University IT Risk Management and Big Data Security Analysis Report
VerifiedAdded on 2020/04/07
|15
|3063
|81
Report
AI Summary
This report comprehensively examines IT risk management within the context of big data, focusing on the ENISA environment. It begins with an overview of big data security infrastructure, including a diagram, and identifies the most significant threats, such as malicious code, data leaks, denial-of-service attacks, rogue certificate usage, improper security system design, and identity fraud. The report delves into threat agents, including corporations, cybercriminals, cyber terrorists, employees, nation states, and script kiddies, and assesses their potential impact and probability. It then explores the ETL (ENISA Threat Landscape) process, suggesting improvements in threat prioritization based on impact rather than frequency. The report concludes by evaluating the current state of IT security at ENISA and recommending measures like enhanced security systems and access controls to mitigate identified risks. The report emphasizes the need for continuous updates to address evolving cyber threats in the big data landscape.

Running head: IT RISK MANAGEMENT
IT Risk Management
Name of the Student
Name of the University
Author’s Note
IT Risk Management
Name of the Student
Name of the University
Author’s Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1IT RISK MANAGEMENT
Table of Contents
Introduction..........................................................................................................................2
1. Overview of the case study and illustration of the big data security Infrastructure........2
1.1 Overview....................................................................................................................2
1.2. Infrastructure Diagram..............................................................................................3
2. Top and most significant threats......................................................................................5
2.1. Most significant threat identified..............................................................................7
3. Threat Agents, Their Impact and threat probability........................................................7
4. ETL process Improvement..............................................................................................9
5. Current State of IT security in ENISA..........................................................................10
Conclusion.........................................................................................................................11
References..........................................................................................................................12
Table of Contents
Introduction..........................................................................................................................2
1. Overview of the case study and illustration of the big data security Infrastructure........2
1.1 Overview....................................................................................................................2
1.2. Infrastructure Diagram..............................................................................................3
2. Top and most significant threats......................................................................................5
2.1. Most significant threat identified..............................................................................7
3. Threat Agents, Their Impact and threat probability........................................................7
4. ETL process Improvement..............................................................................................9
5. Current State of IT security in ENISA..........................................................................10
Conclusion.........................................................................................................................11
References..........................................................................................................................12

2IT RISK MANAGEMENT
Introductions
The case study discusses the threats and the security issues associated with the process of
data mining and use of big data. Big data refers to the storage of large amount of Data that can be
mined for significant benefits in organizations and business (Wu et al., 2014). These data can be
a very useful for business related decision making and therefore holds utmost importance. Thus,
there are certain risks associated with the mining of big data. The case study discusses the
different threats associated with ENISA and the various processes that can be implemented in
elimination of the threats. The different threats agents and the threat mitigation processes are
discussed in the following paragraphs (Inukollu, Arsi & Ravuri, 2014)-
1. Overview of the case study and illustration of the big data security Infrastructure
1.1 Overview
The case study focuses on the big data landscape and the ENISA big data threat. The
content of the case study puts a light to the different use of big data and the associated risk with
the process of data mining (Wright & De Hert, 2012). The key threat agents associated with the
data breaches due the use of big data is clearly depicted in the case study. It further elaborates the
impact of the big data, which is huge in thriving of the data driven economy. The use of big data
is wide in fields such as military applications, fighting terrorism and research work (Gonzalez et
al., 2012). Therefore, protecting the process of data mining and ensuring a secure data mining is
essential. The case study discusses the process of ETL ( ENISA threat landscape) and suggests
different risk management and mitigation processes for mitigating the risks associated with the
big data landscape ( ENISA 2017). The case study aims at giving providing a clear picture of the
risks and threats associated with the big data landscape. The risk is widespread due to the
Introductions
The case study discusses the threats and the security issues associated with the process of
data mining and use of big data. Big data refers to the storage of large amount of Data that can be
mined for significant benefits in organizations and business (Wu et al., 2014). These data can be
a very useful for business related decision making and therefore holds utmost importance. Thus,
there are certain risks associated with the mining of big data. The case study discusses the
different threats associated with ENISA and the various processes that can be implemented in
elimination of the threats. The different threats agents and the threat mitigation processes are
discussed in the following paragraphs (Inukollu, Arsi & Ravuri, 2014)-
1. Overview of the case study and illustration of the big data security Infrastructure
1.1 Overview
The case study focuses on the big data landscape and the ENISA big data threat. The
content of the case study puts a light to the different use of big data and the associated risk with
the process of data mining (Wright & De Hert, 2012). The key threat agents associated with the
data breaches due the use of big data is clearly depicted in the case study. It further elaborates the
impact of the big data, which is huge in thriving of the data driven economy. The use of big data
is wide in fields such as military applications, fighting terrorism and research work (Gonzalez et
al., 2012). Therefore, protecting the process of data mining and ensuring a secure data mining is
essential. The case study discusses the process of ETL ( ENISA threat landscape) and suggests
different risk management and mitigation processes for mitigating the risks associated with the
big data landscape ( ENISA 2017). The case study aims at giving providing a clear picture of the
risks and threats associated with the big data landscape. The risk is widespread due to the
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3IT RISK MANAGEMENT
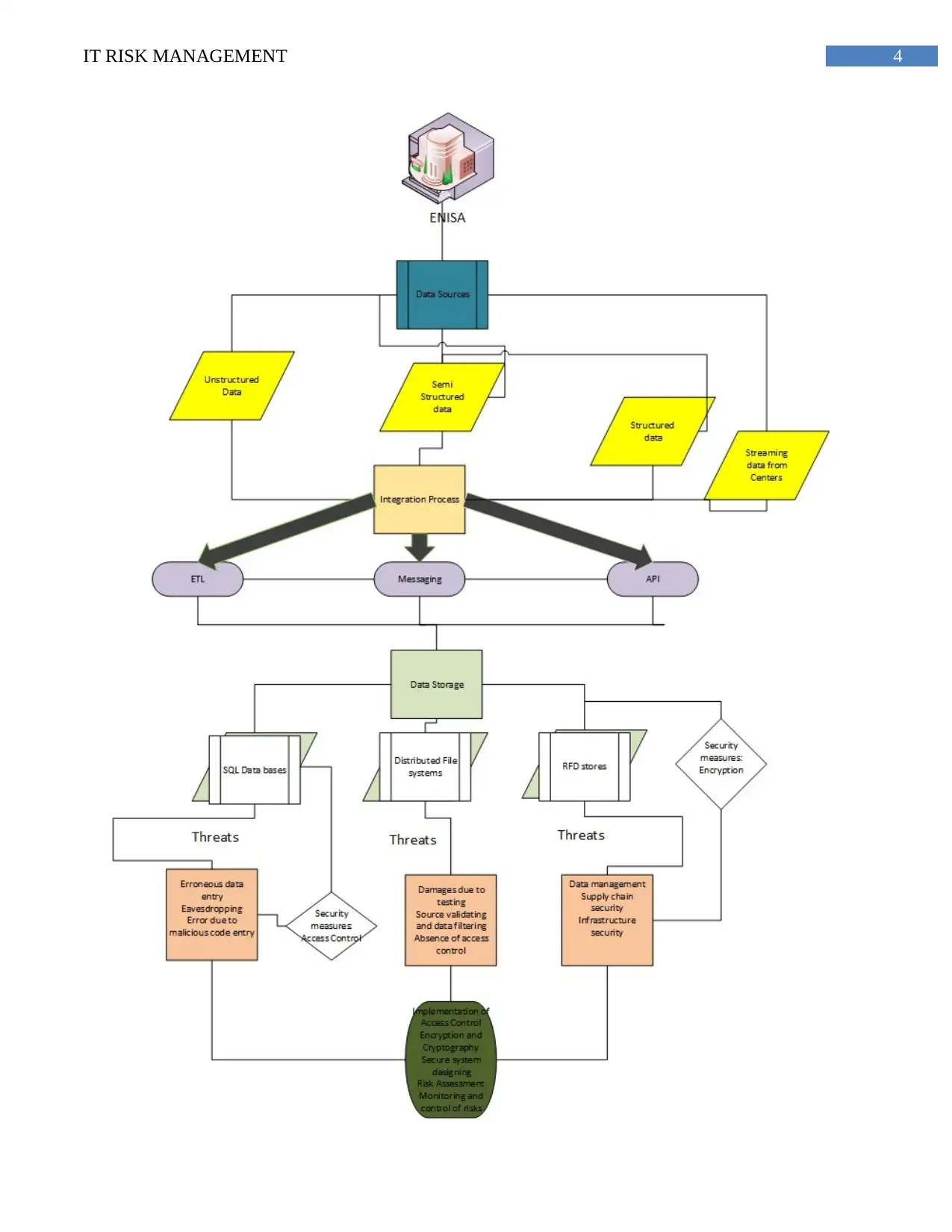
involvement of cloud storage in order to store the big data. The threat infrastructure diagram of
ENISA is illustrated below-
1.2. Infrastructure Diagram
involvement of cloud storage in order to store the big data. The threat infrastructure diagram of
ENISA is illustrated below-
1.2. Infrastructure Diagram
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4IT RISK MANAGEMENT

5IT RISK MANAGEMENT
Figure 1: Representing the ENISA big data security Infrastructure
(Source: created by author using MS Visio)
2. Top and most significant threats
The storage and the access of huge amount of data is subjected to different types of risks.
The top threats associated with ENISA are elaborated below ( ENISA, 2017)-
1) Malicious code/ software activity: One of the top threats associated with the big data is
the use of malicious code and software in order to extract information unethically. These are doe
by infusing different threat agents into the system, which includes, viruses, Trojan horses,
trapdoors, backdoors, ransomware and so on. These threats are infused with the system with the
help of certain malicious codes and software. The attacker installs these programs into the
system and gains access to the entire system by running these codes (Theoharidou, Tsalis &
Gritzalis, 2013). The risk from these malicious activity is high since the malware can easily
spread to different systems.
The assets that are mainly targeted by this threat include database and computing
infrastructure model.
2) Data leak due to unsecure API: Big data is based on cloud storage as it helps in easy
access of the data. however, cloud storage is a very unsecure platform and the use of unsecure
API further leads to significant data breaches and data loss. Different types of injection attacks
can be launched making use of unsecure API and therefore this can be considered as a significant
threat agent.
Figure 1: Representing the ENISA big data security Infrastructure
(Source: created by author using MS Visio)
2. Top and most significant threats
The storage and the access of huge amount of data is subjected to different types of risks.
The top threats associated with ENISA are elaborated below ( ENISA, 2017)-
1) Malicious code/ software activity: One of the top threats associated with the big data is
the use of malicious code and software in order to extract information unethically. These are doe
by infusing different threat agents into the system, which includes, viruses, Trojan horses,
trapdoors, backdoors, ransomware and so on. These threats are infused with the system with the
help of certain malicious codes and software. The attacker installs these programs into the
system and gains access to the entire system by running these codes (Theoharidou, Tsalis &
Gritzalis, 2013). The risk from these malicious activity is high since the malware can easily
spread to different systems.
The assets that are mainly targeted by this threat include database and computing
infrastructure model.
2) Data leak due to unsecure API: Big data is based on cloud storage as it helps in easy
access of the data. however, cloud storage is a very unsecure platform and the use of unsecure
API further leads to significant data breaches and data loss. Different types of injection attacks
can be launched making use of unsecure API and therefore this can be considered as a significant
threat agent.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6IT RISK MANAGEMENT
The assets that are targeted by this threat includes software and computing models of the
information system.
3) Denial of service attack: Denial of service attack freezes the system thus making the
resources unavailable for the legitimate users. A severe denial of service attack may lead to the
permanent unavailability of the resources. These attacks can however be controlled by implying
effective measures (Tan et al., 2014).
The assets that are mainly targeted by this attack includes networks and servers of the
system.
4) Rogue Certificate usage: This is other threat agent associated with the illegal usage of
data and data breach. Rogue or false certificate can be used unethically to gain access to the
systems the attackers are unauthorized to access (Pearson, 2013). This may result in severe data
loss, data leakage and data modification and misuse of data
The assets that are mainly targeted by this threat include hardware , software and its
associated data.
5) Improper designing of the security systems: This is another major reason of the data
security issues associated with the big data. Improper designing of security system or using an
out of date security may lead to severe data loss. An inadequate system may further lead to
improper data update thus giving rise to data redundancy (Theoharidou et al., 2013).
The assets that are targeted by this threat include data and applications.
The assets that are targeted by this threat includes software and computing models of the
information system.
3) Denial of service attack: Denial of service attack freezes the system thus making the
resources unavailable for the legitimate users. A severe denial of service attack may lead to the
permanent unavailability of the resources. These attacks can however be controlled by implying
effective measures (Tan et al., 2014).
The assets that are mainly targeted by this attack includes networks and servers of the
system.
4) Rogue Certificate usage: This is other threat agent associated with the illegal usage of
data and data breach. Rogue or false certificate can be used unethically to gain access to the
systems the attackers are unauthorized to access (Pearson, 2013). This may result in severe data
loss, data leakage and data modification and misuse of data
The assets that are mainly targeted by this threat include hardware , software and its
associated data.
5) Improper designing of the security systems: This is another major reason of the data
security issues associated with the big data. Improper designing of security system or using an
out of date security may lead to severe data loss. An inadequate system may further lead to
improper data update thus giving rise to data redundancy (Theoharidou et al., 2013).
The assets that are targeted by this threat include data and applications.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7IT RISK MANAGEMENT
6) Identity fraud: Accessing the data by unauthorized person, by impersonating someone
one else can be termed as identity theft. This is a significant threat as it might result in loss of
confidential data and information (Roberts, Indermaur & Spiranovic, 2013).
The assets that are mainly targeted by the threat identity fraud includes personal
identifiable information , back end services and the servers associated with the system.
2.1. Most significant threat identified
Out of the top threats identified in the previous section of the report, the top threat is
definitely the threat associated with the usage or infusion of malicious codes and programs into
the system. This is because, with the help of this threat, the attacker may easily gain access to the
system and manipulate the data stored in them (Chen & Zhao, 2012). This risk associated with
this type of threat is very high and therefore, this threat agent is the most significant threat agent
in the big data landscape (Pavlyushchik, 2014).
3. Threat Agents, Their Impact and threat probability
The top threat agents associated with the big data landscape, identified from the case
study are elaborated below-
1) Corporation: The corporation or the organization that uses big data for its business
benefits is a major threat agent associated with the security concerns related to the big data. This
is because it is easier for them to manipulate and misuse these data fro their business benefits and
gain competitive advantage in the market.
2)Cyber criminals: This is one of the most significant threat agents associated with the
data breach and data loss. The main objective of cyber criminals is financial benefit by making
6) Identity fraud: Accessing the data by unauthorized person, by impersonating someone
one else can be termed as identity theft. This is a significant threat as it might result in loss of
confidential data and information (Roberts, Indermaur & Spiranovic, 2013).
The assets that are mainly targeted by the threat identity fraud includes personal
identifiable information , back end services and the servers associated with the system.
2.1. Most significant threat identified
Out of the top threats identified in the previous section of the report, the top threat is
definitely the threat associated with the usage or infusion of malicious codes and programs into
the system. This is because, with the help of this threat, the attacker may easily gain access to the
system and manipulate the data stored in them (Chen & Zhao, 2012). This risk associated with
this type of threat is very high and therefore, this threat agent is the most significant threat agent
in the big data landscape (Pavlyushchik, 2014).
3. Threat Agents, Their Impact and threat probability
The top threat agents associated with the big data landscape, identified from the case
study are elaborated below-
1) Corporation: The corporation or the organization that uses big data for its business
benefits is a major threat agent associated with the security concerns related to the big data. This
is because it is easier for them to manipulate and misuse these data fro their business benefits and
gain competitive advantage in the market.
2)Cyber criminals: This is one of the most significant threat agents associated with the
data breach and data loss. The main objective of cyber criminals is financial benefit by making

8IT RISK MANAGEMENT
the use of the mined data and therefore the impact of the attack by these threat agents is very
high.
3) Cyber Terrorist: Cyber terrorists are more dangerous than cyber criminals as the
methods used in the launching the attacks are more sophisticated in case of cyber terrorists.
These threat agents mainly target large organizations, as impact over these organization effects a
large part of the society as well (Taylor, Fritsch & Liederbach, 2014).
4) Employees: One of the major threat agents is employees of the organization. They can
be termed as threat insiders as well. Employee posses a sound knowledge of the data and security
system of a particular organization and therefore manipulation of data by the threat insider is
easier and sometimes unrecognizable.
5) Nation States: Nation States is one of the most significant threat agent associated with
the security issues of big data landscape. Nation states are the most sophisticated cyber criminals
and have high-level skill and expertise.
6) Script Kiddies: This threat agents uses ready-made code and programs in order to
launch an attack. Therefore, this type of attack and the threat agent is less dangerous and can be
eliminated by implementing proper security measures.
Minimizing the Impact of the Threat
In order to minimize the threats associated with the big data, the recommended measures
that can be taken are elaborated below-
the use of the mined data and therefore the impact of the attack by these threat agents is very
high.
3) Cyber Terrorist: Cyber terrorists are more dangerous than cyber criminals as the
methods used in the launching the attacks are more sophisticated in case of cyber terrorists.
These threat agents mainly target large organizations, as impact over these organization effects a
large part of the society as well (Taylor, Fritsch & Liederbach, 2014).
4) Employees: One of the major threat agents is employees of the organization. They can
be termed as threat insiders as well. Employee posses a sound knowledge of the data and security
system of a particular organization and therefore manipulation of data by the threat insider is
easier and sometimes unrecognizable.
5) Nation States: Nation States is one of the most significant threat agent associated with
the security issues of big data landscape. Nation states are the most sophisticated cyber criminals
and have high-level skill and expertise.
6) Script Kiddies: This threat agents uses ready-made code and programs in order to
launch an attack. Therefore, this type of attack and the threat agent is less dangerous and can be
eliminated by implementing proper security measures.
Minimizing the Impact of the Threat
In order to minimize the threats associated with the big data, the recommended measures
that can be taken are elaborated below-
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9IT RISK MANAGEMENT
1) Using an effective security system coupled with the cryptographic methods of
encryption limits the use and access of the data thus preventing the data loss and data breaches
(Stallings & Tahiliani, 2014).
2) Access control can be implied to limit the access of data only to authorized person.
These may reduce the data breach considerably (Brucker et al., 2012). Access control only
enables a registered person to access and data.
3) Training the staffs and employees in order to build awareness among them can be an
effective method of preventing any sorts of threats by threat insider.
Probability Trend of the Threats
The probability of the threat is high as the attacker is coming up with different methods
of implementing an attack. In order to prevent these attacks, proper security measures are needed
to be taken. The associated threats are increasing in number and therefore, it becomes essential to
eliminate it as soon as possible.
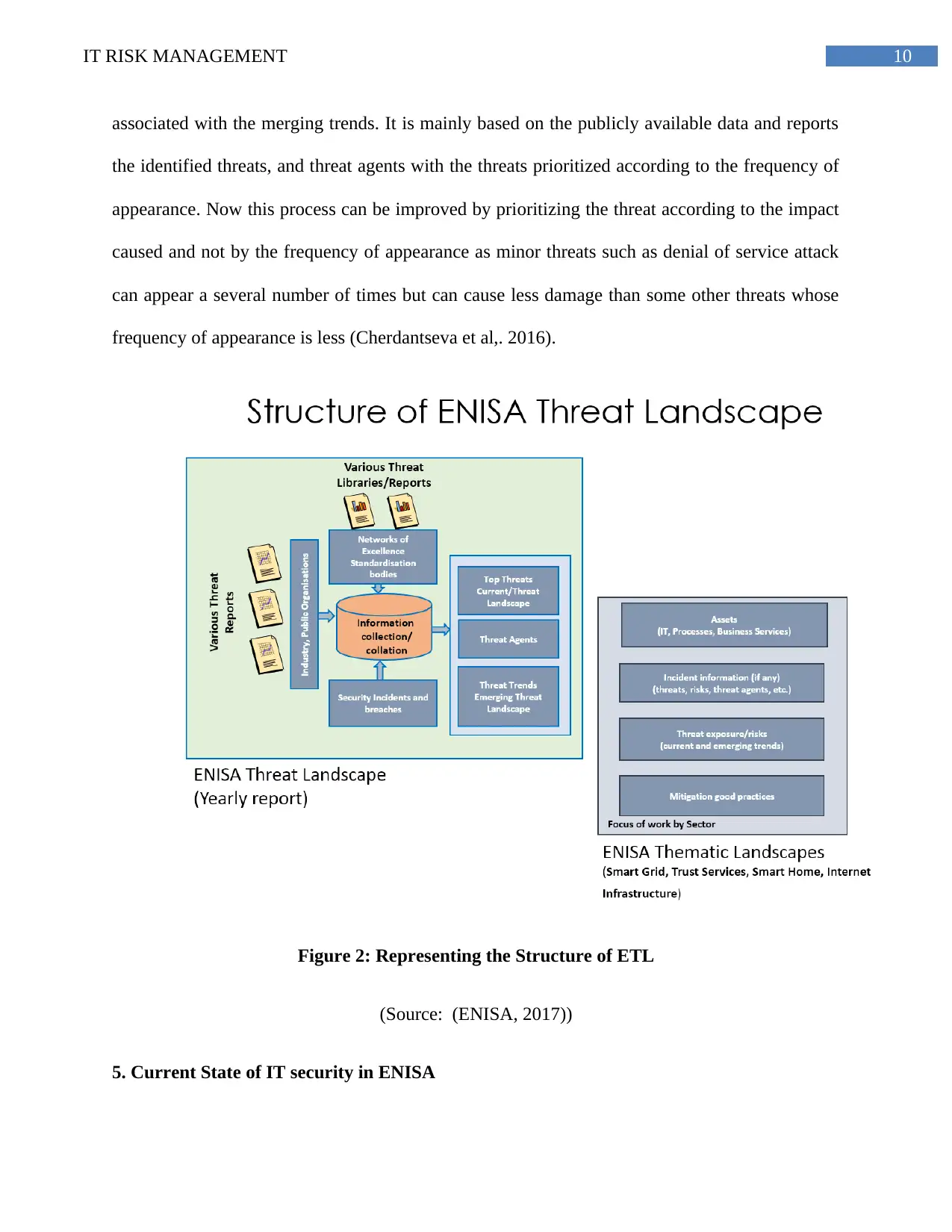
4. ETL process Improvement
ETL or the ENISA Threat landscape investigates and reports about the threats associated
with different organizations. The document or report by ETL mainly deals with the threats
associated with the information and communication technology assets (ENISA, 2017). The
major loophole in the process of ETL is that, I only focuses on the technology issue and not the
issues cause by the threat agents. The process of ETL can be improved by including a detailed
and a structured report of the all types of threats associated with the big data and their possible
effects. ENISA threat landscape or ETL provides a structure and the overview of the threats
1) Using an effective security system coupled with the cryptographic methods of
encryption limits the use and access of the data thus preventing the data loss and data breaches
(Stallings & Tahiliani, 2014).
2) Access control can be implied to limit the access of data only to authorized person.
These may reduce the data breach considerably (Brucker et al., 2012). Access control only
enables a registered person to access and data.
3) Training the staffs and employees in order to build awareness among them can be an
effective method of preventing any sorts of threats by threat insider.
Probability Trend of the Threats
The probability of the threat is high as the attacker is coming up with different methods
of implementing an attack. In order to prevent these attacks, proper security measures are needed
to be taken. The associated threats are increasing in number and therefore, it becomes essential to
eliminate it as soon as possible.
4. ETL process Improvement
ETL or the ENISA Threat landscape investigates and reports about the threats associated
with different organizations. The document or report by ETL mainly deals with the threats
associated with the information and communication technology assets (ENISA, 2017). The
major loophole in the process of ETL is that, I only focuses on the technology issue and not the
issues cause by the threat agents. The process of ETL can be improved by including a detailed
and a structured report of the all types of threats associated with the big data and their possible
effects. ENISA threat landscape or ETL provides a structure and the overview of the threats
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
10IT RISK MANAGEMENT
associated with the merging trends. It is mainly based on the publicly available data and reports
the identified threats, and threat agents with the threats prioritized according to the frequency of
appearance. Now this process can be improved by prioritizing the threat according to the impact
caused and not by the frequency of appearance as minor threats such as denial of service attack
can appear a several number of times but can cause less damage than some other threats whose
frequency of appearance is less (Cherdantseva et al,. 2016).
Figure 2: Representing the Structure of ETL
(Source: (ENISA, 2017))
5. Current State of IT security in ENISA
associated with the merging trends. It is mainly based on the publicly available data and reports
the identified threats, and threat agents with the threats prioritized according to the frequency of
appearance. Now this process can be improved by prioritizing the threat according to the impact
caused and not by the frequency of appearance as minor threats such as denial of service attack
can appear a several number of times but can cause less damage than some other threats whose
frequency of appearance is less (Cherdantseva et al,. 2016).
Figure 2: Representing the Structure of ETL
(Source: (ENISA, 2017))
5. Current State of IT security in ENISA

11IT RISK MANAGEMENT
ENISA is not satisfied with the current security state of the organization as the
organization is still exposed to the several cyber threats. The security essentials are needed to be
updated in order to ensure the security of the big data. The threat agents and the attackers are
growing stronger day by day and therefore updating the security systems becomes essential (Von
Solms & Van Niekerk, 2013). A stronger security system and proper supervision of the system is
essential. The report identifies and discusses the risk associated with the information system of
ENSA, which proves that there are certain loopholes associated with the structure of the security
essentials in the organization. This is a major reason of ENISA being unsatisfied with the current
security state. Different security measures can be undertaken by ENISA in order to remove the
risks associated with the security system, which includes, using a proper intrusion detection
system in order to prevent the data loss and data manipulation. Furthermore, the process of ETL
can be improved by prioritizing the risks according to their impact in order to detect and
eliminate several threats associated with the system (Albakri et al., 2014).
Conclusion
Therefore, from the above discussion, it can be concluded that ENISA is exposed to
number of threats and the report discusses the different threat agents responsible for data
breaches, data loss and data manipulation. The report suggests the different procedures by which
the risk associated with the process of mining the big data can be eliminated. The ENISA Threat
landscape deals with identifying and reporting different threats associated with various
organizations. Use of big data is very significant in today’s world and therefore, ensuring various
security measures for the same is essential as well. The report concludes with the current state of
IT security in ENISA and recommends few ways to address the issues.
ENISA is not satisfied with the current security state of the organization as the
organization is still exposed to the several cyber threats. The security essentials are needed to be
updated in order to ensure the security of the big data. The threat agents and the attackers are
growing stronger day by day and therefore updating the security systems becomes essential (Von
Solms & Van Niekerk, 2013). A stronger security system and proper supervision of the system is
essential. The report identifies and discusses the risk associated with the information system of
ENSA, which proves that there are certain loopholes associated with the structure of the security
essentials in the organization. This is a major reason of ENISA being unsatisfied with the current
security state. Different security measures can be undertaken by ENISA in order to remove the
risks associated with the security system, which includes, using a proper intrusion detection
system in order to prevent the data loss and data manipulation. Furthermore, the process of ETL
can be improved by prioritizing the risks according to their impact in order to detect and
eliminate several threats associated with the system (Albakri et al., 2014).
Conclusion
Therefore, from the above discussion, it can be concluded that ENISA is exposed to
number of threats and the report discusses the different threat agents responsible for data
breaches, data loss and data manipulation. The report suggests the different procedures by which
the risk associated with the process of mining the big data can be eliminated. The ENISA Threat
landscape deals with identifying and reporting different threats associated with various
organizations. Use of big data is very significant in today’s world and therefore, ensuring various
security measures for the same is essential as well. The report concludes with the current state of
IT security in ENISA and recommends few ways to address the issues.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 15
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





