Case Study: IT Risk Management Analysis for VIC Government
VerifiedAdded on 2020/02/24
|19
|3573
|42
Case Study
AI Summary
This case study delves into the IT risk management strategies of the VIC Government, examining various security risks and concerns within its information systems. The analysis includes a detailed breakdown of security threats, vulnerabilities, and the importance of risk assessment. The assignment categorizes risks, comparing accidental and deliberate threats, and ranks them based on their potential impact. It also highlights the security challenges faced by the VIC Government, including system, data, regulatory, organizational, and modeling challenges, along with a comparison of risks versus uncertainties. The study emphasizes the need for proactive measures to mitigate risks and ensure the secure and efficient operation of the government's information systems. The document provides a comprehensive overview of the risk management processes and their application in a real-world scenario within the VIC Government.

Running head: IT RISK MANAGEMENT
IT risk management: Case Study of VIC Government
Student Name:
Student ID:
University Name:
IT risk management: Case Study of VIC Government
Student Name:
Student ID:
University Name:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

2IT RISK MANAGEMENT
TOC
TOC

3IT RISK MANAGEMENT
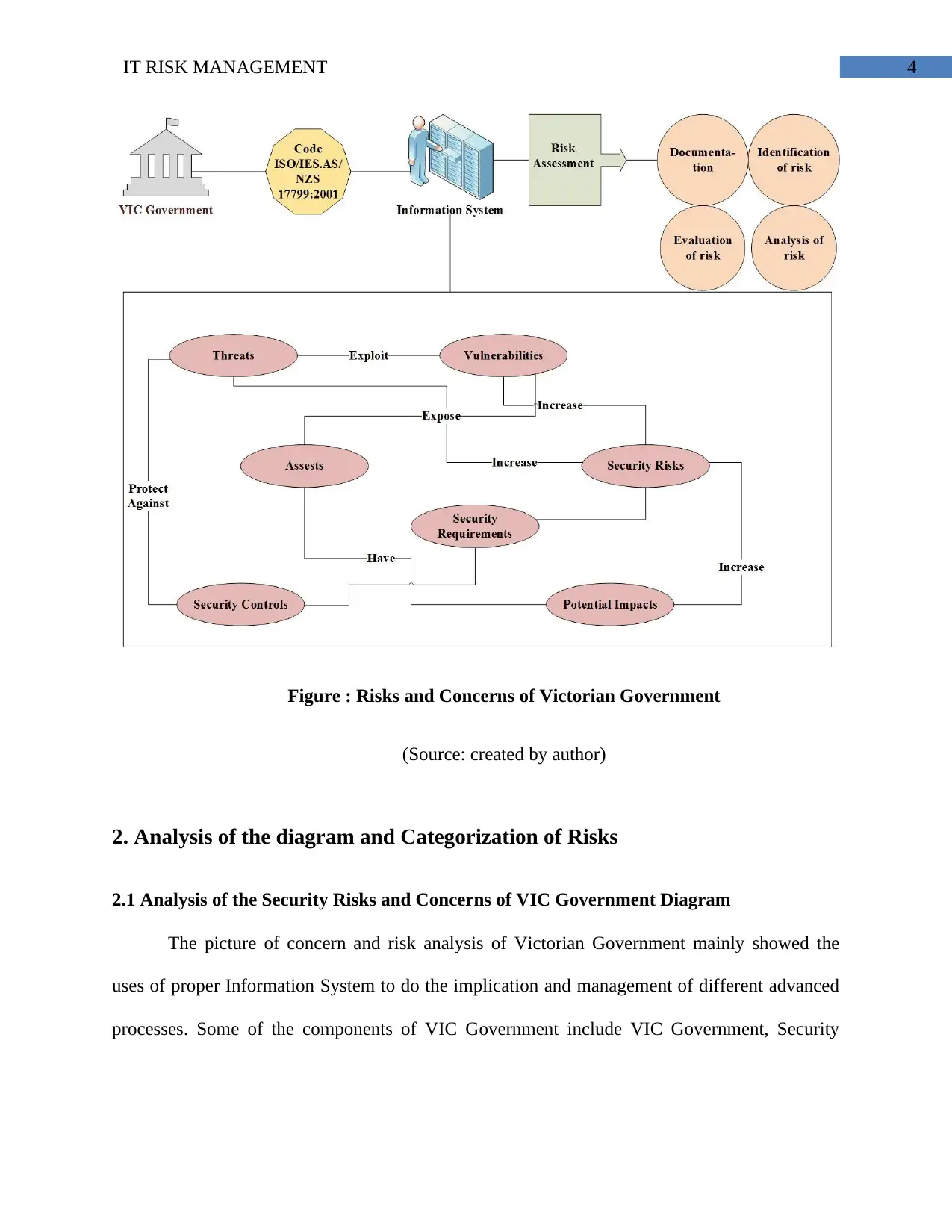
1. Description of the all security risks as well as concerns occurred in VIC
Government
The proper uses of information technology mainly done as unavoidable to do the
formation of different issues that mainly related with the security and privacy of VIC
Government. It also discussed that the Victorian Government mainly needs the proper
development of different concise and improved processes so that it can easily deals with all risks
factors. Apart from that, it also discussed about the formation of operations that directly implies
all smart processing and effective processes in the organization (Xu & Dinev, 2012). Below is
the diagram that mainly shows different risks factors that related with the risk operations of VIC
Government:
1. Description of the all security risks as well as concerns occurred in VIC
Government
The proper uses of information technology mainly done as unavoidable to do the
formation of different issues that mainly related with the security and privacy of VIC
Government. It also discussed that the Victorian Government mainly needs the proper
development of different concise and improved processes so that it can easily deals with all risks
factors. Apart from that, it also discussed about the formation of operations that directly implies
all smart processing and effective processes in the organization (Xu & Dinev, 2012). Below is
the diagram that mainly shows different risks factors that related with the risk operations of VIC
Government:
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
4IT RISK MANAGEMENT
Figure : Risks and Concerns of Victorian Government
(Source: created by author)
2. Analysis of the diagram and Categorization of Risks
2.1 Analysis of the Security Risks and Concerns of VIC Government Diagram
The picture of concern and risk analysis of Victorian Government mainly showed the
uses of proper Information System to do the implication and management of different advanced
processes. Some of the components of VIC Government include VIC Government, Security
Figure : Risks and Concerns of Victorian Government
(Source: created by author)
2. Analysis of the diagram and Categorization of Risks
2.1 Analysis of the Security Risks and Concerns of VIC Government Diagram
The picture of concern and risk analysis of Victorian Government mainly showed the
uses of proper Information System to do the implication and management of different advanced
processes. Some of the components of VIC Government include VIC Government, Security
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

5IT RISK MANAGEMENT
requirements, Security threats, Risk Assessment and different vulnerabilities (Garrick & Hall,
2014).
VIC Government: the Victorian Government mainly symbolizes about both the members
and users of Government that mainly uses about information system and also implies about the
increase rate of different related operations efficiency (United Nations, 2012). However, the
system development also eases all related operations of organization as well as their suggestions
that mainly helps to have improvement in performance of organization (Jain & Shanbhag, 2012).
Information System: The information system mainly implies to integrate the proper
development of different related operations that mainly helps to form an efficient information
processing. Moreover, the system processing mainly results to employ better processing of data
as well as information for the proper guidance of effective flow of information (Boyle, 2012).
Apart from that, the system processing mainly implies to form better data processing as well as
development (Wangwe, Eloff & Venter, 2012).
Risk Factors: Different types of risk factors that mainly affect the information processing
of information within the organization network. Both the vulnerabilities and threats that mainly
results to the integration of different developmental operational issues of organization. Joseph
(2012) discussed that the security control system of VIC Government mainly includes about the
formation of systematic control based on issues and errors. All types of threats and
vulnerabilities causes some serious effect on developmental issues related to the functionalities
of Victorian Government. The system requirement causes some serious errors depending on the
growth factors of smart as well as effective operations (Karokola, Kowalski & Yngström, 2013).
Apart from that, it also discussed about system errors, privacy interference as well as data thefts
requirements, Security threats, Risk Assessment and different vulnerabilities (Garrick & Hall,
2014).
VIC Government: the Victorian Government mainly symbolizes about both the members
and users of Government that mainly uses about information system and also implies about the
increase rate of different related operations efficiency (United Nations, 2012). However, the
system development also eases all related operations of organization as well as their suggestions
that mainly helps to have improvement in performance of organization (Jain & Shanbhag, 2012).
Information System: The information system mainly implies to integrate the proper
development of different related operations that mainly helps to form an efficient information
processing. Moreover, the system processing mainly results to employ better processing of data
as well as information for the proper guidance of effective flow of information (Boyle, 2012).
Apart from that, the system processing mainly implies to form better data processing as well as
development (Wangwe, Eloff & Venter, 2012).
Risk Factors: Different types of risk factors that mainly affect the information processing
of information within the organization network. Both the vulnerabilities and threats that mainly
results to the integration of different developmental operational issues of organization. Joseph
(2012) discussed that the security control system of VIC Government mainly includes about the
formation of systematic control based on issues and errors. All types of threats and
vulnerabilities causes some serious effect on developmental issues related to the functionalities
of Victorian Government. The system requirement causes some serious errors depending on the
growth factors of smart as well as effective operations (Karokola, Kowalski & Yngström, 2013).
Apart from that, it also discussed about system errors, privacy interference as well as data thefts

6IT RISK MANAGEMENT
become some factors of security threats of organizational development (Sitaram & Manjunath,
2012). It also discussed about improved as well as effective procedures that mainly caused more
influence based on the obstacles of different risks factors.
External and Internal Risks: all types of risks, vulnerabilities and threats mainly forms
development of different issues that mainly helps to form various important operations occurred
in an organization. Some risks of the information system of Victorian Government are mainly
get categorized in both internal and external risks (Ofgem, 2012). Collier and Lakoff (2015)
elaborated that internal risks are mainly developed from different types of internal vulnerabilities
and threats like spamming, technical risks, un-authorized access, Denial of Services etc. All
these risks factors mainly imply different technical errors in the organization operation system.
On the other hand, external risks take account of different cyber criminal activities as well as
different user generated technical errors (Karokola, Kowalski & Yngström, 2013). All the errors
are mainly occurred outside of system and also results of the formation of threats to system
development.
Risk Assessment: the risk assessment mainly helps in the development process of
security risk management. It also implies for the development of smart risk analysis to form both
smart processing and effective analysis of information (van Deursen, Buchanan & Duff, 2013).
Apart from that, Garrick and Hall (2014) pointed out that risk assessment mainly consists of
different evaluation techniques, documentation analysis, and different risks identification
techniques. All risk assessment techniques mainly involves the occurrence of improved
processes as well as designing techniques (Amin, Schwartz & Hussain, 2013). The evaluation
and analysis of all risks factors mainly helps to form combined operations in VIC Government.
become some factors of security threats of organizational development (Sitaram & Manjunath,
2012). It also discussed about improved as well as effective procedures that mainly caused more
influence based on the obstacles of different risks factors.
External and Internal Risks: all types of risks, vulnerabilities and threats mainly forms
development of different issues that mainly helps to form various important operations occurred
in an organization. Some risks of the information system of Victorian Government are mainly
get categorized in both internal and external risks (Ofgem, 2012). Collier and Lakoff (2015)
elaborated that internal risks are mainly developed from different types of internal vulnerabilities
and threats like spamming, technical risks, un-authorized access, Denial of Services etc. All
these risks factors mainly imply different technical errors in the organization operation system.
On the other hand, external risks take account of different cyber criminal activities as well as
different user generated technical errors (Karokola, Kowalski & Yngström, 2013). All the errors
are mainly occurred outside of system and also results of the formation of threats to system
development.
Risk Assessment: the risk assessment mainly helps in the development process of
security risk management. It also implies for the development of smart risk analysis to form both
smart processing and effective analysis of information (van Deursen, Buchanan & Duff, 2013).
Apart from that, Garrick and Hall (2014) pointed out that risk assessment mainly consists of
different evaluation techniques, documentation analysis, and different risks identification
techniques. All risk assessment techniques mainly involves the occurrence of improved
processes as well as designing techniques (Amin, Schwartz & Hussain, 2013). The evaluation
and analysis of all risks factors mainly helps to form combined operations in VIC Government.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
7IT RISK MANAGEMENT
2.2 Categorization of Risks and Identification of the Exposure Area
All types of risks are mainly categorised in different types of internal and external risk
factors that mainly helped to develop proper analysis of risk assessment. It also discussed that the
VIC Government mainly deployed information processing techniques to form different improved
processes of data processing (Fan, Zhang & Yen, 2014). On the other hand, in the organization it
mainly occurs different risks assessment factors of VIC Government like potential risk, malware,
vulnerabilities, security risks, data thefts, phishing, and spamming, un-authorized access etc
(Choi, Chun & Cho, 2014). Some the risks are mainly categorised in medium-high, medium-low
as well as low risk exposure.
Risk Type Description Example
High risk exposure areas The high risk exposure areas
mainly creates vital and
significant impacts on all VIC
Government operations. The
high risk exposure areas are
given more priority to be
rectified and treated in the
operational system of project
(Al-ahmad & Mohammad,
2014).
Different privacy
concerns, data theft,
security vulnerabilities,
are some example of high
risk exposure areas.
Medium risk exposure areas In this type, it mainly helps to
form different risk factors that
Malwares, Intrusion,
Design errors, and
2.2 Categorization of Risks and Identification of the Exposure Area
All types of risks are mainly categorised in different types of internal and external risk
factors that mainly helped to develop proper analysis of risk assessment. It also discussed that the
VIC Government mainly deployed information processing techniques to form different improved
processes of data processing (Fan, Zhang & Yen, 2014). On the other hand, in the organization it
mainly occurs different risks assessment factors of VIC Government like potential risk, malware,
vulnerabilities, security risks, data thefts, phishing, and spamming, un-authorized access etc
(Choi, Chun & Cho, 2014). Some the risks are mainly categorised in medium-high, medium-low
as well as low risk exposure.
Risk Type Description Example
High risk exposure areas The high risk exposure areas
mainly creates vital and
significant impacts on all VIC
Government operations. The
high risk exposure areas are
given more priority to be
rectified and treated in the
operational system of project
(Al-ahmad & Mohammad,
2014).
Different privacy
concerns, data theft,
security vulnerabilities,
are some example of high
risk exposure areas.
Medium risk exposure areas In this type, it mainly helps to
form different risk factors that
Malwares, Intrusion,
Design errors, and
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
8IT RISK MANAGEMENT
mainly causes medium impact
on different information
system operations. All the
types of risk exposure areas are
considered with medium
priority to develop and sort
contingency plans. These types
of areas are mainly be treated
with the decrease in impact of
different operations of VIC
Government Information
System (Zhao, Xue &
Whinston, 2013).
technical errors are the
medium risk exposure
areas
Medium low risk exposure areas This medium low risk
exposure areas are less causing
factor that mainly causes
impact on the Information
Processing unit of VIC
Government (Al-Hadadi & Al
Shidhani, 2013). This
particular area is mainly given
with less priority to be
delivered of solution and
denial of service,
spamming, different
minor issues are the
example of medium low
risk exposure areas.
mainly causes medium impact
on different information
system operations. All the
types of risk exposure areas are
considered with medium
priority to develop and sort
contingency plans. These types
of areas are mainly be treated
with the decrease in impact of
different operations of VIC
Government Information
System (Zhao, Xue &
Whinston, 2013).
technical errors are the
medium risk exposure
areas
Medium low risk exposure areas This medium low risk
exposure areas are less causing
factor that mainly causes
impact on the Information
Processing unit of VIC
Government (Al-Hadadi & Al
Shidhani, 2013). This
particular area is mainly given
with less priority to be
delivered of solution and
denial of service,
spamming, different
minor issues are the
example of medium low
risk exposure areas.
9IT RISK MANAGEMENT
processing.
Low risk exposure areas This area causes very minimal
influence that causes impact on
different operations of
information processing unit of
VIC Government. All risk
factors processing mainly
considered minimal time as
well as the impact also causes
very least (Demski, Poortinga
& Pidgeon, 2014).
The Social engineering
generated errors and the
user generated errors are
the low risk exposure
areas.
3. Comparison and Ranking of Threats
3.1 Comparing the Accidental and Deliberate Threats
Jain and Shanbhag (2012) highlighted that the accidental threat mainly have no proper
causes for related operations of organization. In case of accidental threats, it mainly formed due
to some different errors and mistakes that mainly caused without the consent of any personnel.
Accidental threats can get sorted by taking pre-measures based on different operations occurred
in Victorian Government. Apart from that, accidental threats mainly get caused due to both
external as well as internal issues (Boyle, 2012). On the other side, Choi, Chun and Cho (2014)
discussed that the type of deliberate threats mainly caused due to the involvement of different
processing.
Low risk exposure areas This area causes very minimal
influence that causes impact on
different operations of
information processing unit of
VIC Government. All risk
factors processing mainly
considered minimal time as
well as the impact also causes
very least (Demski, Poortinga
& Pidgeon, 2014).
The Social engineering
generated errors and the
user generated errors are
the low risk exposure
areas.
3. Comparison and Ranking of Threats
3.1 Comparing the Accidental and Deliberate Threats
Jain and Shanbhag (2012) highlighted that the accidental threat mainly have no proper
causes for related operations of organization. In case of accidental threats, it mainly formed due
to some different errors and mistakes that mainly caused without the consent of any personnel.
Accidental threats can get sorted by taking pre-measures based on different operations occurred
in Victorian Government. Apart from that, accidental threats mainly get caused due to both
external as well as internal issues (Boyle, 2012). On the other side, Choi, Chun and Cho (2014)
discussed that the type of deliberate threats mainly caused due to the involvement of different
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

10IT RISK MANAGEMENT
external influences. This type of threats is mainly caused because of any person intentional
attacks. This threat mainly caused because of the uses of advanced technology that mainly harms
the operation flows (Al-ahmad & Mohammad, 2013). It also mainly compromise of different
criminal activities as well as hacking technologies that mainly used intentionally to harm the VIC
Government Information System.
3.2 Ranking Threats for VIC Information System
Accidental threats mainly get sorted with the help of different pre-planned actions of all
operations depending on information processing at Victorian Government. All types of system
flaws, natural disasters, system flaws are types of accidental threats based on the implementation
of information system in Victorian Government.
Some of deliberate threats are mainly getting caused because of the use of improvised
technologies to harm the flow of different operations of VIC Government. According to Zhao,
Xue and Whinston, (2013), the storage system device thefts, cyber crimes, hacking, different
viruses and malware attacks are some of the deliberate threats to do the implementation of
information system in Victorian Government. Both the threats are mentioned rank-wise in the
below table:
Rank Threat Type Example Explanation
Ist Deliberate Hacking and
Cyber Crimes,
Theft of Storage
System Device,
Deliberate Data
All of these risks are given highest
priority due to their severe impact on
the information system processing at
the VIC Government
external influences. This type of threats is mainly caused because of any person intentional
attacks. This threat mainly caused because of the uses of advanced technology that mainly harms
the operation flows (Al-ahmad & Mohammad, 2013). It also mainly compromise of different
criminal activities as well as hacking technologies that mainly used intentionally to harm the VIC
Government Information System.
3.2 Ranking Threats for VIC Information System
Accidental threats mainly get sorted with the help of different pre-planned actions of all
operations depending on information processing at Victorian Government. All types of system
flaws, natural disasters, system flaws are types of accidental threats based on the implementation
of information system in Victorian Government.
Some of deliberate threats are mainly getting caused because of the use of improvised
technologies to harm the flow of different operations of VIC Government. According to Zhao,
Xue and Whinston, (2013), the storage system device thefts, cyber crimes, hacking, different
viruses and malware attacks are some of the deliberate threats to do the implementation of
information system in Victorian Government. Both the threats are mentioned rank-wise in the
below table:
Rank Threat Type Example Explanation
Ist Deliberate Hacking and
Cyber Crimes,
Theft of Storage
System Device,
Deliberate Data
All of these risks are given highest
priority due to their severe impact on
the information system processing at
the VIC Government
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

11IT RISK MANAGEMENT
Compromise,
Virus and Mal-
ware Attack
2nd Accidental Accidental Data
Compromise,
Natural
Disasters, System
Flaws, Unknown
File Deletion, etc
All these risks are give low priority
due to the absence of any critical
impact on the operations of
information system of VIC
Government
4. Security Challenges of VIC information system
The execution of information system faces different types of issues based on risk factors
and also form generation of different challenges for VIC Government. The occurrence of
different smart and proper operations may loose due to different types of issues (Collier &
Lakoff, 2015). Some of the different factors of challenges for Victorian Government includes
system and data challenges, regulatory challenges, modeling challenges.
System and Data Challenges: The system as well as data challenges are mainly
understood for the information processing and development of various operation related issues
for system data and challenges. Karokola, Kowalski and Yngström (2013) illustrated that both
Compromise,
Virus and Mal-
ware Attack
2nd Accidental Accidental Data
Compromise,
Natural
Disasters, System
Flaws, Unknown
File Deletion, etc
All these risks are give low priority
due to the absence of any critical
impact on the operations of
information system of VIC
Government
4. Security Challenges of VIC information system
The execution of information system faces different types of issues based on risk factors
and also form generation of different challenges for VIC Government. The occurrence of
different smart and proper operations may loose due to different types of issues (Collier &
Lakoff, 2015). Some of the different factors of challenges for Victorian Government includes
system and data challenges, regulatory challenges, modeling challenges.
System and Data Challenges: The system as well as data challenges are mainly
understood for the information processing and development of various operation related issues
for system data and challenges. Karokola, Kowalski and Yngström (2013) illustrated that both

12IT RISK MANAGEMENT
data and system challenges may resulted to form different issues related to information
processing.
Regulatory Challenges: Garrick and Hall (2014) opined that all types of regulatory
issues of VIC Government becomes crucial as risk assessment techniques that are inter-related
with development of different imperative and effective operational techniques. The fabrication of
different imperative operation leads to the formation of different factors based on different
Victorian Government challenges.
Organizational challenges: System development causes direct implication for the proper
development of different processes of operational development (Jain & Shanbhag, 2012). In
addition to this, Wangwe, Eloff and Venter (2012) discussed that some of organizational
challenges are mainly developed to do the integration of different limited operational processing.
Both smart and effective operations development mainly get slacked based on all identified
operational issues.
Modeling Challenges: According to Sitaram and Manjunath (2012), all modeling
challenges mainly caused because of the implications of various identified errors in the system
designing. It also causes issues in performance as well as operational speed of information
processing. Apart from that, the information system development processes mainly face different
formation issues and system incompatibility issues.
5. Risk vs. Uncertainty in VIC information system
The Victorian Government mainly remark the information processing technique to form
different improved processes of data processing techniques. Hence, this particular organization
data and system challenges may resulted to form different issues related to information
processing.
Regulatory Challenges: Garrick and Hall (2014) opined that all types of regulatory
issues of VIC Government becomes crucial as risk assessment techniques that are inter-related
with development of different imperative and effective operational techniques. The fabrication of
different imperative operation leads to the formation of different factors based on different
Victorian Government challenges.
Organizational challenges: System development causes direct implication for the proper
development of different processes of operational development (Jain & Shanbhag, 2012). In
addition to this, Wangwe, Eloff and Venter (2012) discussed that some of organizational
challenges are mainly developed to do the integration of different limited operational processing.
Both smart and effective operations development mainly get slacked based on all identified
operational issues.
Modeling Challenges: According to Sitaram and Manjunath (2012), all modeling
challenges mainly caused because of the implications of various identified errors in the system
designing. It also causes issues in performance as well as operational speed of information
processing. Apart from that, the information system development processes mainly face different
formation issues and system incompatibility issues.
5. Risk vs. Uncertainty in VIC information system
The Victorian Government mainly remark the information processing technique to form
different improved processes of data processing techniques. Hence, this particular organization
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 19
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





