Comprehensive IT Risk Management Report: ABC Fitness Gym Analysis
VerifiedAdded on 2022/10/13
|12
|3279
|407
Report
AI Summary
This report provides a comprehensive technical risk analysis for ABC Fitness Gym's IT systems. It begins with an executive summary outlining the gym's IT environment, including its infrastructure and user base. The report then delves into a detailed risk assessment, identifying key assets such as client information, sensitive gym data, and trade secrets. It analyzes potential threats like system failures, accidental human errors, and natural disasters, along with vulnerabilities like outdated software and physical security weaknesses. The consequences of these threats are evaluated, considering data loss, system downtime, and legal implications. The report uses an IT control framework to assess risks, including a table detailing assets, threats, vulnerabilities, consequences, likelihood, and risk recommendations. It also includes recommendations for mitigating risks, such as implementing robust password policies, promoting a security-conscious culture through training, and deploying virus scanners. The report identifies skill gaps and customer service gaps through surveys and benchmarking. The report concludes with a rationale for the recommendations, emphasizing the importance of protecting the gym's IT systems and its data. The report provides a clear and actionable plan for ABC Fitness Gym to improve its IT security posture. The assignment follows all guidelines provided in the assignment brief.

Running head: INFORMATION TECHNOLOGY RISK MANAGEMENT
INFORMATION TECHNOLOGY RISK MANAGEMENT
Name of the Student
Name of the University
Author Note:
INFORMATION TECHNOLOGY RISK MANAGEMENT
Name of the Student
Name of the University
Author Note:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1INFORMATION TECHNOLOGY RISK MANAGEMENT
Executive summary
The report highlights the case study of IT system in ABC gym. In the year 1997, the gym was
started. In initial days, the gym had a small space for its members and staff. Due to the increase
in number of members, the gym acquired new space for its members. The owner has around 50
full-time members and 150 part-time members. For running and maintaining the business of
ABC gym, a detail specification was required for the system. The members of gym are corporate
employee members and individual member. All the members of this gym are required to pay
annual subscription fee. Only the corporate employee get benefit that is reduced subscription
rate. ABC gym should make use of virus scanner so that they keep all the software updated.
Installation of anti-virus on the system can easily provide various capabilities for the PC. In
addition, the staff members should keep their system updated, which will prevent them from any
new virus and variation of old threat. IT system can bring huge number of benefits like
operational efficiencies, supply of information, best customer service and lastly development of
communication capabilities.
Executive summary
The report highlights the case study of IT system in ABC gym. In the year 1997, the gym was
started. In initial days, the gym had a small space for its members and staff. Due to the increase
in number of members, the gym acquired new space for its members. The owner has around 50
full-time members and 150 part-time members. For running and maintaining the business of
ABC gym, a detail specification was required for the system. The members of gym are corporate
employee members and individual member. All the members of this gym are required to pay
annual subscription fee. Only the corporate employee get benefit that is reduced subscription
rate. ABC gym should make use of virus scanner so that they keep all the software updated.
Installation of anti-virus on the system can easily provide various capabilities for the PC. In
addition, the staff members should keep their system updated, which will prevent them from any
new virus and variation of old threat. IT system can bring huge number of benefits like
operational efficiencies, supply of information, best customer service and lastly development of
communication capabilities.

2INFORMATION TECHNOLOGY RISK MANAGEMENT
Table of Contents
Introduction..........................................................................................................................3
Discussion............................................................................................................................3
Risk Assessment..................................................................................................................3
TVA based on IT control.................................................................................................3
Risk Recommendation.....................................................................................................8
Mitigating risk.................................................................................................................8
Protection mechanism..........................................................................................................9
Identification of gaps...........................................................................................................9
Conclusion.........................................................................................................................11
References..........................................................................................................................12
Table of Contents
Introduction..........................................................................................................................3
Discussion............................................................................................................................3
Risk Assessment..................................................................................................................3
TVA based on IT control.................................................................................................3
Risk Recommendation.....................................................................................................8
Mitigating risk.................................................................................................................8
Protection mechanism..........................................................................................................9
Identification of gaps...........................................................................................................9
Conclusion.........................................................................................................................11
References..........................................................................................................................12
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3INFORMATION TECHNOLOGY RISK MANAGEMENT
Introduction
The following report is all conducting technical risk analysis for ABC fitness Gym. In the
year 1997, the system was owner was named as ABC fitness Gym. In the beginning days of the
Gym, the owner has a small premise and has a capacity of around 20 members. After that owner
acquired new premises and expanded the Gym size (Schwalbe, 2015). At present, the owner can
employ around 50 full time staff members and 150 part-time employees. In addition, the owner
has increased the customer relationship so that they can provide membership to organization. For
running the business of this Gym, a detail system was used for creating IT system. The gym has
two categories of members that is corporate employee members and individual members. Each
of employee is employed by a particular department and the gym wants to know department
where the employees has worked earlier (Dutta, Geiger & Lanvin, 2015). Before joining the
gym, new members are often are asked to take complete tour for free. The equipment’s of the
Gym merely fall under two category that is weight machines and cardiovascular machines.
In the coming pages, a risk assessment has been done by using assets, vulnerabilities and
consequences that is being derived from IT control framework. An identification has been done
with respect to key threats within the organization. A list of recommendation has been provided
with respect to key threats within the organization.
Discussion
Risk Assessment
TVA based on IT control
Cybersecurity is all about proper management, understanding, control and lastly
mitigation of different kind of risks for important asset of the organization. Risk can be defined
as a new concept in business that ultimately results in likelihood of financial loss for gym that
can be high (Marchewka, 2016). There are mainly three factors which are being used in risk
determination are different threats, vulnerability of system and lastly vital asset of gym that can
be damaged. There are common methods by the gym can suffer financial loss that is
Data loss: Stealing of trade secrets of gym that can bring loss to business. Theft of
member’s detail of gym can ultimately result in trust loss and customer attrition.
Introduction
The following report is all conducting technical risk analysis for ABC fitness Gym. In the
year 1997, the system was owner was named as ABC fitness Gym. In the beginning days of the
Gym, the owner has a small premise and has a capacity of around 20 members. After that owner
acquired new premises and expanded the Gym size (Schwalbe, 2015). At present, the owner can
employ around 50 full time staff members and 150 part-time employees. In addition, the owner
has increased the customer relationship so that they can provide membership to organization. For
running the business of this Gym, a detail system was used for creating IT system. The gym has
two categories of members that is corporate employee members and individual members. Each
of employee is employed by a particular department and the gym wants to know department
where the employees has worked earlier (Dutta, Geiger & Lanvin, 2015). Before joining the
gym, new members are often are asked to take complete tour for free. The equipment’s of the
Gym merely fall under two category that is weight machines and cardiovascular machines.
In the coming pages, a risk assessment has been done by using assets, vulnerabilities and
consequences that is being derived from IT control framework. An identification has been done
with respect to key threats within the organization. A list of recommendation has been provided
with respect to key threats within the organization.
Discussion
Risk Assessment
TVA based on IT control
Cybersecurity is all about proper management, understanding, control and lastly
mitigation of different kind of risks for important asset of the organization. Risk can be defined
as a new concept in business that ultimately results in likelihood of financial loss for gym that
can be high (Marchewka, 2016). There are mainly three factors which are being used in risk
determination are different threats, vulnerability of system and lastly vital asset of gym that can
be damaged. There are common methods by the gym can suffer financial loss that is
Data loss: Stealing of trade secrets of gym that can bring loss to business. Theft of
member’s detail of gym can ultimately result in trust loss and customer attrition.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4INFORMATION TECHNOLOGY RISK MANAGEMENT
Downtime of either system or application: If anyhow a system fail to carry out some of
the basic function, then gym members will get the required service (Baller, Dutta & Lanvin,
2016). In addition, the working staff of staff of gym will not be able to communicate.
Legal aspect: If an individual steal data from member database even if the stolen
information is not important, then it can incur fines and legal cost on gym (Trantopoulos et al.,
2017). The fine is imposed due to the fact that gym has failed to comply with some data
protection requirements like PCI DSS.
Identification and prioritise Assets
Some of the critical asset is merely inclusive of client information, sensitive information
of gym, trade secrets. There is a list of critical asset of the Gym like
Hardware
Data
Interface
Support for personnel
Critical aspect
Functional requirements
IT Security policies of Gym
Protection of stored information
Security control
Identifying threats
Threat can be anything can bring a huge amount of exploiting to the security breach and
can even harm the organization. There are list of threat for IT system of ABC gym like
System Failure: The overall likelihood of system failure merely depends on the system
quality. For some of the new and high-quality equipment, the overall chances of failure of
system are found to low (Wu, Straub & Liang, 2015). But if the gym makes use of equipment
no-name vendor, then there are more chances of system failure. So, it is advised to buy always
high quality equipment or equipment that provide good support.
Accidental human interface: This particular threat is very much high for any business
organization like ABC gym. A staff member of the gym can mistakenly delete files, click on
malware links or even can accidentally damage equipment pieces (Jiao & Onwuegbuzie, 2017).
Downtime of either system or application: If anyhow a system fail to carry out some of
the basic function, then gym members will get the required service (Baller, Dutta & Lanvin,
2016). In addition, the working staff of staff of gym will not be able to communicate.
Legal aspect: If an individual steal data from member database even if the stolen
information is not important, then it can incur fines and legal cost on gym (Trantopoulos et al.,
2017). The fine is imposed due to the fact that gym has failed to comply with some data
protection requirements like PCI DSS.
Identification and prioritise Assets
Some of the critical asset is merely inclusive of client information, sensitive information
of gym, trade secrets. There is a list of critical asset of the Gym like
Hardware
Data
Interface
Support for personnel
Critical aspect
Functional requirements
IT Security policies of Gym
Protection of stored information
Security control
Identifying threats
Threat can be anything can bring a huge amount of exploiting to the security breach and
can even harm the organization. There are list of threat for IT system of ABC gym like
System Failure: The overall likelihood of system failure merely depends on the system
quality. For some of the new and high-quality equipment, the overall chances of failure of
system are found to low (Wu, Straub & Liang, 2015). But if the gym makes use of equipment
no-name vendor, then there are more chances of system failure. So, it is advised to buy always
high quality equipment or equipment that provide good support.
Accidental human interface: This particular threat is very much high for any business
organization like ABC gym. A staff member of the gym can mistakenly delete files, click on
malware links or even can accidentally damage equipment pieces (Jiao & Onwuegbuzie, 2017).

5INFORMATION TECHNOLOGY RISK MANAGEMENT
It is advised to gym to back up their data on regular basis so that they can keep a track of all the
required changes.
Natural disaster: Some of the natural disaster like flood, earthquakes, fire and natural
disaster can bring much more damage in comparison to hacker. In this, the individual will not
lose data, server and associated appliances (Saunders & Brynjolfsson, 2016). At the time of
deciding the server room, the gym owner should take into consideration the location of server
room.
Identification of Vulnerabilities
Vulnerability can be defined as any kind of weakness which the threat can exploit for
security breach. It can even harm the overall reputation of gym. Vulnerability can be identified
by using vulnerability analysis, vendor data, incident response team, analysis of software
security and lastly audit reports. Proper testing of IT system of Gym can be helpful in identifying
some of the key vulnerabilities (Benitez, Ray & Henseler, 2018). The testing is merely inclusive
of information security test and procedure of evaluation, techniques based on penetration testing
and lastly automated vulnerability scanning tools. The staff members of gym can easily reduce
software based vulnerabilities by using proper patch management. Staff members of ABC gym
should consider all the physical vulnerabilities (Luftman, Lyytinen & Zvi, 2017). The server
room of the gym should move to the second floor of building so that it can reduce the
vulnerability of flooding to large extent.
Analysing Consequences
The analysis of the impact of threat are
Mission of system which is all about process included by system
System criticality which is due to the value of data to organization.
Sensitivity of both data and system.
The required information for conducting impact analysis can be easily retrieved the
current
Organization documents. It is merely inclusive of business impact analysis. The given document
can either make use of qualitative and quantitative asset of the organization (Naser & Zaqout,
2016). An attack can have even result in overall loss of data or confidentiality of information
system. It will merely harm the vital asset of the gym. An attack on the information system of
It is advised to gym to back up their data on regular basis so that they can keep a track of all the
required changes.
Natural disaster: Some of the natural disaster like flood, earthquakes, fire and natural
disaster can bring much more damage in comparison to hacker. In this, the individual will not
lose data, server and associated appliances (Saunders & Brynjolfsson, 2016). At the time of
deciding the server room, the gym owner should take into consideration the location of server
room.
Identification of Vulnerabilities
Vulnerability can be defined as any kind of weakness which the threat can exploit for
security breach. It can even harm the overall reputation of gym. Vulnerability can be identified
by using vulnerability analysis, vendor data, incident response team, analysis of software
security and lastly audit reports. Proper testing of IT system of Gym can be helpful in identifying
some of the key vulnerabilities (Benitez, Ray & Henseler, 2018). The testing is merely inclusive
of information security test and procedure of evaluation, techniques based on penetration testing
and lastly automated vulnerability scanning tools. The staff members of gym can easily reduce
software based vulnerabilities by using proper patch management. Staff members of ABC gym
should consider all the physical vulnerabilities (Luftman, Lyytinen & Zvi, 2017). The server
room of the gym should move to the second floor of building so that it can reduce the
vulnerability of flooding to large extent.
Analysing Consequences
The analysis of the impact of threat are
Mission of system which is all about process included by system
System criticality which is due to the value of data to organization.
Sensitivity of both data and system.
The required information for conducting impact analysis can be easily retrieved the
current
Organization documents. It is merely inclusive of business impact analysis. The given document
can either make use of qualitative and quantitative asset of the organization (Naser & Zaqout,
2016). An attack can have even result in overall loss of data or confidentiality of information
system. It will merely harm the vital asset of the gym. An attack on the information system of
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
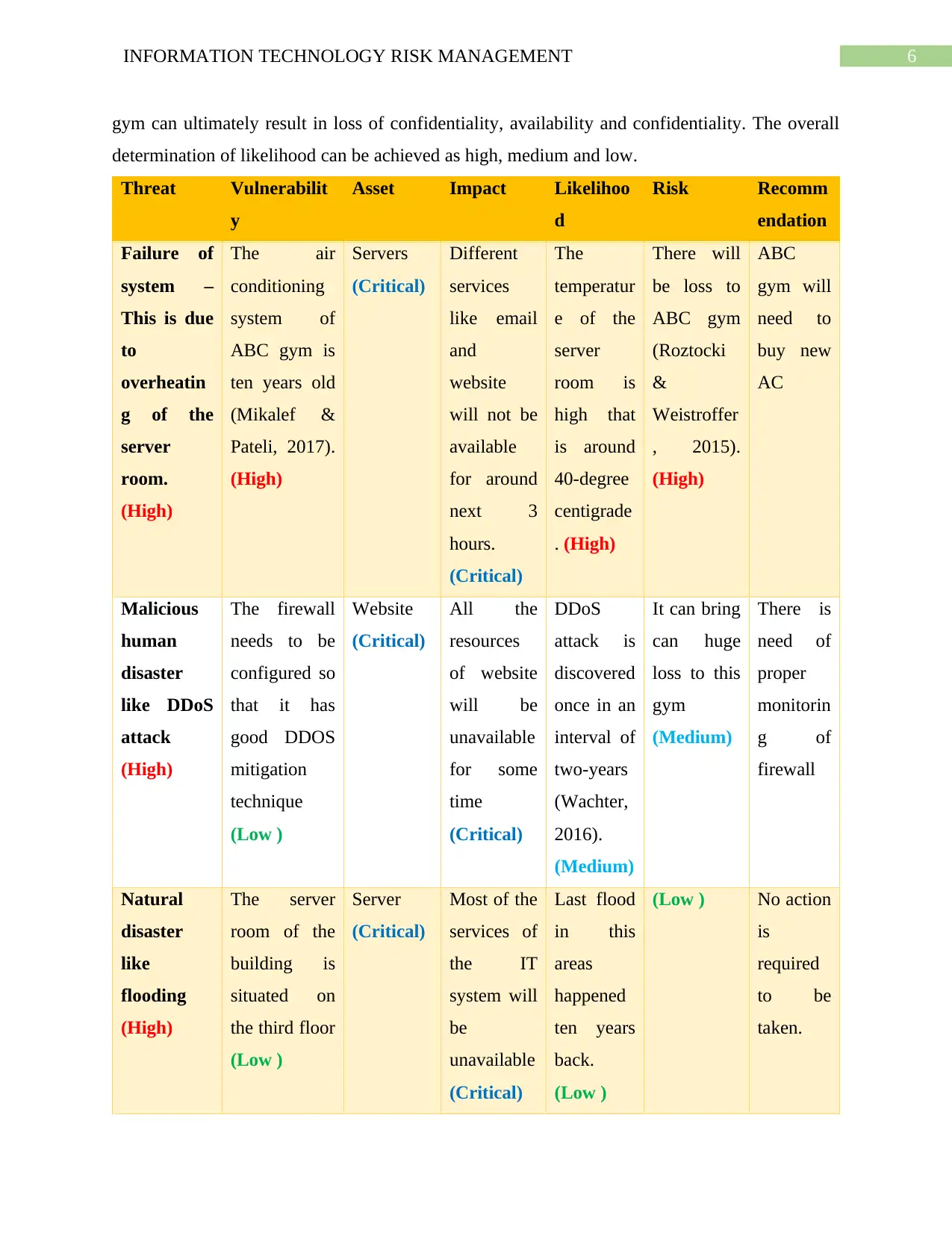
6INFORMATION TECHNOLOGY RISK MANAGEMENT
gym can ultimately result in loss of confidentiality, availability and confidentiality. The overall
determination of likelihood can be achieved as high, medium and low.
Threat Vulnerabilit
y
Asset Impact Likelihoo
d
Risk Recomm
endation
Failure of
system –
This is due
to
overheatin
g of the
server
room.
(High)
The air
conditioning
system of
ABC gym is
ten years old
(Mikalef &
Pateli, 2017).
(High)
Servers
(Critical)
Different
services
like email
and
website
will not be
available
for around
next 3
hours.
(Critical)
The
temperatur
e of the
server
room is
high that
is around
40-degree
centigrade
. (High)
There will
be loss to
ABC gym
(Roztocki
&
Weistroffer
, 2015).
(High)
ABC
gym will
need to
buy new
AC
Malicious
human
disaster
like DDoS
attack
(High)
The firewall
needs to be
configured so
that it has
good DDOS
mitigation
technique
(Low )
Website
(Critical)
All the
resources
of website
will be
unavailable
for some
time
(Critical)
DDoS
attack is
discovered
once in an
interval of
two-years
(Wachter,
2016).
(Medium)
It can bring
can huge
loss to this
gym
(Medium)
There is
need of
proper
monitorin
g of
firewall
Natural
disaster
like
flooding
(High)
The server
room of the
building is
situated on
the third floor
(Low )
Server
(Critical)
Most of the
services of
the IT
system will
be
unavailable
(Critical)
Last flood
in this
areas
happened
ten years
back.
(Low )
(Low ) No action
is
required
to be
taken.
gym can ultimately result in loss of confidentiality, availability and confidentiality. The overall
determination of likelihood can be achieved as high, medium and low.
Threat Vulnerabilit
y
Asset Impact Likelihoo
d
Risk Recomm
endation
Failure of
system –
This is due
to
overheatin
g of the
server
room.
(High)
The air
conditioning
system of
ABC gym is
ten years old
(Mikalef &
Pateli, 2017).
(High)
Servers
(Critical)
Different
services
like email
and
website
will not be
available
for around
next 3
hours.
(Critical)
The
temperatur
e of the
server
room is
high that
is around
40-degree
centigrade
. (High)
There will
be loss to
ABC gym
(Roztocki
&
Weistroffer
, 2015).
(High)
ABC
gym will
need to
buy new
AC
Malicious
human
disaster
like DDoS
attack
(High)
The firewall
needs to be
configured so
that it has
good DDOS
mitigation
technique
(Low )
Website
(Critical)
All the
resources
of website
will be
unavailable
for some
time
(Critical)
DDoS
attack is
discovered
once in an
interval of
two-years
(Wachter,
2016).
(Medium)
It can bring
can huge
loss to this
gym
(Medium)
There is
need of
proper
monitorin
g of
firewall
Natural
disaster
like
flooding
(High)
The server
room of the
building is
situated on
the third floor
(Low )
Server
(Critical)
Most of the
services of
the IT
system will
be
unavailable
(Critical)
Last flood
in this
areas
happened
ten years
back.
(Low )
(Low ) No action
is
required
to be
taken.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
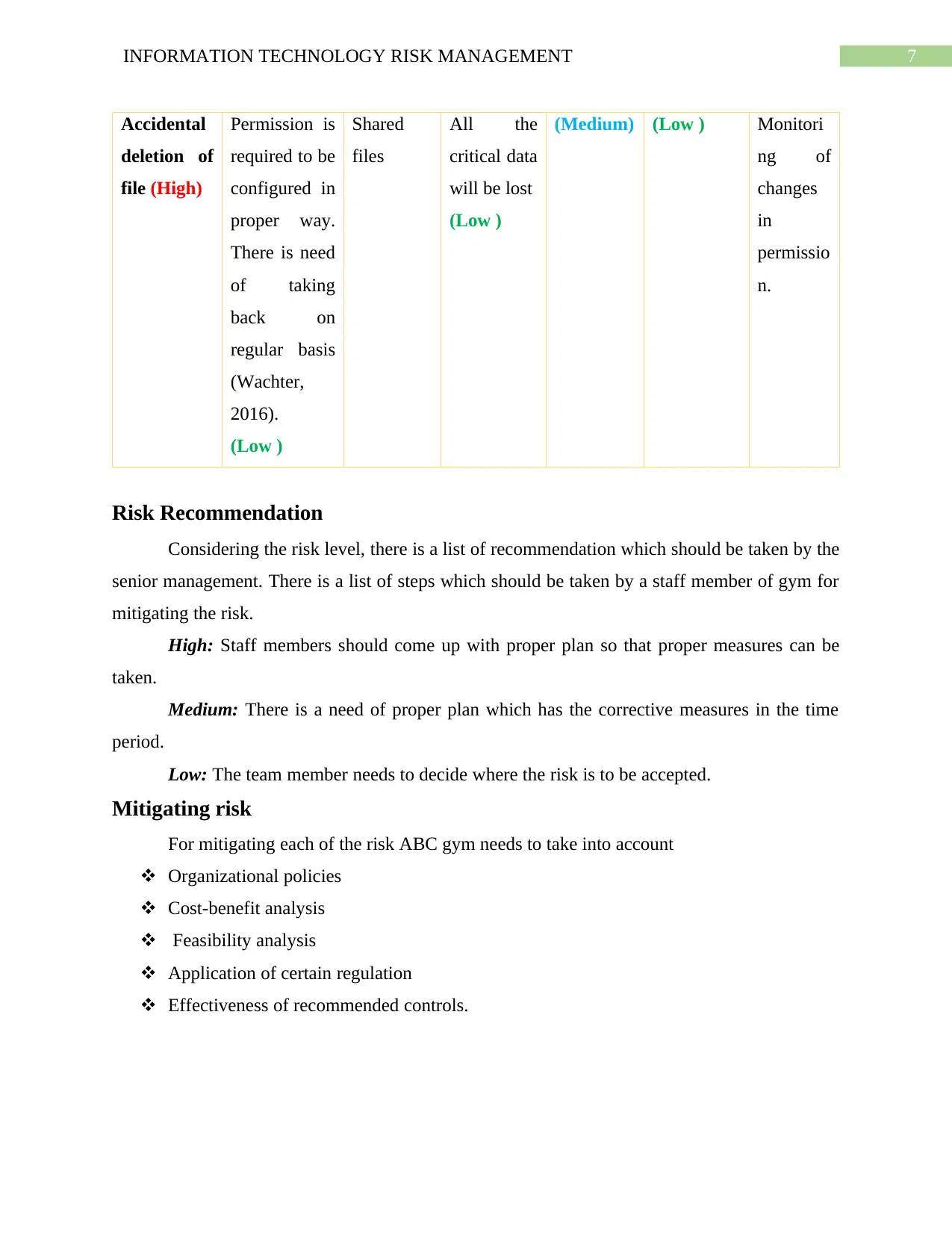
7INFORMATION TECHNOLOGY RISK MANAGEMENT
Accidental
deletion of
file (High)
Permission is
required to be
configured in
proper way.
There is need
of taking
back on
regular basis
(Wachter,
2016).
(Low )
Shared
files
All the
critical data
will be lost
(Low )
(Medium) (Low ) Monitori
ng of
changes
in
permissio
n.
Risk Recommendation
Considering the risk level, there is a list of recommendation which should be taken by the
senior management. There is a list of steps which should be taken by a staff member of gym for
mitigating the risk.
High: Staff members should come up with proper plan so that proper measures can be
taken.
Medium: There is a need of proper plan which has the corrective measures in the time
period.
Low: The team member needs to decide where the risk is to be accepted.
Mitigating risk
For mitigating each of the risk ABC gym needs to take into account
Organizational policies
Cost-benefit analysis
Feasibility analysis
Application of certain regulation
Effectiveness of recommended controls.
Accidental
deletion of
file (High)
Permission is
required to be
configured in
proper way.
There is need
of taking
back on
regular basis
(Wachter,
2016).
(Low )
Shared
files
All the
critical data
will be lost
(Low )
(Medium) (Low ) Monitori
ng of
changes
in
permissio
n.
Risk Recommendation
Considering the risk level, there is a list of recommendation which should be taken by the
senior management. There is a list of steps which should be taken by a staff member of gym for
mitigating the risk.
High: Staff members should come up with proper plan so that proper measures can be
taken.
Medium: There is a need of proper plan which has the corrective measures in the time
period.
Low: The team member needs to decide where the risk is to be accepted.
Mitigating risk
For mitigating each of the risk ABC gym needs to take into account
Organizational policies
Cost-benefit analysis
Feasibility analysis
Application of certain regulation
Effectiveness of recommended controls.

8INFORMATION TECHNOLOGY RISK MANAGEMENT
Protection mechanism
People: It is the duty of ABC staff members to keep the password of the IT system
strong. Most of the security breach around the globe just take place as a result of weak password
(Zhilenkov & Chernyi, 2015). All the wireless network and data should be guarded by using
strong user name and password. Each of the staff member of the ABC should have unique
password for accessing either device or network.
Culture: Security breaches can easily take place in ABC gym as a result of human error.
The gym should focus on building a security culture that focus system security by using training
programs. It will merely warn the overall risk of password practices, bad use of network, devices
and programs (Brooks, Pomerantz & Pomerantz, 2017). All the required security measures needs
to be taken from the perspective of document disposal for handling lost password.
Technology: ABC system should make use of virus scanner and keep the software
updated. Staff members should install proper antivirus for keeping their data safe. All the
software in the system should be keep system updated which is all about security updates (Stein
et al., 2015). This particular step will help in guarding the system from any anti-virus.
Identification of gaps
Gaps analysis can be defined as the process by which business and organization can find
different ways for overall performance improvement (Mikalef & Pateli, 2017). A list of steps can
be used for conducting gap analysis of IT system of ABC Gym.
Skill gap: Proper analysis of organization performance can easily highlight the skill gap
of employees. This particular gym can make use of benchmarking for comparing its performance
with similar gym.
Customer service Gap: Survey can be used for analysing any kind of IT system fault of
the gym. ABC gym can conduct survey for different stakeholders like employee, investor and
customer.
Gap analysis is the best method as the gym can obtain huge number of benefits. One of
the biggest plus point of this is all about measuring the overall online progress. Gap analysis
helps in establishing a proper baseline which highlights the method about how it can be
improved (Roztocki & Weistroffer, 2015). It will help in analysing what the business do for
Protection mechanism
People: It is the duty of ABC staff members to keep the password of the IT system
strong. Most of the security breach around the globe just take place as a result of weak password
(Zhilenkov & Chernyi, 2015). All the wireless network and data should be guarded by using
strong user name and password. Each of the staff member of the ABC should have unique
password for accessing either device or network.
Culture: Security breaches can easily take place in ABC gym as a result of human error.
The gym should focus on building a security culture that focus system security by using training
programs. It will merely warn the overall risk of password practices, bad use of network, devices
and programs (Brooks, Pomerantz & Pomerantz, 2017). All the required security measures needs
to be taken from the perspective of document disposal for handling lost password.
Technology: ABC system should make use of virus scanner and keep the software
updated. Staff members should install proper antivirus for keeping their data safe. All the
software in the system should be keep system updated which is all about security updates (Stein
et al., 2015). This particular step will help in guarding the system from any anti-virus.
Identification of gaps
Gaps analysis can be defined as the process by which business and organization can find
different ways for overall performance improvement (Mikalef & Pateli, 2017). A list of steps can
be used for conducting gap analysis of IT system of ABC Gym.
Skill gap: Proper analysis of organization performance can easily highlight the skill gap
of employees. This particular gym can make use of benchmarking for comparing its performance
with similar gym.
Customer service Gap: Survey can be used for analysing any kind of IT system fault of
the gym. ABC gym can conduct survey for different stakeholders like employee, investor and
customer.
Gap analysis is the best method as the gym can obtain huge number of benefits. One of
the biggest plus point of this is all about measuring the overall online progress. Gap analysis
helps in establishing a proper baseline which highlights the method about how it can be
improved (Roztocki & Weistroffer, 2015). It will help in analysing what the business do for
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9INFORMATION TECHNOLOGY RISK MANAGEMENT
extracting extra resources. It is important for ABC gym is all about developing gap analysis and
IT strategy.
Conclusion
From the above pages it can be concluded that this report is all about technical risk
analysis of ABC fitness Gym. The Gym was started by the owner in the year 1997. The owner of
this Gym has enhanced the membership capacity and can offer membership deals for the
organization. For running and maintaining the business of ABC, a list of details are required for
the system specification. The equipment of this Gym merely fall under two categories that are
weight machine, cardiovascular machines. Gym aims to enhance its service by making use of IT
system for different customer. The system will provide membership renewal in timely way along
with increased retention of members. In addition, it has the ability to process new members detail
in sequential way. Gym aims to ensure that all the health and safety needs are met at the time of
hiring new members. The information system has been designed in such a way that all the details
of the client is maintained for private and confidentiality. Updated hardware and software are
being used for maintaining network, machine, database, web server and operating system. Gym
needs to have time to time interval for back up of important data. Both system and work station
are required to be safe and secure to use. In the above pages of report, risk assessment has been
done for the information system like threats, key assets, vulnerabilities and consequence of IT
based control. After that a protection mechanism has been employed with people, culture and
technology. The last section of the report deals with identification of gaps in gym.
extracting extra resources. It is important for ABC gym is all about developing gap analysis and
IT strategy.
Conclusion
From the above pages it can be concluded that this report is all about technical risk
analysis of ABC fitness Gym. The Gym was started by the owner in the year 1997. The owner of
this Gym has enhanced the membership capacity and can offer membership deals for the
organization. For running and maintaining the business of ABC, a list of details are required for
the system specification. The equipment of this Gym merely fall under two categories that are
weight machine, cardiovascular machines. Gym aims to enhance its service by making use of IT
system for different customer. The system will provide membership renewal in timely way along
with increased retention of members. In addition, it has the ability to process new members detail
in sequential way. Gym aims to ensure that all the health and safety needs are met at the time of
hiring new members. The information system has been designed in such a way that all the details
of the client is maintained for private and confidentiality. Updated hardware and software are
being used for maintaining network, machine, database, web server and operating system. Gym
needs to have time to time interval for back up of important data. Both system and work station
are required to be safe and secure to use. In the above pages of report, risk assessment has been
done for the information system like threats, key assets, vulnerabilities and consequence of IT
based control. After that a protection mechanism has been employed with people, culture and
technology. The last section of the report deals with identification of gaps in gym.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10INFORMATION TECHNOLOGY RISK MANAGEMENT
References
Baller, S., Dutta, S., & Lanvin, B. (2016). Global information technology report 2016. Geneva:
Ouranos.
Benitez, J., Ray, G., & Henseler, J. (2018). Impact of information technology infrastructure
flexibility on mergers and acquisitions. MIS Quarterly, 42(1).
Brooks, D. C., Pomerantz, J., & Pomerantz, J. (2017). ECAR study of undergraduate students
and information technology (Vol. 4, No. 3, p. 3). 2017.
Dutta, S., Geiger, T., & Lanvin, B. (2015). The global information technology report 2015.
In World Economic Forum (Vol. 1, No. 1, pp. P80-85).
Jiao, Q. G., & Onwuegbuzie, A. J. (2017). The impact of information technology on library
anxiety: The role of computer attitudes. Information technology and libraries, 23(4), 138-
144.
Luftman, J., Lyytinen, K., & Zvi, T. B. (2017). Enhancing the measurement of information
technology (IT) business alignment and its influence on company performance. Journal
of Information Technology, 32(1), 26-46.
Marchewka, J. T. (2016). Information technology project management: Providing measurable
organizational value. John Wiley & Sons.
Mikalef, P., & Pateli, A. (2017). Information technology-enabled dynamic capabilities and their
indirect effect on competitive performance: Findings from PLS-SEM and
fsQCA. Journal of Business Research, 70, 1-16.
Naser, S. S. A., & Zaqout, I. S. (2016). Knowledge-based systems that determine the appropriate
students major: In the faculty of engineering and information technology.
Roztocki, N., & Weistroffer, H. R. (2015). Information and communication technology in
transition economies: An assessment of research trends. Information Technology for
Development, 21(3), 330-364.
Sanchez, J. M. (2018). The information technology revolution and the unsecured credit
market. Economic Inquiry, 56(2), 914-930.
Saunders, A., & Brynjolfsson, E. (2016). Valuing Information Technology Related Intangible
Assets. Mis Quarterly, 40(1).
Schwalbe, K. (2015). Information technology project management. Cengage Learning.
References
Baller, S., Dutta, S., & Lanvin, B. (2016). Global information technology report 2016. Geneva:
Ouranos.
Benitez, J., Ray, G., & Henseler, J. (2018). Impact of information technology infrastructure
flexibility on mergers and acquisitions. MIS Quarterly, 42(1).
Brooks, D. C., Pomerantz, J., & Pomerantz, J. (2017). ECAR study of undergraduate students
and information technology (Vol. 4, No. 3, p. 3). 2017.
Dutta, S., Geiger, T., & Lanvin, B. (2015). The global information technology report 2015.
In World Economic Forum (Vol. 1, No. 1, pp. P80-85).
Jiao, Q. G., & Onwuegbuzie, A. J. (2017). The impact of information technology on library
anxiety: The role of computer attitudes. Information technology and libraries, 23(4), 138-
144.
Luftman, J., Lyytinen, K., & Zvi, T. B. (2017). Enhancing the measurement of information
technology (IT) business alignment and its influence on company performance. Journal
of Information Technology, 32(1), 26-46.
Marchewka, J. T. (2016). Information technology project management: Providing measurable
organizational value. John Wiley & Sons.
Mikalef, P., & Pateli, A. (2017). Information technology-enabled dynamic capabilities and their
indirect effect on competitive performance: Findings from PLS-SEM and
fsQCA. Journal of Business Research, 70, 1-16.
Naser, S. S. A., & Zaqout, I. S. (2016). Knowledge-based systems that determine the appropriate
students major: In the faculty of engineering and information technology.
Roztocki, N., & Weistroffer, H. R. (2015). Information and communication technology in
transition economies: An assessment of research trends. Information Technology for
Development, 21(3), 330-364.
Sanchez, J. M. (2018). The information technology revolution and the unsecured credit
market. Economic Inquiry, 56(2), 914-930.
Saunders, A., & Brynjolfsson, E. (2016). Valuing Information Technology Related Intangible
Assets. Mis Quarterly, 40(1).
Schwalbe, K. (2015). Information technology project management. Cengage Learning.

11INFORMATION TECHNOLOGY RISK MANAGEMENT
Stein, M. K., Newell, S., Wagner, E. L., & Galliers, R. D. (2015). Coping with Information
Technology: Mixed Emotions, Vacillation, and Nonconforming Use Patterns. Mis
Quarterly, 39(2), 367-392.
Trantopoulos, K., von Krogh, G., Wallin, M. W., & Woerter, M. (2017). External knowledge and
information technology: Implications for process innovation performance. MIS
quarterly, 41(1), 287-300.
Wachter, R. (2016). Making IT work: harnessing the power of health information technology to
improve care in England. London, UK: Department of Health.
Wu, S. P. J., Straub, D. W., & Liang, T. P. (2015). How information technology governance
mechanisms and strategic alignment influence organizational performance: Insights from
a matched survey of business and IT managers. Mis Quarterly, 39(2), 497-518.
Zhilenkov, A., & Chernyi, S. (2015). Investigation performance of marine equipment with
specialized information technology. Procedia Engineering, 100, 1247-1252.
Stein, M. K., Newell, S., Wagner, E. L., & Galliers, R. D. (2015). Coping with Information
Technology: Mixed Emotions, Vacillation, and Nonconforming Use Patterns. Mis
Quarterly, 39(2), 367-392.
Trantopoulos, K., von Krogh, G., Wallin, M. W., & Woerter, M. (2017). External knowledge and
information technology: Implications for process innovation performance. MIS
quarterly, 41(1), 287-300.
Wachter, R. (2016). Making IT work: harnessing the power of health information technology to
improve care in England. London, UK: Department of Health.
Wu, S. P. J., Straub, D. W., & Liang, T. P. (2015). How information technology governance
mechanisms and strategic alignment influence organizational performance: Insights from
a matched survey of business and IT managers. Mis Quarterly, 39(2), 497-518.
Zhilenkov, A., & Chernyi, S. (2015). Investigation performance of marine equipment with
specialized information technology. Procedia Engineering, 100, 1247-1252.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 12
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.


