IT Risk Management Report: Security, Threats, and Assessment
VerifiedAdded on 2020/03/03
|8
|1569
|49
Report
AI Summary
This report delves into the critical domain of IT Risk Management, examining the multifaceted aspects of securing information systems. It begins with an introduction to the significance of IT security and its impact on organizational objectives, emphasizing the necessity of effective risk management processes. The report then explores the IT security landscape, highlighting the importance of data security and the role of security policies and models in safeguarding information. It further analyzes IT security models and access controls, explaining how they ensure data integrity and confidentiality. The core of the report focuses on IT security threats and risk assessment, detailing various threats such as hackers, spyware, and cyber warfare, and the process of identifying, analyzing, and evaluating risks. The report concludes by summarizing the key findings and reinforcing the importance of proactive measures in mitigating IT risks. The report incorporates figures, tables, and references to support its findings, offering a comprehensive understanding of IT risk management principles and practices.

Running head: IT RISK MANAGEMENT
IT Risk Management
Name of the student
Name of the University
Author Note
IT Risk Management
Name of the student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1IT RISK MANAGEMENT
Table of Contents
Introduction......................................................................................................................................2
IT Security and Technology Landscape......................................................................................2
IT Security Models and Access Controls....................................................................................3
IT Security Threat and Risk Assessment.....................................................................................4
Conclusion.......................................................................................................................................5
References........................................................................................................................................6
Table of Contents
Introduction......................................................................................................................................2
IT Security and Technology Landscape......................................................................................2
IT Security Models and Access Controls....................................................................................3
IT Security Threat and Risk Assessment.....................................................................................4
Conclusion.......................................................................................................................................5
References........................................................................................................................................6

2IT RISK MANAGEMENT
Introduction
There is always a need for the implementation of an effective risk management process in
every organization irrespective of any industry. The aim of the risk management process is to
protect the organization and help it to achieve its objectives (Reason, 2016). IT risk management
deals with the proper application of the principles of risk management in IT industry (McNeil,
Frey & Embrechts, 2015). The security in IT has a relation with the access controls of the
different subjects. The IT security model is the specification and enforcement of the different
security policies. The report takes into account the threats of security in IT and the ways to assess
the risks, the security models, access controls and the technology scenario.
IT Security and Technology Landscape
The security of information and data is very significant for any type of organization since
devices contain many personal and official data that cannot be shared by everyone (Witten et al.,
2016). It will be a huge loss to an individual or any organization if any data is stolen or lost. This
has enabled the companies to think about the various IT security policies and technologies. This
security can be restored by not giving unwanted access to any users. The security of information
and computing system covers a wide area within an organization. Lack of proper understanding
of the areas and the security levels of the different devices, protocols, applications, hardware and
operating systems may cause security vulnerabilities that are having chances of affecting the
organization.
Two significant factors in the security of the information are the security model and the
security policy (Siponen, Mahmood & Pahnila, 2014). The security model defines an outline as
to how the security measures will be implemented. It provides a blueprint and architecture of the
Introduction
There is always a need for the implementation of an effective risk management process in
every organization irrespective of any industry. The aim of the risk management process is to
protect the organization and help it to achieve its objectives (Reason, 2016). IT risk management
deals with the proper application of the principles of risk management in IT industry (McNeil,
Frey & Embrechts, 2015). The security in IT has a relation with the access controls of the
different subjects. The IT security model is the specification and enforcement of the different
security policies. The report takes into account the threats of security in IT and the ways to assess
the risks, the security models, access controls and the technology scenario.
IT Security and Technology Landscape
The security of information and data is very significant for any type of organization since
devices contain many personal and official data that cannot be shared by everyone (Witten et al.,
2016). It will be a huge loss to an individual or any organization if any data is stolen or lost. This
has enabled the companies to think about the various IT security policies and technologies. This
security can be restored by not giving unwanted access to any users. The security of information
and computing system covers a wide area within an organization. Lack of proper understanding
of the areas and the security levels of the different devices, protocols, applications, hardware and
operating systems may cause security vulnerabilities that are having chances of affecting the
organization.
Two significant factors in the security of the information are the security model and the
security policy (Siponen, Mahmood & Pahnila, 2014). The security model defines an outline as
to how the security measures will be implemented. It provides a blueprint and architecture of the
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3IT RISK MANAGEMENT
computer system that has the chance of getting affected by malware or hackers. A security policy
on the other hand, provides an outline as to how the data are accessed, what type of security is
needed and what are the actions that need to be taken to protect the data from getting affected or
lost. The security policy gives an outline of a computing device. The security model gives an
outline of the actions that need to be taken when the necessary requirements are not met. A
security model helps in outlining the required logic as well as the rules that can be implemented
to make it sure that no lower-level subject can access the higher-level objects in any
unauthorized way (Petritsch, 2014). It provides necessary explanation about the development of
the computing system to support the security policies.
IT Security Models and Access Controls
An IT security model is a type of template that provides a description as to how the
security of information is carried out and governed in an organization (Islam et al., 2015). A
security model helps in mapping the abstract goals of the policies of information system terms
through proper specification of the techniques and data structures that are significant for the
enforcement of the security policies (Peltier, 2016).
Access control of the subjects in a computer system is very significant. The subjects can
be any processes, user or computer and the access control deals with whether the subjects are
able to perform certain operations like read, write, search, execute and delete properly on any
objects like a tuple in a database, any files, resources, tables or any service. The main aim of the
access control is to preserve the integrity as well as confidentiality of information (Albrechtsen,
2015). The policies of access control define the permissions of the subjects in the computing
system. These policies are framed on the basis of access control models. These models define the
relationships among the operations, subjects, objects and permissions.
computer system that has the chance of getting affected by malware or hackers. A security policy
on the other hand, provides an outline as to how the data are accessed, what type of security is
needed and what are the actions that need to be taken to protect the data from getting affected or
lost. The security policy gives an outline of a computing device. The security model gives an
outline of the actions that need to be taken when the necessary requirements are not met. A
security model helps in outlining the required logic as well as the rules that can be implemented
to make it sure that no lower-level subject can access the higher-level objects in any
unauthorized way (Petritsch, 2014). It provides necessary explanation about the development of
the computing system to support the security policies.
IT Security Models and Access Controls
An IT security model is a type of template that provides a description as to how the
security of information is carried out and governed in an organization (Islam et al., 2015). A
security model helps in mapping the abstract goals of the policies of information system terms
through proper specification of the techniques and data structures that are significant for the
enforcement of the security policies (Peltier, 2016).
Access control of the subjects in a computer system is very significant. The subjects can
be any processes, user or computer and the access control deals with whether the subjects are
able to perform certain operations like read, write, search, execute and delete properly on any
objects like a tuple in a database, any files, resources, tables or any service. The main aim of the
access control is to preserve the integrity as well as confidentiality of information (Albrechtsen,
2015). The policies of access control define the permissions of the subjects in the computing
system. These policies are framed on the basis of access control models. These models define the
relationships among the operations, subjects, objects and permissions.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
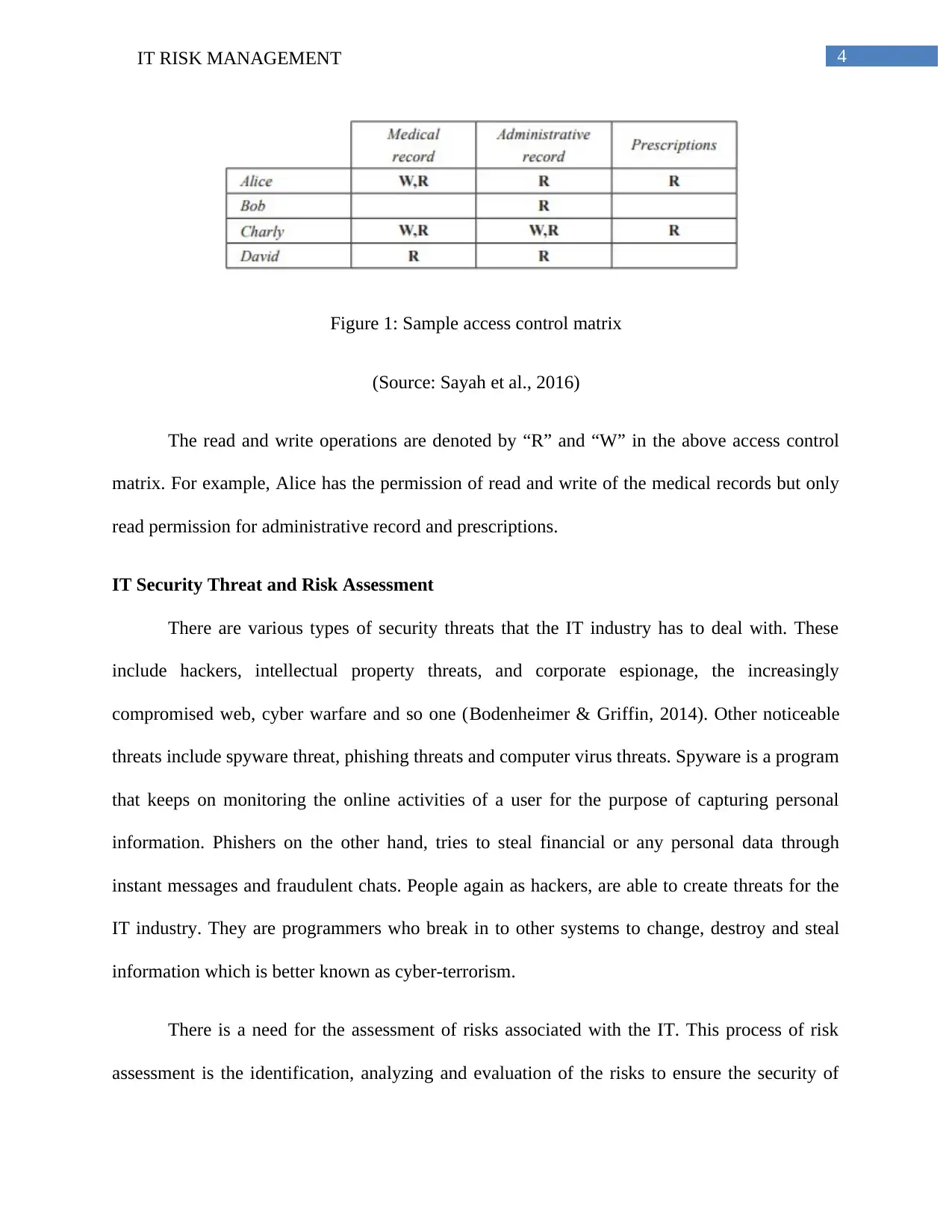
4IT RISK MANAGEMENT
Figure 1: Sample access control matrix
(Source: Sayah et al., 2016)
The read and write operations are denoted by “R” and “W” in the above access control
matrix. For example, Alice has the permission of read and write of the medical records but only
read permission for administrative record and prescriptions.
IT Security Threat and Risk Assessment
There are various types of security threats that the IT industry has to deal with. These
include hackers, intellectual property threats, and corporate espionage, the increasingly
compromised web, cyber warfare and so one (Bodenheimer & Griffin, 2014). Other noticeable
threats include spyware threat, phishing threats and computer virus threats. Spyware is a program
that keeps on monitoring the online activities of a user for the purpose of capturing personal
information. Phishers on the other hand, tries to steal financial or any personal data through
instant messages and fraudulent chats. People again as hackers, are able to create threats for the
IT industry. They are programmers who break in to other systems to change, destroy and steal
information which is better known as cyber-terrorism.
There is a need for the assessment of risks associated with the IT. This process of risk
assessment is the identification, analyzing and evaluation of the risks to ensure the security of
Figure 1: Sample access control matrix
(Source: Sayah et al., 2016)
The read and write operations are denoted by “R” and “W” in the above access control
matrix. For example, Alice has the permission of read and write of the medical records but only
read permission for administrative record and prescriptions.
IT Security Threat and Risk Assessment
There are various types of security threats that the IT industry has to deal with. These
include hackers, intellectual property threats, and corporate espionage, the increasingly
compromised web, cyber warfare and so one (Bodenheimer & Griffin, 2014). Other noticeable
threats include spyware threat, phishing threats and computer virus threats. Spyware is a program
that keeps on monitoring the online activities of a user for the purpose of capturing personal
information. Phishers on the other hand, tries to steal financial or any personal data through
instant messages and fraudulent chats. People again as hackers, are able to create threats for the
IT industry. They are programmers who break in to other systems to change, destroy and steal
information which is better known as cyber-terrorism.
There is a need for the assessment of risks associated with the IT. This process of risk
assessment is the identification, analyzing and evaluation of the risks to ensure the security of

5IT RISK MANAGEMENT
information (Webb et al., 2014). The need for the assessment is to reduce the wastage of efforts,
resources and time. The results of the risk assessment help in formulating strategies in
determining appropriate actions and priorities to manage the security risks. An integrated
assessment of the security risk and the audit approach create a balance between the risks of IT
and the businesses and keep a control of the infrastructures like business processes, databases,
network and platform and applications.
Conclusion
The report has inferred about the different risks that are associated with the information
technology industry. The companies as well as the individuals of the IT industry are facing lot of
problems regarding the security of the information of the various systems of IT. Two important
factors for the security of information in IT have been taken into account in the report. The
various risks have been described in details that will give the companies an insight into how the
data can be stolen. This has prompted the companies to make necessary risks assessments to take
precautionary measures in saving the relevant data.
information (Webb et al., 2014). The need for the assessment is to reduce the wastage of efforts,
resources and time. The results of the risk assessment help in formulating strategies in
determining appropriate actions and priorities to manage the security risks. An integrated
assessment of the security risk and the audit approach create a balance between the risks of IT
and the businesses and keep a control of the infrastructures like business processes, databases,
network and platform and applications.
Conclusion
The report has inferred about the different risks that are associated with the information
technology industry. The companies as well as the individuals of the IT industry are facing lot of
problems regarding the security of the information of the various systems of IT. Two important
factors for the security of information in IT have been taken into account in the report. The
various risks have been described in details that will give the companies an insight into how the
data can be stolen. This has prompted the companies to make necessary risks assessments to take
precautionary measures in saving the relevant data.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6IT RISK MANAGEMENT
References
Albrechtsen, E. (2015). Major accident prevention and management of information systems
security in technology-based work processes. Journal of Loss Prevention in the Process
Industries, 36, 84-91.
Bodenheimer, D. Z., & Griffin, G. (2014). Pillaging the Digital Treasure Troves: The
Technology, Economics, and Law of Cyber Espionage. Scitech Lawyer, 10(2), 16.
Islam, S., Ouedraogo, M., Kalloniatis, C., Mouratidis, H., & Gritzalis, S. (2015). Assurance of
Security and Privacy Requirements for Cloud Deployment Model. IEEE Transactions on
Cloud Computing.
McNeil, A. J., Frey, R., & Embrechts, P. (2015). Quantitative risk management: Concepts,
techniques and tools. Princeton university press.
Peltier, T. R. (2016). Information Security Policies, Procedures, and Standards: guidelines for
effective information security management. CRC Press.
Petritsch, H. (2014). Break-Glass: Handling Exceptional Situations in Access Control. Springer.
Reason, J. (2016). Managing the risks of organizational accidents. Routledge.
Sayah, T., Coquery, E., Thion, R., & Hacid, M. S. (2016). Access Control Enforcement for
Selective Disclosure of Linked Data. In International Workshop on Security and Trust
Management (pp. 47-63). Springer International Publishing.
References
Albrechtsen, E. (2015). Major accident prevention and management of information systems
security in technology-based work processes. Journal of Loss Prevention in the Process
Industries, 36, 84-91.
Bodenheimer, D. Z., & Griffin, G. (2014). Pillaging the Digital Treasure Troves: The
Technology, Economics, and Law of Cyber Espionage. Scitech Lawyer, 10(2), 16.
Islam, S., Ouedraogo, M., Kalloniatis, C., Mouratidis, H., & Gritzalis, S. (2015). Assurance of
Security and Privacy Requirements for Cloud Deployment Model. IEEE Transactions on
Cloud Computing.
McNeil, A. J., Frey, R., & Embrechts, P. (2015). Quantitative risk management: Concepts,
techniques and tools. Princeton university press.
Peltier, T. R. (2016). Information Security Policies, Procedures, and Standards: guidelines for
effective information security management. CRC Press.
Petritsch, H. (2014). Break-Glass: Handling Exceptional Situations in Access Control. Springer.
Reason, J. (2016). Managing the risks of organizational accidents. Routledge.
Sayah, T., Coquery, E., Thion, R., & Hacid, M. S. (2016). Access Control Enforcement for
Selective Disclosure of Linked Data. In International Workshop on Security and Trust
Management (pp. 47-63). Springer International Publishing.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7IT RISK MANAGEMENT
Siponen, M., Mahmood, M. A., & Pahnila, S. (2014). Employees’ adherence to information
security policies: An exploratory field study. Information & management, 51(2), 217-
224.
Webb, J., Ahmad, A., Maynard, S. B., & Shanks, G. (2014). A situation awareness model for
information security risk management. Computers & security, 44, 1-15.
Witten, I. H., Frank, E., Hall, M. A., & Pal, C. J. (2016). Data Mining: Practical machine
learning tools and techniques. Morgan Kaufmann.
Siponen, M., Mahmood, M. A., & Pahnila, S. (2014). Employees’ adherence to information
security policies: An exploratory field study. Information & management, 51(2), 217-
224.
Webb, J., Ahmad, A., Maynard, S. B., & Shanks, G. (2014). A situation awareness model for
information security risk management. Computers & security, 44, 1-15.
Witten, I. H., Frank, E., Hall, M. A., & Pal, C. J. (2016). Data Mining: Practical machine
learning tools and techniques. Morgan Kaufmann.
1 out of 8
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





