IT Risk Management Report: Gigantic Corp. Cyber Security Analysis
VerifiedAdded on 2023/06/05
|21
|4785
|434
Report
AI Summary
This IT Risk Management report, prepared for Gigantic Corporation, provides a comprehensive analysis of cyber security threats and vulnerabilities. It begins with an executive summary outlining the company's IT infrastructure and the role of an IT risk consultant. The report details various cyber threats, including malware, ransomware, phishing, SQL injection attacks, cross-site scripting, DOS attacks, and man-in-the-middle attacks. It then explores the vulnerabilities associated with these threats and proposes an IT control framework, including policies and procedures for data protection, device security, email security, password management, and secure data transfer. The report also includes a literature review on safeguards and security mechanisms and concludes with recommendations for mitigating the identified risks. The report emphasizes the importance of proactive security measures to protect the organization's data and systems.

1. Cover page
IT Risk Management
Name of the Student:
Name of the University:
IT Risk Management
Name of the Student:
Name of the University:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1IT RISK MANAGEMENT
2. Table of contents
1. Cover page.........................................................................................................................0
2. Table of contents................................................................................................................1
3. Executive Summary...........................................................................................................3
3.1 Statement of the technology project............................................................................3
3.1.1 Outline of the company- Gigantic Corporation........................................................3
3.1.2 Role and responsibility.........................................................................................3
3.1.3 Technology used in company....................................................................................4
3.2 Overview of your recommendations................................................................................4
4.0 Risk assessment based on threats, vulnerabilities and consequences..................................4
4.1 IT control framework.......................................................................................................7
4.1.1 Policy and procedure.................................................................................................8
4.2 Key threat agents............................................................................................................10
4.2.1 List of threat agents.................................................................................................11
4.2.2 Issues.......................................................................................................................12
4.3.3 Consequences..........................................................................................................12
4.3 Mitigation of risks and their impact on the system........................................................13
5.0 Literature review................................................................................................................14
5.1 Safeguards......................................................................................................................14
5.2 Security mechanisms......................................................................................................15
2. Table of contents
1. Cover page.........................................................................................................................0
2. Table of contents................................................................................................................1
3. Executive Summary...........................................................................................................3
3.1 Statement of the technology project............................................................................3
3.1.1 Outline of the company- Gigantic Corporation........................................................3
3.1.2 Role and responsibility.........................................................................................3
3.1.3 Technology used in company....................................................................................4
3.2 Overview of your recommendations................................................................................4
4.0 Risk assessment based on threats, vulnerabilities and consequences..................................4
4.1 IT control framework.......................................................................................................7
4.1.1 Policy and procedure.................................................................................................8
4.2 Key threat agents............................................................................................................10
4.2.1 List of threat agents.................................................................................................11
4.2.2 Issues.......................................................................................................................12
4.3.3 Consequences..........................................................................................................12
4.3 Mitigation of risks and their impact on the system........................................................13
5.0 Literature review................................................................................................................14
5.1 Safeguards......................................................................................................................14
5.2 Security mechanisms......................................................................................................15

2IT RISK MANAGEMENT
5.3 Change in key principle of information by which employees can secure their
information...........................................................................................................................16
6.0 Conclusion..........................................................................................................................16
6. References........................................................................................................................18
5.3 Change in key principle of information by which employees can secure their
information...........................................................................................................................16
6.0 Conclusion..........................................................................................................................16
6. References........................................................................................................................18
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3IT RISK MANAGEMENT
3. Executive Summary
Cyber security is a type of protection system for computing devices and it is also called as
IT security. In this advanced generation, the problem of cyber-crimes is growing very fast
and many originations are facing this type of problem. Cyber security provides a platform
where consumers can protect their personal information and they can avoid the problem of
cyber-attacks. The main purpose of this report is to understand the fundamental concept of
cyber security and their potential threats or risks. This report is explaining different types of
threats and vulnerabilities of cyber security and methods to reduce this type of problems in
the gigantic corporation. It is a very serious issue for any organization because hackers can
easily encrypt user’s computer devices with the help of botnet and malware. In the field of
computer science, physical security and cyber security both are very important parts to
protect data from unauthorized access and servers. Information security is a subset of cyber
security which is developed to maintain the integrity, availability, and confidentiality of
consumer’s private data.
3.1 Statement of the technology project
3.1.1 Outline of the company- Gigantic Corporation
Gigantic Corporation is an information and technology organization which provides
telecommunication services to their consumers and it also develops many software and
hardware. This organization is facing various IT risks like security threats, data breach and
other cyber-crimes.
3.1.2 Role and responsibility
Gigantic Corporation is an information and communication organization and in which I
am IT risk lead consultant. The main role of an IT consultant in the field of a computer
3. Executive Summary
Cyber security is a type of protection system for computing devices and it is also called as
IT security. In this advanced generation, the problem of cyber-crimes is growing very fast
and many originations are facing this type of problem. Cyber security provides a platform
where consumers can protect their personal information and they can avoid the problem of
cyber-attacks. The main purpose of this report is to understand the fundamental concept of
cyber security and their potential threats or risks. This report is explaining different types of
threats and vulnerabilities of cyber security and methods to reduce this type of problems in
the gigantic corporation. It is a very serious issue for any organization because hackers can
easily encrypt user’s computer devices with the help of botnet and malware. In the field of
computer science, physical security and cyber security both are very important parts to
protect data from unauthorized access and servers. Information security is a subset of cyber
security which is developed to maintain the integrity, availability, and confidentiality of
consumer’s private data.
3.1 Statement of the technology project
3.1.1 Outline of the company- Gigantic Corporation
Gigantic Corporation is an information and technology organization which provides
telecommunication services to their consumers and it also develops many software and
hardware. This organization is facing various IT risks like security threats, data breach and
other cyber-crimes.
3.1.2 Role and responsibility
Gigantic Corporation is an information and communication organization and in which I
am IT risk lead consultant. The main role of an IT consultant in the field of a computer
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4IT RISK MANAGEMENT
network is to maintain risks and threats of any information security and improve security
systems by which users can secure their private information.
3.1.3 Technology used in company
Gigantic Corporation uses various kinds of information technologies, for example, the
Internet of thing, wireless networks, cloud computing, network protocols, and information
technologies (Chakhchoukh & Ishii, 2015). With the help of these entire technologies, the
gigantic corporation provides communication services to many companies and consumers.
3.2 Overview of your recommendations
Lack of security is the very common problem for the gigantic organization and it is
observed that many consumers use a simple password-based system and hackers can easily
block their peripheral devices by using a complex algorithm process. This report is divided
into two parts such as potential threats of cybersecurity and prevention methods to reduce IT
risk for a gigantic corporation. This organization can adopt security architecture or steps to
reduce various problems and risk such as password-based systems, use of antivirus and
firewall, control and monitor unwanted traffic signals, detect spam emails and messages by
encryption method and cryptography process.
4.0 Risk assessment based on threats, vulnerabilities and consequences
Cyber threats are defined as circumstance with the potential to cause harm and it is
very harmful to human-computer systems. There are many examples of cyber threats such as
flooding process for data systems, an administrator accidentally wiping a production process,
political activities of DDOS attacks (Cherdantseva, et al., 2016) Attackers produce various
malware and botnet by which they can enter into gigantic websites and block their authentic
servers. Vulnerabilities mean weakness in a computer system and the main drawback of the
gigantic corporation is that it does not use any security policy and strategy by which they lost
network is to maintain risks and threats of any information security and improve security
systems by which users can secure their private information.
3.1.3 Technology used in company
Gigantic Corporation uses various kinds of information technologies, for example, the
Internet of thing, wireless networks, cloud computing, network protocols, and information
technologies (Chakhchoukh & Ishii, 2015). With the help of these entire technologies, the
gigantic corporation provides communication services to many companies and consumers.
3.2 Overview of your recommendations
Lack of security is the very common problem for the gigantic organization and it is
observed that many consumers use a simple password-based system and hackers can easily
block their peripheral devices by using a complex algorithm process. This report is divided
into two parts such as potential threats of cybersecurity and prevention methods to reduce IT
risk for a gigantic corporation. This organization can adopt security architecture or steps to
reduce various problems and risk such as password-based systems, use of antivirus and
firewall, control and monitor unwanted traffic signals, detect spam emails and messages by
encryption method and cryptography process.
4.0 Risk assessment based on threats, vulnerabilities and consequences
Cyber threats are defined as circumstance with the potential to cause harm and it is
very harmful to human-computer systems. There are many examples of cyber threats such as
flooding process for data systems, an administrator accidentally wiping a production process,
political activities of DDOS attacks (Cherdantseva, et al., 2016) Attackers produce various
malware and botnet by which they can enter into gigantic websites and block their authentic
servers. Vulnerabilities mean weakness in a computer system and the main drawback of the
gigantic corporation is that it does not use any security policy and strategy by which they lost

5IT RISK MANAGEMENT
their privacy. SQL injection is the very common example of vulnerabilities and to reduce this
problem SQL certificate has been developed (Deshmukh & Devadkar, 2015). There are many
threats and risks of cyber security are detected which are describing below-
Malware
Ransom ware
Phishing
SQL injection attack
Cross-site Scripting
DOS attack
Man in the middle attacks
Malware
Malware is a complex algorithm process which is used by attackers to hack data or
information of any organization. Gigantic Corporation is facing from this problem and they
can lose their private details. It is a type of software which detects detail of authentic servers
and once malware enters into computer device then it can control and monitor
communication systems and other activities (Isozaki et al., 2016) Aggressors will utilize an
assortment of techniques to get malware into your PC, yet at some stage it regularly requires
the client to make a move to introduce the malware. This can incorporate clicking a
connection to download a record, or opening a connection that may look safe (like a Word
report or PDF connection), however really has a malware installer covered up inside.
Phishing
their privacy. SQL injection is the very common example of vulnerabilities and to reduce this
problem SQL certificate has been developed (Deshmukh & Devadkar, 2015). There are many
threats and risks of cyber security are detected which are describing below-
Malware
Ransom ware
Phishing
SQL injection attack
Cross-site Scripting
DOS attack
Man in the middle attacks
Malware
Malware is a complex algorithm process which is used by attackers to hack data or
information of any organization. Gigantic Corporation is facing from this problem and they
can lose their private details. It is a type of software which detects detail of authentic servers
and once malware enters into computer device then it can control and monitor
communication systems and other activities (Isozaki et al., 2016) Aggressors will utilize an
assortment of techniques to get malware into your PC, yet at some stage it regularly requires
the client to make a move to introduce the malware. This can incorporate clicking a
connection to download a record, or opening a connection that may look safe (like a Word
report or PDF connection), however really has a malware installer covered up inside.
Phishing
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6IT RISK MANAGEMENT
The first step of an attacker is that they collect all required information like IP
address, network protocols, type of server, and kind of security system. After that, they install
malware and other hacking processes into computer systems and encrypt complete
information of any organization. Gigantic Corporation received many spam e-mails by which
hackers enter into the authorized server and after that, they demand money to restore their
private data (Johnston, Warkentin, McBride, & Carter, 2016).
SQL injection attack
SQL is defined as a structured query language which is a part of programming
language. The main objective of SQL is to provide communication between network devices
and database systems. Gigantic Corporation uses various servers to store data and SQL is
used to manage the data or information in their database (Liu, et al., 2017). SQL injection
attack on a database of any organization with the help of various malicious source code and
attackers can monitor their peripheral devices.
Cross-Site Scripting
It is a very common type of cyber-attack in which hacker's directly targeting websites
of Gigantic Corporation and they use traffic signals and injected browser process rather than
algorithm code that provides complete information of any organization. A standout amongst
the most well-known ways an assailant can send a cross-site scripting assault is by infusing
noxious code into a remark or a content that could naturally run. For instance, they could
install a connection to a malevolent JavaScript in a remark on a blog (Kateb, Tushar, Assi, &
Debbabi, 2018).
DOS attack
DOS refer as denial of service which is the most common type of attack and it uses
flooding or botnet process to encrypt website of an organization. From last few years, the
The first step of an attacker is that they collect all required information like IP
address, network protocols, type of server, and kind of security system. After that, they install
malware and other hacking processes into computer systems and encrypt complete
information of any organization. Gigantic Corporation received many spam e-mails by which
hackers enter into the authorized server and after that, they demand money to restore their
private data (Johnston, Warkentin, McBride, & Carter, 2016).
SQL injection attack
SQL is defined as a structured query language which is a part of programming
language. The main objective of SQL is to provide communication between network devices
and database systems. Gigantic Corporation uses various servers to store data and SQL is
used to manage the data or information in their database (Liu, et al., 2017). SQL injection
attack on a database of any organization with the help of various malicious source code and
attackers can monitor their peripheral devices.
Cross-Site Scripting
It is a very common type of cyber-attack in which hacker's directly targeting websites
of Gigantic Corporation and they use traffic signals and injected browser process rather than
algorithm code that provides complete information of any organization. A standout amongst
the most well-known ways an assailant can send a cross-site scripting assault is by infusing
noxious code into a remark or a content that could naturally run. For instance, they could
install a connection to a malevolent JavaScript in a remark on a blog (Kateb, Tushar, Assi, &
Debbabi, 2018).
DOS attack
DOS refer as denial of service which is the most common type of attack and it uses
flooding or botnet process to encrypt website of an organization. From last few years, the
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7IT RISK MANAGEMENT
gigantic organization is suffering from DDOS and DOS attack and it is observed that this
occurs due to lack of security. In which hackers design flooding messages and unwanted
traffic signals and an organization do not handle more traffic due to this problem they can
lose privacy as well as personal details like login id and password and account details. n a
few occurrences, these DoS assaults are performed by numerous PCs in the meantime. This
situation of assault is known as a Distributed Denial-of-Service Attack (DDoS). This sort of
assault can be much harder to defeat because of the aggressor showing up from a wide range
of IP addresses the world over at the same time, making deciding the wellspring of the assault
significantly more troublesome for arranging overseers.
Man in middle attacks
In this type of attack, hackers detect login ID and password of an account with the
help of the injection process. In this modern technology, consumers use wireless technology
for communication purpose and attackers can easily block their servers due to which the rate
of unauthorized has increased. Active eavesdropping is a very best example of this attack and
in which hackers develop independent interconnection with the victims and transfer messages
between consumers (Memon, & Kauhaniemi, 2015).
4.1 IT control framework
There are many communication technologies are developed by which users can share
and receive data from long distance and Gigantic Company uses wireless communication
process which is very less in security. Information and communication produced various
kinds of policies and steps to reduce potential IT risks such as use proper security
programmes, adopt biometric recognition methods, remove fraud e-mails and messages, use
antivirus and firewall, and use limited login attempts (Min, Chai, & Han, 2015). Through
these steps, we can improve the privacy of Gigantic Corporation. At that time pattern
gigantic organization is suffering from DDOS and DOS attack and it is observed that this
occurs due to lack of security. In which hackers design flooding messages and unwanted
traffic signals and an organization do not handle more traffic due to this problem they can
lose privacy as well as personal details like login id and password and account details. n a
few occurrences, these DoS assaults are performed by numerous PCs in the meantime. This
situation of assault is known as a Distributed Denial-of-Service Attack (DDoS). This sort of
assault can be much harder to defeat because of the aggressor showing up from a wide range
of IP addresses the world over at the same time, making deciding the wellspring of the assault
significantly more troublesome for arranging overseers.
Man in middle attacks
In this type of attack, hackers detect login ID and password of an account with the
help of the injection process. In this modern technology, consumers use wireless technology
for communication purpose and attackers can easily block their servers due to which the rate
of unauthorized has increased. Active eavesdropping is a very best example of this attack and
in which hackers develop independent interconnection with the victims and transfer messages
between consumers (Memon, & Kauhaniemi, 2015).
4.1 IT control framework
There are many communication technologies are developed by which users can share
and receive data from long distance and Gigantic Company uses wireless communication
process which is very less in security. Information and communication produced various
kinds of policies and steps to reduce potential IT risks such as use proper security
programmes, adopt biometric recognition methods, remove fraud e-mails and messages, use
antivirus and firewall, and use limited login attempts (Min, Chai, & Han, 2015). Through
these steps, we can improve the privacy of Gigantic Corporation. At that time pattern

8IT RISK MANAGEMENT
recognition is very best process by which consumers can improve their privacy and it is
identified that hackers send spam emails to customers and produce unauthorized services.
4.1.1 Policy and procedure
Security policy is a type of process which is used to control the rate of cyber-crimes
and threats. It is a primary method by which users can improve their security and Gigantic
Corporation can adopt security steps and strategies which are described below:
Confidential data
Information is a very important key element of any organization and consumer. There
are many examples of confidential data such as data from partners, patents, formulas, and
modern technologies, and a list of consumers. This policy is developed to understand the
problem of a data breach (Ntalampiras, 2015).
Protect personal and organization devices
When an employee in an organization utilizes their peripheral devices to access gigantic
accounts then they also introduce various security risks (Abomhara & Koien, 2015). The
organization can provide a platform where employees can understand the role of security and
safe their digital devices. There are few steps can be used for the gigantic organization such
as
Use a password-based system
Use antivirus software
Adopt biometric systems
Ensure that users do not leave their computer systems unattended
Keep updating their software on a regular basis
recognition is very best process by which consumers can improve their privacy and it is
identified that hackers send spam emails to customers and produce unauthorized services.
4.1.1 Policy and procedure
Security policy is a type of process which is used to control the rate of cyber-crimes
and threats. It is a primary method by which users can improve their security and Gigantic
Corporation can adopt security steps and strategies which are described below:
Confidential data
Information is a very important key element of any organization and consumer. There
are many examples of confidential data such as data from partners, patents, formulas, and
modern technologies, and a list of consumers. This policy is developed to understand the
problem of a data breach (Ntalampiras, 2015).
Protect personal and organization devices
When an employee in an organization utilizes their peripheral devices to access gigantic
accounts then they also introduce various security risks (Abomhara & Koien, 2015). The
organization can provide a platform where employees can understand the role of security and
safe their digital devices. There are few steps can be used for the gigantic organization such
as
Use a password-based system
Use antivirus software
Adopt biometric systems
Ensure that users do not leave their computer systems unattended
Keep updating their software on a regular basis
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9IT RISK MANAGEMENT
Limited login attempts
Login organization e-mails and accounts into authentic servers.
Employees of gigantic access their personal details and accounts into their computer
devices rather than other.
Keep emails safe
Numbers of hackers attack digital devices of organization with the help of e-mails and
they send spam emails to user’s accounts. The gigantic organization can develop instruction
for employees to secure their emails and messages and a few steps can be used like-
Reduce opening attachments and avoid the use of fraud links or unauthorized servers
Be suspicious of clickbait titles
Check emails and delete spam emails and various unwanted offers
Look for inconsistencies (Abomhara & Koien, 2015).
Manage passwords properly
Hacker’s uses flooding and malware software by which they can detect login ID and
password, so users can use biometric recognition process which is more secure. Gigantic
Corporation can adopt fingerprint and iris technology which can secure consumers private
details. There are the following procedure can be used for this organization such as
Chose string passwords rather than simple
Remember the password of their device as compared to writing in a notebook or
mobile phones.
Use limited access
Limited login attempts
Login organization e-mails and accounts into authentic servers.
Employees of gigantic access their personal details and accounts into their computer
devices rather than other.
Keep emails safe
Numbers of hackers attack digital devices of organization with the help of e-mails and
they send spam emails to user’s accounts. The gigantic organization can develop instruction
for employees to secure their emails and messages and a few steps can be used like-
Reduce opening attachments and avoid the use of fraud links or unauthorized servers
Be suspicious of clickbait titles
Check emails and delete spam emails and various unwanted offers
Look for inconsistencies (Abomhara & Koien, 2015).
Manage passwords properly
Hacker’s uses flooding and malware software by which they can detect login ID and
password, so users can use biometric recognition process which is more secure. Gigantic
Corporation can adopt fingerprint and iris technology which can secure consumers private
details. There are the following procedure can be used for this organization such as
Chose string passwords rather than simple
Remember the password of their device as compared to writing in a notebook or
mobile phones.
Use limited access
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10IT RISK MANAGEMENT
Change password of personal account every two months
Exchange credentials only when absolutely necessary
Transfer data securely
Use encryption method for communication purpose
Adopt encoding and decoding method and use digital communication rather than
analog
Avoid transferring sensitive data
Use authentic Wi-Fi servers
Produce annual report on data breach and scams and analysis problem of security
(Abomhara & Koien, 2015).
Additional measures
Turn off their system when leaving their desks
Identify any unwanted signals and traffic
Change all accounts password when system us stole
Avoid accessing suspicious websites and servers
4.2 Key threat agents
It is defined as a process which is used to breach the security of any system and its
uses exploiting method. Security threats are the very common problem for every intonation
technology and it is observed that vulnerabilities can be avoided by adopting security
programmes (Osho & Onoja, 2015).
Change password of personal account every two months
Exchange credentials only when absolutely necessary
Transfer data securely
Use encryption method for communication purpose
Adopt encoding and decoding method and use digital communication rather than
analog
Avoid transferring sensitive data
Use authentic Wi-Fi servers
Produce annual report on data breach and scams and analysis problem of security
(Abomhara & Koien, 2015).
Additional measures
Turn off their system when leaving their desks
Identify any unwanted signals and traffic
Change all accounts password when system us stole
Avoid accessing suspicious websites and servers
4.2 Key threat agents
It is defined as a process which is used to breach the security of any system and its
uses exploiting method. Security threats are the very common problem for every intonation
technology and it is observed that vulnerabilities can be avoided by adopting security
programmes (Osho & Onoja, 2015).
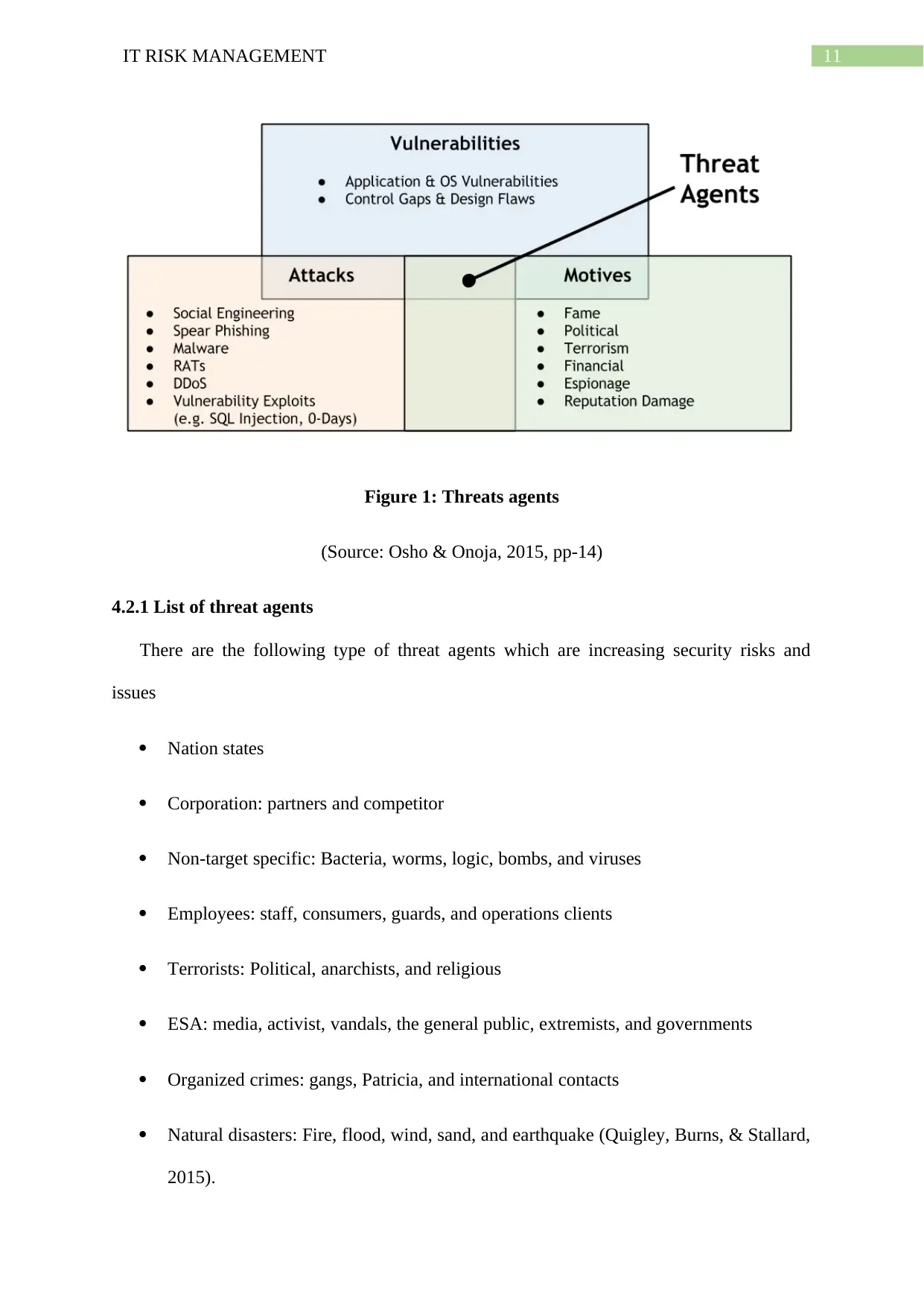
11IT RISK MANAGEMENT
Figure 1: Threats agents
(Source: Osho & Onoja, 2015, pp-14)
4.2.1 List of threat agents
There are the following type of threat agents which are increasing security risks and
issues
Nation states
Corporation: partners and competitor
Non-target specific: Bacteria, worms, logic, bombs, and viruses
Employees: staff, consumers, guards, and operations clients
Terrorists: Political, anarchists, and religious
ESA: media, activist, vandals, the general public, extremists, and governments
Organized crimes: gangs, Patricia, and international contacts
Natural disasters: Fire, flood, wind, sand, and earthquake (Quigley, Burns, & Stallard,
2015).
Figure 1: Threats agents
(Source: Osho & Onoja, 2015, pp-14)
4.2.1 List of threat agents
There are the following type of threat agents which are increasing security risks and
issues
Nation states
Corporation: partners and competitor
Non-target specific: Bacteria, worms, logic, bombs, and viruses
Employees: staff, consumers, guards, and operations clients
Terrorists: Political, anarchists, and religious
ESA: media, activist, vandals, the general public, extremists, and governments
Organized crimes: gangs, Patricia, and international contacts
Natural disasters: Fire, flood, wind, sand, and earthquake (Quigley, Burns, & Stallard,
2015).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 21
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




