IT Risk Management Report
VerifiedAdded on 2020/03/02
|16
|3606
|77
Report
AI Summary
This report discusses the various risks faced by information technology organizations, particularly focusing on the regulations and risk management strategies implemented by the VIC government. It categorizes risks into internal and external threats, compares deliberate and accidental threats, and evaluates the challenges faced in managing these risks. The report emphasizes the importance of adhering to government regulations to enhance security and mitigate risks effectively.

Running head: IT RISK MANAGEMENT
IT RISK MANAGEMENT
Name of the Student
Name of the University
Author note
IT RISK MANAGEMENT
Name of the Student
Name of the University
Author note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1IT RISK MANAGEMENT
Executive summary
The main objective of this report is to discuss the possible risks for the information
technology organisations. There are many risks factors which can be classified according to the
nature. VIC government has made many methods and regulations so that the risks can be
managed and overcome in proper way. It is concluded that the organisations should follow all the
regulations and the rules given by the VIC government to overcome all the possible risk factors.
Executive summary
The main objective of this report is to discuss the possible risks for the information
technology organisations. There are many risks factors which can be classified according to the
nature. VIC government has made many methods and regulations so that the risks can be
managed and overcome in proper way. It is concluded that the organisations should follow all the
regulations and the rules given by the VIC government to overcome all the possible risk factors.

2IT RISK MANAGEMENT
Table of Contents
Introduction......................................................................................................................................3
1. Diagram of risks and risk management of VIC government...................................................4
2. Explanation of the diagram and identification of different levels of risk exposure....................5
3. Comparison between Deliberate and Accidental Threats and ranking of threats according to
the importance.................................................................................................................................7
4. Explanation of the challenges of VIC government regarding the internal and external risk
management.....................................................................................................................................8
5. Difference between Risk and Uncertainty...................................................................................9
6. Discussion and evaluation of several methods available to the VIC government for risk
management.....................................................................................................................................9
Conclusion.....................................................................................................................................11
References......................................................................................................................................12
Table of Contents
Introduction......................................................................................................................................3
1. Diagram of risks and risk management of VIC government...................................................4
2. Explanation of the diagram and identification of different levels of risk exposure....................5
3. Comparison between Deliberate and Accidental Threats and ranking of threats according to
the importance.................................................................................................................................7
4. Explanation of the challenges of VIC government regarding the internal and external risk
management.....................................................................................................................................8
5. Difference between Risk and Uncertainty...................................................................................9
6. Discussion and evaluation of several methods available to the VIC government for risk
management.....................................................................................................................................9
Conclusion.....................................................................................................................................11
References......................................................................................................................................12
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3IT RISK MANAGEMENT
Introduction
In information technology the number of threats and the organisational risk factors are
increasing day by day. It is seen that the organisations are facing lots of risks and threats from
both inside and outside of the organisation (Aldunce et al., 2015). There are also various types of
risks present in an organisation on the basis of the nature. Natural calamities like storm and
earthquake can also lead to the organisation risk factors. Hacking, malware and virus are also
reasons of the security issues. There are many differences between the risk and the uncertainty.
VIC government has provided a list or guidance of regulations which can make the system more
advanced in terms of security.
In this report the risk factors are discussed in details with a diagram. The risk
management methods and regulations of the VIC government are also discussed in the following
discussions of the report.
Introduction
In information technology the number of threats and the organisational risk factors are
increasing day by day. It is seen that the organisations are facing lots of risks and threats from
both inside and outside of the organisation (Aldunce et al., 2015). There are also various types of
risks present in an organisation on the basis of the nature. Natural calamities like storm and
earthquake can also lead to the organisation risk factors. Hacking, malware and virus are also
reasons of the security issues. There are many differences between the risk and the uncertainty.
VIC government has provided a list or guidance of regulations which can make the system more
advanced in terms of security.
In this report the risk factors are discussed in details with a diagram. The risk
management methods and regulations of the VIC government are also discussed in the following
discussions of the report.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
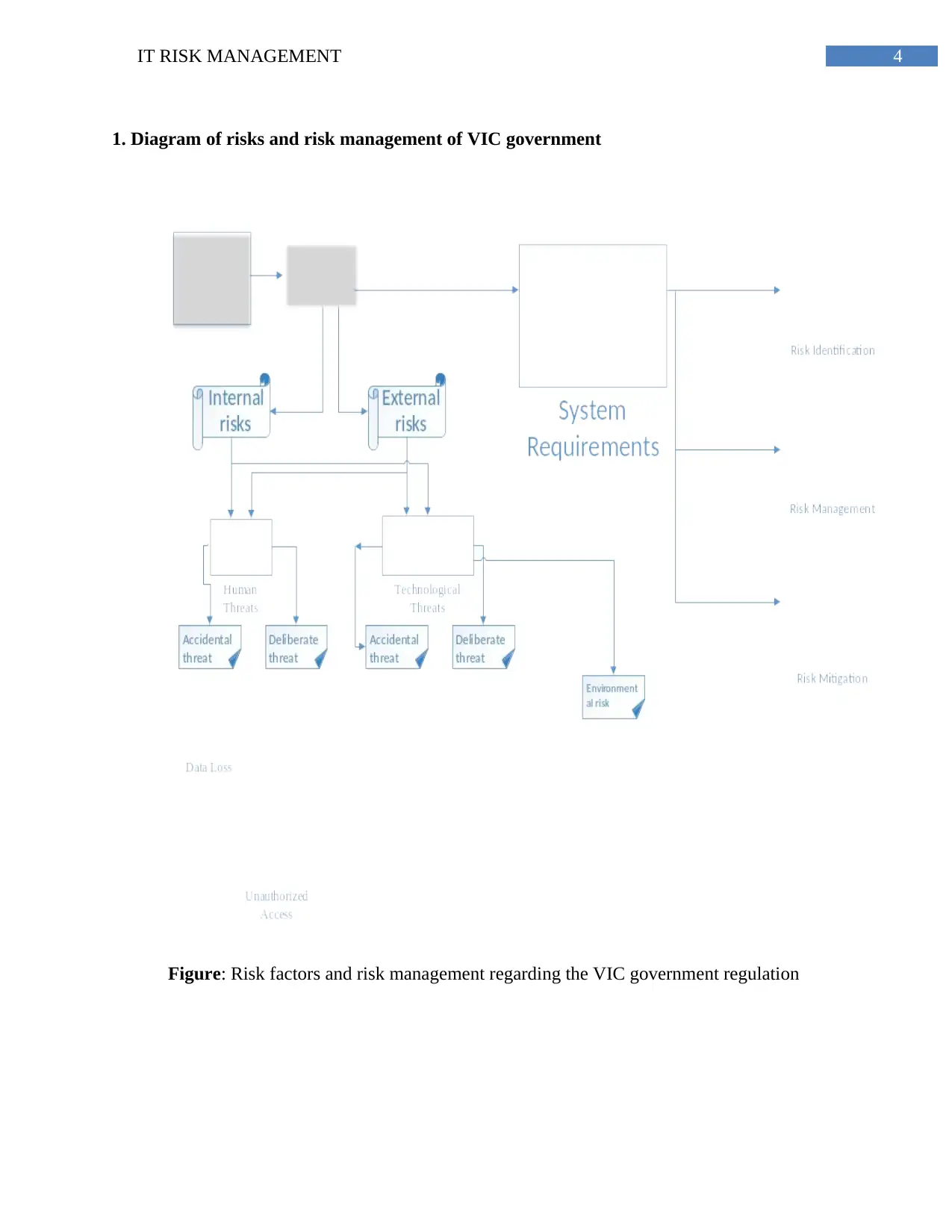
4IT RISK MANAGEMENT
1. Diagram of risks and risk management of VIC government
Figure: Risk factors and risk management regarding the VIC government regulation
1. Diagram of risks and risk management of VIC government
Figure: Risk factors and risk management regarding the VIC government regulation

5IT RISK MANAGEMENT
2. Explanation of the diagram and identification of different levels of risk exposure.
The diagram explains the structure of the flow of the factors in an organization. It has also
provided an outline about risk management regulations of the VIC government. There are
many factors of making the system vulnerable. Most of the factors are dependent upon
various risks and threats. In the diagram all the possible threats are given in accordance
with their place and moment of occurrence (Becken & Hughey, 2013). The risks are
classified into two parts. One is the internal risks and the other is the external risks for the
organization. The internal risks are generated due to various issues regarding the internal
functioning of the organization. Another important factor is that the organization has
many possible ways of creating threats and uncertainties by itself (Bianco et al., 2017).
The internal risk factors can also be divided into two parts and those are deliberate threat
and accidental threat. In case of accidental threats the cause is not due to individual’s
action. Accidental risk factors are caused due to several causes like power loss and lack
of internet connection and many more. These factors are only considered inside the
organization. In case of deliberate threats the reasons behind the threats are generated due
to individual motive. In case of organizational risk the people who are working in the
organization make cause threats and risk factors into the system of the organization so
that the organization faces difficulties and loss of productivity. Unauthorized access, data
loss and intrusion can be considered as the problems regarding the functioning of the
possible risk factors inside the organization (Brindley, 2017). Data breach can also be an
important factor that can be used by the employees of the organization to harm it.
Another type of risk is the external risk. External risk can occur due to the reasons
initiated externally from the organizations. This type of risk factors is the most common
2. Explanation of the diagram and identification of different levels of risk exposure.
The diagram explains the structure of the flow of the factors in an organization. It has also
provided an outline about risk management regulations of the VIC government. There are
many factors of making the system vulnerable. Most of the factors are dependent upon
various risks and threats. In the diagram all the possible threats are given in accordance
with their place and moment of occurrence (Becken & Hughey, 2013). The risks are
classified into two parts. One is the internal risks and the other is the external risks for the
organization. The internal risks are generated due to various issues regarding the internal
functioning of the organization. Another important factor is that the organization has
many possible ways of creating threats and uncertainties by itself (Bianco et al., 2017).
The internal risk factors can also be divided into two parts and those are deliberate threat
and accidental threat. In case of accidental threats the cause is not due to individual’s
action. Accidental risk factors are caused due to several causes like power loss and lack
of internet connection and many more. These factors are only considered inside the
organization. In case of deliberate threats the reasons behind the threats are generated due
to individual motive. In case of organizational risk the people who are working in the
organization make cause threats and risk factors into the system of the organization so
that the organization faces difficulties and loss of productivity. Unauthorized access, data
loss and intrusion can be considered as the problems regarding the functioning of the
possible risk factors inside the organization (Brindley, 2017). Data breach can also be an
important factor that can be used by the employees of the organization to harm it.
Another type of risk is the external risk. External risk can occur due to the reasons
initiated externally from the organizations. This type of risk factors is the most common
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6IT RISK MANAGEMENT
risk factors. Hackers and other unwanted access are always making various kinds of risks
to the system of the organization. Risks can also be divided into two parts according to
the nature of the risk factors. The risk factors can be also determined by the nature of the
risks. One is environmental risk and the other is human made risks (Chance & Brooks,
2015). The environmental risks factors are also important in case of making the system
more vulnerable. Natural disasters like earthquake, storm and sudden temperature change
of the environment can cause a big damage to the system. In the right most side of the
diagram the risk management steps are shown as per the VIC government rules and
regulations. To decrease the risk factors first the risk should be identified properly so that
it can be fought properly. Then the mitigation of the risk factors is done by decreasing the
reasons behind the risks. In case information technology the ICT security risks are also
important factor (Davies, 2014). There are also many layers presenty in the risks
management system. The main thing is that the risks must be clearly understood from the
point of effect it can reach. Several risks are given various levels with respect to their
vulnerability. These levels can be divided into three parts. Those are high, medium and
low risk respectively. The main effects of the risks, which are also the main factors for
the failure of organisation’s functioning, lead to several damages (DeAngelo & Stulz,
2015). Those risks which lead to the failure of most of the organisations functioning and
also very vulnerable in terms of making the system endangered are known as the high
risk factors. Examples of such risks are hacking, intrusion, failure of the total power
system of the organisation. These types of risk factors are also important in case of
making the system more vulnerable and also the source of these risks can be both internal
and external with respect to the organisation (Ferguson at al., 2013). The natural risks
risk factors. Hackers and other unwanted access are always making various kinds of risks
to the system of the organization. Risks can also be divided into two parts according to
the nature of the risk factors. The risk factors can be also determined by the nature of the
risks. One is environmental risk and the other is human made risks (Chance & Brooks,
2015). The environmental risks factors are also important in case of making the system
more vulnerable. Natural disasters like earthquake, storm and sudden temperature change
of the environment can cause a big damage to the system. In the right most side of the
diagram the risk management steps are shown as per the VIC government rules and
regulations. To decrease the risk factors first the risk should be identified properly so that
it can be fought properly. Then the mitigation of the risk factors is done by decreasing the
reasons behind the risks. In case information technology the ICT security risks are also
important factor (Davies, 2014). There are also many layers presenty in the risks
management system. The main thing is that the risks must be clearly understood from the
point of effect it can reach. Several risks are given various levels with respect to their
vulnerability. These levels can be divided into three parts. Those are high, medium and
low risk respectively. The main effects of the risks, which are also the main factors for
the failure of organisation’s functioning, lead to several damages (DeAngelo & Stulz,
2015). Those risks which lead to the failure of most of the organisations functioning and
also very vulnerable in terms of making the system endangered are known as the high
risk factors. Examples of such risks are hacking, intrusion, failure of the total power
system of the organisation. These types of risk factors are also important in case of
making the system more vulnerable and also the source of these risks can be both internal
and external with respect to the organisation (Ferguson at al., 2013). The natural risks
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7IT RISK MANAGEMENT
like earthquake, storm is also considered to be high risk factors for the organisations.
Medium level risks are data loss of the servers. This kind of data loss is also important in
case of making the organisational background more vulnerable and also the importance
of the risk factors is of medium nature (Glendon, Clarke & McKenna, 2016). Sudden
power loss and sudden loss of network connections are also considered to be low risk
factors for the organisation. These risk factors should also be given equal priority in case
of solving them and also these risk factors are to be solved with respect to the
organisational point of view.
3. Comparison between Deliberate and Accidental Threats and ranking of threats
according to the importance
Threats are created by different types of reasons which can be divided in two different ways.
These are deliberate threats and accidental threats. The deliberate threats are those which
are created by intention by individuals or group of individuals (Heazle et al., 2013).
Deliberate threats can be from the inside or from the outside of the organisation. In case
of deliberate threats external deliberate threats are hacking, intrusion and data loss of the
organisation by some external people. The access of the unwanted people can lead to the
threats which are also very important in case of making the deliberate one (Holt,
Smirnova, Chua & Copes, 2015). The main aim of the risk management process is to
cancel out the deliberate threats. Deliberate threats can be considered as the high level
risk factors for the organisations. As the information of the public is the most important
thing in information technology market, it is given the highest priority (Tadeusiewicz &
Horzyk, 2014). Hacking and data intrusion can be big risk factors for the public
information. These kinds of risks are also referred to high level risk factors. From that
like earthquake, storm is also considered to be high risk factors for the organisations.
Medium level risks are data loss of the servers. This kind of data loss is also important in
case of making the organisational background more vulnerable and also the importance
of the risk factors is of medium nature (Glendon, Clarke & McKenna, 2016). Sudden
power loss and sudden loss of network connections are also considered to be low risk
factors for the organisation. These risk factors should also be given equal priority in case
of solving them and also these risk factors are to be solved with respect to the
organisational point of view.
3. Comparison between Deliberate and Accidental Threats and ranking of threats
according to the importance
Threats are created by different types of reasons which can be divided in two different ways.
These are deliberate threats and accidental threats. The deliberate threats are those which
are created by intention by individuals or group of individuals (Heazle et al., 2013).
Deliberate threats can be from the inside or from the outside of the organisation. In case
of deliberate threats external deliberate threats are hacking, intrusion and data loss of the
organisation by some external people. The access of the unwanted people can lead to the
threats which are also very important in case of making the deliberate one (Holt,
Smirnova, Chua & Copes, 2015). The main aim of the risk management process is to
cancel out the deliberate threats. Deliberate threats can be considered as the high level
risk factors for the organisations. As the information of the public is the most important
thing in information technology market, it is given the highest priority (Tadeusiewicz &
Horzyk, 2014). Hacking and data intrusion can be big risk factors for the public
information. These kinds of risks are also referred to high level risk factors. From that

8IT RISK MANAGEMENT
point of view of the organisation is responsible for the risks which are caused internally
as the deliberate threats are also caused from the inside of the organisation. In case of
organisational risks the main source of the risks are the data loss by the employees which
are also considered as deliberate threats. These kinds of deliberate threats are of highest
priority also (Hopkin, 2017). Another type of risks is the accidental risk factor as the risk
factor is caused by uncontrolled reasons. Environmental and natural risks are of this type.
This type of risks is of both high and low priority. As the risk factors which are caused by
the natural disasters like earthquake and storms, are considered to be the high risk factors.
Also the risk factors like sudden power cut and the loss of internet connection are
considered to be of relatively low risk factors.
4. Explanation of the challenges of VIC government regarding the internal and external
risk management
The IT risk management is a challenging task for the organisation in case of making the
organisations free from the reasons which causes vulnerabilities to the system (Reason,
2016). It is already discussed that the risks can be of two types and those are respectively
internal and external risk factors. In case of risk management the risk factors are also
managed by the organisation in such a way that there are two different methods for
dealing with the internal and external risks. The patterns of the internal risks are
completely different from that of the external risk factors (Howard & Beasley, 2017). In
case of internal risk factors the employees of the organisations are sometimes liable for
that. In that case the organisations should be very strict with the employees. The main
actions that can be taken by the organisation administration should be in such a way that
the internal risks are demolished from the organisation (Howes et al., 2015). The
point of view of the organisation is responsible for the risks which are caused internally
as the deliberate threats are also caused from the inside of the organisation. In case of
organisational risks the main source of the risks are the data loss by the employees which
are also considered as deliberate threats. These kinds of deliberate threats are of highest
priority also (Hopkin, 2017). Another type of risks is the accidental risk factor as the risk
factor is caused by uncontrolled reasons. Environmental and natural risks are of this type.
This type of risks is of both high and low priority. As the risk factors which are caused by
the natural disasters like earthquake and storms, are considered to be the high risk factors.
Also the risk factors like sudden power cut and the loss of internet connection are
considered to be of relatively low risk factors.
4. Explanation of the challenges of VIC government regarding the internal and external
risk management
The IT risk management is a challenging task for the organisation in case of making the
organisations free from the reasons which causes vulnerabilities to the system (Reason,
2016). It is already discussed that the risks can be of two types and those are respectively
internal and external risk factors. In case of risk management the risk factors are also
managed by the organisation in such a way that there are two different methods for
dealing with the internal and external risks. The patterns of the internal risks are
completely different from that of the external risk factors (Howard & Beasley, 2017). In
case of internal risk factors the employees of the organisations are sometimes liable for
that. In that case the organisations should be very strict with the employees. The main
actions that can be taken by the organisation administration should be in such a way that
the internal risks are demolished from the organisation (Howes et al., 2015). The
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9IT RISK MANAGEMENT
advantage in case of the internal risk factor is that the organisation has the control on the
risk factors. In case of the external risk factors the reasons behind the risks cannot be
controlled. The organisation should be more careful and constructive in case of external
risk management (Kettl, 2015). The main advantage of the external risk factor is that it
can be caused not intentionally sometimes. For that reason the organisation should be
more technically sounded for opposing the risk factors.
5. Difference between Risk and Uncertainty
There are lots of differences between the risk and uncertainty. Risks are those which actually
happen due to predefined reasons (Lam, 2014). The uncertainties cannot be understood
previously. The main advantages of the risk analysis are that the reasons behind any risks
are already known to the organisation. The risks can be controlled by taking previous
precautions on the basis of the nature of the risks (Lawrence et al., 2015). In case of the
uncertainties the main disadvantage is that the precautions cannot be taken previously as
the reasons behind the uncertainties are not known. The time of happening of the risks
can also predefined but the time and duration of the uncertainties can never be understood
previously. The main advantage of making the risk management in a proper way, is to
make the system secure.
6. Discussion and evaluation of several methods available to the VIC government for risk
management
In this part of the report the risk management methods are discussed in details. The VIC
government has created lots of methods that will help to create the system more secure.
The VIC governments have also created many rules and regulations which should be
advantage in case of the internal risk factor is that the organisation has the control on the
risk factors. In case of the external risk factors the reasons behind the risks cannot be
controlled. The organisation should be more careful and constructive in case of external
risk management (Kettl, 2015). The main advantage of the external risk factor is that it
can be caused not intentionally sometimes. For that reason the organisation should be
more technically sounded for opposing the risk factors.
5. Difference between Risk and Uncertainty
There are lots of differences between the risk and uncertainty. Risks are those which actually
happen due to predefined reasons (Lam, 2014). The uncertainties cannot be understood
previously. The main advantages of the risk analysis are that the reasons behind any risks
are already known to the organisation. The risks can be controlled by taking previous
precautions on the basis of the nature of the risks (Lawrence et al., 2015). In case of the
uncertainties the main disadvantage is that the precautions cannot be taken previously as
the reasons behind the uncertainties are not known. The time of happening of the risks
can also predefined but the time and duration of the uncertainties can never be understood
previously. The main advantage of making the risk management in a proper way, is to
make the system secure.
6. Discussion and evaluation of several methods available to the VIC government for risk
management
In this part of the report the risk management methods are discussed in details. The VIC
government has created lots of methods that will help to create the system more secure.
The VIC governments have also created many rules and regulations which should be
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10IT RISK MANAGEMENT
followed in order to make the system fight the risk factors (McNeil, Frey & Embrechts,
2015). The main advantage of making the risk management procedures are that the
organisations can rely on the standards in case of opposing the risk factors. VIC
government has created many laws and protocols for risk management. The first one is
the privacy and data protection act 2014 (Paton et al., 2014). The Victorian protective
data security framework is also designed to make the system secure. The main features of
the security acts are making the framework, issuing the framework and then to monitor
and regime the data security frameworks related to the organisations. The public sector
data and the protective data security acts are also important in case of making the system
more secured. In this case same features are also taken in order to implement the laws in
proper way (Poniszewska-Marańda, 2014). The primary step of this law is to develop and
documenting the security framework. Then the standards, policies and the guidelines are
also designed to make the system more secure. Compliance should also be delivered in
order to overcome the risk factors. The information access should be also followed
properly in order to make the system more secure and to overcome the risks. The security
requirements should also be monitored properly and the reasons should be understood
properly. Security awareness and training should be provided more so that the
organisations can deal with such employees and public who are reliable enough to access
the system securely. The service providers should be contracted so that the security is
ensured (Pritchard & PMP, .2014). The government rules and regulations should also be
followed properly. Information value is also an important factor in case of making the
system more secured with respect to the organisations. The security should be provided
followed in order to make the system fight the risk factors (McNeil, Frey & Embrechts,
2015). The main advantage of making the risk management procedures are that the
organisations can rely on the standards in case of opposing the risk factors. VIC
government has created many laws and protocols for risk management. The first one is
the privacy and data protection act 2014 (Paton et al., 2014). The Victorian protective
data security framework is also designed to make the system secure. The main features of
the security acts are making the framework, issuing the framework and then to monitor
and regime the data security frameworks related to the organisations. The public sector
data and the protective data security acts are also important in case of making the system
more secured. In this case same features are also taken in order to implement the laws in
proper way (Poniszewska-Marańda, 2014). The primary step of this law is to develop and
documenting the security framework. Then the standards, policies and the guidelines are
also designed to make the system more secure. Compliance should also be delivered in
order to overcome the risk factors. The information access should be also followed
properly in order to make the system more secure and to overcome the risks. The security
requirements should also be monitored properly and the reasons should be understood
properly. Security awareness and training should be provided more so that the
organisations can deal with such employees and public who are reliable enough to access
the system securely. The service providers should be contracted so that the security is
ensured (Pritchard & PMP, .2014). The government rules and regulations should also be
followed properly. Information value is also an important factor in case of making the
system more secured with respect to the organisations. The security should be provided

11IT RISK MANAGEMENT
according to the value of the information. The organisations also follow the regulations in
Case of sharing the information with other organisations.
Conclusion
From the above discussion it is concluded that several organisations face a lot of risk
factors and to make the information secured all the regulations which are made by the VIC
government, should be followed properly. Public personal information is the most important data
from the security point of view. Organisations give public information the highest priority. The
main advantage making the system more secured is that the public reliability is increased on the
organisation and also the quality of the service is better. To overcome all the risk factors it is also
important to identify all the risks and to understand the reasons behind the possible risks. It is
also understood that there is a basic difference between the risk and the uncertainties as the risk
can be controlled but the uncertainties cannot be controlled and mitigated. All the challenges
which are faced by the VIC government in case of making the risk management regulations are
also discussed with respect to the internal and the external risks.
according to the value of the information. The organisations also follow the regulations in
Case of sharing the information with other organisations.
Conclusion
From the above discussion it is concluded that several organisations face a lot of risk
factors and to make the information secured all the regulations which are made by the VIC
government, should be followed properly. Public personal information is the most important data
from the security point of view. Organisations give public information the highest priority. The
main advantage making the system more secured is that the public reliability is increased on the
organisation and also the quality of the service is better. To overcome all the risk factors it is also
important to identify all the risks and to understand the reasons behind the possible risks. It is
also understood that there is a basic difference between the risk and the uncertainties as the risk
can be controlled but the uncertainties cannot be controlled and mitigated. All the challenges
which are faced by the VIC government in case of making the risk management regulations are
also discussed with respect to the internal and the external risks.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 16
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





