ITC 596 - IoT Risk Assessment: IT Risk Management for Gigantic Corp
VerifiedAdded on 2024/07/01
|19
|6971
|265
Report
AI Summary
This report assesses the IT risks associated with Gigantic Corporation's use of Internet of Things (IoT) technology. It identifies potential threats, vulnerabilities, and consequences, offering risk mitigation measures and recommendations for the industry. The report categorizes risks as low, medium, or high, and develops a recommendation model based on this categorization. It details risk components in the IoT system, risk factors that enhance costs, and the impact of threats and vulnerabilities on the organization. The benefits of using intrusion detection, vulnerability scanners, and firewalls are discussed to enhance security. Recommendations include turning off unused features, updating software, using encryption, and implementing multi-factor authentication. The report aims to implement security and privacy mechanisms to prevent data loss and theft, ultimately protecting the organization's finance, customer relations, and image. The findings help in enhancing security in the gigantic corporation in using internet of things technology.

ITC 596- IT RISK MANAGEMENT
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
Executive summary..................................................................................................................................... 2
1. Introduction............................................................................................................................................. 4
2. Overview of risk management................................................................................................................. 5
3. Threat, Vulnerability, and Consequences................................................................................................6
3.1 Risk assessment based on Industry.................................................................................................... 6
3.2 Approaches for mitigating security risk.............................................................................................8
3.3. Identification of threats, Vulnerabilities, and consequences.............................................................9
3.3 Identification of common threats and vulnerabilities areas..............................................................10
3.4 Mitigating Measure in IoT devices.................................................................................................. 13
3.5 Benefits............................................................................................................................................ 14
3.6 Recommendations in existing industry risk.....................................................................................15
4. Summary of the protection mechanism in information security............................................................16
5. Conclusion............................................................................................................................................. 17
6. References............................................................................................................................................. 18
Gigantic Corporation: Risk Assessment- Internet of Things (IoT)
1
Executive summary..................................................................................................................................... 2
1. Introduction............................................................................................................................................. 4
2. Overview of risk management................................................................................................................. 5
3. Threat, Vulnerability, and Consequences................................................................................................6
3.1 Risk assessment based on Industry.................................................................................................... 6
3.2 Approaches for mitigating security risk.............................................................................................8
3.3. Identification of threats, Vulnerabilities, and consequences.............................................................9
3.3 Identification of common threats and vulnerabilities areas..............................................................10
3.4 Mitigating Measure in IoT devices.................................................................................................. 13
3.5 Benefits............................................................................................................................................ 14
3.6 Recommendations in existing industry risk.....................................................................................15
4. Summary of the protection mechanism in information security............................................................16
5. Conclusion............................................................................................................................................. 17
6. References............................................................................................................................................. 18
Gigantic Corporation: Risk Assessment- Internet of Things (IoT)
1

Executive summary
Gigantic Corporation is a company that uses the internet of things for the interconnection of
several devices through the internet. This help to share and access the data remotely through the
internet. The IoT is a technique that uses the internet for interrelating devices, mechanical, and
digital machines to animals and objects that uses the unique id for the data transfer (Serpanos &
Wolf, 2018).
The report is assessed for the management of the gigantic corporation in using the IoT
technology. This help to identify the technical risks present in the business. The effective
decision is taken in the business which facilitates the IT risks solutions (Stoll, 2014).
The report has the purpose of accessing the internet of things as a major technology in the
gigantic corporation. The project involves the up-gradation of a project as compared to a current
legacy system in the organization. The report has the risk assessment overview in IoT, scope,
standards, data policies, vulnerabilities, threat agents associated with it.
The report includes threats, vulnerabilities and the consequences that are associated with the
organization. The risk mitigation measures with recommendation’s in an industry is identified
with the report. The overview of risk that is associated with the gigantic corporation along with
the threats agent, threat value, and the risk factors and recommendations are studied in the report.
The risk is categorizing as low, medium or high or ignore for the assessment of risk. On the
categorization of the risk, a recommendation model is developed (Shapaval & Matulevičius,
2018).
The report has the risk components that are present in the IoT system, risk factors that enhance
the cost. The threat, vulnerabilities and the factors that affect the gigantic organization are
studied. In the report, the threat with the threat agent and the value is described that help the
stakeholder for the analyzing of a level of threats. The risk assessment table is generated where
the impact is calculated for the gigantic corporation that works in IoT (Serpanos & Wolf, 2018).
On the basis of these impacts, the factors are found that help to take the effective decision by the
stakeholders and technologist. In the report, the benefits of using the intrusion detection,
vulnerability scanner and firewalls are discussed that help in the security enhancement in a
gigantic corporation. The insurance benefits and the methods that are used case of disaster are
discussed with the mitigating methods (Thangavel & Sudhaman, 2017).
At last in the report, the recommendations are developed that is based on the findings that are
done internet of things in the gigantic corporation. The recommendations are:
Turn of the things that is not been used like camera, microphone or ports.
The physical access in IoT devices is not been taken by the user.
The software and firmware are updated timely.
Use encryption at various stages of the network.
The multifactor authentication is used.
The identities are protected but gateways are not.
Password usage elimination.
Gigantic Corporation: Risk Assessment- Internet of Things (IoT)
2
Gigantic Corporation is a company that uses the internet of things for the interconnection of
several devices through the internet. This help to share and access the data remotely through the
internet. The IoT is a technique that uses the internet for interrelating devices, mechanical, and
digital machines to animals and objects that uses the unique id for the data transfer (Serpanos &
Wolf, 2018).
The report is assessed for the management of the gigantic corporation in using the IoT
technology. This help to identify the technical risks present in the business. The effective
decision is taken in the business which facilitates the IT risks solutions (Stoll, 2014).
The report has the purpose of accessing the internet of things as a major technology in the
gigantic corporation. The project involves the up-gradation of a project as compared to a current
legacy system in the organization. The report has the risk assessment overview in IoT, scope,
standards, data policies, vulnerabilities, threat agents associated with it.
The report includes threats, vulnerabilities and the consequences that are associated with the
organization. The risk mitigation measures with recommendation’s in an industry is identified
with the report. The overview of risk that is associated with the gigantic corporation along with
the threats agent, threat value, and the risk factors and recommendations are studied in the report.
The risk is categorizing as low, medium or high or ignore for the assessment of risk. On the
categorization of the risk, a recommendation model is developed (Shapaval & Matulevičius,
2018).
The report has the risk components that are present in the IoT system, risk factors that enhance
the cost. The threat, vulnerabilities and the factors that affect the gigantic organization are
studied. In the report, the threat with the threat agent and the value is described that help the
stakeholder for the analyzing of a level of threats. The risk assessment table is generated where
the impact is calculated for the gigantic corporation that works in IoT (Serpanos & Wolf, 2018).
On the basis of these impacts, the factors are found that help to take the effective decision by the
stakeholders and technologist. In the report, the benefits of using the intrusion detection,
vulnerability scanner and firewalls are discussed that help in the security enhancement in a
gigantic corporation. The insurance benefits and the methods that are used case of disaster are
discussed with the mitigating methods (Thangavel & Sudhaman, 2017).
At last in the report, the recommendations are developed that is based on the findings that are
done internet of things in the gigantic corporation. The recommendations are:
Turn of the things that is not been used like camera, microphone or ports.
The physical access in IoT devices is not been taken by the user.
The software and firmware are updated timely.
Use encryption at various stages of the network.
The multifactor authentication is used.
The identities are protected but gateways are not.
Password usage elimination.
Gigantic Corporation: Risk Assessment- Internet of Things (IoT)
2
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

The identity of user and objects are protected.
Use IPS (intrusion prevention systems).
Adoption of risk-driven methods (Tekeoglu & Tosun, 2017).
Optimizing the traffic flow.
Control the environment components like humidity, air, and wind.
Taking data backups timely.
The network firewalls are used (Shi, 2013).
Controlling the network access.
Intrusion prevention.
Installing the CCTV cameras and use access-based security methods.
The warning system is used in the network or at home gateways.
Using anti-virus and anti-malware in the systems or devices.
The DRP (disaster recovery process) is used in the system.
The measures are taken that prevent the data loss.
Congestion is controlled over the network that reduces the data flow.
The report aims to implement and use the security and privacy mechanism in the organization.
The prevention and mitigation measure is used that solve the risks in the organization of data
loss, data theft (Thangavel & Sudhaman, 2017).
The consequences of these risks affect the organization in finance, customer relations partners in
business or trust and image of the organization.
The advantages of using the risk assessment the findings are:
The latest updates of software in devices and network updates will result in improvements of
software security that are assumed to be more advancement in technology and safety in use.
The new implementation in the internet of things will enhance the existing system in the
organization.
The trust among customers in business is built with the security improvements this help to
achieve the organization objective easily.
The improved guidelines and policies help to take the mitigation measure effectively for the
organization in reducing the risks (Jansen & Jeschke, 2018).
The impact with the specific risk is calculated by using the risks assessment matrix which
helps in reducing the risks.
The risk assessment matrix is a risk that assists in the development of effective decisions for
various stakeholders (Thangavel & Sudhaman, 2017).
The overall report concludes that the research did help to enhance the security in the gigantic
corporation in using internet of things technology. The recommendation is taken that help in
security enhancement (Thangavel & Sudhaman, 2017).
Gigantic Corporation: Risk Assessment- Internet of Things (IoT)
3
Use IPS (intrusion prevention systems).
Adoption of risk-driven methods (Tekeoglu & Tosun, 2017).
Optimizing the traffic flow.
Control the environment components like humidity, air, and wind.
Taking data backups timely.
The network firewalls are used (Shi, 2013).
Controlling the network access.
Intrusion prevention.
Installing the CCTV cameras and use access-based security methods.
The warning system is used in the network or at home gateways.
Using anti-virus and anti-malware in the systems or devices.
The DRP (disaster recovery process) is used in the system.
The measures are taken that prevent the data loss.
Congestion is controlled over the network that reduces the data flow.
The report aims to implement and use the security and privacy mechanism in the organization.
The prevention and mitigation measure is used that solve the risks in the organization of data
loss, data theft (Thangavel & Sudhaman, 2017).
The consequences of these risks affect the organization in finance, customer relations partners in
business or trust and image of the organization.
The advantages of using the risk assessment the findings are:
The latest updates of software in devices and network updates will result in improvements of
software security that are assumed to be more advancement in technology and safety in use.
The new implementation in the internet of things will enhance the existing system in the
organization.
The trust among customers in business is built with the security improvements this help to
achieve the organization objective easily.
The improved guidelines and policies help to take the mitigation measure effectively for the
organization in reducing the risks (Jansen & Jeschke, 2018).
The impact with the specific risk is calculated by using the risks assessment matrix which
helps in reducing the risks.
The risk assessment matrix is a risk that assists in the development of effective decisions for
various stakeholders (Thangavel & Sudhaman, 2017).
The overall report concludes that the research did help to enhance the security in the gigantic
corporation in using internet of things technology. The recommendation is taken that help in
security enhancement (Thangavel & Sudhaman, 2017).
Gigantic Corporation: Risk Assessment- Internet of Things (IoT)
3
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1. Introduction
Organization overview with project background
Gigantic Corporation is an IT firm which works in the field of IoT to manage networking of
devices. The aim of the company is to identify and mitigate IT risks associated with the
organization to minimize the risk. The report is presented for the role of interface between
stakeholder and technologists for effective decision making. This helps in managing the risk
associated with the internet of things in a gigantic corporation. The Gigantic Corporation is
going to build an application based on the internet of things. IoT (internet of things) is a
technology where millions of devices around the world are connected through the internet for
collecting and sharing the data (Haber & Hibbert, 2017).
Problem statement
The technical difficulties and risks are seen in Gigantic Corporation project. The risk creates the
issue among the stakeholders and technologists for taking the effective decision to reduce the
data and money loss. In the internet of things the threat and vulnerabilities are present that affect
the operation of organization (Ali, et. al., 2014)
Project purpose
The report focuses on risks assessment which helps in analyzing the security risk associated with
the gigantic corporation projects. The vulnerabilities and threats with respect to IoT in the
gigantic corporation are assessed for managing the security. The report helps to take the
mitigation measures in the gigantic corporation for security improvements in the IoT field. The
current best security measures help to solve the security and privacy issue with IoT. The reports
help to evaluate the opportunities with the gigantic corporation in using the internet of things
(Banerjee, Bouzefrane, & Maupas, 2018).
Project scope
The risk assessment scope has several components under the internet of things project. The
potential risk, threats, and vulnerabilities are identified that is not solved in the internet of things.
The assessment helps to identify the data related issue in a gigantic corporation that help to
enhance the maintaining, receiving, monitoring and transmitting of data by using the IoT. The
internal data, standards, and policies are assessed related to the security and privacy of data-
network, database, host and device levels (Ko, Kim, & Kim, 2017).
The risk assessment helps to manage the risk at the higher level with the findings and assessment
approach. The finding includes the threats, consequences, and vulnerabilities of the gigantic
corporation using the IoT. The recommendation is developed on the basis of the existing risk in
the organizations. The finding helps to solve the security issue of IoT with the use of risk
management techniques (Serpanos & Wolf, 2018).
In this report, the risk associated in the gigantic corporation in the internet of things area the
threat and risks are identified that is present. The recommendations are set for the organization
by doing the risk assessment. The recommendation helps the technologists and stakeholder for
taking the effective decision in ensuring the security in an internet of things so the data loss, data
availability and in case of disaster the recovery is done (Ali, et. al., 2017)
Gigantic Corporation: Risk Assessment- Internet of Things (IoT)
4
Organization overview with project background
Gigantic Corporation is an IT firm which works in the field of IoT to manage networking of
devices. The aim of the company is to identify and mitigate IT risks associated with the
organization to minimize the risk. The report is presented for the role of interface between
stakeholder and technologists for effective decision making. This helps in managing the risk
associated with the internet of things in a gigantic corporation. The Gigantic Corporation is
going to build an application based on the internet of things. IoT (internet of things) is a
technology where millions of devices around the world are connected through the internet for
collecting and sharing the data (Haber & Hibbert, 2017).
Problem statement
The technical difficulties and risks are seen in Gigantic Corporation project. The risk creates the
issue among the stakeholders and technologists for taking the effective decision to reduce the
data and money loss. In the internet of things the threat and vulnerabilities are present that affect
the operation of organization (Ali, et. al., 2014)
Project purpose
The report focuses on risks assessment which helps in analyzing the security risk associated with
the gigantic corporation projects. The vulnerabilities and threats with respect to IoT in the
gigantic corporation are assessed for managing the security. The report helps to take the
mitigation measures in the gigantic corporation for security improvements in the IoT field. The
current best security measures help to solve the security and privacy issue with IoT. The reports
help to evaluate the opportunities with the gigantic corporation in using the internet of things
(Banerjee, Bouzefrane, & Maupas, 2018).
Project scope
The risk assessment scope has several components under the internet of things project. The
potential risk, threats, and vulnerabilities are identified that is not solved in the internet of things.
The assessment helps to identify the data related issue in a gigantic corporation that help to
enhance the maintaining, receiving, monitoring and transmitting of data by using the IoT. The
internal data, standards, and policies are assessed related to the security and privacy of data-
network, database, host and device levels (Ko, Kim, & Kim, 2017).
The risk assessment helps to manage the risk at the higher level with the findings and assessment
approach. The finding includes the threats, consequences, and vulnerabilities of the gigantic
corporation using the IoT. The recommendation is developed on the basis of the existing risk in
the organizations. The finding helps to solve the security issue of IoT with the use of risk
management techniques (Serpanos & Wolf, 2018).
In this report, the risk associated in the gigantic corporation in the internet of things area the
threat and risks are identified that is present. The recommendations are set for the organization
by doing the risk assessment. The recommendation helps the technologists and stakeholder for
taking the effective decision in ensuring the security in an internet of things so the data loss, data
availability and in case of disaster the recovery is done (Ali, et. al., 2017)
Gigantic Corporation: Risk Assessment- Internet of Things (IoT)
4

2. Overview of risk management
The risk management helps in identifying the risks that are associated with the corporation. The
plan is developed for the risk prevention or for solving the occurred risks. The risk management
helps in saving efforts, time, reducing stress and resources. Internet of things platform is
developed by using the varied types of tools, devices, and technologies. For efficient
management of team, the risk assessment is performed for the efficient management (Shapaval &
Matulevicius, 2018).
Figure 1 Risk management process
Source: (By Author)
Gigantic Corporation: Risk Assessment- Internet of Things (IoT)
5
Identify and analyze
exposures
Examine risk
management technqiues
Select risk management
technique
Implement techniques
Monitor results
The risk management helps in identifying the risks that are associated with the corporation. The
plan is developed for the risk prevention or for solving the occurred risks. The risk management
helps in saving efforts, time, reducing stress and resources. Internet of things platform is
developed by using the varied types of tools, devices, and technologies. For efficient
management of team, the risk assessment is performed for the efficient management (Shapaval &
Matulevicius, 2018).
Figure 1 Risk management process
Source: (By Author)
Gigantic Corporation: Risk Assessment- Internet of Things (IoT)
5
Identify and analyze
exposures
Examine risk
management technqiues
Select risk management
technique
Implement techniques
Monitor results
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3. Threat, Vulnerability, and Consequences
3.1 Risk assessment based on Industry
Appliance risk
The gigantic corporation will use several devices and tools that are using the IoT applications.
The computer devices, Smartphone, thermometer, healthcare machines are having the
distinguishing properties. The information on these devices is stored in different forms. The
attacker tries to gain the access to these devices and the data stored in the devices. If the
information access is taken by the hacker then serious risks are faced by the organization
(Fibikova & Mueller, 2012).
Complexity in systems risk
The IoT is a complex heterogeneous network that is composed of several communication
technologies. The communication technologies have delayed fraudulent and non-standardized
behavior. The devices that are connecting to the internet are growing day by day. It is predicted
that the devices connected to the internet by 2020 are 20 billion (Serpanos & Wolf, 2018).
Data likability risk
The data collected and processed by IoT are stored in the databases. The devices are linked with
the database. If at any time the linking is beaked by the attacker then the data is not getting
properly from the database. The issue in running the application is faced by the user (Fibikova &
Mueller, 2012).
Encryption risk
The newer form of attack and risk are encryption attack. The attacker uses the side channel
attack mechanism. This attack violates the encryption technique used in the application. To
control and reduce these attack are not easy (Fibikova & Mueller, 2012).
Software risk
If the technology is not used in the right direction the incorrect usage of technology may
comprise of privacy and security related issue in information and applications sets. Every
application has their own security and privacy norms, limitations and properties. The attacker
uses the technology in the wrong way by evacuating the malware in the network or by utilization
unnecessarily (Wang, et. al., 2017).
Database risk
In IoT application, the physical and cloud-based database is used. The cloud-based database is a
cost-effective database. The cloud-related security attacks and threats are present that result in
compromising the integrity, availability, and confidentiality of dataset and information’s
(Serpanos & Wolf, 2018).
Network risk
The IoT performs operation and function only if it is connected to the network. In most of the
cases, the application needs to require connection due to this the device connection is developed
under the unsecured network. For example, A person wants to see the examination result on the
Gigantic Corporation: Risk Assessment- Internet of Things (IoT)
6
3.1 Risk assessment based on Industry
Appliance risk
The gigantic corporation will use several devices and tools that are using the IoT applications.
The computer devices, Smartphone, thermometer, healthcare machines are having the
distinguishing properties. The information on these devices is stored in different forms. The
attacker tries to gain the access to these devices and the data stored in the devices. If the
information access is taken by the hacker then serious risks are faced by the organization
(Fibikova & Mueller, 2012).
Complexity in systems risk
The IoT is a complex heterogeneous network that is composed of several communication
technologies. The communication technologies have delayed fraudulent and non-standardized
behavior. The devices that are connecting to the internet are growing day by day. It is predicted
that the devices connected to the internet by 2020 are 20 billion (Serpanos & Wolf, 2018).
Data likability risk
The data collected and processed by IoT are stored in the databases. The devices are linked with
the database. If at any time the linking is beaked by the attacker then the data is not getting
properly from the database. The issue in running the application is faced by the user (Fibikova &
Mueller, 2012).
Encryption risk
The newer form of attack and risk are encryption attack. The attacker uses the side channel
attack mechanism. This attack violates the encryption technique used in the application. To
control and reduce these attack are not easy (Fibikova & Mueller, 2012).
Software risk
If the technology is not used in the right direction the incorrect usage of technology may
comprise of privacy and security related issue in information and applications sets. Every
application has their own security and privacy norms, limitations and properties. The attacker
uses the technology in the wrong way by evacuating the malware in the network or by utilization
unnecessarily (Wang, et. al., 2017).
Database risk
In IoT application, the physical and cloud-based database is used. The cloud-based database is a
cost-effective database. The cloud-related security attacks and threats are present that result in
compromising the integrity, availability, and confidentiality of dataset and information’s
(Serpanos & Wolf, 2018).
Network risk
The IoT performs operation and function only if it is connected to the network. In most of the
cases, the application needs to require connection due to this the device connection is developed
under the unsecured network. For example, A person wants to see the examination result on the
Gigantic Corporation: Risk Assessment- Internet of Things (IoT)
6
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
application at the time when the person is in the hospital for treatment. The person connects
their phone through the public Wi-Fi network for accessing the result. The network has the high
possibility of vulnerabilities that are associated in the network (Ko, Kim & Kim, 2017).
The eavesdropping attack is another form of security attack. In the case of eavesdropping the
attacker keep their eye always on the network activities without the permission. The data can be
captured by using the unauthorized way. The man in the middle attack is similar to the case of
data-stealing (Klipper, 2015).
The man in the middle attack is the phenomenon in which the person in the middle creates the
unusual traffic over the network (Miloslavskaya & Tolstoy, 2018).
Risk assessment Plan
The gigantic organization has many goals that help in understanding the risk and vulnerabilities
associated with the IoT. With the risk assessment new laws, regulation and mandates for the
information security are taken. Areas that encompass information technology in assessing the
risk are:
DRP (Disaster recovery plan): The organization has the high amount of risks or threats. Types
of disaster are act of God, war risk, weather risk so the plan is ready for the organization for the
dealing with disaster risk. The DRP solution plan uses the outsource application in replacement
of in-house IT infrastructure.
BCP (Business continuity planning): The organization has the high amount of investment in
IoT infrastructure. The BCP plan calculates the risk and risk assessment value, asset value,
critically and vulnerability assessment value that help the organization to build the BCP plan
properly in the event of the threat, risk and vulnerability (Ko, Kim & Kim, 2017).
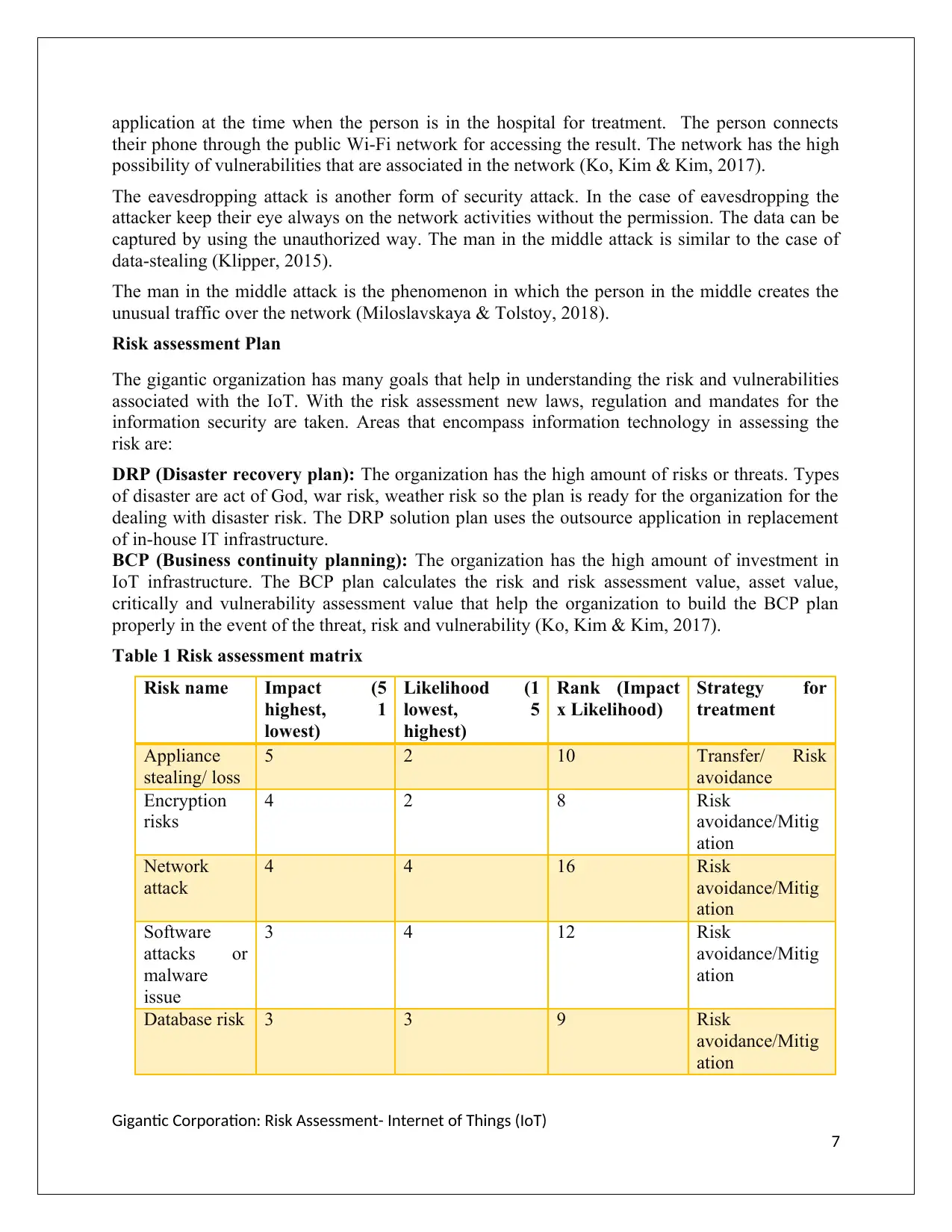
Table 1 Risk assessment matrix
Risk name Impact (5
highest, 1
lowest)
Likelihood (1
lowest, 5
highest)
Rank (Impact
x Likelihood)
Strategy for
treatment
Appliance
stealing/ loss
5 2 10 Transfer/ Risk
avoidance
Encryption
risks
4 2 8 Risk
avoidance/Mitig
ation
Network
attack
4 4 16 Risk
avoidance/Mitig
ation
Software
attacks or
malware
issue
3 4 12 Risk
avoidance/Mitig
ation
Database risk 3 3 9 Risk
avoidance/Mitig
ation
Gigantic Corporation: Risk Assessment- Internet of Things (IoT)
7
their phone through the public Wi-Fi network for accessing the result. The network has the high
possibility of vulnerabilities that are associated in the network (Ko, Kim & Kim, 2017).
The eavesdropping attack is another form of security attack. In the case of eavesdropping the
attacker keep their eye always on the network activities without the permission. The data can be
captured by using the unauthorized way. The man in the middle attack is similar to the case of
data-stealing (Klipper, 2015).
The man in the middle attack is the phenomenon in which the person in the middle creates the
unusual traffic over the network (Miloslavskaya & Tolstoy, 2018).
Risk assessment Plan
The gigantic organization has many goals that help in understanding the risk and vulnerabilities
associated with the IoT. With the risk assessment new laws, regulation and mandates for the
information security are taken. Areas that encompass information technology in assessing the
risk are:
DRP (Disaster recovery plan): The organization has the high amount of risks or threats. Types
of disaster are act of God, war risk, weather risk so the plan is ready for the organization for the
dealing with disaster risk. The DRP solution plan uses the outsource application in replacement
of in-house IT infrastructure.
BCP (Business continuity planning): The organization has the high amount of investment in
IoT infrastructure. The BCP plan calculates the risk and risk assessment value, asset value,
critically and vulnerability assessment value that help the organization to build the BCP plan
properly in the event of the threat, risk and vulnerability (Ko, Kim & Kim, 2017).
Table 1 Risk assessment matrix
Risk name Impact (5
highest, 1
lowest)
Likelihood (1
lowest, 5
highest)
Rank (Impact
x Likelihood)
Strategy for
treatment
Appliance
stealing/ loss
5 2 10 Transfer/ Risk
avoidance
Encryption
risks
4 2 8 Risk
avoidance/Mitig
ation
Network
attack
4 4 16 Risk
avoidance/Mitig
ation
Software
attacks or
malware
issue
3 4 12 Risk
avoidance/Mitig
ation
Database risk 3 3 9 Risk
avoidance/Mitig
ation
Gigantic Corporation: Risk Assessment- Internet of Things (IoT)
7

3.2 Approaches for mitigating security risk
Some of the following techniques for mitigating the security risks in the gigantic corporation are:
1. Monitoring the integrity of file: If any of the files are damaged or altered it sends
the alerts.
2. Segmented networks: The firewalls are used that separate the logically and
physically the hosts that control the compromised hosts (Fischer, 2016)
3. Password management: The password that is used on the website for the access
should be long and complex so no one is emphasizing it.
4. Multifactor authentication: In organizations for managing the passwords internally
the multifactor authentication is used. This has if anyone portion is authenticated than
the second portion still block the unauthorized access (Jansen & Jeschke, 2018).
5. Penetration testing: The penetration testing is performed that identifies the weakness
present in the system like code flaws, operating system patch missing and database
control.
6. Upload controls: The control is used that will limit the user access and
administrative from an unauthorized access and it also ensures that the file can’t be
uploaded at host forcefully.
Figure 2 multi-factor authentication
Source: (CyberSecOn, 2017)
Managing IT risk by using insurance
One of the most common methods of managing the risk is to use the insurance. Once the risk is
identified the insurance is applied to these risks. The insurance is applied that share the property
loss, liability, and income loss. The insurance is applied either to each type or using the
commercial range. Commercial package is cheaper as compared to a separate insurance policy
(Evans, 2018)
The insurance scheme is applied in the Gigantic Corporation that helps in case of disasters. The
risk assessment helps the corporation to overcome the financial loss faced in disaster (Son, Ko,
& Ko, 2015).
Gigantic Corporation: Risk Assessment- Internet of Things (IoT)
8
Some of the following techniques for mitigating the security risks in the gigantic corporation are:
1. Monitoring the integrity of file: If any of the files are damaged or altered it sends
the alerts.
2. Segmented networks: The firewalls are used that separate the logically and
physically the hosts that control the compromised hosts (Fischer, 2016)
3. Password management: The password that is used on the website for the access
should be long and complex so no one is emphasizing it.
4. Multifactor authentication: In organizations for managing the passwords internally
the multifactor authentication is used. This has if anyone portion is authenticated than
the second portion still block the unauthorized access (Jansen & Jeschke, 2018).
5. Penetration testing: The penetration testing is performed that identifies the weakness
present in the system like code flaws, operating system patch missing and database
control.
6. Upload controls: The control is used that will limit the user access and
administrative from an unauthorized access and it also ensures that the file can’t be
uploaded at host forcefully.
Figure 2 multi-factor authentication
Source: (CyberSecOn, 2017)
Managing IT risk by using insurance
One of the most common methods of managing the risk is to use the insurance. Once the risk is
identified the insurance is applied to these risks. The insurance is applied that share the property
loss, liability, and income loss. The insurance is applied either to each type or using the
commercial range. Commercial package is cheaper as compared to a separate insurance policy
(Evans, 2018)
The insurance scheme is applied in the Gigantic Corporation that helps in case of disasters. The
risk assessment helps the corporation to overcome the financial loss faced in disaster (Son, Ko,
& Ko, 2015).
Gigantic Corporation: Risk Assessment- Internet of Things (IoT)
8
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
3.3. Identification of threats, Vulnerabilities, and consequences
Threat identified in Technology components
Networks- firewalls, checkpoints and routers (Shi, 2013).
Gateway
Analytics
Devices connectivity: Pressure sensors, RFID tags, temperature sensors
User interface
Database server
Mobile devices, computer systems, sensors, robots
Automation devices
Threat agents
Hacker/ cybercriminal
Commercial establishment, state
Malicious attacker
Ransomware
Viruses
Environment (like. Natural disaster)
Spoofing and phishing (text messages and fake emails)
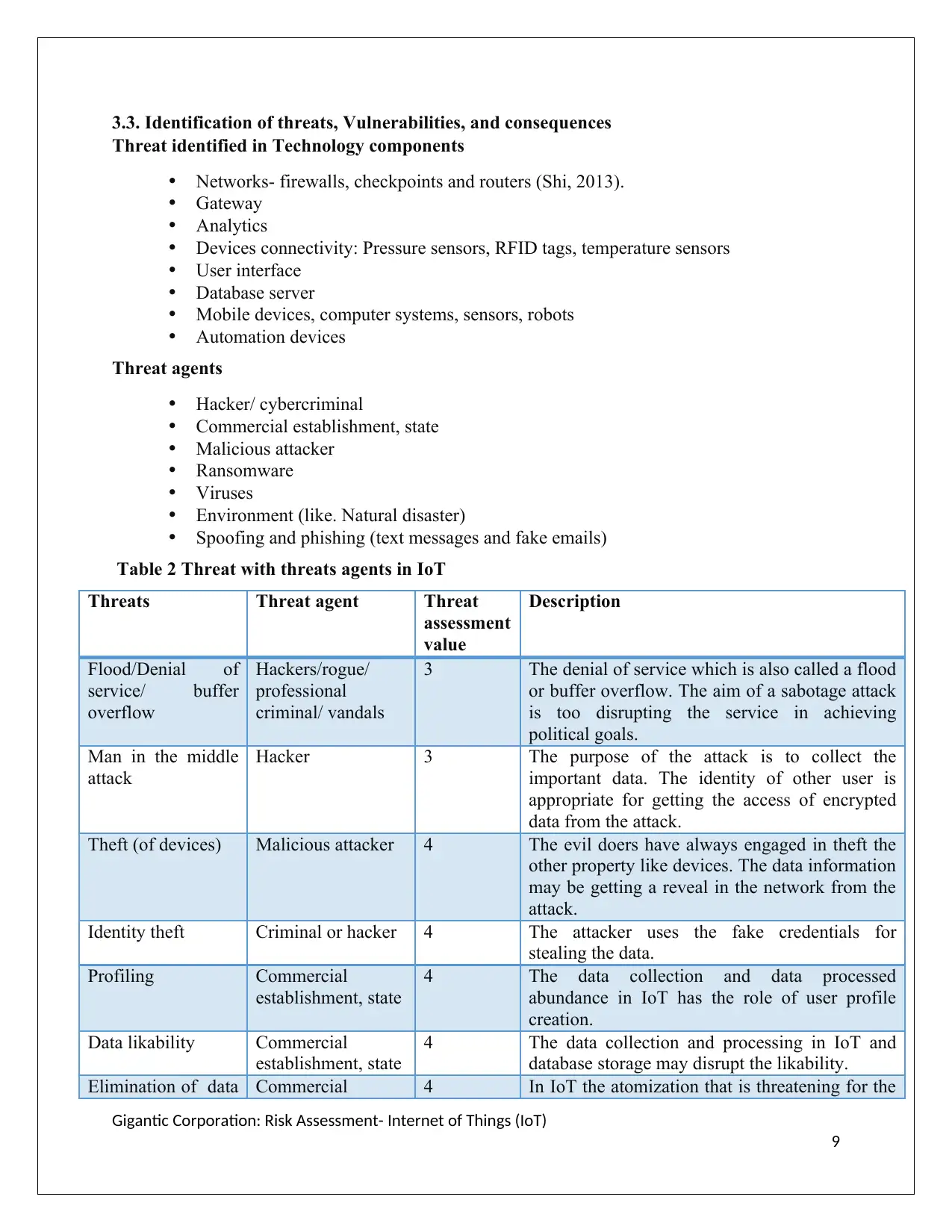
Table 2 Threat with threats agents in IoT
Threats Threat agent Threat
assessment
value
Description
Flood/Denial of
service/ buffer
overflow
Hackers/rogue/
professional
criminal/ vandals
3 The denial of service which is also called a flood
or buffer overflow. The aim of a sabotage attack
is too disrupting the service in achieving
political goals.
Man in the middle
attack
Hacker 3 The purpose of the attack is to collect the
important data. The identity of other user is
appropriate for getting the access of encrypted
data from the attack.
Theft (of devices) Malicious attacker 4 The evil doers have always engaged in theft the
other property like devices. The data information
may be getting a reveal in the network from the
attack.
Identity theft Criminal or hacker 4 The attacker uses the fake credentials for
stealing the data.
Profiling Commercial
establishment, state
4 The data collection and data processed
abundance in IoT has the role of user profile
creation.
Data likability Commercial
establishment, state
4 The data collection and processing in IoT and
database storage may disrupt the likability.
Elimination of data Commercial 4 In IoT the atomization that is threatening for the
Gigantic Corporation: Risk Assessment- Internet of Things (IoT)
9
Threat identified in Technology components
Networks- firewalls, checkpoints and routers (Shi, 2013).
Gateway
Analytics
Devices connectivity: Pressure sensors, RFID tags, temperature sensors
User interface
Database server
Mobile devices, computer systems, sensors, robots
Automation devices
Threat agents
Hacker/ cybercriminal
Commercial establishment, state
Malicious attacker
Ransomware
Viruses
Environment (like. Natural disaster)
Spoofing and phishing (text messages and fake emails)
Table 2 Threat with threats agents in IoT
Threats Threat agent Threat
assessment
value
Description
Flood/Denial of
service/ buffer
overflow
Hackers/rogue/
professional
criminal/ vandals
3 The denial of service which is also called a flood
or buffer overflow. The aim of a sabotage attack
is too disrupting the service in achieving
political goals.
Man in the middle
attack
Hacker 3 The purpose of the attack is to collect the
important data. The identity of other user is
appropriate for getting the access of encrypted
data from the attack.
Theft (of devices) Malicious attacker 4 The evil doers have always engaged in theft the
other property like devices. The data information
may be getting a reveal in the network from the
attack.
Identity theft Criminal or hacker 4 The attacker uses the fake credentials for
stealing the data.
Profiling Commercial
establishment, state
4 The data collection and data processed
abundance in IoT has the role of user profile
creation.
Data likability Commercial
establishment, state
4 The data collection and processing in IoT and
database storage may disrupt the likability.
Elimination of data Commercial 4 In IoT the atomization that is threatening for the
Gigantic Corporation: Risk Assessment- Internet of Things (IoT)
9
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

subject from the
data processing
establishment, state elimination of data subject from data processing.
Vulnerability
It is the term of cyber security that refers to openness in the system say weakness that enhances
the attack in the system.
1. Configuration weakness
Credentials management (Stoll, 2014)
Security maintenance and configuration
Improper authentication
Procedures/ planning/ policy
2. Network weakness
Designing issues
Audit & accountability
Weak rule of firewalls (Shi, 2013)
Implementation issue with components
3. Device security and software weakness
Code quality
Access control, privileges, and permissions
Encryption issue
Management of improper credentials
Security maintenance
Security configuration (Stoll, 2014).
3.3 Identification of common threats and vulnerabilities areas
The devices that are connected through IoT make the life easier for people in sharing, monitoring
and controlling of systems. The data exchange over the internet causes severe security and
privacy issue (Varadharajan & Bansal, 2016).
1. Insecurity over web interface: Most of the IoT devices have built-in web apps that are
hosted by web server has the flawless and error code. These weaknesses in the devices
enhance the security risks. Issues arise in web interface are:
SQL injection
Account enumeration
Session management
XSS (cross-site scripting)
2. Insecurity in network services: The potential security holes in network or network
openness cause the risk in the network such as:
Buffer overflow
Denial of service
Open Ports
Vulnerable services
3. Transportation lacking: The device of IoT is sending private information by using the
insecure security protocol. (Miloslavskaya & Tolstoy, 2018). It is not identified that the IoT
devices involve issues:
Poor in an implementation of SSL/TLS
Gigantic Corporation: Risk Assessment- Internet of Things (IoT)
10
data processing
establishment, state elimination of data subject from data processing.
Vulnerability
It is the term of cyber security that refers to openness in the system say weakness that enhances
the attack in the system.
1. Configuration weakness
Credentials management (Stoll, 2014)
Security maintenance and configuration
Improper authentication
Procedures/ planning/ policy
2. Network weakness
Designing issues
Audit & accountability
Weak rule of firewalls (Shi, 2013)
Implementation issue with components
3. Device security and software weakness
Code quality
Access control, privileges, and permissions
Encryption issue
Management of improper credentials
Security maintenance
Security configuration (Stoll, 2014).
3.3 Identification of common threats and vulnerabilities areas
The devices that are connected through IoT make the life easier for people in sharing, monitoring
and controlling of systems. The data exchange over the internet causes severe security and
privacy issue (Varadharajan & Bansal, 2016).
1. Insecurity over web interface: Most of the IoT devices have built-in web apps that are
hosted by web server has the flawless and error code. These weaknesses in the devices
enhance the security risks. Issues arise in web interface are:
SQL injection
Account enumeration
Session management
XSS (cross-site scripting)
2. Insecurity in network services: The potential security holes in network or network
openness cause the risk in the network such as:
Buffer overflow
Denial of service
Open Ports
Vulnerable services
3. Transportation lacking: The device of IoT is sending private information by using the
insecure security protocol. (Miloslavskaya & Tolstoy, 2018). It is not identified that the IoT
devices involve issues:
Poor in an implementation of SSL/TLS
Gigantic Corporation: Risk Assessment- Internet of Things (IoT)
10

Unencrypted service through the internet and local network
Misconfigured SSL/TLS
4. Improper authentication/ authorization: The user gets the higher level of access then the
required access. The issues are:
Privilege escalation
Lacking in the case of password complexity
Credentials protection by using poor methods (Tekeoglu & Tosun, 2017).
Password recovery insecurely
5. Privacy concerns: The privacy concerns are said to be the data collection process from
automated tools or by simply reviewing the data information. The issue is caused by
collecting the unnecessary information which is personal (Varadharajan & Bansal, 2016).
6. Insecurity in cloud interface: The issue related to the cloud interface in the interaction of
IoT devices. The poor control of authentications is used without the encryption that allows
the attacker to gain the access to device and data such as:
Account enumeration
Revealing of credentials in network traffic
7. Insecurity over mobile interface: Due to weak authentication and authorization the attacker
gain the access of the devices and IoT data (Miloslavskaya & Tolstoy, 2018). The vulnerable
interface of mobile for the user interaction faces issues like:
Account enumeration
Revealing of credentials in network traffic
8. Poor in physical security: This issue is arising if the attacker disconnects the device from
accessing the data. The weakness is also present in accessing the device by using the USB
ports. This cause the unauthorized access of data and device are:
Software access using USB ports and Storage media removal
Figure 3 Threats in IoT
Gigantic Corporation: Risk Assessment- Internet of Things (IoT)
11
Misconfigured SSL/TLS
4. Improper authentication/ authorization: The user gets the higher level of access then the
required access. The issues are:
Privilege escalation
Lacking in the case of password complexity
Credentials protection by using poor methods (Tekeoglu & Tosun, 2017).
Password recovery insecurely
5. Privacy concerns: The privacy concerns are said to be the data collection process from
automated tools or by simply reviewing the data information. The issue is caused by
collecting the unnecessary information which is personal (Varadharajan & Bansal, 2016).
6. Insecurity in cloud interface: The issue related to the cloud interface in the interaction of
IoT devices. The poor control of authentications is used without the encryption that allows
the attacker to gain the access to device and data such as:
Account enumeration
Revealing of credentials in network traffic
7. Insecurity over mobile interface: Due to weak authentication and authorization the attacker
gain the access of the devices and IoT data (Miloslavskaya & Tolstoy, 2018). The vulnerable
interface of mobile for the user interaction faces issues like:
Account enumeration
Revealing of credentials in network traffic
8. Poor in physical security: This issue is arising if the attacker disconnects the device from
accessing the data. The weakness is also present in accessing the device by using the USB
ports. This cause the unauthorized access of data and device are:
Software access using USB ports and Storage media removal
Figure 3 Threats in IoT
Gigantic Corporation: Risk Assessment- Internet of Things (IoT)
11
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 19
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





