IT Risk Management: Risk Assessment, Mitigation & CISO Role
VerifiedAdded on 2023/04/21
|10
|2567
|204
Report
AI Summary
This report provides a comprehensive analysis of IT risk management, focusing on risk assessment and mitigation strategies within an organization. It identifies various cyber security risks, such as data loss, social engineering, and malware threats, and proposes mitigation measures like implementing firewalls, encryption, and regular system updates. The report also emphasizes the importance of appointing a Chief Information Security Officer (CISO) and outlines their roles and responsibilities in maintaining the security of an organization like Commonwealth Scientific and Industrial Research Organization (CSIRO). The CISO's role includes developing security policies, managing risks, ensuring regulatory compliance, and spreading security awareness among employees. The report concludes by highlighting the significance of a CISO for both established and startup businesses in aligning security structures with business goals.

Running head: IT RISK MANAGEMENT
IT Risk management
Name of the student:
Name of the university:
IT Risk management
Name of the student:
Name of the university:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
1IT RISK MANAGEMENT
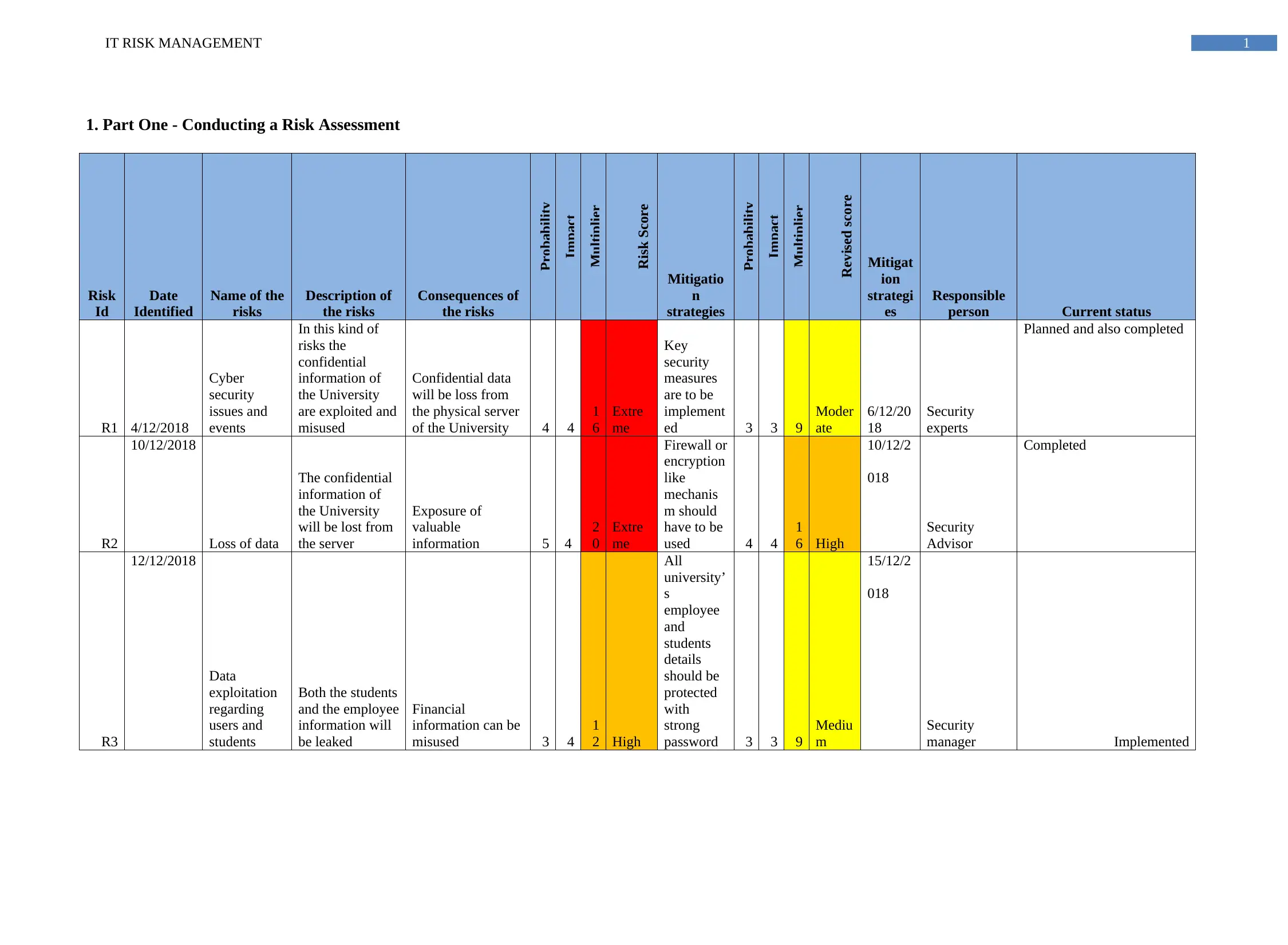
1. Part One - Conducting a Risk Assessment
Risk
Id
Date
Identified
Name of the
risks
Description of
the risks
Consequences of
the risks
Probability
Impact
Multiplier
Risk Score
Mitigatio
n
strategies
Probability
Impact
Multiplier
Revised score
Mitigat
ion
strategi
es
Responsible
person Current status
R1 4/12/2018
Cyber
security
issues and
events
In this kind of
risks the
confidential
information of
the University
are exploited and
misused
Confidential data
will be loss from
the physical server
of the University 4 4
1
6
Extre
me
Key
security
measures
are to be
implement
ed 3 3 9
Moder
ate
6/12/20
18
Security
experts
Planned and also completed
R2
10/12/2018
Loss of data
The confidential
information of
the University
will be lost from
the server
Exposure of
valuable
information 5 4
2
0
Extre
me
Firewall or
encryption
like
mechanis
m should
have to be
used 4 4
1
6 High
10/12/2
018
Security
Advisor
Completed
R3
12/12/2018
Data
exploitation
regarding
users and
students
Both the students
and the employee
information will
be leaked
Financial
information can be
misused 3 4
1
2 High
All
university’
s
employee
and
students
details
should be
protected
with
strong
password 3 3 9
Mediu
m
15/12/2
018
Security
manager Implemented
1. Part One - Conducting a Risk Assessment
Risk
Id
Date
Identified
Name of the
risks
Description of
the risks
Consequences of
the risks
Probability
Impact
Multiplier
Risk Score
Mitigatio
n
strategies
Probability
Impact
Multiplier
Revised score
Mitigat
ion
strategi
es
Responsible
person Current status
R1 4/12/2018
Cyber
security
issues and
events
In this kind of
risks the
confidential
information of
the University
are exploited and
misused
Confidential data
will be loss from
the physical server
of the University 4 4
1
6
Extre
me
Key
security
measures
are to be
implement
ed 3 3 9
Moder
ate
6/12/20
18
Security
experts
Planned and also completed
R2
10/12/2018
Loss of data
The confidential
information of
the University
will be lost from
the server
Exposure of
valuable
information 5 4
2
0
Extre
me
Firewall or
encryption
like
mechanis
m should
have to be
used 4 4
1
6 High
10/12/2
018
Security
Advisor
Completed
R3
12/12/2018
Data
exploitation
regarding
users and
students
Both the students
and the employee
information will
be leaked
Financial
information can be
misused 3 4
1
2 High
All
university’
s
employee
and
students
details
should be
protected
with
strong
password 3 3 9
Mediu
m
15/12/2
018
Security
manager Implemented
2IT RISK MANAGEMENT
R4 16/12/2018
Regulatory
and
compliance
issues
In this risk the
University
policy, law and
other standards
are all violated
All the risks and
policies are being
violated 3 2 6 Low
Advanced
regulatory
complianc
es should
have to be
processed 3 2 6 Low
20/12/2
018
Regulatory
system
authority
Panned and under
implementation phase
R5 19/11/2018
Social
engineering
and Phishing
issues
Mainly for the
broad range of
malicious
activities this
specific terms is
being used. It can
lea different
sensitive
confidential
information
Sensitive
information are
hacked through
electronic
communication 5 2
1
0
Moder
ate
The
electronic
communic
ation
medium
should
protected
from the
external
attackers 2 2 4 Low
22/11/2
018
System
engineer
Planned and not yet
accomplished
R6 22/12/2018
Direct
Daniel of
Service
This DOS attack
are mostly
infected through
Trojan virus and
used to targeting
single system
The hard disk drive
and operating both
can be impacted 3 4
1
2
Extre
me
All filed
should be
stored as a
backup
also 4 2 8
Mediu
m
25/12/2
018
Network
manager Implemented
R7 25/12/2018
Data
hacking,
ransonware
and physical
threats
This is a physical
security threat
which are often
underestimated
with the favour
of technical
threats
The personnel
information of the
victims are threats 5 4
2
0
Extre
me
Using
firewall,
antimalwa
re, anti
ransonwar
e as well
as anti
exploit
technologi
es 4 3
1
2 High
26/12/2
018
Security
experts
Under planning not yet
implemented
R8 26/12/2018
Spyware
threats
Each of the
online activities
are hacked and
misused at the
same time
Confidential
activities are
exploited 3 2 6 Low
All the
unwanted
software
should be
removed
from the
devices 3 2 6 Low
28/12/2
018
Users and
employees Planned and completed
R9 28/12/2018
Increasing
rate of
Cryptojackin
In order to obtain
much rate of
processing power
Compromised
blockchain
technology 3 5
1
5
Extere
me
The users
should
practice
29/12/2
018
Security
managers
Planned but not yet
completed
R4 16/12/2018
Regulatory
and
compliance
issues
In this risk the
University
policy, law and
other standards
are all violated
All the risks and
policies are being
violated 3 2 6 Low
Advanced
regulatory
complianc
es should
have to be
processed 3 2 6 Low
20/12/2
018
Regulatory
system
authority
Panned and under
implementation phase
R5 19/11/2018
Social
engineering
and Phishing
issues
Mainly for the
broad range of
malicious
activities this
specific terms is
being used. It can
lea different
sensitive
confidential
information
Sensitive
information are
hacked through
electronic
communication 5 2
1
0
Moder
ate
The
electronic
communic
ation
medium
should
protected
from the
external
attackers 2 2 4 Low
22/11/2
018
System
engineer
Planned and not yet
accomplished
R6 22/12/2018
Direct
Daniel of
Service
This DOS attack
are mostly
infected through
Trojan virus and
used to targeting
single system
The hard disk drive
and operating both
can be impacted 3 4
1
2
Extre
me
All filed
should be
stored as a
backup
also 4 2 8
Mediu
m
25/12/2
018
Network
manager Implemented
R7 25/12/2018
Data
hacking,
ransonware
and physical
threats
This is a physical
security threat
which are often
underestimated
with the favour
of technical
threats
The personnel
information of the
victims are threats 5 4
2
0
Extre
me
Using
firewall,
antimalwa
re, anti
ransonwar
e as well
as anti
exploit
technologi
es 4 3
1
2 High
26/12/2
018
Security
experts
Under planning not yet
implemented
R8 26/12/2018
Spyware
threats
Each of the
online activities
are hacked and
misused at the
same time
Confidential
activities are
exploited 3 2 6 Low
All the
unwanted
software
should be
removed
from the
devices 3 2 6 Low
28/12/2
018
Users and
employees Planned and completed
R9 28/12/2018
Increasing
rate of
Cryptojackin
In order to obtain
much rate of
processing power
Compromised
blockchain
technology 3 5
1
5
Extere
me
The users
should
practice
29/12/2
018
Security
managers
Planned but not yet
completed
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
3IT RISK MANAGEMENT
g
the attackers are
continuously
moving and
impacting the
confidential
information
safe
browsing
R10 31/12/2018
Malware
threats
It threats
computing
devise through
different virus
such as spyware,
Trojan, worms
and rootkits etc.
The confidentiality
of the
organizations will
be compromised 4 2 8
Moder
ate
Unknown
links and
technical
support
calls
should be
avoided
1/1/201
9
System
administrators Under progress
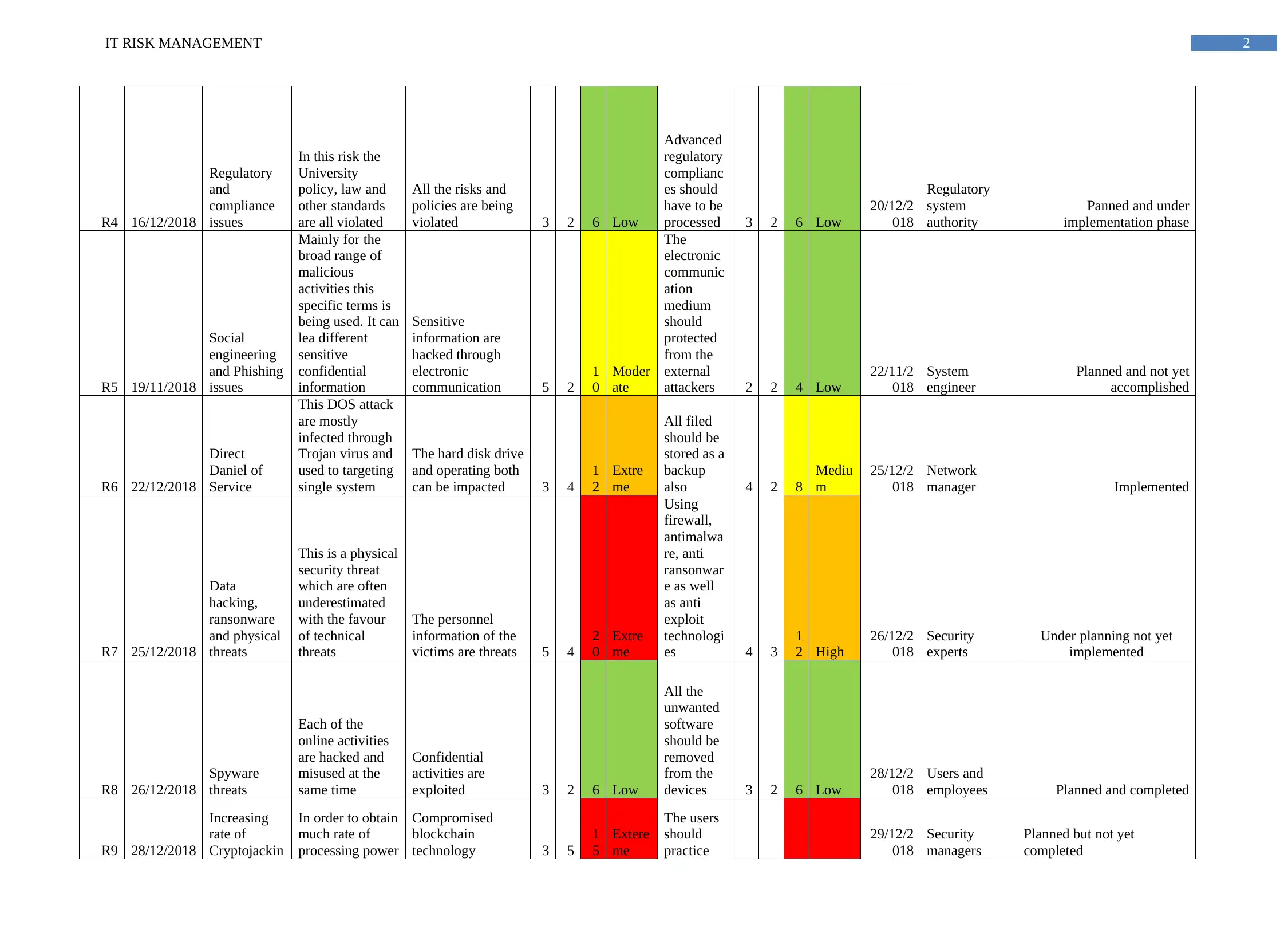
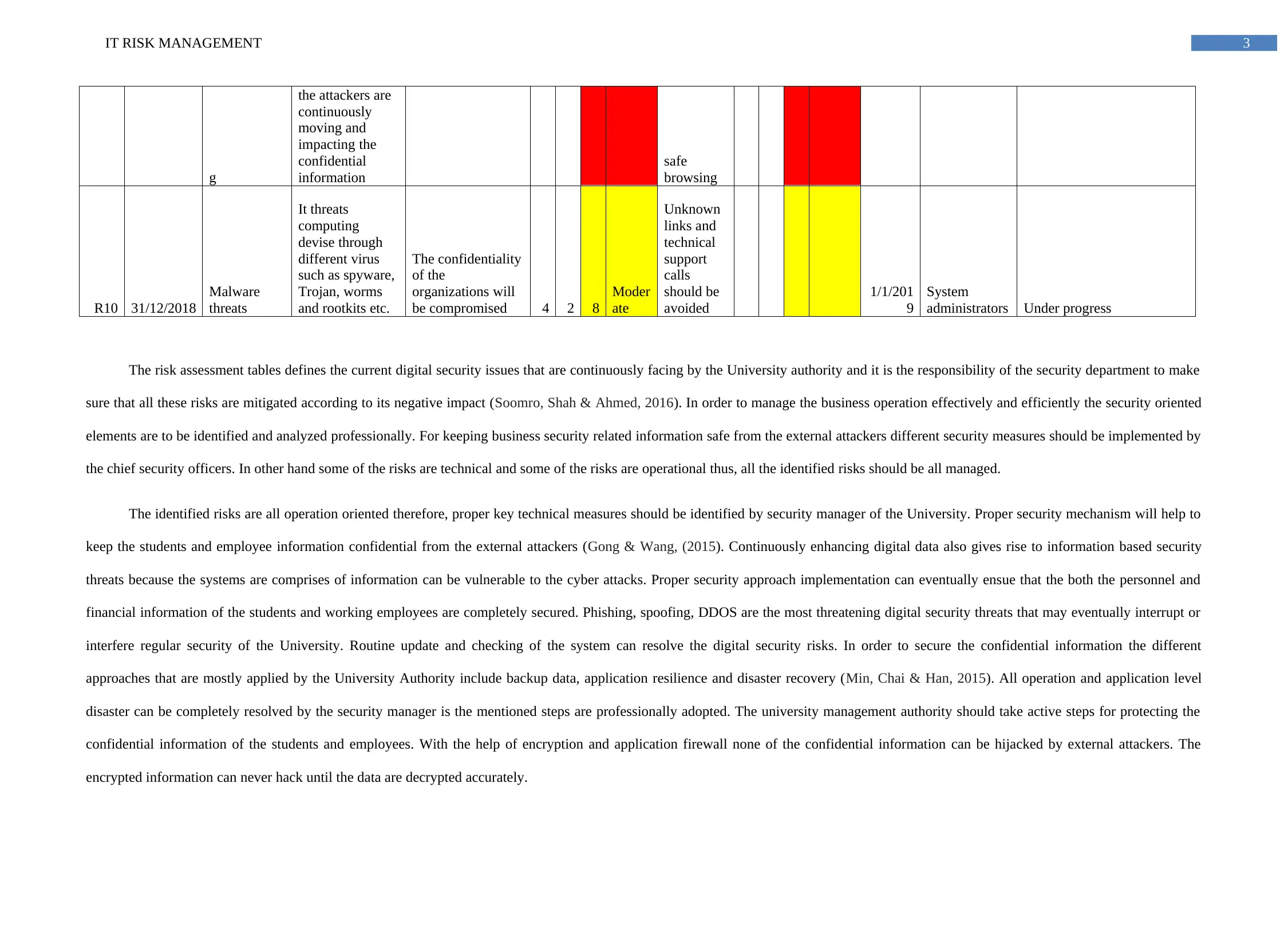
The risk assessment tables defines the current digital security issues that are continuously facing by the University authority and it is the responsibility of the security department to make
sure that all these risks are mitigated according to its negative impact (Soomro, Shah & Ahmed, 2016). In order to manage the business operation effectively and efficiently the security oriented
elements are to be identified and analyzed professionally. For keeping business security related information safe from the external attackers different security measures should be implemented by
the chief security officers. In other hand some of the risks are technical and some of the risks are operational thus, all the identified risks should be all managed.
The identified risks are all operation oriented therefore, proper key technical measures should be identified by security manager of the University. Proper security mechanism will help to
keep the students and employee information confidential from the external attackers (Gong & Wang, (2015). Continuously enhancing digital data also gives rise to information based security
threats because the systems are comprises of information can be vulnerable to the cyber attacks. Proper security approach implementation can eventually ensue that the both the personnel and
financial information of the students and working employees are completely secured. Phishing, spoofing, DDOS are the most threatening digital security threats that may eventually interrupt or
interfere regular security of the University. Routine update and checking of the system can resolve the digital security risks. In order to secure the confidential information the different
approaches that are mostly applied by the University Authority include backup data, application resilience and disaster recovery (Min, Chai & Han, 2015). All operation and application level
disaster can be completely resolved by the security manager is the mentioned steps are professionally adopted. The university management authority should take active steps for protecting the
confidential information of the students and employees. With the help of encryption and application firewall none of the confidential information can be hijacked by external attackers. The
encrypted information can never hack until the data are decrypted accurately.
g
the attackers are
continuously
moving and
impacting the
confidential
information
safe
browsing
R10 31/12/2018
Malware
threats
It threats
computing
devise through
different virus
such as spyware,
Trojan, worms
and rootkits etc.
The confidentiality
of the
organizations will
be compromised 4 2 8
Moder
ate
Unknown
links and
technical
support
calls
should be
avoided
1/1/201
9
System
administrators Under progress
The risk assessment tables defines the current digital security issues that are continuously facing by the University authority and it is the responsibility of the security department to make
sure that all these risks are mitigated according to its negative impact (Soomro, Shah & Ahmed, 2016). In order to manage the business operation effectively and efficiently the security oriented
elements are to be identified and analyzed professionally. For keeping business security related information safe from the external attackers different security measures should be implemented by
the chief security officers. In other hand some of the risks are technical and some of the risks are operational thus, all the identified risks should be all managed.
The identified risks are all operation oriented therefore, proper key technical measures should be identified by security manager of the University. Proper security mechanism will help to
keep the students and employee information confidential from the external attackers (Gong & Wang, (2015). Continuously enhancing digital data also gives rise to information based security
threats because the systems are comprises of information can be vulnerable to the cyber attacks. Proper security approach implementation can eventually ensue that the both the personnel and
financial information of the students and working employees are completely secured. Phishing, spoofing, DDOS are the most threatening digital security threats that may eventually interrupt or
interfere regular security of the University. Routine update and checking of the system can resolve the digital security risks. In order to secure the confidential information the different
approaches that are mostly applied by the University Authority include backup data, application resilience and disaster recovery (Min, Chai & Han, 2015). All operation and application level
disaster can be completely resolved by the security manager is the mentioned steps are professionally adopted. The university management authority should take active steps for protecting the
confidential information of the students and employees. With the help of encryption and application firewall none of the confidential information can be hijacked by external attackers. The
encrypted information can never hack until the data are decrypted accurately.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

3IT RISK MANAGEMENT
Part Two- Option two
2. Recommendation on appointing CISO in Company
2.1 Definition of CISO
For this specific analysis section the organization which is being nominated is
Commonwealth Scientific and Industrial Research Organization (CSIRO). It has been defined
that for appointing any Chief Information Security Officer (CISO) in any organization certain
features of the personnel are measured individually (Safa,Von Solms & Furnell, 2016). The
CISO are the security level experts and they are responsible to take all operational
responsibilities crucial to implement and develop the information security systems in an
organization. It will also help to improve the existing business and operational effectiveness and
efficiency of Commonwealth Scientific and Industrial Research Organization (CSIRO).
Security policy and procedure are the components of information security system which
helps to protect the internal communication direction of the organization (Chang, 2016). The
assets of the organization and both internal and external threats can be completely avoided if
accurate security measures are being adopted by the nominated business organization. Besides
this the role of a Chief Information Officer can also be played by the CISO. In order to procure
products and services the CISO needs to play their assigned role very much professionally. Apart
from this they are also required to pay their pro active attention in disaster recovery, data backup
and application resilience (Kim & Solomon, 2016). Apart from the CIO the CISO also requires
to play the role of security architect, security manager and Corporate Security Officer (CSO).
While CISO plays the roles and responsibilities of overall security systems that time they are
Part Two- Option two
2. Recommendation on appointing CISO in Company
2.1 Definition of CISO
For this specific analysis section the organization which is being nominated is
Commonwealth Scientific and Industrial Research Organization (CSIRO). It has been defined
that for appointing any Chief Information Security Officer (CISO) in any organization certain
features of the personnel are measured individually (Safa,Von Solms & Furnell, 2016). The
CISO are the security level experts and they are responsible to take all operational
responsibilities crucial to implement and develop the information security systems in an
organization. It will also help to improve the existing business and operational effectiveness and
efficiency of Commonwealth Scientific and Industrial Research Organization (CSIRO).
Security policy and procedure are the components of information security system which
helps to protect the internal communication direction of the organization (Chang, 2016). The
assets of the organization and both internal and external threats can be completely avoided if
accurate security measures are being adopted by the nominated business organization. Besides
this the role of a Chief Information Officer can also be played by the CISO. In order to procure
products and services the CISO needs to play their assigned role very much professionally. Apart
from this they are also required to pay their pro active attention in disaster recovery, data backup
and application resilience (Kim & Solomon, 2016). Apart from the CIO the CISO also requires
to play the role of security architect, security manager and Corporate Security Officer (CSO).
While CISO plays the roles and responsibilities of overall security systems that time they are

4IT RISK MANAGEMENT
also assigned as the Chief Information Officer (CIO) of the similar organization. Apart from this
the CISO are also responsible to maintain the physical security of the systems.
As per the changing requirement the responsibilities of the also and CIO can also be
interchanged. The CISO eventually follows the ways through which the data confidentiality as
well as information can be maintained from further disclosure. The data confidentiality and
security of all the information will be kept by the project manager (Kim & Solomon, 2016). The
company CISO must have this much of capacity to handle difficult business situations. They
should use proper business continuity plan for static progress of the business plans. Either highly
technical or operational activities needs to be taken by the CIO are not are measured based on the
situation of the business organization. Each knowledge areas should be individually analyzed
and reported accordingly by the CISO.
2.2 Roles and responsibilities of the CISO
For maintaining the security of Commonwealth Scientific and Industrial Research
Organization (CSIRO), the general roles and responsibilities of a CIO must be followed and the
features that each CIO needs to possess include the below:
Professional writing and communication skills
Accurate knowledge related to legislative and regulatory requirements
Leadership skills
In the field of information security hey must have certain exposure as well as
competencies
Motivating capacities
Strategies that can collectively develop managing capacities
also assigned as the Chief Information Officer (CIO) of the similar organization. Apart from this
the CISO are also responsible to maintain the physical security of the systems.
As per the changing requirement the responsibilities of the also and CIO can also be
interchanged. The CISO eventually follows the ways through which the data confidentiality as
well as information can be maintained from further disclosure. The data confidentiality and
security of all the information will be kept by the project manager (Kim & Solomon, 2016). The
company CISO must have this much of capacity to handle difficult business situations. They
should use proper business continuity plan for static progress of the business plans. Either highly
technical or operational activities needs to be taken by the CIO are not are measured based on the
situation of the business organization. Each knowledge areas should be individually analyzed
and reported accordingly by the CISO.
2.2 Roles and responsibilities of the CISO
For maintaining the security of Commonwealth Scientific and Industrial Research
Organization (CSIRO), the general roles and responsibilities of a CIO must be followed and the
features that each CIO needs to possess include the below:
Professional writing and communication skills
Accurate knowledge related to legislative and regulatory requirements
Leadership skills
In the field of information security hey must have certain exposure as well as
competencies
Motivating capacities
Strategies that can collectively develop managing capacities
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

5IT RISK MANAGEMENT
All the CISOs of Commonwealth Scientific and Industrial Research Organization
(CSIRO) need to work in a collaborative manner to meet strategic project and security
objectives. All the CISO are assigned to their job roles so that instead of resolving the risks make
sure that no risks are being occurring even (Fenz et al., 2014). Before hiring and assigning any
member to these roles it is much important to measure their potential, skills and knowledge. The
CISO of CSIRO should effectively deal with all other security management level executives.
Operational and situational issues can be reduced also by incorporating internal and external
security measures through firewall access and encryption mechanism. The CIO and CISO are
also assigned to plan project policies and information security audit. All of them are required to
assist the information by maintaining them with potential strategies, risk management plan and
improvement planning.
Not only this but also all security experts and CIO of CSIRO must spread security
awareness among working employees so that each individual can take immediate actions for
securing the data and information from getting hacked externally (Hooper & McKissack, 2016).
In other words, the security officers should investigate regarding performance of the security
objectives and metrics. The data privacy is required to be ensured and all maintained. Apart from
this, the project security associates are also required to conduct and investigate on digital
discovery as well as digital forensics.
2.3 Importance of CISO for a startup Business
Not only has the existing operation but also for start up businesses also the CISO played
active role plays. From all the above mentioned general responsibilities it has been evolved that
for the start up businesses also the CISO plays active roles (Karanja & Rosso, 2017). The
operation manager and other associates should take effective initiatives so that the business can
All the CISOs of Commonwealth Scientific and Industrial Research Organization
(CSIRO) need to work in a collaborative manner to meet strategic project and security
objectives. All the CISO are assigned to their job roles so that instead of resolving the risks make
sure that no risks are being occurring even (Fenz et al., 2014). Before hiring and assigning any
member to these roles it is much important to measure their potential, skills and knowledge. The
CISO of CSIRO should effectively deal with all other security management level executives.
Operational and situational issues can be reduced also by incorporating internal and external
security measures through firewall access and encryption mechanism. The CIO and CISO are
also assigned to plan project policies and information security audit. All of them are required to
assist the information by maintaining them with potential strategies, risk management plan and
improvement planning.
Not only this but also all security experts and CIO of CSIRO must spread security
awareness among working employees so that each individual can take immediate actions for
securing the data and information from getting hacked externally (Hooper & McKissack, 2016).
In other words, the security officers should investigate regarding performance of the security
objectives and metrics. The data privacy is required to be ensured and all maintained. Apart from
this, the project security associates are also required to conduct and investigate on digital
discovery as well as digital forensics.
2.3 Importance of CISO for a startup Business
Not only has the existing operation but also for start up businesses also the CISO played
active role plays. From all the above mentioned general responsibilities it has been evolved that
for the start up businesses also the CISO plays active roles (Karanja & Rosso, 2017). The
operation manager and other associates should take effective initiatives so that the business can
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

6IT RISK MANAGEMENT
make strategic moves. It has been determined that CISO role implementation can let the
stakeholders aware about how much curious the business is to maintain its security structures.
In order to align the current business status with business goals and objectives this is very
important to hire a skilled and knowledgeable Chief Information Officer (CIO). Another reason
of hiring a CISO in an organization is to fulfill the business and operational requirements in the
context of current business situation (Cavelty & Mauer, 2016). In order to carry out the business
and functionalities towards success direction this is very important to take effective decision
regarding hiring a CISO so that even wastage of resources including cost and human resources
can be completely avoided.
make strategic moves. It has been determined that CISO role implementation can let the
stakeholders aware about how much curious the business is to maintain its security structures.
In order to align the current business status with business goals and objectives this is very
important to hire a skilled and knowledgeable Chief Information Officer (CIO). Another reason
of hiring a CISO in an organization is to fulfill the business and operational requirements in the
context of current business situation (Cavelty & Mauer, 2016). In order to carry out the business
and functionalities towards success direction this is very important to take effective decision
regarding hiring a CISO so that even wastage of resources including cost and human resources
can be completely avoided.

7IT RISK MANAGEMENT
References
Allen, J. H., Crabb, G., Curtis, P. D., Fitzpatrick, B., Mehravari, N., & Tobar, D.
(2015). Structuring the chief information security officer organization (No. CMU/SEI-
2015-TN-007). CARNEGIE-MELLON UNIV PITTSBURGH PA PITTSBURGH United
States.
Baskerville, R., Spagnoletti, P., & Kim, J. (2014). Incident-centered information security:
Managing a strategic balance between prevention and response. Information &
management, 51(1), 138-151.
Cavelty, M. D., & Mauer, V. (2016). Power and security in the information age: Investigating
the role of the state in cyberspace. Routledge.
Chang, J. F. (2016). Business process management systems: strategy and implementation.
Auerbach Publications.
Collette, R., Gentile, M., & August, T. D. (2016). The CISO Handbook: A Practical Guide to
Securing Your Company. Auerbach Publications.
Fenz, S., Heurix, J., Neubauer, T., & Pechstein, F. (2014). Current challenges in information
security risk management. Information Management & Computer Security, 22(5), 410-
430.
Gong, S., & Wang, Y. (2015, April). Research on Security Strategy of Electronic Commerce
Industry Websites. In International Conference on Advances in Mechanical Enginnering
and Industrial Informatics.
References
Allen, J. H., Crabb, G., Curtis, P. D., Fitzpatrick, B., Mehravari, N., & Tobar, D.
(2015). Structuring the chief information security officer organization (No. CMU/SEI-
2015-TN-007). CARNEGIE-MELLON UNIV PITTSBURGH PA PITTSBURGH United
States.
Baskerville, R., Spagnoletti, P., & Kim, J. (2014). Incident-centered information security:
Managing a strategic balance between prevention and response. Information &
management, 51(1), 138-151.
Cavelty, M. D., & Mauer, V. (2016). Power and security in the information age: Investigating
the role of the state in cyberspace. Routledge.
Chang, J. F. (2016). Business process management systems: strategy and implementation.
Auerbach Publications.
Collette, R., Gentile, M., & August, T. D. (2016). The CISO Handbook: A Practical Guide to
Securing Your Company. Auerbach Publications.
Fenz, S., Heurix, J., Neubauer, T., & Pechstein, F. (2014). Current challenges in information
security risk management. Information Management & Computer Security, 22(5), 410-
430.
Gong, S., & Wang, Y. (2015, April). Research on Security Strategy of Electronic Commerce
Industry Websites. In International Conference on Advances in Mechanical Enginnering
and Industrial Informatics.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

8IT RISK MANAGEMENT
Hooper, V., & McKissack, J. (2016). The emerging role of the CISO. Business Horizons, 59(6),
585-591.
Karanja, E., & Rosso, M. A. (2017). The Chief Information Security Officer: An Exploratory
Study. Journal of International Technology and Information Management, 26(2), 23-47.
Kim, D., & Solomon, M. G. (2016). Fundamentals of information systems security. Jones &
Bartlett Publishers.
Min, K. S., Chai, S. W., & Han, M. (2015). An international comparative study on cyber security
strategy. International Journal of Security and Its Applications, 9(2), 13-20.
Safa, N. S., Von Solms, R., & Furnell, S. (2016). Information security policy compliance model
in organizations. Computers & Security, 56, 70-82.
Soomro, Z. A., Shah, M. H., & Ahmed, J. (2016). Information security management needs more
holistic approach: A literature review. International Journal of Information
Management, 36(2), 215-225.
Tuna, G., Kogias, D. G., Gungor, V. C., Gezer, C., Taşkın, E., & Ayday, E. (2017). A survey on
information security threats and solutions for Machine to Machine (M2M)
communications. Journal of Parallel and Distributed Computing, 109, 142-154.
Hooper, V., & McKissack, J. (2016). The emerging role of the CISO. Business Horizons, 59(6),
585-591.
Karanja, E., & Rosso, M. A. (2017). The Chief Information Security Officer: An Exploratory
Study. Journal of International Technology and Information Management, 26(2), 23-47.
Kim, D., & Solomon, M. G. (2016). Fundamentals of information systems security. Jones &
Bartlett Publishers.
Min, K. S., Chai, S. W., & Han, M. (2015). An international comparative study on cyber security
strategy. International Journal of Security and Its Applications, 9(2), 13-20.
Safa, N. S., Von Solms, R., & Furnell, S. (2016). Information security policy compliance model
in organizations. Computers & Security, 56, 70-82.
Soomro, Z. A., Shah, M. H., & Ahmed, J. (2016). Information security management needs more
holistic approach: A literature review. International Journal of Information
Management, 36(2), 215-225.
Tuna, G., Kogias, D. G., Gungor, V. C., Gezer, C., Taşkın, E., & Ayday, E. (2017). A survey on
information security threats and solutions for Machine to Machine (M2M)
communications. Journal of Parallel and Distributed Computing, 109, 142-154.
1 out of 10
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




