IT Risks Report: Analysis for Aztec Company in Financial Services
VerifiedAdded on 2020/03/23
|19
|4997
|109
Report
AI Summary
This report provides an in-depth analysis of IT risk management for the Aztec Company, operating within the Australian Financial Service Sector. The report explores the company's technology decisions, including cloud hosting solutions, outsourcing of IT functions, and the implementation of cloud computing services. It examines the importance of cloud computing for data storage and processing, the benefits of service-oriented architecture, and the impact of virtualization. The report discusses various techniques and problems related to IT infrastructure, including client-server models, grid computing, and utility computing. It also includes a review of the financial services sector, focusing on security postures, threats, vulnerabilities, and data security measures. The report highlights the importance of data classification, encryption, and user authentication, along with cost-benefit and payback analyses related to cloud computing investments. It also covers security standards, the impact of deployment models, and the responsibilities of service providers and consumers in ensuring data security, providing a comprehensive overview of IT risk management within the financial sector.
Report
IT Risks
IT Risks
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser


Executive Summary
The focus of the work is to handle the IT Risks Management for the Aztec Company which
works over the operations in the different Australian Financial Service Sector. It has been seen
there are different executives who look forward to work on the e-business growth and the
technology to take hold of the strategy as well as the funding set for the deployment. The case
study focusses on the technology decisions that are for operating the Australian Financial Service
Sector along with working over the collection of the projects. They are set for the potential
funding for the deployment which includes that the employees can bring their own laptops or the
mobile phones in the working place. Along with this, there is an easy migration of the business-
critical applications and the other associated forms of the data sources that are set for the cloud
hosting solutions. The outsourcing of the key IT functionality is set with the network,
management of the desktop and the applications. The IT infrastructure is based on handling the
needs of the business and then work on the delivery forms of the system. The technology
includes how the organisation can easily instil and host the services for the cloud vendors with
the co-location facilities. The services are based on the matching to the private cloud physical
resources with the standards set to meet the patterns of computing. It also enables the computer
networks, servers and the storage of the applications with minimising the range of the
management effort. The cloud computing solutions are mainly to take hold of the storage and
then processing the data at the effective level.
The cloud computing is important for the company as it will include the solutions which are
related to the users and working over the different capabilities to store. The range is set to allow
the distance from the areas of the different scale economy mainly to advocate and work on the
cloud computing services. It allows the companies to work on the system efficiency and then
holding the demands of the business as well. the check is also on the avoidance of the up-front
infrastructure costs like the server purchasing. The components are based on the applications and
how it is easy to work through it in the fast and the effective manner. The demands are mainly
based on making use of the pay-as-go-model which defines the requirements when the
administrators do not mainly adapt to the change in the pricing model of the cloud. It is mainly to
meet the higher capacity of the networks with the lower costs only related to the storage devices.
The services oriented architecture is based on the standards which includes the defined
scalability and the accessibility pattern, where the cost of the cheap services is define with the
high performance and scalability. The cloud computing is important and helpful as it can cover
the different schematics and then work over the benefits about the expertise by the different IT
obstacles.
The operating system level is set with the virtualisation that includes the scalability of the system
m with the multiple computing of the device. It includes the involvement of the automation
process with the speeding of the process and then working on the cost of the labour with the
reduction and handling the human errors as well. The migration of the business applications with
the proper assessment of risks is based on the needs to review about the different sources of the
data and then work over the system with the data sources to the external cloud hosting. Aztec
management is important for the assessment through the cloud computing with the hosting
solutions. Here, the users are also able to work on the benefits with the technologies that aim to
The focus of the work is to handle the IT Risks Management for the Aztec Company which
works over the operations in the different Australian Financial Service Sector. It has been seen
there are different executives who look forward to work on the e-business growth and the
technology to take hold of the strategy as well as the funding set for the deployment. The case
study focusses on the technology decisions that are for operating the Australian Financial Service
Sector along with working over the collection of the projects. They are set for the potential
funding for the deployment which includes that the employees can bring their own laptops or the
mobile phones in the working place. Along with this, there is an easy migration of the business-
critical applications and the other associated forms of the data sources that are set for the cloud
hosting solutions. The outsourcing of the key IT functionality is set with the network,
management of the desktop and the applications. The IT infrastructure is based on handling the
needs of the business and then work on the delivery forms of the system. The technology
includes how the organisation can easily instil and host the services for the cloud vendors with
the co-location facilities. The services are based on the matching to the private cloud physical
resources with the standards set to meet the patterns of computing. It also enables the computer
networks, servers and the storage of the applications with minimising the range of the
management effort. The cloud computing solutions are mainly to take hold of the storage and
then processing the data at the effective level.
The cloud computing is important for the company as it will include the solutions which are
related to the users and working over the different capabilities to store. The range is set to allow
the distance from the areas of the different scale economy mainly to advocate and work on the
cloud computing services. It allows the companies to work on the system efficiency and then
holding the demands of the business as well. the check is also on the avoidance of the up-front
infrastructure costs like the server purchasing. The components are based on the applications and
how it is easy to work through it in the fast and the effective manner. The demands are mainly
based on making use of the pay-as-go-model which defines the requirements when the
administrators do not mainly adapt to the change in the pricing model of the cloud. It is mainly to
meet the higher capacity of the networks with the lower costs only related to the storage devices.
The services oriented architecture is based on the standards which includes the defined
scalability and the accessibility pattern, where the cost of the cheap services is define with the
high performance and scalability. The cloud computing is important and helpful as it can cover
the different schematics and then work over the benefits about the expertise by the different IT
obstacles.
The operating system level is set with the virtualisation that includes the scalability of the system
m with the multiple computing of the device. It includes the involvement of the automation
process with the speeding of the process and then working on the cost of the labour with the
reduction and handling the human errors as well. The migration of the business applications with
the proper assessment of risks is based on the needs to review about the different sources of the
data and then work over the system with the data sources to the external cloud hosting. Aztec
management is important for the assessment through the cloud computing with the hosting
solutions. Here, the users are also able to work on the benefits with the technologies that aim to
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

the costs as well as the business needs. With this, the technology change is through virtualisation
where the software is based on working on the software of the operating system levels with the
easy maintenance of the scalability of the system. The virtualisation provides the agility with
easy needs to handle the IT operations and then working over the reduced costs of the increased
utilisation of infrastructure. The process is depending upon the resource on demand where the
user involvement and the automation speeding is important for the processes that will reduce the
user involvement with easy service oriented architecture
The resources are also able to provide with the easy access to the growth of the cloud services in
a proper standardised manner, where the cloud model structure can allow the scalability of the
demands to work on the automatic recovery of the prices. Some of the techniques and the
problems which needs to be discussed are:
a. The client server model needs to be accessed depending upon the application that would
be completely different from the other service providers.
b. The forms of the computation with grid computing includes the distributed setup with the
parallel computing structure that includes the network structure with easy coupled to act
and then perform some of the larger tasks.
c. The computation is also based on the IoT applications which includes the real-time
access and how the network configuration process could easily handle the lower level
services.
d. The utility computing with the resource packaging is based on the computation with the
storage set for the public utility that is a major factor for the computation and the peer-to-
peer standards.
where the software is based on working on the software of the operating system levels with the
easy maintenance of the scalability of the system. The virtualisation provides the agility with
easy needs to handle the IT operations and then working over the reduced costs of the increased
utilisation of infrastructure. The process is depending upon the resource on demand where the
user involvement and the automation speeding is important for the processes that will reduce the
user involvement with easy service oriented architecture
The resources are also able to provide with the easy access to the growth of the cloud services in
a proper standardised manner, where the cloud model structure can allow the scalability of the
demands to work on the automatic recovery of the prices. Some of the techniques and the
problems which needs to be discussed are:
a. The client server model needs to be accessed depending upon the application that would
be completely different from the other service providers.
b. The forms of the computation with grid computing includes the distributed setup with the
parallel computing structure that includes the network structure with easy coupled to act
and then perform some of the larger tasks.
c. The computation is also based on the IoT applications which includes the real-time
access and how the network configuration process could easily handle the lower level
services.
d. The utility computing with the resource packaging is based on the computation with the
storage set for the public utility that is a major factor for the computation and the peer-to-
peer standards.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
Financial Services Sector Review...................................................................................................4
Security Posture for Aztec...............................................................................................................7
Threats, vulnerabilities and consequences.....................................................................................11
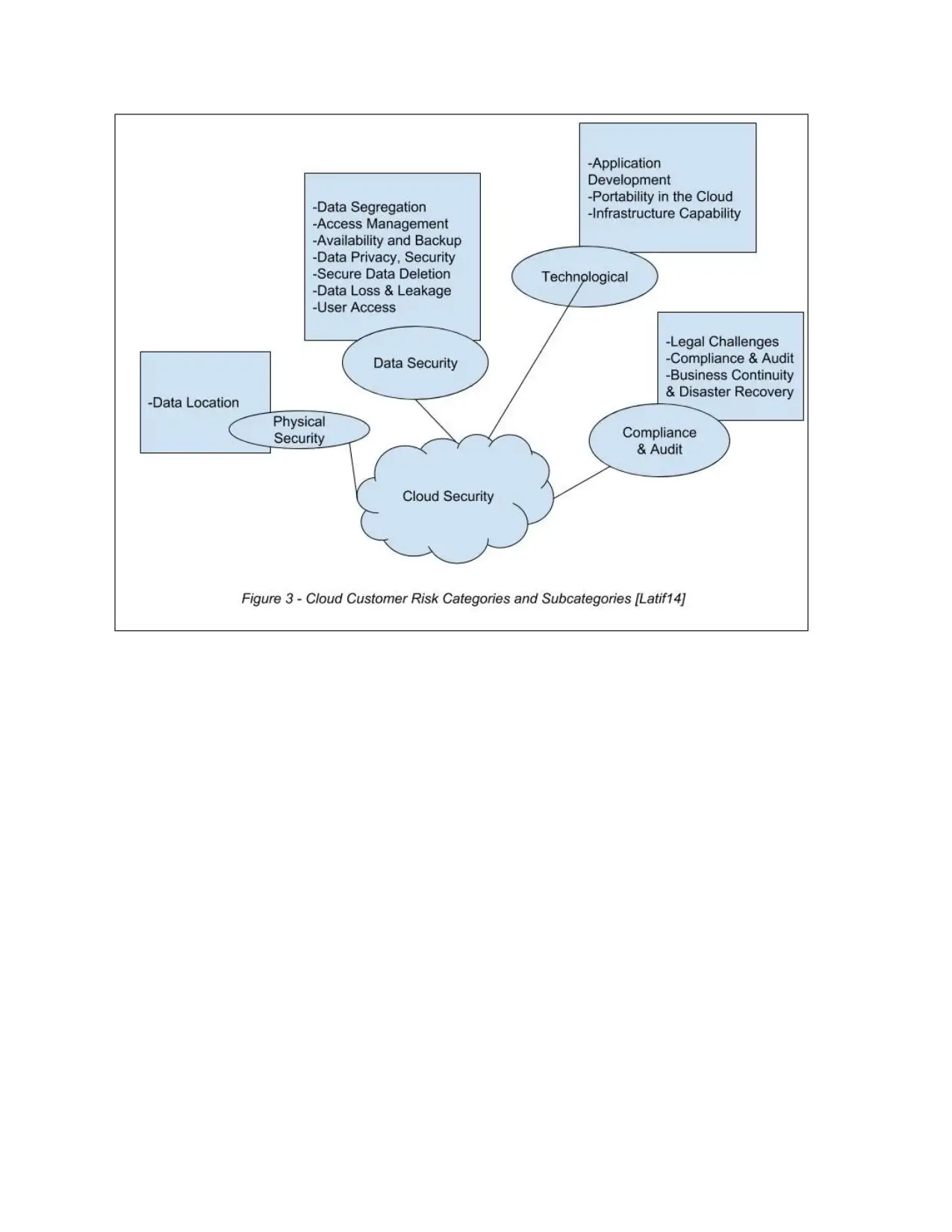
Data Security.................................................................................................................................15
References......................................................................................................................................17
Financial Services Sector Review...................................................................................................4
Security Posture for Aztec...............................................................................................................7
Threats, vulnerabilities and consequences.....................................................................................11
Data Security.................................................................................................................................15
References......................................................................................................................................17

Financial Services Sector Review
As per the setup of the cloud computing factors, there is a need to take hold of the changes with
handling the customer interaction process. The information exchange is based on how the
information in between the organisations need to work with the financial industry. The
understanding is about the cloud adoption with data digitisation which includes the examination
of the financial customer base impacts. The approach is based on the change in technology where
it is important to work over the private, pubic and the hybrid cloud environment. The
deployment models take hold of the cloud strategies with the use of the public and the private
clouds (Jonkers et al., 2016). The additional standards can take hold of the different additional of
the comfort and assure about the practices in the cloud with encouraging the sign in the cloud.
The regulatory standards and the compliance is set to aspire and believe about the achievement
of the efforts to make sure of the different laws and the regulations. The increased regulations
with the consolidation control are mainly to make sure of the necessary governance and how it is
possible to meet the requirements with duplication of efforts. In this, there is a need to check on
the:
a. The assessment is based on how the gap analysis can handle the IT projects which
includes the different set of the laws and the regulation.
b. The communication assessment is to make sure of the regulatory where the assurance of
the quality is mainly through the introduction files to meet the requirements with the
regulators.
c. The target models are defined to operate on the IT infrastructure with easy processes and
the organisation development that leads to the development of the compliance factors.
The financial sectors are mainly for working over the controlled rights and work with the
designing, implementation and then controlling the effectiveness of the system. The forms are
related to understand about the awareness, and the challenges which is mainly related to the
compliance obligations. The market needs to be set with the major impacts highlighting about
the profit and the loss. It comes with the financial services in the organisation that are important
for the short-term consequences. The data accessing is based on the performance where the e-
discovery request needs to be handled through easy encryption of the data with the setup of the
stronger authentication (Buttyan, 2016). The classification of the data, encryption and the
authentication of the users is mainly to make sure of applications that includes the management
and setting the backup as needed.
As per the setup of the cloud computing factors, there is a need to take hold of the changes with
handling the customer interaction process. The information exchange is based on how the
information in between the organisations need to work with the financial industry. The
understanding is about the cloud adoption with data digitisation which includes the examination
of the financial customer base impacts. The approach is based on the change in technology where
it is important to work over the private, pubic and the hybrid cloud environment. The
deployment models take hold of the cloud strategies with the use of the public and the private
clouds (Jonkers et al., 2016). The additional standards can take hold of the different additional of
the comfort and assure about the practices in the cloud with encouraging the sign in the cloud.
The regulatory standards and the compliance is set to aspire and believe about the achievement
of the efforts to make sure of the different laws and the regulations. The increased regulations
with the consolidation control are mainly to make sure of the necessary governance and how it is
possible to meet the requirements with duplication of efforts. In this, there is a need to check on
the:
a. The assessment is based on how the gap analysis can handle the IT projects which
includes the different set of the laws and the regulation.
b. The communication assessment is to make sure of the regulatory where the assurance of
the quality is mainly through the introduction files to meet the requirements with the
regulators.
c. The target models are defined to operate on the IT infrastructure with easy processes and
the organisation development that leads to the development of the compliance factors.
The financial sectors are mainly for working over the controlled rights and work with the
designing, implementation and then controlling the effectiveness of the system. The forms are
related to understand about the awareness, and the challenges which is mainly related to the
compliance obligations. The market needs to be set with the major impacts highlighting about
the profit and the loss. It comes with the financial services in the organisation that are important
for the short-term consequences. The data accessing is based on the performance where the e-
discovery request needs to be handled through easy encryption of the data with the setup of the
stronger authentication (Buttyan, 2016). The classification of the data, encryption and the
authentication of the users is mainly to make sure of applications that includes the management
and setting the backup as needed.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
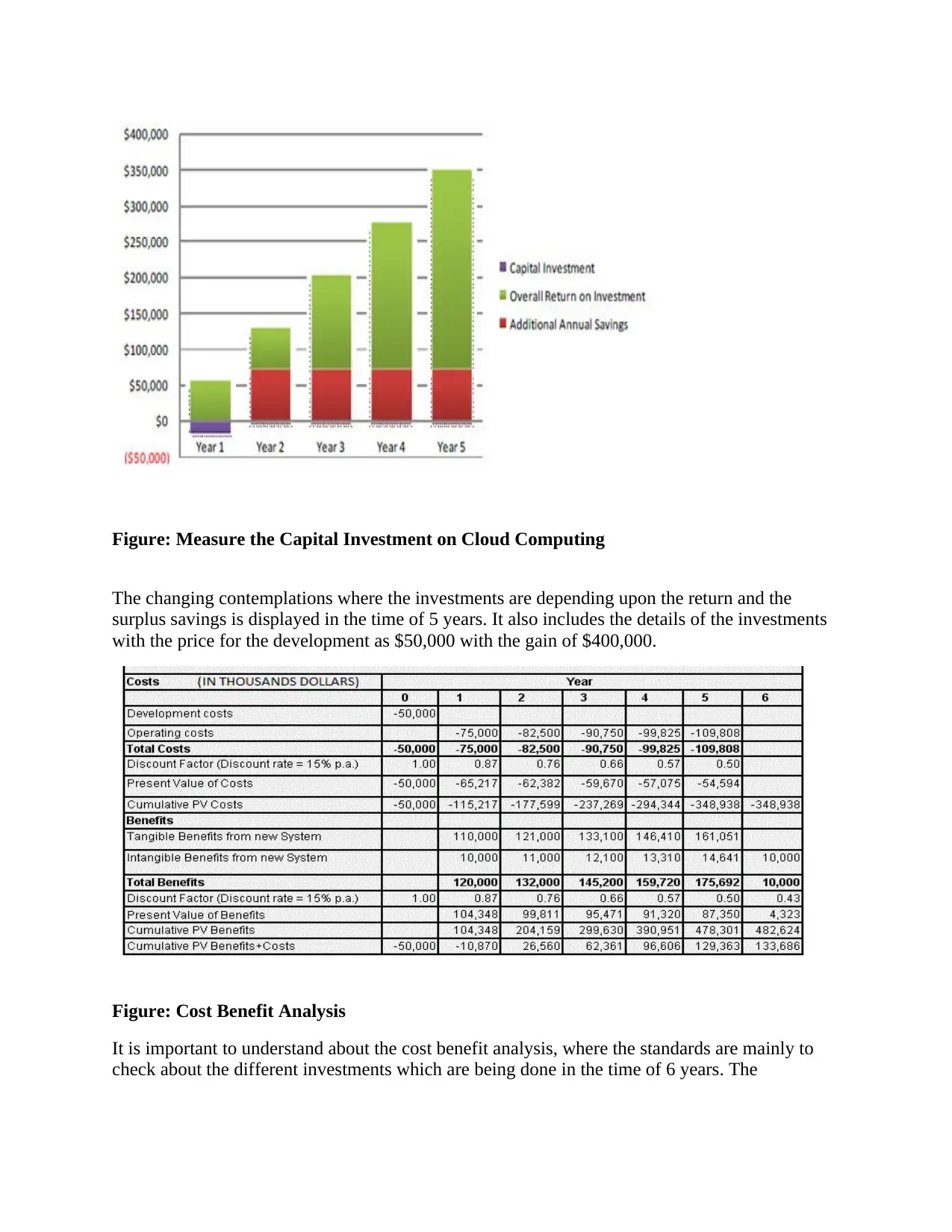
Figure: Measure the Capital Investment on Cloud Computing
The changing contemplations where the investments are depending upon the return and the
surplus savings is displayed in the time of 5 years. It also includes the details of the investments
with the price for the development as $50,000 with the gain of $400,000.
Figure: Cost Benefit Analysis
It is important to understand about the cost benefit analysis, where the standards are mainly to
check about the different investments which are being done in the time of 6 years. The
The changing contemplations where the investments are depending upon the return and the
surplus savings is displayed in the time of 5 years. It also includes the details of the investments
with the price for the development as $50,000 with the gain of $400,000.
Figure: Cost Benefit Analysis
It is important to understand about the cost benefit analysis, where the standards are mainly to
check about the different investments which are being done in the time of 6 years. The
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
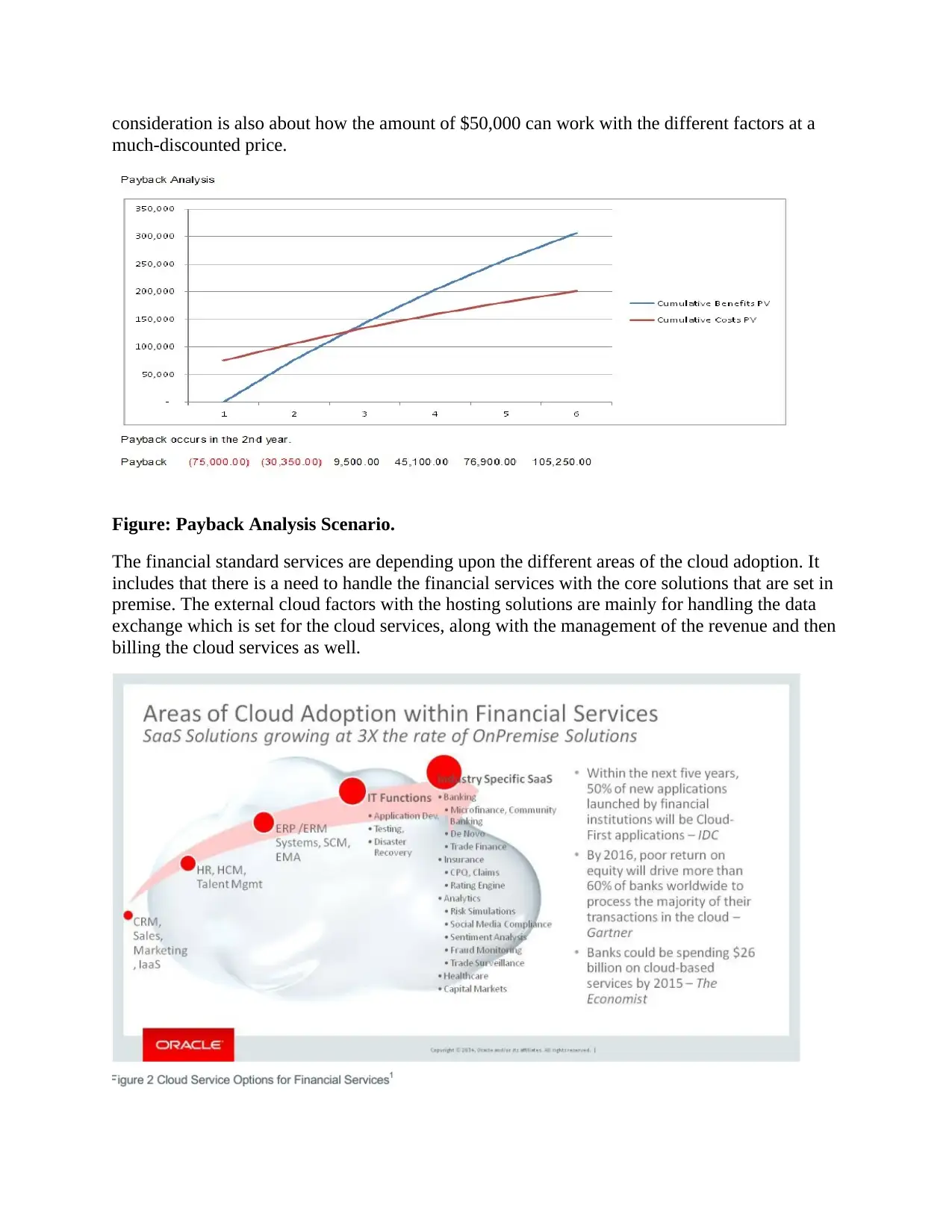
consideration is also about how the amount of $50,000 can work with the different factors at a
much-discounted price.
Figure: Payback Analysis Scenario.
The financial standard services are depending upon the different areas of the cloud adoption. It
includes that there is a need to handle the financial services with the core solutions that are set in
premise. The external cloud factors with the hosting solutions are mainly for handling the data
exchange which is set for the cloud services, along with the management of the revenue and then
billing the cloud services as well.
much-discounted price.
Figure: Payback Analysis Scenario.
The financial standard services are depending upon the different areas of the cloud adoption. It
includes that there is a need to handle the financial services with the core solutions that are set in
premise. The external cloud factors with the hosting solutions are mainly for handling the data
exchange which is set for the cloud services, along with the management of the revenue and then
billing the cloud services as well.

Security Posture for Aztec
As per the management of Aztec, it has been seen that there are different IT applications and the
resources which needs to be defined properly for the security posture. The access is mainly done
to the organisation information resources which is being connected to the network of the
company and managed, operated and worked on by the Aztec. The employees have been
working with the remote management, with the operations that are operated by the Aztec. Hence,
for this, the focus is on the accessing and working over the monitoring, managing and changing
the frameworks of the security. The security standards are set with the different risks that are for
the organisation under the assurance that the data is being secured.
For this, the check is also on providing the huge benefits with the ability to check and handle the
access to the system to properly monitor, manage and then change the framework of security. It
includes the different kinds of the security standards where the risks are in the organisation with
the assurance that the data is being secured (Fernandez et al., 2016).
When Aztec works on deciding about the information standards, there is a need to focus on the
application and the database structure that includes the different kinds of the impacts with the
migration of cloud. The major impact has been on the security which depends on the deployment
model and the service model (Modi et al., 2013). The Public cloud deployment and the
community cloud deployment tend to extend with the security perimeters with the organisation
working to provide the cloud infrastructure with the easy management of the resources. The
forms are set to define the public cloud deployment model and the community cloud which
As per the management of Aztec, it has been seen that there are different IT applications and the
resources which needs to be defined properly for the security posture. The access is mainly done
to the organisation information resources which is being connected to the network of the
company and managed, operated and worked on by the Aztec. The employees have been
working with the remote management, with the operations that are operated by the Aztec. Hence,
for this, the focus is on the accessing and working over the monitoring, managing and changing
the frameworks of the security. The security standards are set with the different risks that are for
the organisation under the assurance that the data is being secured.
For this, the check is also on providing the huge benefits with the ability to check and handle the
access to the system to properly monitor, manage and then change the framework of security. It
includes the different kinds of the security standards where the risks are in the organisation with
the assurance that the data is being secured (Fernandez et al., 2016).
When Aztec works on deciding about the information standards, there is a need to focus on the
application and the database structure that includes the different kinds of the impacts with the
migration of cloud. The major impact has been on the security which depends on the deployment
model and the service model (Modi et al., 2013). The Public cloud deployment and the
community cloud deployment tend to extend with the security perimeters with the organisation
working to provide the cloud infrastructure with the easy management of the resources. The
forms are set to define the public cloud deployment model and the community cloud which
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

includes the provider resources (ISO 27005:2008), which is critical to understand about the
security related obligations. The use of the SLAs and the reporting, networking security
arrangements are based on the obligations which need to be understood with the communication
in the contract. For this the responsibility of the security is based on the forms where the provider
and the consumer can handle the system communication (Almorsy et al., 2016). With this, the
hosting of the critical data like the personal and the payroll is for the employees or the account
details of the customers who try to focus on the cloud that can easily highlight about the
responsibility sharing methods and the other critical cases. The public cloud could be set with the
viable choices when the organisation tends to migrate the information which is made available
for the different consumption process of the public that also tend to carry the lower risks.
The public cloud infrastructure is set when there are equipped security measures for the
information which can easily improve the security posture that is related to the infrastructure
development. It is related to the improvement of the security measures and the postures which
are for the infrastructure when compared to the current posture. The community cloud methods
take hold of the different measures of the security requirements, where the high risks data like
the handling of the customer account information could not be easily trusted with the public or
the community cloud (Cavelty et al, 2016). This is based on the fact how the public cloud is
found to be the best option for handling the different information patterns which are found to be
sensitive. Here, this also includes the versions for minimising the risks and the challenges which
are related to the negative impact on the current postures of the security.
There are some of the benefits which need to focus on:
security related obligations. The use of the SLAs and the reporting, networking security
arrangements are based on the obligations which need to be understood with the communication
in the contract. For this the responsibility of the security is based on the forms where the provider
and the consumer can handle the system communication (Almorsy et al., 2016). With this, the
hosting of the critical data like the personal and the payroll is for the employees or the account
details of the customers who try to focus on the cloud that can easily highlight about the
responsibility sharing methods and the other critical cases. The public cloud could be set with the
viable choices when the organisation tends to migrate the information which is made available
for the different consumption process of the public that also tend to carry the lower risks.
The public cloud infrastructure is set when there are equipped security measures for the
information which can easily improve the security posture that is related to the infrastructure
development. It is related to the improvement of the security measures and the postures which
are for the infrastructure when compared to the current posture. The community cloud methods
take hold of the different measures of the security requirements, where the high risks data like
the handling of the customer account information could not be easily trusted with the public or
the community cloud (Cavelty et al, 2016). This is based on the fact how the public cloud is
found to be the best option for handling the different information patterns which are found to be
sensitive. Here, this also includes the versions for minimising the risks and the challenges which
are related to the negative impact on the current postures of the security.
There are some of the benefits which need to focus on:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
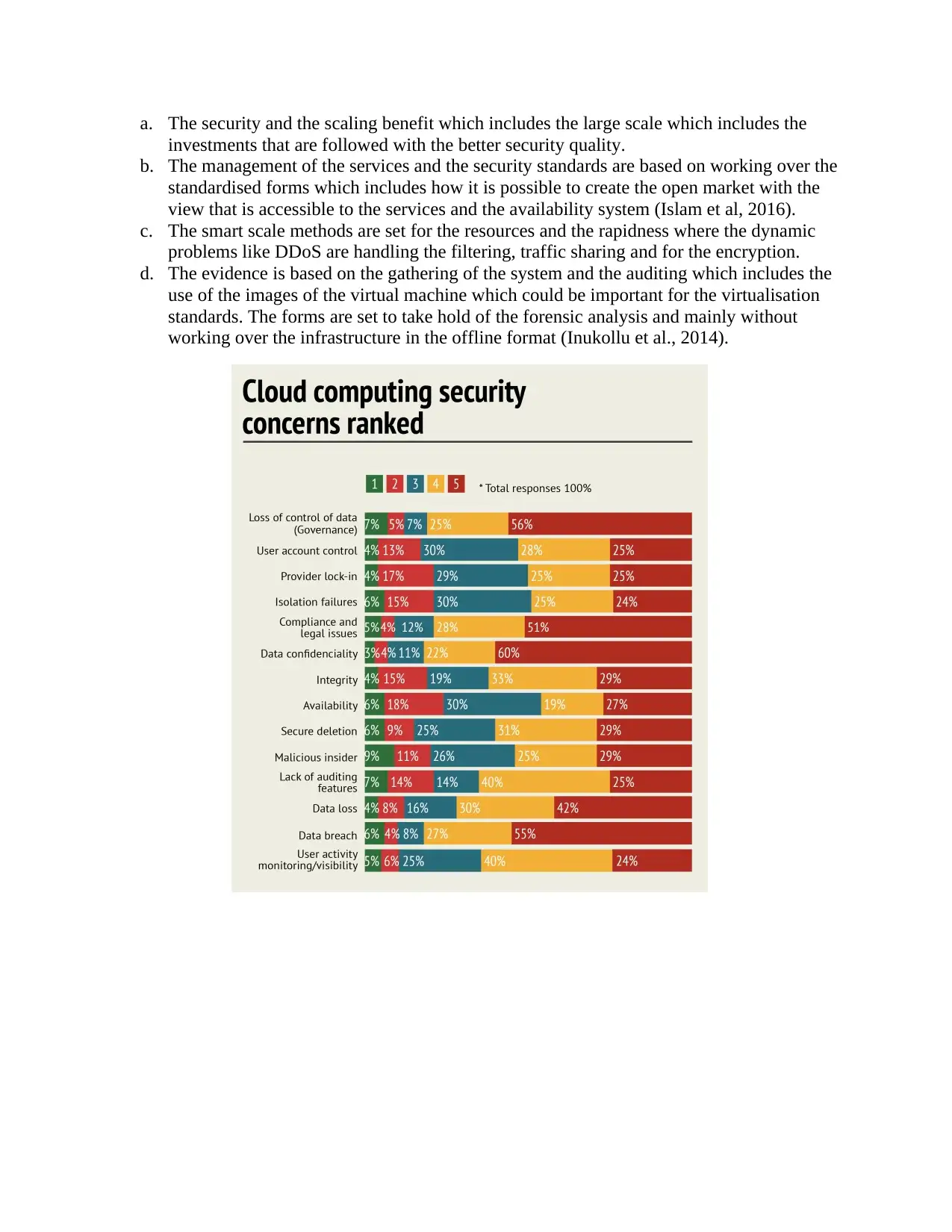
a. The security and the scaling benefit which includes the large scale which includes the
investments that are followed with the better security quality.
b. The management of the services and the security standards are based on working over the
standardised forms which includes how it is possible to create the open market with the
view that is accessible to the services and the availability system (Islam et al, 2016).
c. The smart scale methods are set for the resources and the rapidness where the dynamic
problems like DDoS are handling the filtering, traffic sharing and for the encryption.
d. The evidence is based on the gathering of the system and the auditing which includes the
use of the images of the virtual machine which could be important for the virtualisation
standards. The forms are set to take hold of the forensic analysis and mainly without
working over the infrastructure in the offline format (Inukollu et al., 2014).
investments that are followed with the better security quality.
b. The management of the services and the security standards are based on working over the
standardised forms which includes how it is possible to create the open market with the
view that is accessible to the services and the availability system (Islam et al, 2016).
c. The smart scale methods are set for the resources and the rapidness where the dynamic
problems like DDoS are handling the filtering, traffic sharing and for the encryption.
d. The evidence is based on the gathering of the system and the auditing which includes the
use of the images of the virtual machine which could be important for the virtualisation
standards. The forms are set to take hold of the forensic analysis and mainly without
working over the infrastructure in the offline format (Inukollu et al., 2014).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 19
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.



