IT Risk Management: Security Models, Threats, and Assessment
VerifiedAdded on 2020/03/04
|10
|1552
|83
Report
AI Summary
This report provides an overview of IT risk management, emphasizing the importance of securing public data and IT systems. It explores the IT security and technology landscape, highlighting the gap between customer security needs and IT company provisions, and discusses the roles of various security groups like network, application, and endpoint security. The report then delves into IT security models and access controls, detailing Mandatory Access Control (MAC), Role Based Access Control, Discretionary Access Control (DAC), and the State Machine Model. Furthermore, it examines IT security threats and risk assessments, differentiating between intentional and accidental threats, and discussing various types of risks. The report concludes by emphasizing the need for continuous monitoring and implementation of security measures, such as antivirus software and firewalls, to mitigate risks and threats to computing systems.

Running head: IT RISK MANAGEMENT
IT RISK MANAGEMENT
Name of the Student
Name of the Organisation
Author note
IT RISK MANAGEMENT
Name of the Student
Name of the Organisation
Author note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1IT RISK MANAGEMENT
Executive summary
The aim of this report is to discuss about the security management of different organisations and
the possible risks and threats for the computing system. Security of the information is the subject
that is given highest priority by organisations as public data is important to be confidential from
the reliability point of view. It is concluded that different access and security models should be
implemented to overcome the security issues related to the security of the computing system
Executive summary
The aim of this report is to discuss about the security management of different organisations and
the possible risks and threats for the computing system. Security of the information is the subject
that is given highest priority by organisations as public data is important to be confidential from
the reliability point of view. It is concluded that different access and security models should be
implemented to overcome the security issues related to the security of the computing system

2IT RISK MANAGEMENT
Table of Contents
Introduction......................................................................................................................................3
1. IT Security & Technology Landscape.........................................................................................3
2. IT Security Models & Access Controls.......................................................................................6
3. IT Security Threat and risk assessment.......................................................................................6
Conclusion.......................................................................................................................................7
References........................................................................................................................................8
Table of Contents
Introduction......................................................................................................................................3
1. IT Security & Technology Landscape.........................................................................................3
2. IT Security Models & Access Controls.......................................................................................6
3. IT Security Threat and risk assessment.......................................................................................6
Conclusion.......................................................................................................................................7
References........................................................................................................................................8
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3IT RISK MANAGEMENT
Introduction
It security management is an important subject for the organisations as security of the
public data is given the highest priority in recent time. With the advancement of internet and
technology many loopholes have been created in the security system of the computers and the
information technology system (Rampini & Viswanathan, 2016). There are many threats and
risks which are also responsible for the breakdown of the security system of the IT organisations
database. The organisations are continuously working to make the database and the infrastructure
of the information system more secured.
In this report mainly three topics are discussed and those are IT security and technology
landscape, IT security models and access control and the IT security threats and risk assessment.
These topics are discussed in order to understand the security background and the risks issues for
the information technology organisations and the computing system.
1. IT Security & Technology Landscape
Security is an important parameter in the information technology industry for keeping the
information of public and organization secured. To maintain the security IT companies are
creating new technologies and methods which refer to the IT security and technology landscape.
There is a huge difference between the customer’s security requirement and the security which is
given by the IT organizations (Chance & Brooks, 2015). To overcome this gap IT companies are
emphasizing more on the security and technical landscape. In IT sectors various groups are
working for different security problems in different fields like network security, applications
security and endpoint security. The network security deals with the risk issues regarding various
Introduction
It security management is an important subject for the organisations as security of the
public data is given the highest priority in recent time. With the advancement of internet and
technology many loopholes have been created in the security system of the computers and the
information technology system (Rampini & Viswanathan, 2016). There are many threats and
risks which are also responsible for the breakdown of the security system of the IT organisations
database. The organisations are continuously working to make the database and the infrastructure
of the information system more secured.
In this report mainly three topics are discussed and those are IT security and technology
landscape, IT security models and access control and the IT security threats and risk assessment.
These topics are discussed in order to understand the security background and the risks issues for
the information technology organisations and the computing system.
1. IT Security & Technology Landscape
Security is an important parameter in the information technology industry for keeping the
information of public and organization secured. To maintain the security IT companies are
creating new technologies and methods which refer to the IT security and technology landscape.
There is a huge difference between the customer’s security requirement and the security which is
given by the IT organizations (Chance & Brooks, 2015). To overcome this gap IT companies are
emphasizing more on the security and technical landscape. In IT sectors various groups are
working for different security problems in different fields like network security, applications
security and endpoint security. The network security deals with the risk issues regarding various
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4IT RISK MANAGEMENT
network layers and protocols. Application security works for the security of different
applications and software. Hardware like modem and servers related security is maintained in the
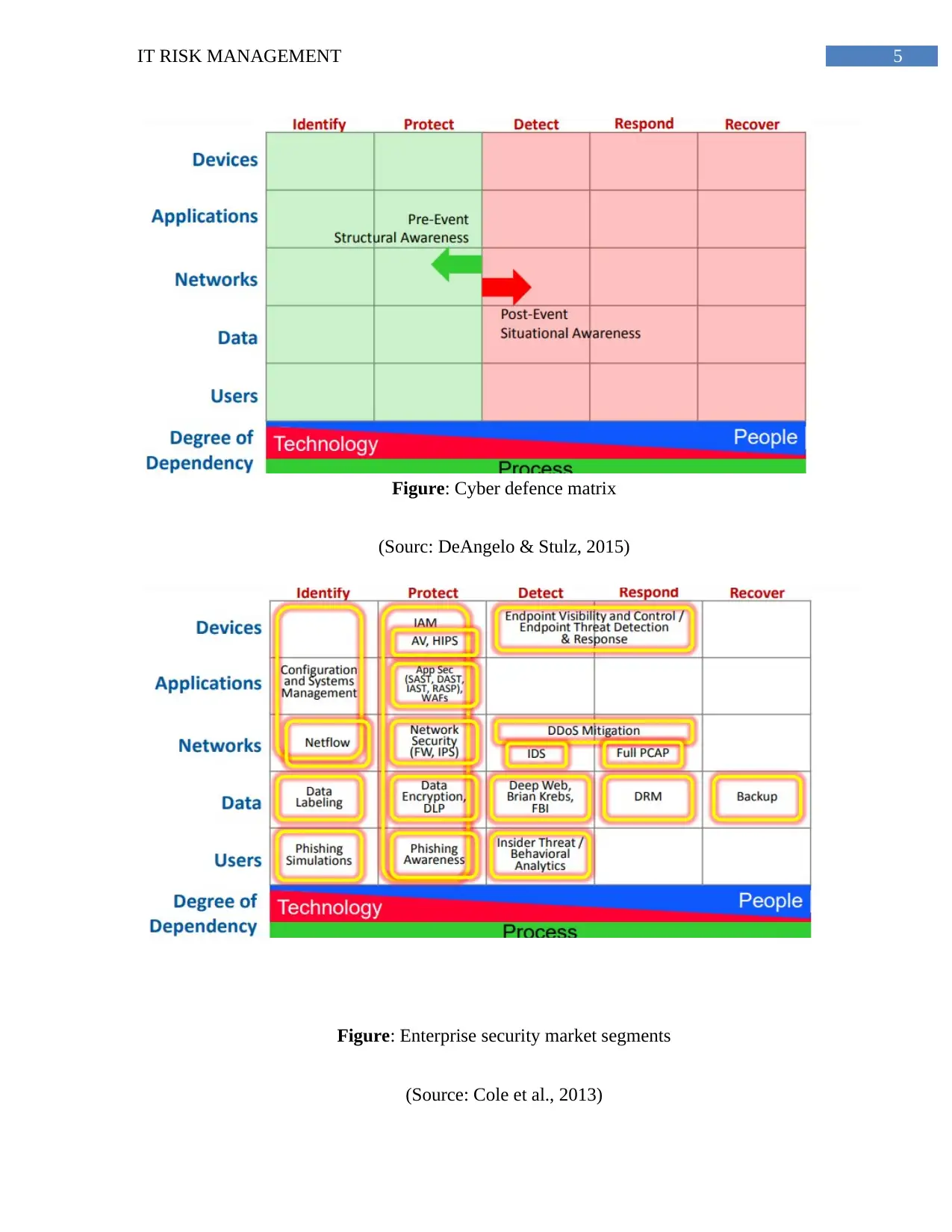
endpoint security (Cole et al., 2013). Devices, applications, data and users are considered as the
assets in the security landscape. To ensure the security different operations like identification,
protection, detection, respond and recovery are executed. First step identification consists of
defining the assets, viruses, malware, measuring attack surface and risk profiling. Protection can
be done by preventing and limiting the impact of the security issues and by managing the access.
The detection process consists of discovering the events, anomalies and finding the intrusions.
The respond and recovery are done by using different restoring operations (DeAngelo & Stulz,
2015). Cyber defense matrix is one of the useful applications that is used to identify the risk
levels of different security related issues and to analyze them with respect to the resources and
operations as discussed earlier. The principles and the priority list of the organization are also
important from the point of view of detection and removing security related issues.
network layers and protocols. Application security works for the security of different
applications and software. Hardware like modem and servers related security is maintained in the
endpoint security (Cole et al., 2013). Devices, applications, data and users are considered as the
assets in the security landscape. To ensure the security different operations like identification,
protection, detection, respond and recovery are executed. First step identification consists of
defining the assets, viruses, malware, measuring attack surface and risk profiling. Protection can
be done by preventing and limiting the impact of the security issues and by managing the access.
The detection process consists of discovering the events, anomalies and finding the intrusions.
The respond and recovery are done by using different restoring operations (DeAngelo & Stulz,
2015). Cyber defense matrix is one of the useful applications that is used to identify the risk
levels of different security related issues and to analyze them with respect to the resources and
operations as discussed earlier. The principles and the priority list of the organization are also
important from the point of view of detection and removing security related issues.
5IT RISK MANAGEMENT
Figure: Cyber defence matrix
(Sourc: DeAngelo & Stulz, 2015)
Figure: Enterprise security market segments
(Source: Cole et al., 2013)
Figure: Cyber defence matrix
(Sourc: DeAngelo & Stulz, 2015)
Figure: Enterprise security market segments
(Source: Cole et al., 2013)
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6IT RISK MANAGEMENT
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7IT RISK MANAGEMENT
2. IT Security Models & Access Controls
Access control is the identification of an individual making a particular process or job by
authenticating and to provide power to the person to decide that who will have the access to the
website or computer. Generally the access is created by making the account of the user first and
then the user is given a username and a password (Glendon, Clarke & McKenna, 2016). For
access control different software are designed in such a way that they can provide the permission
to the user for the access of the website and the computer. The process of provide the permission
to the individuals to make their duties, depends upon the access control models. There are
different types of access control models. These are Mandatory Access Control (MAC), Role
Based Access Control, Discretionary Access Control and Rule based Access Control. The MAC
or Mandatory Access Control is used to provide the access to the administrator or the owner.
This refers that there is no control for the end user to access the settings (Lam, 2014). There are
also two models in MAC and those are Biba and Bell-Lapadula. Biba model works on the
integrity of the model and the other one works for the confidentiality of data. In case of Role
based control the access is given with respect to the user’s position in an organisation. The
Discretionary Access Control or DAC is the lowest restrictive model that allows the users to
access all the programs they use. State machine model is another type of IT security model that
helps to make the state of a system accessible to the user by the help of the finite state model.
3. IT Security Threat and risk assessment
The IT security threat and risk assessment is an important parameter which is given high
priority by the organisations in order to maintain security. Threat can be considered as the
possible danger for the security of a computing system. Threats can be of two types and those are
2. IT Security Models & Access Controls
Access control is the identification of an individual making a particular process or job by
authenticating and to provide power to the person to decide that who will have the access to the
website or computer. Generally the access is created by making the account of the user first and
then the user is given a username and a password (Glendon, Clarke & McKenna, 2016). For
access control different software are designed in such a way that they can provide the permission
to the user for the access of the website and the computer. The process of provide the permission
to the individuals to make their duties, depends upon the access control models. There are
different types of access control models. These are Mandatory Access Control (MAC), Role
Based Access Control, Discretionary Access Control and Rule based Access Control. The MAC
or Mandatory Access Control is used to provide the access to the administrator or the owner.
This refers that there is no control for the end user to access the settings (Lam, 2014). There are
also two models in MAC and those are Biba and Bell-Lapadula. Biba model works on the
integrity of the model and the other one works for the confidentiality of data. In case of Role
based control the access is given with respect to the user’s position in an organisation. The
Discretionary Access Control or DAC is the lowest restrictive model that allows the users to
access all the programs they use. State machine model is another type of IT security model that
helps to make the state of a system accessible to the user by the help of the finite state model.
3. IT Security Threat and risk assessment
The IT security threat and risk assessment is an important parameter which is given high
priority by the organisations in order to maintain security. Threat can be considered as the
possible danger for the security of a computing system. Threats can be of two types and those are

8IT RISK MANAGEMENT
intentional and accidental (McNeil, Frey & Embrechts, 2015). Computer malfunctioning,
possibility of a natural disaster are the reasons of threat. Deliberate threats are created by spying,
illegal processing of data and the accidental threats are created by the equipment failure or
software failure. Threats can make damages to different assets in different way. Risks can be of
various types. There may be sudden power loss or damage of the hardware and the software
connected to a computer system (Pritchard & PMP, 2014). Due to risks data can be loosed and
security can be affected. There is a basic difference between the risks and the treats. Threats can
be predefined and calculate but the risks cannot be pre estimated. Different methods can be
followed to overcome the threats but risks cannot be overcome by taking any progressive action.
The computer system and the information technology of a system should be well maintained and
monitored to overcome the risks and threats. Several antivirus, firewalls can be used to make the
threats away from the computing system.
Conclusion
From the above discussion it is concluded that IT security management is an important
parameter to overcome the possible threats and risks for the computer system. It security and
technology landscape provides the idea about the security model of the computing systems.
There are many access controls which should be implemented in the security models to
overcome the security related issues.
intentional and accidental (McNeil, Frey & Embrechts, 2015). Computer malfunctioning,
possibility of a natural disaster are the reasons of threat. Deliberate threats are created by spying,
illegal processing of data and the accidental threats are created by the equipment failure or
software failure. Threats can make damages to different assets in different way. Risks can be of
various types. There may be sudden power loss or damage of the hardware and the software
connected to a computer system (Pritchard & PMP, 2014). Due to risks data can be loosed and
security can be affected. There is a basic difference between the risks and the treats. Threats can
be predefined and calculate but the risks cannot be pre estimated. Different methods can be
followed to overcome the threats but risks cannot be overcome by taking any progressive action.
The computer system and the information technology of a system should be well maintained and
monitored to overcome the risks and threats. Several antivirus, firewalls can be used to make the
threats away from the computing system.
Conclusion
From the above discussion it is concluded that IT security management is an important
parameter to overcome the possible threats and risks for the computer system. It security and
technology landscape provides the idea about the security model of the computing systems.
There are many access controls which should be implemented in the security models to
overcome the security related issues.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9IT RISK MANAGEMENT
References
Chance, D. M., & Brooks, R. (2015). Introduction to derivatives and risk management. Cengage
Learning.
Cole, S., Giné, X., Tobacman, J., Topalova, P., Townsend, R., & Vickery, J. (2013). Barriers to
household risk management: Evidence from India. American Economic Journal: Applied
Economics, 5(1), 104-135.
DeAngelo, H., & Stulz, R. M. (2015). Liquid-claim production, risk management, and bank
capital structure: Why high leverage is optimal for banks. Journal of Financial
Economics, 116(2), 219-236.
Glendon, A. I., Clarke, S., & McKenna, E. (2016). Human safety and risk management. Crc
Press.
Lam, J. (2014). Enterprise risk management: from incentives to controls. John Wiley & Sons.
McNeil, A. J., Frey, R., & Embrechts, P. (2015). Quantitative risk management: Concepts,
techniques and tools. Princeton university press.
Pritchard, C. L., & PMP, P. R. (2014). Risk management: concepts and guidance. CRC Press.
Rampini, A. A., & Viswanathan, S. (2016). Household risk management (No. w22293). National
Bureau of Economic Research.
References
Chance, D. M., & Brooks, R. (2015). Introduction to derivatives and risk management. Cengage
Learning.
Cole, S., Giné, X., Tobacman, J., Topalova, P., Townsend, R., & Vickery, J. (2013). Barriers to
household risk management: Evidence from India. American Economic Journal: Applied
Economics, 5(1), 104-135.
DeAngelo, H., & Stulz, R. M. (2015). Liquid-claim production, risk management, and bank
capital structure: Why high leverage is optimal for banks. Journal of Financial
Economics, 116(2), 219-236.
Glendon, A. I., Clarke, S., & McKenna, E. (2016). Human safety and risk management. Crc
Press.
Lam, J. (2014). Enterprise risk management: from incentives to controls. John Wiley & Sons.
McNeil, A. J., Frey, R., & Embrechts, P. (2015). Quantitative risk management: Concepts,
techniques and tools. Princeton university press.
Pritchard, C. L., & PMP, P. R. (2014). Risk management: concepts and guidance. CRC Press.
Rampini, A. A., & Viswanathan, S. (2016). Household risk management (No. w22293). National
Bureau of Economic Research.
1 out of 10
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





