IT Risk Management for Aztek: BYOD Risk Assessment Case Study
VerifiedAdded on 2020/04/07
|17
|4994
|31
Case Study
AI Summary
This document is an IT risk assessment report for Aztek, an Australian financial firm, concerning the implementation of a Bring Your Own Device (BYOD) scheme. The report reviews financial and security aspects, addressing government regulations such as ASIC and the NSW Act, and assesses the security posture of Aztek. It identifies specific risks related to data security, including vulnerabilities in outdated systems and the challenges of managing diverse devices. The assessment includes a threat and vulnerability analysis, proposes countermeasures, and discusses data classification. The report evaluates the feasibility of the BYOD project from operational, technical, and political perspectives, highlighting both advantages like cost reduction and efficiency gains, and disadvantages such as increased security risks. Recommendations focus on flexible security strategies, device tracking, application security, and the importance of regular updates and remote management capabilities. The report emphasizes the need for a phased implementation approach to manage costs and maintain business continuity.

1
IT Risk Assessment Case Study
Aztek
9/27/2017
IT Risk Assessment Case Study
Aztek
9/27/2017
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

IT Risk Management for Aztek
Table of Contents
Financial Services Review.....................................................................................................................5
Security Posture & Review of Aztek.....................................................................................................6
Security of the Devices and Information...........................................................................................6
Application Specific Security Risks..................................................................................................7
Risk Assessment....................................................................................................................................8
TVA Analysis (Threat & Vulnerability Assessment)........................................................................8
Countermeasures and Security Steps...............................................................................................10
Data & Information Security...............................................................................................................12
Information Classification & Analysis of Security..........................................................................13
Conclusion...........................................................................................................................................15
References...........................................................................................................................................16
2
Table of Contents
Financial Services Review.....................................................................................................................5
Security Posture & Review of Aztek.....................................................................................................6
Security of the Devices and Information...........................................................................................6
Application Specific Security Risks..................................................................................................7
Risk Assessment....................................................................................................................................8
TVA Analysis (Threat & Vulnerability Assessment)........................................................................8
Countermeasures and Security Steps...............................................................................................10
Data & Information Security...............................................................................................................12
Information Classification & Analysis of Security..........................................................................13
Conclusion...........................................................................................................................................15
References...........................................................................................................................................16
2

IT Risk Management for Aztek
Executive Summary
The document is an IT risk assessment report for an Australian firm called Aztek that deals in the
domain of finance. The report covers the review of a project of Aztek from the financial and security
aspects. Bring Your Own Devices (BYOD) is scheme that has been approved and is soon going to be
implemented and the report is based on the same scheme for Aztek. The issues and specific risk areas
and their control measures have been specified.
The first section of the report explains the government regulations around the financial firms in
Australia and their relevance in case of Aztek. The bodies and acts such as ASIC, NSW, Workplace
privacy etc. have been explained along with their norms that will be applicable in this case.
The second section is the security posture review for Aztek in terms of its BYOD scheme. The current
security policy and the changes required in the current policy have been covered. Risk assessment has
been done in the next section along with the inclusion of a risk register.
The specific risks in the area of data security along with data classification have been covered in the
last section of the report.
Findings & Recommendations
There are financial and security aspects applied to understand the benefits and issues related with
BYOD scheme in Aztek. A feasibility study has been carried out for the project.
The main aim of Aztek is to provide its clients with the reliable and good quality financial services.
There are several stakeholders associated with the organization that are working to achieve this goal.
The BYOD scheme is also an attempt to achieve the same as the employees would be more
comfortable with their personal devices leading to better operational services and efficiencies. The
project has been evaluated as feasible from the organizational perspective.
Currently, there are many operational errors that the employees execute because of the limited time
that they get to spend on the tools and applications that are used. With the implementation of BYOD,
this time window will expand as the employees will be able to access the tools at any time of the day.
This will lead to better operational abilities and therefore, the project has been evaluated as feasible
from the operational perspective.
Aztek is making several changes to upgrade its technical excellence and the technical components that
will be used in the organization will be of latest versions. These tools will therefore be compatible
with the devices of the employees making the project feasible from the technical perspective.
3
Executive Summary
The document is an IT risk assessment report for an Australian firm called Aztek that deals in the
domain of finance. The report covers the review of a project of Aztek from the financial and security
aspects. Bring Your Own Devices (BYOD) is scheme that has been approved and is soon going to be
implemented and the report is based on the same scheme for Aztek. The issues and specific risk areas
and their control measures have been specified.
The first section of the report explains the government regulations around the financial firms in
Australia and their relevance in case of Aztek. The bodies and acts such as ASIC, NSW, Workplace
privacy etc. have been explained along with their norms that will be applicable in this case.
The second section is the security posture review for Aztek in terms of its BYOD scheme. The current
security policy and the changes required in the current policy have been covered. Risk assessment has
been done in the next section along with the inclusion of a risk register.
The specific risks in the area of data security along with data classification have been covered in the
last section of the report.
Findings & Recommendations
There are financial and security aspects applied to understand the benefits and issues related with
BYOD scheme in Aztek. A feasibility study has been carried out for the project.
The main aim of Aztek is to provide its clients with the reliable and good quality financial services.
There are several stakeholders associated with the organization that are working to achieve this goal.
The BYOD scheme is also an attempt to achieve the same as the employees would be more
comfortable with their personal devices leading to better operational services and efficiencies. The
project has been evaluated as feasible from the organizational perspective.
Currently, there are many operational errors that the employees execute because of the limited time
that they get to spend on the tools and applications that are used. With the implementation of BYOD,
this time window will expand as the employees will be able to access the tools at any time of the day.
This will lead to better operational abilities and therefore, the project has been evaluated as feasible
from the operational perspective.
Aztek is making several changes to upgrade its technical excellence and the technical components that
will be used in the organization will be of latest versions. These tools will therefore be compatible
with the devices of the employees making the project feasible from the technical perspective.
3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

IT Risk Management for Aztek
The report covers the several regulations and laws that will be applicable on the organization and the
project. There are no constraints or restrictions that may prevent the implementation of BYOD in
Aztek and therefore, the project has been evaluated as feasible from the political perspective.
The report also highlights numerous risks and disadvantages of the project as it would further enhance
the probability of security attacks. However, there are also controls that can be applied to make sure
that such events do not occur.
BYOD scheme will have many advantages as well. The reduction of the organizational costs will be
the prime advantage as many of the unnecessary costs will be avoided and reduced. The operational
abilities of the employees will also improve which would lead to better levels of efficiencies and
productivities. This is turn will lead to customer satisfaction and engagement with Aztek.
4
The report covers the several regulations and laws that will be applicable on the organization and the
project. There are no constraints or restrictions that may prevent the implementation of BYOD in
Aztek and therefore, the project has been evaluated as feasible from the political perspective.
The report also highlights numerous risks and disadvantages of the project as it would further enhance
the probability of security attacks. However, there are also controls that can be applied to make sure
that such events do not occur.
BYOD scheme will have many advantages as well. The reduction of the organizational costs will be
the prime advantage as many of the unnecessary costs will be avoided and reduced. The operational
abilities of the employees will also improve which would lead to better levels of efficiencies and
productivities. This is turn will lead to customer satisfaction and engagement with Aztek.
4
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

IT Risk Management for Aztek
Financial Services Review
Under the BYOD scheme, the employees of Aztek will be granted with the permission to bring and
use their devices in office for the execution and completion of office related tasks.
Aztek is an Australian firm and there are no particular laws that have been set up in Australia for the
surveillance of the employee devices in case of the outsourcing. There is no specific governance
policy set up; however, the finance industry does have certain rules and guidelines in place. These
specific rules around finance will be applicable as per the territory of operation by Aztek which would
either be South Wales or it would be Australian Capital.
There is a government body called Australian Securities and Investment Commission (ASIC) that
governs the financial activities at the federal level in Australia along with the state and territory levels.
An e-payments code is also defined under ASIC for the tracking, management and regulation of the
electronic payments (Asic, 2017).
If the organizations allow its employees to use or access the organizational components such as
specific tools or applications outside of the office boundaries, then the Government of Australia
provides them with the permission to carry out surveillance on such activities executed by the
employees. There is act that has been set up for this purpose called NSW Act. The employee activities
will be monitored by Aztek as per the principles under this act and also, the employees will be
prevented from sharing the specific organizational details with any external entity. There are specific
applications and software that can also be used for tracking of these activities.
Workplace Privacy Act 2011 is an act that defined the steps that an organization may take to track and
monitor the emails that are sent by the employees for sharing the organizational information. The logs
of the mail server are captured and reviewed as per the norms of this act defined by Australian
Government (Act, 2016).
There are various unknown and unwanted communications that often take place in organizations that
lead to the occurrence of security attacks. Telecommunications Act 1979 was defined to put a check
on such activities by tracking and monitoring the communication integrity (Coe, 2011). It shall also
be monitored by the rules under Intellectual Property.
The privacy of the information associated with Aztek can also be secured and protected by the norms
of Privacy Act (APP 5). It states that the employee-owned devices must never have the private or
sensitive information of the company or any of its stakeholders. The access rights shall be provided
5
Financial Services Review
Under the BYOD scheme, the employees of Aztek will be granted with the permission to bring and
use their devices in office for the execution and completion of office related tasks.
Aztek is an Australian firm and there are no particular laws that have been set up in Australia for the
surveillance of the employee devices in case of the outsourcing. There is no specific governance
policy set up; however, the finance industry does have certain rules and guidelines in place. These
specific rules around finance will be applicable as per the territory of operation by Aztek which would
either be South Wales or it would be Australian Capital.
There is a government body called Australian Securities and Investment Commission (ASIC) that
governs the financial activities at the federal level in Australia along with the state and territory levels.
An e-payments code is also defined under ASIC for the tracking, management and regulation of the
electronic payments (Asic, 2017).
If the organizations allow its employees to use or access the organizational components such as
specific tools or applications outside of the office boundaries, then the Government of Australia
provides them with the permission to carry out surveillance on such activities executed by the
employees. There is act that has been set up for this purpose called NSW Act. The employee activities
will be monitored by Aztek as per the principles under this act and also, the employees will be
prevented from sharing the specific organizational details with any external entity. There are specific
applications and software that can also be used for tracking of these activities.
Workplace Privacy Act 2011 is an act that defined the steps that an organization may take to track and
monitor the emails that are sent by the employees for sharing the organizational information. The logs
of the mail server are captured and reviewed as per the norms of this act defined by Australian
Government (Act, 2016).
There are various unknown and unwanted communications that often take place in organizations that
lead to the occurrence of security attacks. Telecommunications Act 1979 was defined to put a check
on such activities by tracking and monitoring the communication integrity (Coe, 2011). It shall also
be monitored by the rules under Intellectual Property.
The privacy of the information associated with Aztek can also be secured and protected by the norms
of Privacy Act (APP 5). It states that the employee-owned devices must never have the private or
sensitive information of the company or any of its stakeholders. The access rights shall be provided
5

IT Risk Management for Aztek
only on the basis of the use role and any suspicious activity shall be immediately reported to the
concerned authorities for information protection (Oaic, 2014).
Security Posture & Review of Aztek
Many of the prevailing security norms and principles at Aztek shall be analyzed and updated after the
implementation of BYOD in the company. Some of these updates will revolve around the security and
usage of mobile devices, geographical strategies and security methods in general.
The legal and political policies and rules that Aztek shall follow have been discussed in the section
above. Security is another area in which there shall be certain modifications that must be made. After
an analysis of the security aspect and status of Aztek, there are a few loopholes that have been
observed.
The organization is still using the old desktops, computer systems and networking devices
that are based upon the outdated technology. It is also difficult or impossible to upgrade these
systems to the latest concepts and advancements and this may lead to the emergence of many
security attacks.
The company is still using magnetic cards and readers for the purpose of identification of the
resources and their identity. There shall be use of advanced measures for this purpose and it
shall include the biometric recognition.
Most of the servers, applications and systems are present in-house in Aztek. This may possess
a great risk from the security point of view as there is a single failure point associated. There
shall be use of virtual spaces and third party suppliers for server locations.
Many updates need to be done on the legacy systems and databases also.
The replacement of the devices all at once will demand a huge investment for Aztek. They should
make sure that the replacement is done but it shall be carried out in a series of phases. This will ensure
that the expenses can be easily met. The use of BYOD will ensure that the business continuity is
maintained.
Security of the Devices and Information
For the organizations in which there is a single supplier or provider of all the devices and systems, the
control and management in terms of security and tracking becomes easy. There are uniform policies
that can be implemented so that the security is maintained.
In the case of organizations that use outsourcing of the devices or systems, maintenance of security is
rather difficult. In Aztek, employees will have the permission to get their devices as work. These
6
only on the basis of the use role and any suspicious activity shall be immediately reported to the
concerned authorities for information protection (Oaic, 2014).
Security Posture & Review of Aztek
Many of the prevailing security norms and principles at Aztek shall be analyzed and updated after the
implementation of BYOD in the company. Some of these updates will revolve around the security and
usage of mobile devices, geographical strategies and security methods in general.
The legal and political policies and rules that Aztek shall follow have been discussed in the section
above. Security is another area in which there shall be certain modifications that must be made. After
an analysis of the security aspect and status of Aztek, there are a few loopholes that have been
observed.
The organization is still using the old desktops, computer systems and networking devices
that are based upon the outdated technology. It is also difficult or impossible to upgrade these
systems to the latest concepts and advancements and this may lead to the emergence of many
security attacks.
The company is still using magnetic cards and readers for the purpose of identification of the
resources and their identity. There shall be use of advanced measures for this purpose and it
shall include the biometric recognition.
Most of the servers, applications and systems are present in-house in Aztek. This may possess
a great risk from the security point of view as there is a single failure point associated. There
shall be use of virtual spaces and third party suppliers for server locations.
Many updates need to be done on the legacy systems and databases also.
The replacement of the devices all at once will demand a huge investment for Aztek. They should
make sure that the replacement is done but it shall be carried out in a series of phases. This will ensure
that the expenses can be easily met. The use of BYOD will ensure that the business continuity is
maintained.
Security of the Devices and Information
For the organizations in which there is a single supplier or provider of all the devices and systems, the
control and management in terms of security and tracking becomes easy. There are uniform policies
that can be implemented so that the security is maintained.
In the case of organizations that use outsourcing of the devices or systems, maintenance of security is
rather difficult. In Aztek, employees will have the permission to get their devices as work. These
6
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

IT Risk Management for Aztek
devices will have varying properties and nature along with varied security capabilities and status. The
application of a single policy to secure all these devices will not be a possibility. Therefore,
development of suitable and proactive strategies will be required for the management and safety of all
the devices and information (Curran, Maynes and Harkin, 2015).
In case of Aztek, the common approaches that the organizations adapt to like locking of the devices
beyond office network etc. would not work. The devices are the personal properties of the employees
and they will have the right to use them outside of the office. The security strategies to be
implemented will be required to be flexible and adaptable. One of the controls that may be applied
may be in the form of restriction on usage of critical organizational applications beyond office
network (Gillies, 2016).
The devices of the employees will also bring in many attacks and risks from the security perspective.
These devices may get broken, stolen or may also get lost. In case of their connectivity with the VPN
at the time of any of such incident, the information will get disclosed to the party that may access the
device. There shall be use of advanced trackers to track the devices in such events.
Issues around authority and ownership may also come up in this case. The employees would want
complete authority on their devices and may attempt to jailbreak the same to avoid the security
controls set up by the organization. This would be hazardous for the device and for the security as
well. This may lead to avoidance by the employees to bring and use their devices in office
(Tokuyoshi, 2013).
The device and information security shall be enhanced by restricting to some of the basic principles
and mechanisms towards security.
An analysis and investigation of the complete device and its properties must be done in
adherence to the security policies of Aztek before it is approved for the usage.
There shall be use of automated applications and trackers for the management of mobile
devices.
Remote management of the devices must be allowed along with the ability to wipe out all the
information remotely.
Critical and sensitive applications must not be accessible from the networks that are outside
of the office location or VPN (Beckett, 2014).
Application Specific Security Risks
7
devices will have varying properties and nature along with varied security capabilities and status. The
application of a single policy to secure all these devices will not be a possibility. Therefore,
development of suitable and proactive strategies will be required for the management and safety of all
the devices and information (Curran, Maynes and Harkin, 2015).
In case of Aztek, the common approaches that the organizations adapt to like locking of the devices
beyond office network etc. would not work. The devices are the personal properties of the employees
and they will have the right to use them outside of the office. The security strategies to be
implemented will be required to be flexible and adaptable. One of the controls that may be applied
may be in the form of restriction on usage of critical organizational applications beyond office
network (Gillies, 2016).
The devices of the employees will also bring in many attacks and risks from the security perspective.
These devices may get broken, stolen or may also get lost. In case of their connectivity with the VPN
at the time of any of such incident, the information will get disclosed to the party that may access the
device. There shall be use of advanced trackers to track the devices in such events.
Issues around authority and ownership may also come up in this case. The employees would want
complete authority on their devices and may attempt to jailbreak the same to avoid the security
controls set up by the organization. This would be hazardous for the device and for the security as
well. This may lead to avoidance by the employees to bring and use their devices in office
(Tokuyoshi, 2013).
The device and information security shall be enhanced by restricting to some of the basic principles
and mechanisms towards security.
An analysis and investigation of the complete device and its properties must be done in
adherence to the security policies of Aztek before it is approved for the usage.
There shall be use of automated applications and trackers for the management of mobile
devices.
Remote management of the devices must be allowed along with the ability to wipe out all the
information remotely.
Critical and sensitive applications must not be accessible from the networks that are outside
of the office location or VPN (Beckett, 2014).
Application Specific Security Risks
7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

IT Risk Management for Aztek
The applications that would belong to Aztek may get adversely impacted by mainly two forms of
risks. These include malware threats and attacks along with the security weaknesses. There are several
controls that are present for the avoidance and prevention of these two risk categories (Romer, 2014).
The devices and the applications that are installed in these devices must always be scanned and
updated to avoid security risks.
Risk Assessment
The process for risk assessment that shall be used in the case of Aztek shall have the framework
which should include the definition of all the functionalities along with the categories that must be
specified in terms of security and associated references. The process of security and risk management
must include the identification, protection of the assets, control of the access, identification of the
incidents, response planning and data recovery. The security measures must make sure that the
information in the database and the one that is transmitted on the networks is secured and protected.
There are various standards that have been set up to identify the security status of a particular
organization.
Tier 1: It is the security status of the organization in which the assets are partially protected
and there are no formal definitions of the controls and measures to be applied.
Tier 2: It is the security status in which the identification of the risks is completed and a
formal definition is in place for the management of the risks.
Tier 3: It is the state in which the leadership and management provide a go ahead on the
security steps to be taken and the use of methods is also explained clearly.
Tier 4: It is the state in which proactive and adaptive measures are taken that is ad-hoc in
nature and there is no constant policy for the management of the risks. However, any of the
risk or attack can be tackled in this state.
Tier-4 is the state at which Aztek must work upon in order to reach so that the risks associated with
the devices of the employees can be handled. The threats landscape is very dynamic in this case and
would be possible to be handled only by the security mechanisms as defined under tier-4 (Singh et al.,
2014).
TVA Analysis (Threat & Vulnerability Assessment)
Name of the
Risk
Impact of the
risk (5 being
Likelihood of
the risk (5
Risk Ranking (Impact x
Likelihood)
Recommended strategy for
risk control and
8
The applications that would belong to Aztek may get adversely impacted by mainly two forms of
risks. These include malware threats and attacks along with the security weaknesses. There are several
controls that are present for the avoidance and prevention of these two risk categories (Romer, 2014).
The devices and the applications that are installed in these devices must always be scanned and
updated to avoid security risks.
Risk Assessment
The process for risk assessment that shall be used in the case of Aztek shall have the framework
which should include the definition of all the functionalities along with the categories that must be
specified in terms of security and associated references. The process of security and risk management
must include the identification, protection of the assets, control of the access, identification of the
incidents, response planning and data recovery. The security measures must make sure that the
information in the database and the one that is transmitted on the networks is secured and protected.
There are various standards that have been set up to identify the security status of a particular
organization.
Tier 1: It is the security status of the organization in which the assets are partially protected
and there are no formal definitions of the controls and measures to be applied.
Tier 2: It is the security status in which the identification of the risks is completed and a
formal definition is in place for the management of the risks.
Tier 3: It is the state in which the leadership and management provide a go ahead on the
security steps to be taken and the use of methods is also explained clearly.
Tier 4: It is the state in which proactive and adaptive measures are taken that is ad-hoc in
nature and there is no constant policy for the management of the risks. However, any of the
risk or attack can be tackled in this state.
Tier-4 is the state at which Aztek must work upon in order to reach so that the risks associated with
the devices of the employees can be handled. The threats landscape is very dynamic in this case and
would be possible to be handled only by the security mechanisms as defined under tier-4 (Singh et al.,
2014).
TVA Analysis (Threat & Vulnerability Assessment)
Name of the
Risk
Impact of the
risk (5 being
Likelihood of
the risk (5
Risk Ranking (Impact x
Likelihood)
Recommended strategy for
risk control and
8
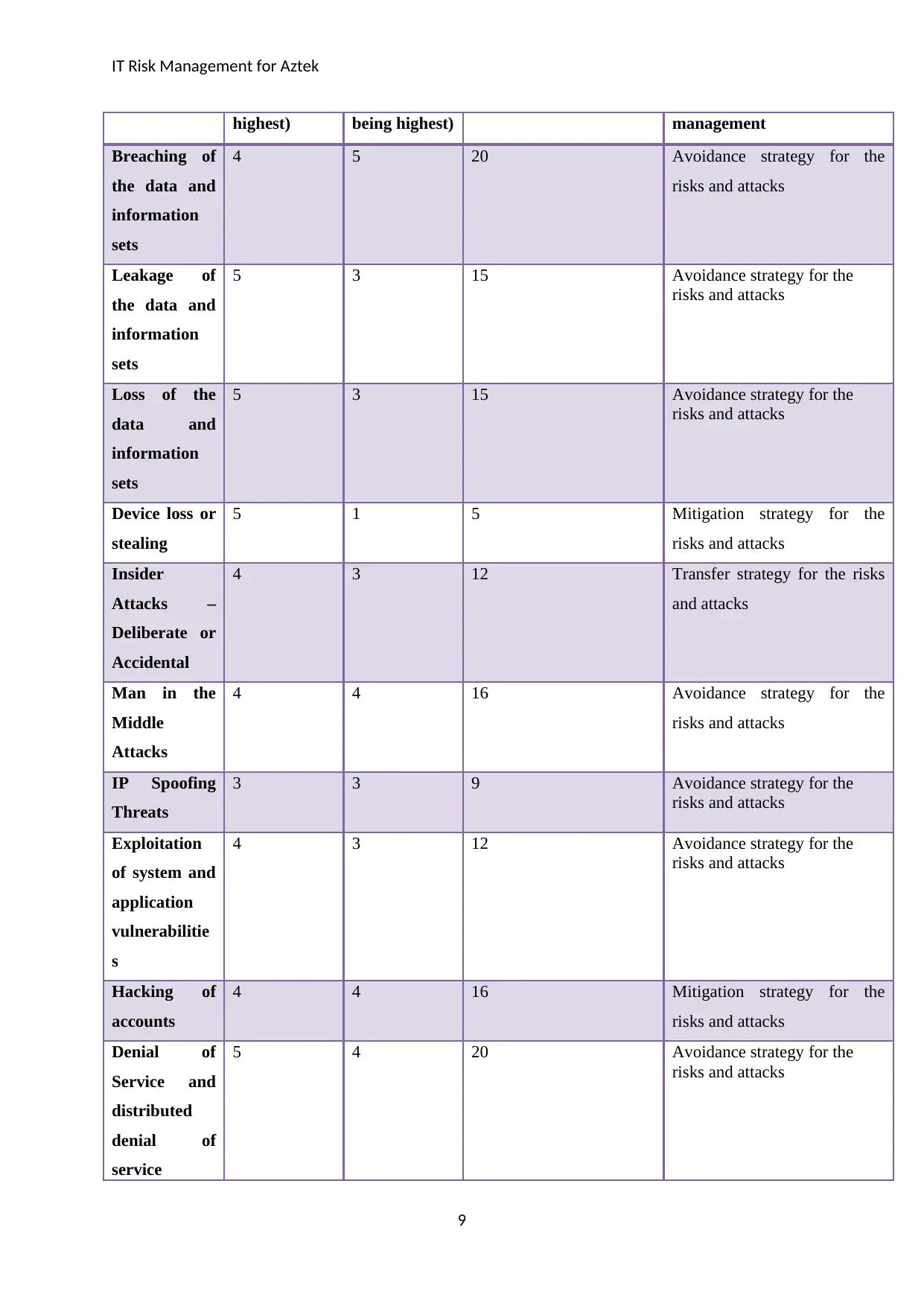
IT Risk Management for Aztek
highest) being highest) management
Breaching of
the data and
information
sets
4 5 20 Avoidance strategy for the
risks and attacks
Leakage of
the data and
information
sets
5 3 15 Avoidance strategy for the
risks and attacks
Loss of the
data and
information
sets
5 3 15 Avoidance strategy for the
risks and attacks
Device loss or
stealing
5 1 5 Mitigation strategy for the
risks and attacks
Insider
Attacks –
Deliberate or
Accidental
4 3 12 Transfer strategy for the risks
and attacks
Man in the
Middle
Attacks
4 4 16 Avoidance strategy for the
risks and attacks
IP Spoofing
Threats
3 3 9 Avoidance strategy for the
risks and attacks
Exploitation
of system and
application
vulnerabilitie
s
4 3 12 Avoidance strategy for the
risks and attacks
Hacking of
accounts
4 4 16 Mitigation strategy for the
risks and attacks
Denial of
Service and
distributed
denial of
service
5 4 20 Avoidance strategy for the
risks and attacks
9
highest) being highest) management
Breaching of
the data and
information
sets
4 5 20 Avoidance strategy for the
risks and attacks
Leakage of
the data and
information
sets
5 3 15 Avoidance strategy for the
risks and attacks
Loss of the
data and
information
sets
5 3 15 Avoidance strategy for the
risks and attacks
Device loss or
stealing
5 1 5 Mitigation strategy for the
risks and attacks
Insider
Attacks –
Deliberate or
Accidental
4 3 12 Transfer strategy for the risks
and attacks
Man in the
Middle
Attacks
4 4 16 Avoidance strategy for the
risks and attacks
IP Spoofing
Threats
3 3 9 Avoidance strategy for the
risks and attacks
Exploitation
of system and
application
vulnerabilitie
s
4 3 12 Avoidance strategy for the
risks and attacks
Hacking of
accounts
4 4 16 Mitigation strategy for the
risks and attacks
Denial of
Service and
distributed
denial of
service
5 4 20 Avoidance strategy for the
risks and attacks
9
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
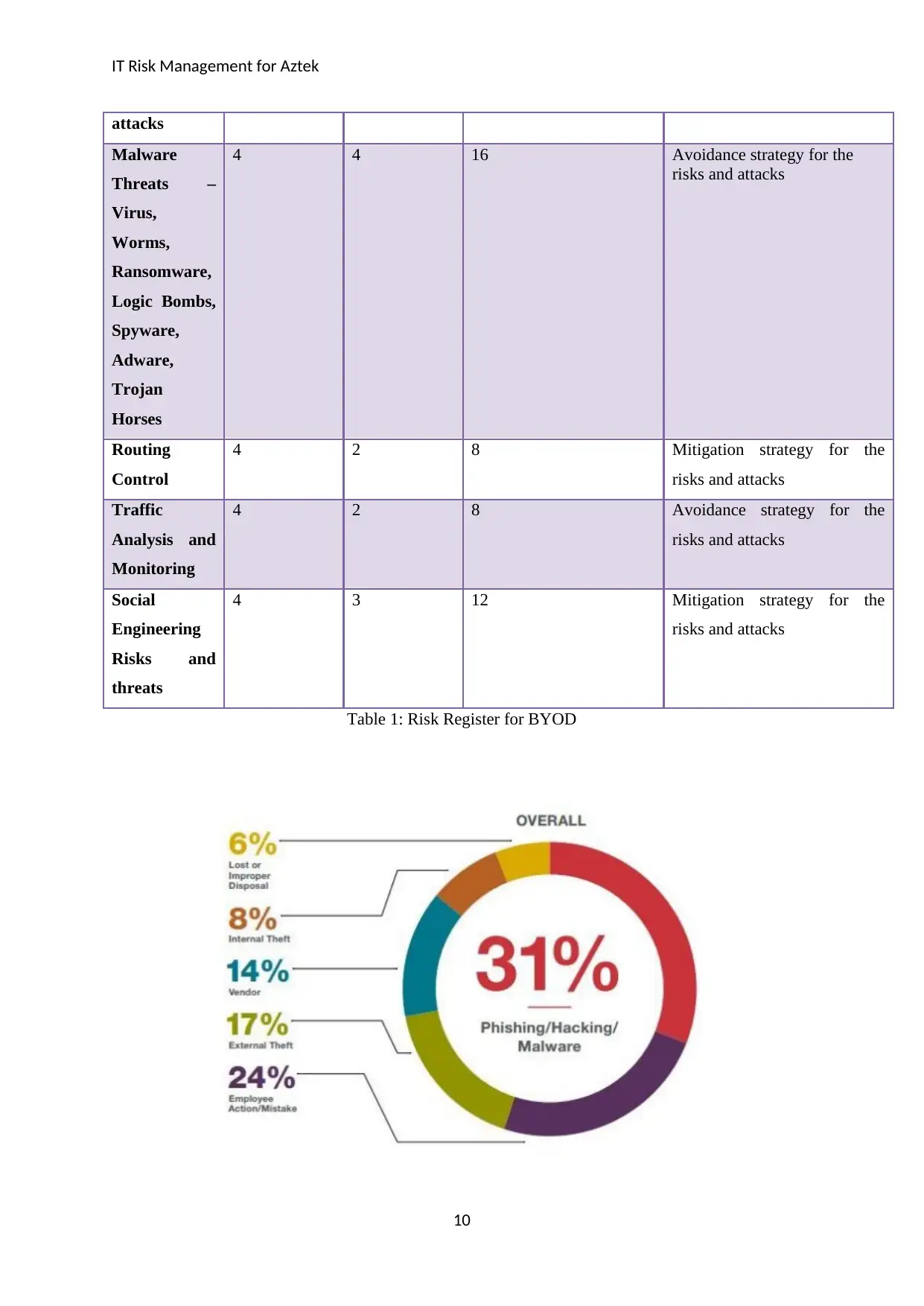
IT Risk Management for Aztek
attacks
Malware
Threats –
Virus,
Worms,
Ransomware,
Logic Bombs,
Spyware,
Adware,
Trojan
Horses
4 4 16 Avoidance strategy for the
risks and attacks
Routing
Control
4 2 8 Mitigation strategy for the
risks and attacks
Traffic
Analysis and
Monitoring
4 2 8 Avoidance strategy for the
risks and attacks
Social
Engineering
Risks and
threats
4 3 12 Mitigation strategy for the
risks and attacks
Table 1: Risk Register for BYOD
10
attacks
Malware
Threats –
Virus,
Worms,
Ransomware,
Logic Bombs,
Spyware,
Adware,
Trojan
Horses
4 4 16 Avoidance strategy for the
risks and attacks
Routing
Control
4 2 8 Mitigation strategy for the
risks and attacks
Traffic
Analysis and
Monitoring
4 2 8 Avoidance strategy for the
risks and attacks
Social
Engineering
Risks and
threats
4 3 12 Mitigation strategy for the
risks and attacks
Table 1: Risk Register for BYOD
10
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

IT Risk Management for Aztek
Figure 1: Occurrence of phishing/hacking/malware attacks in Aztek
Countermeasures and Security Steps
Many different countermeasures can be applied to control the risks and threats listed above in the
table.
Aztek must carry out a detailed planning for the management of the risks by defining the
scopes, objectives and the goals that must be set up in terms of the BYOD scheme. The use of
networks and the range of the devices must be considered for this.
The prioritization in terms of the application of the treatment strategy or the handling of the
identified risks must be set up. There shall be measures that must be taken for the analysis of
the setting up of the priorities (Kumar and Singh, 2015).
The risks that may have a higher likelihood of occurrence along with a higher impact
especially on the sensitive data sets must be separately handled. These risks shall be treated
with the highest priority.
A mapping of the risks with the countermeasures to be applied shall be done. Not all the risks can be
handled by using administrative checks only and not all of them would require extensive technical
control. Such situations shall be decided on the basis of the type of risk (Stoecklin et al., 2016).
There are many different types of controls that have been created for the purpose of risk handling and
management. These control types along with their applicability has been described below.
Preventive Controls: These are the types of controls which shall be applied for the
enhancement of the basic security for the avoidance of the attacks from occurring in Aztek.
The mechanisms like firewalls, access control and proxy servers would be included in this
category.
Detective Controls: The preventive controls may not always be successful and the malicious
attackers may give shape to the attacks. The controls like intrusion detection, integrity checks
along with maintenance of security logs shall be done for the detection of the attacks.
Corrective Controls: In spite of the attack prevention and detection, the occurrence of the
attacks may not be possible to be avoided. There are corrective controls that shall be applied
in this case so that the damage can be controlled and corrected, for instance, information
encryption (Blizzard, 2015).
11
Figure 1: Occurrence of phishing/hacking/malware attacks in Aztek
Countermeasures and Security Steps
Many different countermeasures can be applied to control the risks and threats listed above in the
table.
Aztek must carry out a detailed planning for the management of the risks by defining the
scopes, objectives and the goals that must be set up in terms of the BYOD scheme. The use of
networks and the range of the devices must be considered for this.
The prioritization in terms of the application of the treatment strategy or the handling of the
identified risks must be set up. There shall be measures that must be taken for the analysis of
the setting up of the priorities (Kumar and Singh, 2015).
The risks that may have a higher likelihood of occurrence along with a higher impact
especially on the sensitive data sets must be separately handled. These risks shall be treated
with the highest priority.
A mapping of the risks with the countermeasures to be applied shall be done. Not all the risks can be
handled by using administrative checks only and not all of them would require extensive technical
control. Such situations shall be decided on the basis of the type of risk (Stoecklin et al., 2016).
There are many different types of controls that have been created for the purpose of risk handling and
management. These control types along with their applicability has been described below.
Preventive Controls: These are the types of controls which shall be applied for the
enhancement of the basic security for the avoidance of the attacks from occurring in Aztek.
The mechanisms like firewalls, access control and proxy servers would be included in this
category.
Detective Controls: The preventive controls may not always be successful and the malicious
attackers may give shape to the attacks. The controls like intrusion detection, integrity checks
along with maintenance of security logs shall be done for the detection of the attacks.
Corrective Controls: In spite of the attack prevention and detection, the occurrence of the
attacks may not be possible to be avoided. There are corrective controls that shall be applied
in this case so that the damage can be controlled and corrected, for instance, information
encryption (Blizzard, 2015).
11
IT Risk Management for Aztek
Deterrent Controls: The malicious entities must be made aware of the organization
capabilities and readiness towards the attacks by informing them about the controls that they
have taken. All of the policies and controls will be included in this category.
Recovery Controls: Aztek must take the back up of their data sets so that in case of a risk
occurrence, the damage is controlled and the recovery of the information sets and systems is
possible. These controls would be included under this category.
Compensating Controls: There can be use of alternate security controls in case of scenarios
like unavailability of the desired control and likewise. These compensation controls shall be
used in such cases.
Data & Information Security
There are various assets that Aztek handles and manages. One of the most important and significant
asset for the organization is its data sets. Out of the risks that have been listed in the risk assessment
section of the report above, there are many risks that are specific only to the data and information
security. There are many controls that can be applied for the purpose of securing the data like
implementation of advanced access control mechanisms, recording and resolution of the incidents that
are reported by the users, adherence to the best practices and standards, implementation of anti-
malware packages and many others. The use of encryption techniques and user awareness sessions
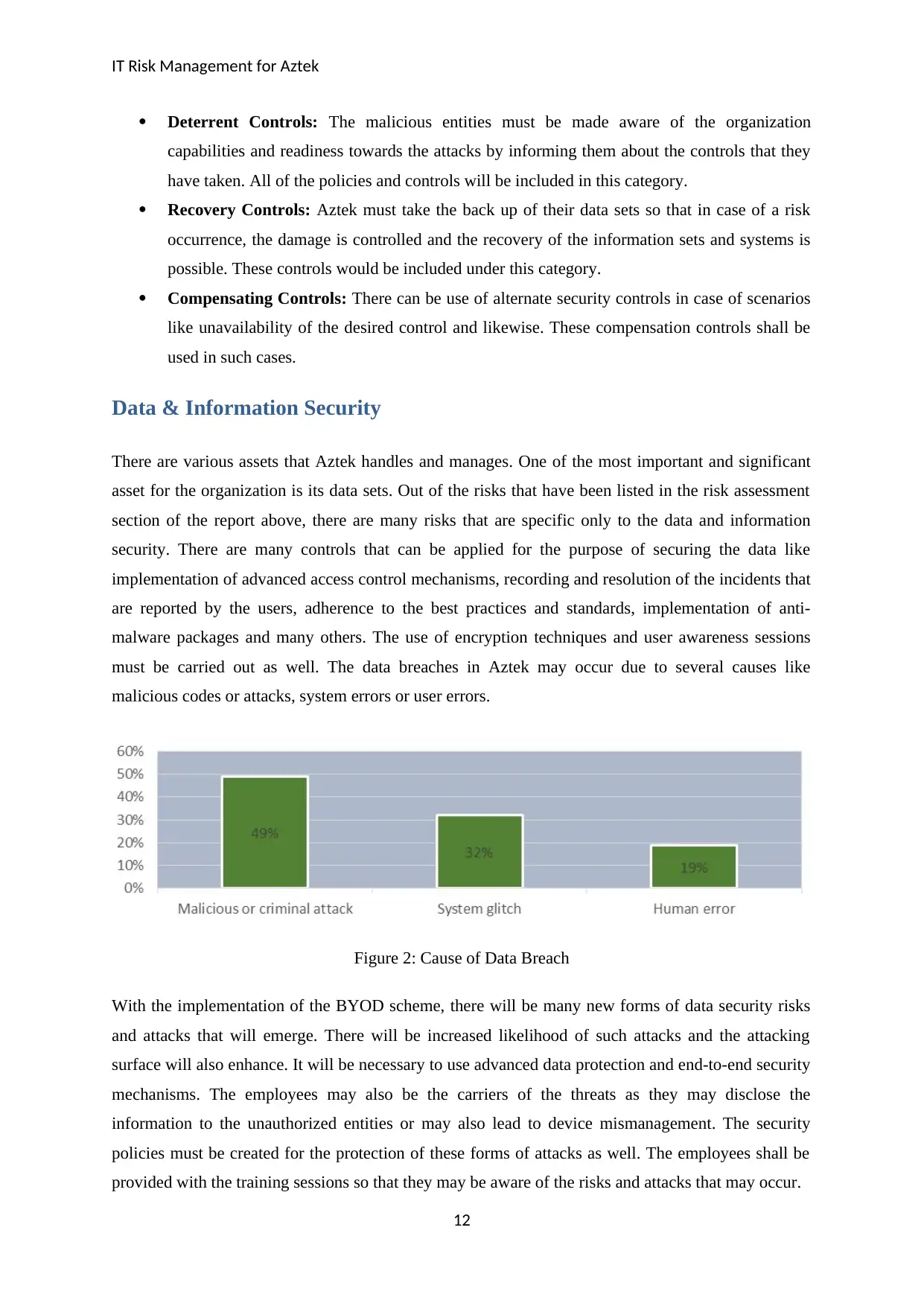
must be carried out as well. The data breaches in Aztek may occur due to several causes like
malicious codes or attacks, system errors or user errors.
Figure 2: Cause of Data Breach
With the implementation of the BYOD scheme, there will be many new forms of data security risks
and attacks that will emerge. There will be increased likelihood of such attacks and the attacking
surface will also enhance. It will be necessary to use advanced data protection and end-to-end security
mechanisms. The employees may also be the carriers of the threats as they may disclose the
information to the unauthorized entities or may also lead to device mismanagement. The security
policies must be created for the protection of these forms of attacks as well. The employees shall be
provided with the training sessions so that they may be aware of the risks and attacks that may occur.
12
Deterrent Controls: The malicious entities must be made aware of the organization
capabilities and readiness towards the attacks by informing them about the controls that they
have taken. All of the policies and controls will be included in this category.
Recovery Controls: Aztek must take the back up of their data sets so that in case of a risk
occurrence, the damage is controlled and the recovery of the information sets and systems is
possible. These controls would be included under this category.
Compensating Controls: There can be use of alternate security controls in case of scenarios
like unavailability of the desired control and likewise. These compensation controls shall be
used in such cases.
Data & Information Security
There are various assets that Aztek handles and manages. One of the most important and significant
asset for the organization is its data sets. Out of the risks that have been listed in the risk assessment
section of the report above, there are many risks that are specific only to the data and information
security. There are many controls that can be applied for the purpose of securing the data like
implementation of advanced access control mechanisms, recording and resolution of the incidents that
are reported by the users, adherence to the best practices and standards, implementation of anti-
malware packages and many others. The use of encryption techniques and user awareness sessions
must be carried out as well. The data breaches in Aztek may occur due to several causes like
malicious codes or attacks, system errors or user errors.
Figure 2: Cause of Data Breach
With the implementation of the BYOD scheme, there will be many new forms of data security risks
and attacks that will emerge. There will be increased likelihood of such attacks and the attacking
surface will also enhance. It will be necessary to use advanced data protection and end-to-end security
mechanisms. The employees may also be the carriers of the threats as they may disclose the
information to the unauthorized entities or may also lead to device mismanagement. The security
policies must be created for the protection of these forms of attacks as well. The employees shall be
provided with the training sessions so that they may be aware of the risks and attacks that may occur.
12
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 17
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





