Comprehensive IT Operations Plan for TreasureChest's SaaS Services
VerifiedAdded on 2023/01/16
|8
|2523
|36
Report
AI Summary
This IT operations plan template, based on the TreasureChest case study, provides a comprehensive analysis of a SaaS environment. The report begins with an assessment of the current infrastructure, including hardware, operating systems, networks, software, and databases. It then outlines strategic goals, such as enhancing products for larger customers and improving business software, along with corresponding IT operational goals. The plan details enhancements needed to support each strategic objective, including network and database improvements, and a communication plan. The report also incorporates a sustainability plan spanning one, three, and five years. Furthermore, it identifies and addresses potential security risks, such as computer viruses and data leaks, and provides an operational workflow for increasing the customer base. References are also included.
IT Operations Plan Template
Record all responses to C927 Task 1 in this template.
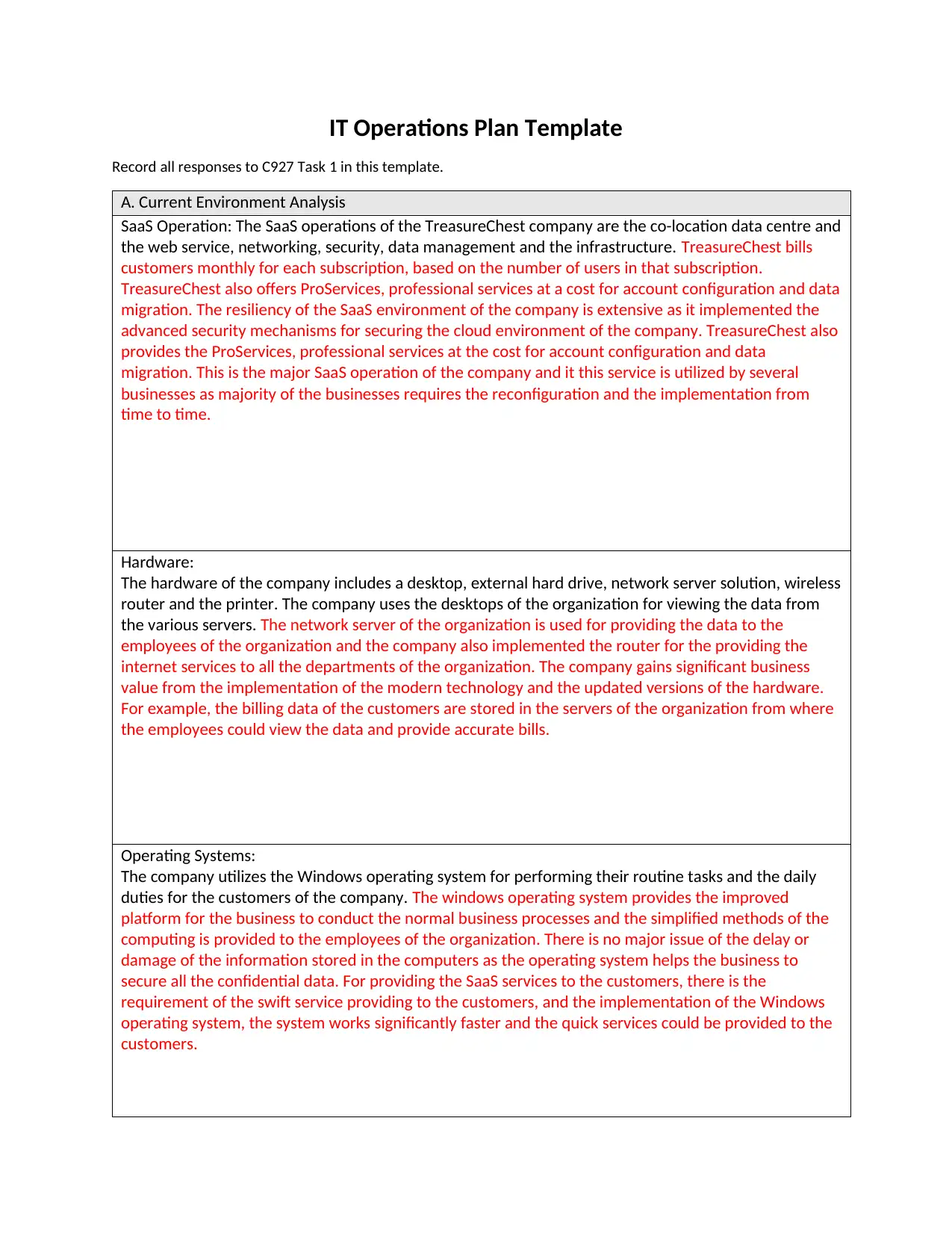
A. Current Environment Analysis
SaaS Operation: The SaaS operations of the TreasureChest company are the co-location data centre and
the web service, networking, security, data management and the infrastructure. TreasureChest bills
customers monthly for each subscription, based on the number of users in that subscription.
TreasureChest also offers ProServices, professional services at a cost for account configuration and data
migration. The resiliency of the SaaS environment of the company is extensive as it implemented the
advanced security mechanisms for securing the cloud environment of the company. TreasureChest also
provides the ProServices, professional services at the cost for account configuration and data
migration. This is the major SaaS operation of the company and it this service is utilized by several
businesses as majority of the businesses requires the reconfiguration and the implementation from
time to time.
Hardware:
The hardware of the company includes a desktop, external hard drive, network server solution, wireless
router and the printer. The company uses the desktops of the organization for viewing the data from
the various servers. The network server of the organization is used for providing the data to the
employees of the organization and the company also implemented the router for the providing the
internet services to all the departments of the organization. The company gains significant business
value from the implementation of the modern technology and the updated versions of the hardware.
For example, the billing data of the customers are stored in the servers of the organization from where
the employees could view the data and provide accurate bills.
Operating Systems:
The company utilizes the Windows operating system for performing their routine tasks and the daily
duties for the customers of the company. The windows operating system provides the improved
platform for the business to conduct the normal business processes and the simplified methods of the
computing is provided to the employees of the organization. There is no major issue of the delay or
damage of the information stored in the computers as the operating system helps the business to
secure all the confidential data. For providing the SaaS services to the customers, there is the
requirement of the swift service providing to the customers, and the implementation of the Windows
operating system, the system works significantly faster and the quick services could be provided to the
customers.
Record all responses to C927 Task 1 in this template.
A. Current Environment Analysis
SaaS Operation: The SaaS operations of the TreasureChest company are the co-location data centre and
the web service, networking, security, data management and the infrastructure. TreasureChest bills
customers monthly for each subscription, based on the number of users in that subscription.
TreasureChest also offers ProServices, professional services at a cost for account configuration and data
migration. The resiliency of the SaaS environment of the company is extensive as it implemented the
advanced security mechanisms for securing the cloud environment of the company. TreasureChest also
provides the ProServices, professional services at the cost for account configuration and data
migration. This is the major SaaS operation of the company and it this service is utilized by several
businesses as majority of the businesses requires the reconfiguration and the implementation from
time to time.
Hardware:
The hardware of the company includes a desktop, external hard drive, network server solution, wireless
router and the printer. The company uses the desktops of the organization for viewing the data from
the various servers. The network server of the organization is used for providing the data to the
employees of the organization and the company also implemented the router for the providing the
internet services to all the departments of the organization. The company gains significant business
value from the implementation of the modern technology and the updated versions of the hardware.
For example, the billing data of the customers are stored in the servers of the organization from where
the employees could view the data and provide accurate bills.
Operating Systems:
The company utilizes the Windows operating system for performing their routine tasks and the daily
duties for the customers of the company. The windows operating system provides the improved
platform for the business to conduct the normal business processes and the simplified methods of the
computing is provided to the employees of the organization. There is no major issue of the delay or
damage of the information stored in the computers as the operating system helps the business to
secure all the confidential data. For providing the SaaS services to the customers, there is the
requirement of the swift service providing to the customers, and the implementation of the Windows
operating system, the system works significantly faster and the quick services could be provided to the
customers.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
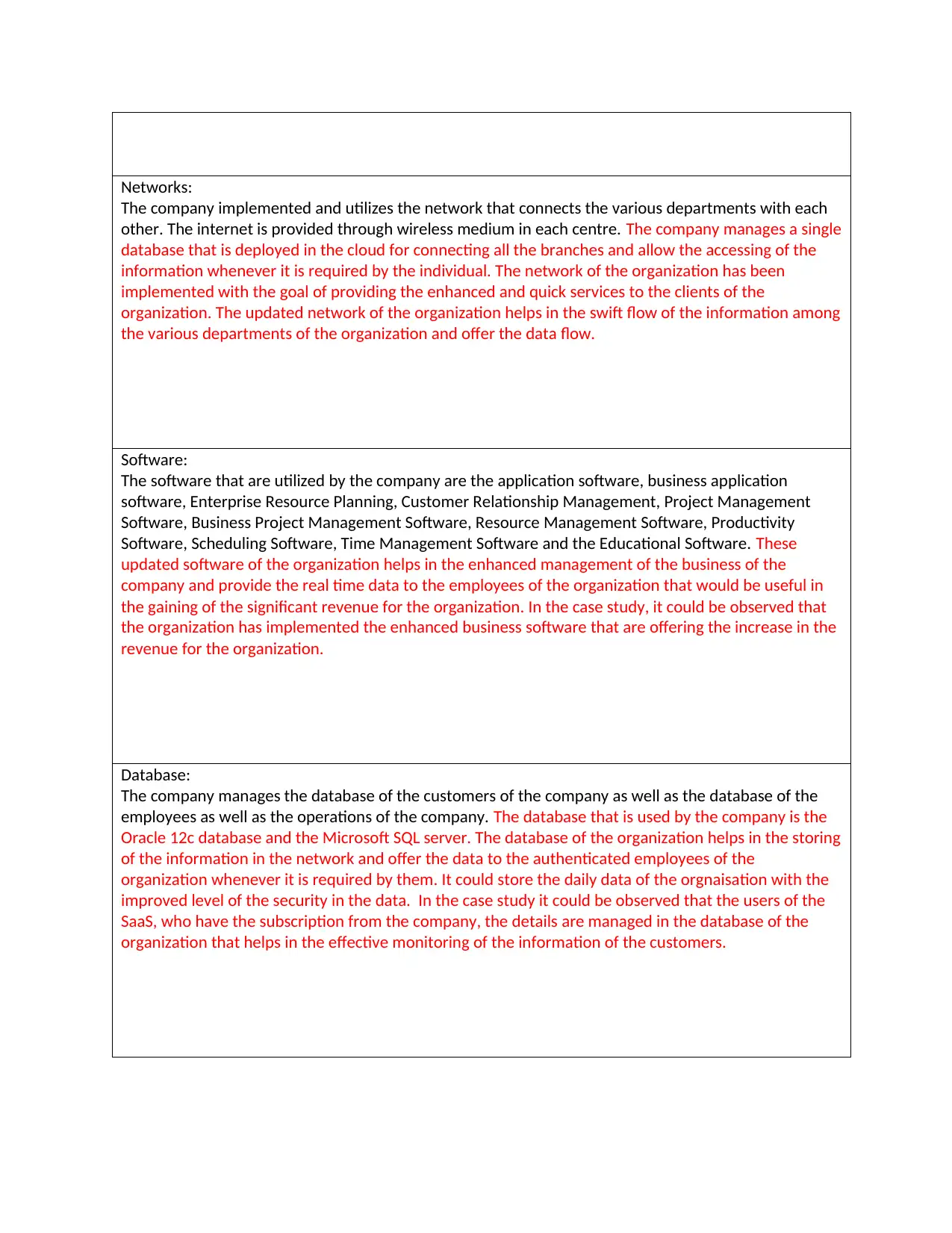
Networks:
The company implemented and utilizes the network that connects the various departments with each
other. The internet is provided through wireless medium in each centre. The company manages a single
database that is deployed in the cloud for connecting all the branches and allow the accessing of the
information whenever it is required by the individual. The network of the organization has been
implemented with the goal of providing the enhanced and quick services to the clients of the
organization. The updated network of the organization helps in the swift flow of the information among
the various departments of the organization and offer the data flow.
Software:
The software that are utilized by the company are the application software, business application
software, Enterprise Resource Planning, Customer Relationship Management, Project Management
Software, Business Project Management Software, Resource Management Software, Productivity
Software, Scheduling Software, Time Management Software and the Educational Software. These
updated software of the organization helps in the enhanced management of the business of the
company and provide the real time data to the employees of the organization that would be useful in
the gaining of the significant revenue for the organization. In the case study, it could be observed that
the organization has implemented the enhanced business software that are offering the increase in the
revenue for the organization.
Database:
The company manages the database of the customers of the company as well as the database of the
employees as well as the operations of the company. The database that is used by the company is the
Oracle 12c database and the Microsoft SQL server. The database of the organization helps in the storing
of the information in the network and offer the data to the authenticated employees of the
organization whenever it is required by them. It could store the daily data of the orgnaisation with the
improved level of the security in the data. In the case study it could be observed that the users of the
SaaS, who have the subscription from the company, the details are managed in the database of the
organization that helps in the effective monitoring of the information of the customers.
The company implemented and utilizes the network that connects the various departments with each
other. The internet is provided through wireless medium in each centre. The company manages a single
database that is deployed in the cloud for connecting all the branches and allow the accessing of the
information whenever it is required by the individual. The network of the organization has been
implemented with the goal of providing the enhanced and quick services to the clients of the
organization. The updated network of the organization helps in the swift flow of the information among
the various departments of the organization and offer the data flow.
Software:
The software that are utilized by the company are the application software, business application
software, Enterprise Resource Planning, Customer Relationship Management, Project Management
Software, Business Project Management Software, Resource Management Software, Productivity
Software, Scheduling Software, Time Management Software and the Educational Software. These
updated software of the organization helps in the enhanced management of the business of the
company and provide the real time data to the employees of the organization that would be useful in
the gaining of the significant revenue for the organization. In the case study, it could be observed that
the organization has implemented the enhanced business software that are offering the increase in the
revenue for the organization.
Database:
The company manages the database of the customers of the company as well as the database of the
employees as well as the operations of the company. The database that is used by the company is the
Oracle 12c database and the Microsoft SQL server. The database of the organization helps in the storing
of the information in the network and offer the data to the authenticated employees of the
organization whenever it is required by them. It could store the daily data of the orgnaisation with the
improved level of the security in the data. In the case study it could be observed that the users of the
SaaS, who have the subscription from the company, the details are managed in the database of the
organization that helps in the effective monitoring of the information of the customers.
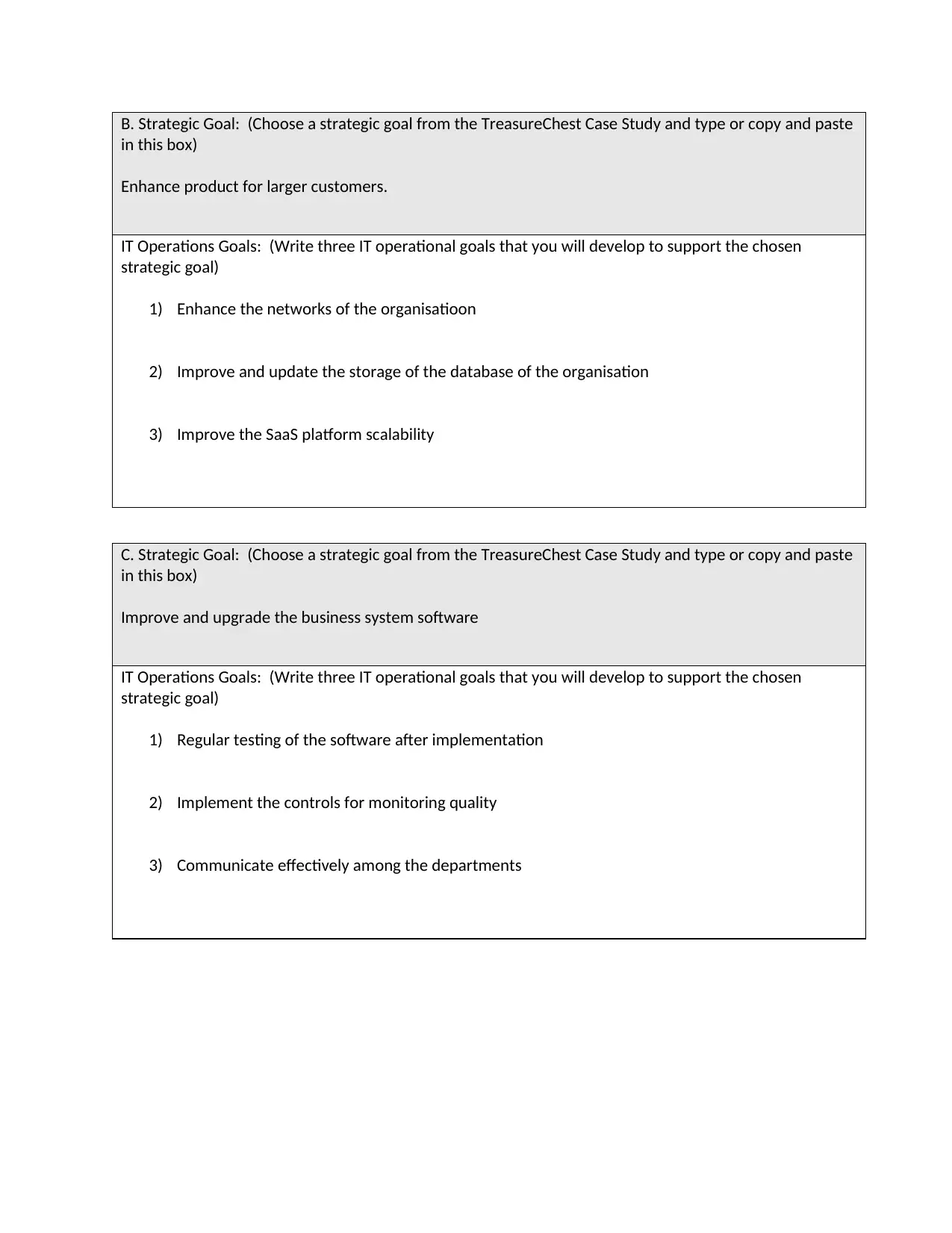
B. Strategic Goal: (Choose a strategic goal from the TreasureChest Case Study and type or copy and paste
in this box)
Enhance product for larger customers.
IT Operations Goals: (Write three IT operational goals that you will develop to support the chosen
strategic goal)
1) Enhance the networks of the organisatioon
2) Improve and update the storage of the database of the organisation
3) Improve the SaaS platform scalability
C. Strategic Goal: (Choose a strategic goal from the TreasureChest Case Study and type or copy and paste
in this box)
Improve and upgrade the business system software
IT Operations Goals: (Write three IT operational goals that you will develop to support the chosen
strategic goal)
1) Regular testing of the software after implementation
2) Implement the controls for monitoring quality
3) Communicate effectively among the departments
in this box)
Enhance product for larger customers.
IT Operations Goals: (Write three IT operational goals that you will develop to support the chosen
strategic goal)
1) Enhance the networks of the organisatioon
2) Improve and update the storage of the database of the organisation
3) Improve the SaaS platform scalability
C. Strategic Goal: (Choose a strategic goal from the TreasureChest Case Study and type or copy and paste
in this box)
Improve and upgrade the business system software
IT Operations Goals: (Write three IT operational goals that you will develop to support the chosen
strategic goal)
1) Regular testing of the software after implementation
2) Implement the controls for monitoring quality
3) Communicate effectively among the departments
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
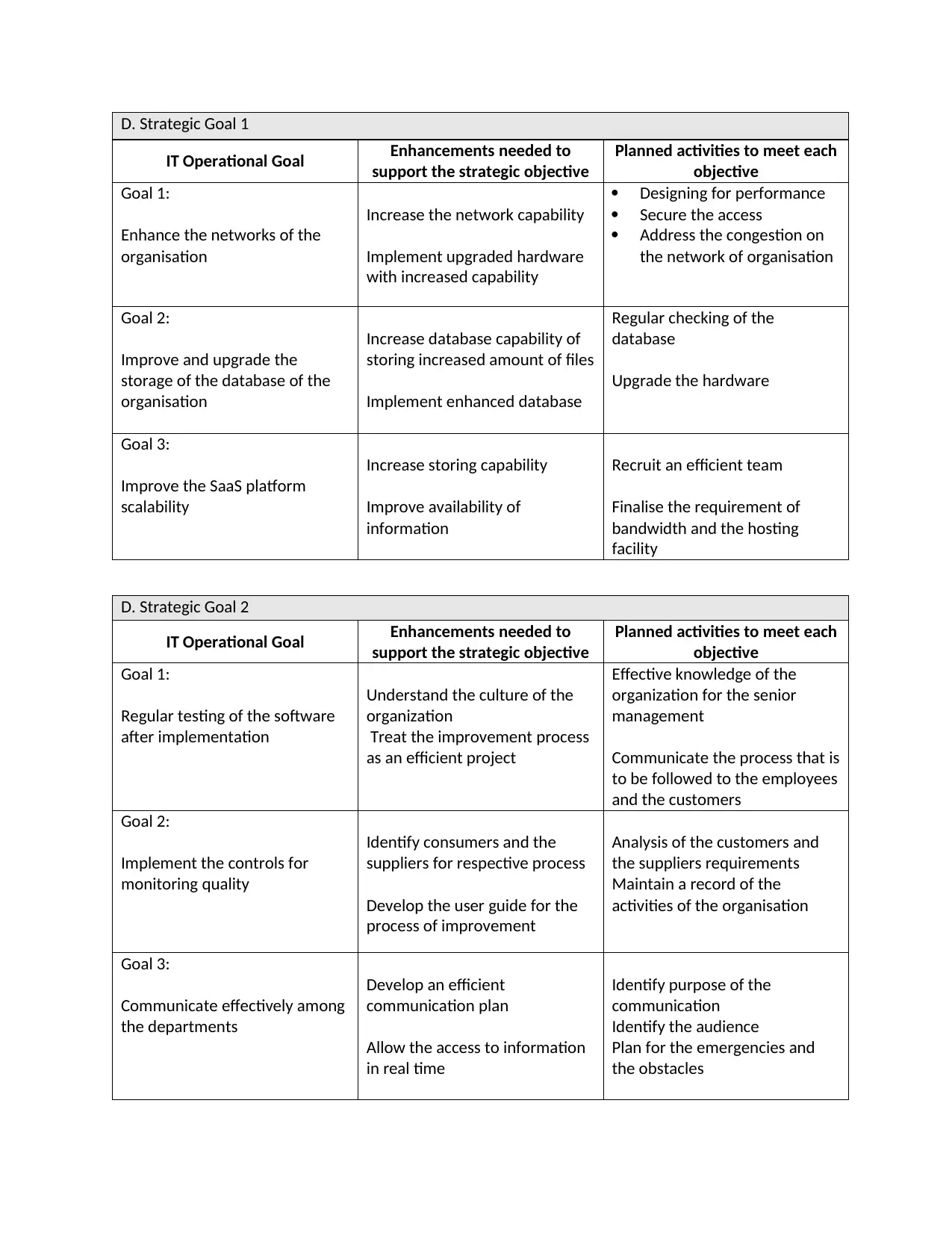
D. Strategic Goal 1
IT Operational Goal Enhancements needed to
support the strategic objective
Planned activities to meet each
objective
Goal 1:
Enhance the networks of the
organisation
Increase the network capability
Implement upgraded hardware
with increased capability
Designing for performance
Secure the access
Address the congestion on
the network of organisation
Goal 2:
Improve and upgrade the
storage of the database of the
organisation
Increase database capability of
storing increased amount of files
Implement enhanced database
Regular checking of the
database
Upgrade the hardware
Goal 3:
Improve the SaaS platform
scalability
Increase storing capability
Improve availability of
information
Recruit an efficient team
Finalise the requirement of
bandwidth and the hosting
facility
D. Strategic Goal 2
IT Operational Goal Enhancements needed to
support the strategic objective
Planned activities to meet each
objective
Goal 1:
Regular testing of the software
after implementation
Understand the culture of the
organization
Treat the improvement process
as an efficient project
Effective knowledge of the
organization for the senior
management
Communicate the process that is
to be followed to the employees
and the customers
Goal 2:
Implement the controls for
monitoring quality
Identify consumers and the
suppliers for respective process
Develop the user guide for the
process of improvement
Analysis of the customers and
the suppliers requirements
Maintain a record of the
activities of the organisation
Goal 3:
Communicate effectively among
the departments
Develop an efficient
communication plan
Allow the access to information
in real time
Identify purpose of the
communication
Identify the audience
Plan for the emergencies and
the obstacles
IT Operational Goal Enhancements needed to
support the strategic objective
Planned activities to meet each
objective
Goal 1:
Enhance the networks of the
organisation
Increase the network capability
Implement upgraded hardware
with increased capability
Designing for performance
Secure the access
Address the congestion on
the network of organisation
Goal 2:
Improve and upgrade the
storage of the database of the
organisation
Increase database capability of
storing increased amount of files
Implement enhanced database
Regular checking of the
database
Upgrade the hardware
Goal 3:
Improve the SaaS platform
scalability
Increase storing capability
Improve availability of
information
Recruit an efficient team
Finalise the requirement of
bandwidth and the hosting
facility
D. Strategic Goal 2
IT Operational Goal Enhancements needed to
support the strategic objective
Planned activities to meet each
objective
Goal 1:
Regular testing of the software
after implementation
Understand the culture of the
organization
Treat the improvement process
as an efficient project
Effective knowledge of the
organization for the senior
management
Communicate the process that is
to be followed to the employees
and the customers
Goal 2:
Implement the controls for
monitoring quality
Identify consumers and the
suppliers for respective process
Develop the user guide for the
process of improvement
Analysis of the customers and
the suppliers requirements
Maintain a record of the
activities of the organisation
Goal 3:
Communicate effectively among
the departments
Develop an efficient
communication plan
Allow the access to information
in real time
Identify purpose of the
communication
Identify the audience
Plan for the emergencies and
the obstacles
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
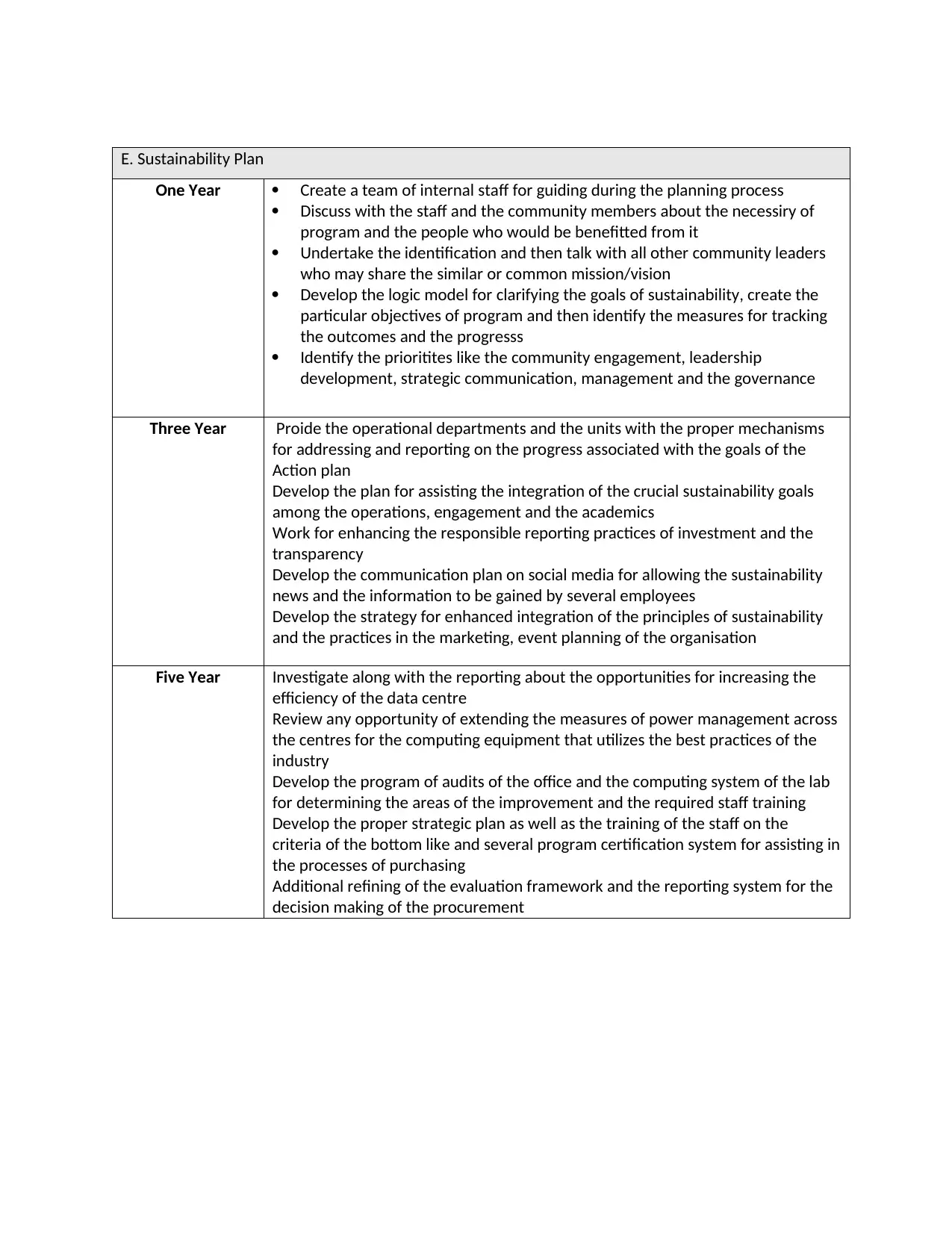
E. Sustainability Plan
One Year Create a team of internal staff for guiding during the planning process
Discuss with the staff and the community members about the necessiry of
program and the people who would be benefitted from it
Undertake the identification and then talk with all other community leaders
who may share the similar or common mission/vision
Develop the logic model for clarifying the goals of sustainability, create the
particular objectives of program and then identify the measures for tracking
the outcomes and the progresss
Identify the prioritites like the community engagement, leadership
development, strategic communication, management and the governance
Three Year Proide the operational departments and the units with the proper mechanisms
for addressing and reporting on the progress associated with the goals of the
Action plan
Develop the plan for assisting the integration of the crucial sustainability goals
among the operations, engagement and the academics
Work for enhancing the responsible reporting practices of investment and the
transparency
Develop the communication plan on social media for allowing the sustainability
news and the information to be gained by several employees
Develop the strategy for enhanced integration of the principles of sustainability
and the practices in the marketing, event planning of the organisation
Five Year Investigate along with the reporting about the opportunities for increasing the
efficiency of the data centre
Review any opportunity of extending the measures of power management across
the centres for the computing equipment that utilizes the best practices of the
industry
Develop the program of audits of the office and the computing system of the lab
for determining the areas of the improvement and the required staff training
Develop the proper strategic plan as well as the training of the staff on the
criteria of the bottom like and several program certification system for assisting in
the processes of purchasing
Additional refining of the evaluation framework and the reporting system for the
decision making of the procurement
One Year Create a team of internal staff for guiding during the planning process
Discuss with the staff and the community members about the necessiry of
program and the people who would be benefitted from it
Undertake the identification and then talk with all other community leaders
who may share the similar or common mission/vision
Develop the logic model for clarifying the goals of sustainability, create the
particular objectives of program and then identify the measures for tracking
the outcomes and the progresss
Identify the prioritites like the community engagement, leadership
development, strategic communication, management and the governance
Three Year Proide the operational departments and the units with the proper mechanisms
for addressing and reporting on the progress associated with the goals of the
Action plan
Develop the plan for assisting the integration of the crucial sustainability goals
among the operations, engagement and the academics
Work for enhancing the responsible reporting practices of investment and the
transparency
Develop the communication plan on social media for allowing the sustainability
news and the information to be gained by several employees
Develop the strategy for enhanced integration of the principles of sustainability
and the practices in the marketing, event planning of the organisation
Five Year Investigate along with the reporting about the opportunities for increasing the
efficiency of the data centre
Review any opportunity of extending the measures of power management across
the centres for the computing equipment that utilizes the best practices of the
industry
Develop the program of audits of the office and the computing system of the lab
for determining the areas of the improvement and the required staff training
Develop the proper strategic plan as well as the training of the staff on the
criteria of the bottom like and several program certification system for assisting in
the processes of purchasing
Additional refining of the evaluation framework and the reporting system for the
decision making of the procurement
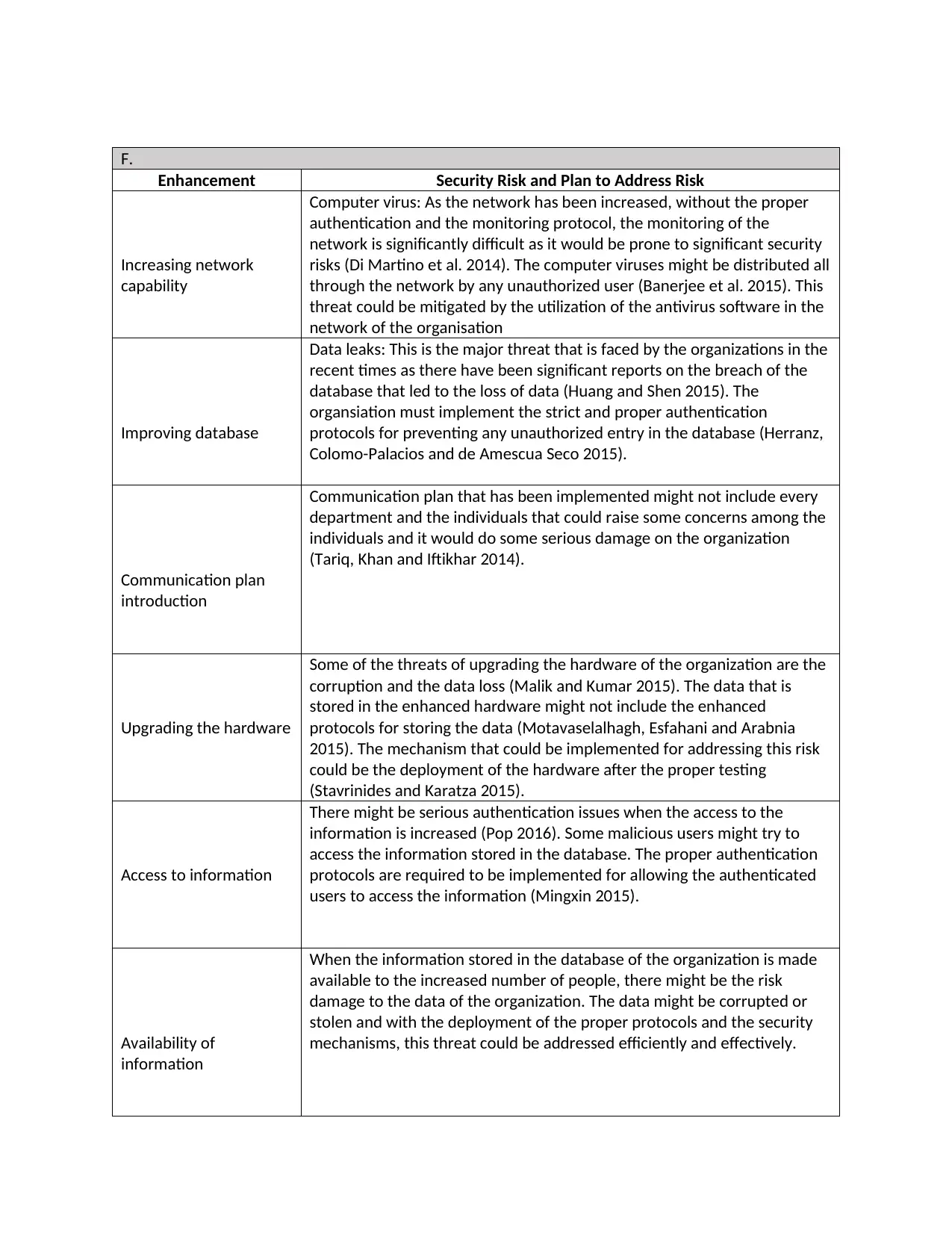
F.
Enhancement Security Risk and Plan to Address Risk
Increasing network
capability
Computer virus: As the network has been increased, without the proper
authentication and the monitoring protocol, the monitoring of the
network is significantly difficult as it would be prone to significant security
risks (Di Martino et al. 2014). The computer viruses might be distributed all
through the network by any unauthorized user (Banerjee et al. 2015). This
threat could be mitigated by the utilization of the antivirus software in the
network of the organisation
Improving database
Data leaks: This is the major threat that is faced by the organizations in the
recent times as there have been significant reports on the breach of the
database that led to the loss of data (Huang and Shen 2015). The
organsiation must implement the strict and proper authentication
protocols for preventing any unauthorized entry in the database (Herranz,
Colomo-Palacios and de Amescua Seco 2015).
Communication plan
introduction
Communication plan that has been implemented might not include every
department and the individuals that could raise some concerns among the
individuals and it would do some serious damage on the organization
(Tariq, Khan and Iftikhar 2014).
Upgrading the hardware
Some of the threats of upgrading the hardware of the organization are the
corruption and the data loss (Malik and Kumar 2015). The data that is
stored in the enhanced hardware might not include the enhanced
protocols for storing the data (Motavaselalhagh, Esfahani and Arabnia
2015). The mechanism that could be implemented for addressing this risk
could be the deployment of the hardware after the proper testing
(Stavrinides and Karatza 2015).
Access to information
There might be serious authentication issues when the access to the
information is increased (Pop 2016). Some malicious users might try to
access the information stored in the database. The proper authentication
protocols are required to be implemented for allowing the authenticated
users to access the information (Mingxin 2015).
Availability of
information
When the information stored in the database of the organization is made
available to the increased number of people, there might be the risk
damage to the data of the organization. The data might be corrupted or
stolen and with the deployment of the proper protocols and the security
mechanisms, this threat could be addressed efficiently and effectively.
Enhancement Security Risk and Plan to Address Risk
Increasing network
capability
Computer virus: As the network has been increased, without the proper
authentication and the monitoring protocol, the monitoring of the
network is significantly difficult as it would be prone to significant security
risks (Di Martino et al. 2014). The computer viruses might be distributed all
through the network by any unauthorized user (Banerjee et al. 2015). This
threat could be mitigated by the utilization of the antivirus software in the
network of the organisation
Improving database
Data leaks: This is the major threat that is faced by the organizations in the
recent times as there have been significant reports on the breach of the
database that led to the loss of data (Huang and Shen 2015). The
organsiation must implement the strict and proper authentication
protocols for preventing any unauthorized entry in the database (Herranz,
Colomo-Palacios and de Amescua Seco 2015).
Communication plan
introduction
Communication plan that has been implemented might not include every
department and the individuals that could raise some concerns among the
individuals and it would do some serious damage on the organization
(Tariq, Khan and Iftikhar 2014).
Upgrading the hardware
Some of the threats of upgrading the hardware of the organization are the
corruption and the data loss (Malik and Kumar 2015). The data that is
stored in the enhanced hardware might not include the enhanced
protocols for storing the data (Motavaselalhagh, Esfahani and Arabnia
2015). The mechanism that could be implemented for addressing this risk
could be the deployment of the hardware after the proper testing
(Stavrinides and Karatza 2015).
Access to information
There might be serious authentication issues when the access to the
information is increased (Pop 2016). Some malicious users might try to
access the information stored in the database. The proper authentication
protocols are required to be implemented for allowing the authenticated
users to access the information (Mingxin 2015).
Availability of
information
When the information stored in the database of the organization is made
available to the increased number of people, there might be the risk
damage to the data of the organization. The data might be corrupted or
stolen and with the deployment of the proper protocols and the security
mechanisms, this threat could be addressed efficiently and effectively.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

G. Operational Workflow
The operational workflow for increasing the number of customers for the
company who could avail the SaaS services includes the proper planning of the
implementation of the development process along with the communication plan
implementation all through the organization for providing the employees and the
managers with the general idea about what is going to happen with the
implementation of the changes desired. Then the proper suppliers are required
to be selected for procuring the required hardware and the software. The
suppliers would provide the required materials for effective deployment. Then
the software would be implemented with the appropriate policies and the
procedures for allowing the efficient and controlled use of the materials.
References
Banerjee, S., Adhikari, M., Kar, S. and Biswas, U., 2015. Development and analysis of a new cloudlet
allocation strategy for QoS improvement in cloud. Arabian Journal for Science and Engineering, 40(5),
pp.1409-1425.
Di Martino, C., Kalbarczyk, Z., Iyer, R.K., Goel, G., Sarkar, S. and Ganesan, R., 2014, May. Characterization
of operational failures from a business data processing saas platform. In Companion Proceedings of the
36th International Conference on Software Engineering (pp. 195-204). ACM.
Herranz, E., Colomo-Palacios, R. and de Amescua Seco, A., 2015, September. Gamiware: a gamification
platform for software process improvement. In European Conference on Software Process
Improvement (pp. 127-139). Springer, Cham.
Huang, K.C. and Shen, B.J., 2015. Service deployment strategies for efficient execution of composite SaaS
applications on cloud platform. Journal of Systems and Software, 107, pp.127-141.
Malik, R. and Kumar, P., 2015. Cloud computing security improvement using Diffie Hellman and
AES. International Journal of Computer Applications, 118(1).
Mingxin, W., 2015. Research on improvement of task scheduling algorithm in cloud computing. Applied
Mathematics & Information Sciences, 9(1), p.507.
The operational workflow for increasing the number of customers for the
company who could avail the SaaS services includes the proper planning of the
implementation of the development process along with the communication plan
implementation all through the organization for providing the employees and the
managers with the general idea about what is going to happen with the
implementation of the changes desired. Then the proper suppliers are required
to be selected for procuring the required hardware and the software. The
suppliers would provide the required materials for effective deployment. Then
the software would be implemented with the appropriate policies and the
procedures for allowing the efficient and controlled use of the materials.
References
Banerjee, S., Adhikari, M., Kar, S. and Biswas, U., 2015. Development and analysis of a new cloudlet
allocation strategy for QoS improvement in cloud. Arabian Journal for Science and Engineering, 40(5),
pp.1409-1425.
Di Martino, C., Kalbarczyk, Z., Iyer, R.K., Goel, G., Sarkar, S. and Ganesan, R., 2014, May. Characterization
of operational failures from a business data processing saas platform. In Companion Proceedings of the
36th International Conference on Software Engineering (pp. 195-204). ACM.
Herranz, E., Colomo-Palacios, R. and de Amescua Seco, A., 2015, September. Gamiware: a gamification
platform for software process improvement. In European Conference on Software Process
Improvement (pp. 127-139). Springer, Cham.
Huang, K.C. and Shen, B.J., 2015. Service deployment strategies for efficient execution of composite SaaS
applications on cloud platform. Journal of Systems and Software, 107, pp.127-141.
Malik, R. and Kumar, P., 2015. Cloud computing security improvement using Diffie Hellman and
AES. International Journal of Computer Applications, 118(1).
Mingxin, W., 2015. Research on improvement of task scheduling algorithm in cloud computing. Applied
Mathematics & Information Sciences, 9(1), p.507.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Motavaselalhagh, F., Esfahani, F.S. and Arabnia, H.R., 2015. Knowledge-based adaptable scheduler for
SaaS providers in cloud computing. Human-centric Computing and Information Sciences, 5(1), p.16.
Pop, D., 2016. Machine learning and cloud computing: Survey of distributed and saas solutions. arXiv
preprint arXiv:1603.08767.
Stavrinides, G.L. and Karatza, H.D., 2015, August. A cost-effective and qos-aware approach to scheduling
real-time workflow applications in paas and saas clouds. In 2015 3rd International Conference on Future
Internet of Things and Cloud (pp. 231-239). IEEE.
Tariq, A., Khan, S.A. and Iftikhar, S., 2014, December. Requirements Engineering process for Software-as-
a-Service (SaaS) cloud environment. In 2014 International Conference on Emerging Technologies
(ICET) (pp. 13-18). IEEE.
SaaS providers in cloud computing. Human-centric Computing and Information Sciences, 5(1), p.16.
Pop, D., 2016. Machine learning and cloud computing: Survey of distributed and saas solutions. arXiv
preprint arXiv:1603.08767.
Stavrinides, G.L. and Karatza, H.D., 2015, August. A cost-effective and qos-aware approach to scheduling
real-time workflow applications in paas and saas clouds. In 2015 3rd International Conference on Future
Internet of Things and Cloud (pp. 231-239). IEEE.
Tariq, A., Khan, S.A. and Iftikhar, S., 2014, December. Requirements Engineering process for Software-as-
a-Service (SaaS) cloud environment. In 2014 International Conference on Emerging Technologies
(ICET) (pp. 13-18). IEEE.
1 out of 8
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





