IT Risk Management Report: Security, Models, and Risk Assessment
VerifiedAdded on 2020/03/01
|9
|1437
|83
Report
AI Summary
This report provides an overview of IT risk management, focusing on data security and threat assessment within organizations. It explores the IT security landscape, emphasizing the importance of data protection and the use of updated firewalls and anti-virus software to mitigate cyber threats. The report delves into IT security models and access controls, specifically examining the Role-Based Access Control (RBAC) model, its functionalities, and its limitations in controlling cyber-attacks. Furthermore, it assesses IT security threats and risks, identifying various vulnerabilities such as human and non-human threats, and the importance of risk assessment in mitigating potential data loss. The conclusion highlights the significance of IT security and technology in maintaining data security and the role of the RBAC model in controlling access within companies. The report emphasizes the need for proper risk management to track and restrict cyber-attacks, ensuring the security of company data and information.

Running head: IT RISK MANGEMENT
IT Risk Management
Name of the Student
Name of the University
Author’s Note
IT Risk Management
Name of the Student
Name of the University
Author’s Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
IT RISK MANAGEMENT
Executive Summary
This report deals with the UT security and risk assessment of the data and information in the
companies. There are many cases in which the data and information has been recovered by the
companies in the market. The use of the updated firewalls and anti-viruses software helps in
reducing the risks of cyber attacking the server of the company. The proper risk management has
helped in tracking these activities over the Internet and making the company free form the cyber-
attacks. The hackers are restricted ti enter into the security firewall of the server.
IT RISK MANAGEMENT
Executive Summary
This report deals with the UT security and risk assessment of the data and information in the
companies. There are many cases in which the data and information has been recovered by the
companies in the market. The use of the updated firewalls and anti-viruses software helps in
reducing the risks of cyber attacking the server of the company. The proper risk management has
helped in tracking these activities over the Internet and making the company free form the cyber-
attacks. The hackers are restricted ti enter into the security firewall of the server.

2
IT RISK MANAGEMENT
Table of Contents
Introduction......................................................................................................................................4
IT security and Technology landscape............................................................................................4
IT Security Models and Access controls.........................................................................................5
IT security Threat and risk assessment............................................................................................7
Conclusion.......................................................................................................................................8
References........................................................................................................................................9
IT RISK MANAGEMENT
Table of Contents
Introduction......................................................................................................................................4
IT security and Technology landscape............................................................................................4
IT Security Models and Access controls.........................................................................................5
IT security Threat and risk assessment............................................................................................7
Conclusion.......................................................................................................................................8
References........................................................................................................................................9
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3
IT RISK MANAGEMENT
Introduction
The data protection in the organization is an important part for the development of the
organization in the market. There are various risk and security threats to the data and
information.
This report deals with the IT security landscape, IT security models and controls and IT security
treat and risk assessment.
This report outlines these three topics in the business organization that helps in the development
of the company in the market. Therefore, there are various techniques for initiating the risk
assessment process in the organization.
IT security and Technology landscape
The IT security and technology in the companies have helped in the maintaining the security of
the data and information of the company in the market (Ackermann, 2012). The various data and
information of the company had need used in the market for various purpose. Therefore, there is
a great need of the security of the data and information in the market. The IoT has helped in
providing security ti the data and information of the company in the market. The cyber-insurance
is a term that is used for recovering the data and information from being lost. There are many
cases in which the data and information has been recovered by the companies in the market
(Bojanc, & Jerman-Blažič, 2013). Various protocols help in recovering the data md information
in the market. In the other hand, Rieke et al., (2012) argued that there is a least chance of
recovering the data and information from being lost. The lost data and information of their
company cannot be recovered and it is a complicated process. The IT security and risks has been
IT RISK MANAGEMENT
Introduction
The data protection in the organization is an important part for the development of the
organization in the market. There are various risk and security threats to the data and
information.
This report deals with the IT security landscape, IT security models and controls and IT security
treat and risk assessment.
This report outlines these three topics in the business organization that helps in the development
of the company in the market. Therefore, there are various techniques for initiating the risk
assessment process in the organization.
IT security and Technology landscape
The IT security and technology in the companies have helped in the maintaining the security of
the data and information of the company in the market (Ackermann, 2012). The various data and
information of the company had need used in the market for various purpose. Therefore, there is
a great need of the security of the data and information in the market. The IoT has helped in
providing security ti the data and information of the company in the market. The cyber-insurance
is a term that is used for recovering the data and information from being lost. There are many
cases in which the data and information has been recovered by the companies in the market
(Bojanc, & Jerman-Blažič, 2013). Various protocols help in recovering the data md information
in the market. In the other hand, Rieke et al., (2012) argued that there is a least chance of
recovering the data and information from being lost. The lost data and information of their
company cannot be recovered and it is a complicated process. The IT security and risks has been
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4
IT RISK MANAGEMENT
focused and maintaining the process of the retrieving the data and information regarding the
company.
IT Security Models and Access controls
There are various access control models in the IT that helps in controlling the data ans
information in the companies.
Role-based Access control
The Role-based access control (RBAC) model constitute of the roles that helps in permitting
various job to the users. It was developed to overcome the administrative problems that are
encountered in the large commercial companies. The major part of the decisions making are dine
with the help of the DAC method. The RBAC model is a hierarchical model that helps in
maintaining a role model in the field of IT security field (Jaferian et al., 2014). Therefore, it
helps in reviewing and relocating the permission of the company. It relates with the cost benefit
analysis of the data and information of the company in the market. The security of the data and
information the company can be controlled by the RBAC model by controlling the access of the
elements in company. The security of the data and information from the cyber-attacks is topmost
priority for the company in the market there are several cases of the cyber-attacks that has caused
huge data loss ti different companies. On the other hand, Rieke et al., (2012) argued that the
RBAC model is not able to control the amount the cyber-attacks as the protocols used in this
model are of older version. Therefore, the viruses and malwares can easily penetrate through the
security systems in this model. This has been a great loss to the company by using this model.
The RBAC model has also helped in maintaining the growth of the company in various fields by
IT RISK MANAGEMENT
focused and maintaining the process of the retrieving the data and information regarding the
company.
IT Security Models and Access controls
There are various access control models in the IT that helps in controlling the data ans
information in the companies.
Role-based Access control
The Role-based access control (RBAC) model constitute of the roles that helps in permitting
various job to the users. It was developed to overcome the administrative problems that are
encountered in the large commercial companies. The major part of the decisions making are dine
with the help of the DAC method. The RBAC model is a hierarchical model that helps in
maintaining a role model in the field of IT security field (Jaferian et al., 2014). Therefore, it
helps in reviewing and relocating the permission of the company. It relates with the cost benefit
analysis of the data and information of the company in the market. The security of the data and
information the company can be controlled by the RBAC model by controlling the access of the
elements in company. The security of the data and information from the cyber-attacks is topmost
priority for the company in the market there are several cases of the cyber-attacks that has caused
huge data loss ti different companies. On the other hand, Rieke et al., (2012) argued that the
RBAC model is not able to control the amount the cyber-attacks as the protocols used in this
model are of older version. Therefore, the viruses and malwares can easily penetrate through the
security systems in this model. This has been a great loss to the company by using this model.
The RBAC model has also helped in maintaining the growth of the company in various fields by
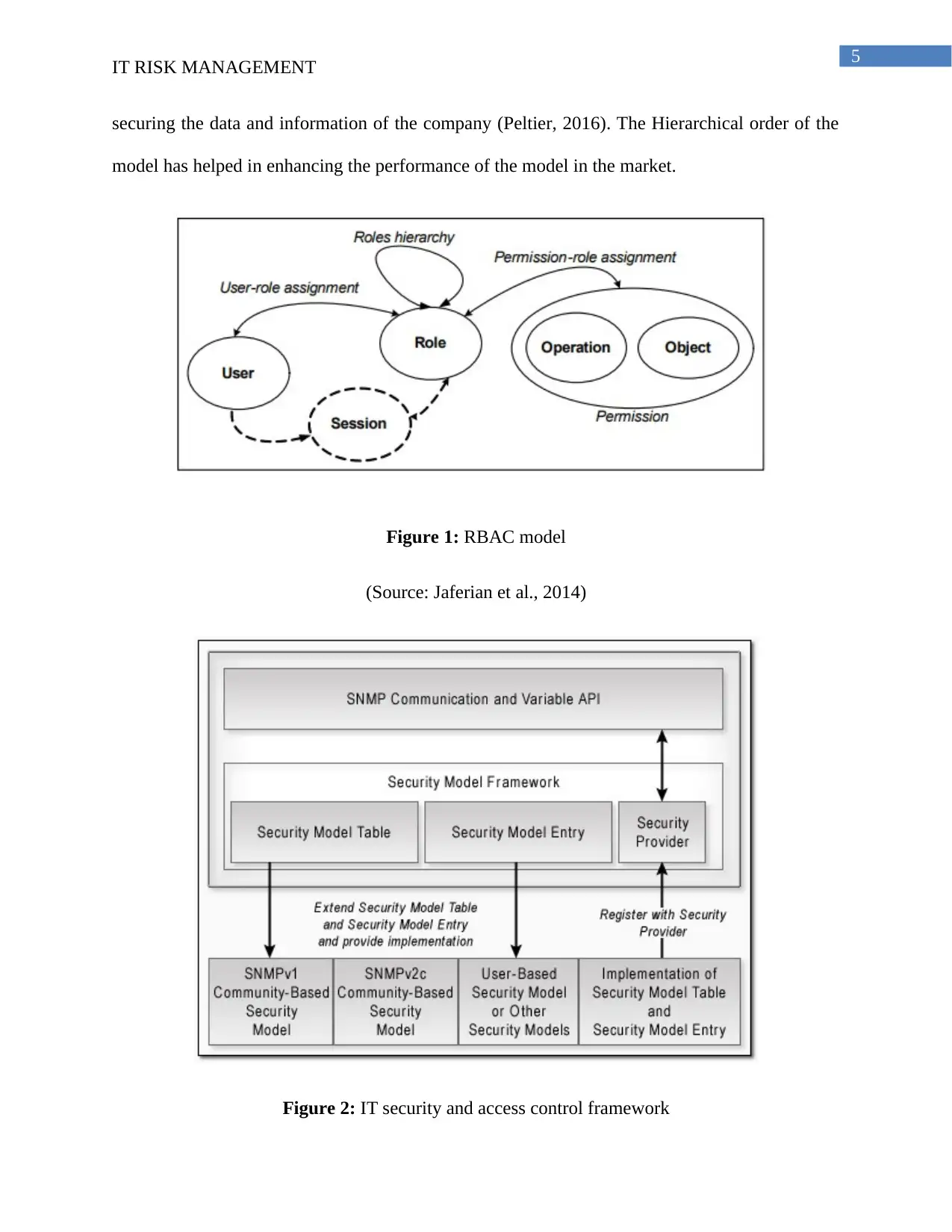
5
IT RISK MANAGEMENT
securing the data and information of the company (Peltier, 2016). The Hierarchical order of the
model has helped in enhancing the performance of the model in the market.
Figure 1: RBAC model
(Source: Jaferian et al., 2014)
Figure 2: IT security and access control framework
IT RISK MANAGEMENT
securing the data and information of the company (Peltier, 2016). The Hierarchical order of the
model has helped in enhancing the performance of the model in the market.
Figure 1: RBAC model
(Source: Jaferian et al., 2014)
Figure 2: IT security and access control framework
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6
IT RISK MANAGEMENT
(Source: Ackermann, 2012)
IT security Threat and risk assessment
The IT security and threat management is an integral part of the company to be measured. There
are various risks are mentioned below in the table.
Human Non-Human
Hackers
· Theft (electronically and
physically)
· Non-technical staff
(financial/accounting)
· Accidental
· Inadequately trained IT staff
· Backup operators
· Technicians, Electricians
Floods
· Lightning strikes
· Plumbing
· Viruses
· Fire
· Electrical
· Air (dust)
· Heat control
Table 1: List of Risks
The risk assessment is a method to identify the risks involved in the IT companies in the market.
The above table shows about the different risks that can be vulnerable in the IT companies. The
risk assessment helps in analyzing various aspects of the risks in the company. The risk
assessment procedure includes the identification of the risks involved in the company and
making strategies ti mitigate these risks in the market. There are various levels of risks that are
IT RISK MANAGEMENT
(Source: Ackermann, 2012)
IT security Threat and risk assessment
The IT security and threat management is an integral part of the company to be measured. There
are various risks are mentioned below in the table.
Human Non-Human
Hackers
· Theft (electronically and
physically)
· Non-technical staff
(financial/accounting)
· Accidental
· Inadequately trained IT staff
· Backup operators
· Technicians, Electricians
Floods
· Lightning strikes
· Plumbing
· Viruses
· Fire
· Electrical
· Air (dust)
· Heat control
Table 1: List of Risks
The risk assessment is a method to identify the risks involved in the IT companies in the market.
The above table shows about the different risks that can be vulnerable in the IT companies. The
risk assessment helps in analyzing various aspects of the risks in the company. The risk
assessment procedure includes the identification of the risks involved in the company and
making strategies ti mitigate these risks in the market. There are various levels of risks that are
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7
IT RISK MANAGEMENT
taken into concern including high-level, medium level and low-level risks. The vulnerability of
the threats in the IT companies are taken out by the risk assessment process. It is the mechanism
of reducing the risks of the data loss in the company. There are several process to control the
cyber-attacks in the companies. The firewall re used to restrict the anonymous viruses and
malwares. There are various intrusion detection systems are installed in the company that helps
in controlling the cyber-attacks in the companies. The use of the updated firewalls and anti-
viruses software helps in reducing the risks of cyber attacking the server of the company (Vacca,
2012). The proper risk management has helped in tracking these activities over the Internet and
making the company free form the cyber-attacks. The hackers are restricted ti enter into the
security firewall of the server.
Conclusion
It can be concluded that the IT security and technology in the companies have helped in the
maintaining the security of the data and information of the company in the market. The various
data and information of the company had need used in the market for various purpose. Therefore,
there is a great need of the security of the data and information in the market. The RBAC model
has helped in maintaining the IT security and access control in the company.
IT RISK MANAGEMENT
taken into concern including high-level, medium level and low-level risks. The vulnerability of
the threats in the IT companies are taken out by the risk assessment process. It is the mechanism
of reducing the risks of the data loss in the company. There are several process to control the
cyber-attacks in the companies. The firewall re used to restrict the anonymous viruses and
malwares. There are various intrusion detection systems are installed in the company that helps
in controlling the cyber-attacks in the companies. The use of the updated firewalls and anti-
viruses software helps in reducing the risks of cyber attacking the server of the company (Vacca,
2012). The proper risk management has helped in tracking these activities over the Internet and
making the company free form the cyber-attacks. The hackers are restricted ti enter into the
security firewall of the server.
Conclusion
It can be concluded that the IT security and technology in the companies have helped in the
maintaining the security of the data and information of the company in the market. The various
data and information of the company had need used in the market for various purpose. Therefore,
there is a great need of the security of the data and information in the market. The RBAC model
has helped in maintaining the IT security and access control in the company.

8
IT RISK MANAGEMENT
References
Ackermann, T. (2012). IT security risk management: perceived IT security risks in the context of
Cloud Computing. Springer Science & Business Media.
Bojanc, R., & Jerman-Blažič, B. (2013). A quantitative model for information-security risk
management. Engineering Management Journal, 25(2), 25-37.
Jaferian, P., Hawkey, K., Sotirakopoulos, A., Velez-Rojas, M., & Beznosov, K. (2014).
Heuristics for evaluating IT security management tools. Human–Computer Interaction,
29(4), 311-350.
Peltier, T. R. (2016). Information Security Policies, Procedures, and Standards: guidelines for
effective information security management. CRC Press.
Rieke, R., Coppolino, L., Hutchison, A., Prieto, E., & Gaber, C. (2012, October). Security and
Reliability Requirements for Advanced Security Event Management. In MMM-ACNS
(pp. 171-180).
Vacca, J. R. (2012). Computer and information security handbook. Newnes.
IT RISK MANAGEMENT
References
Ackermann, T. (2012). IT security risk management: perceived IT security risks in the context of
Cloud Computing. Springer Science & Business Media.
Bojanc, R., & Jerman-Blažič, B. (2013). A quantitative model for information-security risk
management. Engineering Management Journal, 25(2), 25-37.
Jaferian, P., Hawkey, K., Sotirakopoulos, A., Velez-Rojas, M., & Beznosov, K. (2014).
Heuristics for evaluating IT security management tools. Human–Computer Interaction,
29(4), 311-350.
Peltier, T. R. (2016). Information Security Policies, Procedures, and Standards: guidelines for
effective information security management. CRC Press.
Rieke, R., Coppolino, L., Hutchison, A., Prieto, E., & Gaber, C. (2012, October). Security and
Reliability Requirements for Advanced Security Event Management. In MMM-ACNS
(pp. 171-180).
Vacca, J. R. (2012). Computer and information security handbook. Newnes.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 9
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





