IT Networking Design: LAN for Windows Server and Client Environment
VerifiedAdded on 2021/06/14
|12
|2716
|93
Report
AI Summary
This report presents a comprehensive IT networking design for Jones Estates, focusing on a Local Area Network (LAN) to support a Windows Server and client environment. It begins with a requirement analysis, assessing user needs and organizational structure to inform the network design. The report identifies key server roles, including Active Directory for centralized user authentication, DHCP for dynamic IP address allocation, IIS for hosting an internal website, and file servers for data management. It details the configuration process, including IP addressing plans, subnetting schemes, and VLAN creation for different departments. The report provides screenshots and commands for configuring DHCP, IIS, and file server services. It emphasizes the importance of network security through access control rules and Active Directory policies. The report concludes with a discussion of the network's scalability and security, highlighting the importance of a firewall and remote access capabilities. The design aims to provide robust services for the organization while maintaining security and facilitating future growth. The report also includes a summary, conclusions, and a bibliography.

Running head: IT NETWORKING DESIGNING
Local Area Network (LAN) to support Windows Server and Client
Environment
Name of the Student
Name of the University
Author’s Note
Local Area Network (LAN) to support Windows Server and Client
Environment
Name of the Student
Name of the University
Author’s Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
IT NETWORKING DESIGNING
Table of Contents
Introduction...........................................................................................................................................2
Requirement analysis............................................................................................................................2
Identification of the server roles and technologies...............................................................................2
Configuring process description............................................................................................................3
IP Addressing Plan.............................................................................................................................3
Configuration Screenshots or commands..............................................................................................5
Centralised user authentication........................................................................................................5
Print server configuration..................................................................................................................5
DHCP server configuration................................................................................................................6
IIS configuration for hosting own website.........................................................................................7
File server configuration....................................................................................................................8
Summary...............................................................................................................................................8
Conclusions..........................................................................................................................................10
Bibliography.........................................................................................................................................11
IT NETWORKING DESIGNING
Table of Contents
Introduction...........................................................................................................................................2
Requirement analysis............................................................................................................................2
Identification of the server roles and technologies...............................................................................2
Configuring process description............................................................................................................3
IP Addressing Plan.............................................................................................................................3
Configuration Screenshots or commands..............................................................................................5
Centralised user authentication........................................................................................................5
Print server configuration..................................................................................................................5
DHCP server configuration................................................................................................................6
IIS configuration for hosting own website.........................................................................................7
File server configuration....................................................................................................................8
Summary...............................................................................................................................................8
Conclusions..........................................................................................................................................10
Bibliography.........................................................................................................................................11

2
IT NETWORKING DESIGNING
Introduction
The report is prepared for Jones Estates for the development of a local area network solution for
supporting the windows server and the client environment. The network needs to meet the current
needs of the users and support the future growth of the organization for providing different services
to each of the four departments of the organization. For the development of the network solution
the current framework of the organization and the requirement of the organization are analysed.
The different server roles and the network technologies should be analysed for the development of
the network and the configuration process is also depicted in the report. The commands used for the
configuration of the network are attached with the report with the screenshot such that it can be
used for the development of the network solution.
Requirement analysis
The requirement of the network can be analysed with the involvement of the users from different
levels and preparing a set of questionnaires to identify the needs of the network in the organization.
The analysis of the requirement helps in reducing the errors in the configuration and align the
network solution with the current business process of the organization. Interviews can be arranged
with the stakeholders of the organization for identifying the requirement and management of the
users for accessing the sensitive information of the servers connected in the network. The network
needs to support the client server environment. For increasing the security of the network the
servers must be installed in separate subnet than the users because it can help in management of
the users by denying the access of the servers for a certain range of IP address assigned to the client
connected in the same local area network.
Identification of the server roles and technologies
The client server architecture is used for the management of the management of the information
system and it can be used for increasing the responsiveness and effectiveness current flow of
information in the current business process of the organization. The installation of the servers helps
in providing different service such as active directory certificate services for management of the
software certificates using the public key encryption technology. It can be used for centralizing the
user authentication by installing a radius server and allowing the remote users to connect with the
network via authentication with the server. The server can also be configured with the DHCP service
such that it can be used for automatically assign the IP address to the host connected in the
network. For each of the four departments different VLANs must be created and the server must be
configured with DHCP service. Different DHCP pool must be created for each of the VLAN following
the IP subnet scheme such that the device connected in each of the department are automatically
assigned with the IP address. The configuration of the windows server with the Domain name
system helps in binding the IP address with the associated names. It can also be integrated with the
DHCP service for eliminating the requirement of adding DNS records when new hosts are added in
the network. The file service is used for the management of the files and streamlining the client
access to the files. The print servers helps in centralizing the printing jobs and management of the
network printing.
IT NETWORKING DESIGNING
Introduction
The report is prepared for Jones Estates for the development of a local area network solution for
supporting the windows server and the client environment. The network needs to meet the current
needs of the users and support the future growth of the organization for providing different services
to each of the four departments of the organization. For the development of the network solution
the current framework of the organization and the requirement of the organization are analysed.
The different server roles and the network technologies should be analysed for the development of
the network and the configuration process is also depicted in the report. The commands used for the
configuration of the network are attached with the report with the screenshot such that it can be
used for the development of the network solution.
Requirement analysis
The requirement of the network can be analysed with the involvement of the users from different
levels and preparing a set of questionnaires to identify the needs of the network in the organization.
The analysis of the requirement helps in reducing the errors in the configuration and align the
network solution with the current business process of the organization. Interviews can be arranged
with the stakeholders of the organization for identifying the requirement and management of the
users for accessing the sensitive information of the servers connected in the network. The network
needs to support the client server environment. For increasing the security of the network the
servers must be installed in separate subnet than the users because it can help in management of
the users by denying the access of the servers for a certain range of IP address assigned to the client
connected in the same local area network.
Identification of the server roles and technologies
The client server architecture is used for the management of the management of the information
system and it can be used for increasing the responsiveness and effectiveness current flow of
information in the current business process of the organization. The installation of the servers helps
in providing different service such as active directory certificate services for management of the
software certificates using the public key encryption technology. It can be used for centralizing the
user authentication by installing a radius server and allowing the remote users to connect with the
network via authentication with the server. The server can also be configured with the DHCP service
such that it can be used for automatically assign the IP address to the host connected in the
network. For each of the four departments different VLANs must be created and the server must be
configured with DHCP service. Different DHCP pool must be created for each of the VLAN following
the IP subnet scheme such that the device connected in each of the department are automatically
assigned with the IP address. The configuration of the windows server with the Domain name
system helps in binding the IP address with the associated names. It can also be integrated with the
DHCP service for eliminating the requirement of adding DNS records when new hosts are added in
the network. The file service is used for the management of the files and streamlining the client
access to the files. The print servers helps in centralizing the printing jobs and management of the
network printing.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
3
IT NETWORKING DESIGNING
Configuring process description
For the configuration of the network firstly the number of routers and the switches required for
covering the different area of the organizational network should be analysed. The IP addressing plan
should be created for configuring the interfaces of the network device with an IP address for
enabling communication between the different subnets. The expected growth of the organisation
should be identified for the creation of the IP addressing plan and reserve extra number of IPs for
each of the subnets created for the different VLAN in the network.
The configuration of the file server should also be analysed for the development of the network
solution and proper cabling plan should be used for interconnecting the different departments with
each other. An internal website can be hosted with enabling the IIS service in the windows server
and it can be virtualized for creating a backup of the server and storing in the cloud platform for
handling the disaster recovery situation.
IP Addressing Plan
Major Network: 192.168.0.0/23
Available IP addresses in major network: 510
Number of IP addresses needed: 206
Available IP addresses in allocated subnets: 254
About 52% of available major network address space is used
About 81% of subnetted network address space is used
Subnet
Name
Neede
d Size
Allocat
ed Size
Address Mas
k
Dec Mask Assignable
Range
Broadcast
Managem
ent
50 62 192.168.0.6
4
/26 255.255.255.
192
192.168.0.6
5 -
192.168.0.1
26
192.168.0.1
27
Marketing 50 62 192.168.0.1
28
/26 255.255.255.
192
192.168.0.1
29 -
192.168.0.1
90
192.168.0.1
91
Sales 50 62 192.168.0.1
92
/26 255.255.255.
192
192.168.0.1
93 -
192.168.0.2
54
192.168.0.2
55
Accounting 50 62 192.168.0.0 /26 255.255.255.
192
192.168.0.1
-
192.168.0.6
2
192.168.0.6
3
Server 6 6 192.168.1.0 /29 255.255.255.
248
192.168.1.1
-
192.168.1.7
IT NETWORKING DESIGNING
Configuring process description
For the configuration of the network firstly the number of routers and the switches required for
covering the different area of the organizational network should be analysed. The IP addressing plan
should be created for configuring the interfaces of the network device with an IP address for
enabling communication between the different subnets. The expected growth of the organisation
should be identified for the creation of the IP addressing plan and reserve extra number of IPs for
each of the subnets created for the different VLAN in the network.
The configuration of the file server should also be analysed for the development of the network
solution and proper cabling plan should be used for interconnecting the different departments with
each other. An internal website can be hosted with enabling the IIS service in the windows server
and it can be virtualized for creating a backup of the server and storing in the cloud platform for
handling the disaster recovery situation.
IP Addressing Plan
Major Network: 192.168.0.0/23
Available IP addresses in major network: 510
Number of IP addresses needed: 206
Available IP addresses in allocated subnets: 254
About 52% of available major network address space is used
About 81% of subnetted network address space is used
Subnet
Name
Neede
d Size
Allocat
ed Size
Address Mas
k
Dec Mask Assignable
Range
Broadcast
Managem
ent
50 62 192.168.0.6
4
/26 255.255.255.
192
192.168.0.6
5 -
192.168.0.1
26
192.168.0.1
27
Marketing 50 62 192.168.0.1
28
/26 255.255.255.
192
192.168.0.1
29 -
192.168.0.1
90
192.168.0.1
91
Sales 50 62 192.168.0.1
92
/26 255.255.255.
192
192.168.0.1
93 -
192.168.0.2
54
192.168.0.2
55
Accounting 50 62 192.168.0.0 /26 255.255.255.
192
192.168.0.1
-
192.168.0.6
2
192.168.0.6
3
Server 6 6 192.168.1.0 /29 255.255.255.
248
192.168.1.1
-
192.168.1.7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4
IT NETWORKING DESIGNING
192.168.1.6
Centralised User Authentication – the configuration of the windows server with the active directory
helps in centralizing the user authentication process. From the different service the active directory
domain service feature should be added and then in the deployment configuration the addition of
the new forest and configuring the domain name with a password helps in management of the
resources.
Print servers for users – it helps in management of the printing jobs where the server manager add
the feature of print service. The printer connected with the server can be automatically detected
and it can be shared in the network such that the user can use the network printer to print files.
DHCP Configuration – for configuring the server with DHCP the DHCP roles and services should be
enabled in the server and an authorization should be set for authorizing it in the active directory. It
helps in increasing the security of the network and different permission can be created for creating
objects in the net service container residing in the active directory. Security groups can be added
using the command netsh dhcp add securitygroups for securing the network from illegal users.
Website Hosting – for hosting an internal website the windows server is the best choice and the IIS
service should be added from the server manager for hosting an internal website. The different
service such as WWW publishing service, FTP service should be enabled for hosting the website.
File Server configuration – For the configuration of the file server the file and the share services
should be enabled from the server manager and available disk option should be selected for the
configuration of the storage pools and increasing the efficiency of the client server environment. It
would also increase the efficiency of the network and enables the user to send and receive different
files using the server.
IT NETWORKING DESIGNING
192.168.1.6
Centralised User Authentication – the configuration of the windows server with the active directory
helps in centralizing the user authentication process. From the different service the active directory
domain service feature should be added and then in the deployment configuration the addition of
the new forest and configuring the domain name with a password helps in management of the
resources.
Print servers for users – it helps in management of the printing jobs where the server manager add
the feature of print service. The printer connected with the server can be automatically detected
and it can be shared in the network such that the user can use the network printer to print files.
DHCP Configuration – for configuring the server with DHCP the DHCP roles and services should be
enabled in the server and an authorization should be set for authorizing it in the active directory. It
helps in increasing the security of the network and different permission can be created for creating
objects in the net service container residing in the active directory. Security groups can be added
using the command netsh dhcp add securitygroups for securing the network from illegal users.
Website Hosting – for hosting an internal website the windows server is the best choice and the IIS
service should be added from the server manager for hosting an internal website. The different
service such as WWW publishing service, FTP service should be enabled for hosting the website.
File Server configuration – For the configuration of the file server the file and the share services
should be enabled from the server manager and available disk option should be selected for the
configuration of the storage pools and increasing the efficiency of the client server environment. It
would also increase the efficiency of the network and enables the user to send and receive different
files using the server.
5
IT NETWORKING DESIGNING
Configuration Screenshots or commands
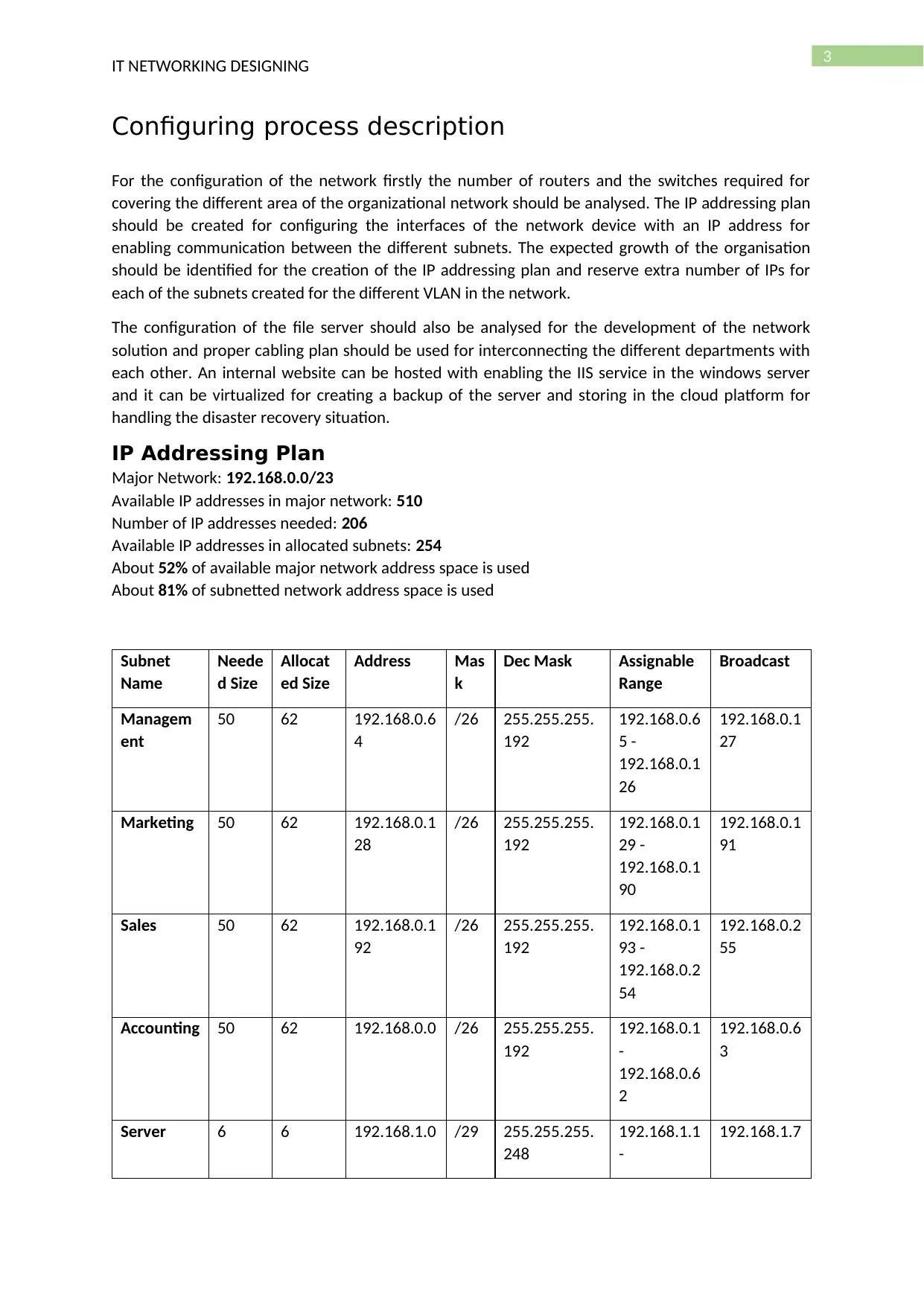
Centralised user authentication
For the configuration of the centralised user authentication the server is configured as RADIUS
server and the active directory is configured for setting the users and the computers. New object is
created and the option protect content from accidental deletion is selected. A new group is created
and the user is added to the group for the management of the user.
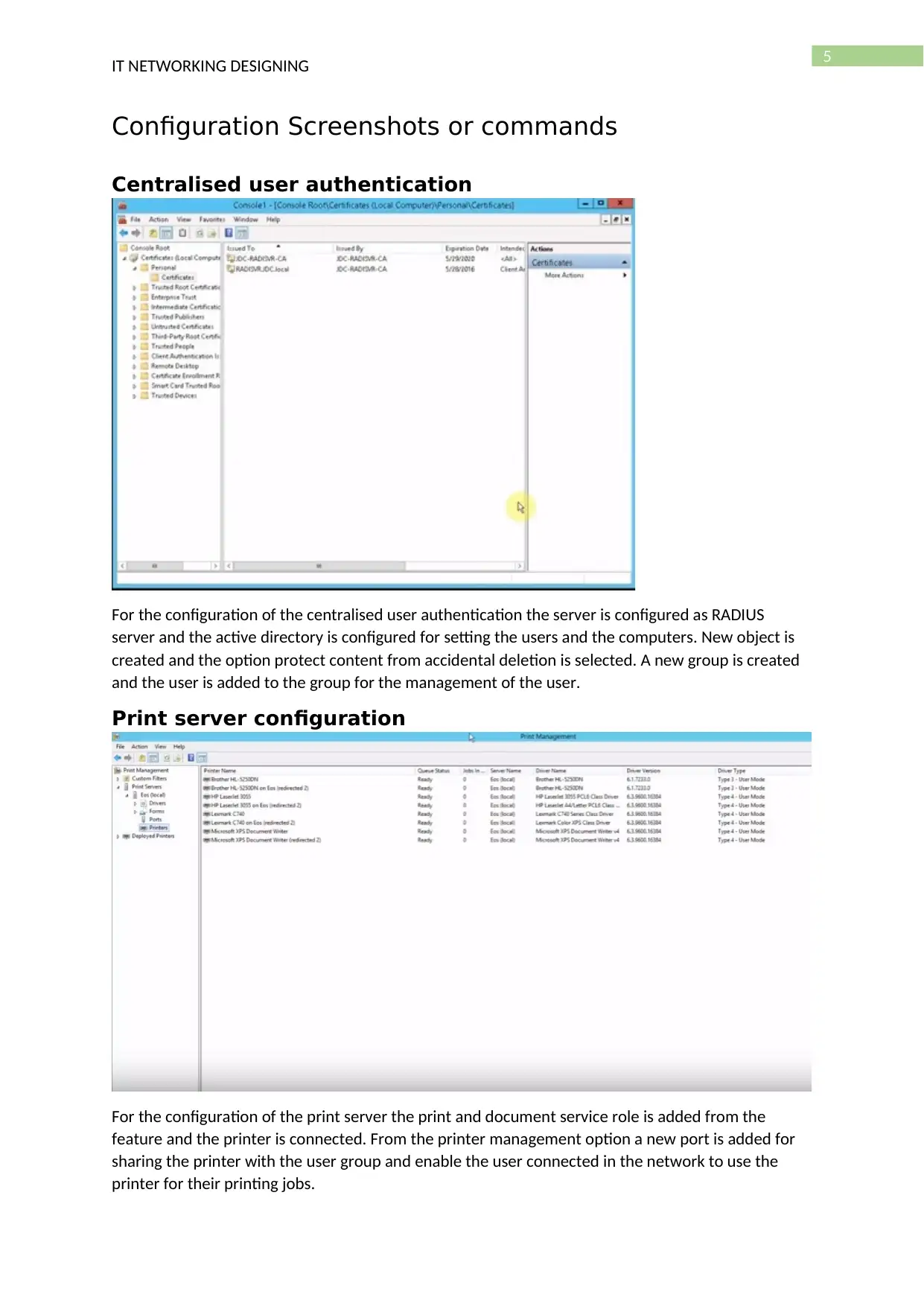
Print server configuration
For the configuration of the print server the print and document service role is added from the
feature and the printer is connected. From the printer management option a new port is added for
sharing the printer with the user group and enable the user connected in the network to use the
printer for their printing jobs.
IT NETWORKING DESIGNING
Configuration Screenshots or commands
Centralised user authentication
For the configuration of the centralised user authentication the server is configured as RADIUS
server and the active directory is configured for setting the users and the computers. New object is
created and the option protect content from accidental deletion is selected. A new group is created
and the user is added to the group for the management of the user.
Print server configuration
For the configuration of the print server the print and document service role is added from the
feature and the printer is connected. From the printer management option a new port is added for
sharing the printer with the user group and enable the user connected in the network to use the
printer for their printing jobs.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
6
IT NETWORKING DESIGNING
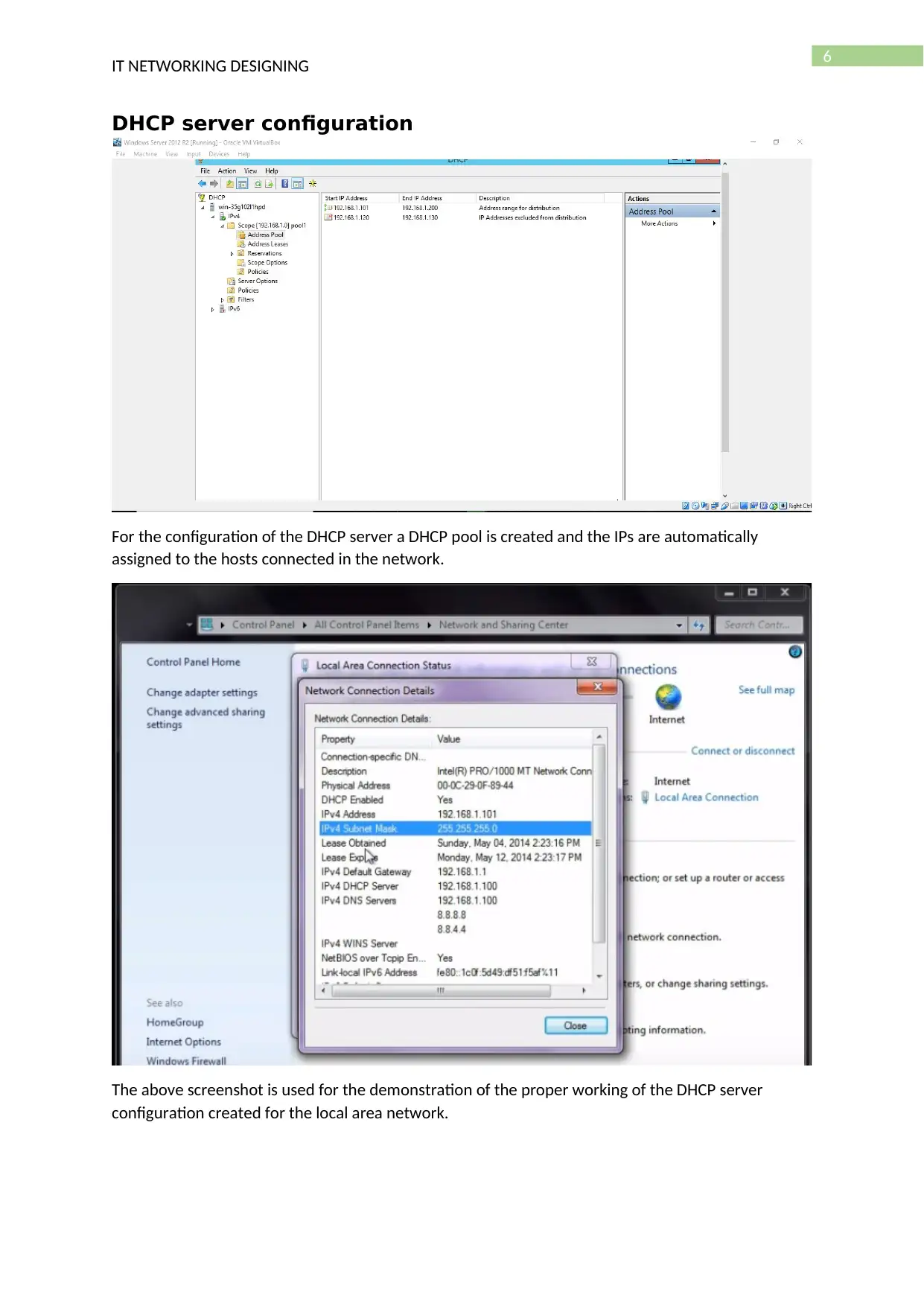
DHCP server configuration
For the configuration of the DHCP server a DHCP pool is created and the IPs are automatically
assigned to the hosts connected in the network.
The above screenshot is used for the demonstration of the proper working of the DHCP server
configuration created for the local area network.
IT NETWORKING DESIGNING
DHCP server configuration
For the configuration of the DHCP server a DHCP pool is created and the IPs are automatically
assigned to the hosts connected in the network.
The above screenshot is used for the demonstration of the proper working of the DHCP server
configuration created for the local area network.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
7
IT NETWORKING DESIGNING
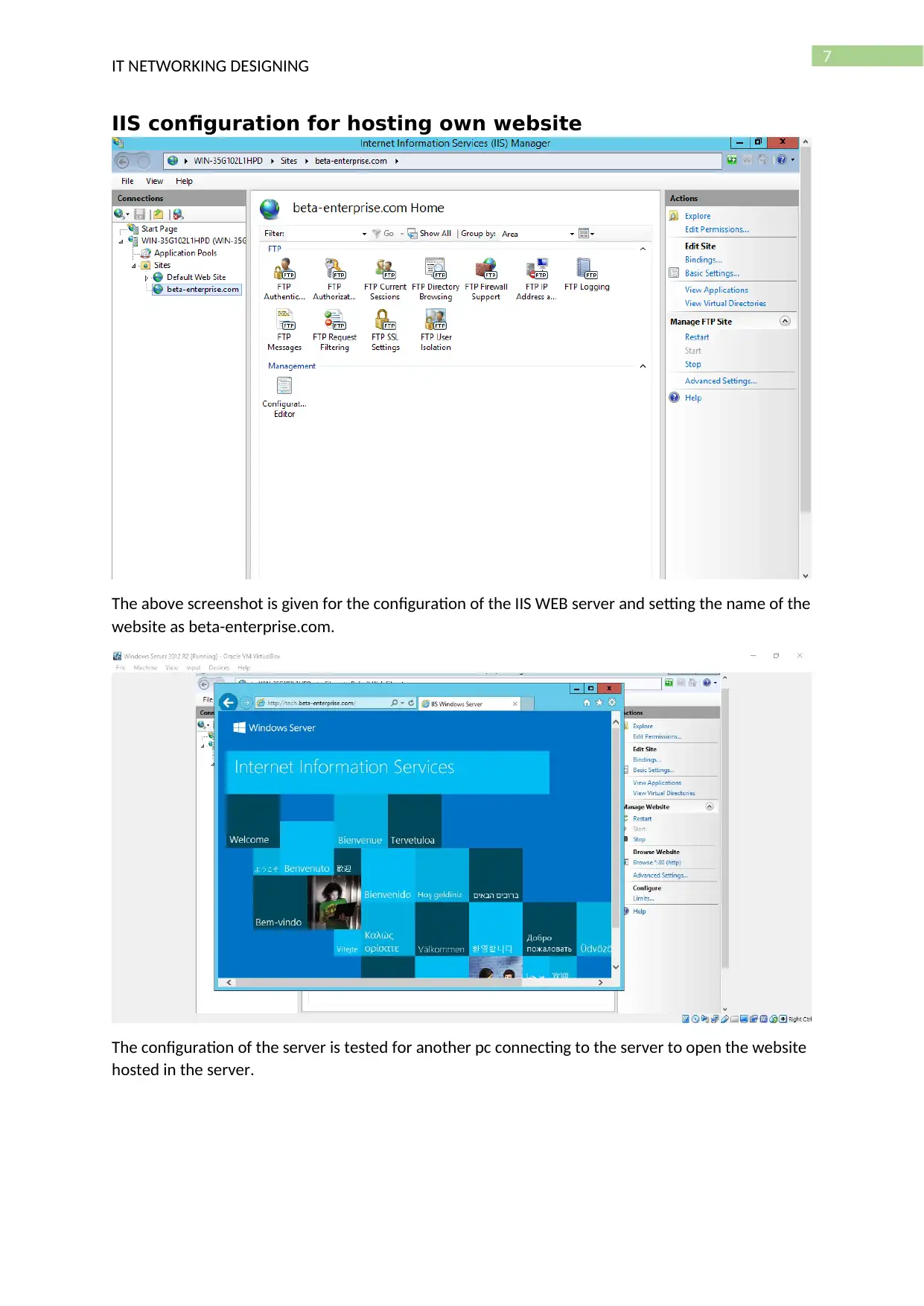
IIS configuration for hosting own website
The above screenshot is given for the configuration of the IIS WEB server and setting the name of the
website as beta-enterprise.com.
The configuration of the server is tested for another pc connecting to the server to open the website
hosted in the server.
IT NETWORKING DESIGNING
IIS configuration for hosting own website
The above screenshot is given for the configuration of the IIS WEB server and setting the name of the
website as beta-enterprise.com.
The configuration of the server is tested for another pc connecting to the server to open the website
hosted in the server.
8
IT NETWORKING DESIGNING
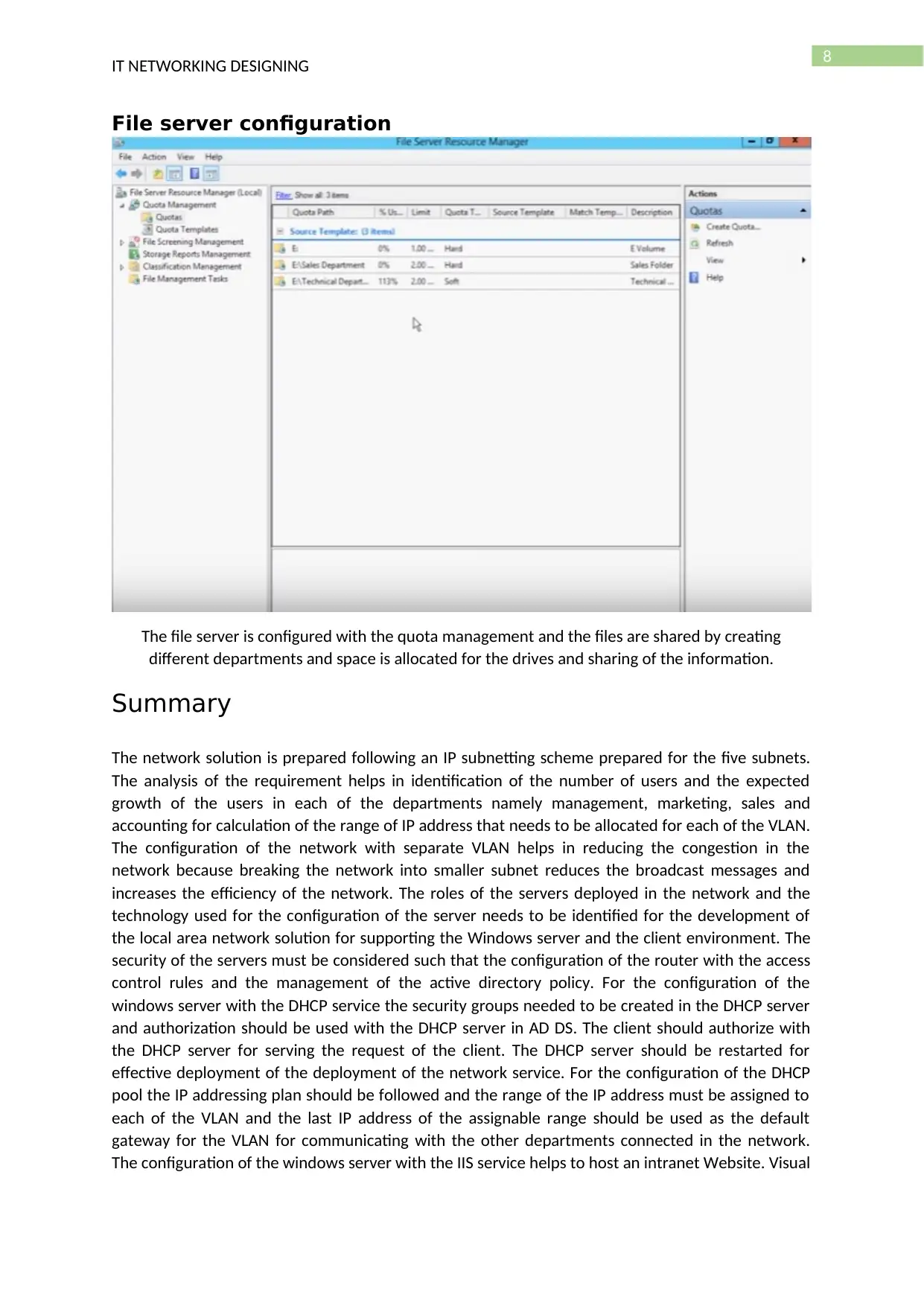
File server configuration
The file server is configured with the quota management and the files are shared by creating
different departments and space is allocated for the drives and sharing of the information.
Summary
The network solution is prepared following an IP subnetting scheme prepared for the five subnets.
The analysis of the requirement helps in identification of the number of users and the expected
growth of the users in each of the departments namely management, marketing, sales and
accounting for calculation of the range of IP address that needs to be allocated for each of the VLAN.
The configuration of the network with separate VLAN helps in reducing the congestion in the
network because breaking the network into smaller subnet reduces the broadcast messages and
increases the efficiency of the network. The roles of the servers deployed in the network and the
technology used for the configuration of the server needs to be identified for the development of
the local area network solution for supporting the Windows server and the client environment. The
security of the servers must be considered such that the configuration of the router with the access
control rules and the management of the active directory policy. For the configuration of the
windows server with the DHCP service the security groups needed to be created in the DHCP server
and authorization should be used with the DHCP server in AD DS. The client should authorize with
the DHCP server for serving the request of the client. The DHCP server should be restarted for
effective deployment of the deployment of the network service. For the configuration of the DHCP
pool the IP addressing plan should be followed and the range of the IP address must be assigned to
each of the VLAN and the last IP address of the assignable range should be used as the default
gateway for the VLAN for communicating with the other departments connected in the network.
The configuration of the windows server with the IIS service helps to host an intranet Website. Visual
IT NETWORKING DESIGNING
File server configuration
The file server is configured with the quota management and the files are shared by creating
different departments and space is allocated for the drives and sharing of the information.
Summary
The network solution is prepared following an IP subnetting scheme prepared for the five subnets.
The analysis of the requirement helps in identification of the number of users and the expected
growth of the users in each of the departments namely management, marketing, sales and
accounting for calculation of the range of IP address that needs to be allocated for each of the VLAN.
The configuration of the network with separate VLAN helps in reducing the congestion in the
network because breaking the network into smaller subnet reduces the broadcast messages and
increases the efficiency of the network. The roles of the servers deployed in the network and the
technology used for the configuration of the server needs to be identified for the development of
the local area network solution for supporting the Windows server and the client environment. The
security of the servers must be considered such that the configuration of the router with the access
control rules and the management of the active directory policy. For the configuration of the
windows server with the DHCP service the security groups needed to be created in the DHCP server
and authorization should be used with the DHCP server in AD DS. The client should authorize with
the DHCP server for serving the request of the client. The DHCP server should be restarted for
effective deployment of the deployment of the network service. For the configuration of the DHCP
pool the IP addressing plan should be followed and the range of the IP address must be assigned to
each of the VLAN and the last IP address of the assignable range should be used as the default
gateway for the VLAN for communicating with the other departments connected in the network.
The configuration of the windows server with the IIS service helps to host an intranet Website. Visual
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9
IT NETWORKING DESIGNING
studio can be used for designing the web interface or simple HTML page can be used for hosting the
website. The local area network solution is prepared for serving the different service that are
required by the organization. The security of the network should be improved such that it helps in
restricting the access of the servers to the unauthorised users. For enabling the remote access of the
network and the file servers the server is configured with the central user authentication service. A
firewall should be installed in the network and configured with the current business policy such that
the security of the network device and the file server is maintained.
IT NETWORKING DESIGNING
studio can be used for designing the web interface or simple HTML page can be used for hosting the
website. The local area network solution is prepared for serving the different service that are
required by the organization. The security of the network should be improved such that it helps in
restricting the access of the servers to the unauthorised users. For enabling the remote access of the
network and the file servers the server is configured with the central user authentication service. A
firewall should be installed in the network and configured with the current business policy such that
the security of the network device and the file server is maintained.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10
IT NETWORKING DESIGNING
Conclusions
From the above report it can be concluded that with the analysis of the requirement for the
development of the local area network solution for the management of the client server network
architecture. The local area network is designed for connecting the hosts on one of the interface of
the router and connect the file server on a separate interface such that it can be secured against the
illegal access of the users or any third party for accessing the secure information residing in the file
server. There is a requirement to configure the router with access control list such that the unknown
IP address can be blocked for accessing the file servers deployed in the network. The local area
network is divided into 5 subnets one for the management, second for the marketing, third for the
sales, fourth for the accounting and the fifth for the servers. The physical access of thee file server
should be restricted and the active directory is configured with user management policy such that a
specific user group is given the access of the file server. Moreover the configuration of the server
with the printing service helps in reducing the management and the hardware cost of the network.
The printing jobs are mainly required for the sales and the accounting department and the thus
installation off the printer and sharing it with the all the department helps in eliminating the need of
installation of separate printers for all the departments.
IT NETWORKING DESIGNING
Conclusions
From the above report it can be concluded that with the analysis of the requirement for the
development of the local area network solution for the management of the client server network
architecture. The local area network is designed for connecting the hosts on one of the interface of
the router and connect the file server on a separate interface such that it can be secured against the
illegal access of the users or any third party for accessing the secure information residing in the file
server. There is a requirement to configure the router with access control list such that the unknown
IP address can be blocked for accessing the file servers deployed in the network. The local area
network is divided into 5 subnets one for the management, second for the marketing, third for the
sales, fourth for the accounting and the fifth for the servers. The physical access of thee file server
should be restricted and the active directory is configured with user management policy such that a
specific user group is given the access of the file server. Moreover the configuration of the server
with the printing service helps in reducing the management and the hardware cost of the network.
The printing jobs are mainly required for the sales and the accounting department and the thus
installation off the printer and sharing it with the all the department helps in eliminating the need of
installation of separate printers for all the departments.

11
IT NETWORKING DESIGNING
Bibliography
[1]. "IEEE/ACM Transactions on Networking society information", IEEE/ACM Transactions on
Networking, vol. 24, no. 5, pp. C3-C3, 2016.
[2]. "Introduction to Information Security", Network Security, vol. 2013, no. 12, p. 4, 2013.
[3]. "Optical Switching and Networking", Optical Switching and Networking, vol. 10, no. 4, pp.
463-464, 2013.
[4]. Parikh, M. Uysal, and P. Shah, Vmware, Inc., Universal virtualized resource management.
U.S. Patent Application 14/333,400. 2014.
[5]. Wagner, C. Trople, and R. DiFalco, Tripwire, Inc., Systems and methods for monitoring and
alerting events that virtual machine software produces in a virtual infrastructure. U.S. Patent
8,875,129. 2014.
[6]. A.L.I. Qasim, V. Pandey, R. Mummidi, and T.A.T.I. Kiran, Vmware, Inc., System and method to
prioritize large memory page allocation in virtualized systems. U.S. Patent 9,116,829. 2015.
[7]. D. Langenhan, VMware View Security Essentials. Packt Publishing, 2013.
[8]. J.M. Mann, Hewlett-Packard Development Company, LP, Installing an application into a
virtualized environment. U.S. Patent 9,176,721. 2015.
[9]. K.M. Adams, J.W. Sheldon, and V.V. Malyugin, Vmware, Inc., Adaptive dynamic selection and
application of multiple virtualization techniques. U.S. Patent 9,513,954, 2016.
[10]. N.F. Mir, J.N. Kotte, and G.A. Pokuri, Implementation of Virtualization in Software
Defined Networking (SDN) for Data Center Networks. ICN 2016, p.136. 2016.
[11]. O. Agesen, B. Weissman, K. Adams, J.A.M. Anderson, and M. Austruy, Vmware, Inc.,
Efficient virtualization of input/output completions for a virtual device. U.S. Patent
8,875,162. 2014.
[12]. R. Brewer, "Advanced persistent threats: minimising the damage", Network Security,
vol. 2014, no. 4, pp. 5-9, 2014.
[13]. R. Purushotham, R.P. Soni, and S.L. Rao, Vmware, Inc., Host management across
virtualization management servers. U.S. Patent Application 14/848,382. 2015.
[14]. S. Subramaniam, M. Brandt-Pearce, P. Demeester and C. Vijaya Saradhi, Cross-Layer
Design in Optical Networks. Boston, MA: Springer US, 2013.
[15]. T.U.C.H. Harvey, P.P. Bungale, S.W. Devine, and L.S. Rogel, Vmware, Inc., Virtualizing
processor memory protection with “L1 iterate and L2 drop/repopulate”. U.S. Patent
9,251,102. 2016.
IT NETWORKING DESIGNING
Bibliography
[1]. "IEEE/ACM Transactions on Networking society information", IEEE/ACM Transactions on
Networking, vol. 24, no. 5, pp. C3-C3, 2016.
[2]. "Introduction to Information Security", Network Security, vol. 2013, no. 12, p. 4, 2013.
[3]. "Optical Switching and Networking", Optical Switching and Networking, vol. 10, no. 4, pp.
463-464, 2013.
[4]. Parikh, M. Uysal, and P. Shah, Vmware, Inc., Universal virtualized resource management.
U.S. Patent Application 14/333,400. 2014.
[5]. Wagner, C. Trople, and R. DiFalco, Tripwire, Inc., Systems and methods for monitoring and
alerting events that virtual machine software produces in a virtual infrastructure. U.S. Patent
8,875,129. 2014.
[6]. A.L.I. Qasim, V. Pandey, R. Mummidi, and T.A.T.I. Kiran, Vmware, Inc., System and method to
prioritize large memory page allocation in virtualized systems. U.S. Patent 9,116,829. 2015.
[7]. D. Langenhan, VMware View Security Essentials. Packt Publishing, 2013.
[8]. J.M. Mann, Hewlett-Packard Development Company, LP, Installing an application into a
virtualized environment. U.S. Patent 9,176,721. 2015.
[9]. K.M. Adams, J.W. Sheldon, and V.V. Malyugin, Vmware, Inc., Adaptive dynamic selection and
application of multiple virtualization techniques. U.S. Patent 9,513,954, 2016.
[10]. N.F. Mir, J.N. Kotte, and G.A. Pokuri, Implementation of Virtualization in Software
Defined Networking (SDN) for Data Center Networks. ICN 2016, p.136. 2016.
[11]. O. Agesen, B. Weissman, K. Adams, J.A.M. Anderson, and M. Austruy, Vmware, Inc.,
Efficient virtualization of input/output completions for a virtual device. U.S. Patent
8,875,162. 2014.
[12]. R. Brewer, "Advanced persistent threats: minimising the damage", Network Security,
vol. 2014, no. 4, pp. 5-9, 2014.
[13]. R. Purushotham, R.P. Soni, and S.L. Rao, Vmware, Inc., Host management across
virtualization management servers. U.S. Patent Application 14/848,382. 2015.
[14]. S. Subramaniam, M. Brandt-Pearce, P. Demeester and C. Vijaya Saradhi, Cross-Layer
Design in Optical Networks. Boston, MA: Springer US, 2013.
[15]. T.U.C.H. Harvey, P.P. Bungale, S.W. Devine, and L.S. Rogel, Vmware, Inc., Virtualizing
processor memory protection with “L1 iterate and L2 drop/repopulate”. U.S. Patent
9,251,102. 2016.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 12
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





