IT Network Security Assignment - Windows, Linux, and System Security
VerifiedAdded on 2022/12/27
|32
|3402
|75
Homework Assignment
AI Summary
This IT Network Security assignment explores various aspects of securing computer systems and networks, with a particular focus on operating systems such as Windows 10 and Linux. The document details the importance of selecting the appropriate operating system based on workplace requirements, including business and educational needs. It covers essential topics like data migration, the role of network administrators, desktop applications, and the installation processes of operating systems. Furthermore, the assignment discusses file systems, software licensing, and data security measures. It provides step-by-step guides for installing Windows and Linux, along with security procedures for staff and students. The document also touches upon network configuration, backup and restore facilities, IP addresses, patches, and diagnostic tools. It emphasizes the significance of firewalls, IDS, and IPS systems in protecting networks from cyber threats. The assignment concludes with a discussion of the boot process, BIOS, and essential hardware components required for operating system installation, alongside an overview of security principals and access control.
Running Head: IT Network Security 0
IT network Security
Individual task
Student name
IT network Security
Individual task
Student name
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

IT Network Security 1
Table of Contents
Part A...........................................................................................................................................................1
Part B...........................................................................................................................................................1
Part C...........................................................................................................................................................1
References...................................................................................................................................................1
Table of Contents
Part A...........................................................................................................................................................1
Part B...........................................................................................................................................................1
Part C...........................................................................................................................................................1
References...................................................................................................................................................1

IT Network Security 2
Part A
1. There are different types of operating systems are available in the market, such as windows, Linux,
Mac, and many others. In addition, it is necessary to install a properly operating system based on
the requirements.
1) Windows 10 S is the best operating system for the workplace, as it requires operating systems for
two purposes, which are education and business (Fisher , 2018). It provides both facilities for the
workplace. The workplace can install different business software for managing different business
processes, such as word processing, payroll management, accounting, and many other types of
software.
2) In the present era, both Windows and Linux operating systems are used. It is necessary to
implement the latest operating system in a computer system to secure them from a different type of
cyber-attacks. In the present situation, the Windows operating system is used and now for staff
members, the university should use windows 10 S operating system because it can manage both
things, which are enterprise and education.
3) Data migration is a risky task because it affects different issues. University should implement
security requirements. Staff members can do different works, which can be related to education and
business purposes as well, such as admission, examination, data analysis, and many others.
2. Network Administrator can provide desktop applications, such as word processing, audio and video
player, browsers, image viewer, network management software, pdf viewer, antivirus, and many others.
Word processing applications are highly used in daily purposes by a user in a computer system for
reporting and other things. Microsoft provides a full version of Microsoft office 2016 including word,
excel, PowerPoint, access, and many others.
3. The installation process takes more than 2 hours for a single system and other software take
individual time in installation. It is necessary to install all the software for different work. There are
different methods for installing the operating system, which are USB drive, CD/DVD drive, network, and
many others. In addition, access control is necessary for securing a computer system form attackers. In
addition, there are many other things, which make effects on the processing of sites. However, a single
operating system takes a minimum two hours for the installation process including desktop application.
Part A
1. There are different types of operating systems are available in the market, such as windows, Linux,
Mac, and many others. In addition, it is necessary to install a properly operating system based on
the requirements.
1) Windows 10 S is the best operating system for the workplace, as it requires operating systems for
two purposes, which are education and business (Fisher , 2018). It provides both facilities for the
workplace. The workplace can install different business software for managing different business
processes, such as word processing, payroll management, accounting, and many other types of
software.
2) In the present era, both Windows and Linux operating systems are used. It is necessary to
implement the latest operating system in a computer system to secure them from a different type of
cyber-attacks. In the present situation, the Windows operating system is used and now for staff
members, the university should use windows 10 S operating system because it can manage both
things, which are enterprise and education.
3) Data migration is a risky task because it affects different issues. University should implement
security requirements. Staff members can do different works, which can be related to education and
business purposes as well, such as admission, examination, data analysis, and many others.
2. Network Administrator can provide desktop applications, such as word processing, audio and video
player, browsers, image viewer, network management software, pdf viewer, antivirus, and many others.
Word processing applications are highly used in daily purposes by a user in a computer system for
reporting and other things. Microsoft provides a full version of Microsoft office 2016 including word,
excel, PowerPoint, access, and many others.
3. The installation process takes more than 2 hours for a single system and other software take
individual time in installation. It is necessary to install all the software for different work. There are
different methods for installing the operating system, which are USB drive, CD/DVD drive, network, and
many others. In addition, access control is necessary for securing a computer system form attackers. In
addition, there are many other things, which make effects on the processing of sites. However, a single
operating system takes a minimum two hours for the installation process including desktop application.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

IT Network Security 3
There are many desktop applications, which are necessary for the user, such as pdf reader, word
processing, and utility software.
Part B
4. It is necessary to define proper file systems in installation time. In the case of Windows operating
system, NTFS is used for primary and logical volumes. Primary volumes should have proper space for all
the applications, such as Master Boot Record (MBR), Primary drive should have proper space, such as
200GB for operating systems and different desktop application software, such as word processing,
antivirus, and many others.
5. There are many licenses are available in the market application software. It is necessary to use
properly licensed software in the university rather than pirated software. It makes a huge impact on the
performance and reputation of the university ( Walli, 2013).
6. Data security is necessary for a system because data and information are so important in a university.
Data migration include different things, which are selecting data, preparing, extracting, and tan forming
from one storage to another storage. It is necessary to check the complete system before connecting
with the main network. Data is important from different points of views, such as confidential data,
sensitive data, and personal information.
Part C
7. Operating system 1 (Windows 10)
Step 1: insert the booting media in the computer system:
There are many desktop applications, which are necessary for the user, such as pdf reader, word
processing, and utility software.
Part B
4. It is necessary to define proper file systems in installation time. In the case of Windows operating
system, NTFS is used for primary and logical volumes. Primary volumes should have proper space for all
the applications, such as Master Boot Record (MBR), Primary drive should have proper space, such as
200GB for operating systems and different desktop application software, such as word processing,
antivirus, and many others.
5. There are many licenses are available in the market application software. It is necessary to use
properly licensed software in the university rather than pirated software. It makes a huge impact on the
performance and reputation of the university ( Walli, 2013).
6. Data security is necessary for a system because data and information are so important in a university.
Data migration include different things, which are selecting data, preparing, extracting, and tan forming
from one storage to another storage. It is necessary to check the complete system before connecting
with the main network. Data is important from different points of views, such as confidential data,
sensitive data, and personal information.
Part C
7. Operating system 1 (Windows 10)
Step 1: insert the booting media in the computer system:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
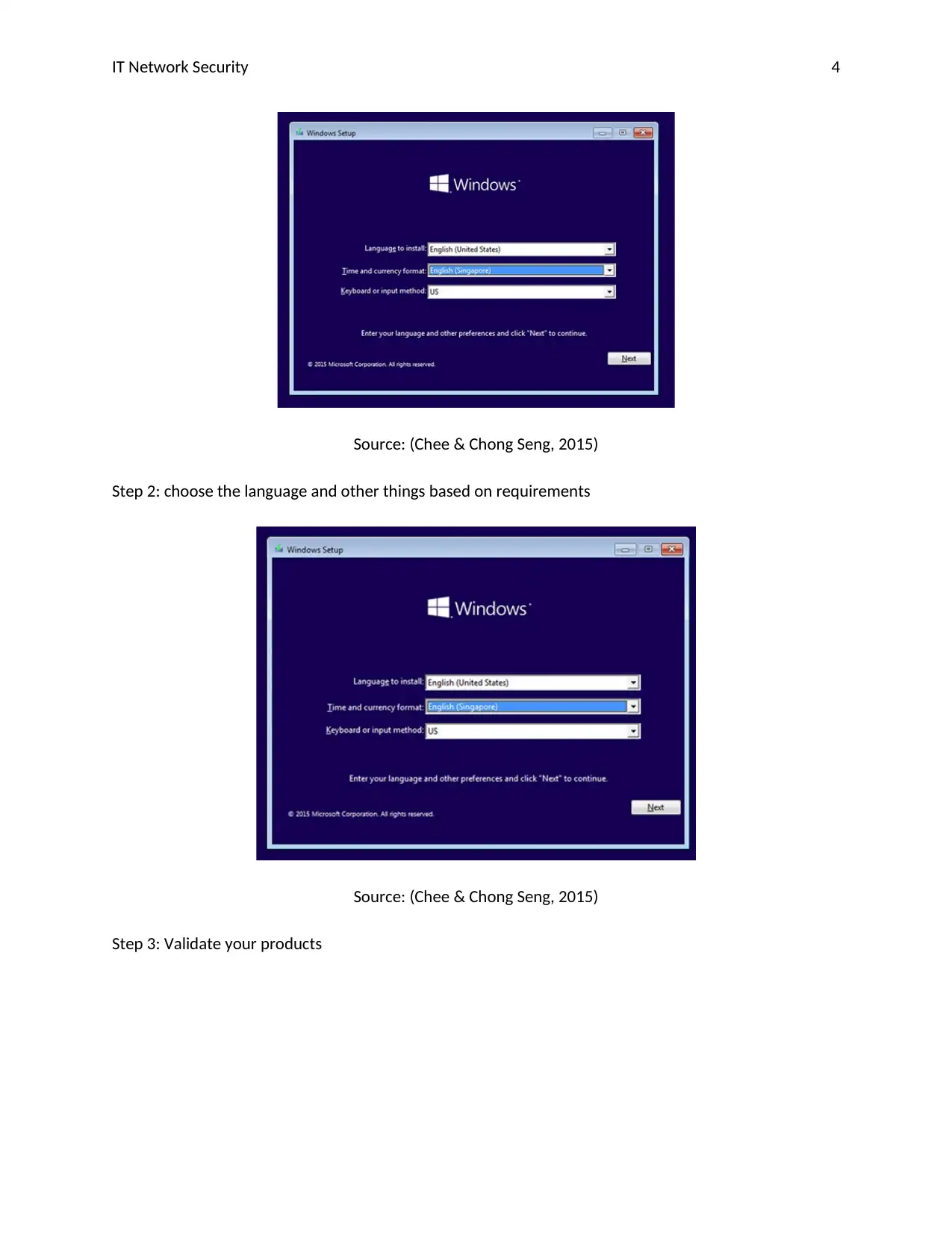
IT Network Security 4
Source: (Chee & Chong Seng, 2015)
Step 2: choose the language and other things based on requirements
Source: (Chee & Chong Seng, 2015)
Step 3: Validate your products
Source: (Chee & Chong Seng, 2015)
Step 2: choose the language and other things based on requirements
Source: (Chee & Chong Seng, 2015)
Step 3: Validate your products
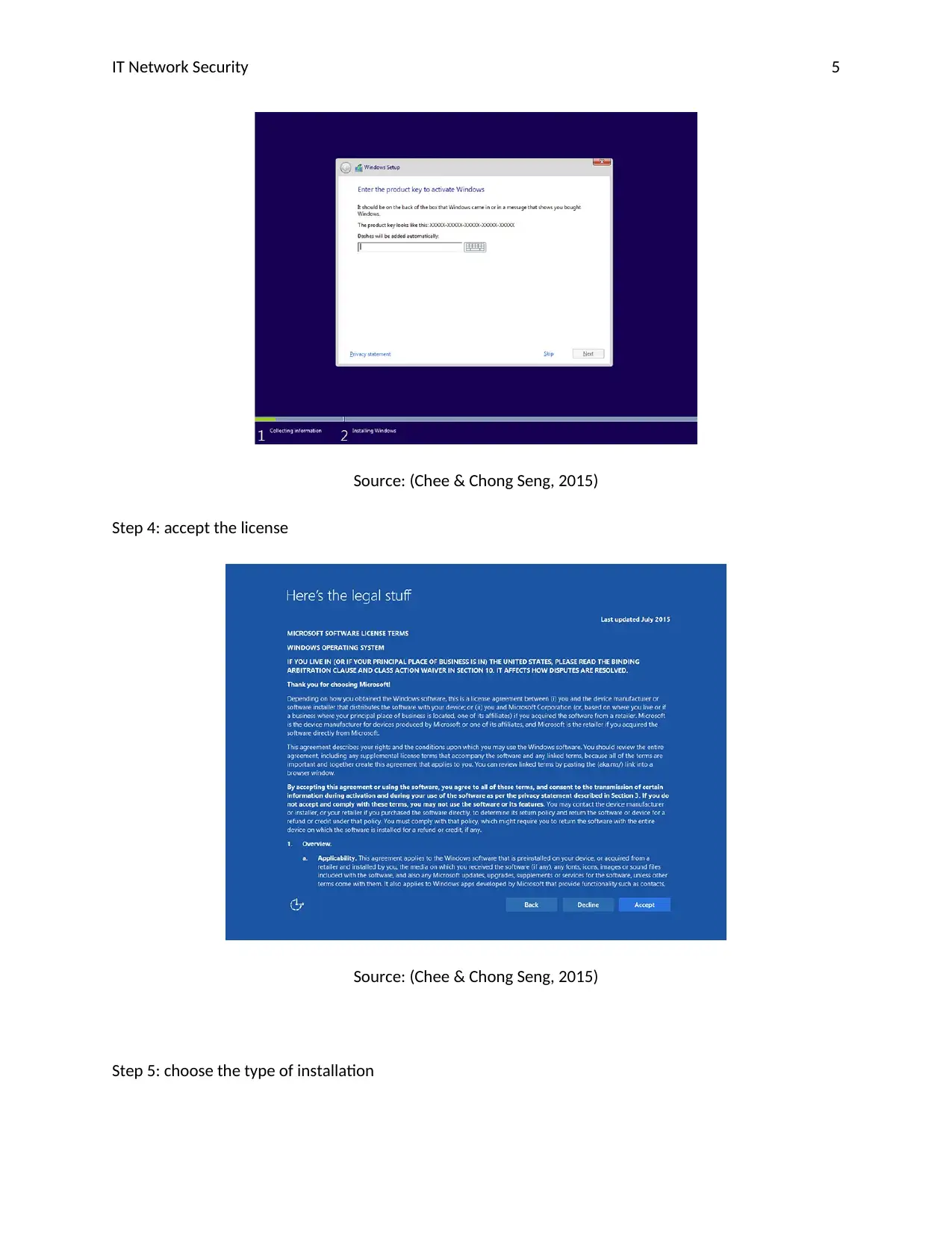
IT Network Security 5
Source: (Chee & Chong Seng, 2015)
Step 4: accept the license
Source: (Chee & Chong Seng, 2015)
Step 5: choose the type of installation
Source: (Chee & Chong Seng, 2015)
Step 4: accept the license
Source: (Chee & Chong Seng, 2015)
Step 5: choose the type of installation
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
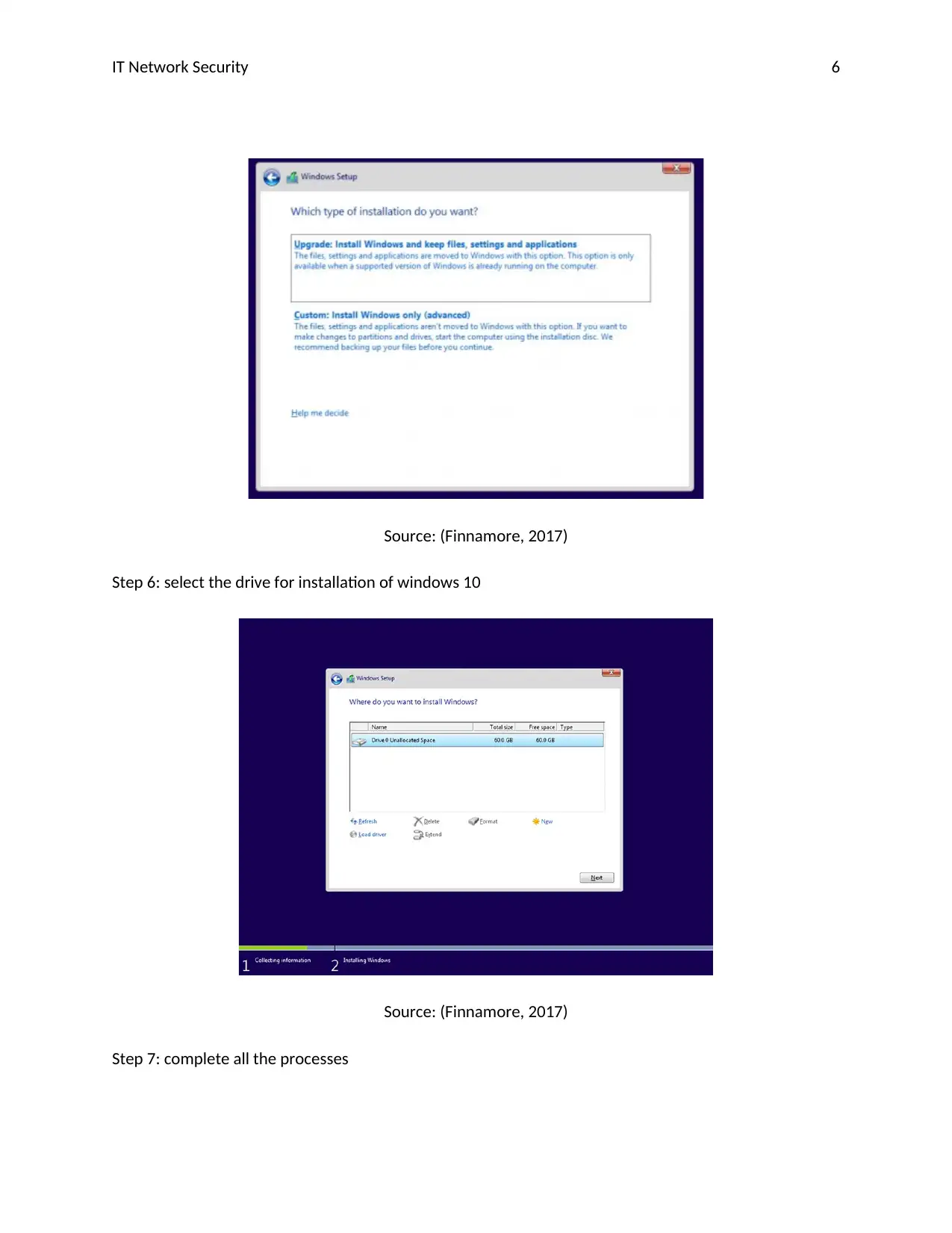
IT Network Security 6
Source: (Finnamore, 2017)
Step 6: select the drive for installation of windows 10
Source: (Finnamore, 2017)
Step 7: complete all the processes
Source: (Finnamore, 2017)
Step 6: select the drive for installation of windows 10
Source: (Finnamore, 2017)
Step 7: complete all the processes
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
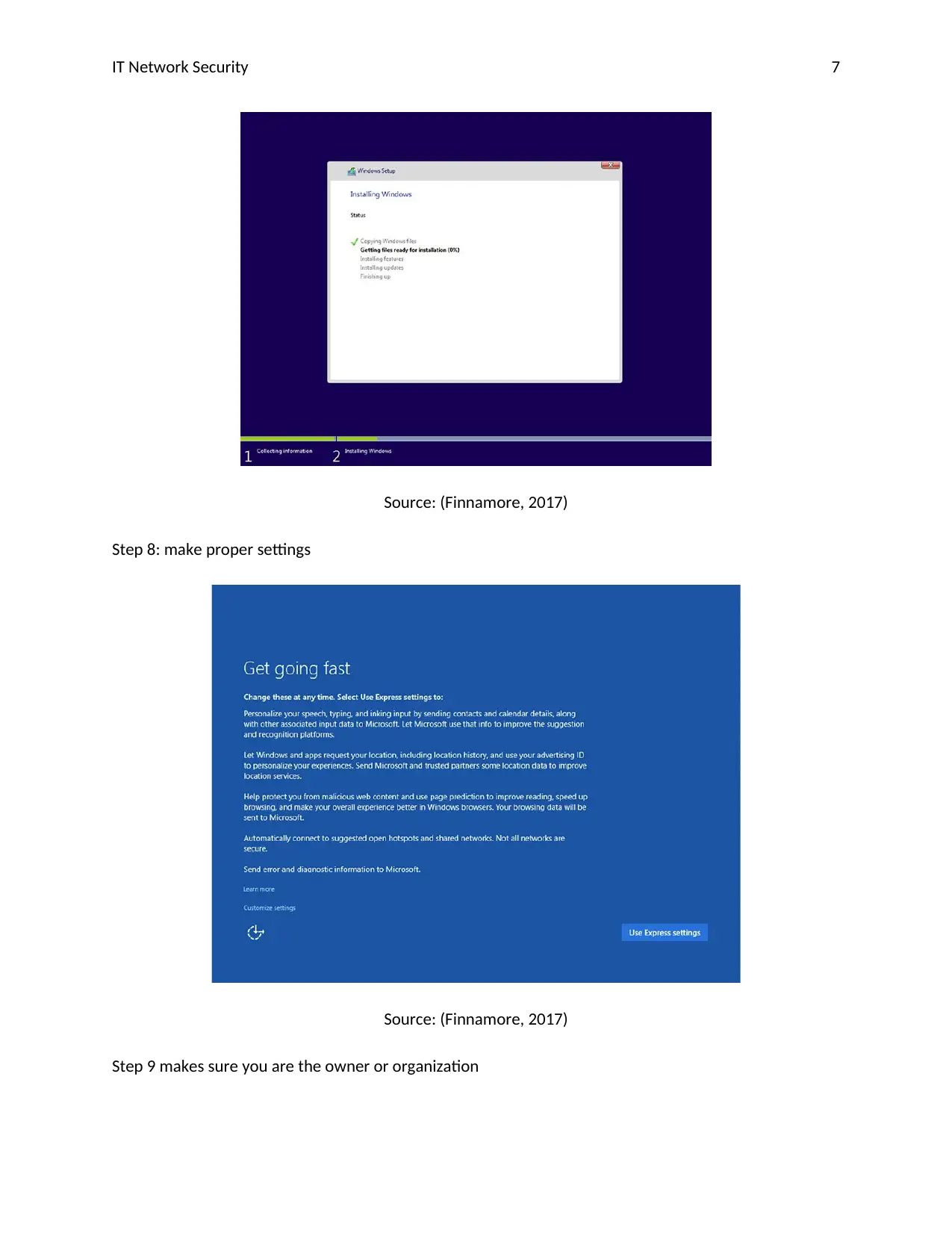
IT Network Security 7
Source: (Finnamore, 2017)
Step 8: make proper settings
Source: (Finnamore, 2017)
Step 9 makes sure you are the owner or organization
Source: (Finnamore, 2017)
Step 8: make proper settings
Source: (Finnamore, 2017)
Step 9 makes sure you are the owner or organization
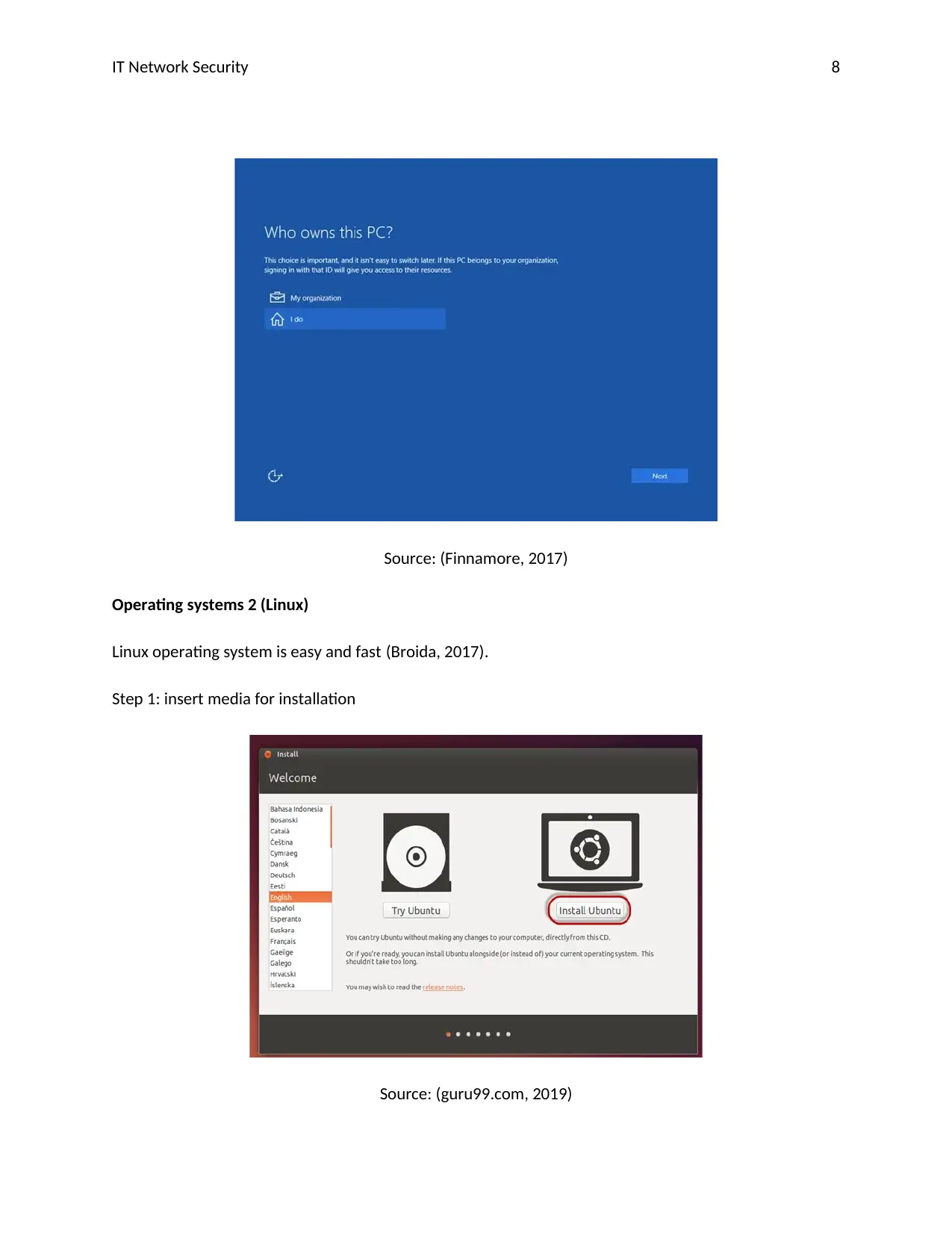
IT Network Security 8
Source: (Finnamore, 2017)
Operating systems 2 (Linux)
Linux operating system is easy and fast (Broida, 2017).
Step 1: insert media for installation
Source: (guru99.com, 2019)
Source: (Finnamore, 2017)
Operating systems 2 (Linux)
Linux operating system is easy and fast (Broida, 2017).
Step 1: insert media for installation
Source: (guru99.com, 2019)
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
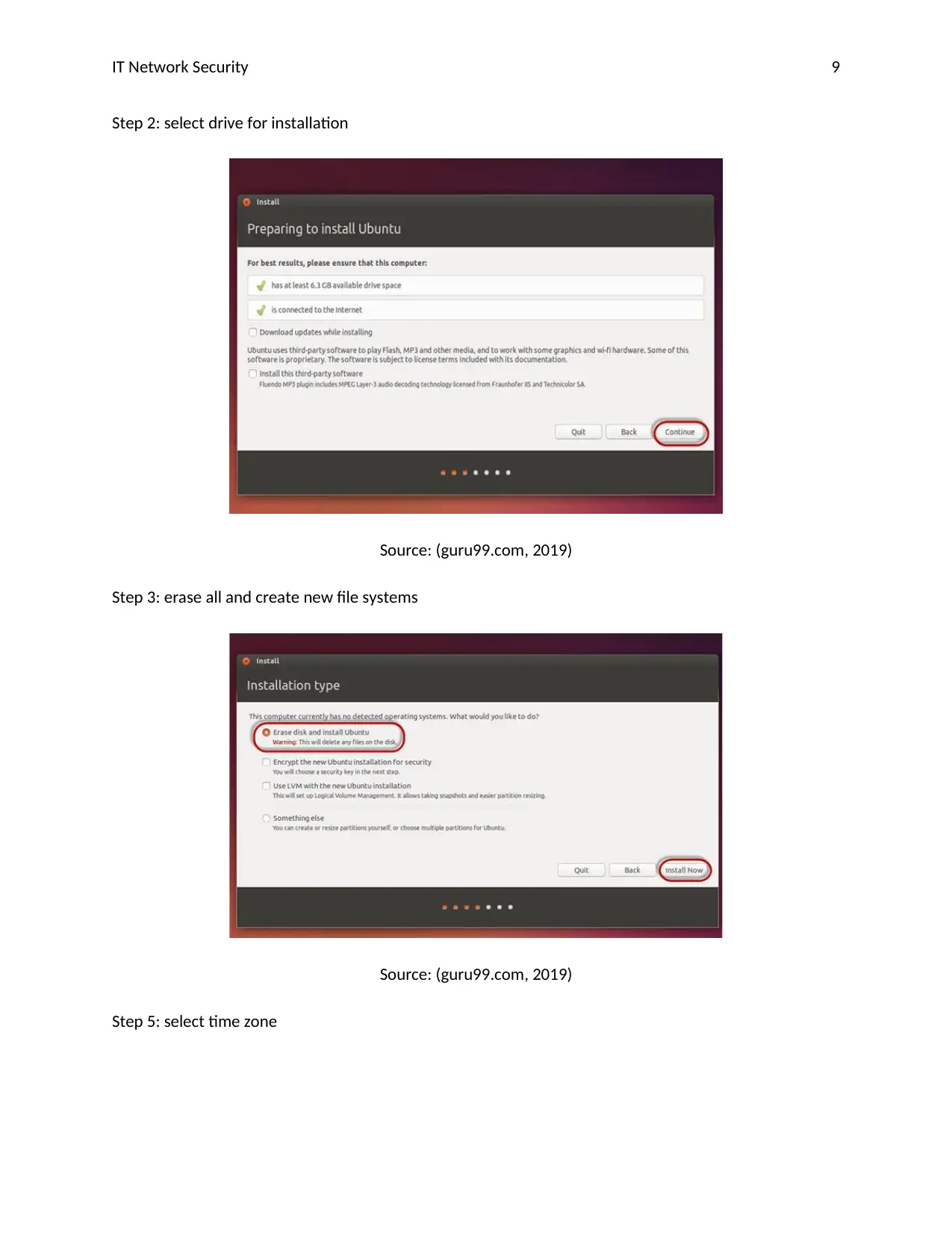
IT Network Security 9
Step 2: select drive for installation
Source: (guru99.com, 2019)
Step 3: erase all and create new file systems
Source: (guru99.com, 2019)
Step 5: select time zone
Step 2: select drive for installation
Source: (guru99.com, 2019)
Step 3: erase all and create new file systems
Source: (guru99.com, 2019)
Step 5: select time zone
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
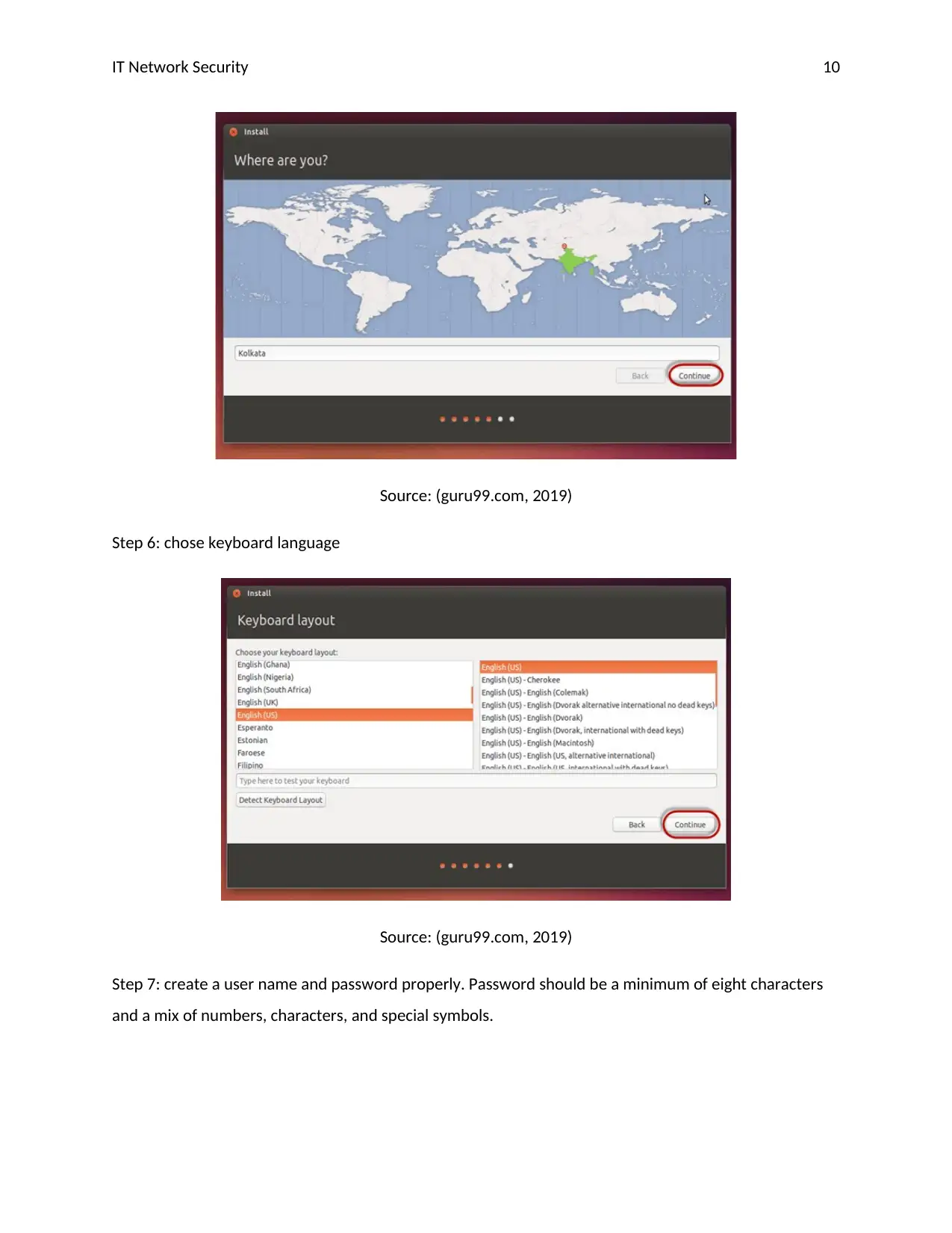
IT Network Security 10
Source: (guru99.com, 2019)
Step 6: chose keyboard language
Source: (guru99.com, 2019)
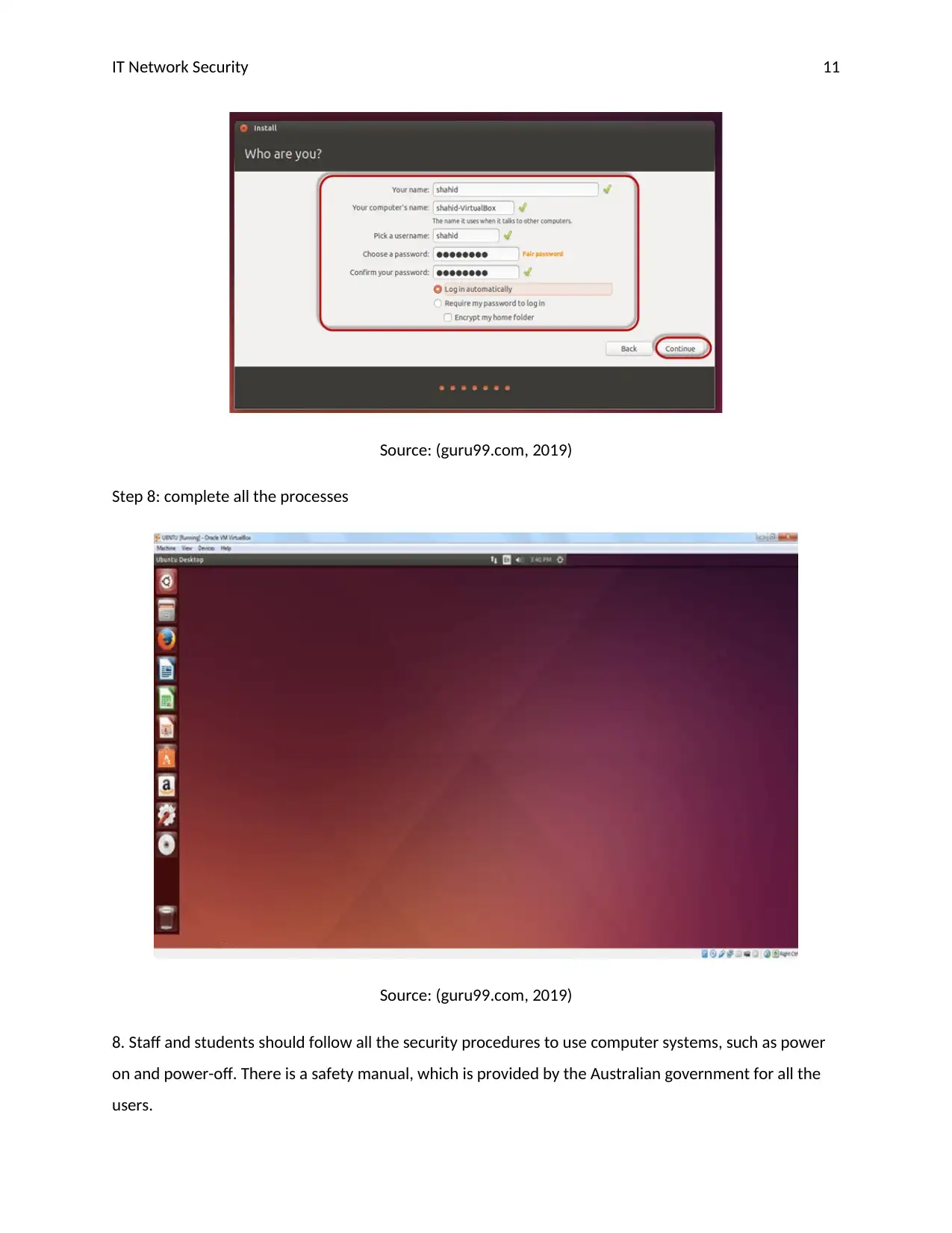
Step 7: create a user name and password properly. Password should be a minimum of eight characters
and a mix of numbers, characters, and special symbols.
Source: (guru99.com, 2019)
Step 6: chose keyboard language
Source: (guru99.com, 2019)
Step 7: create a user name and password properly. Password should be a minimum of eight characters
and a mix of numbers, characters, and special symbols.
IT Network Security 11
Source: (guru99.com, 2019)
Step 8: complete all the processes
Source: (guru99.com, 2019)
8. Staff and students should follow all the security procedures to use computer systems, such as power
on and power-off. There is a safety manual, which is provided by the Australian government for all the
users.
Source: (guru99.com, 2019)
Step 8: complete all the processes
Source: (guru99.com, 2019)
8. Staff and students should follow all the security procedures to use computer systems, such as power
on and power-off. There is a safety manual, which is provided by the Australian government for all the
users.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 32
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




