IT Risk Management Report: Risk Assessment for Regional Gardens Ltd
VerifiedAdded on 2022/09/05
|10
|1007
|19
Report
AI Summary
This report, prepared for Regional Gardens Ltd, presents a comprehensive IT risk management analysis. As the newly appointed Chief Information Officer, the student identifies critical risks within the organization, including issues with the administration system, data storage, lack of security, absence of antivirus software, inadequate password policies, and deficient backup/recovery systems. The report details the impact of each risk, proposes mitigation strategies, and assesses both inherent and residual risks. A risk register is provided, outlining each risk's description, impact, likelihood, priority, and mitigation strategies. Prioritization of risks is performed using a standardized framework. The report emphasizes the importance of implementing robust security measures, proper system monitoring, and data protection protocols to safeguard the organization's assets and ensure business continuity. The analysis is based on a case study of Regional Gardens, focusing on their operational and technological vulnerabilities. The student also provides a bibliography of relevant sources.

0Risks identifiedRisks identified
IT RISK MANAGEMENT- Regional gardens
Name of the Student
Name of the University
Author Note
IT RISK MANAGEMENT- Regional gardens
Name of the Student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

IT RISK MANAGEMENT
Table of Contents
Risks identified................................................................................................................................2
Summary of the impact....................................................................................................................2
Mitigation of risks............................................................................................................................3
Residual risk assessment..................................................................................................................3
Prioritization....................................................................................................................................8
Bibliography....................................................................................................................................9
Table of Contents
Risks identified................................................................................................................................2
Summary of the impact....................................................................................................................2
Mitigation of risks............................................................................................................................3
Residual risk assessment..................................................................................................................3
Prioritization....................................................................................................................................8
Bibliography....................................................................................................................................9

IT RISK MANAGEMENT
Risks identified
The regional gardens ltd is an organization that aims at running a huge number of related
gardening enterprises. The company also owns their regional gardens nursery that sells plants
and garden towards the public. However the organization is facing serious challenges with
managing the services and the staffs that are associated with the organization.
R1- The key risks that are identified within the organization are that the administration
system within the organization is haphazard.
R2- the Company faces serious issues with storage as disks gets fill up regularly. The
company lacks in having proper monitoring system.
R3- the Company does not have any proper firewall or security system. This makes the
system of the organization vulnerable towards the hackers.
R4- The system within the organization does not have any proper anti-virus.
R5- The lacks backup or disaster recovery systems.
R6- The organization does not have any rules for setting passwords for protecting the
personal computer and this sometimes gives access towards the hackers.
Summary of the impact
The risks that are identified within the organization are large in number and thus there is
a need to ensure that the risks have been identified successfully so that the impacts can be
reduced. The organization lacks proper system monitoring and accountability system that
hampers the performance. Thus there is a need to ensure that proper system has been included
within the organization that will be capable of protecting the data from attackers.
Risks identified
The regional gardens ltd is an organization that aims at running a huge number of related
gardening enterprises. The company also owns their regional gardens nursery that sells plants
and garden towards the public. However the organization is facing serious challenges with
managing the services and the staffs that are associated with the organization.
R1- The key risks that are identified within the organization are that the administration
system within the organization is haphazard.
R2- the Company faces serious issues with storage as disks gets fill up regularly. The
company lacks in having proper monitoring system.
R3- the Company does not have any proper firewall or security system. This makes the
system of the organization vulnerable towards the hackers.
R4- The system within the organization does not have any proper anti-virus.
R5- The lacks backup or disaster recovery systems.
R6- The organization does not have any rules for setting passwords for protecting the
personal computer and this sometimes gives access towards the hackers.
Summary of the impact
The risks that are identified within the organization are large in number and thus there is
a need to ensure that the risks have been identified successfully so that the impacts can be
reduced. The organization lacks proper system monitoring and accountability system that
hampers the performance. Thus there is a need to ensure that proper system has been included
within the organization that will be capable of protecting the data from attackers.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
IT RISK MANAGEMENT
Mitigation of risks
Risk mitigation within the organization is essential as this helps in protecting the system
from unwanted attackers. The organization needs to implement proper administration system that
will help in identifying the activities that are carried out within the system. The personal
computer needs to be protected and encrypted with proper strong passwords so that it can ensure
that data are protected. Anti-virus needs to be installed within the system so that the data and
system can be protected from attackers.
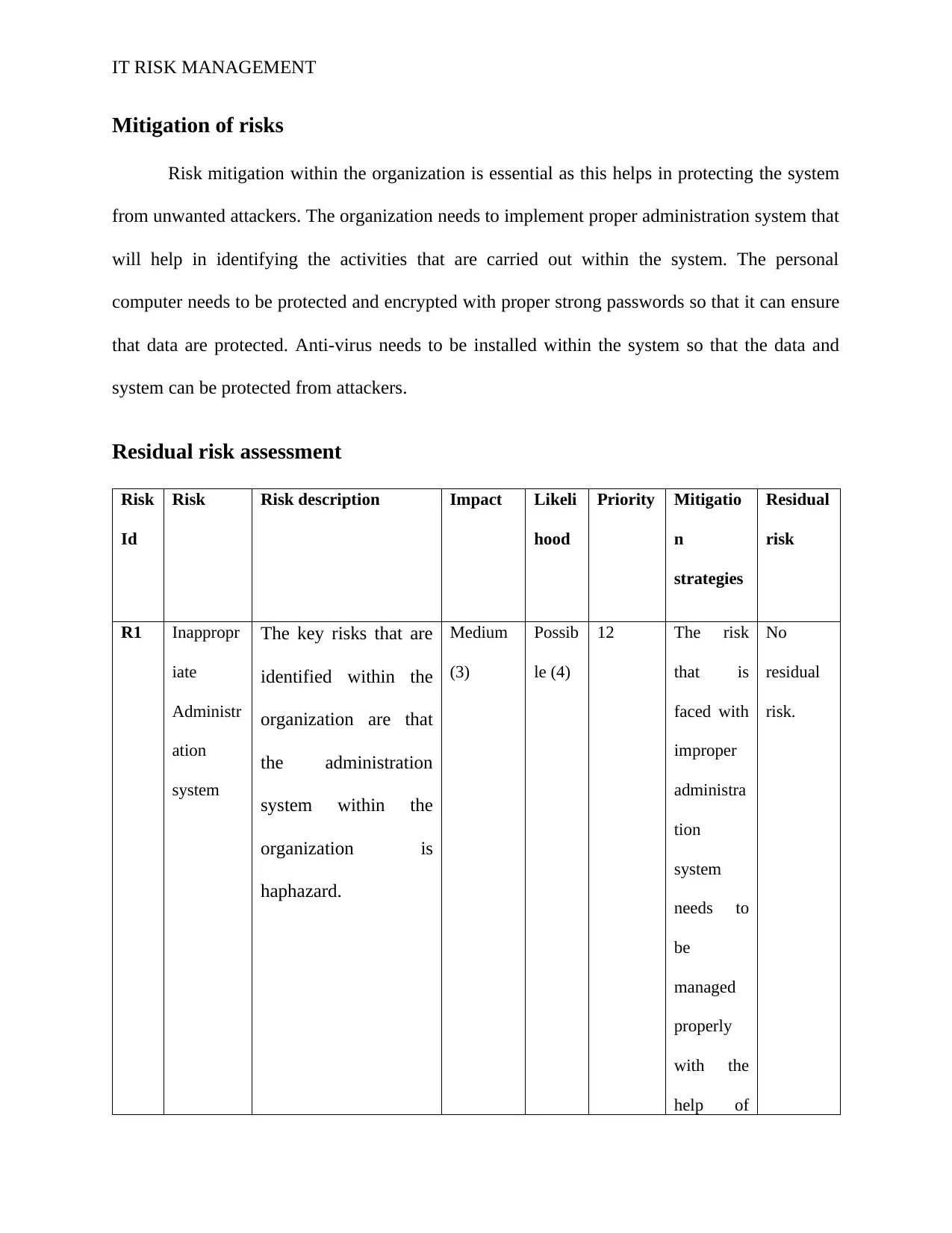
Residual risk assessment
Risk
Id
Risk Risk description Impact Likeli
hood
Priority Mitigatio
n
strategies
Residual
risk
R1 Inappropr
iate
Administr
ation
system
The key risks that are
identified within the
organization are that
the administration
system within the
organization is
haphazard.
Medium
(3)
Possib
le (4)
12 The risk
that is
faced with
improper
administra
tion
system
needs to
be
managed
properly
with the
help of
No
residual
risk.
Mitigation of risks
Risk mitigation within the organization is essential as this helps in protecting the system
from unwanted attackers. The organization needs to implement proper administration system that
will help in identifying the activities that are carried out within the system. The personal
computer needs to be protected and encrypted with proper strong passwords so that it can ensure
that data are protected. Anti-virus needs to be installed within the system so that the data and
system can be protected from attackers.
Residual risk assessment
Risk
Id
Risk Risk description Impact Likeli
hood
Priority Mitigatio
n
strategies
Residual
risk
R1 Inappropr
iate
Administr
ation
system
The key risks that are
identified within the
organization are that
the administration
system within the
organization is
haphazard.
Medium
(3)
Possib
le (4)
12 The risk
that is
faced with
improper
administra
tion
system
needs to
be
managed
properly
with the
help of
No
residual
risk.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
IT RISK MANAGEMENT
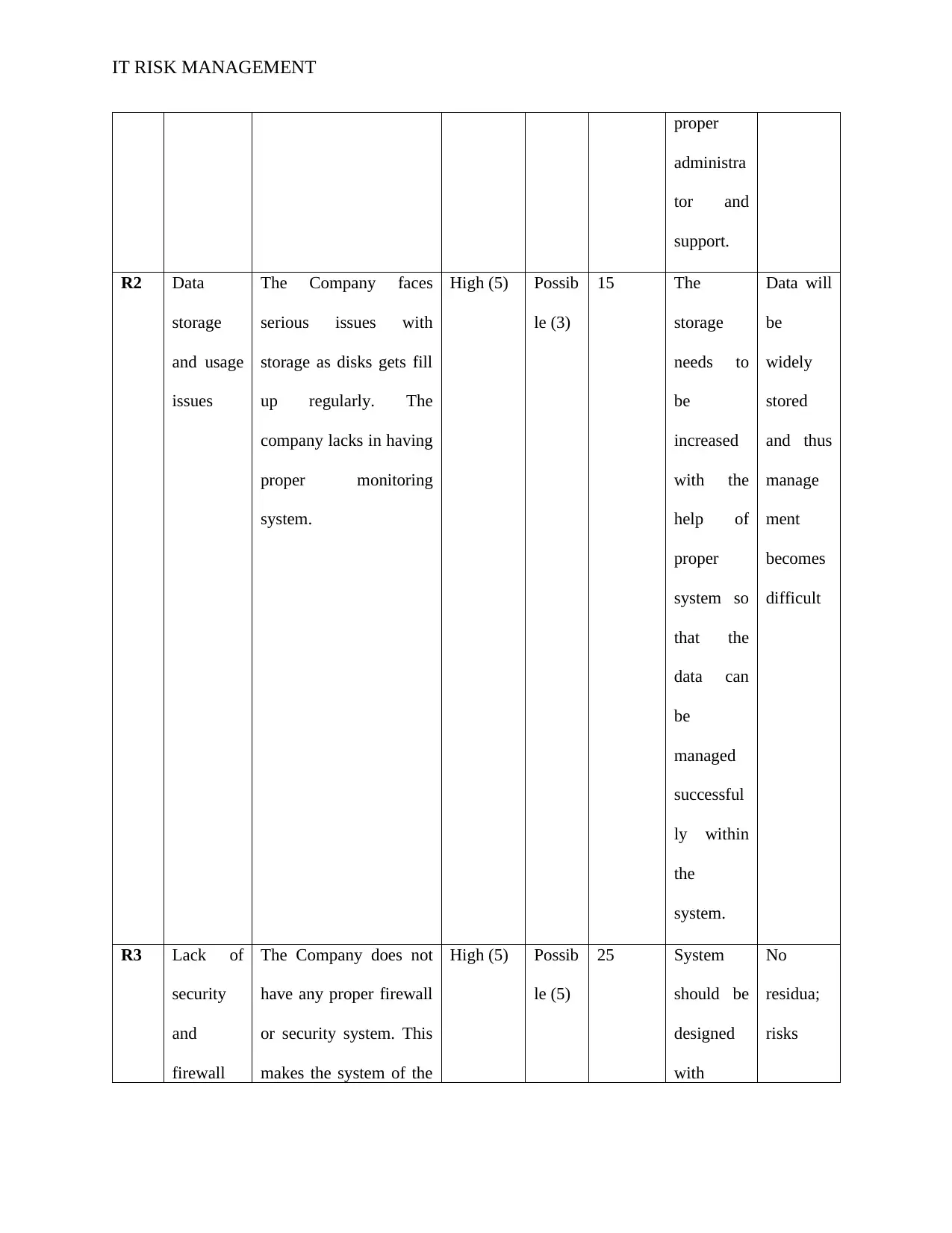
proper
administra
tor and
support.
R2 Data
storage
and usage
issues
The Company faces
serious issues with
storage as disks gets fill
up regularly. The
company lacks in having
proper monitoring
system.
High (5) Possib
le (3)
15 The
storage
needs to
be
increased
with the
help of
proper
system so
that the
data can
be
managed
successful
ly within
the
system.
Data will
be
widely
stored
and thus
manage
ment
becomes
difficult
R3 Lack of
security
and
firewall
The Company does not
have any proper firewall
or security system. This
makes the system of the
High (5) Possib
le (5)
25 System
should be
designed
with
No
residua;
risks
proper
administra
tor and
support.
R2 Data
storage
and usage
issues
The Company faces
serious issues with
storage as disks gets fill
up regularly. The
company lacks in having
proper monitoring
system.
High (5) Possib
le (3)
15 The
storage
needs to
be
increased
with the
help of
proper
system so
that the
data can
be
managed
successful
ly within
the
system.
Data will
be
widely
stored
and thus
manage
ment
becomes
difficult
R3 Lack of
security
and
firewall
The Company does not
have any proper firewall
or security system. This
makes the system of the
High (5) Possib
le (5)
25 System
should be
designed
with
No
residua;
risks
IT RISK MANAGEMENT
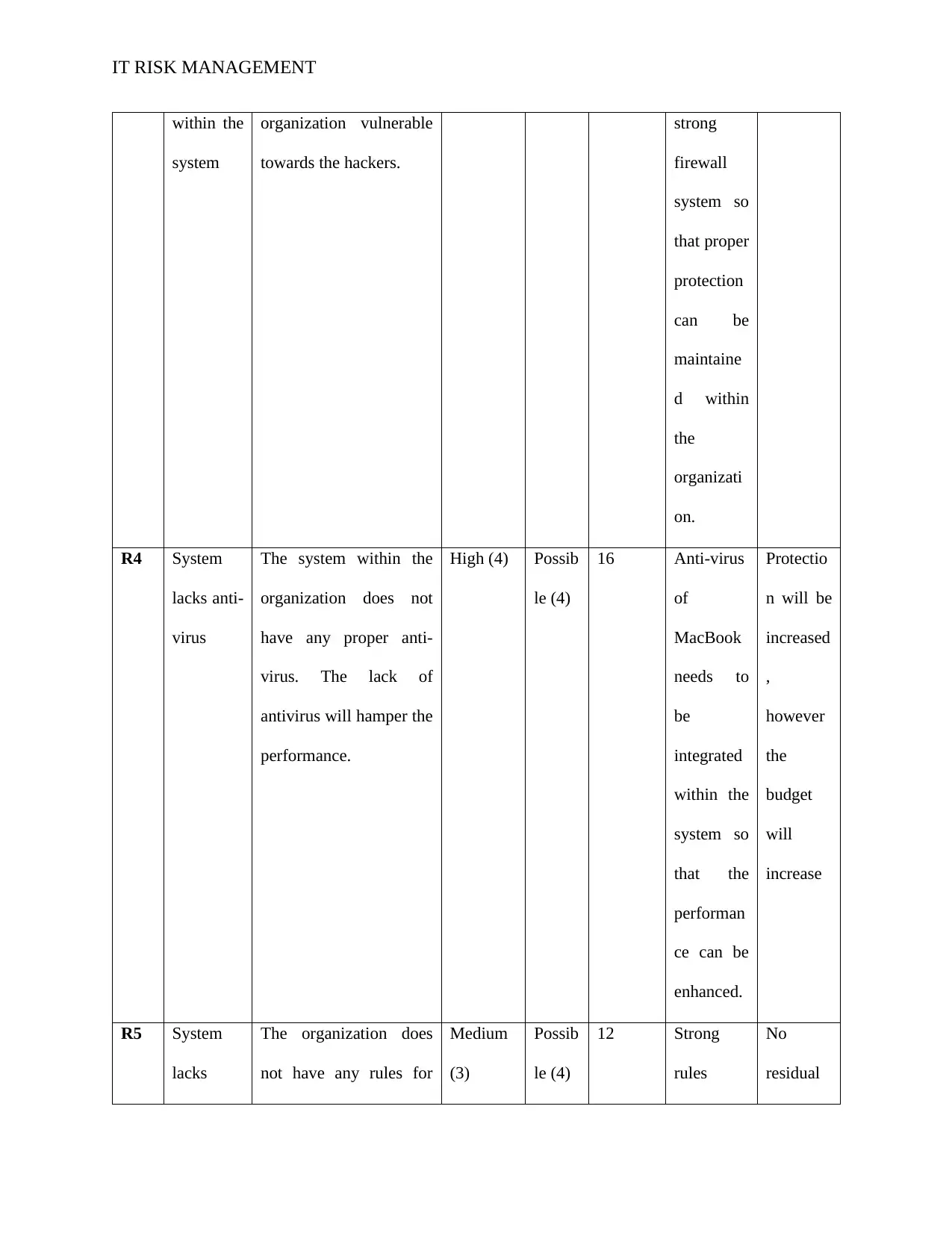
within the
system
organization vulnerable
towards the hackers.
strong
firewall
system so
that proper
protection
can be
maintaine
d within
the
organizati
on.
R4 System
lacks anti-
virus
The system within the
organization does not
have any proper anti-
virus. The lack of
antivirus will hamper the
performance.
High (4) Possib
le (4)
16 Anti-virus
of
MacBook
needs to
be
integrated
within the
system so
that the
performan
ce can be
enhanced.
Protectio
n will be
increased
,
however
the
budget
will
increase
R5 System
lacks
The organization does
not have any rules for
Medium
(3)
Possib
le (4)
12 Strong
rules
No
residual
within the
system
organization vulnerable
towards the hackers.
strong
firewall
system so
that proper
protection
can be
maintaine
d within
the
organizati
on.
R4 System
lacks anti-
virus
The system within the
organization does not
have any proper anti-
virus. The lack of
antivirus will hamper the
performance.
High (4) Possib
le (4)
16 Anti-virus
of
MacBook
needs to
be
integrated
within the
system so
that the
performan
ce can be
enhanced.
Protectio
n will be
increased
,
however
the
budget
will
increase
R5 System
lacks
The organization does
not have any rules for
Medium
(3)
Possib
le (4)
12 Strong
rules
No
residual
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
IT RISK MANAGEMENT
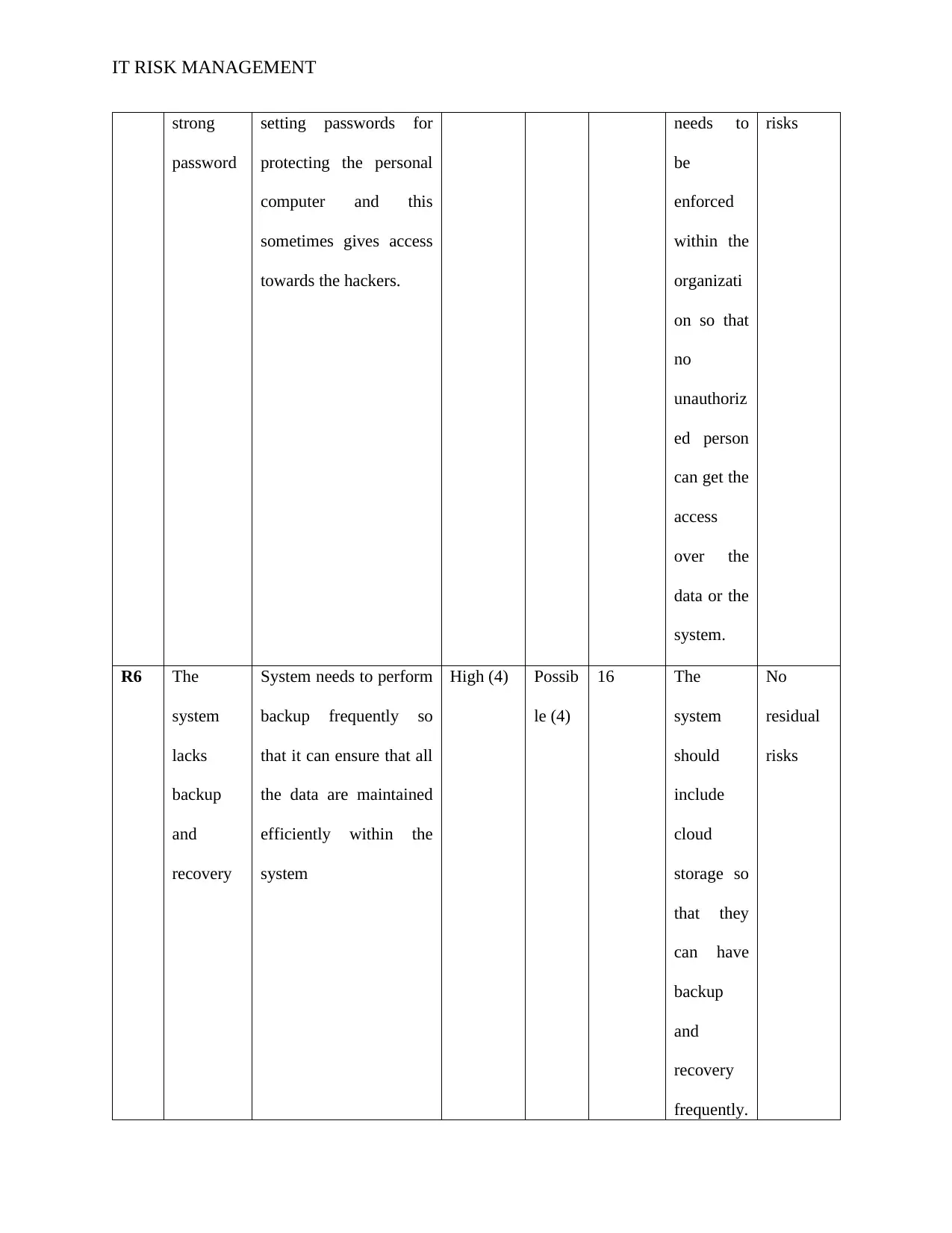
strong
password
setting passwords for
protecting the personal
computer and this
sometimes gives access
towards the hackers.
needs to
be
enforced
within the
organizati
on so that
no
unauthoriz
ed person
can get the
access
over the
data or the
system.
risks
R6 The
system
lacks
backup
and
recovery
System needs to perform
backup frequently so
that it can ensure that all
the data are maintained
efficiently within the
system
High (4) Possib
le (4)
16 The
system
should
include
cloud
storage so
that they
can have
backup
and
recovery
frequently.
No
residual
risks
strong
password
setting passwords for
protecting the personal
computer and this
sometimes gives access
towards the hackers.
needs to
be
enforced
within the
organizati
on so that
no
unauthoriz
ed person
can get the
access
over the
data or the
system.
risks
R6 The
system
lacks
backup
and
recovery
System needs to perform
backup frequently so
that it can ensure that all
the data are maintained
efficiently within the
system
High (4) Possib
le (4)
16 The
system
should
include
cloud
storage so
that they
can have
backup
and
recovery
frequently.
No
residual
risks
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
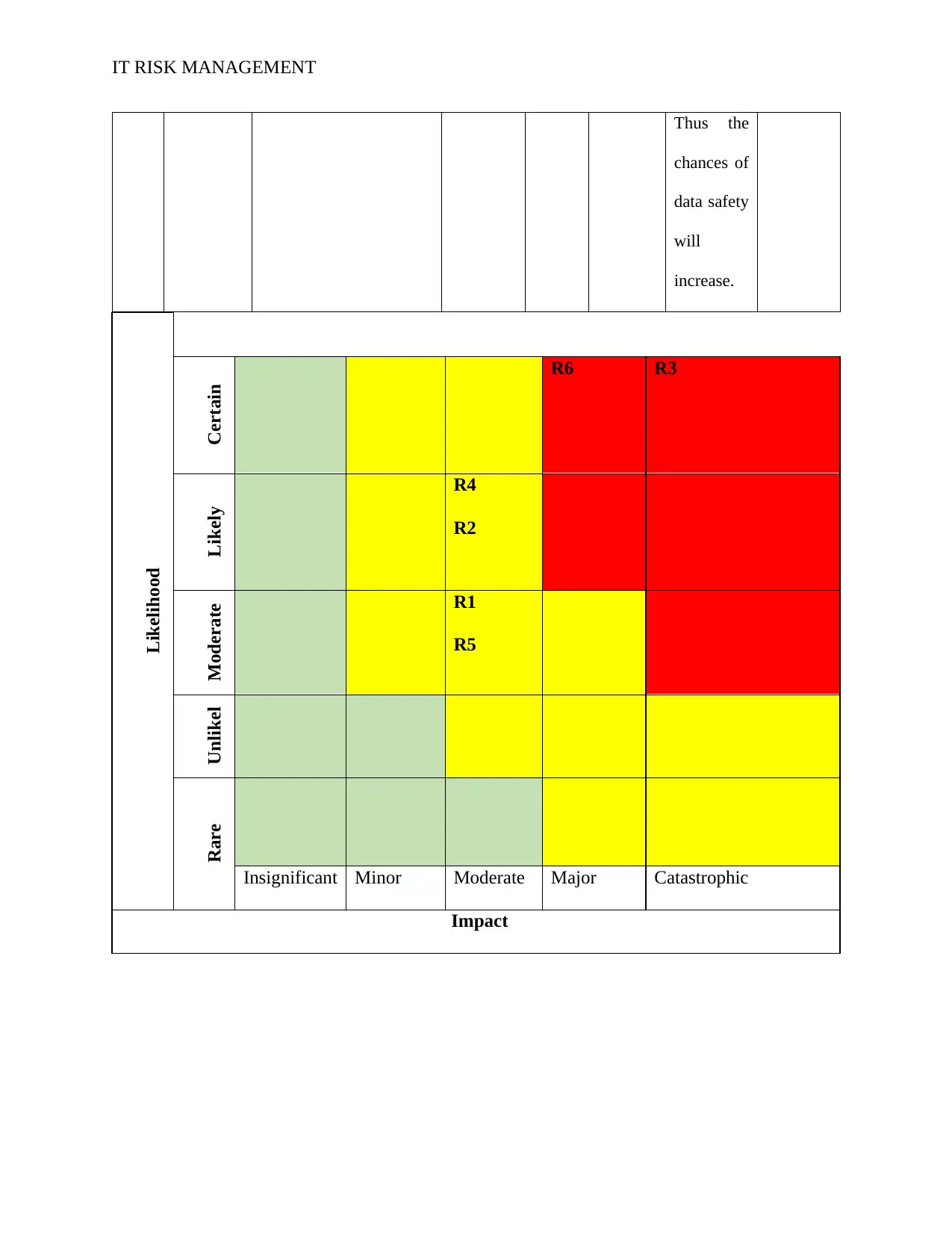
IT RISK MANAGEMENT
Thus the
chances of
data safety
will
increase.
Likelihood
Certain R6 R3
Likely R4
R2
Moderate R1
R5
Unlikel
y
Rare
Insignificant Minor Moderate Major Catastrophic
Impact
Thus the
chances of
data safety
will
increase.
Likelihood
Certain R6 R3
Likely R4
R2
Moderate R1
R5
Unlikel
y
Rare
Insignificant Minor Moderate Major Catastrophic
Impact

IT RISK MANAGEMENT
Prioritization
In order to prioritize the risks that are identified within the company it is important to
identify the risks at the first stage. Once the risks are identified successfully than it becomes easy
to manage the performance of the organization effectively. With the help of proper prioritization
it will become easy to mitigate the risks at early stage. Thus the risks with highest priority needs
to be mitigated at the early stage.
Prioritization
In order to prioritize the risks that are identified within the company it is important to
identify the risks at the first stage. Once the risks are identified successfully than it becomes easy
to manage the performance of the organization effectively. With the help of proper prioritization
it will become easy to mitigate the risks at early stage. Thus the risks with highest priority needs
to be mitigated at the early stage.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

IT RISK MANAGEMENT
Bibliography
[1] J. Heagney, “Fundamentals of project management”. Amacom, 2016.
[2] T.Kendrick, “Identifying and managing project risk: essential tools for failure-proofing your
project”. Amacom, 2015.
[3] H., Kerzner, “Project management: a systems approach to planning, scheduling, and
controlling”. John Wiley & Sons, 2017.
[4] D. Lock, The essentials of project management. Routledge, 2017.
[5] J.R. Meredith, Jr. S.J. Mantel and S.M.Shafer, “Project management: a managerial
approach”. John Wiley & Sons, 2017.
Bibliography
[1] J. Heagney, “Fundamentals of project management”. Amacom, 2016.
[2] T.Kendrick, “Identifying and managing project risk: essential tools for failure-proofing your
project”. Amacom, 2015.
[3] H., Kerzner, “Project management: a systems approach to planning, scheduling, and
controlling”. John Wiley & Sons, 2017.
[4] D. Lock, The essentials of project management. Routledge, 2017.
[5] J.R. Meredith, Jr. S.J. Mantel and S.M.Shafer, “Project management: a managerial
approach”. John Wiley & Sons, 2017.
1 out of 10
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





