Gigantic Corp: IT Risk Management and Cyber Security Project Report
VerifiedAdded on 2023/06/04
|20
|4610
|231
Report
AI Summary
This report focuses on IT risk management within the context of cyber security, using the case study of Gigantic Corporation's cryptography project. It outlines the role of an IT risk assessment lead consultant in translating technical issues into risk language for stakeholders. The report defines cyber security, its components (including application, network, and data security), and identifies key threats such as phishing, Trojan horses, ransomware, DDoS attacks, and others. A risk assessment table categorizes the level of risk for each threat, followed by an analysis of consequences based on the IT control framework. The report emphasizes the importance of cryptography in securing systems and suggests various protection mechanisms. The report highlights the need for proactive measures to mitigate identified risks and protect sensitive information within the organization. Finally, the report emphasizes the importance of applying these principles to protect sensitive information within the organization.

Running head: IT RISK MANAGEMENT
IT Risk Management: Cyber Security
Name of the Student
Name of the University
Author’s Note:
IT Risk Management: Cyber Security
Name of the Student
Name of the University
Author’s Note:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
IT RISK MANAGEMENT
Table of Contents
Executive Summary...................................................................................................................2
Introduction................................................................................................................................4
Risk Assessment.........................................................................................................................4
Various Threats and Vulnerabilities in Cyber Security.........................................................4
Risk Assessment on the Identified Risks in the Cyber Security............................................7
Consequences of the Identified Risks derived from IT Control Framework.........................9
Recommendations for the Project........................................................................................10
Mitigation of Risks and Impact on the System....................................................................11
Literature Review.....................................................................................................................13
Protection Mechanisms Required for Information Security in the Project..........................13
Conclusion................................................................................................................................15
References................................................................................................................................17
IT RISK MANAGEMENT
Table of Contents
Executive Summary...................................................................................................................2
Introduction................................................................................................................................4
Risk Assessment.........................................................................................................................4
Various Threats and Vulnerabilities in Cyber Security.........................................................4
Risk Assessment on the Identified Risks in the Cyber Security............................................7
Consequences of the Identified Risks derived from IT Control Framework.........................9
Recommendations for the Project........................................................................................10
Mitigation of Risks and Impact on the System....................................................................11
Literature Review.....................................................................................................................13
Protection Mechanisms Required for Information Security in the Project..........................13
Conclusion................................................................................................................................15
References................................................................................................................................17

2
IT RISK MANAGEMENT
Executive Summary
The major objective of this report is to learn about the case study of Gigantic Corporation.
The organization would be eventually executing a significant project on the cyber security,
known as Cryptography. This particular organization has hired a specific information
technology risk assessment lead consultant within their company. The major role of the
information technology risk assessment lead consultant will be providing the significant
interface within the technologists as well as the respective business stakeholders. Moreover,
this particular risk assessment consultant will have to translate the significant technical
difficulties and issues to the risk language with the core purpose of facilitating the efficient as
well as effective process of decision making by their stakeholders.
The cyber security can be described as the basic protection of various internet connected
systems that involve the hardware, data and software from all types of cyber attacks. Within
the context of computing, this security consists of two distinct kinds, which are physical
security and cyber security. These two types of securities are being utilized by the
organizations for properly protecting against any type of unauthorized or unauthenticated
access to the data centres or the computer based systems. The information security that is
being designed for the proper maintenance of CIA or confidentiality, integrity and the
availability of sensitive data is the major subset of this cyber security. The main elements of
this cyber security that need the proper coordination of the efforts within any information
system are application securities, information security, network security, business continuity
planning, disaster recovery, operational security as well as the end user education.
The organization of Gigantic Corporation Company has eventually hired the significant
information technology risk assessment leading consultant for the basic purpose to identify
the several IT related risks in the project of cryptography as well as cryptographic algorithms.
IT RISK MANAGEMENT
Executive Summary
The major objective of this report is to learn about the case study of Gigantic Corporation.
The organization would be eventually executing a significant project on the cyber security,
known as Cryptography. This particular organization has hired a specific information
technology risk assessment lead consultant within their company. The major role of the
information technology risk assessment lead consultant will be providing the significant
interface within the technologists as well as the respective business stakeholders. Moreover,
this particular risk assessment consultant will have to translate the significant technical
difficulties and issues to the risk language with the core purpose of facilitating the efficient as
well as effective process of decision making by their stakeholders.
The cyber security can be described as the basic protection of various internet connected
systems that involve the hardware, data and software from all types of cyber attacks. Within
the context of computing, this security consists of two distinct kinds, which are physical
security and cyber security. These two types of securities are being utilized by the
organizations for properly protecting against any type of unauthorized or unauthenticated
access to the data centres or the computer based systems. The information security that is
being designed for the proper maintenance of CIA or confidentiality, integrity and the
availability of sensitive data is the major subset of this cyber security. The main elements of
this cyber security that need the proper coordination of the efforts within any information
system are application securities, information security, network security, business continuity
planning, disaster recovery, operational security as well as the end user education.
The organization of Gigantic Corporation Company has eventually hired the significant
information technology risk assessment leading consultant for the basic purpose to identify
the several IT related risks in the project of cryptography as well as cryptographic algorithms.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3
IT RISK MANAGEMENT
The specific cryptographic algorithms and techniques are majorly responsible for securing
the cyber related issues within any particular system. Cryptography is the basic practice of
several techniques that help to secure confidential data or information in the significant
presence of the adversaries or third parties. Cryptography majorly depends on the proper
construction as well as analysis of the protocols, which could eventually prevent the third
parties or even the public from simply reading the several private messages as well as the
several features within the information security like the data confidentiality, integrity, non
repudiation, availability and finally authorization or authentication. The various applications
of this cryptography majorly involve the digital currencies, confidential data
communications, electronic commerce, computerized passwords and various others. The
cryptographic algorithms are eventually designed for various assumptions and hence these
algorithms are quite tough for breaking by the adversaries.
Cryptography is considered as the basic threat within cyber security. The Gigantic
Corporation Company has hence chosen the specific project of Cryptographic algorithms for
the area of cyber security. There are various types of threats within the cyber security.
Amongst them, the most significant threats are social engineered Trojans, phishing, advanced
persistent threat, unpatched software like Flash, Adobe Reader and Java, botnets,
ransomware, distributed denial of service attacks, data manipulation, and malware, man in the
middle attacks, network travelling worms and various others. These above mentioned cyber
threats are extremely vulnerable and destructive for the information systems and hence
should be mitigated with proper measures.
The report has clearly identified each and every risk related to their area of cyber security and
could be then mitigated by undertaking some of the most significant and proper measures of
cryptography within this company called Gigantic Corporation. Their information technology
risk assessment leading consultant has recognized and the consequences are also provided.
IT RISK MANAGEMENT
The specific cryptographic algorithms and techniques are majorly responsible for securing
the cyber related issues within any particular system. Cryptography is the basic practice of
several techniques that help to secure confidential data or information in the significant
presence of the adversaries or third parties. Cryptography majorly depends on the proper
construction as well as analysis of the protocols, which could eventually prevent the third
parties or even the public from simply reading the several private messages as well as the
several features within the information security like the data confidentiality, integrity, non
repudiation, availability and finally authorization or authentication. The various applications
of this cryptography majorly involve the digital currencies, confidential data
communications, electronic commerce, computerized passwords and various others. The
cryptographic algorithms are eventually designed for various assumptions and hence these
algorithms are quite tough for breaking by the adversaries.
Cryptography is considered as the basic threat within cyber security. The Gigantic
Corporation Company has hence chosen the specific project of Cryptographic algorithms for
the area of cyber security. There are various types of threats within the cyber security.
Amongst them, the most significant threats are social engineered Trojans, phishing, advanced
persistent threat, unpatched software like Flash, Adobe Reader and Java, botnets,
ransomware, distributed denial of service attacks, data manipulation, and malware, man in the
middle attacks, network travelling worms and various others. These above mentioned cyber
threats are extremely vulnerable and destructive for the information systems and hence
should be mitigated with proper measures.
The report has clearly identified each and every risk related to their area of cyber security and
could be then mitigated by undertaking some of the most significant and proper measures of
cryptography within this company called Gigantic Corporation. Their information technology
risk assessment leading consultant has recognized and the consequences are also provided.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4
IT RISK MANAGEMENT
Introduction
The computer security or cyber security is the basic security or protection of the
computerized systems from any type of theft as well as damage to the respective software,
hardware or the electronic data (Von Solms & Van Niekerk, 2013). This cyber security is
also effective from the misdirection and disruption of these services that are being provided.
The reliance on the computers are subsequently incrementing and the wireless networks like
wireless fidelity and Bluetooth as well as the Internet connectivity are becoming quite
popular. The proper growth of the smart devices such as smart televisions and smart phones
or the several tiny devices together constitutes the technology of Internet of Things. There are
some of the major threats and vulnerabilities within this cyber security and hence these
threats should be properly mitigated on time to avoid all types of complexities and issues
(Wang & Lu, 2013)). The following report will be outlining the basic description about
Gigantic Corporation Company as well as their project. The risk assessment will be
eventually done for each and every identified risk or the consequences of these risks as per
the framework of IT control. Moreover, several mechanisms of protection would also be
provided here.
Risk Assessment
Various Threats and Vulnerabilities in Cyber Security
The cyber security is the processes, practices and technologies that are designed for
the protection of the networks, programs, devices as well as data from any type of threat or
attack, unauthorized access or even damages (Hahn et al., 2013). It is also referred to as the
security of information security. The cyber security is extremely important since the
corporate, financial as well as the government organizations eventually collect, process,
IT RISK MANAGEMENT
Introduction
The computer security or cyber security is the basic security or protection of the
computerized systems from any type of theft as well as damage to the respective software,
hardware or the electronic data (Von Solms & Van Niekerk, 2013). This cyber security is
also effective from the misdirection and disruption of these services that are being provided.
The reliance on the computers are subsequently incrementing and the wireless networks like
wireless fidelity and Bluetooth as well as the Internet connectivity are becoming quite
popular. The proper growth of the smart devices such as smart televisions and smart phones
or the several tiny devices together constitutes the technology of Internet of Things. There are
some of the major threats and vulnerabilities within this cyber security and hence these
threats should be properly mitigated on time to avoid all types of complexities and issues
(Wang & Lu, 2013)). The following report will be outlining the basic description about
Gigantic Corporation Company as well as their project. The risk assessment will be
eventually done for each and every identified risk or the consequences of these risks as per
the framework of IT control. Moreover, several mechanisms of protection would also be
provided here.
Risk Assessment
Various Threats and Vulnerabilities in Cyber Security
The cyber security is the processes, practices and technologies that are designed for
the protection of the networks, programs, devices as well as data from any type of threat or
attack, unauthorized access or even damages (Hahn et al., 2013). It is also referred to as the
security of information security. The cyber security is extremely important since the
corporate, financial as well as the government organizations eventually collect, process,

5
IT RISK MANAGEMENT
manipulate and finally store the unprecedented data amount within the computer systems or
any other devices. The major elements of cyber security solely includes network security,
application security, end point security, data security, cloud security, identity management,
database security, infrastructure security, disaster recovery, mobile security, BCP or business
continuity planning and many more (Amin et al., 2013). The organization of Gigantic
Corporation might be facing some of the major risks and threats related to their area of cyber
security. The most significant and vital threats and risks to this specific area of cyber security
are given below:
i) Phishing: The first and the foremost threat to cyber security within the company of
Gigantic Corporation is this phishing. This is the fraudulent attempt for the purpose of
obtaining any sensitive information like the usernames, credentials of credit cards or
passwords for the purpose of spreading malicious activities (Buczak & Guven, 2016). The
hacker disguises himself as the most trustworthy entity within an electronic communication.
ii) Trojan Horses: This Trojan horse is the specific malicious program, which present
itself as the most legal software in front of the users. This particular computer program is
responsible for hiding malware as a normal program.
iii) Ransomware: Another important and significant threat or issue for the cyber
security for Gigantic Corporation organization is the ransomware or ransom malware
(Elmaghraby & Losavio, 2014). It is the kind of malware, which eventually prevents the
users from subsequent accessing of the systems as well as personal files. Next, he demands
for ransom payment for the purpose of regaining their authorized access.
iv) Distributed Denial of Service Attacks: The DDoS or distributed denial of service
attack is the fourth significant cyber attack, where this perpetrator could seek into the
machine as well as network resources for making it absolutely unavailable for all the
IT RISK MANAGEMENT
manipulate and finally store the unprecedented data amount within the computer systems or
any other devices. The major elements of cyber security solely includes network security,
application security, end point security, data security, cloud security, identity management,
database security, infrastructure security, disaster recovery, mobile security, BCP or business
continuity planning and many more (Amin et al., 2013). The organization of Gigantic
Corporation might be facing some of the major risks and threats related to their area of cyber
security. The most significant and vital threats and risks to this specific area of cyber security
are given below:
i) Phishing: The first and the foremost threat to cyber security within the company of
Gigantic Corporation is this phishing. This is the fraudulent attempt for the purpose of
obtaining any sensitive information like the usernames, credentials of credit cards or
passwords for the purpose of spreading malicious activities (Buczak & Guven, 2016). The
hacker disguises himself as the most trustworthy entity within an electronic communication.
ii) Trojan Horses: This Trojan horse is the specific malicious program, which present
itself as the most legal software in front of the users. This particular computer program is
responsible for hiding malware as a normal program.
iii) Ransomware: Another important and significant threat or issue for the cyber
security for Gigantic Corporation organization is the ransomware or ransom malware
(Elmaghraby & Losavio, 2014). It is the kind of malware, which eventually prevents the
users from subsequent accessing of the systems as well as personal files. Next, he demands
for ransom payment for the purpose of regaining their authorized access.
iv) Distributed Denial of Service Attacks: The DDoS or distributed denial of service
attack is the fourth significant cyber attack, where this perpetrator could seek into the
machine as well as network resources for making it absolutely unavailable for all the
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6
IT RISK MANAGEMENT
authorized and intended users wither by indefinitely or by temporarily disrupting the services
of that host that is being connected to the connectivity of Internet.
v) Man in the Middle Attacks: The next vital and noteworthy threat within the cyber
security is the man in the middle attack, in which the hacker or the attacker secretly or
stealthily relays the private message between two authorized parties (Ning, Liu & Yang,
2013). This attacker even alters the messages and hence a modified message reaches to the
receiver. The best example of this type of attack is the eavesdropping, where the attacker
intercepts the messages and then inject the new and the modified versions of messages.
vi) Botnets: Another important and significant threat for the cyber security is the
botnet threat. This botnet is the number of the Internet connected devices; each of these
devices is running one or more bots (Dunn Cavelty, 2013). The botnets are the major
requirements for utilizing to perform the DDoS or distributed denial of service attack or send
spam messages and stealing the data. The attacker gets the scope to access these Internet
connected devices as well as the connectivity.
vii) Data Manipulation: The next significant threat or issue that this specific
organization of Gigantic Corporation will be facing in their area of cyber security is the
significant manipulation of the confidential or sensitive data or information (Sou, Sandberg &
Johansson, 2013). This is the procedure of changing the data for making it much easier to be
read and even to be more organized.
viii) Advanced Persistent Threats: This is the set of continuous and stealthy
procedures of computer hacking by the hackers for the purpose of targeting a typical entity.
Gigantic Corporation is often vulnerable to this type of threat.
IT RISK MANAGEMENT
authorized and intended users wither by indefinitely or by temporarily disrupting the services
of that host that is being connected to the connectivity of Internet.
v) Man in the Middle Attacks: The next vital and noteworthy threat within the cyber
security is the man in the middle attack, in which the hacker or the attacker secretly or
stealthily relays the private message between two authorized parties (Ning, Liu & Yang,
2013). This attacker even alters the messages and hence a modified message reaches to the
receiver. The best example of this type of attack is the eavesdropping, where the attacker
intercepts the messages and then inject the new and the modified versions of messages.
vi) Botnets: Another important and significant threat for the cyber security is the
botnet threat. This botnet is the number of the Internet connected devices; each of these
devices is running one or more bots (Dunn Cavelty, 2013). The botnets are the major
requirements for utilizing to perform the DDoS or distributed denial of service attack or send
spam messages and stealing the data. The attacker gets the scope to access these Internet
connected devices as well as the connectivity.
vii) Data Manipulation: The next significant threat or issue that this specific
organization of Gigantic Corporation will be facing in their area of cyber security is the
significant manipulation of the confidential or sensitive data or information (Sou, Sandberg &
Johansson, 2013). This is the procedure of changing the data for making it much easier to be
read and even to be more organized.
viii) Advanced Persistent Threats: This is the set of continuous and stealthy
procedures of computer hacking by the hackers for the purpose of targeting a typical entity.
Gigantic Corporation is often vulnerable to this type of threat.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
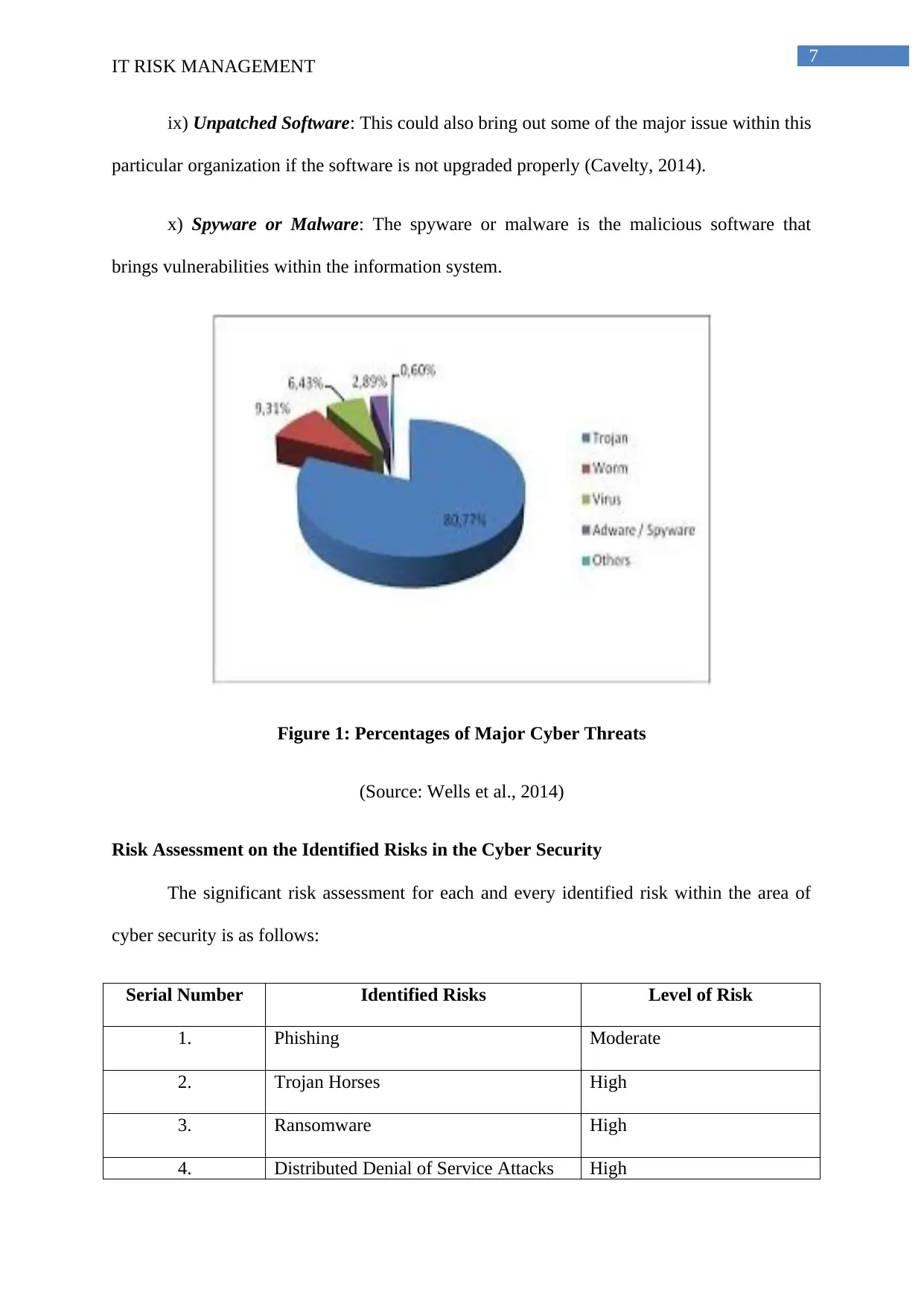
7
IT RISK MANAGEMENT
ix) Unpatched Software: This could also bring out some of the major issue within this
particular organization if the software is not upgraded properly (Cavelty, 2014).
x) Spyware or Malware: The spyware or malware is the malicious software that
brings vulnerabilities within the information system.
Figure 1: Percentages of Major Cyber Threats
(Source: Wells et al., 2014)
Risk Assessment on the Identified Risks in the Cyber Security
The significant risk assessment for each and every identified risk within the area of
cyber security is as follows:
Serial Number Identified Risks Level of Risk
1. Phishing Moderate
2. Trojan Horses High
3. Ransomware High
4. Distributed Denial of Service Attacks High
IT RISK MANAGEMENT
ix) Unpatched Software: This could also bring out some of the major issue within this
particular organization if the software is not upgraded properly (Cavelty, 2014).
x) Spyware or Malware: The spyware or malware is the malicious software that
brings vulnerabilities within the information system.
Figure 1: Percentages of Major Cyber Threats
(Source: Wells et al., 2014)
Risk Assessment on the Identified Risks in the Cyber Security
The significant risk assessment for each and every identified risk within the area of
cyber security is as follows:
Serial Number Identified Risks Level of Risk
1. Phishing Moderate
2. Trojan Horses High
3. Ransomware High
4. Distributed Denial of Service Attacks High

8
IT RISK MANAGEMENT
5. Man in the Middle Attacks High
6. Botnets Low
7. Data Manipulation Moderate
8. Advanced Persistent Threats Low
9. Unpatched Software Low
10. Spyware or Malware Moderate
Table 1: Risk Assessment of the Identified Risks in the Cyber Security
This above given table has eventually assessed each and every identified risks for this
area of cyber security and these must be mitigated within time to stop the enhancement of the
vulnerabilities (Sommestad, Ekstedt & Holm, 2013).
IT RISK MANAGEMENT
5. Man in the Middle Attacks High
6. Botnets Low
7. Data Manipulation Moderate
8. Advanced Persistent Threats Low
9. Unpatched Software Low
10. Spyware or Malware Moderate
Table 1: Risk Assessment of the Identified Risks in the Cyber Security
This above given table has eventually assessed each and every identified risks for this
area of cyber security and these must be mitigated within time to stop the enhancement of the
vulnerabilities (Sommestad, Ekstedt & Holm, 2013).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9
IT RISK MANAGEMENT
Figure 2: Cyber Security
(Source: Abawajy, 2014)
Consequences of the Identified Risks derived from IT Control Framework
The information technology control framework or the IT control framework, which is
the data structure, is solely responsible for organizing as well as categorizing the internal
controls of the company (McGraw, 2013). There are certain practices or procedures that are
established for the proper creation of the business value and then minimizing the threats and
risks. This particular framework is subsequently designed for providing a specific model,
which could be used by the corporations for running the efficient or well controlled financial
environment. The major components of this framework are internal control environment,
setting of objectives, event identifications, risk assessment and response, the control actions
and many more (Cherdantseva et al., 2016).
The various consequences of all the identified risks according to the IT control
framework are as follows:
i) Phishing: The consequence for the threat of phishing is moderate as per the control
framework as the risk can be mitigated by undertaking some counter measures.
ii) Trojan Horses: The consequence for the threat of Trojan horse is major as the
policies and procedures could not stop this risk (Amin et al., 2013).
iii) Ransomware: The consequence for this threat of ransomware is major since
procedures or policies of IT control framework cannot resist the risk.
iv) Distributed Denial of Service Attacks: The consequence for this threat of DDoS
attack is major as this framework cannot resist the risk.
IT RISK MANAGEMENT
Figure 2: Cyber Security
(Source: Abawajy, 2014)
Consequences of the Identified Risks derived from IT Control Framework
The information technology control framework or the IT control framework, which is
the data structure, is solely responsible for organizing as well as categorizing the internal
controls of the company (McGraw, 2013). There are certain practices or procedures that are
established for the proper creation of the business value and then minimizing the threats and
risks. This particular framework is subsequently designed for providing a specific model,
which could be used by the corporations for running the efficient or well controlled financial
environment. The major components of this framework are internal control environment,
setting of objectives, event identifications, risk assessment and response, the control actions
and many more (Cherdantseva et al., 2016).
The various consequences of all the identified risks according to the IT control
framework are as follows:
i) Phishing: The consequence for the threat of phishing is moderate as per the control
framework as the risk can be mitigated by undertaking some counter measures.
ii) Trojan Horses: The consequence for the threat of Trojan horse is major as the
policies and procedures could not stop this risk (Amin et al., 2013).
iii) Ransomware: The consequence for this threat of ransomware is major since
procedures or policies of IT control framework cannot resist the risk.
iv) Distributed Denial of Service Attacks: The consequence for this threat of DDoS
attack is major as this framework cannot resist the risk.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10
IT RISK MANAGEMENT
v) Man in the Middle Attacks: The consequence for this threat of man in the middle
attack is major since the policies and procedures will not be resisted.
vi) Botnets: The consequence for this threat of botnet is minor as it is easier to stop
this threat (Knowles et al., 2015).
vii) Data Manipulation: The consequence for the threat of data manipulation is
moderate as per the control framework as the risk can be mitigated by undertaking some
counter measures.
viii) Advanced Persistent Threats: The consequence for this threat of APT is minor
as it is easier to stop this threat (Hong, Liu & Govindarasu, 2014).
ix) Unpatched Software: The consequence for this threat of unpatched software is
minor as it is easier to stop this threat.
x) Spyware or Malware: The consequence for the threat of spyware or malware is
moderate according to the control framework as the risk can be mitigated by undertaking
some counter measures.
Recommendations for the Project
The significant recommendations for this project of cryptography within the
organization of Gigantic Corporation, so that it could easily mitigate the identified problems
of cyber security are given below:
i) Using Asymmetric Key Algorithms: The first and the foremost recommendation for
the project in Gigantic Corporation is utilizing the asymmetric key algorithm (Luiijf,
Besseling & De Graaf, 2013). This is considered as one of the major and the most secured
algorithm of cryptography. The decryption keys are produced with the help of this particular
algorithm. The most widely utilized algorithm of the asymmetric key is the RSA or Rivest
IT RISK MANAGEMENT
v) Man in the Middle Attacks: The consequence for this threat of man in the middle
attack is major since the policies and procedures will not be resisted.
vi) Botnets: The consequence for this threat of botnet is minor as it is easier to stop
this threat (Knowles et al., 2015).
vii) Data Manipulation: The consequence for the threat of data manipulation is
moderate as per the control framework as the risk can be mitigated by undertaking some
counter measures.
viii) Advanced Persistent Threats: The consequence for this threat of APT is minor
as it is easier to stop this threat (Hong, Liu & Govindarasu, 2014).
ix) Unpatched Software: The consequence for this threat of unpatched software is
minor as it is easier to stop this threat.
x) Spyware or Malware: The consequence for the threat of spyware or malware is
moderate according to the control framework as the risk can be mitigated by undertaking
some counter measures.
Recommendations for the Project
The significant recommendations for this project of cryptography within the
organization of Gigantic Corporation, so that it could easily mitigate the identified problems
of cyber security are given below:
i) Using Asymmetric Key Algorithms: The first and the foremost recommendation for
the project in Gigantic Corporation is utilizing the asymmetric key algorithm (Luiijf,
Besseling & De Graaf, 2013). This is considered as one of the major and the most secured
algorithm of cryptography. The decryption keys are produced with the help of this particular
algorithm. The most widely utilized algorithm of the asymmetric key is the RSA or Rivest

11
IT RISK MANAGEMENT
Shamir Adleman. This is being embedded within the protocol of SSL and TLS for the
purpose of providing the communication security within the computer network. This is the
public key cryptography that utilizes the public as well as the private keys for the encryption
or decryption of the confidential and sensitive data. All of these keys are larger numbers,
which are paired together. One of this key within the pair is shared with all the members and
hence is known as public key (Fielder et al., 2016). The next key within the pair is kept secret
and is termed as private key.
ii) Hybrid Encryption: The second recommendation for their project of cryptography
is hybrid encryption. It is the method of encryption, which merges two and more encryption
techniques. It hence incorporates the combination of symmetric and asymmetric encryption
or providing advantages from the encryption technique (Bada & Sasse, 2014). It would be
extremely safe and secured for Gigantic Corporation to provide security from cyber threats.
Mitigation of Risks and Impact on the System
The proper risk mitigation of the identified risks for the cyber threats are as follows:
i) Implementation of Firewalls: The next important technique to mitigate the
identified risks of cyber security is the proper implementation of the firewalls. These threats
are easily detected as well as prevented by undertaking the help of firewalls as the incoming
or outgoing traffic of the network security system is monitored and controlled as per the
previously determined security rules (Ashok, Hahn & Govindarasu, 2014). Network firewalls
are the best type of firewalls that would be effective for the proper detection of untrusted
external network and internal network.
IT RISK MANAGEMENT
Shamir Adleman. This is being embedded within the protocol of SSL and TLS for the
purpose of providing the communication security within the computer network. This is the
public key cryptography that utilizes the public as well as the private keys for the encryption
or decryption of the confidential and sensitive data. All of these keys are larger numbers,
which are paired together. One of this key within the pair is shared with all the members and
hence is known as public key (Fielder et al., 2016). The next key within the pair is kept secret
and is termed as private key.
ii) Hybrid Encryption: The second recommendation for their project of cryptography
is hybrid encryption. It is the method of encryption, which merges two and more encryption
techniques. It hence incorporates the combination of symmetric and asymmetric encryption
or providing advantages from the encryption technique (Bada & Sasse, 2014). It would be
extremely safe and secured for Gigantic Corporation to provide security from cyber threats.
Mitigation of Risks and Impact on the System
The proper risk mitigation of the identified risks for the cyber threats are as follows:
i) Implementation of Firewalls: The next important technique to mitigate the
identified risks of cyber security is the proper implementation of the firewalls. These threats
are easily detected as well as prevented by undertaking the help of firewalls as the incoming
or outgoing traffic of the network security system is monitored and controlled as per the
previously determined security rules (Ashok, Hahn & Govindarasu, 2014). Network firewalls
are the best type of firewalls that would be effective for the proper detection of untrusted
external network and internal network.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 20
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




