Comprehensive IT Risk Management Report for Regional Gardens
VerifiedAdded on 2022/08/31
|12
|1493
|16
Report
AI Summary
This report, prepared for Regional Gardens, addresses critical IT risk management concerns. As the newly appointed CIO, the author analyzes the company's IT infrastructure, identifying key risks such as unrestricted internet access, excessive costs, lack of onboarding/offboarding processes, system maintenance issues, data loss, data integrity failures, inadequate monitoring, and lack of backup/disaster recovery. A detailed risk register is presented, outlining each risk, its description, potential impact, assessment, likelihood, consequences, control strategies, residual risks, and priority. The report emphasizes the importance of proactive risk mitigation, including restricting internet access, managing budgets, establishing formal processes, improving system maintenance, updating storage, encrypting data, implementing monitoring systems, and ensuring data backup and recovery procedures. The risks are prioritized based on their impact and likelihood, emphasizing the need for immediate action on high-priority issues. The report concludes that effective risk assessment is crucial for enhancing the overall performance of the organization, and that proper risk identification strategies are essential for mitigating potential issues.

Running head: IT RISK MANAGEMENT
IT RISK MANAGEMENT
Name of the Student
Name of the university
Author Note
IT RISK MANAGEMENT
Name of the Student
Name of the university
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
IT RISK MANAGEMENT
Table of Contents
Introduction......................................................................................................................................2
Risk register.....................................................................................................................................2
Conclusion.......................................................................................................................................9
References......................................................................................................................................10
IT RISK MANAGEMENT
Table of Contents
Introduction......................................................................................................................................2
Risk register.....................................................................................................................................2
Conclusion.......................................................................................................................................9
References......................................................................................................................................10
2
IT RISK MANAGEMENT
Introduction
Regional Gardens Ltd is the company that runs a wide number of related gardening
enterprises. The large display garden is made available for performing public inspection
throughout the year. Apart from this the company also owns a regional garden planners that aims
at providing garden advice, services and design. The staff population of the company is around
65 staffs including administrative, regional garden planner’s staff, nursery and management. The
company operates on a wide range of relatively old personal computers. Thus there are several
issues that hampers the performance of the organization.
In order to remove the risk issues it becomes essential to identify the risks at the early
stage so that proper mitigation can be included. The company operates the performance with a
small number of system administration staffs it becomes difficult to manage the server
infrastructure (Hopkinson, 2017). The report will focus entirely on identifying the key risks that
are likely to impact the performance of the organization. Along with this possible mitigation
strategies will also be offered for enhancing the performance.
Risk register
Ri
sk
id
Name Descrip
tion
Impa
ct
Assessm
ent
Likeli
hood
Consequ
ences
Control
strategy
Residua
l risks
Prio
rity
R
1
Issue
with
unrestri
cted
The
organiza
tion
does not
High
(5)
In order
to
understa
nd the
(4) This has
the
potential
to
Restricti
ng the
access
over
No
residual
risk will
be there
High
est
IT RISK MANAGEMENT
Introduction
Regional Gardens Ltd is the company that runs a wide number of related gardening
enterprises. The large display garden is made available for performing public inspection
throughout the year. Apart from this the company also owns a regional garden planners that aims
at providing garden advice, services and design. The staff population of the company is around
65 staffs including administrative, regional garden planner’s staff, nursery and management. The
company operates on a wide range of relatively old personal computers. Thus there are several
issues that hampers the performance of the organization.
In order to remove the risk issues it becomes essential to identify the risks at the early
stage so that proper mitigation can be included. The company operates the performance with a
small number of system administration staffs it becomes difficult to manage the server
infrastructure (Hopkinson, 2017). The report will focus entirely on identifying the key risks that
are likely to impact the performance of the organization. Along with this possible mitigation
strategies will also be offered for enhancing the performance.
Risk register
Ri
sk
id
Name Descrip
tion
Impa
ct
Assessm
ent
Likeli
hood
Consequ
ences
Control
strategy
Residua
l risks
Prio
rity
R
1
Issue
with
unrestri
cted
The
organiza
tion
does not
High
(5)
In order
to
understa
nd the
(4) This has
the
potential
to
Restricti
ng the
access
over
No
residual
risk will
be there
High
est
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
3
IT RISK MANAGEMENT
access
over
Internet
have
any
proper
restricti
on over
the use
of the
internet
(Latvala
et al.,
2016).
This
further
hampers
the
resource
s that
are
accesse
d
risk it
becomes
essential
to
monitor
the
website
performa
nce
hamper
the
activities
that are
carried
out
througho
ut the
internet.
internet after
mitigati
on
R
2
Excessi
ve cost
Huge
amount
of
High
(4)
For the
purpose
of
(4) Hampers
the
economy
The
budget
needs to
Less
chances
of
Medi
um
IT RISK MANAGEMENT
access
over
Internet
have
any
proper
restricti
on over
the use
of the
internet
(Latvala
et al.,
2016).
This
further
hampers
the
resource
s that
are
accesse
d
risk it
becomes
essential
to
monitor
the
website
performa
nce
hamper
the
activities
that are
carried
out
througho
ut the
internet.
internet after
mitigati
on
R
2
Excessi
ve cost
Huge
amount
of
High
(4)
For the
purpose
of
(4) Hampers
the
economy
The
budget
needs to
Less
chances
of
Medi
um
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4
IT RISK MANAGEMENT
money
is used
for
accessin
g web
services
determin
ing the
amount
of
money
wasted it
is
importan
t to
perform
proper
analysis
on the
rate of
the
organizat
ion
be
identifie
d at early
stage so
that it
become
easy to
manage
the
performa
nce
having
residual
risks
R
3
Lack of
formal
onboard
ing and
offboar
ding
process
The
system
lacks off
on
boardin
g and
off
boardin
g
facilities
Medi
um
(3)
The
organizat
ional
laws
have
been
determin
ed so
that it
becomes
(5) The
performa
nce will
be
impacted
widely
and thus
it is
importan
t to
With the
help of
proper
laws it
will
become
easy to
maintain
the
performa
No
residual
risks
Medi
um
IT RISK MANAGEMENT
money
is used
for
accessin
g web
services
determin
ing the
amount
of
money
wasted it
is
importan
t to
perform
proper
analysis
on the
rate of
the
organizat
ion
be
identifie
d at early
stage so
that it
become
easy to
manage
the
performa
nce
having
residual
risks
R
3
Lack of
formal
onboard
ing and
offboar
ding
process
The
system
lacks off
on
boardin
g and
off
boardin
g
facilities
Medi
um
(3)
The
organizat
ional
laws
have
been
determin
ed so
that it
becomes
(5) The
performa
nce will
be
impacted
widely
and thus
it is
importan
t to
With the
help of
proper
laws it
will
become
easy to
maintain
the
performa
No
residual
risks
Medi
um
5
IT RISK MANAGEMENT
that
impacts
the
ongoing
process
of the
organiza
tion.
easy to
organize
the
performa
nce.
include
proper
system
nce
(Singhal
& Ou,
2017).
R
4
Lack of
system
mainten
ance
The
system
mainten
ance is
not
perform
ed
efficient
ly that
hampers
the tasks
that are
perform
ed by
the
High
(5)
While
working
within
the
system it
has been
observed
that the
high
resolutio
n
applicati
ons
cannot
be run
(5) The
system
and the
activities
will be
impacted
. This
will
further
lead to
hamperi
ng the
performa
nce of
the
System
needs to
be
monitore
d and
maintain
ed
frequentl
y so that
it can
support
better
performa
nce
System
needs to
be
maintai
ned and
updated
frequent
ly so
that it
can
ensure
better
perform
ance.
High
est
priori
ty
IT RISK MANAGEMENT
that
impacts
the
ongoing
process
of the
organiza
tion.
easy to
organize
the
performa
nce.
include
proper
system
nce
(Singhal
& Ou,
2017).
R
4
Lack of
system
mainten
ance
The
system
mainten
ance is
not
perform
ed
efficient
ly that
hampers
the tasks
that are
perform
ed by
the
High
(5)
While
working
within
the
system it
has been
observed
that the
high
resolutio
n
applicati
ons
cannot
be run
(5) The
system
and the
activities
will be
impacted
. This
will
further
lead to
hamperi
ng the
performa
nce of
the
System
needs to
be
monitore
d and
maintain
ed
frequentl
y so that
it can
support
better
performa
nce
System
needs to
be
maintai
ned and
updated
frequent
ly so
that it
can
ensure
better
perform
ance.
High
est
priori
ty
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
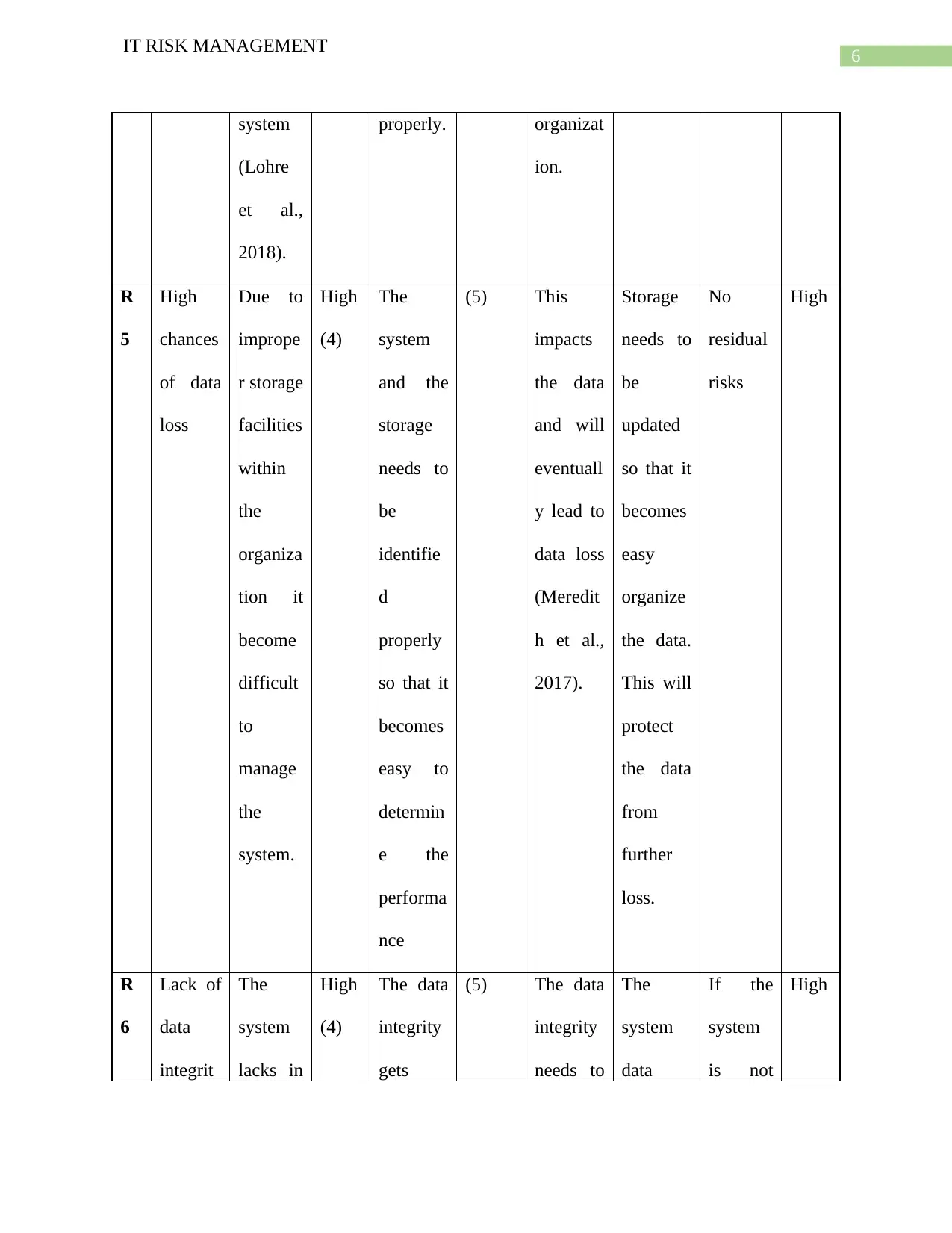
6
IT RISK MANAGEMENT
system
(Lohre
et al.,
2018).
properly. organizat
ion.
R
5
High
chances
of data
loss
Due to
imprope
r storage
facilities
within
the
organiza
tion it
become
difficult
to
manage
the
system.
High
(4)
The
system
and the
storage
needs to
be
identifie
d
properly
so that it
becomes
easy to
determin
e the
performa
nce
(5) This
impacts
the data
and will
eventuall
y lead to
data loss
(Meredit
h et al.,
2017).
Storage
needs to
be
updated
so that it
becomes
easy
organize
the data.
This will
protect
the data
from
further
loss.
No
residual
risks
High
R
6
Lack of
data
integrit
The
system
lacks in
High
(4)
The data
integrity
gets
(5) The data
integrity
needs to
The
system
data
If the
system
is not
High
IT RISK MANAGEMENT
system
(Lohre
et al.,
2018).
properly. organizat
ion.
R
5
High
chances
of data
loss
Due to
imprope
r storage
facilities
within
the
organiza
tion it
become
difficult
to
manage
the
system.
High
(4)
The
system
and the
storage
needs to
be
identifie
d
properly
so that it
becomes
easy to
determin
e the
performa
nce
(5) This
impacts
the data
and will
eventuall
y lead to
data loss
(Meredit
h et al.,
2017).
Storage
needs to
be
updated
so that it
becomes
easy
organize
the data.
This will
protect
the data
from
further
loss.
No
residual
risks
High
R
6
Lack of
data
integrit
The
system
lacks in
High
(4)
The data
integrity
gets
(5) The data
integrity
needs to
The
system
data
If the
system
is not
High
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
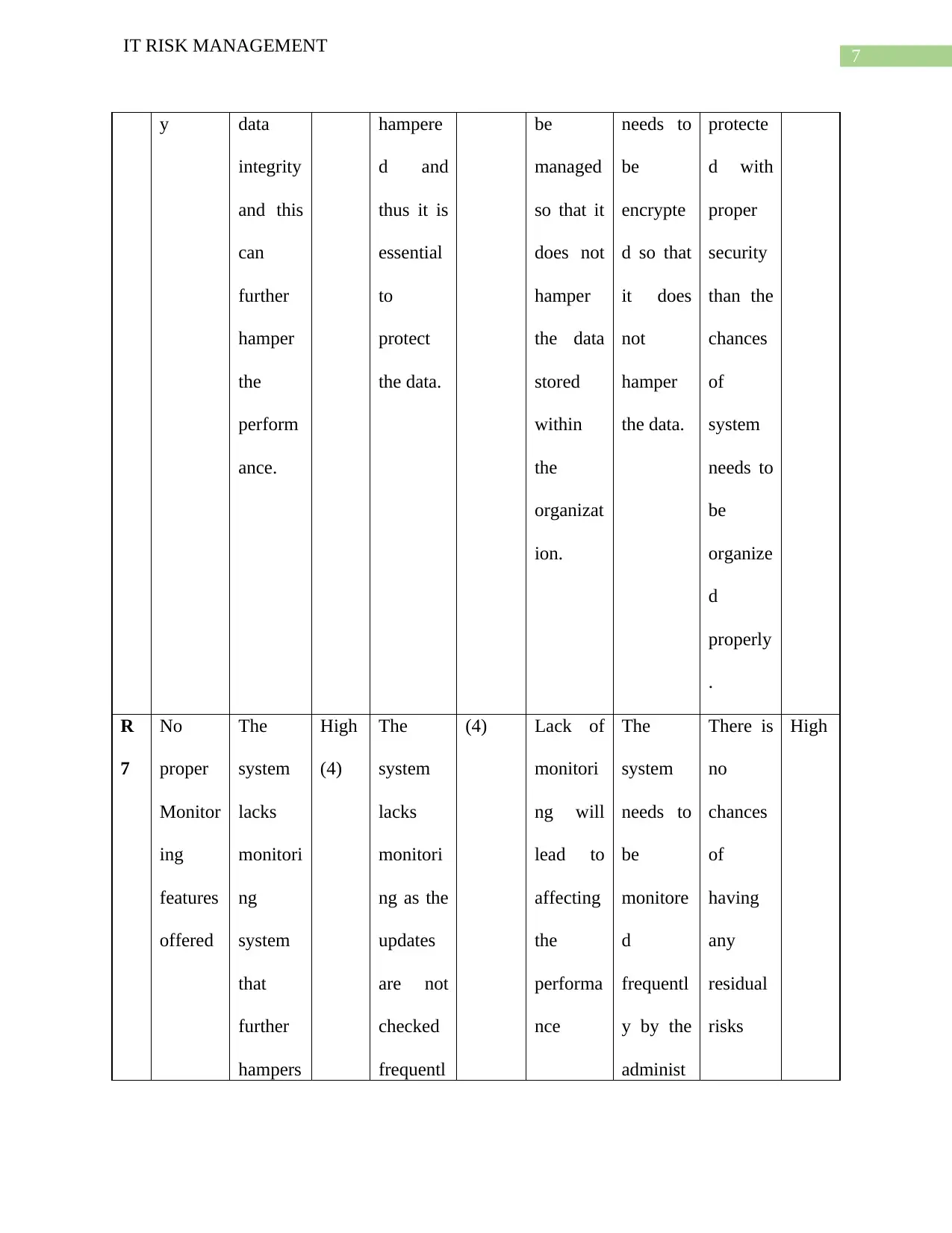
7
IT RISK MANAGEMENT
y data
integrity
and this
can
further
hamper
the
perform
ance.
hampere
d and
thus it is
essential
to
protect
the data.
be
managed
so that it
does not
hamper
the data
stored
within
the
organizat
ion.
needs to
be
encrypte
d so that
it does
not
hamper
the data.
protecte
d with
proper
security
than the
chances
of
system
needs to
be
organize
d
properly
.
R
7
No
proper
Monitor
ing
features
offered
The
system
lacks
monitori
ng
system
that
further
hampers
High
(4)
The
system
lacks
monitori
ng as the
updates
are not
checked
frequentl
(4) Lack of
monitori
ng will
lead to
affecting
the
performa
nce
The
system
needs to
be
monitore
d
frequentl
y by the
administ
There is
no
chances
of
having
any
residual
risks
High
IT RISK MANAGEMENT
y data
integrity
and this
can
further
hamper
the
perform
ance.
hampere
d and
thus it is
essential
to
protect
the data.
be
managed
so that it
does not
hamper
the data
stored
within
the
organizat
ion.
needs to
be
encrypte
d so that
it does
not
hamper
the data.
protecte
d with
proper
security
than the
chances
of
system
needs to
be
organize
d
properly
.
R
7
No
proper
Monitor
ing
features
offered
The
system
lacks
monitori
ng
system
that
further
hampers
High
(4)
The
system
lacks
monitori
ng as the
updates
are not
checked
frequentl
(4) Lack of
monitori
ng will
lead to
affecting
the
performa
nce
The
system
needs to
be
monitore
d
frequentl
y by the
administ
There is
no
chances
of
having
any
residual
risks
High
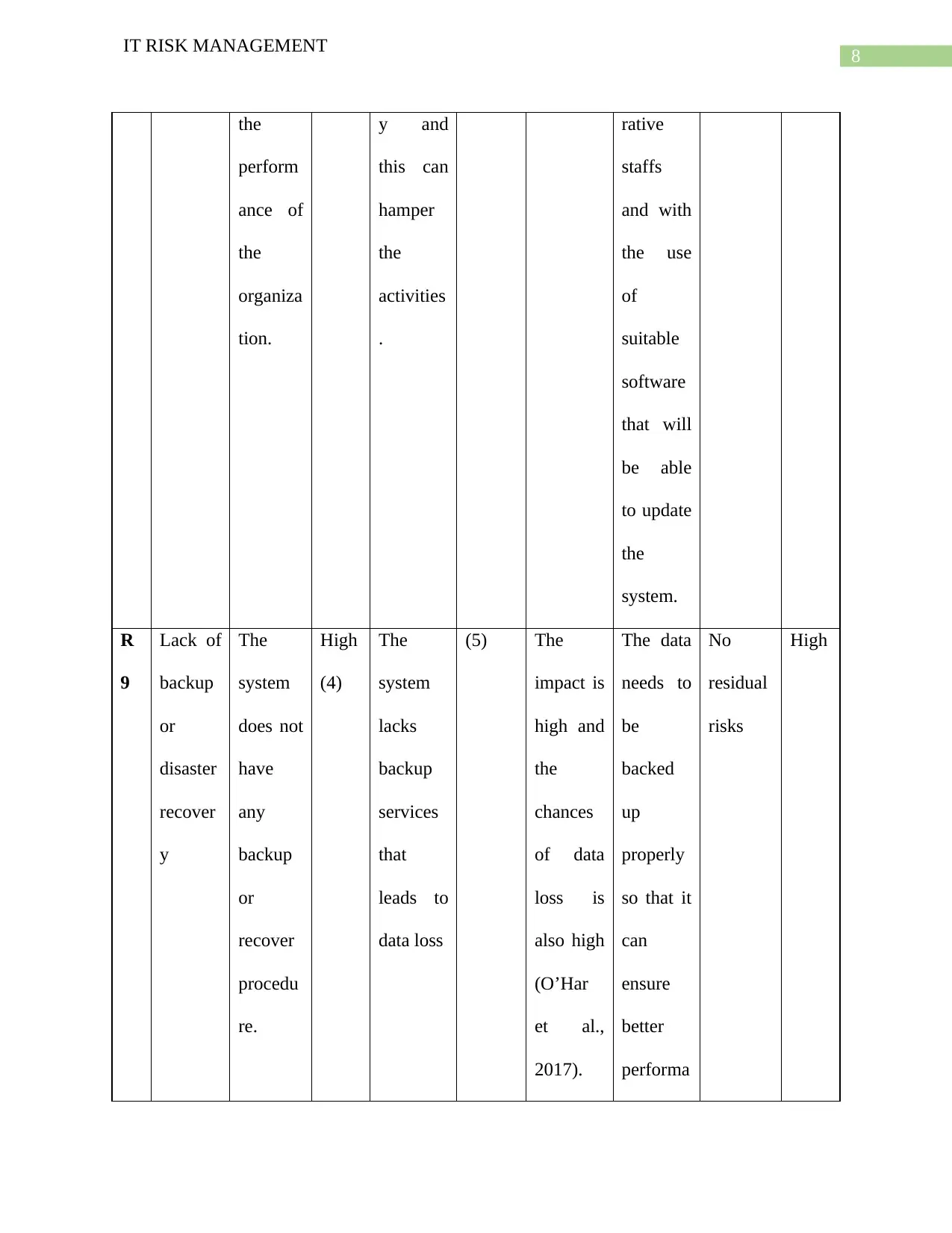
8
IT RISK MANAGEMENT
the
perform
ance of
the
organiza
tion.
y and
this can
hamper
the
activities
.
rative
staffs
and with
the use
of
suitable
software
that will
be able
to update
the
system.
R
9
Lack of
backup
or
disaster
recover
y
The
system
does not
have
any
backup
or
recover
procedu
re.
High
(4)
The
system
lacks
backup
services
that
leads to
data loss
(5) The
impact is
high and
the
chances
of data
loss is
also high
(O’Har
et al.,
2017).
The data
needs to
be
backed
up
properly
so that it
can
ensure
better
performa
No
residual
risks
High
IT RISK MANAGEMENT
the
perform
ance of
the
organiza
tion.
y and
this can
hamper
the
activities
.
rative
staffs
and with
the use
of
suitable
software
that will
be able
to update
the
system.
R
9
Lack of
backup
or
disaster
recover
y
The
system
does not
have
any
backup
or
recover
procedu
re.
High
(4)
The
system
lacks
backup
services
that
leads to
data loss
(5) The
impact is
high and
the
chances
of data
loss is
also high
(O’Har
et al.,
2017).
The data
needs to
be
backed
up
properly
so that it
can
ensure
better
performa
No
residual
risks
High
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9
IT RISK MANAGEMENT
nce.
The above table is designed for the purpose of describing the risks that are associated
with Regional case study. Risk id column is used for the purpose of the purpose of listing the
number of risks that are associated with the case study. The risk description is used for
discussing the risks in detailed so that it becomes easy to understand the risks. The risk
assessment is used for the purpose of identifying the main reason behind the risks (Altulyan et
al., 2019). The control strategy is being described so that it becomes easy to identify the process
with which it becomes easy to manage the issues. The risks are identified based on the impacts
created (Torabi et al., 2016). Thus the risks are needed to be analyzed and sorted based on the
priority.
Conclusion
Thus from the above report it can be stated that with the help of proper risk assessment it
becomes easy to identify the risks that will impact the overall performance of the organization.
The report has focused on determining the key risks and the possible mitigation strategies that
will be able to manage the performance of the organization. The risks are prioritized based on the
impacts and likelihood. Thus it can be stated that with the help of proper risk identification
strategies it becomes easy to mitigate the issues.
IT RISK MANAGEMENT
nce.
The above table is designed for the purpose of describing the risks that are associated
with Regional case study. Risk id column is used for the purpose of the purpose of listing the
number of risks that are associated with the case study. The risk description is used for
discussing the risks in detailed so that it becomes easy to understand the risks. The risk
assessment is used for the purpose of identifying the main reason behind the risks (Altulyan et
al., 2019). The control strategy is being described so that it becomes easy to identify the process
with which it becomes easy to manage the issues. The risks are identified based on the impacts
created (Torabi et al., 2016). Thus the risks are needed to be analyzed and sorted based on the
priority.
Conclusion
Thus from the above report it can be stated that with the help of proper risk assessment it
becomes easy to identify the risks that will impact the overall performance of the organization.
The report has focused on determining the key risks and the possible mitigation strategies that
will be able to manage the performance of the organization. The risks are prioritized based on the
impacts and likelihood. Thus it can be stated that with the help of proper risk identification
strategies it becomes easy to mitigate the issues.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10
IT RISK MANAGEMENT
References
Altulyan, M., Yao, L., Kanhere, S. S., Wang, X., & Huang, C. (2019). A unified framework for
data integrity protection in people-centric smart cities. Multimedia Tools and
Applications, 1-14.
Hopkinson, M. (2017). The project risk maturity model: Measuring and improving risk
management capability. Routledge.
Latvala, O. M., Toivonen, J., Evesti, A., Sihvonen, M., & Jordan, V. (2016). Security risk
visualization with semantic risk model. Procedia Computer Science, 83, 1194-1199.
Lohre, H., Happersberger, D., & Radatz, E. (2018). Evaluating risk mitigation strategies. Risk &
Reward, 27-31.
Meredith, J. R., Mantel Jr, S. J., & Shafer, S. M. (2017). Project management: a managerial
approach. John Wiley & Sons.
O'Har, J. P., Senesi, C. W., & Molenaar, K. R. (2017). Development of a risk register
spreadsheet tool for enterprise-and program-level risk management. Transportation
research record, 2604(1), 19-27.
Singhal, A., & Ou, X. (2017). Security risk analysis of enterprise networks using probabilistic
attack graphs. In Network Security Metrics (pp. 53-73). Springer, Cham.
Torabi, S. A., Giahi, R., & Sahebjamnia, N. (2016). An enhanced risk assessment framework for
business continuity management systems. Safety Science, 89, 201-218.
IT RISK MANAGEMENT
References
Altulyan, M., Yao, L., Kanhere, S. S., Wang, X., & Huang, C. (2019). A unified framework for
data integrity protection in people-centric smart cities. Multimedia Tools and
Applications, 1-14.
Hopkinson, M. (2017). The project risk maturity model: Measuring and improving risk
management capability. Routledge.
Latvala, O. M., Toivonen, J., Evesti, A., Sihvonen, M., & Jordan, V. (2016). Security risk
visualization with semantic risk model. Procedia Computer Science, 83, 1194-1199.
Lohre, H., Happersberger, D., & Radatz, E. (2018). Evaluating risk mitigation strategies. Risk &
Reward, 27-31.
Meredith, J. R., Mantel Jr, S. J., & Shafer, S. M. (2017). Project management: a managerial
approach. John Wiley & Sons.
O'Har, J. P., Senesi, C. W., & Molenaar, K. R. (2017). Development of a risk register
spreadsheet tool for enterprise-and program-level risk management. Transportation
research record, 2604(1), 19-27.
Singhal, A., & Ou, X. (2017). Security risk analysis of enterprise networks using probabilistic
attack graphs. In Network Security Metrics (pp. 53-73). Springer, Cham.
Torabi, S. A., Giahi, R., & Sahebjamnia, N. (2016). An enhanced risk assessment framework for
business continuity management systems. Safety Science, 89, 201-218.

11
IT RISK MANAGEMENT
IT RISK MANAGEMENT
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 12
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





