IT Risk Management Report: Security Risks and Mitigation in VIC Gov
VerifiedAdded on 2020/03/13
|17
|3721
|49
Report
AI Summary
This report provides an in-depth analysis of IT risk management within the Victorian Government, focusing on the Victorian Protective Data Security Framework (VPDSF) and its role in safeguarding information. It identifies key security risks and concerns, particularly in the transport sector, and explores areas of risk exposure, including accountability and data breaches. The report differentiates between risk and uncertainty, analyzes deliberate and accidental threats, and discusses the challenges faced by the VIC government in implementing effective risk management strategies. It evaluates the availability of VIC government for risk control and mitigation, highlighting the importance of proactive measures such as intrusion detection systems and vulnerability scanners. The report also covers directives, the VGPB strategy, and the roles of stakeholders within the process of risk management, offering a comprehensive overview of the current IT risk landscape and potential improvements. This report is contributed by a student and is available on Desklib, a platform offering AI-based study tools for students.

Running Head: IT RISK MANAGEMENT
IT RISK MANAGEMENT
Name of the Student
Name of the University
IT RISK MANAGEMENT
Name of the Student
Name of the University
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1IT RISK MANAGEMENT
Executive Summary
For the IT risk management and security in Victorian Government the Privacy and Data
Protection Act provides security over the collection and data handling of the personal and
professional field of information. Thus, they established a framework on protective data
security for the public sector. This PDPA encourages the government for the further
development and implementation of this framework collectively known as the Victorian
Protective Data Security Framework (VPDSF).
Executive Summary
For the IT risk management and security in Victorian Government the Privacy and Data
Protection Act provides security over the collection and data handling of the personal and
professional field of information. Thus, they established a framework on protective data
security for the public sector. This PDPA encourages the government for the further
development and implementation of this framework collectively known as the Victorian
Protective Data Security Framework (VPDSF).

2IT RISK MANAGEMENT
Table of Contents
Introduction................................................................................................................................3
1. Identifying the security risks and concerns in VIC government............................................4
2. Identifying areas of Risk Exposure........................................................................................5
3. Analysis of Deliberate and Accidental Threats......................................................................8
4. Challenges in VIC government..............................................................................................8
5. Difference between “Risk” and “Uncertainty”....................................................................10
6. Evaluating the availability of VIC government for Risk Control and Mitigation...............11
Conclusion................................................................................................................................12
References................................................................................................................................13
Table of Contents
Introduction................................................................................................................................3
1. Identifying the security risks and concerns in VIC government............................................4
2. Identifying areas of Risk Exposure........................................................................................5
3. Analysis of Deliberate and Accidental Threats......................................................................8
4. Challenges in VIC government..............................................................................................8
5. Difference between “Risk” and “Uncertainty”....................................................................10
6. Evaluating the availability of VIC government for Risk Control and Mitigation...............11
Conclusion................................................................................................................................12
References................................................................................................................................13
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3IT RISK MANAGEMENT
Introduction
The application of applying principles of risk management in an IT organization that
provides management for the risks and security associated with the IT field is the process
called the IT risk management process. It is combination of culture system and processes that
has been undertaken by the organizations that identifies and coordinates management of risk.
This risk management to achieve the objectives they aim and to prevent the harm should
spread awareness and evidence that explains the need of risk management for the further
decision making process in the organizations (Chance & Brooks 2015). The methodology of
risk management should identify and characterize the threats, determine the general impact of
the risk, identify the way to reduce the risks and hence prioritize the risk reduction based on
the planned strategy in IT sectors. The risks are managed in the sectors of ownership,
involvement, adoption, influence and the use of IT in a larger enterprise. The several numbers
of standards provides general guidance on the practice of risk management. There are much
benefits of using intrusion detection system, firewalls and vulnerability scanner to reduce the
risk and can be used by common people very easily.
In this report we are going to discuss the current security risks and concerns in VIC
government using a diagram. Further explaining the areas of risk exposure in the organization
and analyzing the accidental threats. Justifying the threats and ranking accordingly focusing
on the importance. Explaining and analyzing the security guideline of the private and public
organization. Moreover discussing about the challenges faced by the by the VIC government
during risk management as well as evaluating the available approach of VIC government for
risk control and mitigation with relatable examples. Hence, critically analyzing approaches
for mitigating security risks and evaluating the risks management in terms of vulnerabilities
targeted by hackers.
Introduction
The application of applying principles of risk management in an IT organization that
provides management for the risks and security associated with the IT field is the process
called the IT risk management process. It is combination of culture system and processes that
has been undertaken by the organizations that identifies and coordinates management of risk.
This risk management to achieve the objectives they aim and to prevent the harm should
spread awareness and evidence that explains the need of risk management for the further
decision making process in the organizations (Chance & Brooks 2015). The methodology of
risk management should identify and characterize the threats, determine the general impact of
the risk, identify the way to reduce the risks and hence prioritize the risk reduction based on
the planned strategy in IT sectors. The risks are managed in the sectors of ownership,
involvement, adoption, influence and the use of IT in a larger enterprise. The several numbers
of standards provides general guidance on the practice of risk management. There are much
benefits of using intrusion detection system, firewalls and vulnerability scanner to reduce the
risk and can be used by common people very easily.
In this report we are going to discuss the current security risks and concerns in VIC
government using a diagram. Further explaining the areas of risk exposure in the organization
and analyzing the accidental threats. Justifying the threats and ranking accordingly focusing
on the importance. Explaining and analyzing the security guideline of the private and public
organization. Moreover discussing about the challenges faced by the by the VIC government
during risk management as well as evaluating the available approach of VIC government for
risk control and mitigation with relatable examples. Hence, critically analyzing approaches
for mitigating security risks and evaluating the risks management in terms of vulnerabilities
targeted by hackers.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4IT RISK MANAGEMENT
1. Identifying the security risks and concerns in VIC government
Risk is basically the effect of uncertainty over the objectives. But there is a prior
difference between ‘risks’ and ‘uncertainty’ (will be discussing later in this report). The risk
management process hence implies: 1. The analysis, assessment, identification and
prioritizing the risk for the achievement of the organizational objectives, 2. Allocating the
resources to monitor, communicate, minimize and control risk impact that minimizes the
realization of opportunities, 3. Coordinating to the activities (Chance & Brooks 2015).
The VIC government deals with several processes as mentioned above. The platform
the government mainly concerns about are:
Archives and Record management
Ethical Decision making
Information
Risk Management
Security Management
Safety Response
Using the Social Media
Here we are going to discuss about the Risk Management in the Victorian
Government and it’s impact on the private and public sector of the country (Daly, Cooper &
Ma 2014).
1. Identifying the security risks and concerns in VIC government
Risk is basically the effect of uncertainty over the objectives. But there is a prior
difference between ‘risks’ and ‘uncertainty’ (will be discussing later in this report). The risk
management process hence implies: 1. The analysis, assessment, identification and
prioritizing the risk for the achievement of the organizational objectives, 2. Allocating the
resources to monitor, communicate, minimize and control risk impact that minimizes the
realization of opportunities, 3. Coordinating to the activities (Chance & Brooks 2015).
The VIC government deals with several processes as mentioned above. The platform
the government mainly concerns about are:
Archives and Record management
Ethical Decision making
Information
Risk Management
Security Management
Safety Response
Using the Social Media
Here we are going to discuss about the Risk Management in the Victorian
Government and it’s impact on the private and public sector of the country (Daly, Cooper &
Ma 2014).
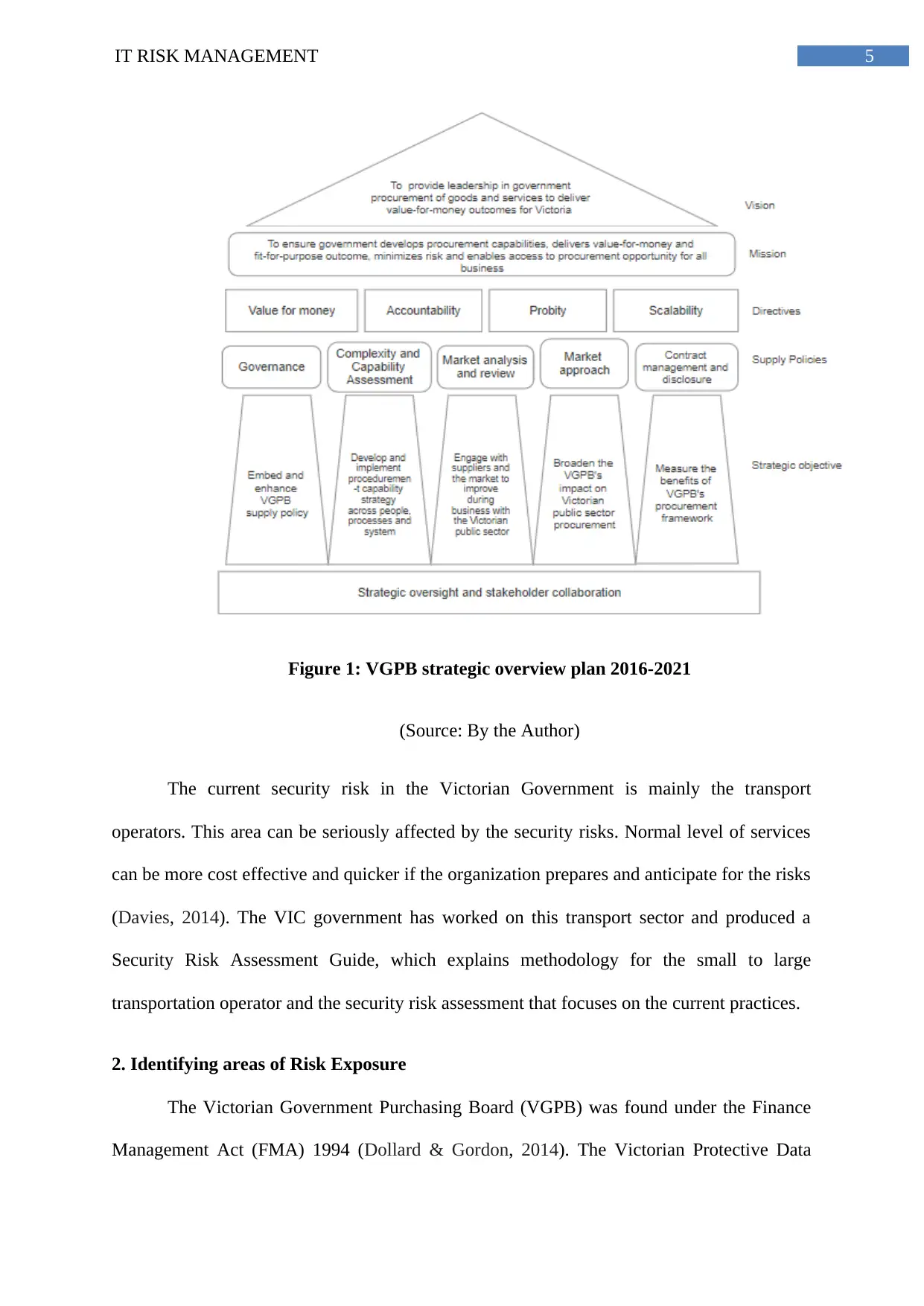
5IT RISK MANAGEMENT
Figure 1: VGPB strategic overview plan 2016-2021
(Source: By the Author)
The current security risk in the Victorian Government is mainly the transport
operators. This area can be seriously affected by the security risks. Normal level of services
can be more cost effective and quicker if the organization prepares and anticipate for the risks
(Davies, 2014). The VIC government has worked on this transport sector and produced a
Security Risk Assessment Guide, which explains methodology for the small to large
transportation operator and the security risk assessment that focuses on the current practices.
2. Identifying areas of Risk Exposure
The Victorian Government Purchasing Board (VGPB) was found under the Finance
Management Act (FMA) 1994 (Dollard & Gordon, 2014). The Victorian Protective Data
Figure 1: VGPB strategic overview plan 2016-2021
(Source: By the Author)
The current security risk in the Victorian Government is mainly the transport
operators. This area can be seriously affected by the security risks. Normal level of services
can be more cost effective and quicker if the organization prepares and anticipate for the risks
(Davies, 2014). The VIC government has worked on this transport sector and produced a
Security Risk Assessment Guide, which explains methodology for the small to large
transportation operator and the security risk assessment that focuses on the current practices.
2. Identifying areas of Risk Exposure
The Victorian Government Purchasing Board (VGPB) was found under the Finance
Management Act (FMA) 1994 (Dollard & Gordon, 2014). The Victorian Protective Data
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6IT RISK MANAGEMENT
Security Framework was established under the Privacy and Data Protection Act in 2014 that
provides data security obligations to the agencies of Victorian public sector (Glendon, Clarke
& McKenna, 2016). It builds the security risk management maturity as well as capabilities by
using the principles and guidelines that already exists; this reflects the unique operating
requirements of the sector.
The Victorian government developed the “Victorian Protective Data Security
Framework” (VPDSF) to monitor, establish and assure the security of information within the
boundaries of Victorian government. The current security risks and concerns of the VIC
government are:
to determine the ownership and identify information
assess the value of information
identifying and managing the data security risks
applying needed security measures
creating positive security culture
maturing the capability of protective data security
Across four protective security domains and governance, VPDSF provides the
organization data security protection. The Victorian government takes care of the national
interest, it remains mandatory for the Protective Security Policy Framework requirements
(Hopkin, 2017).
On the basis of the above diagram we can note that there are five major levels of
VGPB strategy:
Security Framework was established under the Privacy and Data Protection Act in 2014 that
provides data security obligations to the agencies of Victorian public sector (Glendon, Clarke
& McKenna, 2016). It builds the security risk management maturity as well as capabilities by
using the principles and guidelines that already exists; this reflects the unique operating
requirements of the sector.
The Victorian government developed the “Victorian Protective Data Security
Framework” (VPDSF) to monitor, establish and assure the security of information within the
boundaries of Victorian government. The current security risks and concerns of the VIC
government are:
to determine the ownership and identify information
assess the value of information
identifying and managing the data security risks
applying needed security measures
creating positive security culture
maturing the capability of protective data security
Across four protective security domains and governance, VPDSF provides the
organization data security protection. The Victorian government takes care of the national
interest, it remains mandatory for the Protective Security Policy Framework requirements
(Hopkin, 2017).
On the basis of the above diagram we can note that there are five major levels of
VGPB strategy:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7IT RISK MANAGEMENT
1. Vision: This provides leadership of goods and services that delivers value-for-
money in government procurement outcomes for Victorian government
(Howes et al., 2015).
2. Mission: This level ensures the government the ability to minimize risks and
develop the procurement capabilities and enables the accessibility to these
procurement opportunities for all business. This also delivers the value-for-
money and fit-for opportunity.
This policy framework changed the tactics of Victorian Government procure
services and goods after being introduced by VGPB: 1. Enhanced and embed
VGPB supply policy, 2. Implementation and development of a procurement
capability strategy across process, people as well as system, 3. Engaging with
suppliers and the market such that to improve business with the public sector
of Victorian government, 4. Enlarging the impact of VGPB’s on the Victorian
public sector procurement, and 5. Measuring the importance and benefits of
the framework of VGPB procurement.
3. Directives: This section manages the Value-of-money, Accountability,
Probity and Scalability of the framework.
The Assurance model aims to enhance the maturity of the protective data security
practice of an organization and ensures the protection of information against security
breaches.
There is a difference between Risk analysis and Risk Exposure. The areas of risk
exposure can be part of any and every activity (Jaeger et al., 2013). Risk Exposure provides a
measure to the upcoming possibility of losses that may occurs form an activity or event. In IT
business risk exposure often use ranks like low, medium-low, medium and high risk exposure
1. Vision: This provides leadership of goods and services that delivers value-for-
money in government procurement outcomes for Victorian government
(Howes et al., 2015).
2. Mission: This level ensures the government the ability to minimize risks and
develop the procurement capabilities and enables the accessibility to these
procurement opportunities for all business. This also delivers the value-for-
money and fit-for opportunity.
This policy framework changed the tactics of Victorian Government procure
services and goods after being introduced by VGPB: 1. Enhanced and embed
VGPB supply policy, 2. Implementation and development of a procurement
capability strategy across process, people as well as system, 3. Engaging with
suppliers and the market such that to improve business with the public sector
of Victorian government, 4. Enlarging the impact of VGPB’s on the Victorian
public sector procurement, and 5. Measuring the importance and benefits of
the framework of VGPB procurement.
3. Directives: This section manages the Value-of-money, Accountability,
Probity and Scalability of the framework.
The Assurance model aims to enhance the maturity of the protective data security
practice of an organization and ensures the protection of information against security
breaches.
There is a difference between Risk analysis and Risk Exposure. The areas of risk
exposure can be part of any and every activity (Jaeger et al., 2013). Risk Exposure provides a
measure to the upcoming possibility of losses that may occurs form an activity or event. In IT
business risk exposure often use ranks like low, medium-low, medium and high risk exposure

8IT RISK MANAGEMENT
depending on the different kind of losses either it is acceptable or unacceptable. This may
include legal liability, damaged or loss of property, employee’s unexpected turnover or in the
change in demand of the customers (Kaine et al., 2017).
In the Figure 1, the area of higher risk exposure is the Accountability since the
accountancy part is risky and can be data breaches by penetrating the security system. The
area of low-medium risk is the value of money (Lam, 2014). The third position for medium
risk is the scalability and the lowest is the probity since it deals with the public sector.
3. Analysis of Deliberate and Accidental Threats
An example of a common threat in VIC:
Threats to damage and destroy property-
A person can be determined as a threat for another person on not having lawful
excuse (Lane et al., 2017)
a) To damage and destroy a property that may belong to himself or any third person
b) To damage and destroy one’s own property in complete sense of knowing or
believing that the property can endanger the life of others.
Threats to kill-
A person can be determined as a threat for another person who threatens to kill the other
person
a) The other person is intended to fear the threat and hence would be carried out forward
b) Being reckless about the person’s intension of fearing the threat can be carried out
further
The current security risk in the Victorian Government is mainly the transport
operators. This area can be seriously affected by the security risks (Liu et al., 2016). Normal
level of services can be more cost effective and quicker if the organization prepares and
depending on the different kind of losses either it is acceptable or unacceptable. This may
include legal liability, damaged or loss of property, employee’s unexpected turnover or in the
change in demand of the customers (Kaine et al., 2017).
In the Figure 1, the area of higher risk exposure is the Accountability since the
accountancy part is risky and can be data breaches by penetrating the security system. The
area of low-medium risk is the value of money (Lam, 2014). The third position for medium
risk is the scalability and the lowest is the probity since it deals with the public sector.
3. Analysis of Deliberate and Accidental Threats
An example of a common threat in VIC:
Threats to damage and destroy property-
A person can be determined as a threat for another person on not having lawful
excuse (Lane et al., 2017)
a) To damage and destroy a property that may belong to himself or any third person
b) To damage and destroy one’s own property in complete sense of knowing or
believing that the property can endanger the life of others.
Threats to kill-
A person can be determined as a threat for another person who threatens to kill the other
person
a) The other person is intended to fear the threat and hence would be carried out forward
b) Being reckless about the person’s intension of fearing the threat can be carried out
further
The current security risk in the Victorian Government is mainly the transport
operators. This area can be seriously affected by the security risks (Liu et al., 2016). Normal
level of services can be more cost effective and quicker if the organization prepares and
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9IT RISK MANAGEMENT
anticipate for the risks. The VIC government has worked on this transport sector and
produced a Security Risk Assessment Guide, which explains methodology for the small to
large transportation operator and the security risk assessment that focuses on the current
practices (McNeil, Frey & Embrechts, 2015). The methodology of risk management should
identify and characterize the threats, determine the general impact of the risk, identify the
way to reduce the risks and hence prioritize the risk reduction based on the planned strategy
in IT sectors. On the case study of NSW Government Disaster Recovery, the risks are
managed in the sectors of ownership, involvement, adoption, influence and the use of IT in a
larger enterprise. The several numbers of standards provides general guidance on the practice
of risk management. There are much benefits of using intrusion detection system, firewalls
and vulnerability scanner to reduce the risk and can be used by common people very easily.
4. Challenges in VIC government
The main challenges are faced by the public sector in the VIC government (Nicholson
et al., 2015). Hence there are several principle based on which the VIC government should
carry forward the risk management via outsourcing:
Risk Management Applying technique Importance
1. Creating and protecting the
value
Mainly incorporated in
governance framework
Part of organizational
culture should be considered
Improvement of
performance
Achievement of the
objective
2. Integral part of the agency
planning and management
process
Maintaining the strategic
and business planning
Part of change management
process
Avoids delicacy
Guides the prioritization
Classifies responsibilities
anticipate for the risks. The VIC government has worked on this transport sector and
produced a Security Risk Assessment Guide, which explains methodology for the small to
large transportation operator and the security risk assessment that focuses on the current
practices (McNeil, Frey & Embrechts, 2015). The methodology of risk management should
identify and characterize the threats, determine the general impact of the risk, identify the
way to reduce the risks and hence prioritize the risk reduction based on the planned strategy
in IT sectors. On the case study of NSW Government Disaster Recovery, the risks are
managed in the sectors of ownership, involvement, adoption, influence and the use of IT in a
larger enterprise. The several numbers of standards provides general guidance on the practice
of risk management. There are much benefits of using intrusion detection system, firewalls
and vulnerability scanner to reduce the risk and can be used by common people very easily.
4. Challenges in VIC government
The main challenges are faced by the public sector in the VIC government (Nicholson
et al., 2015). Hence there are several principle based on which the VIC government should
carry forward the risk management via outsourcing:
Risk Management Applying technique Importance
1. Creating and protecting the
value
Mainly incorporated in
governance framework
Part of organizational
culture should be considered
Improvement of
performance
Achievement of the
objective
2. Integral part of the agency
planning and management
process
Maintaining the strategic
and business planning
Part of change management
process
Avoids delicacy
Guides the prioritization
Classifies responsibilities
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
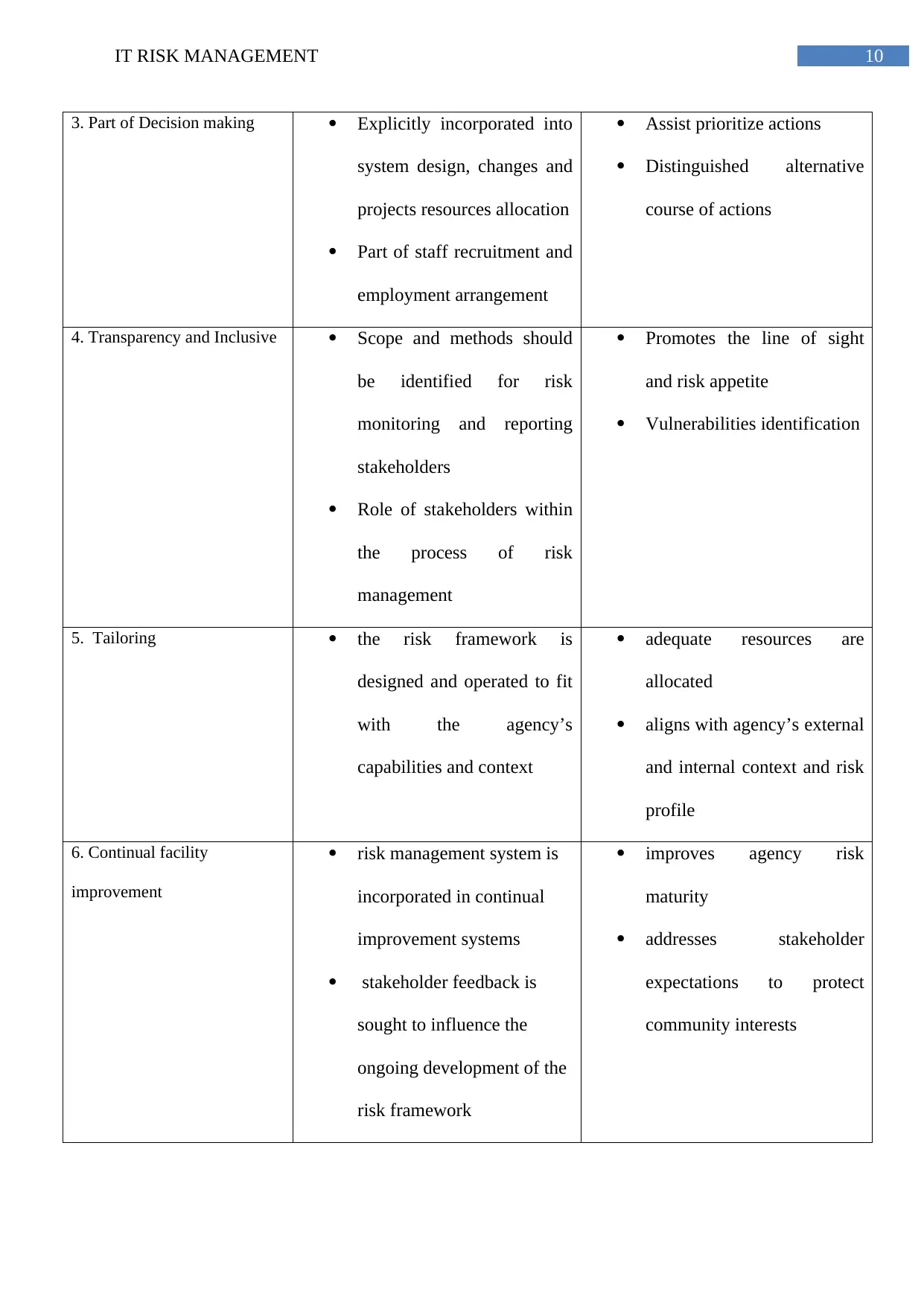
10IT RISK MANAGEMENT
3. Part of Decision making Explicitly incorporated into
system design, changes and
projects resources allocation
Part of staff recruitment and
employment arrangement
Assist prioritize actions
Distinguished alternative
course of actions
4. Transparency and Inclusive Scope and methods should
be identified for risk
monitoring and reporting
stakeholders
Role of stakeholders within
the process of risk
management
Promotes the line of sight
and risk appetite
Vulnerabilities identification
5. Tailoring the risk framework is
designed and operated to fit
with the agency’s
capabilities and context
adequate resources are
allocated
aligns with agency’s external
and internal context and risk
profile
6. Continual facility
improvement
risk management system is
incorporated in continual
improvement systems
stakeholder feedback is
sought to influence the
ongoing development of the
risk framework
improves agency risk
maturity
addresses stakeholder
expectations to protect
community interests
3. Part of Decision making Explicitly incorporated into
system design, changes and
projects resources allocation
Part of staff recruitment and
employment arrangement
Assist prioritize actions
Distinguished alternative
course of actions
4. Transparency and Inclusive Scope and methods should
be identified for risk
monitoring and reporting
stakeholders
Role of stakeholders within
the process of risk
management
Promotes the line of sight
and risk appetite
Vulnerabilities identification
5. Tailoring the risk framework is
designed and operated to fit
with the agency’s
capabilities and context
adequate resources are
allocated
aligns with agency’s external
and internal context and risk
profile
6. Continual facility
improvement
risk management system is
incorporated in continual
improvement systems
stakeholder feedback is
sought to influence the
ongoing development of the
risk framework
improves agency risk
maturity
addresses stakeholder
expectations to protect
community interests

11IT RISK MANAGEMENT
5. Difference between “Risk” and “Uncertainty”
The main difference between the risk and uncertainty is that risk is an unplanned
event and occurrence of risk may affect of the objectives in management (Paschen & Beilin,
2017). It may either affect the project positively or negatively hence risk can both be a
positive risk as well as a negative risk. The main objective is to minimize the negative
strategy impact of risks and to maximize the positive risk response is the chances of
happening positive risks. Risks have been identified during the risk identifying process (Potts,
Rajabifard & Bennett, 2017). The Unknown risks are those risks which cannot be identified
during the risk identification processes.
Lack of certainty is known as the uncertainty. The outcome of any event is said to be
completely unknown in uncertainty, and it cannot be guessed or measured thus we don’t get
any background information on certain event. In uncertainty, one completely lacks the
information of the event even though it has been identified earlier (Slovic, 2016). In case of
such unknown risks, although having the information background, people simply ignores it
during the identify risks process.
The following are a few differences between risk and uncertainty:
The possibility of future outcome cannot be predicted while being in uncertainty
Uncertainty is uncontrollable but risk can still be managed
Uncertainty cannot be measures and quantified while risk can be
One can assign the probability of risk events but with uncertainty one cannot
In the considered case study of VIC government the risk and uncertainty are governance and
the sector of market approach respectively.
5. Difference between “Risk” and “Uncertainty”
The main difference between the risk and uncertainty is that risk is an unplanned
event and occurrence of risk may affect of the objectives in management (Paschen & Beilin,
2017). It may either affect the project positively or negatively hence risk can both be a
positive risk as well as a negative risk. The main objective is to minimize the negative
strategy impact of risks and to maximize the positive risk response is the chances of
happening positive risks. Risks have been identified during the risk identifying process (Potts,
Rajabifard & Bennett, 2017). The Unknown risks are those risks which cannot be identified
during the risk identification processes.
Lack of certainty is known as the uncertainty. The outcome of any event is said to be
completely unknown in uncertainty, and it cannot be guessed or measured thus we don’t get
any background information on certain event. In uncertainty, one completely lacks the
information of the event even though it has been identified earlier (Slovic, 2016). In case of
such unknown risks, although having the information background, people simply ignores it
during the identify risks process.
The following are a few differences between risk and uncertainty:
The possibility of future outcome cannot be predicted while being in uncertainty
Uncertainty is uncontrollable but risk can still be managed
Uncertainty cannot be measures and quantified while risk can be
One can assign the probability of risk events but with uncertainty one cannot
In the considered case study of VIC government the risk and uncertainty are governance and
the sector of market approach respectively.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 17
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





