IT Risk Management Report: Analysis of Biometric Systems and WSNs
VerifiedAdded on 2020/05/28
|12
|2578
|59
Report
AI Summary
This report provides a comprehensive overview of IT risk management, focusing on key areas such as biometric systems, privacy-enhancing technologies (PET), and wireless sensor networks (WSN). It begins with an introduction to the growing importance of IT security in business organizations and then delves into the applications, advantages, and disadvantages of biometric systems like palm print, face recognition, and gait recognition. The report then explores PETs, explaining their role in enhancing data privacy over the internet, with examples like encryption tools, cookie-cutters, and the Platform for Privacy Preferences. Following this, the report examines wireless sensor networks (WSNs), discussing their architecture, various applications (military, area monitoring, transportation, and health), and associated threats and risks, including denial-of-service attacks, jamming, and wormhole attacks. The report concludes with a summary of the key findings and recommendations for mitigating IT risks.

Running head: IT RISK MANAGEMENT
IT risk management
Name of the Student
Name of the University
Author’s Note
IT risk management
Name of the Student
Name of the University
Author’s Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

2
IT RISK MANAGEMENT
Table of Contents
Introduction......................................................................................................................................3
Biometric Systems...........................................................................................................................3
Privacy Enhancing Technologies (PET)..........................................................................................6
Wireless Sensor Networks (WSN)..................................................................................................7
Conclusion.......................................................................................................................................9
References......................................................................................................................................11
IT RISK MANAGEMENT
Table of Contents
Introduction......................................................................................................................................3
Biometric Systems...........................................................................................................................3
Privacy Enhancing Technologies (PET)..........................................................................................6
Wireless Sensor Networks (WSN)..................................................................................................7
Conclusion.......................................................................................................................................9
References......................................................................................................................................11

3
IT RISK MANAGEMENT
Introduction
Information technology has gained prior attention from different researchers all over the
world. The use of information systems has been increased in the business organizations. Various
advanced devices are being used in the business organization for various purposes including
safety and security.
This report deals with the use of biometric systems in access control systems. The
advantages and disadvantages of these systems are discussed in this report. The use of the
Privacy Enhancing Technologies (PET) has been described properly. Three PETs that are used
over the internet have been explained.
This report outlines the wireless sensor networks (WSNs) and its architectural stack.
Different threats and risks to the WSNs have been identified and critically analyzed in the report.
Some recommendations have been provided at the end of the report.
Biometric Systems
Biometric technology is used to identify and recognize the physical identity of an
individual involving in physical and behavioural characteristics. However, a biometric system is
able to calculate biometric information of a person by comparing the results stored in its database
(Rampini, Sufi & Viswanathan, 2014). There are various applications of the biometric
technology including palm print, face recognition and gait recognition.
Palm Print
Palm print technology has been an emerging technology and accepted by biometric
systems. The processing level of a system includes image acquisition level, feature acquisition
IT RISK MANAGEMENT
Introduction
Information technology has gained prior attention from different researchers all over the
world. The use of information systems has been increased in the business organizations. Various
advanced devices are being used in the business organization for various purposes including
safety and security.
This report deals with the use of biometric systems in access control systems. The
advantages and disadvantages of these systems are discussed in this report. The use of the
Privacy Enhancing Technologies (PET) has been described properly. Three PETs that are used
over the internet have been explained.
This report outlines the wireless sensor networks (WSNs) and its architectural stack.
Different threats and risks to the WSNs have been identified and critically analyzed in the report.
Some recommendations have been provided at the end of the report.
Biometric Systems
Biometric technology is used to identify and recognize the physical identity of an
individual involving in physical and behavioural characteristics. However, a biometric system is
able to calculate biometric information of a person by comparing the results stored in its database
(Rampini, Sufi & Viswanathan, 2014). There are various applications of the biometric
technology including palm print, face recognition and gait recognition.
Palm Print
Palm print technology has been an emerging technology and accepted by biometric
systems. The processing level of a system includes image acquisition level, feature acquisition
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

4
IT RISK MANAGEMENT
level, feature extraction level, match score level and decision level. There are various advantages
of the palm print technology (Meyer & Reniers, 2016). As the palm area is larger than other
body parts, it contains some pattern. Therefore, it provides more secured structure than the
fingerprint. However, this helps in identifying systems in fingerprints. On the other hand, it has
some disadvantages including more processing time during identification of palm prints. The
extraction method used in the palm print technology is complex than other biometric systems.
There are various applications of print palm technology used in different companies including
NEC and PRINTAK, for criminal applications (Brown & Moles, 2014). These companies use
various devices that include palm print technology for monitoring criminal activities around.
Face Recognition
Face Recognition technology has emerged in the recent world in order to provide security
to data and information. The sensor in the system detects the structure if the face and matches
with data stored in its database. Face recognition technology depends on facial expression of
humans. Face detection methodology helps in detecting facial expression and structure regardless
of their position, scale and illuminations (McNeil, Frey & Embrechts, 2015). Various techniques
are used for detecting a face of humans including knowledge-based face detection, Structural
matching detection, Appearance-based detecting and template matching. There are various
advantages of the face recognition technology including face detection even having two identical
twins. However, it creates difficulties in matching face structure with original structure stored in
a database. It does not work of wearing a mask on face. It creates difficulties during enrollment.
This technology is used in providing access control to various devices including cameras, mobile
phones and computers.
Gait Recognition
IT RISK MANAGEMENT
level, feature extraction level, match score level and decision level. There are various advantages
of the palm print technology (Meyer & Reniers, 2016). As the palm area is larger than other
body parts, it contains some pattern. Therefore, it provides more secured structure than the
fingerprint. However, this helps in identifying systems in fingerprints. On the other hand, it has
some disadvantages including more processing time during identification of palm prints. The
extraction method used in the palm print technology is complex than other biometric systems.
There are various applications of print palm technology used in different companies including
NEC and PRINTAK, for criminal applications (Brown & Moles, 2014). These companies use
various devices that include palm print technology for monitoring criminal activities around.
Face Recognition
Face Recognition technology has emerged in the recent world in order to provide security
to data and information. The sensor in the system detects the structure if the face and matches
with data stored in its database. Face recognition technology depends on facial expression of
humans. Face detection methodology helps in detecting facial expression and structure regardless
of their position, scale and illuminations (McNeil, Frey & Embrechts, 2015). Various techniques
are used for detecting a face of humans including knowledge-based face detection, Structural
matching detection, Appearance-based detecting and template matching. There are various
advantages of the face recognition technology including face detection even having two identical
twins. However, it creates difficulties in matching face structure with original structure stored in
a database. It does not work of wearing a mask on face. It creates difficulties during enrollment.
This technology is used in providing access control to various devices including cameras, mobile
phones and computers.
Gait Recognition
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
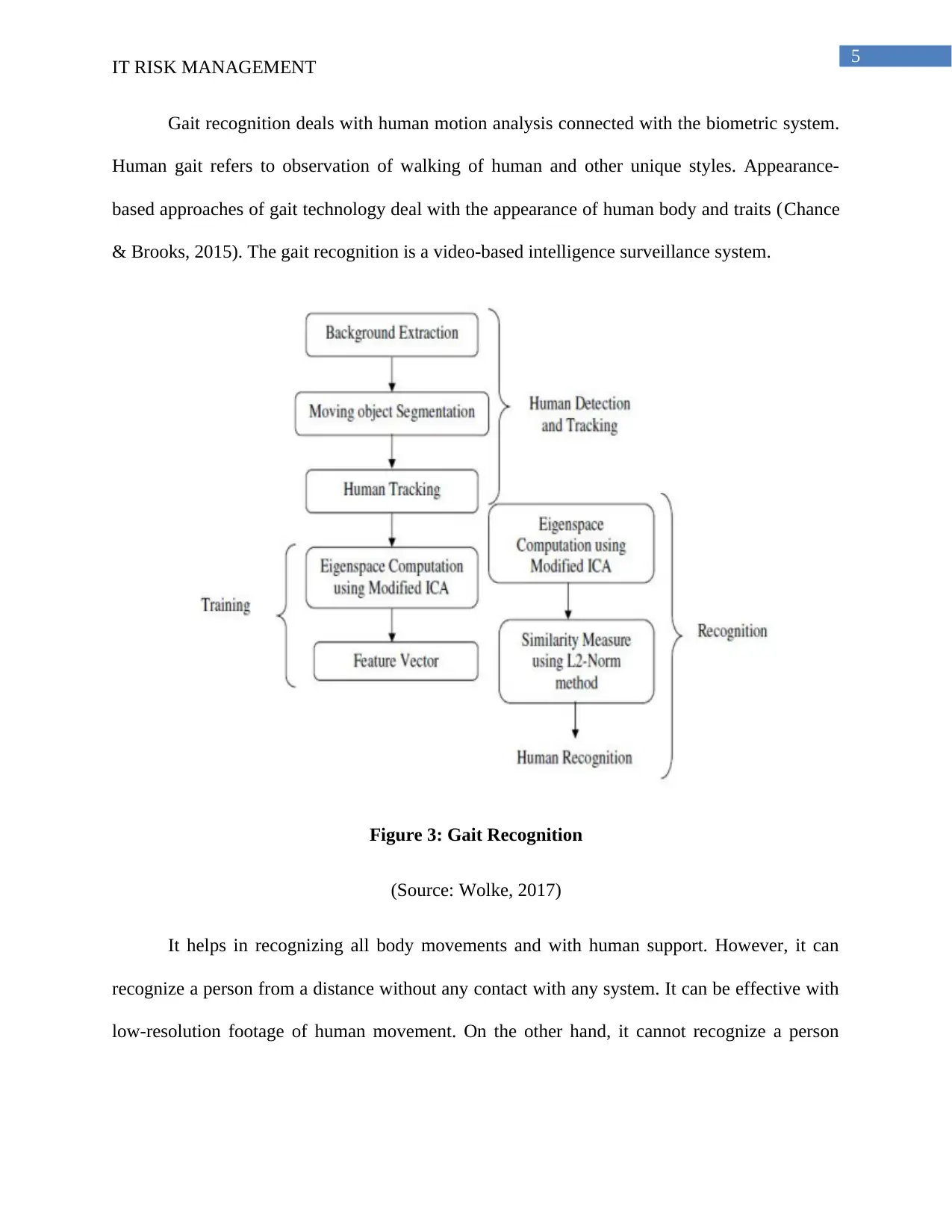
5
IT RISK MANAGEMENT
Gait recognition deals with human motion analysis connected with the biometric system.
Human gait refers to observation of walking of human and other unique styles. Appearance-
based approaches of gait technology deal with the appearance of human body and traits (Chance
& Brooks, 2015). The gait recognition is a video-based intelligence surveillance system.
Figure 3: Gait Recognition
(Source: Wolke, 2017)
It helps in recognizing all body movements and with human support. However, it can
recognize a person from a distance without any contact with any system. It can be effective with
low-resolution footage of human movement. On the other hand, it cannot recognize a person
IT RISK MANAGEMENT
Gait recognition deals with human motion analysis connected with the biometric system.
Human gait refers to observation of walking of human and other unique styles. Appearance-
based approaches of gait technology deal with the appearance of human body and traits (Chance
& Brooks, 2015). The gait recognition is a video-based intelligence surveillance system.
Figure 3: Gait Recognition
(Source: Wolke, 2017)
It helps in recognizing all body movements and with human support. However, it can
recognize a person from a distance without any contact with any system. It can be effective with
low-resolution footage of human movement. On the other hand, it cannot recognize a person

6
IT RISK MANAGEMENT
wearing an attire including trench or long coat, hat and footwear. It is used in 3D view systems
including the camera for surveillance (Fu et al., 2016).
Privacy Enhancing Technologies (PET)
The privacy concern of data and information over the internet is an important element in
the market. Therefore, the use of the privacy enhancing technologies is playing an important role
in providing privacy to the different field in the market. The PET refers to both existing and new
technologies for enhancing the privacy of data and information (Galbally, Marcel & Fierrez,
2014). The privacy-enhancing technologies reused for enhancing privacy and minimize different
threats to data d information over the internet. Some privacy tools are actively involved in
providing privacy to different systems. The use of the PETs helps in designing information and
communication systems services in order to minimize collection of private data and information
to protect data rules. The use of PETs helps in minimizing certain breaches of data and
information. There are various examples of privacy enhancing technologies (Ayday et al., 2017).
Encryption tools help in preventing hacking during transfer of data and information over
the internet. This helps in preventing private data and information of an organization. Cookie-
cutters helps in blocking cookies in the user’s computer system. This helps in monitoring the
session of the internet used by users. Therefore, the privacy of data and information has been
managed in order to protect different areas of users. The loss of data and information is
controlled by cookie cutters (Chow et al., 2014). The Platform for Privacy Preferences allows
internet users to maintain the use of the illegal websites by the users. The use of various privacy
preferences helps in monitoring privacy policies of the websites and comparing them with
carious logical algorithms. This helps in processing different algorithms in order to maintain data
subjects consent. The PETs are used in various cases for embedding custom-built policies.
IT RISK MANAGEMENT
wearing an attire including trench or long coat, hat and footwear. It is used in 3D view systems
including the camera for surveillance (Fu et al., 2016).
Privacy Enhancing Technologies (PET)
The privacy concern of data and information over the internet is an important element in
the market. Therefore, the use of the privacy enhancing technologies is playing an important role
in providing privacy to the different field in the market. The PET refers to both existing and new
technologies for enhancing the privacy of data and information (Galbally, Marcel & Fierrez,
2014). The privacy-enhancing technologies reused for enhancing privacy and minimize different
threats to data d information over the internet. Some privacy tools are actively involved in
providing privacy to different systems. The use of the PETs helps in designing information and
communication systems services in order to minimize collection of private data and information
to protect data rules. The use of PETs helps in minimizing certain breaches of data and
information. There are various examples of privacy enhancing technologies (Ayday et al., 2017).
Encryption tools help in preventing hacking during transfer of data and information over
the internet. This helps in preventing private data and information of an organization. Cookie-
cutters helps in blocking cookies in the user’s computer system. This helps in monitoring the
session of the internet used by users. Therefore, the privacy of data and information has been
managed in order to protect different areas of users. The loss of data and information is
controlled by cookie cutters (Chow et al., 2014). The Platform for Privacy Preferences allows
internet users to maintain the use of the illegal websites by the users. The use of various privacy
preferences helps in monitoring privacy policies of the websites and comparing them with
carious logical algorithms. This helps in processing different algorithms in order to maintain data
subjects consent. The PETs are used in various cases for embedding custom-built policies.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

7
IT RISK MANAGEMENT
Acceptance of privacy enhancing technologies in the market haes been great challenges for the
experts. However, the privacy concern has helped in maintaining the acceptance of PETs in the
market. Users are the concern with the privacy of their personal data and information.
The concept of the information scurry has been an important point in the context of
privacy of data and information over the internet. There have been various threats to the privacy
of data and information over the internet (Majeed et al., 2016). Loss of confidentiality of data
and information has been a major issue over the internet. Users do not feel safe over the internet
due to cyber-attacks and cyber bullying the identity theft has been increasing day by day.
Different organizations are facing cyber-attacks in their network and server. These have created a
lot of chaos in the organization. The market share of the various companies is going down due to
the loss of data and information. Therefore, these PETs have help in preventing from cyber-
attacks over the internet. Enhanced Privacy ID (EPID) is a digital signature that helps in
providing a password to various field and accounts of the user. This unique signature of user
helps in preventing various cyber-attacks over the internet (Tree, 2014). The encryption policy of
data and information have helped in encrypting data into packets that helps in creating an extra
layer of security to data. Data and information are encrypted with the help of a secret key that is
only known to receivers and sender of data and information.
Wireless Sensor Networks (WSN)
Wireless sensor networks are self-configured networks that help in monitoring physical
and environmental conditions around. Wireless sensor networks are capable to enable new
applications and require non-conventional paradigms to design several constraints (Yang, 2014).
The use of the WSNs helps in providing security and privacy to data and information stored over
the internet and during transferring of data and information. This helps in motivating different
IT RISK MANAGEMENT
Acceptance of privacy enhancing technologies in the market haes been great challenges for the
experts. However, the privacy concern has helped in maintaining the acceptance of PETs in the
market. Users are the concern with the privacy of their personal data and information.
The concept of the information scurry has been an important point in the context of
privacy of data and information over the internet. There have been various threats to the privacy
of data and information over the internet (Majeed et al., 2016). Loss of confidentiality of data
and information has been a major issue over the internet. Users do not feel safe over the internet
due to cyber-attacks and cyber bullying the identity theft has been increasing day by day.
Different organizations are facing cyber-attacks in their network and server. These have created a
lot of chaos in the organization. The market share of the various companies is going down due to
the loss of data and information. Therefore, these PETs have help in preventing from cyber-
attacks over the internet. Enhanced Privacy ID (EPID) is a digital signature that helps in
providing a password to various field and accounts of the user. This unique signature of user
helps in preventing various cyber-attacks over the internet (Tree, 2014). The encryption policy of
data and information have helped in encrypting data into packets that helps in creating an extra
layer of security to data. Data and information are encrypted with the help of a secret key that is
only known to receivers and sender of data and information.
Wireless Sensor Networks (WSN)
Wireless sensor networks are self-configured networks that help in monitoring physical
and environmental conditions around. Wireless sensor networks are capable to enable new
applications and require non-conventional paradigms to design several constraints (Yang, 2014).
The use of the WSNs helps in providing security and privacy to data and information stored over
the internet and during transferring of data and information. This helps in motivating different
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

8
IT RISK MANAGEMENT
research activities and communication between the receiver and sender if the data and
information. The standard process of the WSNs is maintaining in order to minimize privacy
concerns of data and information. There are various applications of wireless sensor networks that
are discussed below:
Military applications: Wireless sensor networks be likely an integral part of a military
command, control, communications, computing, intelligence, battlefield surveillance,
reconnaissance and targeting systems (Li et al., 2014).
Area Monitoring: The sensor nodes are placed in the various region that helps in
communicating with other nodes and collect data and information from surroundings. These
sensors detect light and sound in order to provide security and privacy to data and information
(Iyengar & Brooks, 2016).
Transportation: various real-time traffic information is provided by these sensors placed
on the road. These create a model of the roads and traffic and send to a responsible station for
getting knowledge about road traffic.
Heath applications: Various health applications are associated with health care services.
The use of advanced technology in the form of healthcare tools and techniques helps in
enhancing the quality of care services provided to several patients. The use of psychological data
about human help in monitoring the changes in human brain.
Structural Monitoring: Wireless sensor networks can be utilized for monitoring
movement within buildings and infrastructure including bridges, embankments and tunnels.
There are various types of threats and risks over the internet.
Denial of Service Attacks
IT RISK MANAGEMENT
research activities and communication between the receiver and sender if the data and
information. The standard process of the WSNs is maintaining in order to minimize privacy
concerns of data and information. There are various applications of wireless sensor networks that
are discussed below:
Military applications: Wireless sensor networks be likely an integral part of a military
command, control, communications, computing, intelligence, battlefield surveillance,
reconnaissance and targeting systems (Li et al., 2014).
Area Monitoring: The sensor nodes are placed in the various region that helps in
communicating with other nodes and collect data and information from surroundings. These
sensors detect light and sound in order to provide security and privacy to data and information
(Iyengar & Brooks, 2016).
Transportation: various real-time traffic information is provided by these sensors placed
on the road. These create a model of the roads and traffic and send to a responsible station for
getting knowledge about road traffic.
Heath applications: Various health applications are associated with health care services.
The use of advanced technology in the form of healthcare tools and techniques helps in
enhancing the quality of care services provided to several patients. The use of psychological data
about human help in monitoring the changes in human brain.
Structural Monitoring: Wireless sensor networks can be utilized for monitoring
movement within buildings and infrastructure including bridges, embankments and tunnels.
There are various types of threats and risks over the internet.
Denial of Service Attacks

9
IT RISK MANAGEMENT
DOS is an unintentional failure of nodes and malicious action. DOS attacks diminish a
network capability for providing services to the client. The simplest DOS attacks try to exhaust
resources available for the victim node (Fu et al., 2016). Unnecessary sending of attacks creates
the jam in the network and causing the denial of service attacks.
Jamming
Jamming is a denial of service attack that occurs at a physical layer. The interferences of
radio frequencies at network nodes create a jamming condition at the exit and entrance. A
jamming process contains interference of viruses and malware that damages systems.
Wormhole attack
The wormhole attack occurs at initial phase during the sensor starts discovering
neighbour information. The attacker records the packets at one node and transfer rate of packets
through a channel. The tunnelling of retransmitting the data packets through channel creates
critical conditions that initiate wormhole attack. With the help of connected network, wormhole
tries to spread throughout the spectrum and damaging systems (Wolke, 2017).
The use of firewall and antivirus night help in minimizing these threats over the network.
Firewalls and antivirus help in restricting these worms and viruses from entering into a network.
The use of strong password helps in creating privacy to data and information stored on the
server. The passwords need to be complex and 8 characters long with a combination of letters,
symbols and characters.
Conclusion
It can be concluded that use of biometric system has helped in maintaining the security of
the data and system. Different types of the biometric stem have been discussed in the report. The
IT RISK MANAGEMENT
DOS is an unintentional failure of nodes and malicious action. DOS attacks diminish a
network capability for providing services to the client. The simplest DOS attacks try to exhaust
resources available for the victim node (Fu et al., 2016). Unnecessary sending of attacks creates
the jam in the network and causing the denial of service attacks.
Jamming
Jamming is a denial of service attack that occurs at a physical layer. The interferences of
radio frequencies at network nodes create a jamming condition at the exit and entrance. A
jamming process contains interference of viruses and malware that damages systems.
Wormhole attack
The wormhole attack occurs at initial phase during the sensor starts discovering
neighbour information. The attacker records the packets at one node and transfer rate of packets
through a channel. The tunnelling of retransmitting the data packets through channel creates
critical conditions that initiate wormhole attack. With the help of connected network, wormhole
tries to spread throughout the spectrum and damaging systems (Wolke, 2017).
The use of firewall and antivirus night help in minimizing these threats over the network.
Firewalls and antivirus help in restricting these worms and viruses from entering into a network.
The use of strong password helps in creating privacy to data and information stored on the
server. The passwords need to be complex and 8 characters long with a combination of letters,
symbols and characters.
Conclusion
It can be concluded that use of biometric system has helped in maintaining the security of
the data and system. Different types of the biometric stem have been discussed in the report. The
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
10
IT RISK MANAGEMENT
face recognition, gait recognition and palm printing have been discussed in the report. The
privacy-enhancing technologies have been explained in the report. There are various advantages
and disadvantages of WSNs depicted in the report.
IT RISK MANAGEMENT
face recognition, gait recognition and palm printing have been discussed in the report. The
privacy-enhancing technologies have been explained in the report. There are various advantages
and disadvantages of WSNs depicted in the report.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

11
IT RISK MANAGEMENT
References
Ayday, E., Hubaux, J. P., Raisaro, J. L., Telenti, A., Fellay, J., McLaren, P. J., ... & Humbert, M.
(2017). U.S. Patent No. 9,536,047. Washington, DC: U.S. Patent and Trademark Office.
Brown, K., & Moles, P. (2014). Credit risk management. K. Brown & P. Moles, Credit Risk
Management, 16.
Chance, D. M., & Brooks, R. (2015). Introduction to derivatives and risk management. Cengage
Learning.
Chow, C. Y., Xu, W., & He, T. (2014). Privacy enhancing technologies for wireless sensor
networks. In The Art of Wireless Sensor Networks (pp. 609-641). Springer Berlin
Heidelberg.
Fu, P. L., Bradley, K. L., Viswanathan, S., Chan, J. M., & Stampfer, M. (2016). Trends in
Biometric Health Indices Within an Employer-Sponsored Wellness Program With
Outcome-Based Incentives. American Journal of Health Promotion, 30(6), 453-457.
Galbally, J., Marcel, S., & Fierrez, J. (2014). Image quality assessment for fake biometric
detection: Application to iris, fingerprint, and face recognition. IEEE transactions on
image processing, 23(2), 710-724.
Iyengar, S. S., & Brooks, R. R. (Eds.). (2016). Distributed sensor networks: sensor networking
and applications. CRC press.
Li, W., Guoqing, W. A. N. G., Dongchao, M. A., & Jianpei, H. E. (2014). Wireless Sensor
Networks.
IT RISK MANAGEMENT
References
Ayday, E., Hubaux, J. P., Raisaro, J. L., Telenti, A., Fellay, J., McLaren, P. J., ... & Humbert, M.
(2017). U.S. Patent No. 9,536,047. Washington, DC: U.S. Patent and Trademark Office.
Brown, K., & Moles, P. (2014). Credit risk management. K. Brown & P. Moles, Credit Risk
Management, 16.
Chance, D. M., & Brooks, R. (2015). Introduction to derivatives and risk management. Cengage
Learning.
Chow, C. Y., Xu, W., & He, T. (2014). Privacy enhancing technologies for wireless sensor
networks. In The Art of Wireless Sensor Networks (pp. 609-641). Springer Berlin
Heidelberg.
Fu, P. L., Bradley, K. L., Viswanathan, S., Chan, J. M., & Stampfer, M. (2016). Trends in
Biometric Health Indices Within an Employer-Sponsored Wellness Program With
Outcome-Based Incentives. American Journal of Health Promotion, 30(6), 453-457.
Galbally, J., Marcel, S., & Fierrez, J. (2014). Image quality assessment for fake biometric
detection: Application to iris, fingerprint, and face recognition. IEEE transactions on
image processing, 23(2), 710-724.
Iyengar, S. S., & Brooks, R. R. (Eds.). (2016). Distributed sensor networks: sensor networking
and applications. CRC press.
Li, W., Guoqing, W. A. N. G., Dongchao, M. A., & Jianpei, H. E. (2014). Wireless Sensor
Networks.

12
IT RISK MANAGEMENT
Majeed, A., Bhana, R., Haq, A. U., Kyaruzi, I., Pervaz, S., & Williams, M. L. (2016). Internet of
Everything (Ioe): Analysing the Individual Concerns Over Privacy Enhancing
Technologies (Pets). International journal of advanced computer science and
applications, 7(3), 15-22.
McNeil, A. J., Frey, R., & Embrechts, P. (2015). Quantitative risk management: Concepts,
techniques and tools. Princeton university press.
Meyer, T., & Reniers, G. (2016). Engineering risk management. Walter de Gruyter GmbH & Co
KG.
Rampini, A. A., Sufi, A., & Viswanathan, S. (2014). Dynamic risk management. Journal of
Financial Economics, 111(2), 271-296.
Tree, S. (2014). Wireless sensor networks. Self, 1(R2), C0.
Wolke, T. (2017). Risk Management. Walter de Gruyter GmbH & Co KG.
Yang, K. (2014). Wireless sensor networks. Principles, Design and Applications.
IT RISK MANAGEMENT
Majeed, A., Bhana, R., Haq, A. U., Kyaruzi, I., Pervaz, S., & Williams, M. L. (2016). Internet of
Everything (Ioe): Analysing the Individual Concerns Over Privacy Enhancing
Technologies (Pets). International journal of advanced computer science and
applications, 7(3), 15-22.
McNeil, A. J., Frey, R., & Embrechts, P. (2015). Quantitative risk management: Concepts,
techniques and tools. Princeton university press.
Meyer, T., & Reniers, G. (2016). Engineering risk management. Walter de Gruyter GmbH & Co
KG.
Rampini, A. A., Sufi, A., & Viswanathan, S. (2014). Dynamic risk management. Journal of
Financial Economics, 111(2), 271-296.
Tree, S. (2014). Wireless sensor networks. Self, 1(R2), C0.
Wolke, T. (2017). Risk Management. Walter de Gruyter GmbH & Co KG.
Yang, K. (2014). Wireless sensor networks. Principles, Design and Applications.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 12
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




