ITC596 IT Risk Management Assessment: Biometrics and WSN Security
VerifiedAdded on 2024/07/01
|15
|2412
|429
Report
AI Summary
This report provides an assessment of IT risk management, focusing on biometric authentication methods such as fingerprint recognition, hand geometry, and iris recognition, along with an analysis of wireless sensor network (WSN) security. It details the advantages and disadvantages of each biometric method, highlighting their applications in various sectors. The report also addresses privacy concerns related to data collection and storage, emphasizing the importance of privacy-enhancing technologies like encryption. Furthermore, it explores the architecture and characteristics of WSNs, identifying potential threats such as botnets and hacking. The report concludes by referencing relevant literature, offering a comprehensive overview of the discussed topics. Desklib provides access to this and other solved assignments for students.

ITC596 IT RISK MANAGEMENT
ASSESSMENT 2
ASSESSMENT 2
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
PART-2...................................................................................................................................... 3
Part A..................................................................................................................................... 3
Fingerprint..........................................................................................................................3
Hand Geometry.................................................................................................................. 8
Iris Recognition................................................................................................................ 10
Part B....................................................................................................................................11
Part-C...................................................................................................................................13
References:............................................................................................................................... 16
PART-2...................................................................................................................................... 3
Part A..................................................................................................................................... 3
Fingerprint..........................................................................................................................3
Hand Geometry.................................................................................................................. 8
Iris Recognition................................................................................................................ 10
Part B....................................................................................................................................11
Part-C...................................................................................................................................13
References:............................................................................................................................... 16

PART-2
Part A
Fingerprint
The word Biometric has two parts i.e. Bio and Metric. The word bio is defined as life and
metric is used to measure something. The Biometrics is used to determine the actual identity
of a person. This aspect of identification is mostly used than any other methods like pattern
drawing, passwords and pin numbers. These type systems used to detect the identification of
the validate users in the system. Biometric system is divided into various types which contain
fingerprint recognition, iris pattern, face recognition, vein pattern etc.
Figure 1: Biometric Sensors
Biometric of a person is used to recognize a person’s verification. A biometric sensor is
tending to change a person into electrical signals. Methods for biometric includes fingerprint
identification, face recognition, iris recognition, voice recognition etc. These sensors use
many different measures many different aspects like speed, temperature and many different
types of energies. In every type of biometric devices, at least one type of sensor device is
used. The devices which use biometrics use many applications like high-quality camera for
face detection, capture voice in microphones. Some biometrics is specially designed to
identify special features in recognizing technology. (Higgins et al., 2009)
Part A
Fingerprint
The word Biometric has two parts i.e. Bio and Metric. The word bio is defined as life and
metric is used to measure something. The Biometrics is used to determine the actual identity
of a person. This aspect of identification is mostly used than any other methods like pattern
drawing, passwords and pin numbers. These type systems used to detect the identification of
the validate users in the system. Biometric system is divided into various types which contain
fingerprint recognition, iris pattern, face recognition, vein pattern etc.
Figure 1: Biometric Sensors
Biometric of a person is used to recognize a person’s verification. A biometric sensor is
tending to change a person into electrical signals. Methods for biometric includes fingerprint
identification, face recognition, iris recognition, voice recognition etc. These sensors use
many different measures many different aspects like speed, temperature and many different
types of energies. In every type of biometric devices, at least one type of sensor device is
used. The devices which use biometrics use many applications like high-quality camera for
face detection, capture voice in microphones. Some biometrics is specially designed to
identify special features in recognizing technology. (Higgins et al., 2009)
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
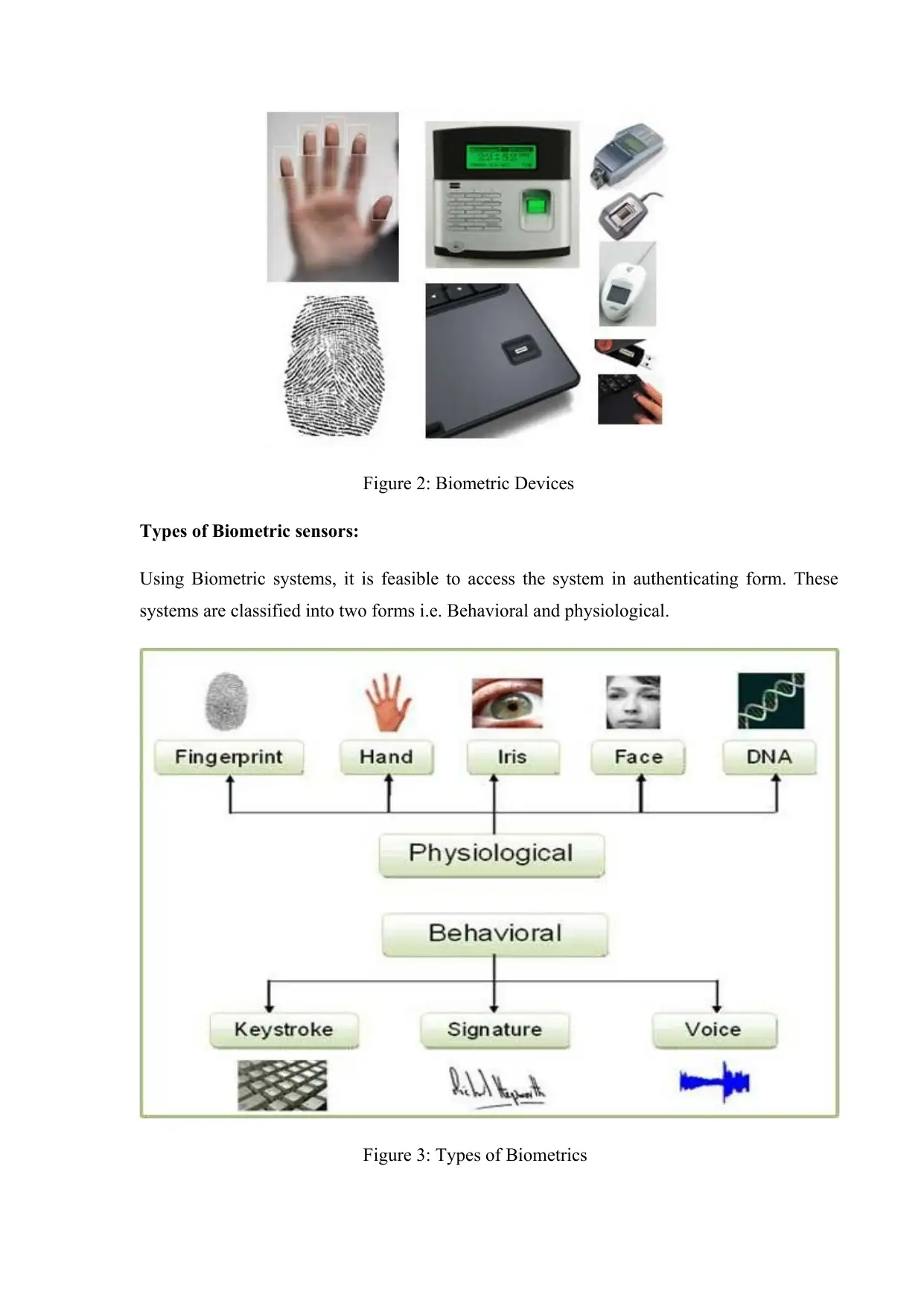
Figure 2: Biometric Devices
Types of Biometric sensors:
Using Biometric systems, it is feasible to access the system in authenticating form. These
systems are classified into two forms i.e. Behavioral and physiological.
Figure 3: Types of Biometrics
Types of Biometric sensors:
Using Biometric systems, it is feasible to access the system in authenticating form. These
systems are classified into two forms i.e. Behavioral and physiological.
Figure 3: Types of Biometrics
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Finger Print Identification: This type of verification method take the image of the finger
and store the features of the finger for further identification. This feature matches the finger
using three attempts like match the equivalent pixels between two images, match the set of
points in an image, capture ridges. This method is very stable and provides reliability to the
users. This sensor is used at doors for safety. Nowadays some banks also initiate the
fingerprint sensor recognition at ATM.
Figure 4: Finger Print Scanner device
Advantages:
1. These sensors are highly secured and unique.
2. This sensor is used to unlock the system and applications without remembering the
password.
3. Fingerprint identification provides high accuracy.
4. These sensors make system convenient and provide transaction facility in the
minimum amount of time.
5. It uses the minimum amount of data to store in the system and reduce the size of
memory.
6. It is the most widely used security method. It is difficult to create a fake identity for
the user. The users cannot guess the password to unlock the system.
Disadvantage:
1. Sometimes, hackers steal the fingerprint of the target on other surfaces and using
these prints to access the device.
2. Fingerprint details are easy to steal and if some consequences occur then a large
amount of data destroy.
and store the features of the finger for further identification. This feature matches the finger
using three attempts like match the equivalent pixels between two images, match the set of
points in an image, capture ridges. This method is very stable and provides reliability to the
users. This sensor is used at doors for safety. Nowadays some banks also initiate the
fingerprint sensor recognition at ATM.
Figure 4: Finger Print Scanner device
Advantages:
1. These sensors are highly secured and unique.
2. This sensor is used to unlock the system and applications without remembering the
password.
3. Fingerprint identification provides high accuracy.
4. These sensors make system convenient and provide transaction facility in the
minimum amount of time.
5. It uses the minimum amount of data to store in the system and reduce the size of
memory.
6. It is the most widely used security method. It is difficult to create a fake identity for
the user. The users cannot guess the password to unlock the system.
Disadvantage:
1. Sometimes, hackers steal the fingerprint of the target on other surfaces and using
these prints to access the device.
2. Fingerprint details are easy to steal and if some consequences occur then a large
amount of data destroy.

3. Sometimes, cheap components are used in the development of the device and this
results in the denial of the authorized person. This technique is very sensitive.
Example of Fingerprint application is:
A system is developed known as Automated Fingerprint identification system is a
technique which is used to store and identify data of print in the system. It is mainly used
for the identification of criminals. It helps in preventing from fraud people. This system is
also acceptable in court cases for identification. It has revealed an advanced version on
the live scanning of records. (Gu et al., 2009)
results in the denial of the authorized person. This technique is very sensitive.
Example of Fingerprint application is:
A system is developed known as Automated Fingerprint identification system is a
technique which is used to store and identify data of print in the system. It is mainly used
for the identification of criminals. It helps in preventing from fraud people. This system is
also acceptable in court cases for identification. It has revealed an advanced version on
the live scanning of records. (Gu et al., 2009)
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Hand Geometry
It identifies users with the shape of their hands. This technique measures the hand in many
ways. They compare the dimensions in multiple forms and measurements are stored in a file.
It provides access to too many systems. Hand Geometry technique is not that much unique as
fingerprint recognition but it is very highly demanding and more secured for applications.
This technique is highly reliable for the system to provide the best security to the users. In
this process of verification, the system captures the images of the hand and associates a
verification process. It checks the similarity associated and after this, it produces the results
of acceptance or rejection. It is basically based on the size of hand i.e. its length, breadth and
other aspects.
Figure 5: Hand Geometry sensor
Advantages of Hand Geometry:
1. This technology is very simple and easy for the users.
2. It is not costly for the users.
3. The data maintained in the system is easy to use and provides secure transmission of
data sets.
4. It is less used in place of other sensors like fingerprint recognition.
5. Environment factors are not considered as the major aspect and it doesn’t provide any
issue for the system.
The disadvantage of Hand Geometry:
1. It is not majorly used in the process of identification.
2. The features of the hand are not the same as it keeps changing as the growth of the
children.
3. The hand geometry system required to store a large amount of data.
It identifies users with the shape of their hands. This technique measures the hand in many
ways. They compare the dimensions in multiple forms and measurements are stored in a file.
It provides access to too many systems. Hand Geometry technique is not that much unique as
fingerprint recognition but it is very highly demanding and more secured for applications.
This technique is highly reliable for the system to provide the best security to the users. In
this process of verification, the system captures the images of the hand and associates a
verification process. It checks the similarity associated and after this, it produces the results
of acceptance or rejection. It is basically based on the size of hand i.e. its length, breadth and
other aspects.
Figure 5: Hand Geometry sensor
Advantages of Hand Geometry:
1. This technology is very simple and easy for the users.
2. It is not costly for the users.
3. The data maintained in the system is easy to use and provides secure transmission of
data sets.
4. It is less used in place of other sensors like fingerprint recognition.
5. Environment factors are not considered as the major aspect and it doesn’t provide any
issue for the system.
The disadvantage of Hand Geometry:
1. It is not majorly used in the process of identification.
2. The features of the hand are not the same as it keeps changing as the growth of the
children.
3. The hand geometry system required to store a large amount of data.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Example of Hand Geometry application is:
It is used in Automated Identification and Data capture systems. These systems are helpful in
providing high security to the users. All the features involve the identification of a particular
user and maintain its known criteria. (Kozuka, Wan & Sato, 2008)
It is used in Automated Identification and Data capture systems. These systems are helpful in
providing high security to the users. All the features involve the identification of a particular
user and maintain its known criteria. (Kozuka, Wan & Sato, 2008)

Iris Recognition
Iris recognition system is an automatic method used to identify the individual eye and this
methodology is unique and stable for long period of time. It is the most secure method for the
identification and authentication of an individual. It considers unique patterns for people in
the recognition process. It allows searching the patterns of the individuals. Its database can
store multiple aspects and provide speed in matching the eyes recognition.
Figure 6: Iris Recognition Sensor
Advantages of Iris Recognition System:
1. Iris recognition system is one of the accurate systems for an individual to provide
authenticate access. It helps a fast accessing of the system in a valid form.
2. This system is highly scalable because it is used for both large and small-scale
systems.
3. It provides access from large distances and it is easy to use these systems.
Disadvantages of Iris Recognition system:
1. It is very costly for a person to use this feature.
2. A person is required to be in a static position for enabling the access to the users.
3. It is very difficult to provide stability to the systems due to reflection.
Example of Iris recognition application is:
It is used in the finance and banking sectors. It helps to replace the use of passwords and pins
for security and save the time in the process. These systems are expected to improve the
financial services and became free in the given amount of time. It provides safety to the
systems and gives high security to the users. (Xiao, Sun & Tan, 2012)
Iris recognition system is an automatic method used to identify the individual eye and this
methodology is unique and stable for long period of time. It is the most secure method for the
identification and authentication of an individual. It considers unique patterns for people in
the recognition process. It allows searching the patterns of the individuals. Its database can
store multiple aspects and provide speed in matching the eyes recognition.
Figure 6: Iris Recognition Sensor
Advantages of Iris Recognition System:
1. Iris recognition system is one of the accurate systems for an individual to provide
authenticate access. It helps a fast accessing of the system in a valid form.
2. This system is highly scalable because it is used for both large and small-scale
systems.
3. It provides access from large distances and it is easy to use these systems.
Disadvantages of Iris Recognition system:
1. It is very costly for a person to use this feature.
2. A person is required to be in a static position for enabling the access to the users.
3. It is very difficult to provide stability to the systems due to reflection.
Example of Iris recognition application is:
It is used in the finance and banking sectors. It helps to replace the use of passwords and pins
for security and save the time in the process. These systems are expected to improve the
financial services and became free in the given amount of time. It provides safety to the
systems and gives high security to the users. (Xiao, Sun & Tan, 2012)
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Part B
The protection is defined as the relation between the collection of data and technology
together. It allows showing the legal and certain issues in the system. Some privacy issues are
considering a wide variety of sources. The motive of data privacy is to use information and
protect individual privacy. It has contained the information about individual privacy. Some
techniques are providing for security like data security, system security, and information
security. It provides software and hardware services to utilize the issues. Some laws for
protecting and maintaining privacy are constantly changing.
Some privacy concerns are:
1. Internet: It has the power to control the information that someone leaks it on the
network. Data is available in the large amount and it can be adapted from many
sources. Some sources of the internet are required to be of privacy concern like email.
2. Cable Television: It describes the utilization of information that which type of
information should be kept private or public. The scheduled list of the events is
tracked by someone.
3. Medical: It is important for a person to not leak the medical information in front of
others. It is required to be kept private.
Privacy Enhancing Technologies:
The amount of data which comes from personal data is increased. Some risk occurs in
data protection and some laws are generated. Sometimes, laws are created to protect the
world I response to users. There is some organization which helps to provide great use of
automated controls. Privacy Enhancing Technologies can protect confidential
information:
1. Encryption: Today, encryption is used to protect data. Encryption helps in protecting
data and security laws. Encryption is defined as a simple and highly effective tool.
2. Application programming: In software systems, private data determines how rules
are processed. Those rules are required to help data and regulate the protection
requirements. These activities are applied on software provider than protecting data.
The protection is defined as the relation between the collection of data and technology
together. It allows showing the legal and certain issues in the system. Some privacy issues are
considering a wide variety of sources. The motive of data privacy is to use information and
protect individual privacy. It has contained the information about individual privacy. Some
techniques are providing for security like data security, system security, and information
security. It provides software and hardware services to utilize the issues. Some laws for
protecting and maintaining privacy are constantly changing.
Some privacy concerns are:
1. Internet: It has the power to control the information that someone leaks it on the
network. Data is available in the large amount and it can be adapted from many
sources. Some sources of the internet are required to be of privacy concern like email.
2. Cable Television: It describes the utilization of information that which type of
information should be kept private or public. The scheduled list of the events is
tracked by someone.
3. Medical: It is important for a person to not leak the medical information in front of
others. It is required to be kept private.
Privacy Enhancing Technologies:
The amount of data which comes from personal data is increased. Some risk occurs in
data protection and some laws are generated. Sometimes, laws are created to protect the
world I response to users. There is some organization which helps to provide great use of
automated controls. Privacy Enhancing Technologies can protect confidential
information:
1. Encryption: Today, encryption is used to protect data. Encryption helps in protecting
data and security laws. Encryption is defined as a simple and highly effective tool.
2. Application programming: In software systems, private data determines how rules
are processed. Those rules are required to help data and regulate the protection
requirements. These activities are applied on software provider than protecting data.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Figure 7: Privacy Enhancing Technologies
3. System Design: Architecture of the system has the basic effect on data protection.
The design of the architecture of the system supports the privacy requirement.
Architecture has become the strategy to support all principles of data protection.
(Buchanan, Kwecka & Ekonomou, 2012)
3. System Design: Architecture of the system has the basic effect on data protection.
The design of the architecture of the system supports the privacy requirement.
Architecture has become the strategy to support all principles of data protection.
(Buchanan, Kwecka & Ekonomou, 2012)
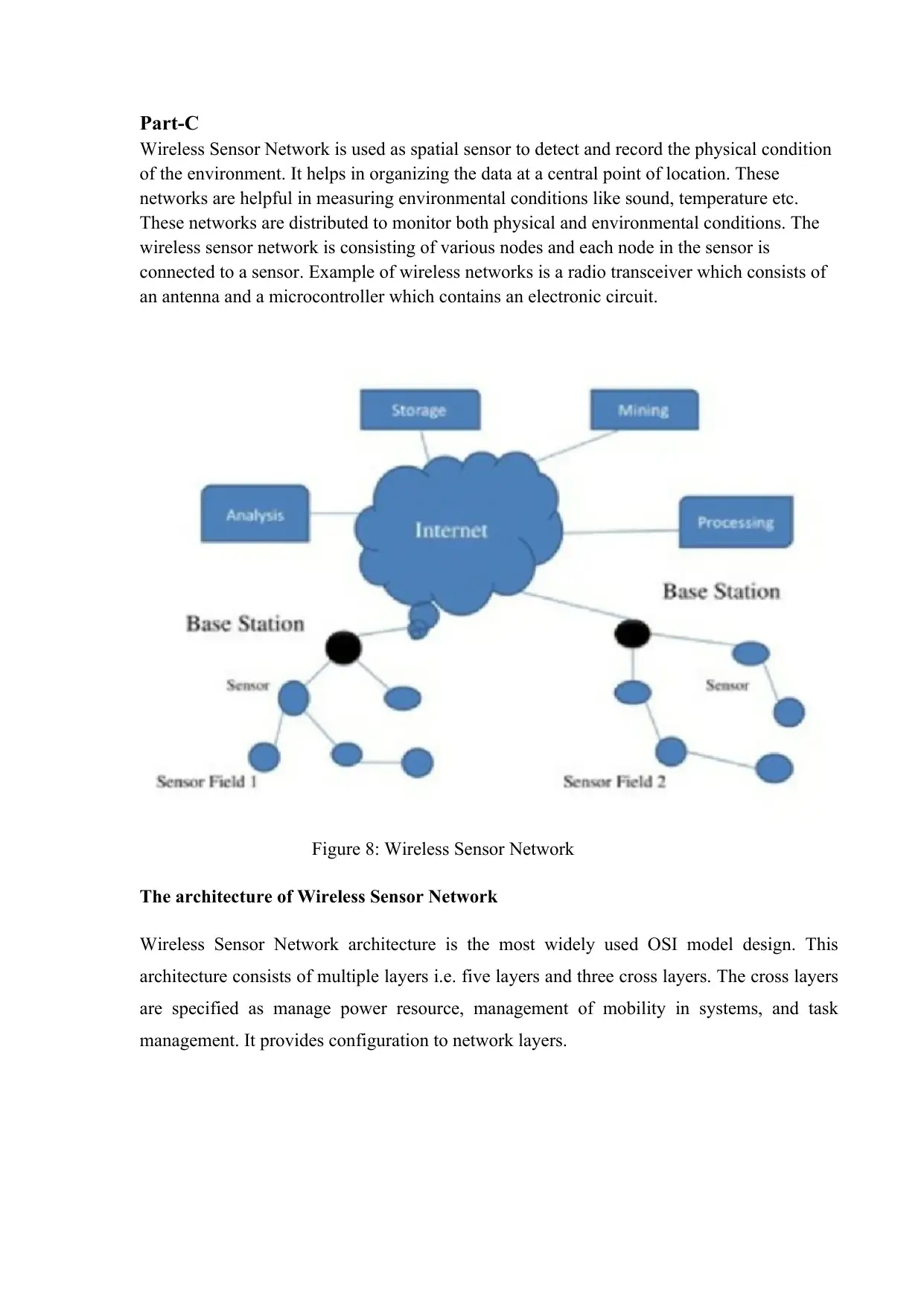
Part-C
Wireless Sensor Network is used as spatial sensor to detect and record the physical condition
of the environment. It helps in organizing the data at a central point of location. These
networks are helpful in measuring environmental conditions like sound, temperature etc.
These networks are distributed to monitor both physical and environmental conditions. The
wireless sensor network is consisting of various nodes and each node in the sensor is
connected to a sensor. Example of wireless networks is a radio transceiver which consists of
an antenna and a microcontroller which contains an electronic circuit.
Figure 8: Wireless Sensor Network
The architecture of Wireless Sensor Network
Wireless Sensor Network architecture is the most widely used OSI model design. This
architecture consists of multiple layers i.e. five layers and three cross layers. The cross layers
are specified as manage power resource, management of mobility in systems, and task
management. It provides configuration to network layers.
Wireless Sensor Network is used as spatial sensor to detect and record the physical condition
of the environment. It helps in organizing the data at a central point of location. These
networks are helpful in measuring environmental conditions like sound, temperature etc.
These networks are distributed to monitor both physical and environmental conditions. The
wireless sensor network is consisting of various nodes and each node in the sensor is
connected to a sensor. Example of wireless networks is a radio transceiver which consists of
an antenna and a microcontroller which contains an electronic circuit.
Figure 8: Wireless Sensor Network
The architecture of Wireless Sensor Network
Wireless Sensor Network architecture is the most widely used OSI model design. This
architecture consists of multiple layers i.e. five layers and three cross layers. The cross layers
are specified as manage power resource, management of mobility in systems, and task
management. It provides configuration to network layers.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 15
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





