ITC 596: IT Risk Management Report on Security Policy and Risk
VerifiedAdded on 2020/09/09
|8
|2207
|231
Report
AI Summary
This report, prepared for ITC 596, delves into IT risk management, focusing on security policies and risk assessments within the context of a health record system and a banking IT system (NetBank). Part one examines the planning, development, and management of security policies, including strategic planning, resource planning, and the roles of individuals in policy implementation. Part two conducts a risk assessment, identifying risks such as integration risk, unauthorized access, backup system failure, network failure, and application software failure. The report includes a risk register detailing each risk, its description, impact, likelihood, and mitigation strategies, along with justifications for conducting the risk assessment and conclusions summarizing the findings and providing references to support the analysis. The report emphasizes the importance of proactive risk management and the implementation of appropriate security measures.

ITC 596
IT Risk Management
ASSESSMENT ITEM 2
Student name:
Lecturer Name:
Student ID:
1
IT Risk Management
ASSESSMENT ITEM 2
Student name:
Lecturer Name:
Student ID:
1
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
Part One – Plan, Develop and Manage a Security Policy................................................................3
Introduction..................................................................................................................................3
Plan Security Policy.....................................................................................................................3
Develop a Security Policy...........................................................................................................4
Manage Security Policy...............................................................................................................4
Conclusion...................................................................................................................................5
Part Two - Conducting a Risk Assessment......................................................................................5
Introduction..................................................................................................................................5
Risk Assessment..........................................................................................................................5
Risk Register................................................................................................................................6
Justification to Conduct Risk Assessment...................................................................................7
Conclusion...................................................................................................................................7
References........................................................................................................................................8
2
Part One – Plan, Develop and Manage a Security Policy................................................................3
Introduction..................................................................................................................................3
Plan Security Policy.....................................................................................................................3
Develop a Security Policy...........................................................................................................4
Manage Security Policy...............................................................................................................4
Conclusion...................................................................................................................................5
Part Two - Conducting a Risk Assessment......................................................................................5
Introduction..................................................................................................................................5
Risk Assessment..........................................................................................................................5
Risk Register................................................................................................................................6
Justification to Conduct Risk Assessment...................................................................................7
Conclusion...................................................................................................................................7
References........................................................................................................................................8
2

Part One – Plan, Develop and Manage a Security Policy
Introduction
This report is designing to explain “My Health Record” system’s planning information.
Australian’s Commonwealth Government is planning for launching a health record system for all
Australians. This system will keep information about the doctor, pathologist, nurse,
administrator, and patient’s health. Part one will describe the information about planning of
security policy, development of security policy, and management of security policy.
Plan Security Policy
Role of Security Policy’s planning: Security policy plan works as formal security plan that is
utilized to define an action plan for protecting and controlling information system or computer
system such as “My Health Record” system. Typically security policy’s plan includes:
List of authorized users / persons that can be accessed the system.
Access control method (how persons will use the system)
Weakness and strengths of the system & how weaknesses will handle
Also, include system restoration / backup procedures (Techopedia, 2019).
Best Strategic planning for security policy: The strategic planning for security policy is a very
important document for organization to maintain the security of information of users. The best
strategic planning of security policy is detailed process that contains initialization, planning,
implementation, monitoring and controlling of the user’s information. The best strategic
planning prioritizes and defines security initiatives and information assurance that organization
should enhance the information’s protection & related technology (Bada et al., 2019).
The requirement of Resources planning for security policy: Proper resource planning is also
playing important role to make security policy for IT system (health record system) because,
with the help of proper resource planning, organization can make best use of each employee’s
skills. It will also help to manage the entire user’s information at one place in the IT system. It
will also helpful to predict the different risk that can be affected the security policy of IT system
in the future. The proper resource planning also keeps all the information about security policy in
visual format. Hence, it is essential for security policy’s planning in IT system.
On the basis of learned information, the two-way authentication process can be implemented in
the security policy of IT system that will be helpful for Australian’s Commonwealth Government
to save the information of users and they can enhance the security level of health record system.
3
Introduction
This report is designing to explain “My Health Record” system’s planning information.
Australian’s Commonwealth Government is planning for launching a health record system for all
Australians. This system will keep information about the doctor, pathologist, nurse,
administrator, and patient’s health. Part one will describe the information about planning of
security policy, development of security policy, and management of security policy.
Plan Security Policy
Role of Security Policy’s planning: Security policy plan works as formal security plan that is
utilized to define an action plan for protecting and controlling information system or computer
system such as “My Health Record” system. Typically security policy’s plan includes:
List of authorized users / persons that can be accessed the system.
Access control method (how persons will use the system)
Weakness and strengths of the system & how weaknesses will handle
Also, include system restoration / backup procedures (Techopedia, 2019).
Best Strategic planning for security policy: The strategic planning for security policy is a very
important document for organization to maintain the security of information of users. The best
strategic planning of security policy is detailed process that contains initialization, planning,
implementation, monitoring and controlling of the user’s information. The best strategic
planning prioritizes and defines security initiatives and information assurance that organization
should enhance the information’s protection & related technology (Bada et al., 2019).
The requirement of Resources planning for security policy: Proper resource planning is also
playing important role to make security policy for IT system (health record system) because,
with the help of proper resource planning, organization can make best use of each employee’s
skills. It will also help to manage the entire user’s information at one place in the IT system. It
will also helpful to predict the different risk that can be affected the security policy of IT system
in the future. The proper resource planning also keeps all the information about security policy in
visual format. Hence, it is essential for security policy’s planning in IT system.
On the basis of learned information, the two-way authentication process can be implemented in
the security policy of IT system that will be helpful for Australian’s Commonwealth Government
to save the information of users and they can enhance the security level of health record system.
3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Develop a Security Policy
Intent & Rationale of Security Policy: The main purpose of security policy is to ensure or
confirm the security’s integrity of the IT system so that maintain the security level of the IT
system. The second purpose of security policy is to plan proper guidelines for the users so that
the health information of the users can be saved or secured from the unauthorized users. The
security policy also intends to identify IT security risks in a prior manner so that they can be
eliminated at right time and secure the health information of all users in the health record system.
Definition: The security policy will work as a written document for Australian’s Commonwealth
Government to protect and handle the health information of users from security threats and
authenticated users. It also provides proper guidelines to handle the security threats if these types
of threats will occur in the health record system of Australian’s Commonwealth Government.
Responsibilities of Individuals: In this health record system, the main three members will be
responsible to develop the security policy for this IT system such as:
The first member will be responsible to implement and set the user access control & access
management system in IT health record system.
The second member will be responsible to monitor application and network security
performance by identifying irregular activities.
The third member will be responsible to control and update the security policy of a new
health record system from time to time according to the situation (Varadharajan et al., 2018).
Scope of Policy: The scope of security policy is concerned with the security and management of
the IT system’s information assets. The information assets can be health information of users,
information processing system, and information storage system in health record system. Main
scope of security policy is to maintain security in the health record system (Cho & Ip, 2018).
On the basis of learned information, it can be said that Australian’s Commonwealth Government
can use endpoint prevention and detection tools to maintain the malicious hacks in the IT system.
Manage Security Policy
Monitoring of Security Policy: Australian’s Commonwealth Government will utilize the
intrusion detection and prevention technology to monitor the security policy of the health record
system, the. The organization is also using network layer anti-malware and advanced threat
protection technique to protect health data from any security issue. They are also using data loss
prevention technique to monitor the unauthorized access of health data of user
4
Intent & Rationale of Security Policy: The main purpose of security policy is to ensure or
confirm the security’s integrity of the IT system so that maintain the security level of the IT
system. The second purpose of security policy is to plan proper guidelines for the users so that
the health information of the users can be saved or secured from the unauthorized users. The
security policy also intends to identify IT security risks in a prior manner so that they can be
eliminated at right time and secure the health information of all users in the health record system.
Definition: The security policy will work as a written document for Australian’s Commonwealth
Government to protect and handle the health information of users from security threats and
authenticated users. It also provides proper guidelines to handle the security threats if these types
of threats will occur in the health record system of Australian’s Commonwealth Government.
Responsibilities of Individuals: In this health record system, the main three members will be
responsible to develop the security policy for this IT system such as:
The first member will be responsible to implement and set the user access control & access
management system in IT health record system.
The second member will be responsible to monitor application and network security
performance by identifying irregular activities.
The third member will be responsible to control and update the security policy of a new
health record system from time to time according to the situation (Varadharajan et al., 2018).
Scope of Policy: The scope of security policy is concerned with the security and management of
the IT system’s information assets. The information assets can be health information of users,
information processing system, and information storage system in health record system. Main
scope of security policy is to maintain security in the health record system (Cho & Ip, 2018).
On the basis of learned information, it can be said that Australian’s Commonwealth Government
can use endpoint prevention and detection tools to maintain the malicious hacks in the IT system.
Manage Security Policy
Monitoring of Security Policy: Australian’s Commonwealth Government will utilize the
intrusion detection and prevention technology to monitor the security policy of the health record
system, the. The organization is also using network layer anti-malware and advanced threat
protection technique to protect health data from any security issue. They are also using data loss
prevention technique to monitor the unauthorized access of health data of user
4
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Controlling of Security Policy: By blocking the unauthorized users, the organization control
security policy of the IT system. For that purpose, they utilize the two-way authentication login
to limit these types of users. They also utilize firewalls, logical access control and antivirus
software to control the malware and unwanted material to the maintain security of IT system.
Outcome of Security Policy: The security policy has offered the physical and technical control
for protecting integrity, availability, and confidentiality of health information of users in the
health record system. These policies have also reduced the occurrence of malware and security
threats by identifying different types of security risks in the IT system (Ketel, 2018).
Update Security Policy in Regular Intervals: Organization conducts a top to bottom security
policy audits to keep track of policies and identify security issue. After that, organization
implements new security policy by implementing new antivirus and malware prevention method.
The organization also implements new rules and regulations of data security to enhance security
policy on the regular intervals in the IT health record system (Infosec Resources, 2018).
Conclusion
From part one, it has concluded that Australian’s Commonwealth Government has planned and
developed the security policy to manage the security of health data of users in the health record
system. They have also utilized different techniques to monitor and control the security policies
so that they can enhance the security policy at regular intervals.
Part Two - Conducting a Risk Assessment
Introduction
Commonwealth Bank of Australia is one of the Australian multinational banks which are
working in the US, UK, Asia, and New Zealand. It delivers the different types of financial
serveries such as fund management, broking & investment services, superannuation insurance,
etc. The Commonwealth Bank utilizes IT system to provide banking services facilities at the
instant time. For providing online banking services, Commonwealth Bank utilizes NetBank IT
system that allows bank’s customers for transferring funds, managing account information, etc.
Risk Assessment
The bank utilizes risk assessment for identifying those situations, things, processes, etc. that can
be harmed bank and user’s information. After identification of risks, bank eliminates those risks
by using proper mitigation techniques in the IT system (Modarres, 2018).
5
security policy of the IT system. For that purpose, they utilize the two-way authentication login
to limit these types of users. They also utilize firewalls, logical access control and antivirus
software to control the malware and unwanted material to the maintain security of IT system.
Outcome of Security Policy: The security policy has offered the physical and technical control
for protecting integrity, availability, and confidentiality of health information of users in the
health record system. These policies have also reduced the occurrence of malware and security
threats by identifying different types of security risks in the IT system (Ketel, 2018).
Update Security Policy in Regular Intervals: Organization conducts a top to bottom security
policy audits to keep track of policies and identify security issue. After that, organization
implements new security policy by implementing new antivirus and malware prevention method.
The organization also implements new rules and regulations of data security to enhance security
policy on the regular intervals in the IT health record system (Infosec Resources, 2018).
Conclusion
From part one, it has concluded that Australian’s Commonwealth Government has planned and
developed the security policy to manage the security of health data of users in the health record
system. They have also utilized different techniques to monitor and control the security policies
so that they can enhance the security policy at regular intervals.
Part Two - Conducting a Risk Assessment
Introduction
Commonwealth Bank of Australia is one of the Australian multinational banks which are
working in the US, UK, Asia, and New Zealand. It delivers the different types of financial
serveries such as fund management, broking & investment services, superannuation insurance,
etc. The Commonwealth Bank utilizes IT system to provide banking services facilities at the
instant time. For providing online banking services, Commonwealth Bank utilizes NetBank IT
system that allows bank’s customers for transferring funds, managing account information, etc.
Risk Assessment
The bank utilizes risk assessment for identifying those situations, things, processes, etc. that can
be harmed bank and user’s information. After identification of risks, bank eliminates those risks
by using proper mitigation techniques in the IT system (Modarres, 2018).
5
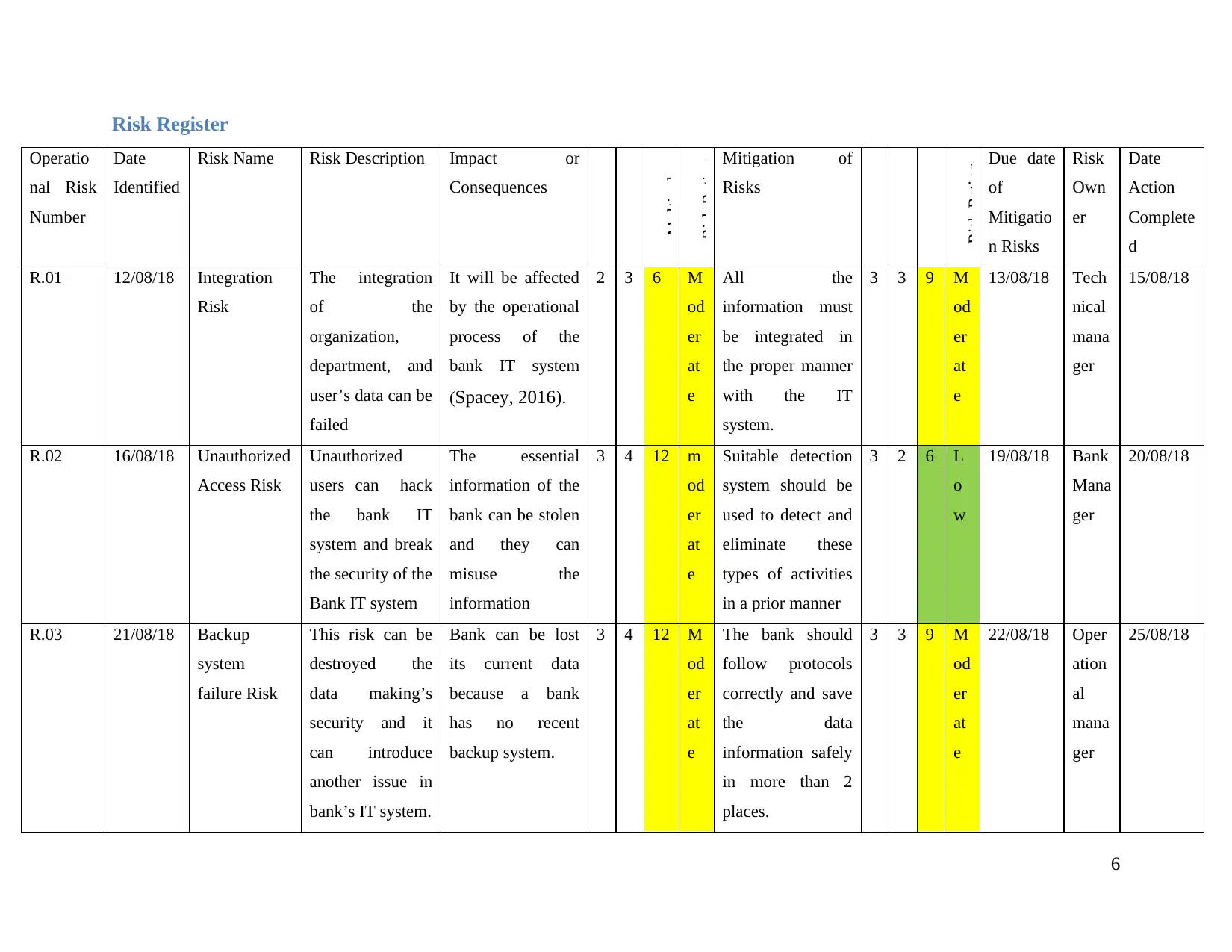
Risk Register
Operatio
nal Risk
Number
Date
Identified
Risk Name Risk Description Impact or
Consequences
Likelihood
Impact
Multipolar
Risk Rating Mitigation of
Risks
Likelihood
Impact
Multipolar
Risk Rating Due date
of
Mitigatio
n Risks
Risk
Own
er
Date
Action
Complete
d
R.01 12/08/18 Integration
Risk
The integration
of the
organization,
department, and
user’s data can be
failed
It will be affected
by the operational
process of the
bank IT system
(Spacey, 2016).
2 3 6 M
od
er
at
e
All the
information must
be integrated in
the proper manner
with the IT
system.
3 3 9 M
od
er
at
e
13/08/18 Tech
nical
mana
ger
15/08/18
R.02 16/08/18 Unauthorized
Access Risk
Unauthorized
users can hack
the bank IT
system and break
the security of the
Bank IT system
The essential
information of the
bank can be stolen
and they can
misuse the
information
3 4 12 m
od
er
at
e
Suitable detection
system should be
used to detect and
eliminate these
types of activities
in a prior manner
3 2 6 L
o
w
19/08/18 Bank
Mana
ger
20/08/18
R.03 21/08/18 Backup
system
failure Risk
This risk can be
destroyed the
data making’s
security and it
can introduce
another issue in
bank’s IT system.
Bank can be lost
its current data
because a bank
has no recent
backup system.
3 4 12 M
od
er
at
e
The bank should
follow protocols
correctly and save
the data
information safely
in more than 2
places.
3 3 9 M
od
er
at
e
22/08/18 Oper
ation
al
mana
ger
25/08/18
6
Operatio
nal Risk
Number
Date
Identified
Risk Name Risk Description Impact or
Consequences
Likelihood
Impact
Multipolar
Risk Rating Mitigation of
Risks
Likelihood
Impact
Multipolar
Risk Rating Due date
of
Mitigatio
n Risks
Risk
Own
er
Date
Action
Complete
d
R.01 12/08/18 Integration
Risk
The integration
of the
organization,
department, and
user’s data can be
failed
It will be affected
by the operational
process of the
bank IT system
(Spacey, 2016).
2 3 6 M
od
er
at
e
All the
information must
be integrated in
the proper manner
with the IT
system.
3 3 9 M
od
er
at
e
13/08/18 Tech
nical
mana
ger
15/08/18
R.02 16/08/18 Unauthorized
Access Risk
Unauthorized
users can hack
the bank IT
system and break
the security of the
Bank IT system
The essential
information of the
bank can be stolen
and they can
misuse the
information
3 4 12 m
od
er
at
e
Suitable detection
system should be
used to detect and
eliminate these
types of activities
in a prior manner
3 2 6 L
o
w
19/08/18 Bank
Mana
ger
20/08/18
R.03 21/08/18 Backup
system
failure Risk
This risk can be
destroyed the
data making’s
security and it
can introduce
another issue in
bank’s IT system.
Bank can be lost
its current data
because a bank
has no recent
backup system.
3 4 12 M
od
er
at
e
The bank should
follow protocols
correctly and save
the data
information safely
in more than 2
places.
3 3 9 M
od
er
at
e
22/08/18 Oper
ation
al
mana
ger
25/08/18
6
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
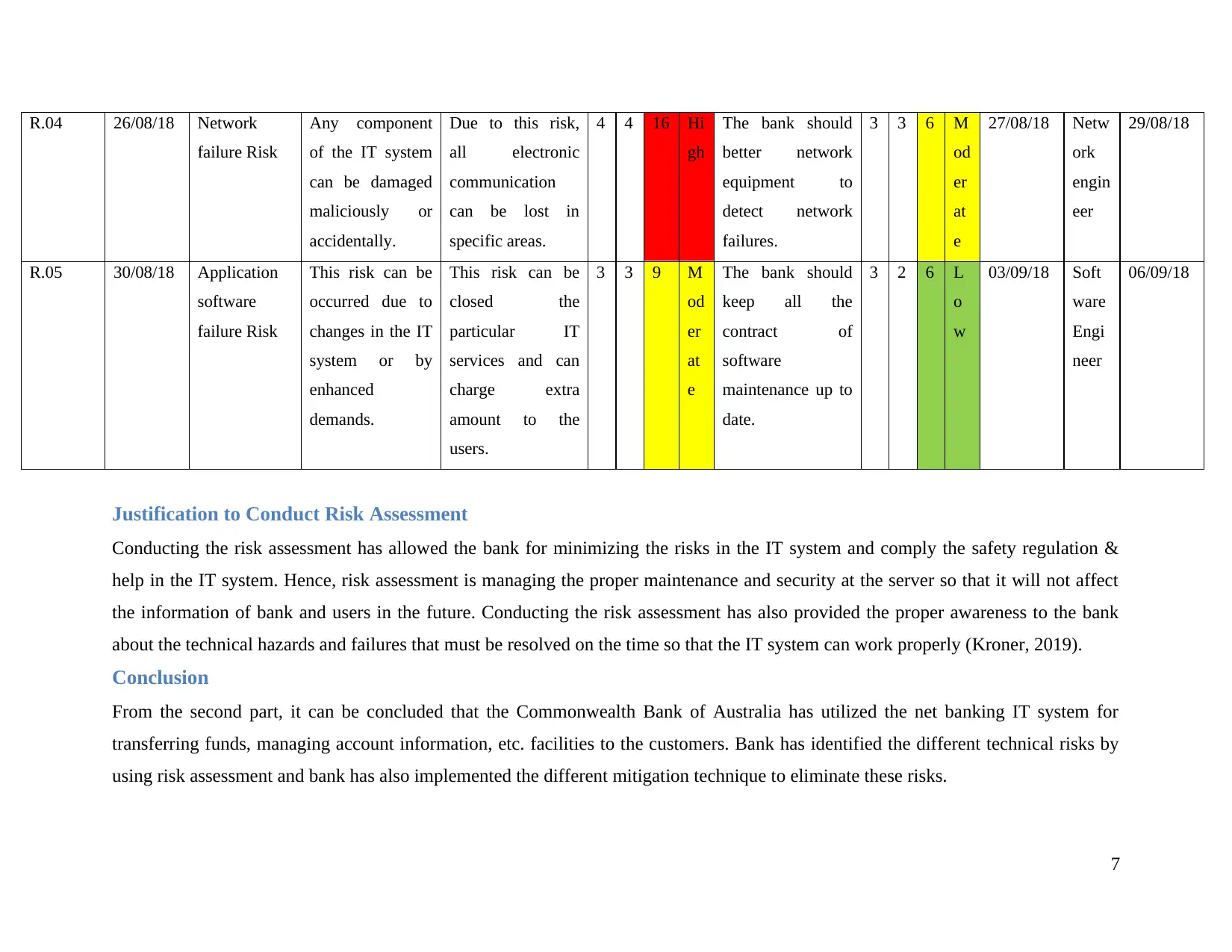
R.04 26/08/18 Network
failure Risk
Any component
of the IT system
can be damaged
maliciously or
accidentally.
Due to this risk,
all electronic
communication
can be lost in
specific areas.
4 4 16 Hi
gh
The bank should
better network
equipment to
detect network
failures.
3 3 6 M
od
er
at
e
27/08/18 Netw
ork
engin
eer
29/08/18
R.05 30/08/18 Application
software
failure Risk
This risk can be
occurred due to
changes in the IT
system or by
enhanced
demands.
This risk can be
closed the
particular IT
services and can
charge extra
amount to the
users.
3 3 9 M
od
er
at
e
The bank should
keep all the
contract of
software
maintenance up to
date.
3 2 6 L
o
w
03/09/18 Soft
ware
Engi
neer
06/09/18
Justification to Conduct Risk Assessment
Conducting the risk assessment has allowed the bank for minimizing the risks in the IT system and comply the safety regulation &
help in the IT system. Hence, risk assessment is managing the proper maintenance and security at the server so that it will not affect
the information of bank and users in the future. Conducting the risk assessment has also provided the proper awareness to the bank
about the technical hazards and failures that must be resolved on the time so that the IT system can work properly (Kroner, 2019).
Conclusion
From the second part, it can be concluded that the Commonwealth Bank of Australia has utilized the net banking IT system for
transferring funds, managing account information, etc. facilities to the customers. Bank has identified the different technical risks by
using risk assessment and bank has also implemented the different mitigation technique to eliminate these risks.
7
failure Risk
Any component
of the IT system
can be damaged
maliciously or
accidentally.
Due to this risk,
all electronic
communication
can be lost in
specific areas.
4 4 16 Hi
gh
The bank should
better network
equipment to
detect network
failures.
3 3 6 M
od
er
at
e
27/08/18 Netw
ork
engin
eer
29/08/18
R.05 30/08/18 Application
software
failure Risk
This risk can be
occurred due to
changes in the IT
system or by
enhanced
demands.
This risk can be
closed the
particular IT
services and can
charge extra
amount to the
users.
3 3 9 M
od
er
at
e
The bank should
keep all the
contract of
software
maintenance up to
date.
3 2 6 L
o
w
03/09/18 Soft
ware
Engi
neer
06/09/18
Justification to Conduct Risk Assessment
Conducting the risk assessment has allowed the bank for minimizing the risks in the IT system and comply the safety regulation &
help in the IT system. Hence, risk assessment is managing the proper maintenance and security at the server so that it will not affect
the information of bank and users in the future. Conducting the risk assessment has also provided the proper awareness to the bank
about the technical hazards and failures that must be resolved on the time so that the IT system can work properly (Kroner, 2019).
Conclusion
From the second part, it can be concluded that the Commonwealth Bank of Australia has utilized the net banking IT system for
transferring funds, managing account information, etc. facilities to the customers. Bank has identified the different technical risks by
using risk assessment and bank has also implemented the different mitigation technique to eliminate these risks.
7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

References
Bada, M., Sasse, A. M., & Nurse, J. R. (2019). Cyber security awareness campaigns: Why do
they fail to change behaviour?. arXiv preprint arXiv:1901.02672.
Cho, V., & Ip, W. H. (2018). A Study of BYOD adoption from the lens of threat and coping
appraisal of its security policy. Enterprise Information Systems, 12(6), 659-673.
Infosec Resources. (2018). Key Elements of an Information Security Policy. Retrieved from
https://resources.infosecinstitute.com/key-elements-information-security-policy/#gref
Ketel, M. (2018). Enhancing BYOD Security Through SDN. In SoutheastCon 2018, 1-2, IEEE.
Kroner, D. G. (2019). The Roles of the Risk Estimate and Clinical Information in Risk
Assessments. The Wiley International Handbook of Correctional Psychology, 446-460.
Modarres, M. (2018). What every engineer should know about reliability and risk analysis. US:
CRC Press.
Spacey, J. (2016). 36 Types of Technology Risk. Simplicable. Retrieved 5 September 2019, from
https://simplicable.com/new/technology-risk
Techopedia. (2019). What is a System Security Plan? - Definition from Techopedia. Retrieved
from https://www.techopedia.com/definition/29713/system-security-plan
Varadharajan, V., Karmakar, K., Tupakula, U., & Hitchens, M. (2018). A policy-based security
architecture for software-defined networks. IEEE Transactions on Information Forensics and
Security, 14(4), 897-912.
8
Bada, M., Sasse, A. M., & Nurse, J. R. (2019). Cyber security awareness campaigns: Why do
they fail to change behaviour?. arXiv preprint arXiv:1901.02672.
Cho, V., & Ip, W. H. (2018). A Study of BYOD adoption from the lens of threat and coping
appraisal of its security policy. Enterprise Information Systems, 12(6), 659-673.
Infosec Resources. (2018). Key Elements of an Information Security Policy. Retrieved from
https://resources.infosecinstitute.com/key-elements-information-security-policy/#gref
Ketel, M. (2018). Enhancing BYOD Security Through SDN. In SoutheastCon 2018, 1-2, IEEE.
Kroner, D. G. (2019). The Roles of the Risk Estimate and Clinical Information in Risk
Assessments. The Wiley International Handbook of Correctional Psychology, 446-460.
Modarres, M. (2018). What every engineer should know about reliability and risk analysis. US:
CRC Press.
Spacey, J. (2016). 36 Types of Technology Risk. Simplicable. Retrieved 5 September 2019, from
https://simplicable.com/new/technology-risk
Techopedia. (2019). What is a System Security Plan? - Definition from Techopedia. Retrieved
from https://www.techopedia.com/definition/29713/system-security-plan
Varadharajan, V., Karmakar, K., Tupakula, U., & Hitchens, M. (2018). A policy-based security
architecture for software-defined networks. IEEE Transactions on Information Forensics and
Security, 14(4), 897-912.
8
1 out of 8
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




