IT Risk Management Report: Security Threats and Mitigation Strategies
VerifiedAdded on 2020/03/01
|15
|2864
|45
Report
AI Summary
This report provides an in-depth analysis of IT risk management within the Victorian government, focusing on the Victorian Protective Data Security Framework (VPDSF). It begins with a diagram illustrating current security risks and concerns, followed by a detailed explanation. The report then conducts a comparative analysis of deliberate and accidental threats, including trespass, information extortion, social engineering, and poor password security. It explores the challenges the Victorian government faces in implementing risk management, such as outsourcing security and protecting against global IT infrastructure threats. Furthermore, the report differentiates between risk and uncertainty, outlining their key differences in terms of meaning, outcome, control, and insurability. Finally, it discusses and evaluates various approaches for risk control and mitigation, including establishing context, risk identification, risk analysis, risk treatment, consultation and communication, and monitoring and review. The report utilizes examples and theoretical explanations to provide a comprehensive understanding of IT risk management within the public sector.

Running head: IT RISK MANAGEMENT
IT risk management
(Victoria government)
Name of the student:
Name of the university:
Author Note
IT risk management
(Victoria government)
Name of the student:
Name of the university:
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1IT RISK MANAGEMENT
Executive summary
The report has utilized diagram and theoretical explanations about the areas of risk faced by VIC
government. It has performed the comparative analysis on accidental and deliberate threats and the
challenges faced by VIC government to implement the risk management. It has also compared the
ideas of risk and uncertainty and lastly discussed with examples the process to control and mitigate
risks.
Executive summary
The report has utilized diagram and theoretical explanations about the areas of risk faced by VIC
government. It has performed the comparative analysis on accidental and deliberate threats and the
challenges faced by VIC government to implement the risk management. It has also compared the
ideas of risk and uncertainty and lastly discussed with examples the process to control and mitigate
risks.

2IT RISK MANAGEMENT
Table of Contents
Introduction:..........................................................................................................................................3
1. Diagram illustrating the current security risks and concerns considered by VIC government:........4
2. Explanation of the diagram:...............................................................................................................4
3. Comparative analysis of the Deliberate and Accidental Threats:......................................................6
4. Challenges that VIC government might face:...................................................................................7
5. Difference between the ‘’Risk’’ and ‘’Uncertainty’’:......................................................................8
6. Discussion and evaluation of different approaches available for risk control and mitigation:.......11
Conclusion:..........................................................................................................................................12
References:..........................................................................................................................................14
Table of Contents
Introduction:..........................................................................................................................................3
1. Diagram illustrating the current security risks and concerns considered by VIC government:........4
2. Explanation of the diagram:...............................................................................................................4
3. Comparative analysis of the Deliberate and Accidental Threats:......................................................6
4. Challenges that VIC government might face:...................................................................................7
5. Difference between the ‘’Risk’’ and ‘’Uncertainty’’:......................................................................8
6. Discussion and evaluation of different approaches available for risk control and mitigation:.......11
Conclusion:..........................................................................................................................................12
References:..........................................................................................................................................14
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3IT RISK MANAGEMENT
Introduction:
The VPDSF or the “Victorian Protective Data Security Framework” has been the overall
scheme to manage the protective risks of data security at the public sector of Victoria. The
framework has been encouraging the cultural transformation in the sector through the promotion of
protective security of data as the part of daily business ("CPDP - Home", 2017).
The following report used diagram and theoretical explanations about the areas of risk. It has
covered the comparative analysis on accidental and deliberate threats and the challenges faced by
VIC or Victoria government to implement the risk management. Further, it has compared the ideas
of risk and uncertainty and lastly discussed with examples the process to control and mitigate risks.
Introduction:
The VPDSF or the “Victorian Protective Data Security Framework” has been the overall
scheme to manage the protective risks of data security at the public sector of Victoria. The
framework has been encouraging the cultural transformation in the sector through the promotion of
protective security of data as the part of daily business ("CPDP - Home", 2017).
The following report used diagram and theoretical explanations about the areas of risk. It has
covered the comparative analysis on accidental and deliberate threats and the challenges faced by
VIC or Victoria government to implement the risk management. Further, it has compared the ideas
of risk and uncertainty and lastly discussed with examples the process to control and mitigate risks.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
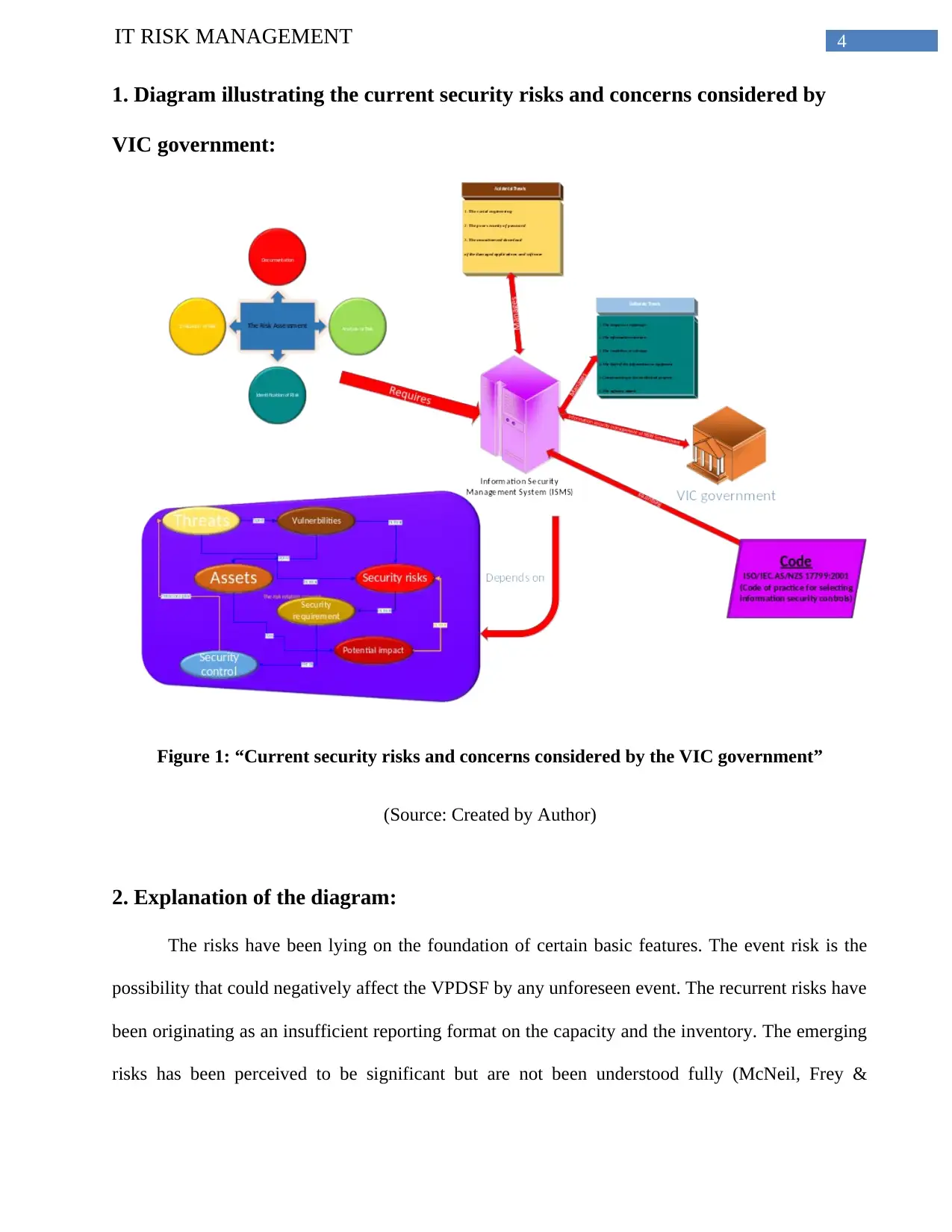
4IT RISK MANAGEMENT
1. Diagram illustrating the current security risks and concerns considered by
VIC government:
Figure 1: “Current security risks and concerns considered by the VIC government”
(Source: Created by Author)
2. Explanation of the diagram:
The risks have been lying on the foundation of certain basic features. The event risk is the
possibility that could negatively affect the VPDSF by any unforeseen event. The recurrent risks have
been originating as an insufficient reporting format on the capacity and the inventory. The emerging
risks has been perceived to be significant but are not been understood fully (McNeil, Frey &
1. Diagram illustrating the current security risks and concerns considered by
VIC government:
Figure 1: “Current security risks and concerns considered by the VIC government”
(Source: Created by Author)
2. Explanation of the diagram:
The risks have been lying on the foundation of certain basic features. The event risk is the
possibility that could negatively affect the VPDSF by any unforeseen event. The recurrent risks have
been originating as an insufficient reporting format on the capacity and the inventory. The emerging
risks has been perceived to be significant but are not been understood fully (McNeil, Frey &
5IT RISK MANAGEMENT
Embrechts, 2015). There have been the creeping risks also. They have been originating from the
present non-planning. These are done by various jurisdictions of the rising demographic changes in
the workplace.
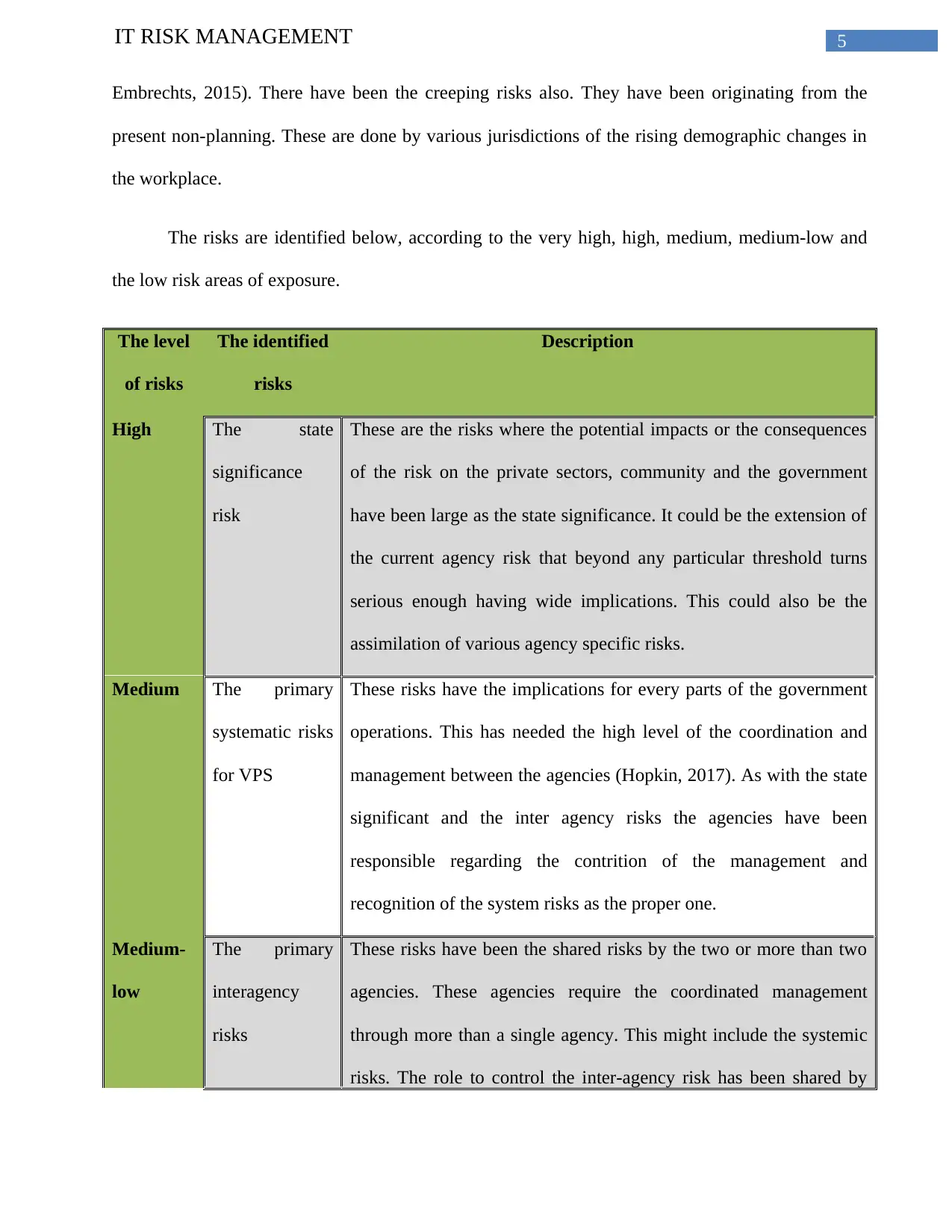
The risks are identified below, according to the very high, high, medium, medium-low and
the low risk areas of exposure.
The level
of risks
The identified
risks
Description
High The state
significance
risk
These are the risks where the potential impacts or the consequences
of the risk on the private sectors, community and the government
have been large as the state significance. It could be the extension of
the current agency risk that beyond any particular threshold turns
serious enough having wide implications. This could also be the
assimilation of various agency specific risks.
Medium The primary
systematic risks
for VPS
These risks have the implications for every parts of the government
operations. This has needed the high level of the coordination and
management between the agencies (Hopkin, 2017). As with the state
significant and the inter agency risks the agencies have been
responsible regarding the contrition of the management and
recognition of the system risks as the proper one.
Medium-
low
The primary
interagency
risks
These risks have been the shared risks by the two or more than two
agencies. These agencies require the coordinated management
through more than a single agency. This might include the systemic
risks. The role to control the inter-agency risk has been shared by
Embrechts, 2015). There have been the creeping risks also. They have been originating from the
present non-planning. These are done by various jurisdictions of the rising demographic changes in
the workplace.
The risks are identified below, according to the very high, high, medium, medium-low and
the low risk areas of exposure.
The level
of risks
The identified
risks
Description
High The state
significance
risk
These are the risks where the potential impacts or the consequences
of the risk on the private sectors, community and the government
have been large as the state significance. It could be the extension of
the current agency risk that beyond any particular threshold turns
serious enough having wide implications. This could also be the
assimilation of various agency specific risks.
Medium The primary
systematic risks
for VPS
These risks have the implications for every parts of the government
operations. This has needed the high level of the coordination and
management between the agencies (Hopkin, 2017). As with the state
significant and the inter agency risks the agencies have been
responsible regarding the contrition of the management and
recognition of the system risks as the proper one.
Medium-
low
The primary
interagency
risks
These risks have been the shared risks by the two or more than two
agencies. These agencies require the coordinated management
through more than a single agency. This might include the systemic
risks. The role to control the inter-agency risk has been shared by
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6IT RISK MANAGEMENT
every related agency and takes advantages from the coordinated
responses. Here one of the agencies has been taking the lead role.
Low The agency
specific risks
These risks could be managed completely under one operation of the
agency (Davies, 2014). It could be well understood generally and
managed effectively with the simple process of risk management.
3. Comparative analysis of the Deliberate and Accidental Threats:
The deliberate threats:
These types of threats are arranged according to their order of importance.
1. The trespass or espionage:
This has been taking place as any unauthorized people try to have illegal access.
2. The information extortion:
This has been happening as the attackers threatened by the conditions commit any theft or
they possess their individual intention in committing theft of the data under VPDSF.
3. The vandalism or sabotage:
This has also been taking place which id the international act involving the destruction of the
website of VPDSF.
4. The theft of the information or equipment:
As the storage devices or the computers experience the decrease in size and the rise in
strength the devices could be stolen easily. The cost of the loss of the electronic devices like the
every related agency and takes advantages from the coordinated
responses. Here one of the agencies has been taking the lead role.
Low The agency
specific risks
These risks could be managed completely under one operation of the
agency (Davies, 2014). It could be well understood generally and
managed effectively with the simple process of risk management.
3. Comparative analysis of the Deliberate and Accidental Threats:
The deliberate threats:
These types of threats are arranged according to their order of importance.
1. The trespass or espionage:
This has been taking place as any unauthorized people try to have illegal access.
2. The information extortion:
This has been happening as the attackers threatened by the conditions commit any theft or
they possess their individual intention in committing theft of the data under VPDSF.
3. The vandalism or sabotage:
This has also been taking place which id the international act involving the destruction of the
website of VPDSF.
4. The theft of the information or equipment:
As the storage devices or the computers experience the decrease in size and the rise in
strength the devices could be stolen easily. The cost of the loss of the electronic devices like the
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7IT RISK MANAGEMENT
laptops has been including the loss of intellectual property, data, productivity and new laptop
replacement.
5. Compromising to the intellectual property:
This has been created by various people and organizations. They are protected by the
copyright laws, patent and trade secret.
6. The software attack:
This has been rising in the age of computerization as the attackers have been using the
malicious software infecting more companies worldwide (Haimes, 2015).
The accidental threats:
The accidental threats have been happening as the staffs have not been vigilant or alert. They
have been moreover unaware of the consequences or risks of the cyber attacks and are unaware of
the security policies. These threats have been regarding the following.
1. The social engineering:
This has been occurring as the staffs fall victim to the phishing attacks where the attackers
retrieve the sensitive data through impersonating anyone trusted.
2. The poor security of password:
This take place as the staff sets weak passwords or possesses poor behavior such as wiring or
sharing them down anywhere. This has been thus permitting the access to the unauthorized people.
laptops has been including the loss of intellectual property, data, productivity and new laptop
replacement.
5. Compromising to the intellectual property:
This has been created by various people and organizations. They are protected by the
copyright laws, patent and trade secret.
6. The software attack:
This has been rising in the age of computerization as the attackers have been using the
malicious software infecting more companies worldwide (Haimes, 2015).
The accidental threats:
The accidental threats have been happening as the staffs have not been vigilant or alert. They
have been moreover unaware of the consequences or risks of the cyber attacks and are unaware of
the security policies. These threats have been regarding the following.
1. The social engineering:
This has been occurring as the staffs fall victim to the phishing attacks where the attackers
retrieve the sensitive data through impersonating anyone trusted.
2. The poor security of password:
This take place as the staff sets weak passwords or possesses poor behavior such as wiring or
sharing them down anywhere. This has been thus permitting the access to the unauthorized people.

8IT RISK MANAGEMENT
3. The unauthorized download of the damaged applications and software:
This has been taking place without the department of IT knowing about that. These
downloads could have the malware spread around the entire network (Mcube, Gerber & Von Solms,
2016).
4. Challenges that VIC government might face:
The message stating that the security should be the essential component of outsourcing is not
new in the market. Similarly the requirement of setting particular criteria, to select the suppliers as
the tool, for managing the outsourcing security risks is also documented. Despite that, the taking in
account of the patterns, of lesser time frames, is often associated with the outsourcing decisions. The
security risk analysis might also be conducted at the proper time and with the needed granularity. In
few cases, the challenges for the risks might not be taken into consideration (Lam, 2014). For
instance, this take place where the very preliminary theory of “Lift and shift” attitude has been
applied in the outsourcing of the activities of business. Also as the security necessities are agreed,
the challenges could also take place with the current responsibility ownership and the security
controls. This happens especially as the amount of vendors is included with the deliveries of the
similar service or product.
The stakeholders or the customers have turned out to be more concerned regarding the
information and privacy confidentiality. This is due to the rise of the abuse of personal information
via identity theft and fraud. The other challenges from the threat levels have also been occurring.
The VIC‘s prominent position under the ICT sector has been pointing to the target for the agent of
threats. They have been finding the comprising of availability, integrity and confidentiality of the
data or the operational capability. Additional concerns have been lying under the global extension of
3. The unauthorized download of the damaged applications and software:
This has been taking place without the department of IT knowing about that. These
downloads could have the malware spread around the entire network (Mcube, Gerber & Von Solms,
2016).
4. Challenges that VIC government might face:
The message stating that the security should be the essential component of outsourcing is not
new in the market. Similarly the requirement of setting particular criteria, to select the suppliers as
the tool, for managing the outsourcing security risks is also documented. Despite that, the taking in
account of the patterns, of lesser time frames, is often associated with the outsourcing decisions. The
security risk analysis might also be conducted at the proper time and with the needed granularity. In
few cases, the challenges for the risks might not be taken into consideration (Lam, 2014). For
instance, this take place where the very preliminary theory of “Lift and shift” attitude has been
applied in the outsourcing of the activities of business. Also as the security necessities are agreed,
the challenges could also take place with the current responsibility ownership and the security
controls. This happens especially as the amount of vendors is included with the deliveries of the
similar service or product.
The stakeholders or the customers have turned out to be more concerned regarding the
information and privacy confidentiality. This is due to the rise of the abuse of personal information
via identity theft and fraud. The other challenges from the threat levels have also been occurring.
The VIC‘s prominent position under the ICT sector has been pointing to the target for the agent of
threats. They have been finding the comprising of availability, integrity and confidentiality of the
data or the operational capability. Additional concerns have been lying under the global extension of
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9IT RISK MANAGEMENT
the IT infrastructures of the country external to the conventional protection domains (Sadgrove,
2016). The selection of the lesser supplier numbers for the critical processes of business have been
resulting in the aggregation of data. This might not take place under the own infrastructure of IT of
VIC. The changes have been delivering new scopes for the agents of identity information
vulnerabilities and assets. This has been in the geographical sectors that might have been more
susceptible to the targeting attacks.
5. Difference between the ‘’Risk’’ and ‘’Uncertainty’’:
There has been a saying that without any risk there has been no gain. As the VIC government
needs to survive in the long term, they require taking the measured risks where the losing probability
has been less comparatively. Moreover the changes of benefits have been higher here. The difference
between the concepts of risk and uncertainty is described below:
The basis Risk Uncertainty
Meaning It has been the probability to
loose or win anything worthy.
This has been implying to the case where the
future vents have been unknown.
Outcome The changes of the outcome
are already known.
Here, the chances of the outcomes are not known.
Control This is controllable. This has been uncontrollable.
Ascertainment It could be measured It could never be measured.
Minimization Here the minimization take
place
Here no minimization take place
Probabilities Here the probabilities are Here no probabilities are assigned.
the IT infrastructures of the country external to the conventional protection domains (Sadgrove,
2016). The selection of the lesser supplier numbers for the critical processes of business have been
resulting in the aggregation of data. This might not take place under the own infrastructure of IT of
VIC. The changes have been delivering new scopes for the agents of identity information
vulnerabilities and assets. This has been in the geographical sectors that might have been more
susceptible to the targeting attacks.
5. Difference between the ‘’Risk’’ and ‘’Uncertainty’’:
There has been a saying that without any risk there has been no gain. As the VIC government
needs to survive in the long term, they require taking the measured risks where the losing probability
has been less comparatively. Moreover the changes of benefits have been higher here. The difference
between the concepts of risk and uncertainty is described below:
The basis Risk Uncertainty
Meaning It has been the probability to
loose or win anything worthy.
This has been implying to the case where the
future vents have been unknown.
Outcome The changes of the outcome
are already known.
Here, the chances of the outcomes are not known.
Control This is controllable. This has been uncontrollable.
Ascertainment It could be measured It could never be measured.
Minimization Here the minimization take
place
Here no minimization take place
Probabilities Here the probabilities are Here no probabilities are assigned.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
10IT RISK MANAGEMENT
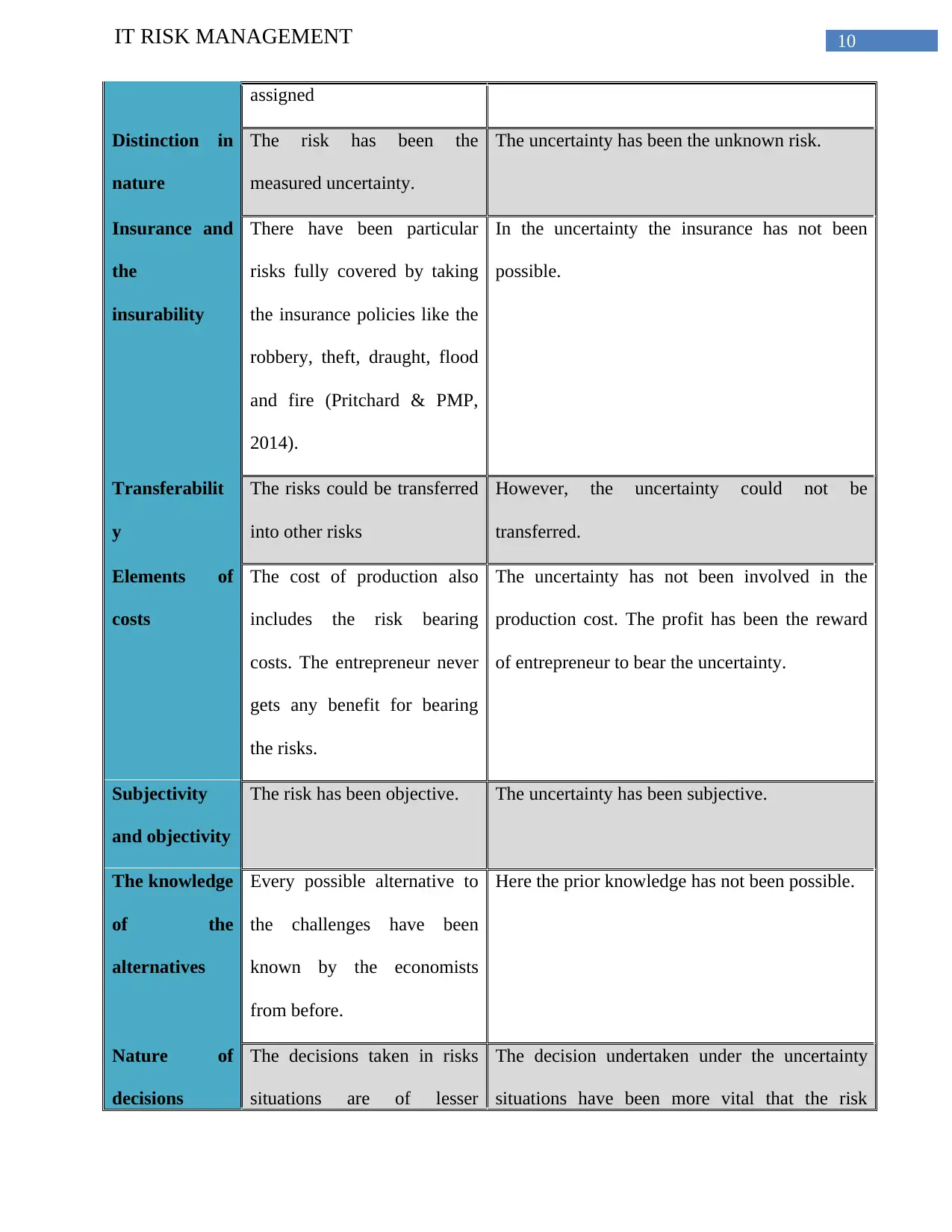
assigned
Distinction in
nature
The risk has been the
measured uncertainty.
The uncertainty has been the unknown risk.
Insurance and
the
insurability
There have been particular
risks fully covered by taking
the insurance policies like the
robbery, theft, draught, flood
and fire (Pritchard & PMP,
2014).
In the uncertainty the insurance has not been
possible.
Transferabilit
y
The risks could be transferred
into other risks
However, the uncertainty could not be
transferred.
Elements of
costs
The cost of production also
includes the risk bearing
costs. The entrepreneur never
gets any benefit for bearing
the risks.
The uncertainty has not been involved in the
production cost. The profit has been the reward
of entrepreneur to bear the uncertainty.
Subjectivity
and objectivity
The risk has been objective. The uncertainty has been subjective.
The knowledge
of the
alternatives
Every possible alternative to
the challenges have been
known by the economists
from before.
Here the prior knowledge has not been possible.
Nature of
decisions
The decisions taken in risks
situations are of lesser
The decision undertaken under the uncertainty
situations have been more vital that the risk
assigned
Distinction in
nature
The risk has been the
measured uncertainty.
The uncertainty has been the unknown risk.
Insurance and
the
insurability
There have been particular
risks fully covered by taking
the insurance policies like the
robbery, theft, draught, flood
and fire (Pritchard & PMP,
2014).
In the uncertainty the insurance has not been
possible.
Transferabilit
y
The risks could be transferred
into other risks
However, the uncertainty could not be
transferred.
Elements of
costs
The cost of production also
includes the risk bearing
costs. The entrepreneur never
gets any benefit for bearing
the risks.
The uncertainty has not been involved in the
production cost. The profit has been the reward
of entrepreneur to bear the uncertainty.
Subjectivity
and objectivity
The risk has been objective. The uncertainty has been subjective.
The knowledge
of the
alternatives
Every possible alternative to
the challenges have been
known by the economists
from before.
Here the prior knowledge has not been possible.
Nature of
decisions
The decisions taken in risks
situations are of lesser
The decision undertaken under the uncertainty
situations have been more vital that the risk

11IT RISK MANAGEMENT
importance. decisions taken under the risk situations
(Webster, 2014). This has been due to the
measuring of the alternatives has not been
possible in the condition of uncertainty.
importance. decisions taken under the risk situations
(Webster, 2014). This has been due to the
measuring of the alternatives has not been
possible in the condition of uncertainty.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 15
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





