IT Risk Management Report
VerifiedAdded on 2020/03/01
|17
|4057
|40
Report
AI Summary
The report delves into IT risk management, particularly focusing on the security challenges posed by Big Data. It discusses various threats identified by ENISA, including eavesdropping, criminal activities, and legal risks. The report emphasizes the importance of understanding these threats and suggests strategies for mitigating their impact on organizations. It also highlights the need for continuous monitoring and improvement of security measures in the context of evolving cyber threats.

Running Head: IT RISK MANAGEMENT
IT RISK MANAGEMENT
Name of the Student
Name of the University
IT RISK MANAGEMENT
Name of the Student
Name of the University
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1IT RISK MANAGEMENT
Table of Contents
Introduction......................................................................................................................................2
Question 1........................................................................................................................................3
Question 2........................................................................................................................................5
Question 3........................................................................................................................................7
Question 4........................................................................................................................................9
Question 5......................................................................................................................................11
Conclusion.....................................................................................................................................14
References......................................................................................................................................15
Table of Contents
Introduction......................................................................................................................................2
Question 1........................................................................................................................................3
Question 2........................................................................................................................................5
Question 3........................................................................................................................................7
Question 4........................................................................................................................................9
Question 5......................................................................................................................................11
Conclusion.....................................................................................................................................14
References......................................................................................................................................15

2IT RISK MANAGEMENT
Introduction
Huge information frequently shows the assigned stage of calculations, framework
business and innovation that gathers the information of unmatched esteems, assortment and
volume. This extraction is finished by huge measure of investigations that are progressed and can
parallel calculation. The Big Data sources are various and are in vast number. The sight and
sound sensors are circulated more than a few perspectives portable media transmission gadgets,
IoT (Internet of Things), business process conveyance and other online applications. These are
all hopeful information suppliers. With the expansion of Big Data calculations and advances, are
gradually expanding the adequacy in basic leadership in complex groups and association. Yet,
the expansion of advantages there are additionally augmentation of malignant advancements that
makes dangers to the association. ENISA talks about the above issue in this exploration paper
and investigates the parts of both the significance and dangers identified with Big Data. This
examination and its result depend on work area research and audit of gathering papers, articles,
specialized online journals and an assortment of other open wellsprings of data important to Big
Data. This report recognizes the larger part of sources counseled; the points of interest of every
single narrative source counseled amid this examination are accessible on ask.
Introduction
Huge information frequently shows the assigned stage of calculations, framework
business and innovation that gathers the information of unmatched esteems, assortment and
volume. This extraction is finished by huge measure of investigations that are progressed and can
parallel calculation. The Big Data sources are various and are in vast number. The sight and
sound sensors are circulated more than a few perspectives portable media transmission gadgets,
IoT (Internet of Things), business process conveyance and other online applications. These are
all hopeful information suppliers. With the expansion of Big Data calculations and advances, are
gradually expanding the adequacy in basic leadership in complex groups and association. Yet,
the expansion of advantages there are additionally augmentation of malignant advancements that
makes dangers to the association. ENISA talks about the above issue in this exploration paper
and investigates the parts of both the significance and dangers identified with Big Data. This
examination and its result depend on work area research and audit of gathering papers, articles,
specialized online journals and an assortment of other open wellsprings of data important to Big
Data. This report recognizes the larger part of sources counseled; the points of interest of every
single narrative source counseled amid this examination are accessible on ask.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3IT RISK MANAGEMENT
Question 1
Provide a brief overview of the case study and prepare a diagram for the ENISA Big Data
security infrastructure.
By the circumstance examination of ENISA, relating to Big Data there are elaborations
on threats that may occur. There has been exceedingly grabbed balance inside latest couple of
years and thus the data gathering and development of information has been required to expect a
real part on a couple of new perspectives in the overall population (Marinos, 2013). The point of
views that must be made and impacted by the change of information development and Big data
supports the security, prosperity security, surroundings and resources that are capable to
imperativeness, accurately assess the transport system and insightful urban groups. The potential
impact of the Big Data has been perceived by the European Commission by recognizing the
indispensable approach in the Big Data. The data is according to the manner that is conceivable
to the money related drive in the definitive system (Marinos, Belmonte &Rekleitis, 2014).
However, increase in the use of this Big Data advancement has moreover as frequently as
conceivable extended the chances of computerized strikes, data breaks and hacking. In the field
of science and research there is also an enormous impact of the Big Data that continues rising.
Front line and exceptionally novel ICT systems are used as a piece of the approach of Big Data.
The additions of this kind of troubles are both inclining the number in complex and impact. By
increase in the amount of convenience of Big Data in business and affiliations, the aggressors get
spurring powers for making and practices strikes against the examination of Big Data (Fischer
2014). Development has also the ability to be used as a gadget that fights the computerized risks
by offering security and insurance specialists that has vital bits of information in event
Question 1
Provide a brief overview of the case study and prepare a diagram for the ENISA Big Data
security infrastructure.
By the circumstance examination of ENISA, relating to Big Data there are elaborations
on threats that may occur. There has been exceedingly grabbed balance inside latest couple of
years and thus the data gathering and development of information has been required to expect a
real part on a couple of new perspectives in the overall population (Marinos, 2013). The point of
views that must be made and impacted by the change of information development and Big data
supports the security, prosperity security, surroundings and resources that are capable to
imperativeness, accurately assess the transport system and insightful urban groups. The potential
impact of the Big Data has been perceived by the European Commission by recognizing the
indispensable approach in the Big Data. The data is according to the manner that is conceivable
to the money related drive in the definitive system (Marinos, Belmonte &Rekleitis, 2014).
However, increase in the use of this Big Data advancement has moreover as frequently as
conceivable extended the chances of computerized strikes, data breaks and hacking. In the field
of science and research there is also an enormous impact of the Big Data that continues rising.
Front line and exceptionally novel ICT systems are used as a piece of the approach of Big Data.
The additions of this kind of troubles are both inclining the number in complex and impact. By
increase in the amount of convenience of Big Data in business and affiliations, the aggressors get
spurring powers for making and practices strikes against the examination of Big Data (Fischer
2014). Development has also the ability to be used as a gadget that fights the computerized risks
by offering security and insurance specialists that has vital bits of information in event
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4IT RISK MANAGEMENT
organization and perils. Threats Landscapes ENISA passes on scope of this in the field of Big
Data examination, by the commitments from the ENISA Threat Landscape works out. The
relevant examination looks at about the plan, the advantage logical characterization of Big Data,
ENISA peril logical order the concentrated on gathering of spectators of Big Data approach, the
methodology by which the context oriented examination has been done, openings of the
examination in conclusion recommending the approach.
Dispersed figuring is depicted as the establishment layer of Big Data system in ENISA. This may
meet the structure essential like the flexibility, cost-sufficiency and the ability to scale all over
(Marinos, Belmonte &Rekleitis, 2014). The security structure of Big Data system in ENISA
takes after:
Data sources layer: This layer includes spouting data from the sensor, remarkable data
sources, and sorted out information like social database, semi-composed and unstructured
data.
Data storing layer: This data layer is involving considerable grouping of benefits like
RDF stores, NoSQL, scattered record structure and NewSQL database, that are sensible
for broad number of datasets that consistent accumulating.
Integration process layer: the layer stresses with indispensable data having pre-planning
operation getting data along these lines joined the datasets into a sorted out casing.
Presentation layer: This layer enables the portrayal progresses like web programs,
desktop, PDAs and web organizations.
Analytics and figuring model layer: This layer encapsulates particular data contraptions
like the MapReduce that continues running over the advantages that are secured, includes
the model programming and data organization.
organization and perils. Threats Landscapes ENISA passes on scope of this in the field of Big
Data examination, by the commitments from the ENISA Threat Landscape works out. The
relevant examination looks at about the plan, the advantage logical characterization of Big Data,
ENISA peril logical order the concentrated on gathering of spectators of Big Data approach, the
methodology by which the context oriented examination has been done, openings of the
examination in conclusion recommending the approach.
Dispersed figuring is depicted as the establishment layer of Big Data system in ENISA. This may
meet the structure essential like the flexibility, cost-sufficiency and the ability to scale all over
(Marinos, Belmonte &Rekleitis, 2014). The security structure of Big Data system in ENISA
takes after:
Data sources layer: This layer includes spouting data from the sensor, remarkable data
sources, and sorted out information like social database, semi-composed and unstructured
data.
Data storing layer: This data layer is involving considerable grouping of benefits like
RDF stores, NoSQL, scattered record structure and NewSQL database, that are sensible
for broad number of datasets that consistent accumulating.
Integration process layer: the layer stresses with indispensable data having pre-planning
operation getting data along these lines joined the datasets into a sorted out casing.
Presentation layer: This layer enables the portrayal progresses like web programs,
desktop, PDAs and web organizations.
Analytics and figuring model layer: This layer encapsulates particular data contraptions
like the MapReduce that continues running over the advantages that are secured, includes
the model programming and data organization.
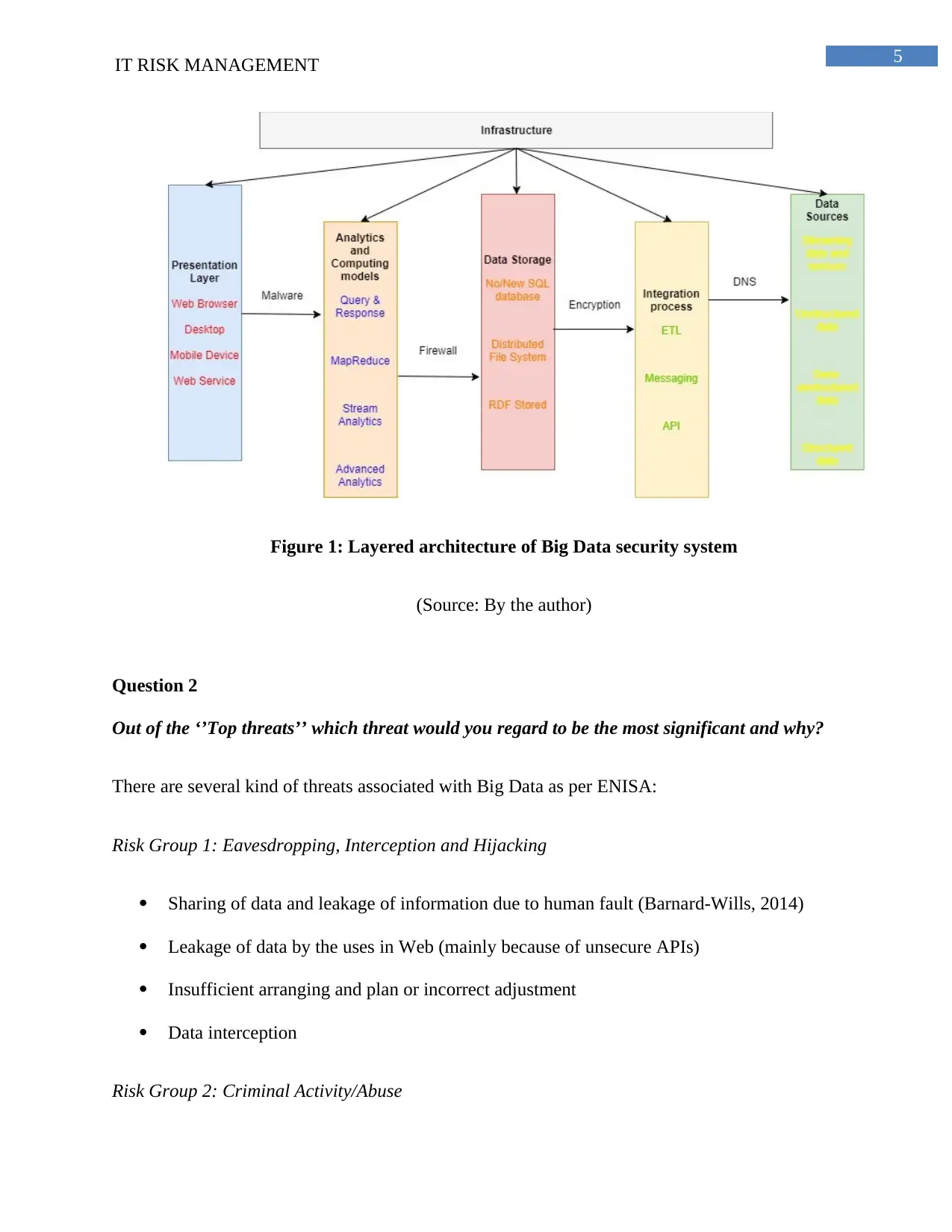
5IT RISK MANAGEMENT
Figure 1: Layered architecture of Big Data security system
(Source: By the author)
Question 2
Out of the ‘’Top threats’’ which threat would you regard to be the most significant and why?
There are several kind of threats associated with Big Data as per ENISA:
Risk Group 1: Eavesdropping, Interception and Hijacking
Sharing of data and leakage of information due to human fault (Barnard-Wills, 2014)
Leakage of data by the uses in Web (mainly because of unsecure APIs)
Insufficient arranging and plan or incorrect adjustment
Data interception
Risk Group 2: Criminal Activity/Abuse
Figure 1: Layered architecture of Big Data security system
(Source: By the author)
Question 2
Out of the ‘’Top threats’’ which threat would you regard to be the most significant and why?
There are several kind of threats associated with Big Data as per ENISA:
Risk Group 1: Eavesdropping, Interception and Hijacking
Sharing of data and leakage of information due to human fault (Barnard-Wills, 2014)
Leakage of data by the uses in Web (mainly because of unsecure APIs)
Insufficient arranging and plan or incorrect adjustment
Data interception
Risk Group 2: Criminal Activity/Abuse
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6IT RISK MANAGEMENT
Extortion of identity
Administration denial
Malicious code/movement or programming
Utilization and generalization of declaration from rebel
Instrumentation misuse /approval of abuse / Unauthorized exercises
Disappointment in the process of business (Lévy-Bencheton et al., 2015)
Risk Group 3: Legal
Enactment breaches/ Individual data abusing/ Directions or law violation
Lacking skills
Concurring the examination of the three threats bundles the most essential hazard is the
"Listening stealthily, Interception and Hijacking", since the most data and security risks are
related to this peril stands up to most prominent inconveniences, like the data ruptures, hacking,
advanced ambush and some more. Impacting the most private and grouped resources of the
association. The rule strikes by this hazard groups are Leakage of Information/sharing on
account of human bungle, Leaks of data by methods for Web applications (unsecure APIs),
lacking blueprint and orchestrating or erroneous modification and Interception of information
(Cho et al., 2016). The dedication of sharp contraptions and PC organize from the incredible
frameworks organization to the Big Data may act assurance concern where a man's region, trade
and other lead are recorded deliberately. This threat expert is adversarial in nature. Their goal is
basically money related advantage having higher capacity level. Cybercriminals can be dealt
with on an area, national or even overall level (Scott et al., 2016). These authorities are socially
and politically motivated individuals using the framework or the PC system for testing and
Extortion of identity
Administration denial
Malicious code/movement or programming
Utilization and generalization of declaration from rebel
Instrumentation misuse /approval of abuse / Unauthorized exercises
Disappointment in the process of business (Lévy-Bencheton et al., 2015)
Risk Group 3: Legal
Enactment breaches/ Individual data abusing/ Directions or law violation
Lacking skills
Concurring the examination of the three threats bundles the most essential hazard is the
"Listening stealthily, Interception and Hijacking", since the most data and security risks are
related to this peril stands up to most prominent inconveniences, like the data ruptures, hacking,
advanced ambush and some more. Impacting the most private and grouped resources of the
association. The rule strikes by this hazard groups are Leakage of Information/sharing on
account of human bungle, Leaks of data by methods for Web applications (unsecure APIs),
lacking blueprint and orchestrating or erroneous modification and Interception of information
(Cho et al., 2016). The dedication of sharp contraptions and PC organize from the incredible
frameworks organization to the Big Data may act assurance concern where a man's region, trade
and other lead are recorded deliberately. This threat expert is adversarial in nature. Their goal is
basically money related advantage having higher capacity level. Cybercriminals can be dealt
with on an area, national or even overall level (Scott et al., 2016). These authorities are socially
and politically motivated individuals using the framework or the PC system for testing and
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7IT RISK MANAGEMENT
propelling purposes behind the mischief. Noticeable destinations are generally being engaged
nearby information associations and military foundations (Wang, Anokhin & Anderl, 2017).
Question 3
Identify and discuss the key Threat Agents. What could be done to minimize their impact on
the system? Based on the data provided, discuss the trends in threat probability.
As per the ENISA threat Landscape, the risk are depicted as “something or someone
having better capacity, and reasonable aims may show the risks associated and records past
exercise in such manner” (Barnard-Wills, Marinos & Portesi, 2014). The organization utilizes
Big Data applications must have knowledge about the threats that may rise and from which
brunch of risk that may occur. Classifications are made by which the threats operators have been
isolated in:
Organizational: This arrangement suggests the endeavors or affiliations that may attract
or change any systems that may be innovative and antagonistic to the wander. These are
the undermining hazard administrators having the perspective to amass high ground over
the contenders (Brender & Markov, 2013). The relationship generally sorts their
guideline targets and focusing over the size and sections the endeavors have capacities to
the district of vitality, and from the region of imaginative point of view to human
building knowledge in the field of dominance.
Cyber Criminals: This hazard administrator is undermining in nature. Their goal is
basically financial benefit having higher fitness level. Cybercriminals can be dealt with
on an adjacent, national or even overall level (Le Bray, Mayer & Aubert, 2016).
propelling purposes behind the mischief. Noticeable destinations are generally being engaged
nearby information associations and military foundations (Wang, Anokhin & Anderl, 2017).
Question 3
Identify and discuss the key Threat Agents. What could be done to minimize their impact on
the system? Based on the data provided, discuss the trends in threat probability.
As per the ENISA threat Landscape, the risk are depicted as “something or someone
having better capacity, and reasonable aims may show the risks associated and records past
exercise in such manner” (Barnard-Wills, Marinos & Portesi, 2014). The organization utilizes
Big Data applications must have knowledge about the threats that may rise and from which
brunch of risk that may occur. Classifications are made by which the threats operators have been
isolated in:
Organizational: This arrangement suggests the endeavors or affiliations that may attract
or change any systems that may be innovative and antagonistic to the wander. These are
the undermining hazard administrators having the perspective to amass high ground over
the contenders (Brender & Markov, 2013). The relationship generally sorts their
guideline targets and focusing over the size and sections the endeavors have capacities to
the district of vitality, and from the region of imaginative point of view to human
building knowledge in the field of dominance.
Cyber Criminals: This hazard administrator is undermining in nature. Their goal is
basically financial benefit having higher fitness level. Cybercriminals can be dealt with
on an adjacent, national or even overall level (Le Bray, Mayer & Aubert, 2016).

8IT RISK MANAGEMENT
Advanced mental oppressors: The motivation of this hazard administrator can either be
religious or political, that expands the development participating in computerized attacks.
The targets that are supported by the computerized mental oppressors are on a very basic
level completed fundamental structure like in media transmission, imperativeness era or
open human administrations system (Olesen, 2016).
Content kiddies: These experts use the substance and the tasks made since these are
generally bumbling, that strikes the framework or the PC structures and also destinations.
Online social software engineers (hacktivists): These masters are socially and politically
propelled individuals using the framework or the PC system for disagreeing and
propelling explanations behind the damage. Noticeable destinations are generally being
engaged close by knowledge associations and military foundations (Bugeja, Jacobsson &
Davidsson, 2017).
Agents: Sometime the laborers for the breaking down of the association get to the
association's advantages from inside and therefore hostile and non-adversarial authorities
there are both considered as delegrate. This administrator fuses staffs, operational staffs,
transitory laborers or security guards of the association (Belmonte Martin et al., 2015). A
considerable measure of data is required for this kind of risks, which causes them in
setting the suitable strike against the upsides of the association.
Nation communicates: these administrators generally have antagonistic capacities in
computerized security and may use it over an attempt.
Question 4
How could the ETL process be improved? Discuss.
Advanced mental oppressors: The motivation of this hazard administrator can either be
religious or political, that expands the development participating in computerized attacks.
The targets that are supported by the computerized mental oppressors are on a very basic
level completed fundamental structure like in media transmission, imperativeness era or
open human administrations system (Olesen, 2016).
Content kiddies: These experts use the substance and the tasks made since these are
generally bumbling, that strikes the framework or the PC structures and also destinations.
Online social software engineers (hacktivists): These masters are socially and politically
propelled individuals using the framework or the PC system for disagreeing and
propelling explanations behind the damage. Noticeable destinations are generally being
engaged close by knowledge associations and military foundations (Bugeja, Jacobsson &
Davidsson, 2017).
Agents: Sometime the laborers for the breaking down of the association get to the
association's advantages from inside and therefore hostile and non-adversarial authorities
there are both considered as delegrate. This administrator fuses staffs, operational staffs,
transitory laborers or security guards of the association (Belmonte Martin et al., 2015). A
considerable measure of data is required for this kind of risks, which causes them in
setting the suitable strike against the upsides of the association.
Nation communicates: these administrators generally have antagonistic capacities in
computerized security and may use it over an attempt.
Question 4
How could the ETL process be improved? Discuss.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9IT RISK MANAGEMENT
The risks logical classification as made by the ENISA Threat Landscape (ETL) Group
and this joins perils that are apropos for the upsides of the Big Data and these can be improves
by the going with ways:
Tackling Bottlenecks: Creating question, for example, time, number of records
orchestrated and use of equipment. Checking what number of focal points each piece of
the philosophy takes and address the heaviest one (Rhee et al., 2013). Building realities
and estimations in the arranging condition. Wherever your bottleneck might be, take a
full breath and jump into the code. The power is in all likelihood going to be with the
clients embraced.
Load Data Incrementally: Changes stacked inside the old and new information that extras
exceedingly arrangements of the present time. It is much hard to execute and
consequently clutch the schedule, not relying upon the bother. In this manner the
increased stacking can execute the ETL upgrade though these are been sorted out with
add up to loads.
Partition significant tables: The utilization of broad social database that may upgrade the
data taking care of windows can be allocated tremendous tables. Means slash huge tables
that are physically littler fundamentally by the date of execution. Each bundle has its own
records and the documents tree is shallower accordingly considering snappier access to
the data. It in like manner helps in trading the information inside a table smart Meta data
operation instead of genuine expansion or eradication of information records.
Cut out coincidental data: The social occasion of data however much as could sensibly
be normal is basic, may be only one out of every odd one of the data yet rather it is select
praiseworthy to enter the server farm conveyance. In case: BI agents pointless by the
The risks logical classification as made by the ENISA Threat Landscape (ETL) Group
and this joins perils that are apropos for the upsides of the Big Data and these can be improves
by the going with ways:
Tackling Bottlenecks: Creating question, for example, time, number of records
orchestrated and use of equipment. Checking what number of focal points each piece of
the philosophy takes and address the heaviest one (Rhee et al., 2013). Building realities
and estimations in the arranging condition. Wherever your bottleneck might be, take a
full breath and jump into the code. The power is in all likelihood going to be with the
clients embraced.
Load Data Incrementally: Changes stacked inside the old and new information that extras
exceedingly arrangements of the present time. It is much hard to execute and
consequently clutch the schedule, not relying upon the bother. In this manner the
increased stacking can execute the ETL upgrade though these are been sorted out with
add up to loads.
Partition significant tables: The utilization of broad social database that may upgrade the
data taking care of windows can be allocated tremendous tables. Means slash huge tables
that are physically littler fundamentally by the date of execution. Each bundle has its own
records and the documents tree is shallower accordingly considering snappier access to
the data. It in like manner helps in trading the information inside a table smart Meta data
operation instead of genuine expansion or eradication of information records.
Cut out coincidental data: The social occasion of data however much as could sensibly
be normal is basic, may be only one out of every odd one of the data yet rather it is select
praiseworthy to enter the server farm conveyance. In case: BI agents pointless by the
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10IT RISK MANAGEMENT
furniture model's photo. The main thing that should be changed in the improvement of
the ETL execution, sitting down and nature definitely that the data must be arranged and
left unessential sections/lines out. It is a decent arrangement to start little and create with
the development instead of making a nonsensical arrangement that may take ages to get
execute.
Cache the data: It is plausible for the save data to quicken fundamentally since get to
memory performs speedier than the hard drives. It is to be noticed that putting away is
compelled by the most preposterous measure of memory your apparatus bolster, so it is
difficult to fit every one of the plastics information.
Process in parallel: Other than serial planning, change of benefits is basic by parallel
alteration the entire time. These techniques can scale up by updating the CPU, yet simply
up to an obliged part. There can be better courses of action too.
Use Hadoop: Apache Hadoop writing computer programs is an open source library
including programming organization that allows the scattering method of significant
game plans of data over the groups of PCs by using clear program models. It has been
proposed that scales up from one-to-various machines that is, from single server to
various distinctive machines and even servers storing and estimation (Skopik, Settanni &
Fiedler, 2016).
Question 5
To sum up, should ENISA be satisfied with its current state of IT Security? Why? Or Why
not?
As indicated by the ENISA Big Data there are few concentrates on the security structure:
furniture model's photo. The main thing that should be changed in the improvement of
the ETL execution, sitting down and nature definitely that the data must be arranged and
left unessential sections/lines out. It is a decent arrangement to start little and create with
the development instead of making a nonsensical arrangement that may take ages to get
execute.
Cache the data: It is plausible for the save data to quicken fundamentally since get to
memory performs speedier than the hard drives. It is to be noticed that putting away is
compelled by the most preposterous measure of memory your apparatus bolster, so it is
difficult to fit every one of the plastics information.
Process in parallel: Other than serial planning, change of benefits is basic by parallel
alteration the entire time. These techniques can scale up by updating the CPU, yet simply
up to an obliged part. There can be better courses of action too.
Use Hadoop: Apache Hadoop writing computer programs is an open source library
including programming organization that allows the scattering method of significant
game plans of data over the groups of PCs by using clear program models. It has been
proposed that scales up from one-to-various machines that is, from single server to
various distinctive machines and even servers storing and estimation (Skopik, Settanni &
Fiedler, 2016).
Question 5
To sum up, should ENISA be satisfied with its current state of IT Security? Why? Or Why
not?
As indicated by the ENISA Big Data there are few concentrates on the security structure:

11IT RISK MANAGEMENT
For the application level to the framework tradition the trusted sections may constantly be
used as a piece of all levels of the information structure, which are by and large in
perspective of the key organization and the most grounded methodology to encode
(Karchefsky & Rao, 2017). A bit of the instances of this trusted establishment are secure
correspondence traditions, approval structure open key establishment parts and some
more.
It is major for the relationship to assert a place stock in establishment, to such a degree, to
the point that to amass the information security on the commence of the wellbeing
exertion at each level and thusly giving the approval structures and assistants with trust in
worth trades, affiliation and electronic imprints.
As the ENISA elucidated, there would be an extraordinary potential impact on increase in
the gathering of data in appropriated registering for the developers, since there is
constantly a probability for abuse of private and individual information. The
computerized guilty parties routinely store malwares in the framework system or may use
the phase to dispatch an attack for their own advantage.
As a creating security issue immense data is on the most noteworthy need on the
rundown as a comprehensively spreading result of dispersed figuring, social
developments and other web enrollments. This has transformed into an as of late creating
security issue.
The data assurance is generally affected by mishandling this colossal data by unapproved
customers. In any case, if there ought to be an event of promotion, tremendous data
manhandle may welcome new sorts of strike vectors.
For the application level to the framework tradition the trusted sections may constantly be
used as a piece of all levels of the information structure, which are by and large in
perspective of the key organization and the most grounded methodology to encode
(Karchefsky & Rao, 2017). A bit of the instances of this trusted establishment are secure
correspondence traditions, approval structure open key establishment parts and some
more.
It is major for the relationship to assert a place stock in establishment, to such a degree, to
the point that to amass the information security on the commence of the wellbeing
exertion at each level and thusly giving the approval structures and assistants with trust in
worth trades, affiliation and electronic imprints.
As the ENISA elucidated, there would be an extraordinary potential impact on increase in
the gathering of data in appropriated registering for the developers, since there is
constantly a probability for abuse of private and individual information. The
computerized guilty parties routinely store malwares in the framework system or may use
the phase to dispatch an attack for their own advantage.
As a creating security issue immense data is on the most noteworthy need on the
rundown as a comprehensively spreading result of dispersed figuring, social
developments and other web enrollments. This has transformed into an as of late creating
security issue.
The data assurance is generally affected by mishandling this colossal data by unapproved
customers. In any case, if there ought to be an event of promotion, tremendous data
manhandle may welcome new sorts of strike vectors.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 17
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.



