network plan followed for the development of the network. The network
is secured from outside intruder by installation of firewall ate the entry and the exit point of the
network. The routers used in the network are properly labelled for each of the floor and switches
are used and the routers are configured with VPN and proper cabling layout is used for creation
of the design. The design is created following the WAN technology and remote connectivity of
the network is enabled for increasing the efficiency and flexibility of the network. The firewall is
required to be configured for allowing the administrative PC to gain access of the resources.
Separate router and switches are used for each of the floor for reducing congestion in the traffic
and separate VLAN are created for the different group if employees for easy management of the
network. Power management and cooling of the data center is required for designing the network
and the space allocation is also important for reducing the risk of tampering of the network
IT NETWORKING DESIGNING
1. Introduction
The report is prepared for the development of network design for a building having 3
floors and the data center is located at the 3rd floor of the building. Each of the floor of the
building have desktops and servers and are connected with the data center. The network topology
and the cabling plan used for interconnecting the servers, PCs and the data centers are analyzed
and the network design is created. The need for creation of the Virtual private network and the
security measures that are required to be applied for securing the network from external access is
documented in the report.
2. Designing the network
The network design is created including all the necessary networking devices and the
diagram illustrates the network plan followed for the development of the network. The network
is secured from outside intruder by installation of firewall ate the entry and the exit point of the
network. The routers used in the network are properly labelled for each of the floor and switches
are used and the routers are configured with VPN and proper cabling layout is used for creation
of the design. The design is created following the WAN technology and remote connectivity of
the network is enabled for increasing the efficiency and flexibility of the network. The firewall is
required to be configured for allowing the administrative PC to gain access of the resources.
Separate router and switches are used for each of the floor for reducing congestion in the traffic
and separate VLAN are created for the different group if employees for easy management of the
network. Power management and cooling of the data center is required for designing the network
and the space allocation is also important for reducing the risk of tampering of the network
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
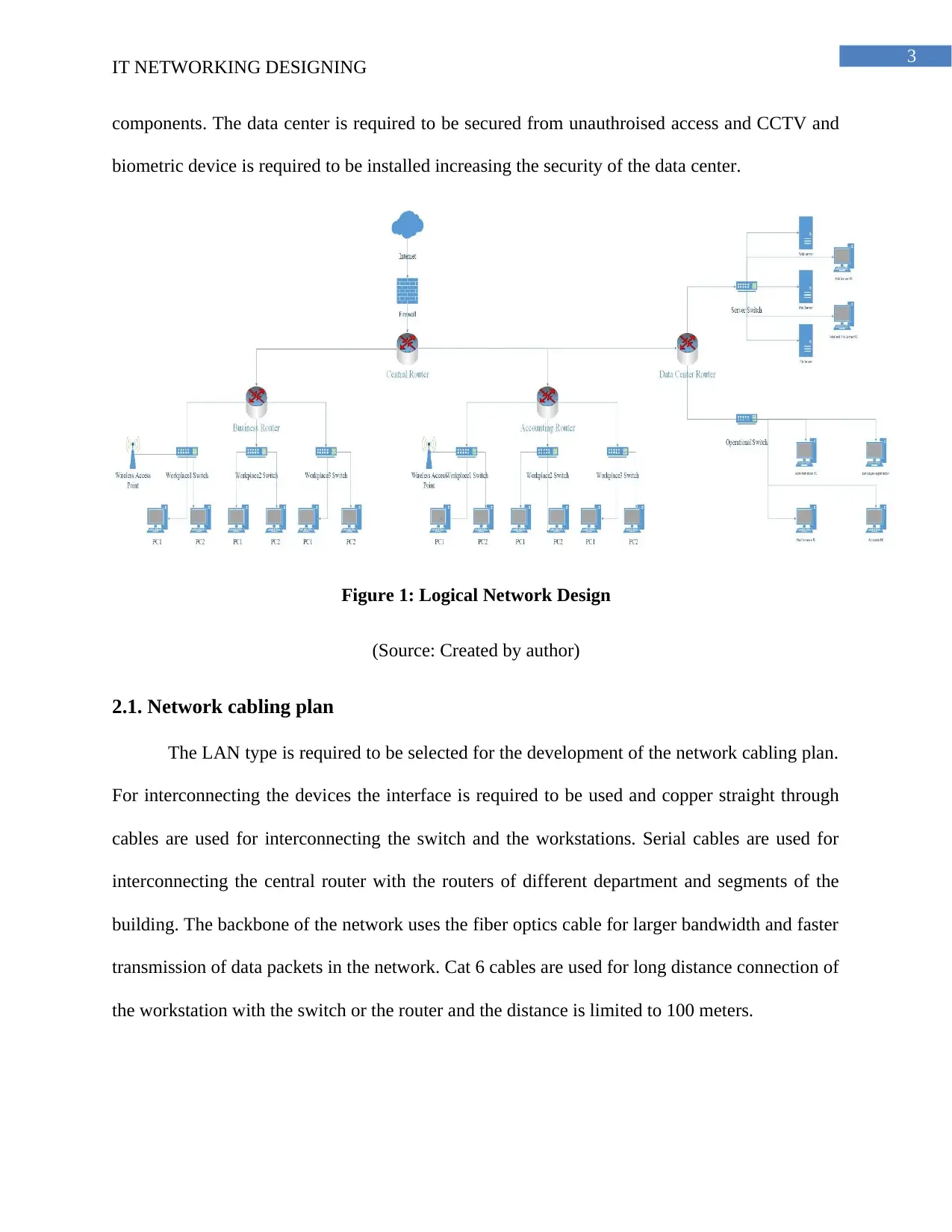
3
IT NETWORKING DESIGNING
components. The data center is required to be secured from unauthroised access and CCTV and
biometric device is required to be installed increasing the security of the data center.
Figure 1: Logical Network Design
(Source: Created by author)
2.1. Network cabling plan
The LAN type is required to be selected for the development of the network cabling plan.
For interconnecting the devices the interface is required to be used and copper straight through
cables are used for interconnecting the switch and the workstations. Serial cables are used for
interconnecting the central router with the routers of different department and segments of the
building. The backbone of the network uses the fiber optics cable for larger bandwidth and faster
transmission of data packets in the network. Cat 6 cables are used for long distance connection of
the workstation with the switch or the router and the distance is limited to 100 meters.
IT NETWORKING DESIGNING
components. The data center is required to be secured from unauthroised access and CCTV and
biometric device is required to be installed increasing the security of the data center.
Figure 1: Logical Network Design
(Source: Created by author)
2.1. Network cabling plan
The LAN type is required to be selected for the development of the network cabling plan.
For interconnecting the devices the interface is required to be used and copper straight through
cables are used for interconnecting the switch and the workstations. Serial cables are used for
interconnecting the central router with the routers of different department and segments of the
building. The backbone of the network uses the fiber optics cable for larger bandwidth and faster
transmission of data packets in the network. Cat 6 cables are used for long distance connection of
the workstation with the switch or the router and the distance is limited to 100 meters.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4
IT NETWORKING DESIGNING
2.2. Implementation of Active Directory Service
Emerging technology can be used for increasing the efficiency of the network and
configuration of the active directory in the server used in the network would help in managing
the network from a single point. The virtualization of the server helps in sharing of the resources
and thus reduces the extra hardware cost. The main sources of the internet is protected with the
installation of the firewall and appropriate authentication is used for protecting the data center
and privacy of the organizational data. A DNS model is adopted for the configuration of the
server and the network development team works on mixed mode for the implementation of the
active directory. A central router connects the data center and the other routers installed at
different floors of the building. A subnet is created for each of the floor and the devices in the
network are provided with the IP address for connecting in the network. The central router is
configured with VPN and it is used by the user to send and receive data in the public and the
shared network. The VPN is used for securing the intranet and access the office network from
remote location. The router is configures with tunneling and encryption protocol and it provides
benefit for the wide area network. The router is configured with ACL (Access Control List) for
limiting the access of the resource and adding permission to the authorized staffs for the
development of the network. Active directory is required to be configured on the server and best
practice is required to be followed for the management of the group policy in the network. The
occupational and the safety of the devices are required to be developed for the development of
the network. The network is design by eliminating the risk and hazards associated with the
network and proper ventilation and air conditioning is required to be installed get the best
performance from the devices used in the network. The installation of rack cabinet would help to
IT NETWORKING DESIGNING
2.2. Implementation of Active Directory Service
Emerging technology can be used for increasing the efficiency of the network and
configuration of the active directory in the server used in the network would help in managing
the network from a single point. The virtualization of the server helps in sharing of the resources
and thus reduces the extra hardware cost. The main sources of the internet is protected with the
installation of the firewall and appropriate authentication is used for protecting the data center
and privacy of the organizational data. A DNS model is adopted for the configuration of the
server and the network development team works on mixed mode for the implementation of the
active directory. A central router connects the data center and the other routers installed at
different floors of the building. A subnet is created for each of the floor and the devices in the
network are provided with the IP address for connecting in the network. The central router is
configured with VPN and it is used by the user to send and receive data in the public and the
shared network. The VPN is used for securing the intranet and access the office network from
remote location. The router is configures with tunneling and encryption protocol and it provides
benefit for the wide area network. The router is configured with ACL (Access Control List) for
limiting the access of the resource and adding permission to the authorized staffs for the
development of the network. Active directory is required to be configured on the server and best
practice is required to be followed for the management of the group policy in the network. The
occupational and the safety of the devices are required to be developed for the development of
the network. The network is design by eliminating the risk and hazards associated with the
network and proper ventilation and air conditioning is required to be installed get the best
performance from the devices used in the network. The installation of rack cabinet would help to

5
IT NETWORKING DESIGNING
save space in the workplace and a power management is also essential for avoiding situation of
network downtime.
3. Identification of the service and the Server
There are different servers required to be installed for the management of the network
and the data center is required to be managed for the identification of the server and the service.
Web server: The web server is required to be installed in the floor for the management of
the information system and it comes as a package of the internet and the intranet related
program. The server side programming is required to be done for optimization of the interface
used for connecting the data center.
Mail Server: A mail server is configured for the management of the email account of the
user and the various staffs need to communicate via the email server installed in organizational
network. The deployment of the mail server in the organizational network helps to keep the
records of the employees and helps in easy management.
File Server: The file server is used for storing the various files and folders and fetch them
when required. The access of the file server is required to be limited and write permission should
not be provided to the reducing the risk of data loss
4. Allocation of the IP address and subnet masking
The IP address and subnet mask is required to be assigned for each of the routers installed
in the network and they are listed as follows:
Central router- 172.28.0.1/24
Business Router – 172.28.2.1/24
IT NETWORKING DESIGNING
save space in the workplace and a power management is also essential for avoiding situation of
network downtime.
3. Identification of the service and the Server
There are different servers required to be installed for the management of the network
and the data center is required to be managed for the identification of the server and the service.
Web server: The web server is required to be installed in the floor for the management of
the information system and it comes as a package of the internet and the intranet related
program. The server side programming is required to be done for optimization of the interface
used for connecting the data center.
Mail Server: A mail server is configured for the management of the email account of the
user and the various staffs need to communicate via the email server installed in organizational
network. The deployment of the mail server in the organizational network helps to keep the
records of the employees and helps in easy management.
File Server: The file server is used for storing the various files and folders and fetch them
when required. The access of the file server is required to be limited and write permission should
not be provided to the reducing the risk of data loss
4. Allocation of the IP address and subnet masking
The IP address and subnet mask is required to be assigned for each of the routers installed
in the network and they are listed as follows:
Central router- 172.28.0.1/24
Business Router – 172.28.2.1/24
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
6
IT NETWORKING DESIGNING
Accounting Router – 172.28.3.1/24
Administrative Router – 172.28.4.1/24
Web Server – 172.28.4.2/24
Mail Server – 192.28.4.3/24
File Server – 172.28.4.4/24
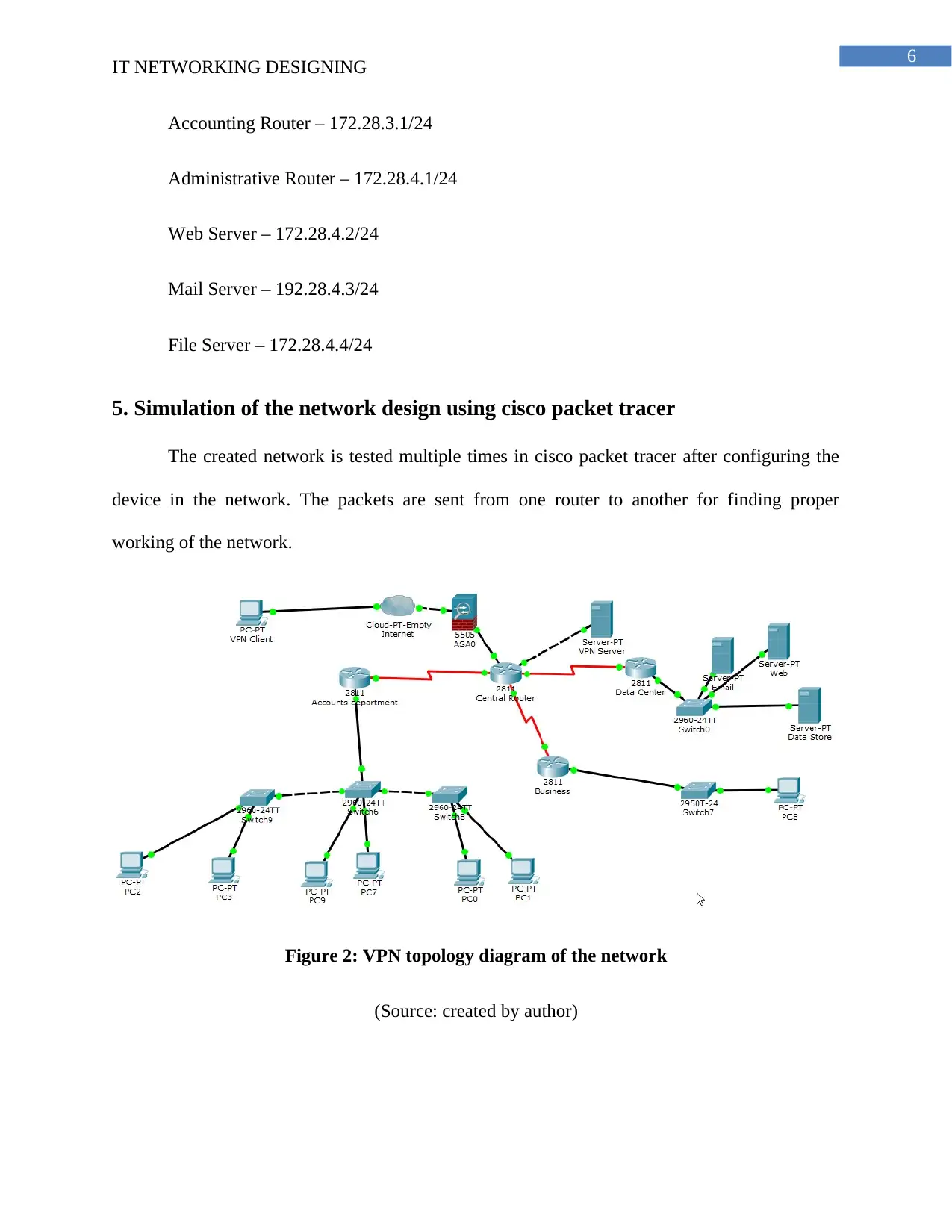
5. Simulation of the network design using cisco packet tracer
The created network is tested multiple times in cisco packet tracer after configuring the
device in the network. The packets are sent from one router to another for finding proper
working of the network.
Figure 2: VPN topology diagram of the network
(Source: created by author)
IT NETWORKING DESIGNING
Accounting Router – 172.28.3.1/24
Administrative Router – 172.28.4.1/24
Web Server – 172.28.4.2/24
Mail Server – 192.28.4.3/24
File Server – 172.28.4.4/24
5. Simulation of the network design using cisco packet tracer
The created network is tested multiple times in cisco packet tracer after configuring the
device in the network. The packets are sent from one router to another for finding proper
working of the network.
Figure 2: VPN topology diagram of the network
(Source: created by author)
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
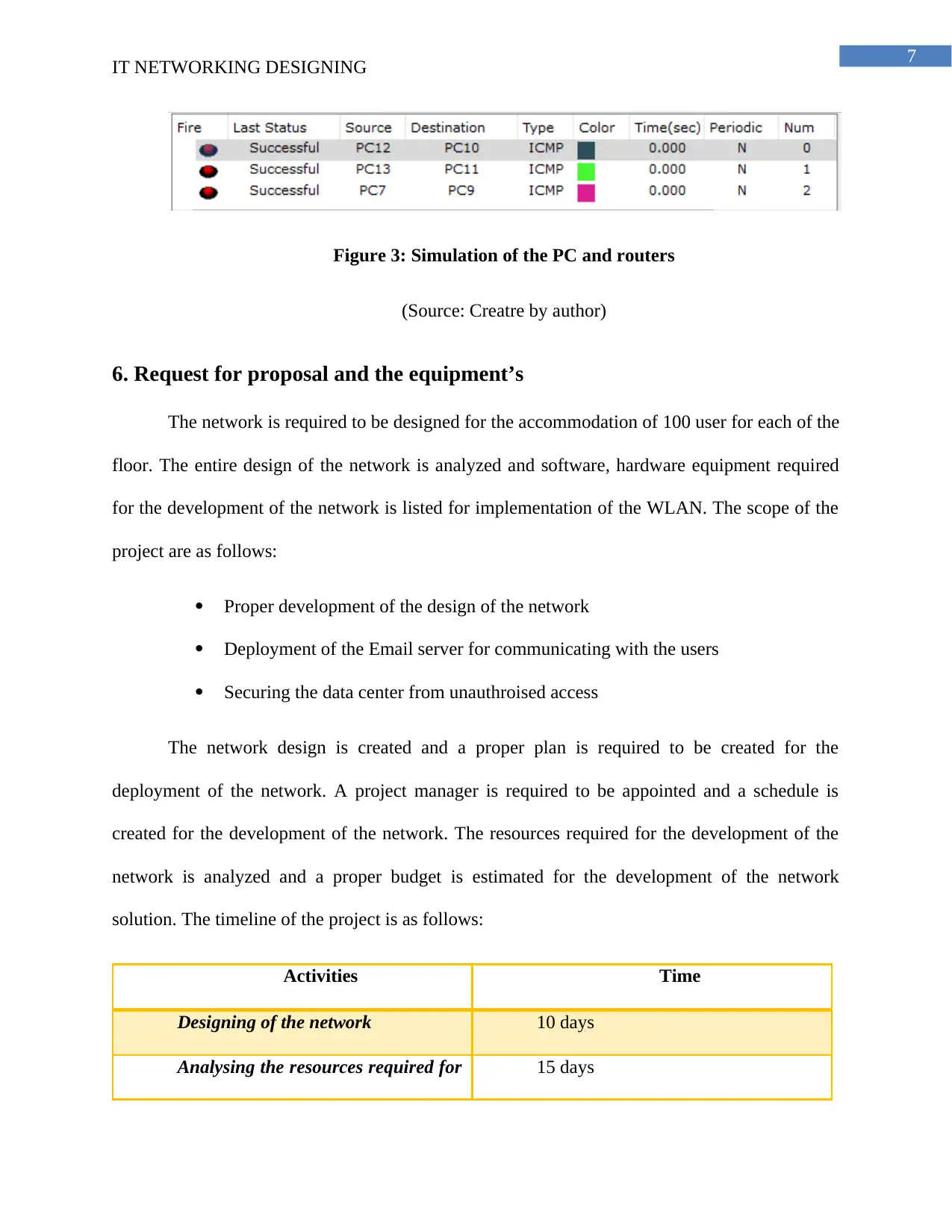
7
IT NETWORKING DESIGNING
Figure 3: Simulation of the PC and routers
(Source: Creatre by author)
6. Request for proposal and the equipment’s
The network is required to be designed for the accommodation of 100 user for each of the
floor. The entire design of the network is analyzed and software, hardware equipment required
for the development of the network is listed for implementation of the WLAN. The scope of the
project are as follows:
Proper development of the design of the network
Deployment of the Email server for communicating with the users
Securing the data center from unauthroised access
The network design is created and a proper plan is required to be created for the
deployment of the network. A project manager is required to be appointed and a schedule is
created for the development of the network. The resources required for the development of the
network is analyzed and a proper budget is estimated for the development of the network
solution. The timeline of the project is as follows:
Activities Time
Designing of the network 10 days
Analysing the resources required for 15 days
IT NETWORKING DESIGNING
Figure 3: Simulation of the PC and routers
(Source: Creatre by author)
6. Request for proposal and the equipment’s
The network is required to be designed for the accommodation of 100 user for each of the
floor. The entire design of the network is analyzed and software, hardware equipment required
for the development of the network is listed for implementation of the WLAN. The scope of the
project are as follows:
Proper development of the design of the network
Deployment of the Email server for communicating with the users
Securing the data center from unauthroised access
The network design is created and a proper plan is required to be created for the
deployment of the network. A project manager is required to be appointed and a schedule is
created for the development of the network. The resources required for the development of the
network is analyzed and a proper budget is estimated for the development of the network
solution. The timeline of the project is as follows:
Activities Time
Designing of the network 10 days
Analysing the resources required for 15 days
8
IT NETWORKING DESIGNING
designing the network
Preparation of the cabling plan 30 days
Creation of the project development
team
15 days
Deployment of the network 10 days
Project Closure 10 days
Different service are required to be embedded like ISP internet service provider, mail
service and web service for the managing the different function of the network.
7. Measures for prevention of security attacks
For maintaining the confidentiality of the network it is required to be secured from
unauthroised access and the network resources such as the routers and the switches is required to
be protected with passwords. The hackers mainly uses the application layer in the network for
gaining access of the resources and for prevention of the attack the firewall is installed at the
entry point and the router is segmented with different security requirements. The security patches
is required to be installed when released by the application vendor for reducing the risk of DoS
attacks or SQL injections. The intranet based application is required to be blocked to use the
internet and the database server is required to be encrypted for protecting the sensitive
information.
8. Summary and conclusion
From the report it can be concluded that for the development of the network solution the
requirement of the organization is required to be analyzed. The different networking devices are
required to be secured with the installation of the firewall and it is required to be configured for
IT NETWORKING DESIGNING
designing the network
Preparation of the cabling plan 30 days
Creation of the project development
team
15 days
Deployment of the network 10 days
Project Closure 10 days
Different service are required to be embedded like ISP internet service provider, mail
service and web service for the managing the different function of the network.
7. Measures for prevention of security attacks
For maintaining the confidentiality of the network it is required to be secured from
unauthroised access and the network resources such as the routers and the switches is required to
be protected with passwords. The hackers mainly uses the application layer in the network for
gaining access of the resources and for prevention of the attack the firewall is installed at the
entry point and the router is segmented with different security requirements. The security patches
is required to be installed when released by the application vendor for reducing the risk of DoS
attacks or SQL injections. The intranet based application is required to be blocked to use the
internet and the database server is required to be encrypted for protecting the sensitive
information.
8. Summary and conclusion
From the report it can be concluded that for the development of the network solution the
requirement of the organization is required to be analyzed. The different networking devices are
required to be secured with the installation of the firewall and it is required to be configured for
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9
IT NETWORKING DESIGNING
securing the network from unauthroised access. The data center designed for the network is
required to be available during the peak time and it is required to be flexible for connecting the
users in the network. An appropriate area is required to be analyzed for using the cable and
connecting the devices getting the maximum performance from the devices. The network cable is
required to be selected for maintaining a balance of the cost of the network for the copper and the
fiber medium. The power supply and other electrical interference is required to be removed for
reducing the risk of signal distortion and loss of data packets.
IT NETWORKING DESIGNING
securing the network from unauthroised access. The data center designed for the network is
required to be available during the peak time and it is required to be flexible for connecting the
users in the network. An appropriate area is required to be analyzed for using the cable and
connecting the devices getting the maximum performance from the devices. The network cable is
required to be selected for maintaining a balance of the cost of the network for the copper and the
fiber medium. The power supply and other electrical interference is required to be removed for
reducing the risk of signal distortion and loss of data packets.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10
IT NETWORKING DESIGNING
Bibliography
Carthern, C., Wilson, W., Bedwell, R., & Rivera, N. (2015). The Network Layer with IP. In
Cisco Networks (pp. 49-68). Apress.
Dowler, P., Demleitner, M., Taylor, M., & Tody, D. (2013). Data access layer interface, version
1.0. IVOA Recommendation. URL: http://www. ivoa. net/documents/DALI.
Jia, Y., Shelhamer, E., Donahue, J., Karayev, S., Long, J., Girshick, R., ... & Darrell, T. (2014,
November). Caffe: Convolutional architecture for fast feature embedding. In Proceedings
of the 22nd ACM international conference on Multimedia (pp. 675-678). ACM.
Kumari, N., Sharma, E. B., & Saini, R. K. (2016). Comparative Study of RIPng and OSPFV3
with IPV6. International Journal, 6(9).
Morgan, W., Tam, R., Gerasimova, N., Gastauer, K., Rasgado, S., Einstein, K., ... & Townsend,
E. (2016). U.S. Patent Application No. 15/361,769.
Sánchez, A., Villarrubia, G., Zato, C., Rodríguez, S. and Chamoso, P., 2013. A gateway protocol
based on FIPA-ACL for the new agent platform PANGEA. In Trends in Practical
Applications of Agents and Multiagent Systems (pp. 41-51). Springer International
Publishing.
Simmons, J. M. (2014). Optical network design and planning. Springer.
Wan, W. and Li, J., 2014, February. Investigation of state division in botnet detection model. In
Advanced Communication Technology (ICACT), 2014 16th International Conference on
(pp. 265-268). IEEE.
IT NETWORKING DESIGNING
Bibliography
Carthern, C., Wilson, W., Bedwell, R., & Rivera, N. (2015). The Network Layer with IP. In
Cisco Networks (pp. 49-68). Apress.
Dowler, P., Demleitner, M., Taylor, M., & Tody, D. (2013). Data access layer interface, version
1.0. IVOA Recommendation. URL: http://www. ivoa. net/documents/DALI.
Jia, Y., Shelhamer, E., Donahue, J., Karayev, S., Long, J., Girshick, R., ... & Darrell, T. (2014,
November). Caffe: Convolutional architecture for fast feature embedding. In Proceedings
of the 22nd ACM international conference on Multimedia (pp. 675-678). ACM.
Kumari, N., Sharma, E. B., & Saini, R. K. (2016). Comparative Study of RIPng and OSPFV3
with IPV6. International Journal, 6(9).
Morgan, W., Tam, R., Gerasimova, N., Gastauer, K., Rasgado, S., Einstein, K., ... & Townsend,
E. (2016). U.S. Patent Application No. 15/361,769.
Sánchez, A., Villarrubia, G., Zato, C., Rodríguez, S. and Chamoso, P., 2013. A gateway protocol
based on FIPA-ACL for the new agent platform PANGEA. In Trends in Practical
Applications of Agents and Multiagent Systems (pp. 41-51). Springer International
Publishing.
Simmons, J. M. (2014). Optical network design and planning. Springer.
Wan, W. and Li, J., 2014, February. Investigation of state division in botnet detection model. In
Advanced Communication Technology (ICACT), 2014 16th International Conference on
(pp. 265-268). IEEE.

11
IT NETWORKING DESIGNING
IT NETWORKING DESIGNING
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 12
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





