Comprehensive IT Risk Management Report for Big Data Environments
VerifiedAdded on 2019/11/08
|13
|2769
|478
Report
AI Summary
This report provides a comprehensive analysis of IT risk management in the context of big data environments, focusing on the ENISA development authority's role in streamlining processes, threat identification, and mitigation policies. It examines the infrastructure of big data security, including the 6V's architecture (Volume, Velocity, Variety, Veracity, Variability, Value), and details the layers involved in big data management (Presentation, Analytical/Computing Model, Data Storage, Process Integration, and Data Source Management). The report presents a detailed analysis of various threats, categorizing them and assessing their probabilities, alongside the classification of threat agents. It further explores procedures for minimizing threats, including data protection methods, encryption, and authentication. The report highlights the Extract, Transform, and Load (ETL) process using Hadoop, and concludes with recommendations for evaluating and enhancing big data management practices, emphasizing the importance of security and risk mitigation. The report also contains a detailed table of contents and references.

IT RISK MANAGEMENT
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

IT risk management
Table of Contents
Case scenario:..........................................................................................................................................2
Vision:......................................................................................................................................................2
Infrastructure of Big data security:..........................................................................................................3
Analysis of threats:..................................................................................................................................5
Significance:............................................................................................................................................7
Classification of threat agents:.................................................................................................................7
Procedure for minimizing threats:...........................................................................................................8
Trends and probability associated with the threats:.................................................................................8
Deployment of Extract, transforms, and load process:..........................................................................10
Evaluation and Recommendation:.........................................................................................................10
Conclusion:............................................................................................................................................11
References:.............................................................................................................................................11
1
Table of Contents
Case scenario:..........................................................................................................................................2
Vision:......................................................................................................................................................2
Infrastructure of Big data security:..........................................................................................................3
Analysis of threats:..................................................................................................................................5
Significance:............................................................................................................................................7
Classification of threat agents:.................................................................................................................7
Procedure for minimizing threats:...........................................................................................................8
Trends and probability associated with the threats:.................................................................................8
Deployment of Extract, transforms, and load process:..........................................................................10
Evaluation and Recommendation:.........................................................................................................10
Conclusion:............................................................................................................................................11
References:.............................................................................................................................................11
1

IT risk management
Case scenario:
The ENISA is the development authority which focuses on streamlining the functionality of
the processes, threat identification and mitigation policies, and organization of information
security for the big data management program. The handling of the big data is equipped with
some of the risks for which the control management program should be undertaken. The
identification of the threats associated with the big data helps in developing mitigation plans
to develop proactive action plan for the management of the big data over the network.
Vision:
The big data storage requires the deployment of high level replication strategies. “The
inclusion of new threats focuses on the outsourcing of the big data management program”
(Wang, 2014). The threats are associated with the data leakages and the degradation in losing
the confidentiality of the system. The data protection and privacy methods are used for
increasing the storage capability of the big data. The data collection method is used for
specifying the key requirement for managing the big data. The management of the big data
performance can be measured in terms of data leakages and associated breaches. The asset
owners associated with the big data management are categorised as data owners, data
transformers, computation providers, and storage service providers. The processes of the big
data schemes are aligned with the help of coordination between the activities and conflicts.
“The complexity of the data management processes can be resolved with the implementation
of security schemes in the different phases of project life cycle” (Zhang, 2014). The large
volumes of big data can affect the security measures which are undertaken for its
management. The security principles and guidelines are used in the big data paradigm for
reducing the security and privacy risks associated with the big data storage. The theory of gap
analysis is used for threat identification and develops new policies for mitigation. The
mitigation policies are used for developing the flawless big data security infrastructure. The
availability of the technology can result in the development of secure system for storing big
data. “The processes which are equipped in the deployment of big data management are
analysis of the traditional approach, threats identification, activities planning, deployment of
the big data environment, security procedures, big data asset management, and identification
of mitigation procedures” (Mobarak, 2016). The infrastructure provides different techniques
to overcome the problem of threats associated with the management of the big data over the
network.
2
Case scenario:
The ENISA is the development authority which focuses on streamlining the functionality of
the processes, threat identification and mitigation policies, and organization of information
security for the big data management program. The handling of the big data is equipped with
some of the risks for which the control management program should be undertaken. The
identification of the threats associated with the big data helps in developing mitigation plans
to develop proactive action plan for the management of the big data over the network.
Vision:
The big data storage requires the deployment of high level replication strategies. “The
inclusion of new threats focuses on the outsourcing of the big data management program”
(Wang, 2014). The threats are associated with the data leakages and the degradation in losing
the confidentiality of the system. The data protection and privacy methods are used for
increasing the storage capability of the big data. The data collection method is used for
specifying the key requirement for managing the big data. The management of the big data
performance can be measured in terms of data leakages and associated breaches. The asset
owners associated with the big data management are categorised as data owners, data
transformers, computation providers, and storage service providers. The processes of the big
data schemes are aligned with the help of coordination between the activities and conflicts.
“The complexity of the data management processes can be resolved with the implementation
of security schemes in the different phases of project life cycle” (Zhang, 2014). The large
volumes of big data can affect the security measures which are undertaken for its
management. The security principles and guidelines are used in the big data paradigm for
reducing the security and privacy risks associated with the big data storage. The theory of gap
analysis is used for threat identification and develops new policies for mitigation. The
mitigation policies are used for developing the flawless big data security infrastructure. The
availability of the technology can result in the development of secure system for storing big
data. “The processes which are equipped in the deployment of big data management are
analysis of the traditional approach, threats identification, activities planning, deployment of
the big data environment, security procedures, big data asset management, and identification
of mitigation procedures” (Mobarak, 2016). The infrastructure provides different techniques
to overcome the problem of threats associated with the management of the big data over the
network.
2
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
IT risk management
Infrastructure of Big data security:
The analysis of the threat involves the amalgamation of different strategies for carrying out
cyber security program. The gathering and collecting of information from different sources
helps in the implementation of security infrastructure for the big data management. The
functioning of the big data is adversely affected by the inclusion of the threats on the storage
units. The interrelationship should be developed between different computation units such as
power, storage, power, and analytics. The digital information should be collected from
secured massive data on the internet. The procedures and policies should be developed for
solving issues related with privacy and data protection. The 6V’s architecture is deployed for
the development of big data management program which are described in the table below:
6V’s Architecture Description
Volume The data should be collected and gathered from different
sources from the internet.
Velocity The velocity focuses on the speed by which data packets are
sends and received on the request of the user.
Variety The different types of data can be collected from different
sources which are available on the internet.
Veracity The quality of the data collected can be improved by
making use of authentication tools and technologies.
Variability “The scheduling of activities helps in overcoming the
problem of inconsistencies which is associated with the data
arrival” (Terzi, 2015). The big data can effectively manage
over the internet with the use of variability process.
Value “The potential revenues can be collected with the values
associated with the amalgamation of big data available on
the internet” (Damiani, 2016).
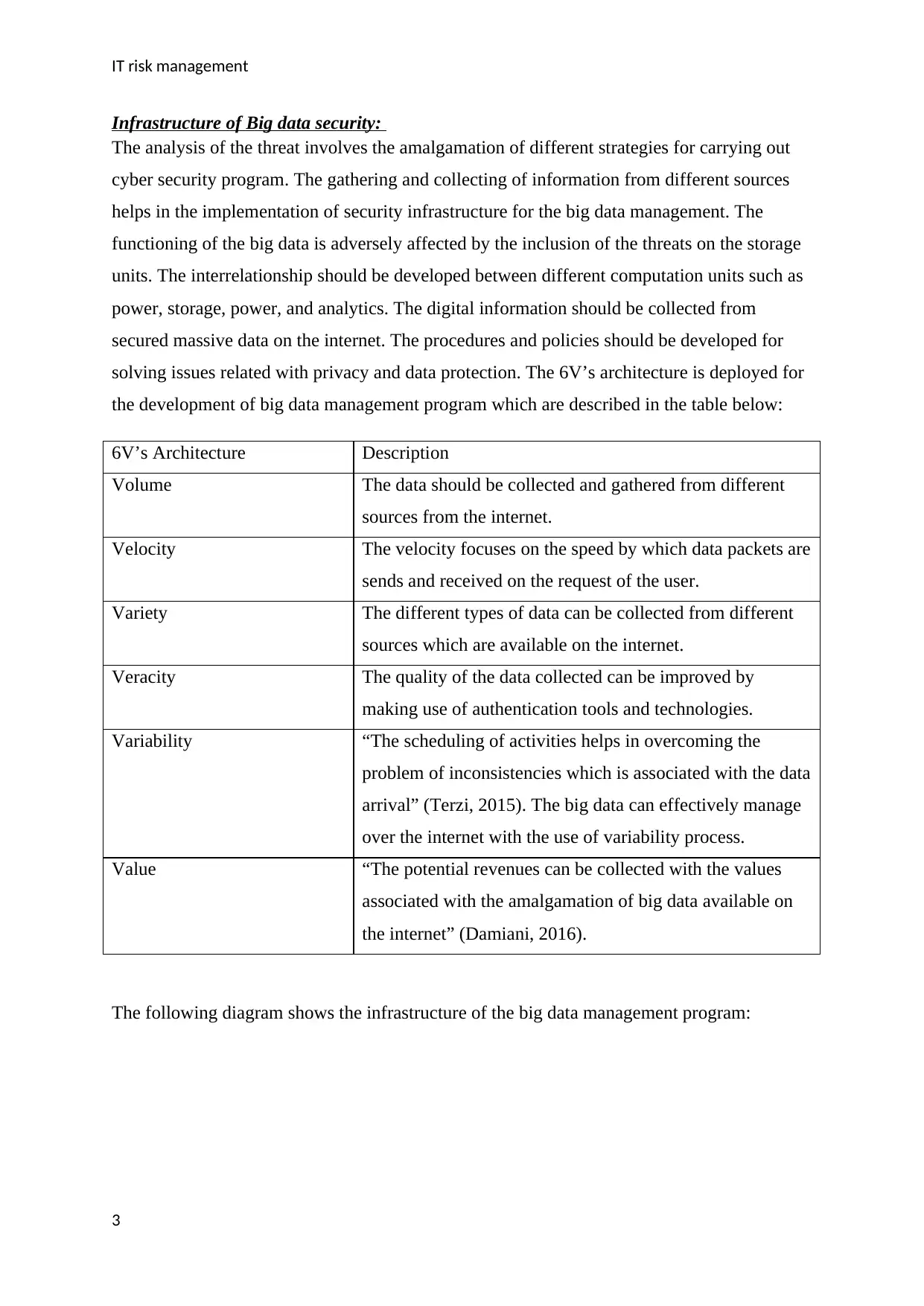
The following diagram shows the infrastructure of the big data management program:
3
Infrastructure of Big data security:
The analysis of the threat involves the amalgamation of different strategies for carrying out
cyber security program. The gathering and collecting of information from different sources
helps in the implementation of security infrastructure for the big data management. The
functioning of the big data is adversely affected by the inclusion of the threats on the storage
units. The interrelationship should be developed between different computation units such as
power, storage, power, and analytics. The digital information should be collected from
secured massive data on the internet. The procedures and policies should be developed for
solving issues related with privacy and data protection. The 6V’s architecture is deployed for
the development of big data management program which are described in the table below:
6V’s Architecture Description
Volume The data should be collected and gathered from different
sources from the internet.
Velocity The velocity focuses on the speed by which data packets are
sends and received on the request of the user.
Variety The different types of data can be collected from different
sources which are available on the internet.
Veracity The quality of the data collected can be improved by
making use of authentication tools and technologies.
Variability “The scheduling of activities helps in overcoming the
problem of inconsistencies which is associated with the data
arrival” (Terzi, 2015). The big data can effectively manage
over the internet with the use of variability process.
Value “The potential revenues can be collected with the values
associated with the amalgamation of big data available on
the internet” (Damiani, 2016).
The following diagram shows the infrastructure of the big data management program:
3
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
IT risk management
The description of the layers is given below:
Presentation layer: “The presentation layer is composed of web browsers, laptops and
desktops, mobile devices, and the deployment of the web services” (Jaseena, 2013).
Analytical and computing model layer: This layer is comprised of reporting and query
tools, techniques used for map reduction, deployment of the stream analytics, and
used of advanced analytics.
Data storage layer: The data storage layer is deal with deployment of the SQL
databases, management of the distributed file system, and implementation of the RDF
stores.
Process integration: “The integration of different processes involves the use of
messaging system with the use of correspondent API’s” (Munaye, 2016).
Data source management: This layer is comprised of streamlining of data and
deployment of the unstructured, semi-structured, and structured data.
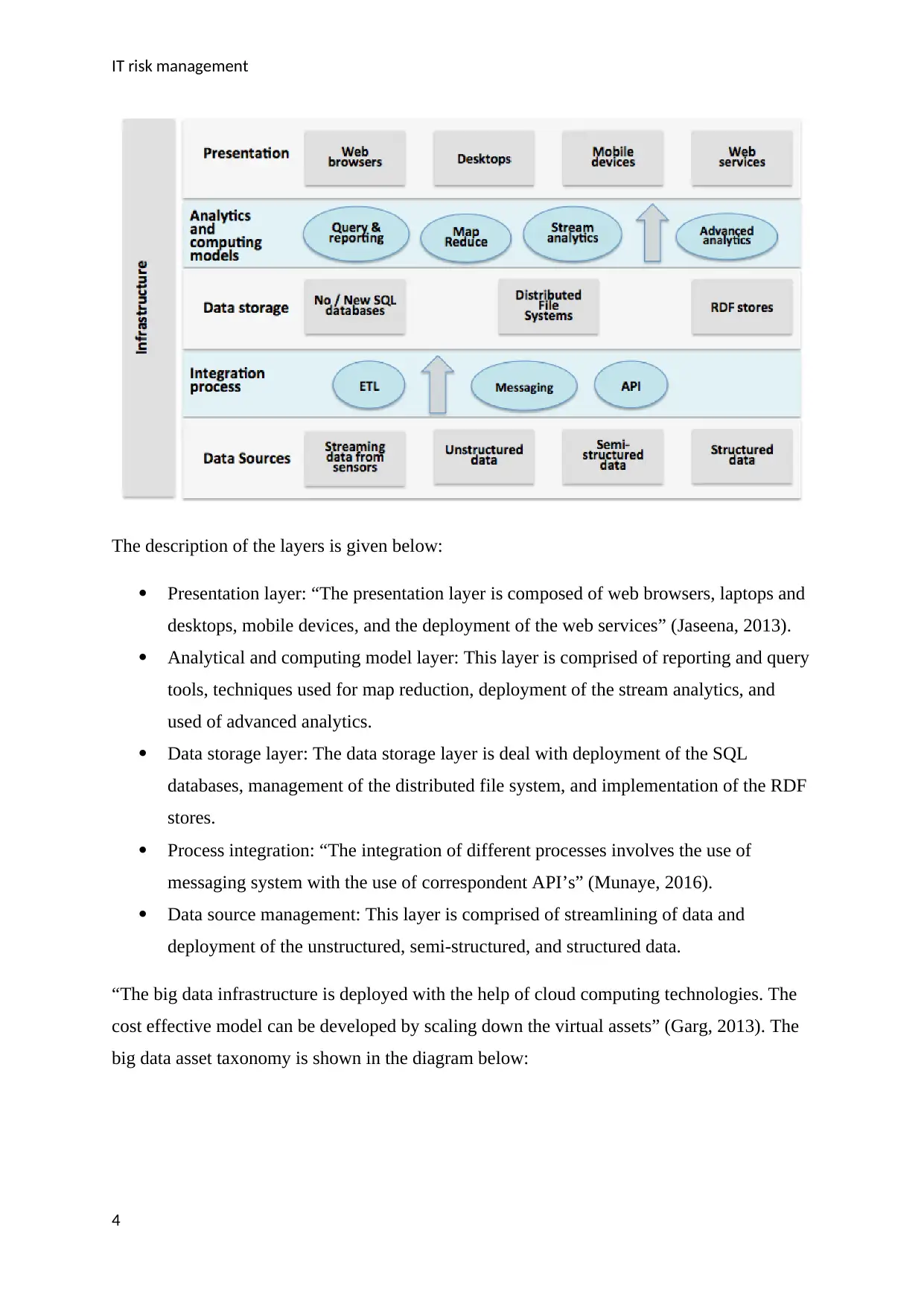
“The big data infrastructure is deployed with the help of cloud computing technologies. The
cost effective model can be developed by scaling down the virtual assets” (Garg, 2013). The
big data asset taxonomy is shown in the diagram below:
4
The description of the layers is given below:
Presentation layer: “The presentation layer is composed of web browsers, laptops and
desktops, mobile devices, and the deployment of the web services” (Jaseena, 2013).
Analytical and computing model layer: This layer is comprised of reporting and query
tools, techniques used for map reduction, deployment of the stream analytics, and
used of advanced analytics.
Data storage layer: The data storage layer is deal with deployment of the SQL
databases, management of the distributed file system, and implementation of the RDF
stores.
Process integration: “The integration of different processes involves the use of
messaging system with the use of correspondent API’s” (Munaye, 2016).
Data source management: This layer is comprised of streamlining of data and
deployment of the unstructured, semi-structured, and structured data.
“The big data infrastructure is deployed with the help of cloud computing technologies. The
cost effective model can be developed by scaling down the virtual assets” (Garg, 2013). The
big data asset taxonomy is shown in the diagram below:
4
IT risk management
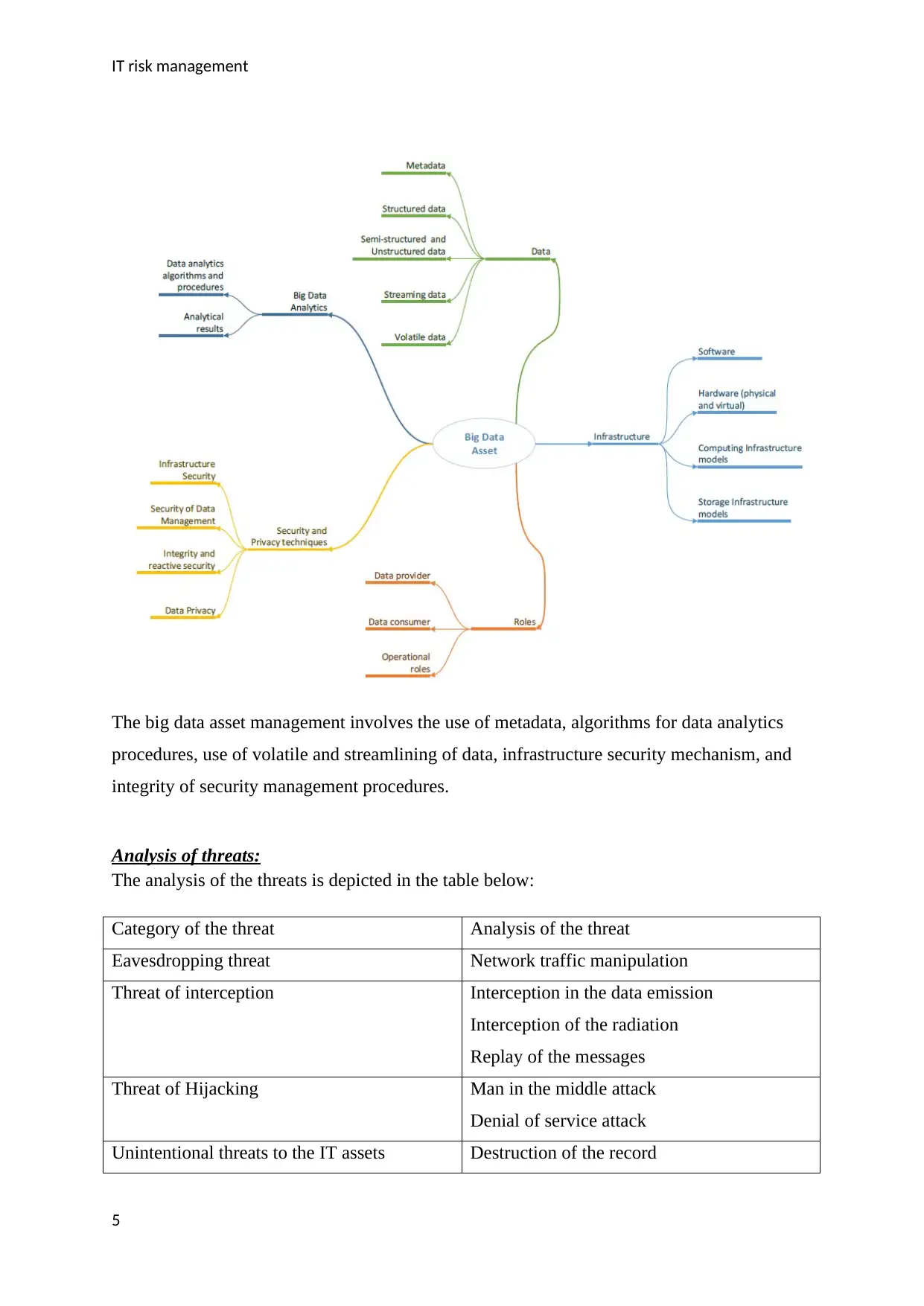
The big data asset management involves the use of metadata, algorithms for data analytics
procedures, use of volatile and streamlining of data, infrastructure security mechanism, and
integrity of security management procedures.
Analysis of threats:
The analysis of the threats is depicted in the table below:
Category of the threat Analysis of the threat
Eavesdropping threat Network traffic manipulation
Threat of interception Interception in the data emission
Interception of the radiation
Replay of the messages
Threat of Hijacking Man in the middle attack
Denial of service attack
Unintentional threats to the IT assets Destruction of the record
5
The big data asset management involves the use of metadata, algorithms for data analytics
procedures, use of volatile and streamlining of data, infrastructure security mechanism, and
integrity of security management procedures.
Analysis of threats:
The analysis of the threats is depicted in the table below:
Category of the threat Analysis of the threat
Eavesdropping threat Network traffic manipulation
Threat of interception Interception in the data emission
Interception of the radiation
Replay of the messages
Threat of Hijacking Man in the middle attack
Denial of service attack
Unintentional threats to the IT assets Destruction of the record
5
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
IT risk management
Data leakages in application and processes
Damage to the devices used for media
storage
Damage to the sensitive information
Loss of information deployed on the cloud
Testing of the penetrated threats
Damage caused with the inclusion of third
party
Deployment of the inadequate design for the
management of the big data.
Changes required in the information system
Use of unreliable sources for data collection
Deployment of the administration errors
Threats related with the working of the
organization
Unavailability of the skilled labour according
to the requirement of the project
Unavailability of the data resources required
to complete the project.
Legal issues Laws and regulation are violated regularly
Violation in the data management schemes.
Contract requirement are not completely
available
Inappropriateness in the management of the
personal data.
Brute force attack on the big data
management
Inadequacy in the business procedures and
guidelines
Leakage of confidential information
Other threats Denial of service attack
Problem associated with authorization and
authentication
Attachment of malicious code with activity
program of big data
Threats associated with the social
6
Data leakages in application and processes
Damage to the devices used for media
storage
Damage to the sensitive information
Loss of information deployed on the cloud
Testing of the penetrated threats
Damage caused with the inclusion of third
party
Deployment of the inadequate design for the
management of the big data.
Changes required in the information system
Use of unreliable sources for data collection
Deployment of the administration errors
Threats related with the working of the
organization
Unavailability of the skilled labour according
to the requirement of the project
Unavailability of the data resources required
to complete the project.
Legal issues Laws and regulation are violated regularly
Violation in the data management schemes.
Contract requirement are not completely
available
Inappropriateness in the management of the
personal data.
Brute force attack on the big data
management
Inadequacy in the business procedures and
guidelines
Leakage of confidential information
Other threats Denial of service attack
Problem associated with authorization and
authentication
Attachment of malicious code with activity
program of big data
Threats associated with the social
6
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
IT risk management
engineering
Target attacks performed by the hackers
Fraud emails and other tactics
Remote handling of the big data
“Manipulation and modification in the
available information” (Singh, 2015).
Significance:
The process of analysing the threats helps in managing the proactive action associated with
the deployment of big data assets. “The infrastructure malfunctioning can occurs due to the
attacks of threat on the big data storage” (Do, 2013). The effects of the threats are categorised
as granting of the unauthorised access of data retrieval, activities responsible for the
destruction of the confidentiality, integrity, and accuracy of the data, modification and
manipulation in the available data, denial of service attack, man in the middle attack, and
others. “The mitigation procedures are used for reducing the effects of threats on the big data
storage units” (Sebaa, 2014). The functioning of the big data is adversely affected by the
inclusion of the threats on the storage units. The availability of the threat is categorised into
two types which are inclusion of data breaches and data leakages in the big data storage unit.
Classification of threat agents:
The following table shows the classification of the threat agents:
Key threat agents Description
Corporation or organization The inefficiency in the working curriculum
of the organization can results in the
inclusion of the threats from external sources.
The organization capabilities can estimate on
the basis of sector, size, human intelligence,
and expertise area.
Inclusion of cyber criminals The cyber criminals can attack on the
confidentiality of the big data
Inclusion of the cyber-terrorist The cyber terrorist can negatively affect the
cyber infrastructure
7
engineering
Target attacks performed by the hackers
Fraud emails and other tactics
Remote handling of the big data
“Manipulation and modification in the
available information” (Singh, 2015).
Significance:
The process of analysing the threats helps in managing the proactive action associated with
the deployment of big data assets. “The infrastructure malfunctioning can occurs due to the
attacks of threat on the big data storage” (Do, 2013). The effects of the threats are categorised
as granting of the unauthorised access of data retrieval, activities responsible for the
destruction of the confidentiality, integrity, and accuracy of the data, modification and
manipulation in the available data, denial of service attack, man in the middle attack, and
others. “The mitigation procedures are used for reducing the effects of threats on the big data
storage units” (Sebaa, 2014). The functioning of the big data is adversely affected by the
inclusion of the threats on the storage units. The availability of the threat is categorised into
two types which are inclusion of data breaches and data leakages in the big data storage unit.
Classification of threat agents:
The following table shows the classification of the threat agents:
Key threat agents Description
Corporation or organization The inefficiency in the working curriculum
of the organization can results in the
inclusion of the threats from external sources.
The organization capabilities can estimate on
the basis of sector, size, human intelligence,
and expertise area.
Inclusion of cyber criminals The cyber criminals can attack on the
confidentiality of the big data
Inclusion of the cyber-terrorist The cyber terrorist can negatively affect the
cyber infrastructure
7
IT risk management
Use of script kiddies The use of script an programs for acquiring
the confidential information
Social Hackers The intelligence agencies focus on stealing
the information.
Employees The computer resources can be hacked by the
employees of the enterprise
Procedure for minimizing threats:
“The protection and security mechanism should be used for protecting the information
available on the large volume of the big data” (Zuech, 2015). “The sensitivity of the
information should be taken into consideration for managing the confidentiality of the
personal information” (Bouchard, 2012). The data transfer rate should be minimised. The
organization should take step forward to put restriction on the downloading of the data. The
files should not be shared without the authentication procedures. The encryption methods and
public key infrastructure should be used for preserving the large volume of data.
Trends and probability associated with the threats:
Threat Probability
Network traffic manipulation Low
Interception in the data emission
Interception of the radiation
Replay of the messages
Low
Man in the middle attack
Denial of service attack
High
Destruction of the record
Data leakages in application and processes
Damage to the devices used for media
storage
Damage to the sensitive information
Loss of information deployed on the cloud
Testing of the penetrated threats
Damage caused with the inclusion of third
party
Medium
Low
Low
High
Low
High
Low
Low
8
Use of script kiddies The use of script an programs for acquiring
the confidential information
Social Hackers The intelligence agencies focus on stealing
the information.
Employees The computer resources can be hacked by the
employees of the enterprise
Procedure for minimizing threats:
“The protection and security mechanism should be used for protecting the information
available on the large volume of the big data” (Zuech, 2015). “The sensitivity of the
information should be taken into consideration for managing the confidentiality of the
personal information” (Bouchard, 2012). The data transfer rate should be minimised. The
organization should take step forward to put restriction on the downloading of the data. The
files should not be shared without the authentication procedures. The encryption methods and
public key infrastructure should be used for preserving the large volume of data.
Trends and probability associated with the threats:
Threat Probability
Network traffic manipulation Low
Interception in the data emission
Interception of the radiation
Replay of the messages
Low
Man in the middle attack
Denial of service attack
High
Destruction of the record
Data leakages in application and processes
Damage to the devices used for media
storage
Damage to the sensitive information
Loss of information deployed on the cloud
Testing of the penetrated threats
Damage caused with the inclusion of third
party
Medium
Low
Low
High
Low
High
Low
Low
8
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
IT risk management
Deployment of the inadequate design for the
management of the big data.
Changes required in the information system
Use of unreliable sources for data collection
Deployment of the administration errors
High
Low
High
Unavailability of the skilled labour according
to the requirement of the project
Unavailability of the data resources required
to complete the project.
Low
High
Laws and regulation are violated regularly
Violation in the data management schemes.
Contract requirement are not completely
available
Inappropriateness in the management of the
personal data.
Brute force attack on the big data
management
Inadequacy in the business procedures and
guidelines
Leakage of confidential information
Low
Low
Low
High
High
High
Medium
Denial of service attack
Problem associated with authorization and
authentication
Attachment of malicious code with activity
program of big data
Threats associated with the social
engineering
Target attacks performed by the hackers
Fraud emails and other tactics
Remote handling of the big data
Manipulation and modification in the
available information.
Medium
High
High
Medium
Low
Low
Low
High
9
Deployment of the inadequate design for the
management of the big data.
Changes required in the information system
Use of unreliable sources for data collection
Deployment of the administration errors
High
Low
High
Unavailability of the skilled labour according
to the requirement of the project
Unavailability of the data resources required
to complete the project.
Low
High
Laws and regulation are violated regularly
Violation in the data management schemes.
Contract requirement are not completely
available
Inappropriateness in the management of the
personal data.
Brute force attack on the big data
management
Inadequacy in the business procedures and
guidelines
Leakage of confidential information
Low
Low
Low
High
High
High
Medium
Denial of service attack
Problem associated with authorization and
authentication
Attachment of malicious code with activity
program of big data
Threats associated with the social
engineering
Target attacks performed by the hackers
Fraud emails and other tactics
Remote handling of the big data
Manipulation and modification in the
available information.
Medium
High
High
Medium
Low
Low
Low
High
9
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
IT risk management
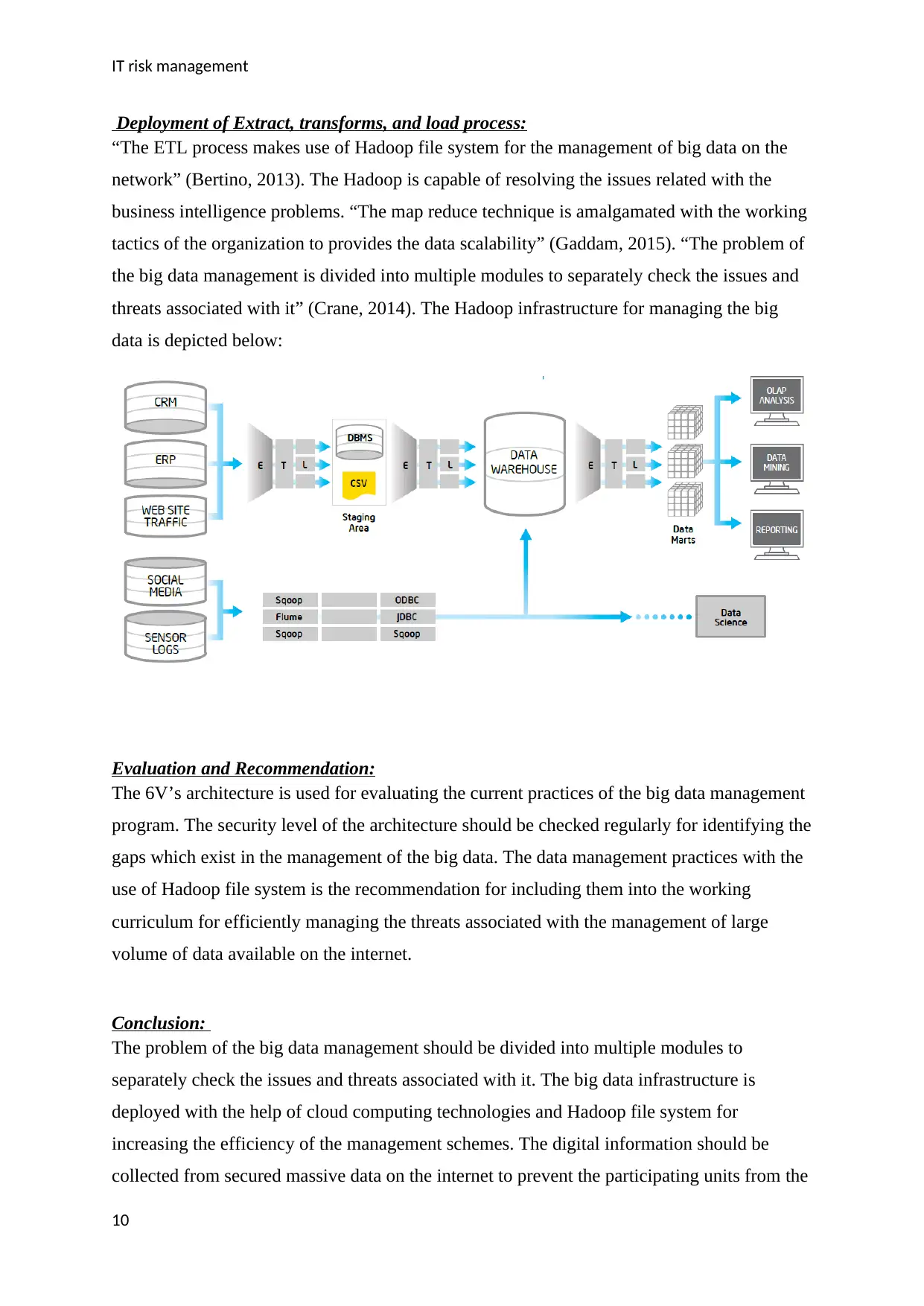
Deployment of Extract, transforms, and load process:
“The ETL process makes use of Hadoop file system for the management of big data on the
network” (Bertino, 2013). The Hadoop is capable of resolving the issues related with the
business intelligence problems. “The map reduce technique is amalgamated with the working
tactics of the organization to provides the data scalability” (Gaddam, 2015). “The problem of
the big data management is divided into multiple modules to separately check the issues and
threats associated with it” (Crane, 2014). The Hadoop infrastructure for managing the big
data is depicted below:
Evaluation and Recommendation:
The 6V’s architecture is used for evaluating the current practices of the big data management
program. The security level of the architecture should be checked regularly for identifying the
gaps which exist in the management of the big data. The data management practices with the
use of Hadoop file system is the recommendation for including them into the working
curriculum for efficiently managing the threats associated with the management of large
volume of data available on the internet.
Conclusion:
The problem of the big data management should be divided into multiple modules to
separately check the issues and threats associated with it. The big data infrastructure is
deployed with the help of cloud computing technologies and Hadoop file system for
increasing the efficiency of the management schemes. The digital information should be
collected from secured massive data on the internet to prevent the participating units from the
10
Deployment of Extract, transforms, and load process:
“The ETL process makes use of Hadoop file system for the management of big data on the
network” (Bertino, 2013). The Hadoop is capable of resolving the issues related with the
business intelligence problems. “The map reduce technique is amalgamated with the working
tactics of the organization to provides the data scalability” (Gaddam, 2015). “The problem of
the big data management is divided into multiple modules to separately check the issues and
threats associated with it” (Crane, 2014). The Hadoop infrastructure for managing the big
data is depicted below:
Evaluation and Recommendation:
The 6V’s architecture is used for evaluating the current practices of the big data management
program. The security level of the architecture should be checked regularly for identifying the
gaps which exist in the management of the big data. The data management practices with the
use of Hadoop file system is the recommendation for including them into the working
curriculum for efficiently managing the threats associated with the management of large
volume of data available on the internet.
Conclusion:
The problem of the big data management should be divided into multiple modules to
separately check the issues and threats associated with it. The big data infrastructure is
deployed with the help of cloud computing technologies and Hadoop file system for
increasing the efficiency of the management schemes. The digital information should be
collected from secured massive data on the internet to prevent the participating units from the
10

IT risk management
inclusion of the threats and risks associated with it which can adversely affect the working of
the system.
References:
Bertino, E. (2013). Data security challenges and research opportunities. Retrieved from
https://www.cs.purdue.edu/homes/bertino/sdm13.pdf
Bouchard, M. (2012). Big data for advanced threat protection. Retrieved from
http://www.trendmicro.co.in/cloud-content/us/pdfs/about/wp_aimpoint_group_big-
data-for-advanced-threat-protection.pdf
Crane, L. (2014). Big data analytics: A threat or an opportunity for knowledge management.
Retrieved from
https://www.researchgate.net/publication/265531901_Big_Data_Analytics_A_Threat
_or_an_Opportunity_for_Knowledge_Management
Damiani, A. (2016). Big data threat landscape and good practice guide. Retrieved from
http://www.google.co.in/url?sa=t&rct=j&q=Research%20paper%20pdf%20on
%20threat%20associated%20with%20big%20data
%20management&source=web&cd=2&cad=rja&uact=8&ved=0ahUKEwjzuZf5gZr
WAhVFL48KHTXEDMQQFgguMAE&url=https://www.enisa.europa.eu/
publications/bigdata-threat-landscape/at_download/
fullReport&usg=AFQjCNE80pGVaYBw0Tl7tZbBo4XAMMpUcA
Do, H. (2013). Data cleaning problem and current approaches. Retrieved from
http://citeseerx.ist.psu.edu/viewdoc/download?
doi=10.1.1.98.8661&rep=rep1&type=pdf
Gaddam, A. (2015). Securing your big data environment. Retrieved from
https://www.blackhat.com/docs/us-15/materials/us-15-Gaddam-Securing-Your-Big-
Data-Environment-wp.pdf
Garg, N. (2013). Big data analytics for security intelligence. Retrieved from
https://downloads.cloudsecurityalliance.org/initiatives/bdwg/Big_Data_Analytics_for
_Security_Intelligence.pdf
11
inclusion of the threats and risks associated with it which can adversely affect the working of
the system.
References:
Bertino, E. (2013). Data security challenges and research opportunities. Retrieved from
https://www.cs.purdue.edu/homes/bertino/sdm13.pdf
Bouchard, M. (2012). Big data for advanced threat protection. Retrieved from
http://www.trendmicro.co.in/cloud-content/us/pdfs/about/wp_aimpoint_group_big-
data-for-advanced-threat-protection.pdf
Crane, L. (2014). Big data analytics: A threat or an opportunity for knowledge management.
Retrieved from
https://www.researchgate.net/publication/265531901_Big_Data_Analytics_A_Threat
_or_an_Opportunity_for_Knowledge_Management
Damiani, A. (2016). Big data threat landscape and good practice guide. Retrieved from
http://www.google.co.in/url?sa=t&rct=j&q=Research%20paper%20pdf%20on
%20threat%20associated%20with%20big%20data
%20management&source=web&cd=2&cad=rja&uact=8&ved=0ahUKEwjzuZf5gZr
WAhVFL48KHTXEDMQQFgguMAE&url=https://www.enisa.europa.eu/
publications/bigdata-threat-landscape/at_download/
fullReport&usg=AFQjCNE80pGVaYBw0Tl7tZbBo4XAMMpUcA
Do, H. (2013). Data cleaning problem and current approaches. Retrieved from
http://citeseerx.ist.psu.edu/viewdoc/download?
doi=10.1.1.98.8661&rep=rep1&type=pdf
Gaddam, A. (2015). Securing your big data environment. Retrieved from
https://www.blackhat.com/docs/us-15/materials/us-15-Gaddam-Securing-Your-Big-
Data-Environment-wp.pdf
Garg, N. (2013). Big data analytics for security intelligence. Retrieved from
https://downloads.cloudsecurityalliance.org/initiatives/bdwg/Big_Data_Analytics_for
_Security_Intelligence.pdf
11
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 13
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





