IT Risk Management Report
VerifiedAdded on 2020/03/16
|15
|3004
|30
Report
AI Summary
The report discusses IT risk management, focusing on the threats posed by big data technology. It highlights the role of ENISA in providing security measures and recommendations to mitigate risks associated with data breaches and cyber threats. The report covers various types of threats, including accidental and deliberate threats, and emphasizes the importance of implementing robust security protocols to protect sensitive information.

0
IT RISK MANAGEMENT
Name of the Student
Name of the University
Authors Note:
IT RISK MANAGEMENT
Name of the Student
Name of the University
Authors Note:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
IT RISK MANAGEMENT
Table of Contents
Introduction..........................................................................................................................2
Question 1............................................................................................................................3
Question 2............................................................................................................................4
Question 3............................................................................................................................5
Question 4............................................................................................................................6
Question 5............................................................................................................................7
References............................................................................................................................8
IT RISK MANAGEMENT
Table of Contents
Introduction..........................................................................................................................2
Question 1............................................................................................................................3
Question 2............................................................................................................................4
Question 3............................................................................................................................5
Question 4............................................................................................................................6
Question 5............................................................................................................................7
References............................................................................................................................8

2
IT RISK MANAGEMENT
Introduction
The following report is all about risk analysis and security is vital for the firm to
implement proper operation and integration of workflow for development of the system.
Development of the given project will ultimately help in development of operation and applying
proper methods for analyzing the risk associated with given firm. Operational analysis
emphasizes on checking various risks of organization. The report is all about European union
Agency and information security is nothing but a network center and security of information
experts for private sector and various European citizen. ENISA works with the following sectors
and aims in providing advice for good practice in information security.
In this report ENISA emphasizes on various threats to Big data technology which plays a
key role in various parts like health, food security, climate and various sources of energy. Big
data technology has a high level of replication in data storage portion and frequent outsourcing
of Big Data technology often leads to breach, leakage and others threats which are specific to
this big data technology. Additional information created by Big data can increase the effect of
data leaks and various breaches.
IT RISK MANAGEMENT
Introduction
The following report is all about risk analysis and security is vital for the firm to
implement proper operation and integration of workflow for development of the system.
Development of the given project will ultimately help in development of operation and applying
proper methods for analyzing the risk associated with given firm. Operational analysis
emphasizes on checking various risks of organization. The report is all about European union
Agency and information security is nothing but a network center and security of information
experts for private sector and various European citizen. ENISA works with the following sectors
and aims in providing advice for good practice in information security.
In this report ENISA emphasizes on various threats to Big data technology which plays a
key role in various parts like health, food security, climate and various sources of energy. Big
data technology has a high level of replication in data storage portion and frequent outsourcing
of Big Data technology often leads to breach, leakage and others threats which are specific to
this big data technology. Additional information created by Big data can increase the effect of
data leaks and various breaches.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3
IT RISK MANAGEMENT
Question 1
The report is all about European union Agency and information security is nothing but a
center of network and security of information for private sector and various European citizen.
ENISA works with the following sectors and aims in providing advice for good practice in
information security. In this report ENISA emphasizes on various threats to Big data technology
which plays a key role in various parts like health, food security, climate and various sources of
energy (Bartsch & Frey, 2017). Big Data is more often useful for collecting data for various
algorithms, technology and various system (Bendiek,2015). There are mainly source of big data
that is mobile communication device and networks and various web based application. Since the
use of big data technology has increased a lot in the last few years with different adaptation for
proper adaptation. Big data technology can help in increasing the productivity and provides
better decision making in various organization (Bastl, Mareš, & Tvrdá, 2015). It can be expected
that it can have all the data with application in various domains like science, business and
military. On the contrary Big data technology has a various number of risk. Different Big data
system are becoming more prone to attacks caused by hackers and threat agents.
Big data technology has a high level of replication in data storage portion and frequent
outsourcing of Big Data technology often leads to breach, leakage and others threats which are
specific to this big data technology (Catteddu & Hogben, 2015). Additional information created
by Big data can increase the effect of data leaks and various breaches (Christou, 2017). Interest
of various big data owners like data owners, data transformers, computation and storage in the
big data area may lead to some conflict which ultimately leads to the creation of complex
ecosystem where various security measures should be carefully planned and executed (Eininger,
Skopik & Fiedler, 2015).
IT RISK MANAGEMENT
Question 1
The report is all about European union Agency and information security is nothing but a
center of network and security of information for private sector and various European citizen.
ENISA works with the following sectors and aims in providing advice for good practice in
information security. In this report ENISA emphasizes on various threats to Big data technology
which plays a key role in various parts like health, food security, climate and various sources of
energy (Bartsch & Frey, 2017). Big Data is more often useful for collecting data for various
algorithms, technology and various system (Bendiek,2015). There are mainly source of big data
that is mobile communication device and networks and various web based application. Since the
use of big data technology has increased a lot in the last few years with different adaptation for
proper adaptation. Big data technology can help in increasing the productivity and provides
better decision making in various organization (Bastl, Mareš, & Tvrdá, 2015). It can be expected
that it can have all the data with application in various domains like science, business and
military. On the contrary Big data technology has a various number of risk. Different Big data
system are becoming more prone to attacks caused by hackers and threat agents.
Big data technology has a high level of replication in data storage portion and frequent
outsourcing of Big Data technology often leads to breach, leakage and others threats which are
specific to this big data technology (Catteddu & Hogben, 2015). Additional information created
by Big data can increase the effect of data leaks and various breaches (Christou, 2017). Interest
of various big data owners like data owners, data transformers, computation and storage in the
big data area may lead to some conflict which ultimately leads to the creation of complex
ecosystem where various security measures should be carefully planned and executed (Eininger,
Skopik & Fiedler, 2015).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4
IT RISK MANAGEMENT
In this report a set of recommendation for big data threats has been provided like to
change the method of approach of data for proper approach to Big-Data solution, checking the
needs for present standards and planning the definition of given standard, it also focuses on
training of various professional working for the organization, defining proper tools for the
security and privacy protection of Big data in different environment, clearly judging various
assets of Big data and providing solution to overcome various threats and risks.
KNOX can be used to provide important information about the specific ways and
protection of data sources from the time it is added (Exchange, 2016). Ranger can be considered
to be authorized system which manly aims in blocking the access of user to the big data system
(Hänisch & Rogge, 2017). User has to send a request to Ranger before getting an authentication
entry into the system. Encryption is the best way of protection of data from unknown or
unauthenticated source (Jentzsch, 2016). Data is mainly modified using cryptographic technique
do that it becomes wasteful for others. Firewall can be considered to be the best method for
protection from various network issues. Wireless devices lead to formation proper preventive
information issues.
IT RISK MANAGEMENT
In this report a set of recommendation for big data threats has been provided like to
change the method of approach of data for proper approach to Big-Data solution, checking the
needs for present standards and planning the definition of given standard, it also focuses on
training of various professional working for the organization, defining proper tools for the
security and privacy protection of Big data in different environment, clearly judging various
assets of Big data and providing solution to overcome various threats and risks.
KNOX can be used to provide important information about the specific ways and
protection of data sources from the time it is added (Exchange, 2016). Ranger can be considered
to be authorized system which manly aims in blocking the access of user to the big data system
(Hänisch & Rogge, 2017). User has to send a request to Ranger before getting an authentication
entry into the system. Encryption is the best way of protection of data from unknown or
unauthenticated source (Jentzsch, 2016). Data is mainly modified using cryptographic technique
do that it becomes wasteful for others. Firewall can be considered to be the best method for
protection from various network issues. Wireless devices lead to formation proper preventive
information issues.
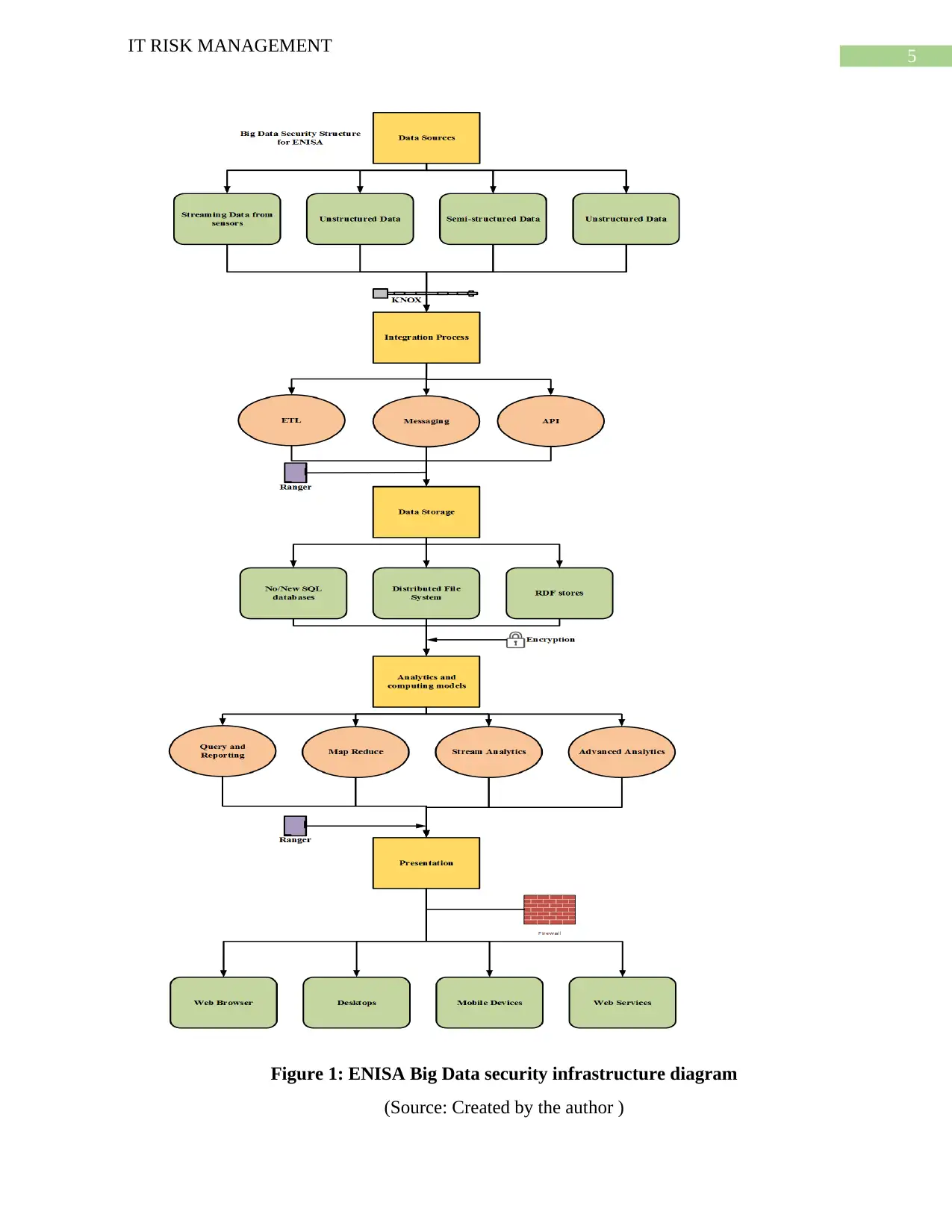
5
IT RISK MANAGEMENT
Figure 1: ENISA Big Data security infrastructure diagram
(Source: Created by the author )
IT RISK MANAGEMENT
Figure 1: ENISA Big Data security infrastructure diagram
(Source: Created by the author )
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6
IT RISK MANAGEMENT
Question 2
Threat agent can be someone or something with proper capabilities with clear intention
of manipulating a record form past activities. For Big data owners it is very important for
keeping a track of the emerging threats (Kleineidam et al., 2017). Various threats of ENISA big
data technology are accidental threats, deliberate threats, threats of technology, organization
threat, legal threats. This threats will ultimately result in the improvisation of ENISA.
Accidental threat are threats which results in damage of records, leakage of data through
various application, losing of storage devices, loss of important information, loss of information
form cloud, damage due to penetration testing, improper design and planning of threat, changing
data by mistake, undependable way of information and various errors cause by human.
Deliberate threats are mainly caused due to problems form network traffic, server issues,
interception of information, driving of wars, hijacking of sessions. Legal threat comprises of
avoidance of regulation, failure to satisfy the requirements, misuse of data containing personal
information.
Threat of Technology abuse are leakage of information, problems with social
engineering, surplus codes, failure in business, service denial, targeted attacks, improper use of
tools, data breach, improper use of audit tools, manipulation of various hardware and software.
Organization threats mainly include various shortage of IT skills.
Threat of Technology abuse is the main critical threat during the implementation of Big
data technology for the upgradation of proper control techniques (Kubicek & Diederich, 2015).
Threat of technology are mainly leaks of information, social engineering, malicious code, failure
of various business process, service of denial, data breach. Threat of Technology is considered to
IT RISK MANAGEMENT
Question 2
Threat agent can be someone or something with proper capabilities with clear intention
of manipulating a record form past activities. For Big data owners it is very important for
keeping a track of the emerging threats (Kleineidam et al., 2017). Various threats of ENISA big
data technology are accidental threats, deliberate threats, threats of technology, organization
threat, legal threats. This threats will ultimately result in the improvisation of ENISA.
Accidental threat are threats which results in damage of records, leakage of data through
various application, losing of storage devices, loss of important information, loss of information
form cloud, damage due to penetration testing, improper design and planning of threat, changing
data by mistake, undependable way of information and various errors cause by human.
Deliberate threats are mainly caused due to problems form network traffic, server issues,
interception of information, driving of wars, hijacking of sessions. Legal threat comprises of
avoidance of regulation, failure to satisfy the requirements, misuse of data containing personal
information.
Threat of Technology abuse are leakage of information, problems with social
engineering, surplus codes, failure in business, service denial, targeted attacks, improper use of
tools, data breach, improper use of audit tools, manipulation of various hardware and software.
Organization threats mainly include various shortage of IT skills.
Threat of Technology abuse is the main critical threat during the implementation of Big
data technology for the upgradation of proper control techniques (Kubicek & Diederich, 2015).
Threat of technology are mainly leaks of information, social engineering, malicious code, failure
of various business process, service of denial, data breach. Threat of Technology is considered to
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7
IT RISK MANAGEMENT
be important threat because major problem in adding of various operations. The abuse of
technology is mainly done for affecting the organization, various problems in integration of
operations. Information leakage can have led to problem of loss of sensitive and important
information from the database which can be misused for personal reasons.
Question 3
Threat agents in the following case study is someone or something with proper
capabilities and having clear intention in manipulating a threat and record from past (Lanfer,
2017). The big data asset owner must be important to be aware of the emerging threats from
different threat agent group. The key threats agents are cyber criminals, insiders, nation-state,
hacktivist, cyber fights, cyber terrorist, script kiddies.
Cyber criminals are considered to be most effective group which records to around two
third of various cases that occur in cybercrimes (Reuter, 2015). The group of cybercrimes has
changed a lot in the last few years. It has progressed and grown in the last few years.
Cybercrimes are famous in eHealth and banking sectors.
Insiders attack the cyber space intentionally in some cases and unintentionally in some
cases. Intention, error and negligence are the main three types of attacks that are mainly
performed by insider of a company. Inside threat mainly attacks the employees or executive
manager of a firm.
Nation state and corporation are together known as cyber spines the military
organizations and various agency of intelligence (Witt & Freudenberg, 2016). The differentiation
between cyber combating and cyber spying are not clear till now because of the lack of maturity
of cyber capabilities.
IT RISK MANAGEMENT
be important threat because major problem in adding of various operations. The abuse of
technology is mainly done for affecting the organization, various problems in integration of
operations. Information leakage can have led to problem of loss of sensitive and important
information from the database which can be misused for personal reasons.
Question 3
Threat agents in the following case study is someone or something with proper
capabilities and having clear intention in manipulating a threat and record from past (Lanfer,
2017). The big data asset owner must be important to be aware of the emerging threats from
different threat agent group. The key threats agents are cyber criminals, insiders, nation-state,
hacktivist, cyber fights, cyber terrorist, script kiddies.
Cyber criminals are considered to be most effective group which records to around two
third of various cases that occur in cybercrimes (Reuter, 2015). The group of cybercrimes has
changed a lot in the last few years. It has progressed and grown in the last few years.
Cybercrimes are famous in eHealth and banking sectors.
Insiders attack the cyber space intentionally in some cases and unintentionally in some
cases. Intention, error and negligence are the main three types of attacks that are mainly
performed by insider of a company. Inside threat mainly attacks the employees or executive
manager of a firm.
Nation state and corporation are together known as cyber spines the military
organizations and various agency of intelligence (Witt & Freudenberg, 2016). The differentiation
between cyber combating and cyber spying are not clear till now because of the lack of maturity
of cyber capabilities.

8
IT RISK MANAGEMENT
Hacktivists have emerged in the year of 2016 and they protest it for discrimination,
corruption, problems of health, help form minorities, various environmental policies. Olympic
games and tournament of football are considered to be active example of hacktivist.
Cyber fights are of aggressive and high capability persons and group lies in grey zone for
ideological values. All over the globe this type of threat is spread uniformly.
Cyber terrorist emphasizes on cyber security and is moving to cyber terrorism as per the
international agreement with different reports of media against the ISIS. Such attacks are not
generally categorized for different cyber-attacks (Weber & Weber, 2015). The main room for
cyber terrorist are hijacking social media and hacking.
Script kiddies are known to be type of attackers are known as copy cats or simple attack.
These type of attack has mainly low intention and low capability which is used for hacking
practices. Script kiddies uses different tools which are available and attack methods to become
dangerous.
To reduce the effect of attack on systems defenders have found out some solution and
have been improvised for adjusting with the different hackers.
Various agencies intend to defend cyber-attacks from all round the globe and proper
infrastructure is needed for it. No statistical proofs of hackers are made from this cybercriminal.
Cybercrime has been capitalized because due increased records at every time.
Monetization has helped a lot in turning over the cyber activities due to some trend.
IT RISK MANAGEMENT
Hacktivists have emerged in the year of 2016 and they protest it for discrimination,
corruption, problems of health, help form minorities, various environmental policies. Olympic
games and tournament of football are considered to be active example of hacktivist.
Cyber fights are of aggressive and high capability persons and group lies in grey zone for
ideological values. All over the globe this type of threat is spread uniformly.
Cyber terrorist emphasizes on cyber security and is moving to cyber terrorism as per the
international agreement with different reports of media against the ISIS. Such attacks are not
generally categorized for different cyber-attacks (Weber & Weber, 2015). The main room for
cyber terrorist are hijacking social media and hacking.
Script kiddies are known to be type of attackers are known as copy cats or simple attack.
These type of attack has mainly low intention and low capability which is used for hacking
practices. Script kiddies uses different tools which are available and attack methods to become
dangerous.
To reduce the effect of attack on systems defenders have found out some solution and
have been improvised for adjusting with the different hackers.
Various agencies intend to defend cyber-attacks from all round the globe and proper
infrastructure is needed for it. No statistical proofs of hackers are made from this cybercriminal.
Cybercrime has been capitalized because due increased records at every time.
Monetization has helped a lot in turning over the cyber activities due to some trend.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9
IT RISK MANAGEMENT
Question 4
ETL stands for ENISA threat landscape group is nothing but a collection of threats and
various process and extensive research (Schneider, 2017). ENISA has faced a number of
performance issue due to database problem and it will ultimately help in development of
slackness operation for various firms. The process of ETL can be improvised by following
practices
Reducing data usage: The technique of batch will be exhausted by considerable amount
of memory storage by taking huge amount of data for its operation. Extraction of minimum data
will be help in improvisation of the performance of data operation.
Avoidance of row-by-row lookup: ETL process emphasizes on the use of row by row
lookup for performing various data operation, when it comes bulk loading this process can be
considered to be time consuming and slower process (Schaumüller-Bichl, & Kolberger, 2016).
ETL bulk loading process is very helpful for checking very huge amount of data when it comes
to operation of data.
IT RISK MANAGEMENT
Question 4
ETL stands for ENISA threat landscape group is nothing but a collection of threats and
various process and extensive research (Schneider, 2017). ENISA has faced a number of
performance issue due to database problem and it will ultimately help in development of
slackness operation for various firms. The process of ETL can be improvised by following
practices
Reducing data usage: The technique of batch will be exhausted by considerable amount
of memory storage by taking huge amount of data for its operation. Extraction of minimum data
will be help in improvisation of the performance of data operation.
Avoidance of row-by-row lookup: ETL process emphasizes on the use of row by row
lookup for performing various data operation, when it comes bulk loading this process can be
considered to be time consuming and slower process (Schaumüller-Bichl, & Kolberger, 2016).
ETL bulk loading process is very helpful for checking very huge amount of data when it comes
to operation of data.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10
IT RISK MANAGEMENT
Question 5
The IT security of ENISA is used for the upgradation of various operations of the
company and protection of structure of big data different threats of security. Security of
information technology is helpful against the protection of present data and information from
various threats and factors of risk (Silva, Rocha & Guimaraes, 2016). Important security in
ENISA are KNOX, Ranger, Firewall and Encryption. The above mentioned parameters has been
setup at a proper layer of Big data structure for ENISA (Unger, 2014).
The present system structure of ENISA is very simple and it has the privacy of data
containing important information for the upgradation of existing techniques. Encryption, KNOX,
firewall and ranger can be considered to be helpful in protection of various layers of Big data.
The implementation of IDS/ IPS can be helpful in protection of network filtration by detecting
and checking the access to ENISA database (Stupka, Horák, & Husák, 2017).
Conclusion
From the above discussion it can be stated that the use of Big data technology has led to
some problem and threats of various information that is processing in an organization. The main
part of the information processing that uses big data technology. Process of ETL can be
improvised by use of low data usage and ignoring lookup row by row. Bulk loading option of
ETL is very helpful for faster processing of huge amount of data in the data operation. KNOX,
Encryption, Ranger, IDS/IPS and firewall can have considered to be useful method for protection
of infiltration of network by checking and blocking the access to ENISA database. Big data
technology has a high level of replication in data storage portion and frequent outsourcing of Big
Data technology often leads to breach, leakage and others threats which are specific to this big
IT RISK MANAGEMENT
Question 5
The IT security of ENISA is used for the upgradation of various operations of the
company and protection of structure of big data different threats of security. Security of
information technology is helpful against the protection of present data and information from
various threats and factors of risk (Silva, Rocha & Guimaraes, 2016). Important security in
ENISA are KNOX, Ranger, Firewall and Encryption. The above mentioned parameters has been
setup at a proper layer of Big data structure for ENISA (Unger, 2014).
The present system structure of ENISA is very simple and it has the privacy of data
containing important information for the upgradation of existing techniques. Encryption, KNOX,
firewall and ranger can be considered to be helpful in protection of various layers of Big data.
The implementation of IDS/ IPS can be helpful in protection of network filtration by detecting
and checking the access to ENISA database (Stupka, Horák, & Husák, 2017).
Conclusion
From the above discussion it can be stated that the use of Big data technology has led to
some problem and threats of various information that is processing in an organization. The main
part of the information processing that uses big data technology. Process of ETL can be
improvised by use of low data usage and ignoring lookup row by row. Bulk loading option of
ETL is very helpful for faster processing of huge amount of data in the data operation. KNOX,
Encryption, Ranger, IDS/IPS and firewall can have considered to be useful method for protection
of infiltration of network by checking and blocking the access to ENISA database. Big data
technology has a high level of replication in data storage portion and frequent outsourcing of Big
Data technology often leads to breach, leakage and others threats which are specific to this big

11
IT RISK MANAGEMENT
data technology. Additional information created by Big data can increase the effect of data leaks
and various breaches. Interest of various big data owners like data owners, data transformers,
computation and storage in the big data area may lead to some conflict which ultimately leads to
the creation of complex ecosystem where various security measures should be carefully planned
and executed.
IT RISK MANAGEMENT
data technology. Additional information created by Big data can increase the effect of data leaks
and various breaches. Interest of various big data owners like data owners, data transformers,
computation and storage in the big data area may lead to some conflict which ultimately leads to
the creation of complex ecosystem where various security measures should be carefully planned
and executed.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 15
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





