IT Risk Assessment Case Study: BYOD Policy at Altium Limited
VerifiedAdded on 2019/10/31
|15
|6227
|173
Case Study
AI Summary
This case study examines the IT risk assessment for a Bring Your Own Device (BYOD) implementation at Altium Limited, an Australian IT and software development company. The report analyzes the risks associated with BYOD, including data security, authentication problems, and vulnerabilities in personal devices. It includes an executive summary, a review of project impact, and a detailed risk assessment process. The assessment covers risk identification, qualitative and quantitative analysis, and risk response planning. The report emphasizes the importance of data security in the context of Altium Limited's operations, providing insights into the potential threats and mitigation strategies. The study highlights the need for a well-developed BYOD policy and the use of project management tools to ensure successful implementation, addressing both the positive and negative aspects of BYOD, such as potential cost savings and increased security concerns. The document aims to interface between technologists and business stakeholders, facilitating effective decision-making for mitigating the identified risks and threats.

Running head: IT RISK ASSESSMENT CASE STUDY
Bring your own Device (BYOD): IT Risk Assessment Case Study
Name of the Student
Name of the University
Author’s Note
Bring your own Device (BYOD): IT Risk Assessment Case Study
Name of the Student
Name of the University
Author’s Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1IT RISK ASSESSMENT CASE STUDY
Table of Contents
Executive Summary.........................................................................................................................2
With respect to Financial Service Sector.........................................................................................3
Security Posture...............................................................................................................................4
Threats, Vulnerabilities and Consequences Assessment.................................................................6
Risk Identification.......................................................................................................................7
Qualitative Risk Analysis............................................................................................................8
Quantitative Risk Analysis..........................................................................................................9
Risk Response Planning..............................................................................................................9
Procurement Planning..................................................................................................................9
Data Security...................................................................................................................................9
Conclusion.....................................................................................................................................10
References......................................................................................................................................12
Table of Contents
Executive Summary.........................................................................................................................2
With respect to Financial Service Sector.........................................................................................3
Security Posture...............................................................................................................................4
Threats, Vulnerabilities and Consequences Assessment.................................................................6
Risk Identification.......................................................................................................................7
Qualitative Risk Analysis............................................................................................................8
Quantitative Risk Analysis..........................................................................................................9
Risk Response Planning..............................................................................................................9
Procurement Planning..................................................................................................................9
Data Security...................................................................................................................................9
Conclusion.....................................................................................................................................10
References......................................................................................................................................12

2IT RISK ASSESSMENT CASE STUDY
Executive Summary
As mobile devices that are becoming more dominant towards customer products with
business world and these devices are essential for changing the way to business. The
organizations and corporations should incorporate a policy to allow utilization of BYOD devices
in order to protect their personal data, employee details and customer information. Here, in this
report, Altium Limited organization required to implement BYOD policy in their business in
order to improve business growth and gradual increment of profitability. The Altium Limited
organization operates in Australian IT and Software development Sector where the senior
executives of business and technology divisions planned to implement BYOD (Bring Your Own
Device) policy in form of project. Altium Limited organization (formerly known as Protel), is an
Australian-owned public company that specialized in providing Printed Circuit Boards (PCBs) to
clients as Volkswagen, Toyota, Siemens, Philips, Microsoft, Lenovo, HP, Honeywell and others.
The organization has addressable market size of $500M USD, and they captured 10% of the
entire mainstream market value. The organization has operational centers in Australia, China and
Sydney, Shanghai, USA, and San Diego.
The agenda of the study and corresponding report is to devise a risk management process
with setting out all IT issues, security concerns and associated threats in BYOD policy. The risk
management is carried out identifying risks, assessing risk outcomes, and formulating risk
mitigation plan. The risk assessment portrayed several issues along with risk register, detailed
overview of potential threats that should be considered while risk assessment is conducted. In
order to prepare the prologue of the risk assessment in this report; the project review is
demonstrated. Project review section clearly mentions about the Bring Your Own Device
(BYOD) policy and this section discussed about project deliverables, assumptions, associated
risk concerns, and an overall plan of implementation. The review of project impact section stated
about the project importance considering Australian IT and Software Development Sector as
Altium Limited organization is operating in same sector. Project impact stated the influence of
bringing personal device into workplace and related the influences with how the concept of work
process could improve entire business activity along with mitigating some basic work issues.
In later section, risk assessment was performed with following practical approach of risk
mitigation and handling in Altium Limited organizational context. The risk management and
overall threat assessment is conducted with following some simple steps such as risk
identification, preparation of risk register, risk assessment, and risk mitigation planning. Risk
assessment contributed the outcomes of the assessment over the study; so that while
implementation of BYOD policy, the organizational administration could take essential
precautions for preventing the risk situations. Furthermore, another section is included to provide
closer look at data security risks for obvious reasons. Altium Limited organization operates in
Australian IT and Software Development Sector; therefore, due to certain business activities, the
organization required to process huge amount of data daily and work with large amount of data.
For this reason, it is quite essential to provide greater emphasize over data security risks while
implementing BYOD project in Altium Limited organizational context.
In an overall, the report provided major findings about certain risks that Australian IT and
Software Development Sector could face. In “project impact review” section, risks are stated
from previous studies with mentioning their potential harmfulness to ruin organizational
Executive Summary
As mobile devices that are becoming more dominant towards customer products with
business world and these devices are essential for changing the way to business. The
organizations and corporations should incorporate a policy to allow utilization of BYOD devices
in order to protect their personal data, employee details and customer information. Here, in this
report, Altium Limited organization required to implement BYOD policy in their business in
order to improve business growth and gradual increment of profitability. The Altium Limited
organization operates in Australian IT and Software development Sector where the senior
executives of business and technology divisions planned to implement BYOD (Bring Your Own
Device) policy in form of project. Altium Limited organization (formerly known as Protel), is an
Australian-owned public company that specialized in providing Printed Circuit Boards (PCBs) to
clients as Volkswagen, Toyota, Siemens, Philips, Microsoft, Lenovo, HP, Honeywell and others.
The organization has addressable market size of $500M USD, and they captured 10% of the
entire mainstream market value. The organization has operational centers in Australia, China and
Sydney, Shanghai, USA, and San Diego.
The agenda of the study and corresponding report is to devise a risk management process
with setting out all IT issues, security concerns and associated threats in BYOD policy. The risk
management is carried out identifying risks, assessing risk outcomes, and formulating risk
mitigation plan. The risk assessment portrayed several issues along with risk register, detailed
overview of potential threats that should be considered while risk assessment is conducted. In
order to prepare the prologue of the risk assessment in this report; the project review is
demonstrated. Project review section clearly mentions about the Bring Your Own Device
(BYOD) policy and this section discussed about project deliverables, assumptions, associated
risk concerns, and an overall plan of implementation. The review of project impact section stated
about the project importance considering Australian IT and Software Development Sector as
Altium Limited organization is operating in same sector. Project impact stated the influence of
bringing personal device into workplace and related the influences with how the concept of work
process could improve entire business activity along with mitigating some basic work issues.
In later section, risk assessment was performed with following practical approach of risk
mitigation and handling in Altium Limited organizational context. The risk management and
overall threat assessment is conducted with following some simple steps such as risk
identification, preparation of risk register, risk assessment, and risk mitigation planning. Risk
assessment contributed the outcomes of the assessment over the study; so that while
implementation of BYOD policy, the organizational administration could take essential
precautions for preventing the risk situations. Furthermore, another section is included to provide
closer look at data security risks for obvious reasons. Altium Limited organization operates in
Australian IT and Software Development Sector; therefore, due to certain business activities, the
organization required to process huge amount of data daily and work with large amount of data.
For this reason, it is quite essential to provide greater emphasize over data security risks while
implementing BYOD project in Altium Limited organizational context.
In an overall, the report provided major findings about certain risks that Australian IT and
Software Development Sector could face. In “project impact review” section, risks are stated
from previous studies with mentioning their potential harmfulness to ruin organizational
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3IT RISK ASSESSMENT CASE STUDY
activities and integrity. The risk assessment section is prepared to state a particular methodology
for the risk assessment process for Altium Limited organization so that senior executives,
technologists, and business stakeholders. As a risk assessment lead in Altium Limited, the report
is aimed to interface between technologists and business stakeholders so that security and BYOD
potential risks can be conveyed to all levels of stakeholders. Business stakeholders can be able to
identify potential technical difficulties in the project and technologists can be able to translate the
difficulties into risk assessment. The risk assessment can provide facilitation to perform effective
decision-making from stakeholders for mitigating the identified risks and threats.
With respect to Financial Service Sector
In current organization and corporation aspect, mobile devices are more consumer-
oriented and the devices are susceptible to changes the way of business. The computing power in
business entirely casts influence over allowing consumers and employees to replace traditional
end-user computing device with laptop (Al Ayubi et al., 2016). The BYOD concept increase
security concerns and puts every organization in verge of multiple risks and threats.
Organizations in different sectors such as banking, retailing, information technology, financial,
and online clientele, have significant level of consideration for incorporating BYOD into
business. The organizations need to deal with new level of security considerations and data
threats with personal and corporate data. The risk management over personal and business data
should consider appropriate level of risk mitigation planning (Faulds et al., 2016). Therefore, the
complications in this situation should devise a policy as protection of data, staffs, and customer
is critical for any business to grow with its potential to the fullest. Ownership of data is becoming
more of an issue within business that operates in regulated market.
Several organizations have planned to implement “Bring Your Own Device” (BYOD)
policy so that employees can be allowed to utilize their favorite devices with bringing down
costs to accommodate devices. The BYOD policy-based work model is expected to complicate
the data control and policies for organizations that can increase importance of having well-
developed policy (Laudon & Laudon, 2016). Successful implementation of mobile device policy
can incorporate BYOD initiative into business. The entire life cycle of project can be covered
with BYOD initiatives as well. The project and outcomes can be achieved with utilization of
discipline of project management; however, the PMP strategy is not expected to provide
guarantee though, the PMP strategy can increase chances of meeting all planned outcomes
(Rittinghouse & Ransome, 2016). The project management tools are necessary for Altium
Limited organization to successfully implement BYOD project inside IT department and
development workforce. Every project is ephemeral with pre-defined start and derived end date;
the projects do not completely depend over on-going work activities and responsibilities
(Steelman, Lacity & Sabherwal, 2016). In this Altium Limited organizational aspect, the BYOD
project is part of planned deliverables and a defined period.
The project deliverables are mentioned as per project initiatives and objectives; the
deliverables included all activities in a short overview.
1. First and primary activity for BYOD project should be to prepare Bring Your
Own Device (BYOD) policy. The policy should be documented with clear
understanding about the policy guidelines, all aspects that should be obeyed from
employees and how the policy should work (Kearns, 2016). The project
activities and integrity. The risk assessment section is prepared to state a particular methodology
for the risk assessment process for Altium Limited organization so that senior executives,
technologists, and business stakeholders. As a risk assessment lead in Altium Limited, the report
is aimed to interface between technologists and business stakeholders so that security and BYOD
potential risks can be conveyed to all levels of stakeholders. Business stakeholders can be able to
identify potential technical difficulties in the project and technologists can be able to translate the
difficulties into risk assessment. The risk assessment can provide facilitation to perform effective
decision-making from stakeholders for mitigating the identified risks and threats.
With respect to Financial Service Sector
In current organization and corporation aspect, mobile devices are more consumer-
oriented and the devices are susceptible to changes the way of business. The computing power in
business entirely casts influence over allowing consumers and employees to replace traditional
end-user computing device with laptop (Al Ayubi et al., 2016). The BYOD concept increase
security concerns and puts every organization in verge of multiple risks and threats.
Organizations in different sectors such as banking, retailing, information technology, financial,
and online clientele, have significant level of consideration for incorporating BYOD into
business. The organizations need to deal with new level of security considerations and data
threats with personal and corporate data. The risk management over personal and business data
should consider appropriate level of risk mitigation planning (Faulds et al., 2016). Therefore, the
complications in this situation should devise a policy as protection of data, staffs, and customer
is critical for any business to grow with its potential to the fullest. Ownership of data is becoming
more of an issue within business that operates in regulated market.
Several organizations have planned to implement “Bring Your Own Device” (BYOD)
policy so that employees can be allowed to utilize their favorite devices with bringing down
costs to accommodate devices. The BYOD policy-based work model is expected to complicate
the data control and policies for organizations that can increase importance of having well-
developed policy (Laudon & Laudon, 2016). Successful implementation of mobile device policy
can incorporate BYOD initiative into business. The entire life cycle of project can be covered
with BYOD initiatives as well. The project and outcomes can be achieved with utilization of
discipline of project management; however, the PMP strategy is not expected to provide
guarantee though, the PMP strategy can increase chances of meeting all planned outcomes
(Rittinghouse & Ransome, 2016). The project management tools are necessary for Altium
Limited organization to successfully implement BYOD project inside IT department and
development workforce. Every project is ephemeral with pre-defined start and derived end date;
the projects do not completely depend over on-going work activities and responsibilities
(Steelman, Lacity & Sabherwal, 2016). In this Altium Limited organizational aspect, the BYOD
project is part of planned deliverables and a defined period.
The project deliverables are mentioned as per project initiatives and objectives; the
deliverables included all activities in a short overview.
1. First and primary activity for BYOD project should be to prepare Bring Your
Own Device (BYOD) policy. The policy should be documented with clear
understanding about the policy guidelines, all aspects that should be obeyed from
employees and how the policy should work (Kearns, 2016). The project
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4IT RISK ASSESSMENT CASE STUDY
management can follow Plan-Do-Check-Act (PDCA) cycle over the entire
lifecycle.
2. Next activity that should be included into the list of deliverable is to declare the
BYOD policy and the policy should be clearly described among all employees so
that they can easily follow the guidelines and maintain the rules.
3. Furthermore, the project deliverable is to provide necessary training and start a
pilot project (Sadgrove, 2016). The aim of the pilot project is to start the policy
for some period to assess the employees as in whether they are capable of
following the policy guidelines and rules or not. In case, any employee failed to
follow the policy guideline; they should be trained for a certain time.
4. Furthermore, the project deliverable should be to activate the BYOD policy into
the workflow of Altium Limited organization.
The assumptions are considered to conduct the project within the boundary or the entire
work process. The major assumptions in the project are mentioned as following:
a) The employees should understand the BYOD policy importance and should
attempt to follow the guidelines and rules (Singh, Chan & Zulkefli, 2017).
b) The BYOD policy should written with considering all aspects and depicting
individual guidelines as well.
c) The policy should be incorporated into existing work process of Altium Limited
organization without hampering the overall profitability and stability of workflow
(Sebescen & Vitak, 2017).
However, some risk concerns exist in the project as in data security risks, authentication
problems, and putting personal and corporate data at stake by having vulnerabilities in personal
devices.
Security Posture
BYOD project has some major impacts on the implementation process; the Altium
Limited organization should follow this section to realize whether the organization can meet
business requirements or not. BYOD project influences are included in this section so that
significant benefits of BYOD project can be addressed (Martinez, Borycki & Courtney, 2017).
The review of project impacts are considered and mentioned as following:
Saving of Expenditure: Initially, the assumption about BYOD project is that the project
have ability to being down expenditure as the employees are using their personal devices in case
of using organization provided devices (Peltier, 2016). However, recent statistics from study
revealed that 67% of the European IT professionals felt that BYOD could increase cost and to
some extent, this conception could be right. It is clear that BYOD policy is major part for starting
a business case; though these costs required to be specified and offset costs against other
advantages (Tanimoto et al., 2017). Therefore, the question arises how the cost increased; the
discussion pinpointed the reasons here.
Firstly, there is vocal minority that will require BYOD scheme for several employees
who does not want to be involved in these initiatives. The employees over median incomes are
not agreed to be involved in the scheme as they are unprepared and they refuse to bear any cost
management can follow Plan-Do-Check-Act (PDCA) cycle over the entire
lifecycle.
2. Next activity that should be included into the list of deliverable is to declare the
BYOD policy and the policy should be clearly described among all employees so
that they can easily follow the guidelines and maintain the rules.
3. Furthermore, the project deliverable is to provide necessary training and start a
pilot project (Sadgrove, 2016). The aim of the pilot project is to start the policy
for some period to assess the employees as in whether they are capable of
following the policy guidelines and rules or not. In case, any employee failed to
follow the policy guideline; they should be trained for a certain time.
4. Furthermore, the project deliverable should be to activate the BYOD policy into
the workflow of Altium Limited organization.
The assumptions are considered to conduct the project within the boundary or the entire
work process. The major assumptions in the project are mentioned as following:
a) The employees should understand the BYOD policy importance and should
attempt to follow the guidelines and rules (Singh, Chan & Zulkefli, 2017).
b) The BYOD policy should written with considering all aspects and depicting
individual guidelines as well.
c) The policy should be incorporated into existing work process of Altium Limited
organization without hampering the overall profitability and stability of workflow
(Sebescen & Vitak, 2017).
However, some risk concerns exist in the project as in data security risks, authentication
problems, and putting personal and corporate data at stake by having vulnerabilities in personal
devices.
Security Posture
BYOD project has some major impacts on the implementation process; the Altium
Limited organization should follow this section to realize whether the organization can meet
business requirements or not. BYOD project influences are included in this section so that
significant benefits of BYOD project can be addressed (Martinez, Borycki & Courtney, 2017).
The review of project impacts are considered and mentioned as following:
Saving of Expenditure: Initially, the assumption about BYOD project is that the project
have ability to being down expenditure as the employees are using their personal devices in case
of using organization provided devices (Peltier, 2016). However, recent statistics from study
revealed that 67% of the European IT professionals felt that BYOD could increase cost and to
some extent, this conception could be right. It is clear that BYOD policy is major part for starting
a business case; though these costs required to be specified and offset costs against other
advantages (Tanimoto et al., 2017). Therefore, the question arises how the cost increased; the
discussion pinpointed the reasons here.
Firstly, there is vocal minority that will require BYOD scheme for several employees
who does not want to be involved in these initiatives. The employees over median incomes are
not agreed to be involved in the scheme as they are unprepared and they refuse to bear any cost

5IT RISK ASSESSMENT CASE STUDY
for personal device (Filkins et al., 2016). This represents that in case someone wants to start a
company based program then the employer need to provide adequate financial support and
incentive for buying personal device. Furthermore, when money is provided to the employees are
part of income tax, therefore, privately purchased device cost will be increased with non-
reclaimable sales tax (VAT) (Trewin et al., 2016). Hence, the actual cost will be considered
exponentially more than the organization has bought; if both costs are compared side-by-side. In
similar perspective, the Smartphone Allowance is between AU$30 to AU$50 and this expense
can be more rather than corporate negotiations.
Secondly, the increased Wi-Fi coverage is another reason for growing BYOD policy
scheme and at the same time, the organization needs to provide better Wi-Fi coverage than
before due to BYOD initiatives (Russell, 2016; Lobelo et al., 2016). When employees are
capable of bringing personal devices such as laptops, phone, and tablet using IP addresses; then
the existing network should be upgraded. This issue has tendency to occur in educational
institutions where numerous students need Wi-Fi coverage; however, Altium Limited
organization needs to consider this issue as well.
Finally, due to security risks in BYOD policy, the organization needs to consider Mobile
Device Management (MDM) with security solution. The security solution should be able to
catalogue the devices, and the security policies should be applied (Shedden et al., 2016). Once, a
device is either lost or stolen; the devices should be wiped clean or devices should be locked
before the data is visible to unauthorized persons.
There are not only negative aspects of the BYOD policy; some positive aspects are
visible with BYOD policy as well. The positive aspects are listed as following:
A. The organization can offer top-up values to the employees so that they can buy
better devices for helping to improve productivity and work performance
(Souppaya & Scarfone, 2016).
B. The employee ownership of device may convey that the devices can last longer
as employees will take care of their devices.
C. The organization can have better profit in support section, as the support goes
down at significant level. For instance, employees can perform the upgrade of
iOS device typically and therefore, no intervention from employer is required
(Reid & Pechenkina, 2016). The employer does not need to be involved in the
support work when BYOD scheme is activated; employee forum and discussion
works much better and reducing cost as well.
Increment in Productivity: Productivity is another important part of BYOD business
case that acts as primary driver. Primary reason is that BYOD can bring increment in
productivity. In spite of 30 minutes of email interaction that every employee needs to do before
starting work and that mails were sent after their previous shift hours (Dorsemaine et al., 2017).
Now, in BYOD scheme, the employees can check and view the emails at their home, on the way
to office or while sitting at home on following evening. This reason increases work hours inside
office at conservative estimate of 10%. Whereas, if this is viewed in another aspect; employees
can take advantage of BYOD with having personal devices for Twitter and Facebook during
work hours (Gillon, 2017; Dawson, 2016). However, those employees will be easily identified
for personal device (Filkins et al., 2016). This represents that in case someone wants to start a
company based program then the employer need to provide adequate financial support and
incentive for buying personal device. Furthermore, when money is provided to the employees are
part of income tax, therefore, privately purchased device cost will be increased with non-
reclaimable sales tax (VAT) (Trewin et al., 2016). Hence, the actual cost will be considered
exponentially more than the organization has bought; if both costs are compared side-by-side. In
similar perspective, the Smartphone Allowance is between AU$30 to AU$50 and this expense
can be more rather than corporate negotiations.
Secondly, the increased Wi-Fi coverage is another reason for growing BYOD policy
scheme and at the same time, the organization needs to provide better Wi-Fi coverage than
before due to BYOD initiatives (Russell, 2016; Lobelo et al., 2016). When employees are
capable of bringing personal devices such as laptops, phone, and tablet using IP addresses; then
the existing network should be upgraded. This issue has tendency to occur in educational
institutions where numerous students need Wi-Fi coverage; however, Altium Limited
organization needs to consider this issue as well.
Finally, due to security risks in BYOD policy, the organization needs to consider Mobile
Device Management (MDM) with security solution. The security solution should be able to
catalogue the devices, and the security policies should be applied (Shedden et al., 2016). Once, a
device is either lost or stolen; the devices should be wiped clean or devices should be locked
before the data is visible to unauthorized persons.
There are not only negative aspects of the BYOD policy; some positive aspects are
visible with BYOD policy as well. The positive aspects are listed as following:
A. The organization can offer top-up values to the employees so that they can buy
better devices for helping to improve productivity and work performance
(Souppaya & Scarfone, 2016).
B. The employee ownership of device may convey that the devices can last longer
as employees will take care of their devices.
C. The organization can have better profit in support section, as the support goes
down at significant level. For instance, employees can perform the upgrade of
iOS device typically and therefore, no intervention from employer is required
(Reid & Pechenkina, 2016). The employer does not need to be involved in the
support work when BYOD scheme is activated; employee forum and discussion
works much better and reducing cost as well.
Increment in Productivity: Productivity is another important part of BYOD business
case that acts as primary driver. Primary reason is that BYOD can bring increment in
productivity. In spite of 30 minutes of email interaction that every employee needs to do before
starting work and that mails were sent after their previous shift hours (Dorsemaine et al., 2017).
Now, in BYOD scheme, the employees can check and view the emails at their home, on the way
to office or while sitting at home on following evening. This reason increases work hours inside
office at conservative estimate of 10%. Whereas, if this is viewed in another aspect; employees
can take advantage of BYOD with having personal devices for Twitter and Facebook during
work hours (Gillon, 2017; Dawson, 2016). However, those employees will be easily identified
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6IT RISK ASSESSMENT CASE STUDY
when they will seek for more time in other ways. BYOD can improve daily productivity of
workforce by providing technology to people without having access to technology at all.
Meeting Employees Satisfaction at work: BYOD is identified as tool for attracting and
retaining employees taking younger staffs at work. Recent studies have presented that 20-30 year
aged employees conveyed that 50% of them consider BYOD as a right not a privilege (Martinelli
& Milosevic, 2016). Therefore, as year goes around, if BYOD is not implemented; some bright
employees may leave the workforce soon.
Understanding Customer needs and requirements: The retail organizations are utilizing
consumer devices in stores. The BYOD can provide better situations for presenting marketing
materials (Goldes et al., 2017). Retail employees can check about available products and
customer can get instant information about inventory.
Flexibility in Operation: The operational flexibility may be overlooked however, for
some reasons, it is most important part of BYOD scheme.
Firstly, employees can be forced to do work from home or can be provided with proper
accommodation so that they can work from home at situations of industrial actions, bad or
unfavorable weather, and even terrorism (M'manga et al., 2017). BYOD includes the aspect of
unplanned home working so that lost time can be used with workforce.
Secondly, in any industry, in presence of several mergers and acquisitions, BYOD policy
can help the employees by treating new company devices as under BYOD guidelines. The
organization can incorporate BYOD standards with mergers as well.
Finally, the organization within higher growth of business can speed up new employee
outputs with BYOD policy (Vithanwattana, Mapp & George, 2017). In similar point of view,
employer can have short-term workers over BYOD policy so that time spent can be reduced
rather spending time over provisioning new devices.
Threats, Vulnerabilities and Consequences Assessment
Dove (2016) opined that during project lifecycle, the risks may occur are often identified
as allowing project manager for recognize and treat them as risks. The risks can cast influence
over project in terms of cost, time, deliverable quality, and morale. The risk management
planning included definition as the project definition, monitoring, and controlling risks through
the project. Risk assessment and management plan deals with accepting risk into planning,
tracking and updating risk plan along with removing risk form the plan (Halford, 2016). The
escalation of risk can be made when it is necessary. Maintaining existing risk plan allows project
manager to set out expectations for multiple stakeholders and sponsors, allowing team to focus
over project work along with providing support when expectation fails. Factors that can affect
the risk management and the factors are identified as either internal or external as policies,
project objectives, politics, industry trends, historical factors, company direction, economics,
social issues and others (Zahadat, 2016; Muzammal et al., 2016). BYOD risk management plan
can recognize associated risks along with project and its deliverables. However, it is viewed that
not every risk is negative; some risks can be positive and therefore, can increase benefits for the
project.
when they will seek for more time in other ways. BYOD can improve daily productivity of
workforce by providing technology to people without having access to technology at all.
Meeting Employees Satisfaction at work: BYOD is identified as tool for attracting and
retaining employees taking younger staffs at work. Recent studies have presented that 20-30 year
aged employees conveyed that 50% of them consider BYOD as a right not a privilege (Martinelli
& Milosevic, 2016). Therefore, as year goes around, if BYOD is not implemented; some bright
employees may leave the workforce soon.
Understanding Customer needs and requirements: The retail organizations are utilizing
consumer devices in stores. The BYOD can provide better situations for presenting marketing
materials (Goldes et al., 2017). Retail employees can check about available products and
customer can get instant information about inventory.
Flexibility in Operation: The operational flexibility may be overlooked however, for
some reasons, it is most important part of BYOD scheme.
Firstly, employees can be forced to do work from home or can be provided with proper
accommodation so that they can work from home at situations of industrial actions, bad or
unfavorable weather, and even terrorism (M'manga et al., 2017). BYOD includes the aspect of
unplanned home working so that lost time can be used with workforce.
Secondly, in any industry, in presence of several mergers and acquisitions, BYOD policy
can help the employees by treating new company devices as under BYOD guidelines. The
organization can incorporate BYOD standards with mergers as well.
Finally, the organization within higher growth of business can speed up new employee
outputs with BYOD policy (Vithanwattana, Mapp & George, 2017). In similar point of view,
employer can have short-term workers over BYOD policy so that time spent can be reduced
rather spending time over provisioning new devices.
Threats, Vulnerabilities and Consequences Assessment
Dove (2016) opined that during project lifecycle, the risks may occur are often identified
as allowing project manager for recognize and treat them as risks. The risks can cast influence
over project in terms of cost, time, deliverable quality, and morale. The risk management
planning included definition as the project definition, monitoring, and controlling risks through
the project. Risk assessment and management plan deals with accepting risk into planning,
tracking and updating risk plan along with removing risk form the plan (Halford, 2016). The
escalation of risk can be made when it is necessary. Maintaining existing risk plan allows project
manager to set out expectations for multiple stakeholders and sponsors, allowing team to focus
over project work along with providing support when expectation fails. Factors that can affect
the risk management and the factors are identified as either internal or external as policies,
project objectives, politics, industry trends, historical factors, company direction, economics,
social issues and others (Zahadat, 2016; Muzammal et al., 2016). BYOD risk management plan
can recognize associated risks along with project and its deliverables. However, it is viewed that
not every risk is negative; some risks can be positive and therefore, can increase benefits for the
project.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
7IT RISK ASSESSMENT CASE STUDY
Risk Identification
Risk identification is an important process where project manager gathers threat and
related concern as in what could go wrong in this particular project. In this risk identification
process, the project team performs identification based on risk aspects, its consequences, and
likely occurrence of risks. Risk assessment provides the working team an opportunity to identify
better ways to address project objectives and deliverables (Vorakulpipat et al., 2017). The risk
identification can be performed with categorizing them based on risk contexts. Risk
categorization can be performed for BYOD project; however, some categories should be omitted
from the risk identification process. The ecological or structural risks should be omitted from
BYOD project risk identification due to project nature; other areas are significant concern for the
project in Altium Limited ("About Altium | Innovative PCB Design, ECAD / MCAD
Collaboration & EDA Software", 2017). The resulting risks are included in a table for creating
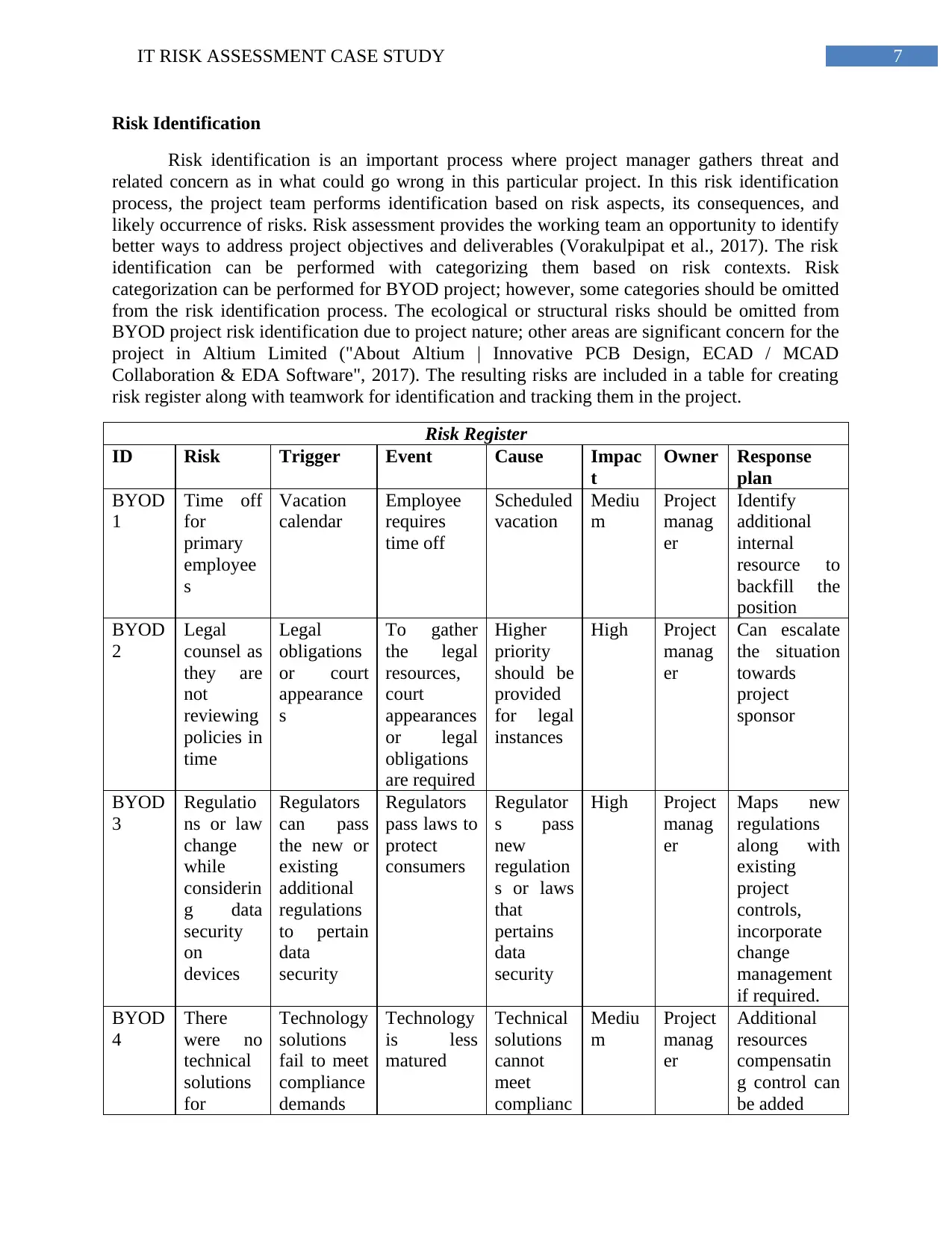
risk register along with teamwork for identification and tracking them in the project.
Risk Register
ID Risk Trigger Event Cause Impac
t
Owner Response
plan
BYOD
1
Time off
for
primary
employee
s
Vacation
calendar
Employee
requires
time off
Scheduled
vacation
Mediu
m
Project
manag
er
Identify
additional
internal
resource to
backfill the
position
BYOD
2
Legal
counsel as
they are
not
reviewing
policies in
time
Legal
obligations
or court
appearance
s
To gather
the legal
resources,
court
appearances
or legal
obligations
are required
Higher
priority
should be
provided
for legal
instances
High Project
manag
er
Can escalate
the situation
towards
project
sponsor
BYOD
3
Regulatio
ns or law
change
while
considerin
g data
security
on
devices
Regulators
can pass
the new or
existing
additional
regulations
to pertain
data
security
Regulators
pass laws to
protect
consumers
Regulator
s pass
new
regulation
s or laws
that
pertains
data
security
High Project
manag
er
Maps new
regulations
along with
existing
project
controls,
incorporate
change
management
if required.
BYOD
4
There
were no
technical
solutions
for
Technology
solutions
fail to meet
compliance
demands
Technology
is less
matured
Technical
solutions
cannot
meet
complianc
Mediu
m
Project
manag
er
Additional
resources
compensatin
g control can
be added
Risk Identification
Risk identification is an important process where project manager gathers threat and
related concern as in what could go wrong in this particular project. In this risk identification
process, the project team performs identification based on risk aspects, its consequences, and
likely occurrence of risks. Risk assessment provides the working team an opportunity to identify
better ways to address project objectives and deliverables (Vorakulpipat et al., 2017). The risk
identification can be performed with categorizing them based on risk contexts. Risk
categorization can be performed for BYOD project; however, some categories should be omitted
from the risk identification process. The ecological or structural risks should be omitted from
BYOD project risk identification due to project nature; other areas are significant concern for the
project in Altium Limited ("About Altium | Innovative PCB Design, ECAD / MCAD
Collaboration & EDA Software", 2017). The resulting risks are included in a table for creating
risk register along with teamwork for identification and tracking them in the project.
Risk Register
ID Risk Trigger Event Cause Impac
t
Owner Response
plan
BYOD
1
Time off
for
primary
employee
s
Vacation
calendar
Employee
requires
time off
Scheduled
vacation
Mediu
m
Project
manag
er
Identify
additional
internal
resource to
backfill the
position
BYOD
2
Legal
counsel as
they are
not
reviewing
policies in
time
Legal
obligations
or court
appearance
s
To gather
the legal
resources,
court
appearances
or legal
obligations
are required
Higher
priority
should be
provided
for legal
instances
High Project
manag
er
Can escalate
the situation
towards
project
sponsor
BYOD
3
Regulatio
ns or law
change
while
considerin
g data
security
on
devices
Regulators
can pass
the new or
existing
additional
regulations
to pertain
data
security
Regulators
pass laws to
protect
consumers
Regulator
s pass
new
regulation
s or laws
that
pertains
data
security
High Project
manag
er
Maps new
regulations
along with
existing
project
controls,
incorporate
change
management
if required.
BYOD
4
There
were no
technical
solutions
for
Technology
solutions
fail to meet
compliance
demands
Technology
is less
matured
Technical
solutions
cannot
meet
complianc
Mediu
m
Project
manag
er
Additional
resources
compensatin
g control can
be added
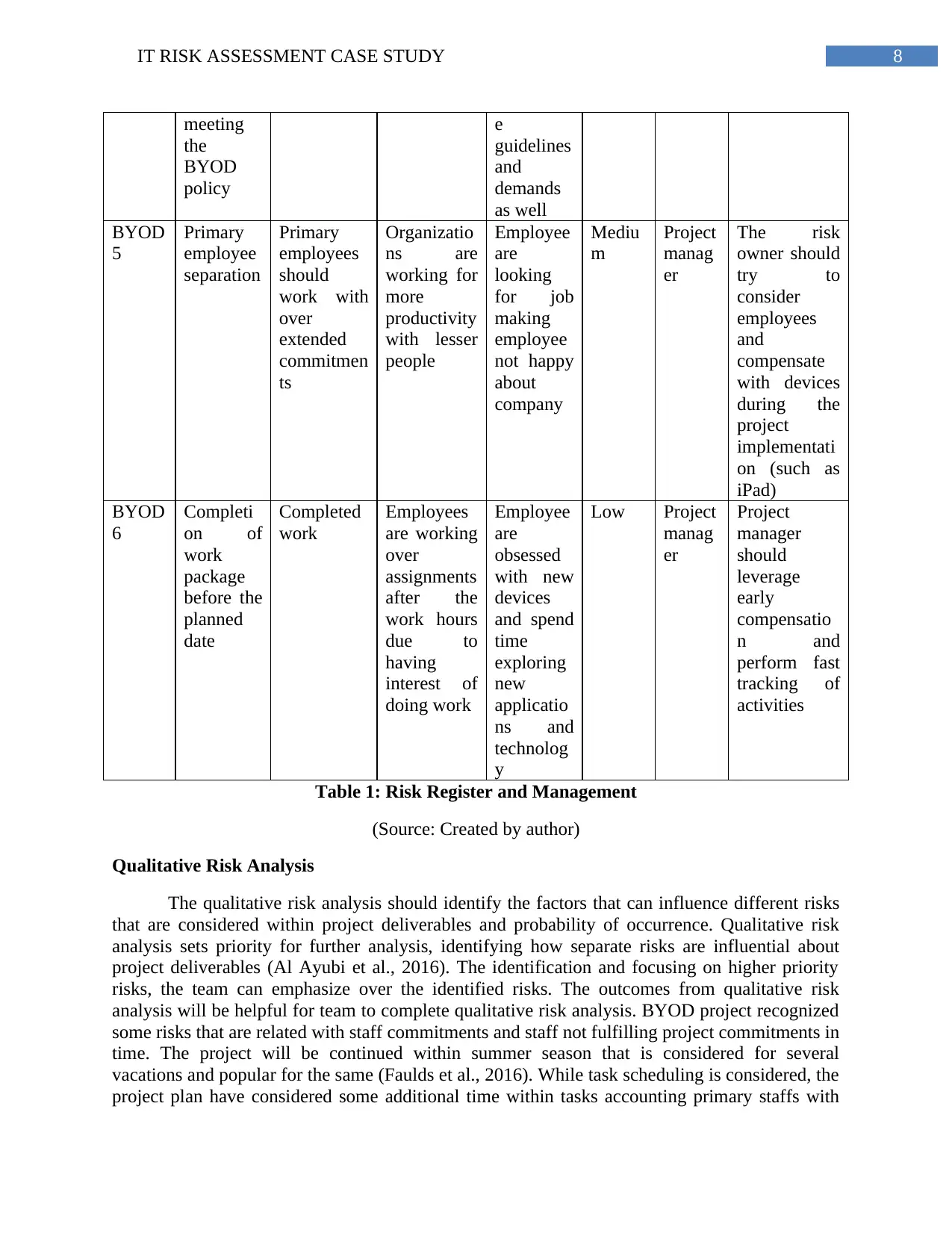
8IT RISK ASSESSMENT CASE STUDY
meeting
the
BYOD
policy
e
guidelines
and
demands
as well
BYOD
5
Primary
employee
separation
Primary
employees
should
work with
over
extended
commitmen
ts
Organizatio
ns are
working for
more
productivity
with lesser
people
Employee
are
looking
for job
making
employee
not happy
about
company
Mediu
m
Project
manag
er
The risk
owner should
try to
consider
employees
and
compensate
with devices
during the
project
implementati
on (such as
iPad)
BYOD
6
Completi
on of
work
package
before the
planned
date
Completed
work
Employees
are working
over
assignments
after the
work hours
due to
having
interest of
doing work
Employee
are
obsessed
with new
devices
and spend
time
exploring
new
applicatio
ns and
technolog
y
Low Project
manag
er
Project
manager
should
leverage
early
compensatio
n and
perform fast
tracking of
activities
Table 1: Risk Register and Management
(Source: Created by author)
Qualitative Risk Analysis
The qualitative risk analysis should identify the factors that can influence different risks
that are considered within project deliverables and probability of occurrence. Qualitative risk
analysis sets priority for further analysis, identifying how separate risks are influential about
project deliverables (Al Ayubi et al., 2016). The identification and focusing on higher priority
risks, the team can emphasize over the identified risks. The outcomes from qualitative risk
analysis will be helpful for team to complete qualitative risk analysis. BYOD project recognized
some risks that are related with staff commitments and staff not fulfilling project commitments in
time. The project will be continued within summer season that is considered for several
vacations and popular for the same (Faulds et al., 2016). While task scheduling is considered, the
project plan have considered some additional time within tasks accounting primary staffs with
meeting
the
BYOD
policy
e
guidelines
and
demands
as well
BYOD
5
Primary
employee
separation
Primary
employees
should
work with
over
extended
commitmen
ts
Organizatio
ns are
working for
more
productivity
with lesser
people
Employee
are
looking
for job
making
employee
not happy
about
company
Mediu
m
Project
manag
er
The risk
owner should
try to
consider
employees
and
compensate
with devices
during the
project
implementati
on (such as
iPad)
BYOD
6
Completi
on of
work
package
before the
planned
date
Completed
work
Employees
are working
over
assignments
after the
work hours
due to
having
interest of
doing work
Employee
are
obsessed
with new
devices
and spend
time
exploring
new
applicatio
ns and
technolog
y
Low Project
manag
er
Project
manager
should
leverage
early
compensatio
n and
perform fast
tracking of
activities
Table 1: Risk Register and Management
(Source: Created by author)
Qualitative Risk Analysis
The qualitative risk analysis should identify the factors that can influence different risks
that are considered within project deliverables and probability of occurrence. Qualitative risk
analysis sets priority for further analysis, identifying how separate risks are influential about
project deliverables (Al Ayubi et al., 2016). The identification and focusing on higher priority
risks, the team can emphasize over the identified risks. The outcomes from qualitative risk
analysis will be helpful for team to complete qualitative risk analysis. BYOD project recognized
some risks that are related with staff commitments and staff not fulfilling project commitments in
time. The project will be continued within summer season that is considered for several
vacations and popular for the same (Faulds et al., 2016). While task scheduling is considered, the
project plan have considered some additional time within tasks accounting primary staffs with
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9IT RISK ASSESSMENT CASE STUDY
vacations. Most critical part risk is identified in qualitative risk analysis is scheduling legal
documents and reviews (Laudon & Laudon, 2016). While the in-house legal review of document
is considered as milestone that one team cannot outsource to outside of the firm. Then the team
can keep track of work schedules and consider legal commitments with escalating towards the
project sponsor.
Quantitative Risk Analysis
Every risk that is identified should be considered for qualitative risk analysis for putting
priority against them. On the other hand, quantitative risk analysis is not part of every project and
it cannot be applied for BYOD project (Steelman, Lacity & Sabherwal, 2016). The quantitative
risk analysis utilizes numerical or quantitative rating associated with developing probabilistic
analysis of the risks. The quantitative risk analysis needs to consider quality data, proper project
mode and prioritized project risk lists (Kearns, 2016; Sadgrove, 2016). The quantitative risk
analysis can lead to realistic costs, schedule, and scoping project targets. Project has faced
limited deliverables and scope; this particular analysis would be essential for providing adequate
benefits without any required effort.
Risk Response Planning
The risk responses are planned to identify the actions that should be taken for reducing
threats and taking advantages of explored opportunities while risk analysis process is conducted.
The risk register and management plan is considered for using inputs from risk responses. Two
types of threats can exist such as negative and positive risks (Singh, Chan & Zulkefli, 2017).
Identified risks in risk register are generally negative and steering committee has agreed to
provide combination of acceptance towards dealing with the risks. The project team have
identified that only one positive risk can exploit; the main positive risk that is identified as earlier
completion of work package before the planned date (Martinez, Borycki & Courtney, 2017). The
team did not consider this particular risk as negative risk. The considered committee accepted the
risks of possible delay in work as legal team could take more time and priorities. Positive risk of
finishing work can allow team for crashing down the activities if possible.
Procurement Planning
Procurement planning is another process for identification of products and services that
project require for purchasing from outsider vendor. As BYOD is an internal project considering
internal resources only, therefore, no specific requirement of purchasing products or service is
required (Tanimoto et al., 2017). Project may face or incur some expenses in this duration, the
senior executives could consider budget to consider operating expenses.
Data Security
As potential risks are identified in the Altium Limited organization scenario for
consideration in Australian IT Sector. The growing trend in several other organizations and
industries; BYOD can be considered to follow data security risks mitigation. The Altium Limited
should consider the starting of allowance towards employees to work over their personal devices
(Peltier, 2016; Filkins et al., 2016). The organization should choose to consider the data security
vacations. Most critical part risk is identified in qualitative risk analysis is scheduling legal
documents and reviews (Laudon & Laudon, 2016). While the in-house legal review of document
is considered as milestone that one team cannot outsource to outside of the firm. Then the team
can keep track of work schedules and consider legal commitments with escalating towards the
project sponsor.
Quantitative Risk Analysis
Every risk that is identified should be considered for qualitative risk analysis for putting
priority against them. On the other hand, quantitative risk analysis is not part of every project and
it cannot be applied for BYOD project (Steelman, Lacity & Sabherwal, 2016). The quantitative
risk analysis utilizes numerical or quantitative rating associated with developing probabilistic
analysis of the risks. The quantitative risk analysis needs to consider quality data, proper project
mode and prioritized project risk lists (Kearns, 2016; Sadgrove, 2016). The quantitative risk
analysis can lead to realistic costs, schedule, and scoping project targets. Project has faced
limited deliverables and scope; this particular analysis would be essential for providing adequate
benefits without any required effort.
Risk Response Planning
The risk responses are planned to identify the actions that should be taken for reducing
threats and taking advantages of explored opportunities while risk analysis process is conducted.
The risk register and management plan is considered for using inputs from risk responses. Two
types of threats can exist such as negative and positive risks (Singh, Chan & Zulkefli, 2017).
Identified risks in risk register are generally negative and steering committee has agreed to
provide combination of acceptance towards dealing with the risks. The project team have
identified that only one positive risk can exploit; the main positive risk that is identified as earlier
completion of work package before the planned date (Martinez, Borycki & Courtney, 2017). The
team did not consider this particular risk as negative risk. The considered committee accepted the
risks of possible delay in work as legal team could take more time and priorities. Positive risk of
finishing work can allow team for crashing down the activities if possible.
Procurement Planning
Procurement planning is another process for identification of products and services that
project require for purchasing from outsider vendor. As BYOD is an internal project considering
internal resources only, therefore, no specific requirement of purchasing products or service is
required (Tanimoto et al., 2017). Project may face or incur some expenses in this duration, the
senior executives could consider budget to consider operating expenses.
Data Security
As potential risks are identified in the Altium Limited organization scenario for
consideration in Australian IT Sector. The growing trend in several other organizations and
industries; BYOD can be considered to follow data security risks mitigation. The Altium Limited
should consider the starting of allowance towards employees to work over their personal devices
(Peltier, 2016; Filkins et al., 2016). The organization should choose to consider the data security
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10IT RISK ASSESSMENT CASE STUDY
on first priority, as IT sectors are evitable to work with large amount of data. The data security
risks are considered as following:
Access Risks: The access risk pertains in organizational profile as per the BYOD scheme.
In current organization and corporation aspect, mobile devices are more consumer-oriented and
the devices are susceptible to changes the way of business (Trewin et al., 2016). The computing
power in business entirely casts influence over allowing consumers and employees to replace
traditional end-user computing device with laptop. The BYOD concept increase security
concerns and puts every organization in verge of multiple risks and threats (Russell, 2016).
Organizations in different sectors such as banking, retailing, information technology, financial,
and online clientele, have significant level of consideration for incorporating BYOD into
business.
Authentication Risks: The authentication risk exists for BYOD policy as per individual
devices pose authentication threat. The organizations need to deal with new level of security
considerations and data threats with personal and corporate data (Shedden et al., 2016). The risk
management over personal and business data should consider appropriate level of risk mitigation
planning. Therefore, the complications in this situation should devise a policy as protection of
data, staffs, and customer is critical for any business to grow with its potential to the fullest (Reid
& Pechenkina, 2016). Ownership of data is becoming more of an issue within business that
operates in regulated market.
Corporate Data Risks: The corporate data risks exist for insider threats in Altium
Limited organization. Several organizations have planned to implement “Bring Your Own
Device” (BYOD) policy so that employees can be allowed to utilize their favorite devices with
bringing down costs to accommodate devices (Dorsemaine et al., 2017). The BYOD policy-
based work model is expected to complicate the data control and policies for organizations that
can increase importance of having well-developed policy. Successful implementation of mobile
device policy can incorporate BYOD initiative into business.
Personal Data Risks: Personal data risks may exist for BYOD scheme, as the employees
may not be able to keep personal data secured. The organizations and corporations should
incorporate a policy to allow utilization of BYOD devices in order to protect their personal data,
employee details and customer information (Gillon, 2017; Dawson, 2016). Here, in this report,
Altium Limited organization required to implement BYOD policy in their business in order to
improve business growth and gradual increment of profitability. Personal data is considered to be
major asset for any individual employee; however, the employees should consider locking
personal devices with proper and secure passwords.
Conclusion
To address all aspects of BYOD solution implementation; the researcher have chosen
organization scenario of Altium Limited Australian organization. The mobile device is alike of
having using dual-core processor in individual pocket. The businesses are becoming entirely
centered towards BYOD policies to manage the individual devices in business activities and
process. In the era of dynamic workload and considering all constraints of workforce, the
primary consideration of accommodation is defined to be BYOD scheme. However, for faster
growing organization as Altium Limited, the scheme is favorable to provide employees to use
on first priority, as IT sectors are evitable to work with large amount of data. The data security
risks are considered as following:
Access Risks: The access risk pertains in organizational profile as per the BYOD scheme.
In current organization and corporation aspect, mobile devices are more consumer-oriented and
the devices are susceptible to changes the way of business (Trewin et al., 2016). The computing
power in business entirely casts influence over allowing consumers and employees to replace
traditional end-user computing device with laptop. The BYOD concept increase security
concerns and puts every organization in verge of multiple risks and threats (Russell, 2016).
Organizations in different sectors such as banking, retailing, information technology, financial,
and online clientele, have significant level of consideration for incorporating BYOD into
business.
Authentication Risks: The authentication risk exists for BYOD policy as per individual
devices pose authentication threat. The organizations need to deal with new level of security
considerations and data threats with personal and corporate data (Shedden et al., 2016). The risk
management over personal and business data should consider appropriate level of risk mitigation
planning. Therefore, the complications in this situation should devise a policy as protection of
data, staffs, and customer is critical for any business to grow with its potential to the fullest (Reid
& Pechenkina, 2016). Ownership of data is becoming more of an issue within business that
operates in regulated market.
Corporate Data Risks: The corporate data risks exist for insider threats in Altium
Limited organization. Several organizations have planned to implement “Bring Your Own
Device” (BYOD) policy so that employees can be allowed to utilize their favorite devices with
bringing down costs to accommodate devices (Dorsemaine et al., 2017). The BYOD policy-
based work model is expected to complicate the data control and policies for organizations that
can increase importance of having well-developed policy. Successful implementation of mobile
device policy can incorporate BYOD initiative into business.
Personal Data Risks: Personal data risks may exist for BYOD scheme, as the employees
may not be able to keep personal data secured. The organizations and corporations should
incorporate a policy to allow utilization of BYOD devices in order to protect their personal data,
employee details and customer information (Gillon, 2017; Dawson, 2016). Here, in this report,
Altium Limited organization required to implement BYOD policy in their business in order to
improve business growth and gradual increment of profitability. Personal data is considered to be
major asset for any individual employee; however, the employees should consider locking
personal devices with proper and secure passwords.
Conclusion
To address all aspects of BYOD solution implementation; the researcher have chosen
organization scenario of Altium Limited Australian organization. The mobile device is alike of
having using dual-core processor in individual pocket. The businesses are becoming entirely
centered towards BYOD policies to manage the individual devices in business activities and
process. In the era of dynamic workload and considering all constraints of workforce, the
primary consideration of accommodation is defined to be BYOD scheme. However, for faster
growing organization as Altium Limited, the scheme is favorable to provide employees to use
11IT RISK ASSESSMENT CASE STUDY
personal devices into organization premises. BYOD can provide benefits to Altium Limited
work culture with prompt operations. Therefore, the chosen organization case scenario is
justified along with widespread operations and management in different countries, clients, and
several services.
personal devices into organization premises. BYOD can provide benefits to Altium Limited
work culture with prompt operations. Therefore, the chosen organization case scenario is
justified along with widespread operations and management in different countries, clients, and
several services.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 15
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





