IT Networking Design Report: Seraphine Insurance PLC Network Design
VerifiedAdded on 2023/05/28
|22
|4836
|216
Report
AI Summary
This report presents a comprehensive IT networking design for Seraphine Insurance PLC, addressing the company's need to integrate recently acquired companies and reduce operational costs. The design incorporates a hybrid network framework with a site-to-site VPN to securely connect remote branches. The report analyzes network topologies, emphasizing the benefits of a centralized network for improved security, scalability, and reduced costs. It also details bandwidth requirements for various applications, including email, web browsing, and video streaming. The design includes network devices, hardware, and software considerations, along with discussions on the OSI model, VPN technologies (IPSec), and network security measures. Furthermore, the report covers the impact of topology, communication requirements, and configuration considerations to optimize network performance and reliability. The report also contains details on testing, evaluation, and investigation of the designed network's growth capabilities.

Running head: IT NETWORKING DESIGNING
IT Networking Designing
Name of the Student
Name of the University
Author’s Note
IT Networking Designing
Name of the Student
Name of the University
Author’s Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
IT NETWORKING DESIGNING
Table of Contents
Introduction................................................................................................................................2
Benefits and constraints for the different types of network and standards................................2
Impact of the topology...............................................................................................................3
Communication and requirement of bandwidth.........................................................................4
Network device and operations..................................................................................................6
Interdependency between the hardware and the relevant software............................................7
Description if the LAN topology and technology used for the development of the network....7
Network Design Scenario........................................................................................................10
Network Design Diagram........................................................................................................11
Configuration consideration of the network............................................................................13
Distribution policy and technical details..................................................................................14
Network Device and hardware.................................................................................................15
Testing and evaluation of the design........................................................................................16
Test and diagnosis of the network system................................................................................18
Investigation for analysing the ability of growth of the network.............................................18
Conclusion................................................................................................................................18
Bibliography.............................................................................................................................20
IT NETWORKING DESIGNING
Table of Contents
Introduction................................................................................................................................2
Benefits and constraints for the different types of network and standards................................2
Impact of the topology...............................................................................................................3
Communication and requirement of bandwidth.........................................................................4
Network device and operations..................................................................................................6
Interdependency between the hardware and the relevant software............................................7
Description if the LAN topology and technology used for the development of the network....7
Network Design Scenario........................................................................................................10
Network Design Diagram........................................................................................................11
Configuration consideration of the network............................................................................13
Distribution policy and technical details..................................................................................14
Network Device and hardware.................................................................................................15
Testing and evaluation of the design........................................................................................16
Test and diagnosis of the network system................................................................................18
Investigation for analysing the ability of growth of the network.............................................18
Conclusion................................................................................................................................18
Bibliography.............................................................................................................................20

2
IT NETWORKING DESIGNING
Introduction
The report is prepared for Seraphine Insurance PLC for the development of a network
design for securing the communication between the different departments and users
connected in the network. For the development of the network solution different
organizational network framework is analysed and a high level network design is created
with the application of different technologies that are capable of solving real life problems.
The organization have a requirement of expanding the business and reach more number of
customer and reduce the operation cost of the business. The company purchased three small
insurance companies and the companies infrastructure is needed to be combined with
Seraphines’s framework for operating from a single place.
Benefits and constraints for the different types of network and standards
It is important to select an appropriate network topology depending on the needs of
the organization and develop an appropriate network structure for connecting the different
branches with each other. The router is needed to be configured with access control list for
preventing the access of the unauthorised users to connect with the servers containing
sensitive organizational information. The benefits and risk of selection of the topology is
needed to be analysed for its implementation in the current network and development of the
physical and logical network framework. The LAN is used for interconnecting the network
device of the branches and enabling short distance communication in the building. The
WAN is used for connecting the branches with each other and multiple LANs for enabling
communication between the different local area network. Different technologies are used
such as frame relay, ATM for creating a secure network connection between the hosts
connected in different location of the network. There are different other networks that can
IT NETWORKING DESIGNING
Introduction
The report is prepared for Seraphine Insurance PLC for the development of a network
design for securing the communication between the different departments and users
connected in the network. For the development of the network solution different
organizational network framework is analysed and a high level network design is created
with the application of different technologies that are capable of solving real life problems.
The organization have a requirement of expanding the business and reach more number of
customer and reduce the operation cost of the business. The company purchased three small
insurance companies and the companies infrastructure is needed to be combined with
Seraphines’s framework for operating from a single place.
Benefits and constraints for the different types of network and standards
It is important to select an appropriate network topology depending on the needs of
the organization and develop an appropriate network structure for connecting the different
branches with each other. The router is needed to be configured with access control list for
preventing the access of the unauthorised users to connect with the servers containing
sensitive organizational information. The benefits and risk of selection of the topology is
needed to be analysed for its implementation in the current network and development of the
physical and logical network framework. The LAN is used for interconnecting the network
device of the branches and enabling short distance communication in the building. The
WAN is used for connecting the branches with each other and multiple LANs for enabling
communication between the different local area network. Different technologies are used
such as frame relay, ATM for creating a secure network connection between the hosts
connected in different location of the network. There are different other networks that can
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3
IT NETWORKING DESIGNING
also be used for long distance communication such as metropolitan area network, campus
area network that can be used for connecting the data centre with a high speed link.
Impact of the topology
The efficiency of the network and its operation depends on the selection of the right
topology and proper cabling plan for interconnecting the network devices. The types of
network cable needed to connect the hardware device with each other should be identified for
utilizing the available bandwidth and reducing the risk of congestion in the network. A
centralized network topology is needed such that the communication is done via a central
server and storing the records of communication and the accounts of the user for
improvement of security of the network. The selection of the centralized management of the
network also helps in reducing the errors and increases the reliability of the network. It helps
in enforcing a control on the network and eliminates the extra cost that is needed for
deployment of duplicate device in each of the sites for management of the service. The
network can be upgraded by upgrading the centralized server and the devices and there in no
need to replace all the old system installed in the local sites. The scalability of the network
can be improved and new sites can be added or removed according to the requirement of the
organization for the management of the network framework.
High speed link should be used for connecting the sites with the centralized server
such that the response time is minimum and the performance of the network is higher. The
loads and the request of the user should be handled with the application of virtualization of
the server and installation of load balancer for dividing the traffic with the physical and
virtual server for increasing the capacity of the server. The virtualization of the server helps
in full utilization of the resource and increasing reliability of the network. Th load balancer
IT NETWORKING DESIGNING
also be used for long distance communication such as metropolitan area network, campus
area network that can be used for connecting the data centre with a high speed link.
Impact of the topology
The efficiency of the network and its operation depends on the selection of the right
topology and proper cabling plan for interconnecting the network devices. The types of
network cable needed to connect the hardware device with each other should be identified for
utilizing the available bandwidth and reducing the risk of congestion in the network. A
centralized network topology is needed such that the communication is done via a central
server and storing the records of communication and the accounts of the user for
improvement of security of the network. The selection of the centralized management of the
network also helps in reducing the errors and increases the reliability of the network. It helps
in enforcing a control on the network and eliminates the extra cost that is needed for
deployment of duplicate device in each of the sites for management of the service. The
network can be upgraded by upgrading the centralized server and the devices and there in no
need to replace all the old system installed in the local sites. The scalability of the network
can be improved and new sites can be added or removed according to the requirement of the
organization for the management of the network framework.
High speed link should be used for connecting the sites with the centralized server
such that the response time is minimum and the performance of the network is higher. The
loads and the request of the user should be handled with the application of virtualization of
the server and installation of load balancer for dividing the traffic with the physical and
virtual server for increasing the capacity of the server. The virtualization of the server helps
in full utilization of the resource and increasing reliability of the network. Th load balancer
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4
IT NETWORKING DESIGNING
helps in equal distribution of the workload and utilization of the processor and the memory
for maximizing the throughput and minimizing the response time of the server.
Communication and requirement of bandwidth
The network capacity is needed to be estimated for the allocation of sufficient
bandwidth and distribution of the channel for increasing the rate of transfer of data. The rate
of data transfer is dependent on the available bandwidth and reducing the latency for
eliminating the lags in the network. The lags in the network is needed to be identified for
increasing the network efficiency and management of the communication service needed by
the organization for running their business efficiently.
Application Bandwidth Required Note
Email 10 – 100 Kbps The emails are sent in
asynchronous manner and it
can tolerate a little bit of
latency in the network.
Sufficient bandwidth is
needed for the large
attachment and file sharing.
Messaging < 10 Kbps It is infrequent and thus can
tolerate latency of the
network.
Web Browsing 128 – 256 + Kbps It is dependent on the type of
the web site or web
application used by the user
IT NETWORKING DESIGNING
helps in equal distribution of the workload and utilization of the processor and the memory
for maximizing the throughput and minimizing the response time of the server.
Communication and requirement of bandwidth
The network capacity is needed to be estimated for the allocation of sufficient
bandwidth and distribution of the channel for increasing the rate of transfer of data. The rate
of data transfer is dependent on the available bandwidth and reducing the latency for
eliminating the lags in the network. The lags in the network is needed to be identified for
increasing the network efficiency and management of the communication service needed by
the organization for running their business efficiently.
Application Bandwidth Required Note
Email 10 – 100 Kbps The emails are sent in
asynchronous manner and it
can tolerate a little bit of
latency in the network.
Sufficient bandwidth is
needed for the large
attachment and file sharing.
Messaging < 10 Kbps It is infrequent and thus can
tolerate latency of the
network.
Web Browsing 128 – 256 + Kbps It is dependent on the type of
the web site or web
application used by the user
5
IT NETWORKING DESIGNING
and the fair lag can be
tolerated and there is an
increase in the requirement
of bandwidth if the request
of the user increases.
Audio Streaming 96 -160 Kbps It is needed for streaming
voice message and the lag in
the network can cause
buffering and thus the
latency should be eliminated
for reducing the risk of
outrage of the session.
VOIP 24 – 100+ Kbps It is needed for the VOIP
service and no lags can be
tolerated because it causes
drop in the call and not clear
voice. The lag can cause mis
communication and thus
separate channel should be
used for transmission of the
voice packets in the network.
Video Streaming 96 – 200+ Kbps The latency is needed to be
avoided for getting the
maximum throughput and
IT NETWORKING DESIGNING
and the fair lag can be
tolerated and there is an
increase in the requirement
of bandwidth if the request
of the user increases.
Audio Streaming 96 -160 Kbps It is needed for streaming
voice message and the lag in
the network can cause
buffering and thus the
latency should be eliminated
for reducing the risk of
outrage of the session.
VOIP 24 – 100+ Kbps It is needed for the VOIP
service and no lags can be
tolerated because it causes
drop in the call and not clear
voice. The lag can cause mis
communication and thus
separate channel should be
used for transmission of the
voice packets in the network.
Video Streaming 96 – 200+ Kbps The latency is needed to be
avoided for getting the
maximum throughput and
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
6
IT NETWORKING DESIGNING
the buffer size should be
increased for proper
streaming of the video.
File Sharing 0 – infinity Mbps Sufficient bandwidth should
be available for transferring
large files over the network
and p2p protocol should be
used for increasing the
transmission speed.
The total bandwidth requirement is calculate by analysing the application and service
used by the user multiplying them by the number of user using the application or service.
Network device and operations
For interconnecting the different offices and their branches with the Seraphine
headquarter different types of network device and technology is needed that should be
connected with the means of different cabling option for successfully transmit the data from
the source to the destination address in the network. The different layers of the OSI model is
utilized for establishment of secure communication between the source and the destination
address. The end device is connected with the switch for enabling communication between
the sender and receiver in the network. The selection of the VPN for communicating with the
remote site helps in reducing the cost of communication and maintenance. The data can be
send securely via the encrypted channels and reduces the risk of man in the middle attack and
improves the security of the network. Traffic filtering is also applied on the router for
dropping the unknown packets and restrict them to reach the internal network of the
organization. The head office is installed with different types of servers for the management
IT NETWORKING DESIGNING
the buffer size should be
increased for proper
streaming of the video.
File Sharing 0 – infinity Mbps Sufficient bandwidth should
be available for transferring
large files over the network
and p2p protocol should be
used for increasing the
transmission speed.
The total bandwidth requirement is calculate by analysing the application and service
used by the user multiplying them by the number of user using the application or service.
Network device and operations
For interconnecting the different offices and their branches with the Seraphine
headquarter different types of network device and technology is needed that should be
connected with the means of different cabling option for successfully transmit the data from
the source to the destination address in the network. The different layers of the OSI model is
utilized for establishment of secure communication between the source and the destination
address. The end device is connected with the switch for enabling communication between
the sender and receiver in the network. The selection of the VPN for communicating with the
remote site helps in reducing the cost of communication and maintenance. The data can be
send securely via the encrypted channels and reduces the risk of man in the middle attack and
improves the security of the network. Traffic filtering is also applied on the router for
dropping the unknown packets and restrict them to reach the internal network of the
organization. The head office is installed with different types of servers for the management
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7
IT NETWORKING DESIGNING
of the different service needed for running the business and increase the performance of the
network. The access to the servers is needed to be controlled for the users such that sensitive
information residing in the file servers cannot be accessed for illegal use.
Interdependency between the hardware and the relevant software
The workstation installed in the different location of the organizational network
should meet the minimum hardware specification such that different application can be
installed for the management of service provided to the users. The networking software are
used for monitoring the flow of data traffic in the network and maintaining a control on the
transmission data packets from different location in the network. The network interface of the
workstation is needed to be configured with IP address and the default gateway for enabling
communication with the other users connected in the network. The servers installed in the
network should be installed with proper network operating system such that entire network
can be managed. The workstation should support the virtualization such that if there is an
increase in the load on the network the servers can be virtualized for handling more number
of request and reduce the waiting time of the user. The design phase should be analysed for
implementation of the security measures and analysing the vulnerabilities on the network.
The users should be given proper training such that the hackers does not have access to the
organizational data and the unforeseen vulnerabilities are eliminated.
Description if the LAN topology and technology used for the development
of the network
For the development of the network framework a hybrid network framework is
created and a VPN server is used for connecting the remote branches using the site to site
VPN approach. It uses a public network for the establishment of the connection and the
network is intranet based as the company have the requirement of connecting all the remote
IT NETWORKING DESIGNING
of the different service needed for running the business and increase the performance of the
network. The access to the servers is needed to be controlled for the users such that sensitive
information residing in the file servers cannot be accessed for illegal use.
Interdependency between the hardware and the relevant software
The workstation installed in the different location of the organizational network
should meet the minimum hardware specification such that different application can be
installed for the management of service provided to the users. The networking software are
used for monitoring the flow of data traffic in the network and maintaining a control on the
transmission data packets from different location in the network. The network interface of the
workstation is needed to be configured with IP address and the default gateway for enabling
communication with the other users connected in the network. The servers installed in the
network should be installed with proper network operating system such that entire network
can be managed. The workstation should support the virtualization such that if there is an
increase in the load on the network the servers can be virtualized for handling more number
of request and reduce the waiting time of the user. The design phase should be analysed for
implementation of the security measures and analysing the vulnerabilities on the network.
The users should be given proper training such that the hackers does not have access to the
organizational data and the unforeseen vulnerabilities are eliminated.
Description if the LAN topology and technology used for the development
of the network
For the development of the network framework a hybrid network framework is
created and a VPN server is used for connecting the remote branches using the site to site
VPN approach. It uses a public network for the establishment of the connection and the
network is intranet based as the company have the requirement of connecting all the remote

8
IT NETWORKING DESIGNING
branches and work as a single private network. An intranet VPN is created for connecting the
local area network of each of the branch to form a single wide area network. The site to site
VPN is selected since it does not needs each of the client connected in the network to use the
vpn software to connect with the remote host. In the site to site VPN a tunnel is used for
encapsulating the data packets and forwarding it over IP based networks. Encryption is
applied for ensuring authentication and privacy such that integrity of the data packets are
maintained. IPSec security policy is used for defining the characteristics of the site to site vpn
for the management of the security of the data traffic flowing in the network. Different types
of policies are required for configuration of the network framework and it is dependent on the
type of the IPSec technology. The types of IPSec consists of GRE Dynamic IP, Regular
IPSec, GET VPN, large scale DMVPN, etc. There are some mandatory and optional IPSec
technologies and policies available for site to site VPN that are needed to be applied for the
development of the network.
Technology Optional Policies Mandatory Policies
Regular IPSec
IPSec/GRE
VPN Global settings
VPN Global settings
IPSec proposal
IKE Proposal
If IKEv1 allowed,
one IKEv1 preshared
key / IKEv1 Public
key framework
If IKEv2 allowed,
authentication of
IKEv2
Proposal of IKE
IT NETWORKING DESIGNING
branches and work as a single private network. An intranet VPN is created for connecting the
local area network of each of the branch to form a single wide area network. The site to site
VPN is selected since it does not needs each of the client connected in the network to use the
vpn software to connect with the remote host. In the site to site VPN a tunnel is used for
encapsulating the data packets and forwarding it over IP based networks. Encryption is
applied for ensuring authentication and privacy such that integrity of the data packets are
maintained. IPSec security policy is used for defining the characteristics of the site to site vpn
for the management of the security of the data traffic flowing in the network. Different types
of policies are required for configuration of the network framework and it is dependent on the
type of the IPSec technology. The types of IPSec consists of GRE Dynamic IP, Regular
IPSec, GET VPN, large scale DMVPN, etc. There are some mandatory and optional IPSec
technologies and policies available for site to site VPN that are needed to be applied for the
development of the network.
Technology Optional Policies Mandatory Policies
Regular IPSec
IPSec/GRE
VPN Global settings
VPN Global settings
IPSec proposal
IKE Proposal
If IKEv1 allowed,
one IKEv1 preshared
key / IKEv1 Public
key framework
If IKEv2 allowed,
authentication of
IKEv2
Proposal of IKE
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
9
IT NETWORKING DESIGNING
Dynamic Multipoint VPN
Large Scale DMVPN
Easy VPN
VPN Global settings
VPN Global settings
VPN Global settings
IKEv1 Public key
framework
Proposal of IPSec
one IKEv1 preshared
key / IKEv1 Public
key framework
Generic Routing
Encapsulation
Modes
Proposal of IKE
Proposal of IPSec
one IKEv1 preshared
key / IKEv1 Public
key framework
Generic Routing
Encapsulation
Modes
Proposal of IKE
Proposal of IPSec
one IKEv1 preshared
key / IKEv1 Public
key framework
Generic Routing
Encapsulation
Modes
Load balance for
IT NETWORKING DESIGNING
Dynamic Multipoint VPN
Large Scale DMVPN
Easy VPN
VPN Global settings
VPN Global settings
VPN Global settings
IKEv1 Public key
framework
Proposal of IPSec
one IKEv1 preshared
key / IKEv1 Public
key framework
Generic Routing
Encapsulation
Modes
Proposal of IKE
Proposal of IPSec
one IKEv1 preshared
key / IKEv1 Public
key framework
Generic Routing
Encapsulation
Modes
Proposal of IKE
Proposal of IPSec
one IKEv1 preshared
key / IKEv1 Public
key framework
Generic Routing
Encapsulation
Modes
Load balance for
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10
IT NETWORKING DESIGNING
GET VPN
Global Settings for GET
VPN
servers
Proposal of IKE
IPSec proposal for
easy VPN
Characteristics of
client connection
User group for IOS
server
Connection profiles
for ASA servers
IKE Proposal for
GET VPN
Group Encryption
one IKEv1 preshared
key / IKEv1 Public
key framework
Network Design Scenario
The network is designed for Seraphine insurance Plc for interconnecting its 35
branches with each other following the different requirement of each of the branches. For the
development of the network solution the network is divided into subnets allocating 200 IP
address for each of the branch such that it can accommodate the future growth of the
organization. An wireless access point is also installed for each of the branches such that the
employees can connect their wireless device for transferring of files and information. A
IT NETWORKING DESIGNING
GET VPN
Global Settings for GET
VPN
servers
Proposal of IKE
IPSec proposal for
easy VPN
Characteristics of
client connection
User group for IOS
server
Connection profiles
for ASA servers
IKE Proposal for
GET VPN
Group Encryption
one IKEv1 preshared
key / IKEv1 Public
key framework
Network Design Scenario
The network is designed for Seraphine insurance Plc for interconnecting its 35
branches with each other following the different requirement of each of the branches. For the
development of the network solution the network is divided into subnets allocating 200 IP
address for each of the branch such that it can accommodate the future growth of the
organization. An wireless access point is also installed for each of the branches such that the
employees can connect their wireless device for transferring of files and information. A
11
IT NETWORKING DESIGNING
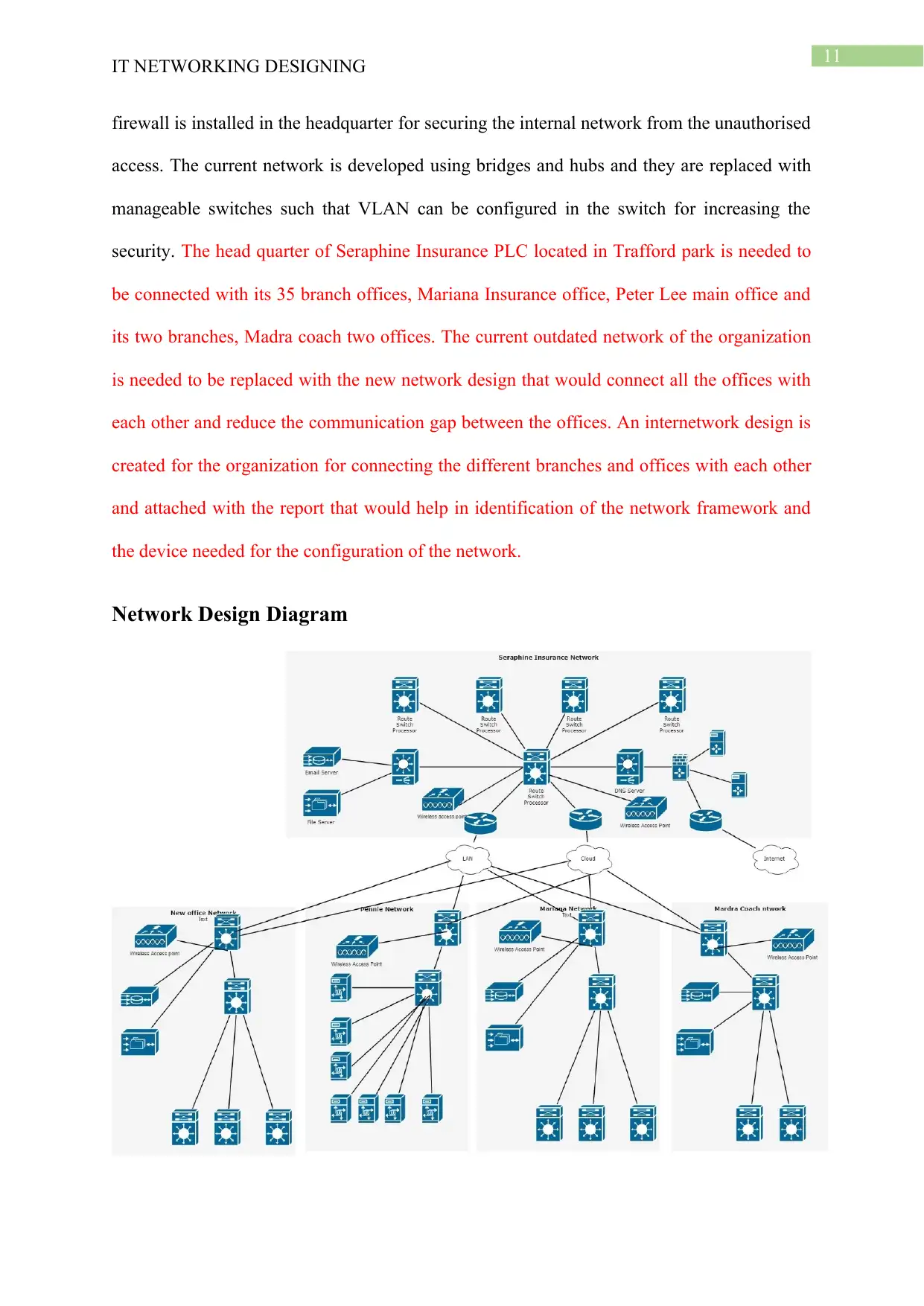
firewall is installed in the headquarter for securing the internal network from the unauthorised
access. The current network is developed using bridges and hubs and they are replaced with
manageable switches such that VLAN can be configured in the switch for increasing the
security. The head quarter of Seraphine Insurance PLC located in Trafford park is needed to
be connected with its 35 branch offices, Mariana Insurance office, Peter Lee main office and
its two branches, Madra coach two offices. The current outdated network of the organization
is needed to be replaced with the new network design that would connect all the offices with
each other and reduce the communication gap between the offices. An internetwork design is
created for the organization for connecting the different branches and offices with each other
and attached with the report that would help in identification of the network framework and
the device needed for the configuration of the network.
Network Design Diagram
IT NETWORKING DESIGNING
firewall is installed in the headquarter for securing the internal network from the unauthorised
access. The current network is developed using bridges and hubs and they are replaced with
manageable switches such that VLAN can be configured in the switch for increasing the
security. The head quarter of Seraphine Insurance PLC located in Trafford park is needed to
be connected with its 35 branch offices, Mariana Insurance office, Peter Lee main office and
its two branches, Madra coach two offices. The current outdated network of the organization
is needed to be replaced with the new network design that would connect all the offices with
each other and reduce the communication gap between the offices. An internetwork design is
created for the organization for connecting the different branches and offices with each other
and attached with the report that would help in identification of the network framework and
the device needed for the configuration of the network.
Network Design Diagram
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 22
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





