IT Risk Management: Analysis of Outsourcing Risks for Aztec Pvt. Ltd.
VerifiedAdded on 2020/04/07
|20
|4975
|430
Report
AI Summary
This report provides a comprehensive analysis of IT risk management strategies for the Aztec organization, specifically focusing on the outsourcing of its operational processes. It begins with an executive summary outlining the scope and objectives, which include designing qualitative and quantitative research methodologies to assess the risks and security issues associated with outsourcing to a third-party network. The report delves into the vision of the Aztec organization, the rationale behind outsourcing IT functionalities, and the adoption process. It outlines various research methodologies, including questionnaires, sampling techniques, data collection from multiple sources, interviews, and surveys, to gather relevant data. The report also reviews the impact of outsourcing on the financial sector and the traditional security system, emphasizing the importance of data security and risk assessment. A risk assessment matrix is developed and explained, along with a risk mitigation plan and recommendations. The conclusion summarizes the key findings and recommendations, highlighting the benefits of outsourcing, such as increased turnover and improved employee skills, while also addressing the need for robust security measures to protect sensitive data and ensure the integrity of business processes. The report emphasizes the amalgamation of international security standards and the establishment of a new security architecture to safeguard data confidentiality and accuracy during transmission.

IT Risk Management
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Executive summary:
The purpose of this paper is to design a qualitative and quantitative research methodologies
for analysing the risks and security issues associated with the outsourcing of the Aztec
organization operational processes to the network of the third party. The activities which are
outsourced by the Aztec organization to the third party are integration of the system
development, maintenance of the data network, deployment of the data centre with the use of
mainframe, repairing and maintenance program for the application, and many others. The
reputation of the company can be improved with the increasing turnover of the company. The
skills of the working employees can be sharpen according to the requirement of the global
market to remain in front of the competitors. The changes required in the traditional security
system involve the amalgamation of international standard of security policies and
procedures. It helps in establishing new security architecture for the Aztec organization to
outsource their business data and processes by maintaining the confidentiality, accuracy, and
integrity of data in the transmission process. It is recommended that the outsourcing of the
business process to the third party for the management of data application is beneficial for the
Aztec enterprise. The outsourcing helps in increasing the turnover of the enterprise from 30%
to 45% with the involvement of third party to resolve the business issues and risks associated
with the completion of activities.
The purpose of this paper is to design a qualitative and quantitative research methodologies
for analysing the risks and security issues associated with the outsourcing of the Aztec
organization operational processes to the network of the third party. The activities which are
outsourced by the Aztec organization to the third party are integration of the system
development, maintenance of the data network, deployment of the data centre with the use of
mainframe, repairing and maintenance program for the application, and many others. The
reputation of the company can be improved with the increasing turnover of the company. The
skills of the working employees can be sharpen according to the requirement of the global
market to remain in front of the competitors. The changes required in the traditional security
system involve the amalgamation of international standard of security policies and
procedures. It helps in establishing new security architecture for the Aztec organization to
outsource their business data and processes by maintaining the confidentiality, accuracy, and
integrity of data in the transmission process. It is recommended that the outsourcing of the
business process to the third party for the management of data application is beneficial for the
Aztec enterprise. The outsourcing helps in increasing the turnover of the enterprise from 30%
to 45% with the involvement of third party to resolve the business issues and risks associated
with the completion of activities.

Contents
Executive summary:...................................................................................................................1
1. Vision..................................................................................................................................4
2. Outsourcing of the IT functionality....................................................................................4
3. Adoption of Outsourcing of business activities:.................................................................6
4. Research methodologies:....................................................................................................7
5. Review of outsourcing of functionality in relation with financial sector...........................8
6. Impact of outsourcing of the functionality on the traditional security system...................9
7. Data security risks and Data flow:....................................................................................10
8. Risk assessment matrix.....................................................................................................11
9. Explanation.......................................................................................................................15
10. Risks Mitigation plan:...................................................................................................16
11. Recommendation...........................................................................................................17
12. Conclusion:...................................................................................................................17
13. References:....................................................................................................................18
Executive summary:...................................................................................................................1
1. Vision..................................................................................................................................4
2. Outsourcing of the IT functionality....................................................................................4
3. Adoption of Outsourcing of business activities:.................................................................6
4. Research methodologies:....................................................................................................7
5. Review of outsourcing of functionality in relation with financial sector...........................8
6. Impact of outsourcing of the functionality on the traditional security system...................9
7. Data security risks and Data flow:....................................................................................10
8. Risk assessment matrix.....................................................................................................11
9. Explanation.......................................................................................................................15
10. Risks Mitigation plan:...................................................................................................16
11. Recommendation...........................................................................................................17
12. Conclusion:...................................................................................................................17
13. References:....................................................................................................................18
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1. Vision
The Aztec Pvt. Ltd. wants to transform their traditional working system with the upgraded
business tactics. The owner of the company decided to outsource their business processes and
functionality to the network used by the third party for the management of the data
application. After the outsourcing of business operation, it has been analysed that there are IT
risks associated with the process of outsourcing. The company is looking forward for the plan
to develop a risks assessment matrix which helps in developing proactive action plan to
overcome the risks associated with the outsourcing of the processes. The coordination of the
functionality should be analysed and taken into consideration to develop the risks assessment
plan. The purpose of this paper is to design a qualitative and quantitative research
methodologies for analysing the risks and security issues associated with the outsourcing of
the organization operational processes to the network of the third party. The focus should also
be given on reviewing the impact of outsourcing on the financial sector and the traditional
security architecture with the development of the risks assessment management plan.
2. Outsourcing of the IT functionality
Outsourcing is the process which helps in enhancing the strategic decision taken for
facilitating the cost associated with the development program of knowledge domain to access
the organization goal within minimum period of time and cost. The outsourcing of the
activities is the tactical decision to enhance the resource management program of the
enterprise (Shacklett, 2012). The business activities which are outsourced on the network of
the third party are categorised as operation related with the deployment of the helpdesk
portfolio, data centre management schemes, and management of the application related to
control the business activities and processes. The outsourcing of the activities helps in
establishing continuous deployment of procurement process from the third party. The
communication between the stakeholders should be effectively managed to formulate the
requirement of establishing outsourcing program within the working curriculum of the Aztec
enterprise. The integration of processes helps in developing effective system for improving
the capabilities of the business operations (Wayne, 2013). The need of outsourcing arises for
the Aztec Organization due to the occurrence of following reasons:
Steps to reduce the cost associated with the deployment of resources and business
activities
The Aztec Pvt. Ltd. wants to transform their traditional working system with the upgraded
business tactics. The owner of the company decided to outsource their business processes and
functionality to the network used by the third party for the management of the data
application. After the outsourcing of business operation, it has been analysed that there are IT
risks associated with the process of outsourcing. The company is looking forward for the plan
to develop a risks assessment matrix which helps in developing proactive action plan to
overcome the risks associated with the outsourcing of the processes. The coordination of the
functionality should be analysed and taken into consideration to develop the risks assessment
plan. The purpose of this paper is to design a qualitative and quantitative research
methodologies for analysing the risks and security issues associated with the outsourcing of
the organization operational processes to the network of the third party. The focus should also
be given on reviewing the impact of outsourcing on the financial sector and the traditional
security architecture with the development of the risks assessment management plan.
2. Outsourcing of the IT functionality
Outsourcing is the process which helps in enhancing the strategic decision taken for
facilitating the cost associated with the development program of knowledge domain to access
the organization goal within minimum period of time and cost. The outsourcing of the
activities is the tactical decision to enhance the resource management program of the
enterprise (Shacklett, 2012). The business activities which are outsourced on the network of
the third party are categorised as operation related with the deployment of the helpdesk
portfolio, data centre management schemes, and management of the application related to
control the business activities and processes. The outsourcing of the activities helps in
establishing continuous deployment of procurement process from the third party. The
communication between the stakeholders should be effectively managed to formulate the
requirement of establishing outsourcing program within the working curriculum of the Aztec
enterprise. The integration of processes helps in developing effective system for improving
the capabilities of the business operations (Wayne, 2013). The need of outsourcing arises for
the Aztec Organization due to the occurrence of following reasons:
Steps to reduce the cost associated with the deployment of resources and business
activities

The large investment for the resources at one time should be avoided
Managing the availability of resources on demand for carrying over the business
activities
To remain ahead for their core competencies in the global market
The upgrading of the technology according to the digital innovation in the global
market
Creating new values for the product to raise the contentment level of the customer to a
high extent (Peters, 2015).
The outsourcing of the business activities to the third party involves the development of the
outsourcing model with the inclusion of business process outsourcing techniques, outsourcing
process for administrative control, service providers used for deploying application,
maintenance and development of operation for application maintenance, and the management
of IT services. it has been analysed that the services provided by the outsourcing model are
categorised as fixing of the procurement support, enhancing and upgrading of the IT services,
and development of the new application according to the requirement of the Aztec
organization. It is an efficient technology for providing security to the business process by
peer to peer management of the activities (Patil, 2013). It is capable of providing security
with the help of firewall management system, intrusion detection and prevention system,
development of policies and standards for security, and the development of the IT
management system. The management of the data centre for remote accessing of the
information can be efficiently done with the help of outsourcing program. The inclusion of
help desk helps in the management of global hub for the efficient development of the
technical hub. The activities which are outsourced by the Aztec organization to the third party
are integration of the system development, maintenance of the data network, deployment of
the data centre with the use of mainframe, repairing and maintenance program for the
application, and many others. The following diagram shows the outsourcing model
implemented by the Aztec organization for upgrading its business operational program:
Managing the availability of resources on demand for carrying over the business
activities
To remain ahead for their core competencies in the global market
The upgrading of the technology according to the digital innovation in the global
market
Creating new values for the product to raise the contentment level of the customer to a
high extent (Peters, 2015).
The outsourcing of the business activities to the third party involves the development of the
outsourcing model with the inclusion of business process outsourcing techniques, outsourcing
process for administrative control, service providers used for deploying application,
maintenance and development of operation for application maintenance, and the management
of IT services. it has been analysed that the services provided by the outsourcing model are
categorised as fixing of the procurement support, enhancing and upgrading of the IT services,
and development of the new application according to the requirement of the Aztec
organization. It is an efficient technology for providing security to the business process by
peer to peer management of the activities (Patil, 2013). It is capable of providing security
with the help of firewall management system, intrusion detection and prevention system,
development of policies and standards for security, and the development of the IT
management system. The management of the data centre for remote accessing of the
information can be efficiently done with the help of outsourcing program. The inclusion of
help desk helps in the management of global hub for the efficient development of the
technical hub. The activities which are outsourced by the Aztec organization to the third party
are integration of the system development, maintenance of the data network, deployment of
the data centre with the use of mainframe, repairing and maintenance program for the
application, and many others. The following diagram shows the outsourcing model
implemented by the Aztec organization for upgrading its business operational program:
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
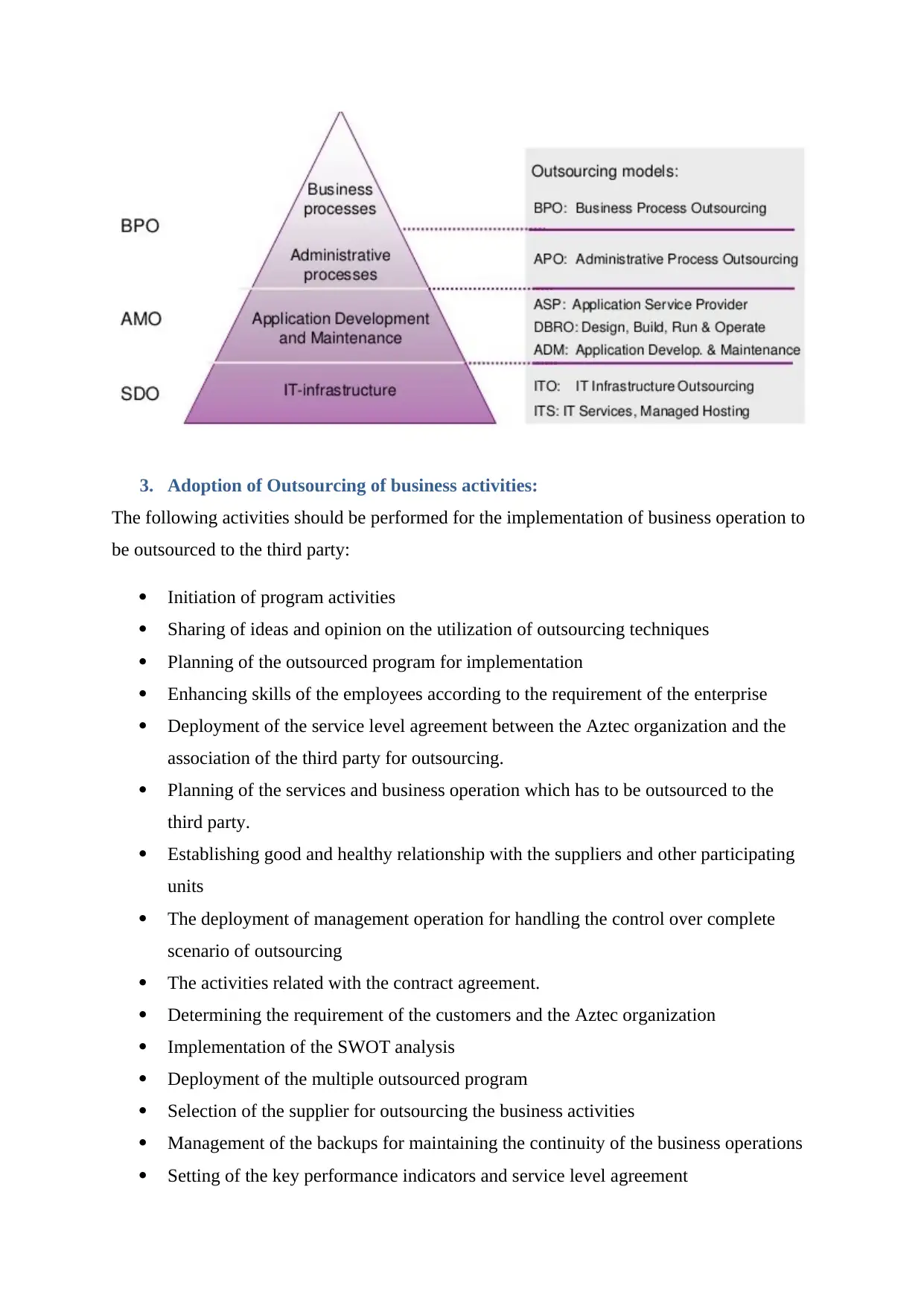
3. Adoption of Outsourcing of business activities:
The following activities should be performed for the implementation of business operation to
be outsourced to the third party:
Initiation of program activities
Sharing of ideas and opinion on the utilization of outsourcing techniques
Planning of the outsourced program for implementation
Enhancing skills of the employees according to the requirement of the enterprise
Deployment of the service level agreement between the Aztec organization and the
association of the third party for outsourcing.
Planning of the services and business operation which has to be outsourced to the
third party.
Establishing good and healthy relationship with the suppliers and other participating
units
The deployment of management operation for handling the control over complete
scenario of outsourcing
The activities related with the contract agreement.
Determining the requirement of the customers and the Aztec organization
Implementation of the SWOT analysis
Deployment of the multiple outsourced program
Selection of the supplier for outsourcing the business activities
Management of the backups for maintaining the continuity of the business operations
Setting of the key performance indicators and service level agreement
The following activities should be performed for the implementation of business operation to
be outsourced to the third party:
Initiation of program activities
Sharing of ideas and opinion on the utilization of outsourcing techniques
Planning of the outsourced program for implementation
Enhancing skills of the employees according to the requirement of the enterprise
Deployment of the service level agreement between the Aztec organization and the
association of the third party for outsourcing.
Planning of the services and business operation which has to be outsourced to the
third party.
Establishing good and healthy relationship with the suppliers and other participating
units
The deployment of management operation for handling the control over complete
scenario of outsourcing
The activities related with the contract agreement.
Determining the requirement of the customers and the Aztec organization
Implementation of the SWOT analysis
Deployment of the multiple outsourced program
Selection of the supplier for outsourcing the business activities
Management of the backups for maintaining the continuity of the business operations
Setting of the key performance indicators and service level agreement
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
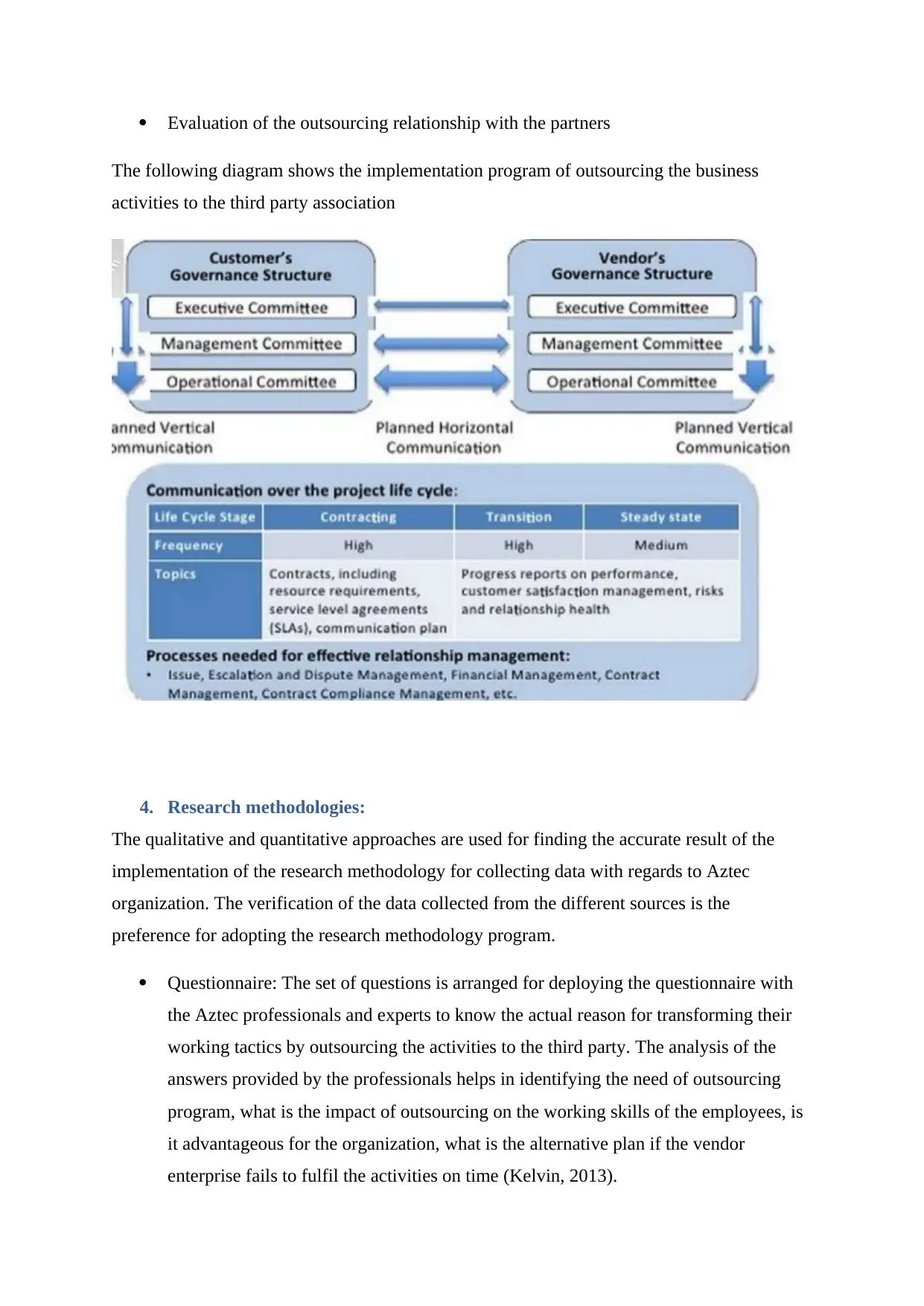
Evaluation of the outsourcing relationship with the partners
The following diagram shows the implementation program of outsourcing the business
activities to the third party association
4. Research methodologies:
The qualitative and quantitative approaches are used for finding the accurate result of the
implementation of the research methodology for collecting data with regards to Aztec
organization. The verification of the data collected from the different sources is the
preference for adopting the research methodology program.
Questionnaire: The set of questions is arranged for deploying the questionnaire with
the Aztec professionals and experts to know the actual reason for transforming their
working tactics by outsourcing the activities to the third party. The analysis of the
answers provided by the professionals helps in identifying the need of outsourcing
program, what is the impact of outsourcing on the working skills of the employees, is
it advantageous for the organization, what is the alternative plan if the vendor
enterprise fails to fulfil the activities on time (Kelvin, 2013).
The following diagram shows the implementation program of outsourcing the business
activities to the third party association
4. Research methodologies:
The qualitative and quantitative approaches are used for finding the accurate result of the
implementation of the research methodology for collecting data with regards to Aztec
organization. The verification of the data collected from the different sources is the
preference for adopting the research methodology program.
Questionnaire: The set of questions is arranged for deploying the questionnaire with
the Aztec professionals and experts to know the actual reason for transforming their
working tactics by outsourcing the activities to the third party. The analysis of the
answers provided by the professionals helps in identifying the need of outsourcing
program, what is the impact of outsourcing on the working skills of the employees, is
it advantageous for the organization, what is the alternative plan if the vendor
enterprise fails to fulfil the activities on time (Kelvin, 2013).

Sampling techniques: The target audience is chosen to perform the sampling testing
program to collect the information about the benefits of outsourcing to the client
company. From the research, it has been determined that the turnover of the company
has increased from 30% to 45% with the use of outsourcing business process because
it helps in reducing the risks associated with the activities which are to be undertaken
to complete the project on time. It helps in determining strategic decision to adopt the
outsource program for the company or not (Mitchell, 2017).
Data collection from multiple sources: The data is gathered from different sources to
analyse the facts from the primary data which is collected. It helps in analysing the
positive and the negative points of the outsourcing program.
Interview: The face to face arrangement of the interview with the top executives of
the Aztec organization helps in identifying the facts for changing the business tactics
with the inclusion of outsourcing program.
Survey: The survey is arranged on different organizations which are currently
working on the outsourced program to identify the benefits and drawbacks of this
newer approach of operation (Mirkovic, 2007). It has been analysed that it is the cost
effective program for controlling the flow of business activities.
5. Review of outsourcing of functionality in relation with financial sector
The implementation of the outsourcing program is the cost effective program for controlling
the flow of business activities. The financial activities of the enterprise can be enhanced with
the active participation of the outsourcing vendor company. The reputation of the company
can be improved with the increasing turnover of the company. The skills of the working
employees can be sharpen according to the requirement of the global market to remain in
front of the competitors. The competitive advantage can be gained with the utilization of
skilled worker in the efficient manner. The satisfaction of the customers can be effectively
improved due to the active participation of the customers to specify their requirement
specification clearly to the outsourcing company. The follow up of the regulatory compliance
of government helps in improving the functionality of the outsourcing company. The
reduction in the cost is the major factor to adopt the working tactics of the outsourced
program. The good and healthy relationship between the service provider and the outsourcing
organization helps in completing the tasks before the baseline. The difficulties of the time
completion can be resolved with the effective utilization of the labour and the resources for
program to collect the information about the benefits of outsourcing to the client
company. From the research, it has been determined that the turnover of the company
has increased from 30% to 45% with the use of outsourcing business process because
it helps in reducing the risks associated with the activities which are to be undertaken
to complete the project on time. It helps in determining strategic decision to adopt the
outsource program for the company or not (Mitchell, 2017).
Data collection from multiple sources: The data is gathered from different sources to
analyse the facts from the primary data which is collected. It helps in analysing the
positive and the negative points of the outsourcing program.
Interview: The face to face arrangement of the interview with the top executives of
the Aztec organization helps in identifying the facts for changing the business tactics
with the inclusion of outsourcing program.
Survey: The survey is arranged on different organizations which are currently
working on the outsourced program to identify the benefits and drawbacks of this
newer approach of operation (Mirkovic, 2007). It has been analysed that it is the cost
effective program for controlling the flow of business activities.
5. Review of outsourcing of functionality in relation with financial sector
The implementation of the outsourcing program is the cost effective program for controlling
the flow of business activities. The financial activities of the enterprise can be enhanced with
the active participation of the outsourcing vendor company. The reputation of the company
can be improved with the increasing turnover of the company. The skills of the working
employees can be sharpen according to the requirement of the global market to remain in
front of the competitors. The competitive advantage can be gained with the utilization of
skilled worker in the efficient manner. The satisfaction of the customers can be effectively
improved due to the active participation of the customers to specify their requirement
specification clearly to the outsourcing company. The follow up of the regulatory compliance
of government helps in improving the functionality of the outsourcing company. The
reduction in the cost is the major factor to adopt the working tactics of the outsourced
program. The good and healthy relationship between the service provider and the outsourcing
organization helps in completing the tasks before the baseline. The difficulties of the time
completion can be resolved with the effective utilization of the labour and the resources for
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

completing the business processes. The cost spent on running the application and business
processes can be controlled with the use of outsourcing program. The competency can be
achieved with the inflow of regulatory compliance for the effective working within the
government norms. The financial growth of the company can be improved if the outsourcing
company can efficiently understand the requirement and business activities forum to get the
required output. The on-demand accessing of the resources helps in increasing the
compatibility with the offered business activities by the Aztec organization. It has reviewed
that the efficient handling of the risks associated with the project helps in efficiently
managing the flow of activities.
6. Impact of outsourcing of the functionality on the traditional security system
The security procedures which are used for handling the traditional business functionality
have to be changed according to the requirement of the outsourcing programs. The
arrangement of the business processes on the outsource environment helps in managing the
risks associated with the business activities. The operations are selected according to the
requirement of completing the business processes which helps in improving the turnover of
the enterprise. The application development program should be arranged for effective
utilization of the data centres (Chaudhary, 2013). The intranet and extranet should be
effectively employed within the working curriculum of the enterprise to have a check on the
business activities by the outsourcing company. The outsourcing of the business processes is
mainly done with the aim of reducing the cost of the resources used, overcoming the
limitation of the skilled labour availability, the difficulty in hiring the employees from
external sources is resolved, the risks of the organization can be transferred to the
outsourcing industry, helps in minimizing the risks, the development of the strategic
relationship with the supplier, and the project can be delivered within the baseline of the
project The focus should be given on the following activities to develop the new security
system according to the requirement of outsourcing of the business processes.
Migration of data and processes to the outsourcing organization
Conversion of data required to transmit the data to the outsourcing enterprise
Development of IT infrastructure which helps in transferring of data and processes to
the third party for carrying over the tasks provided within the available time and cost
with the management of availability of resources (Buhalis, 2014).
Functions related with performing maintenance and control system
processes can be controlled with the use of outsourcing program. The competency can be
achieved with the inflow of regulatory compliance for the effective working within the
government norms. The financial growth of the company can be improved if the outsourcing
company can efficiently understand the requirement and business activities forum to get the
required output. The on-demand accessing of the resources helps in increasing the
compatibility with the offered business activities by the Aztec organization. It has reviewed
that the efficient handling of the risks associated with the project helps in efficiently
managing the flow of activities.
6. Impact of outsourcing of the functionality on the traditional security system
The security procedures which are used for handling the traditional business functionality
have to be changed according to the requirement of the outsourcing programs. The
arrangement of the business processes on the outsource environment helps in managing the
risks associated with the business activities. The operations are selected according to the
requirement of completing the business processes which helps in improving the turnover of
the enterprise. The application development program should be arranged for effective
utilization of the data centres (Chaudhary, 2013). The intranet and extranet should be
effectively employed within the working curriculum of the enterprise to have a check on the
business activities by the outsourcing company. The outsourcing of the business processes is
mainly done with the aim of reducing the cost of the resources used, overcoming the
limitation of the skilled labour availability, the difficulty in hiring the employees from
external sources is resolved, the risks of the organization can be transferred to the
outsourcing industry, helps in minimizing the risks, the development of the strategic
relationship with the supplier, and the project can be delivered within the baseline of the
project The focus should be given on the following activities to develop the new security
system according to the requirement of outsourcing of the business processes.
Migration of data and processes to the outsourcing organization
Conversion of data required to transmit the data to the outsourcing enterprise
Development of IT infrastructure which helps in transferring of data and processes to
the third party for carrying over the tasks provided within the available time and cost
with the management of availability of resources (Buhalis, 2014).
Functions related with performing maintenance and control system
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Role of service provider in providing the services to the external parties
The relationship between the customers and the external parties for satisfying the
requirement of the consumer
The changes required in the traditional security system involve the amalgamation of
international standard of security policies and procedures. It helps in establishing new
security architecture for the Aztec organization to outsource their business data and processes
by maintaining the confidentiality, accuracy, and integrity of data in the transmission process.
The legal requirement of the enterprise should comprise with the government regulatory
compliance. The privacy of the customer personal information should be maintained. The
requirement of the vendor should be fulfilled in the complete life cycle of the project
development. The stages mentioned in the service level agreement should be changed
according to the requirement of outsourcing of the business process. The contract should be
developed for managing the security portfolio throughout the project development life cycle.
7. Data security risks and Data flow:
The deployment of outsourcing program is equipped with some challenges and risks which
should be taken under consideration such as geographically distribution in the company’s
location, inadequacy and unclear accountability program for resource procurement plan, no
support of delegation, procedures are not completed within the allocated turnaround time,
discontentment in the customers and the employees, the cost of resources get increased due to
the crossing of the baseline, inclusion of training and development program put extra pressure
on the management team, and no solution for data capturing.
The following diagram shows the flow of data for outsourcing the business processes to the
third party. The Aztec organization first identifies the requirement or need for outsourcing the
business processes and then signs the agreement with the outsourcing third part to carry over
the business processes. The Aztec organization checks the quality of the project after the
completion of activities by the outsourcing company and delivered the final product to the
stakeholder for use.
The relationship between the customers and the external parties for satisfying the
requirement of the consumer
The changes required in the traditional security system involve the amalgamation of
international standard of security policies and procedures. It helps in establishing new
security architecture for the Aztec organization to outsource their business data and processes
by maintaining the confidentiality, accuracy, and integrity of data in the transmission process.
The legal requirement of the enterprise should comprise with the government regulatory
compliance. The privacy of the customer personal information should be maintained. The
requirement of the vendor should be fulfilled in the complete life cycle of the project
development. The stages mentioned in the service level agreement should be changed
according to the requirement of outsourcing of the business process. The contract should be
developed for managing the security portfolio throughout the project development life cycle.
7. Data security risks and Data flow:
The deployment of outsourcing program is equipped with some challenges and risks which
should be taken under consideration such as geographically distribution in the company’s
location, inadequacy and unclear accountability program for resource procurement plan, no
support of delegation, procedures are not completed within the allocated turnaround time,
discontentment in the customers and the employees, the cost of resources get increased due to
the crossing of the baseline, inclusion of training and development program put extra pressure
on the management team, and no solution for data capturing.
The following diagram shows the flow of data for outsourcing the business processes to the
third party. The Aztec organization first identifies the requirement or need for outsourcing the
business processes and then signs the agreement with the outsourcing third part to carry over
the business processes. The Aztec organization checks the quality of the project after the
completion of activities by the outsourcing company and delivered the final product to the
stakeholder for use.
8. Risk assessment matrix
The following table shows the risks associated with the outsourcing of business processes to
the third party for the management of data:
Risk Description
Inclusion of weak management tactics used
by the third party
The measurement of the performance of the
business activities helps in analysing the
efficiency of the third party to carry out the
business operation. The poor performance
indicates that the third party is not efficient in
carrying over the business processes. The
cost incurred in the activities help in
The following table shows the risks associated with the outsourcing of business processes to
the third party for the management of data:
Risk Description
Inclusion of weak management tactics used
by the third party
The measurement of the performance of the
business activities helps in analysing the
efficiency of the third party to carry out the
business operation. The poor performance
indicates that the third party is not efficient in
carrying over the business processes. The
cost incurred in the activities help in
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 20
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





