IT Security Risks, Procedures, and Solutions: BTEC L5C Report
VerifiedAdded on 2022/06/08
|70
|29740
|26
Report
AI Summary
This report provides a comprehensive overview of IT security, addressing various risks and outlining essential organizational procedures. It begins by identifying different types of security risks, including unauthorized system use, data copying, virus attacks, malware, technical failures, physical threats, human error, and vulnerabilities associated with unsafe website browsing and social media use. The report then details organizational security procedures, such as general access controls, virus protection protocols for networks, devices, and files, as well as router and switch security measures. It also covers staff access procedures. The report further explores risk assessment, data protection processes, and the ISO 31000 risk management methodology. It discusses the impact of IT security audits, alignment with organizational policy, and the design and implementation of a security policy, including disaster recovery planning. Finally, it considers the roles of stakeholders in implementing security audit recommendations and evaluates the suitability of tools used in organizational policy.

SECURITY / BTEC -L5C/FT/04/18 / KH58922
Contents
LO1 Assess risks to IT security........................................................................................................................ 2
P1 Identify types of security risks to organisations:.................................................................................. 2
P2 Describe organisational security procedures:....................................................................................... 5
M1 Propose a method to assess and treat IT security risks:......................................................................8
LO2 Describe IT security solutions............................................................................................................... 15
P3 Identify the potential impact to IT security of incorrect configuration of firewall policies and
third-party VPNs:....................................................................................................................................... 15
P4 Show, using an example for each, how implementing a DMZ, static IP and NAT in a network can
improve Network Security:........................................................................................................................ 17
M2 Discuss three benefits to implement network monitoring systems with supporting reasons:........21
LO1 & LO2 D1 Investigate how a ‘trusted network’ may be part of an IT security solution:.................24
LO3 Review mechanisms to control organisational IT security..................................................................28
P5 Discuss risk assessment procedures:.................................................................................................... 28
P6 Explain data protection processes and regulations as applicable to an organization:.....................31
M3 Summarize the ISO 31000 risk management methodology and its application in IT security:.....36
M4 Discuss possible impacts to organizational security resulting from an IT security audit:..............39
D2 Consider how IT security can be aligned with organizational policy, detailing the security impact
of any misalignment:.................................................................................................................................. 42
LO4 Manage organisational security............................................................................................................ 44
P7 Design and implement a security policy for an organization:............................................................44
P8 List the main components of an organizational disaster recovery plan, justifying the reasons for
inclusion:..................................................................................................................................................... 50
M5 Discuss the roles of stakeholders in the organization to implement security audit
recommendations........................................................................................................................................ 54
D3 Evaluate the suitability of the tools used in an organizational policy:..............................................56
References....................................................................................................................................................... 62
SITI NORHADIAYTUL FITRI BINTI HAJI ABD RASHID 1
Contents
LO1 Assess risks to IT security........................................................................................................................ 2
P1 Identify types of security risks to organisations:.................................................................................. 2
P2 Describe organisational security procedures:....................................................................................... 5
M1 Propose a method to assess and treat IT security risks:......................................................................8
LO2 Describe IT security solutions............................................................................................................... 15
P3 Identify the potential impact to IT security of incorrect configuration of firewall policies and
third-party VPNs:....................................................................................................................................... 15
P4 Show, using an example for each, how implementing a DMZ, static IP and NAT in a network can
improve Network Security:........................................................................................................................ 17
M2 Discuss three benefits to implement network monitoring systems with supporting reasons:........21
LO1 & LO2 D1 Investigate how a ‘trusted network’ may be part of an IT security solution:.................24
LO3 Review mechanisms to control organisational IT security..................................................................28
P5 Discuss risk assessment procedures:.................................................................................................... 28
P6 Explain data protection processes and regulations as applicable to an organization:.....................31
M3 Summarize the ISO 31000 risk management methodology and its application in IT security:.....36
M4 Discuss possible impacts to organizational security resulting from an IT security audit:..............39
D2 Consider how IT security can be aligned with organizational policy, detailing the security impact
of any misalignment:.................................................................................................................................. 42
LO4 Manage organisational security............................................................................................................ 44
P7 Design and implement a security policy for an organization:............................................................44
P8 List the main components of an organizational disaster recovery plan, justifying the reasons for
inclusion:..................................................................................................................................................... 50
M5 Discuss the roles of stakeholders in the organization to implement security audit
recommendations........................................................................................................................................ 54
D3 Evaluate the suitability of the tools used in an organizational policy:..............................................56
References....................................................................................................................................................... 62
SITI NORHADIAYTUL FITRI BINTI HAJI ABD RASHID 1
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

SECURITY / BTEC -L5C/FT/04/18 / KH58922
LO1 Assess risks to IT security
P1 Identify types of security risks to organisations:
Unauthorized use of a system
Use of the computer or its data for unapproved or illegal activity. The following example should be
considered invalid or unauthorized by the organization:
Download, store or distribute pornography.
Use the system to run private businesses for personal gain or profit, including payment-based
services or subscription or stock trading
Accessing or downloading web site materials or sending messages that are defamatory, harassing
or discriminating
Online gambling or accessing online dating services
Interfere with ICT and device facilities in ways such as spam or mass mailing forms or transmit
files that may cause unnecessary burden on agency resources
Scan signature images into email messages or attached documents as they may provide personal
signatures to others who may copy and use it as verification of fraudulent material
Knowingly loading materials from the internet or email containing viruses, worms, trojan horses,
spyware or any defamatory features or damaging others.
Unauthorised copying of data from a system
By accessing the data from a system then stealing also copying computer-based confidential
information with intent to cause wrongful damages to owners of confidential information and wrong
gains to the perpetrator. Illegal data copying is a growing problem for an organization.
What is the mode of copy without permission?
USB Card Drivers & Drives (Pen) - This is the easiest and cheapest option according to these
criminals and very easy to hide. Memory cards now come in variants of 256GB and 512 GB, so it
becomes easier to move large amounts of data.
Email - Some actors only use email to transfer files from their official account to personal or
home computer accounts, they slowly transfer data to avoid detection by IT departments to
transmit a large amount of data. The perpetrators send this email to their personal accounts for
reasons of 'work from home'.
Printing - They will not leave any electronic evidence behind, they just take the print of the main
document and steal the same copy.
Remote Access - This can be used by unauthorized access (Hacking) or authorized access, as
some organizations provide remote access to their employees so they can work from their home
SITI NORHADIAYTUL FITRI BINTI HAJI ABD RASHID 2
LO1 Assess risks to IT security
P1 Identify types of security risks to organisations:
Unauthorized use of a system
Use of the computer or its data for unapproved or illegal activity. The following example should be
considered invalid or unauthorized by the organization:
Download, store or distribute pornography.
Use the system to run private businesses for personal gain or profit, including payment-based
services or subscription or stock trading
Accessing or downloading web site materials or sending messages that are defamatory, harassing
or discriminating
Online gambling or accessing online dating services
Interfere with ICT and device facilities in ways such as spam or mass mailing forms or transmit
files that may cause unnecessary burden on agency resources
Scan signature images into email messages or attached documents as they may provide personal
signatures to others who may copy and use it as verification of fraudulent material
Knowingly loading materials from the internet or email containing viruses, worms, trojan horses,
spyware or any defamatory features or damaging others.
Unauthorised copying of data from a system
By accessing the data from a system then stealing also copying computer-based confidential
information with intent to cause wrongful damages to owners of confidential information and wrong
gains to the perpetrator. Illegal data copying is a growing problem for an organization.
What is the mode of copy without permission?
USB Card Drivers & Drives (Pen) - This is the easiest and cheapest option according to these
criminals and very easy to hide. Memory cards now come in variants of 256GB and 512 GB, so it
becomes easier to move large amounts of data.
Email - Some actors only use email to transfer files from their official account to personal or
home computer accounts, they slowly transfer data to avoid detection by IT departments to
transmit a large amount of data. The perpetrators send this email to their personal accounts for
reasons of 'work from home'.
Printing - They will not leave any electronic evidence behind, they just take the print of the main
document and steal the same copy.
Remote Access - This can be used by unauthorized access (Hacking) or authorized access, as
some organizations provide remote access to their employees so they can work from their home
SITI NORHADIAYTUL FITRI BINTI HAJI ABD RASHID 2

SECURITY / BTEC -L5C/FT/04/18 / KH58922
computer, it also makes confidential data detection for law enforcement. agency law or private
investigator.
Everything stored in the organization has some potential values, some of the targets for
breaking data are as follows:
Client & Finance contact information such as credit card and debit card information
source code & algorithm
network qualification such as Passwords & Certificates
records of personnel and data of private employees
other user's personal documents stored on company computer
The company's strategic data, including executive and executive staff communications.
Virus
If the virus hits it, the news is always bad. This virus can copy itself and infect other machines
without users even knowing that the machine has been infected until a disaster attack. If the virus hits
the network then it may spread to files on other machines that are connected to the network. Viruses
can also be sent via e-mail, instant messaging, intranets and other shared networks that cause
networks and machines to load or crash. They can also capture keystrokes where security problems
are located because the password and banking details can be obtained in this way. Viruses can cause
great security risks and start a problem cycle for organizations. Implementing anti-virus solutions can
save your network and all your files and e-mails that are easily lost and damaged.
Malware Attacks
Malware is software designed to interrupt the computer system. It also has the ability to collect
sensitive information from a user's computer. Business-related malware attacks are business details
that can be compromised and also have the ability to prevent employee access to their accounts.
Pests can come from USB emails, files, or memory sticks, where as soon as they are opened or
inserted, malware will spread to the computer system and begin to interrupt the system without users
viewing it. As a result, businesses will be able to lose data, compromised data, loss of trust also affect
their reputation, as users will experience malware attacks. For example, information business plans
can be leaked.
Technical failures
Such as software bugs, computer crashes or complete failure of computer components. Technical
failures can be a disaster if, for example, you cannot retrieve data on a failed hard drive and no
backup copy is available.
Physical threats
Due to physical access or damage to IT resources such as servers. These include theft, damage
caused by fire or flood, or unauthorized access to confidential data by employees or outsiders.
Human error
For example, people may accidentally delete important data, or fail to comply with security
procedures properly.
SITI NORHADIAYTUL FITRI BINTI HAJI ABD RASHID 3
computer, it also makes confidential data detection for law enforcement. agency law or private
investigator.
Everything stored in the organization has some potential values, some of the targets for
breaking data are as follows:
Client & Finance contact information such as credit card and debit card information
source code & algorithm
network qualification such as Passwords & Certificates
records of personnel and data of private employees
other user's personal documents stored on company computer
The company's strategic data, including executive and executive staff communications.
Virus
If the virus hits it, the news is always bad. This virus can copy itself and infect other machines
without users even knowing that the machine has been infected until a disaster attack. If the virus hits
the network then it may spread to files on other machines that are connected to the network. Viruses
can also be sent via e-mail, instant messaging, intranets and other shared networks that cause
networks and machines to load or crash. They can also capture keystrokes where security problems
are located because the password and banking details can be obtained in this way. Viruses can cause
great security risks and start a problem cycle for organizations. Implementing anti-virus solutions can
save your network and all your files and e-mails that are easily lost and damaged.
Malware Attacks
Malware is software designed to interrupt the computer system. It also has the ability to collect
sensitive information from a user's computer. Business-related malware attacks are business details
that can be compromised and also have the ability to prevent employee access to their accounts.
Pests can come from USB emails, files, or memory sticks, where as soon as they are opened or
inserted, malware will spread to the computer system and begin to interrupt the system without users
viewing it. As a result, businesses will be able to lose data, compromised data, loss of trust also affect
their reputation, as users will experience malware attacks. For example, information business plans
can be leaked.
Technical failures
Such as software bugs, computer crashes or complete failure of computer components. Technical
failures can be a disaster if, for example, you cannot retrieve data on a failed hard drive and no
backup copy is available.
Physical threats
Due to physical access or damage to IT resources such as servers. These include theft, damage
caused by fire or flood, or unauthorized access to confidential data by employees or outsiders.
Human error
For example, people may accidentally delete important data, or fail to comply with security
procedures properly.
SITI NORHADIAYTUL FITRI BINTI HAJI ABD RASHID 3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

SECURITY / BTEC -L5C/FT/04/18 / KH58922
Browsing to an unsafe website and naivety with Social Media
Employees can cause damage to the organization not only by using personal devices for work but
also by making personal use of the tool. This includes browsing unsafe websites. While it is not
appropriate for employees to view adult content on work devices, it is also very dangerous. Many
pornographic websites hide malicious content in their URLs, which means users can install malicious
software onto corporate networks by clicking on obscene links. Like most online users, employees
like to create their social media profile. But where they check in and what they post can pose a threat
to the organization. To illustrate, social media users often recognize shortened links. Companies used
URL shortening services to help track link click rates on social media. However, because shortened
URLs do not disclose information about their real purpose, attackers also use it to trick users into
visiting malicious websites. If the employee clicks a link while logged in to one of their accounts on
the work device, which can parse problems for the network of organizations. In addition, what
workers in social media can do is a threat to the organization. For example, if the employee displays
detailed information about their work on social media sites, attackers can use that information to
create bull phishing emails aimed at steal their corporate credentials. The employee may also post
pictures that inadvertently associate sensitive information about the organization, such as by
installing a selfie that includes parts of documents that contain organizational financial information.
SITI NORHADIAYTUL FITRI BINTI HAJI ABD RASHID 4
Browsing to an unsafe website and naivety with Social Media
Employees can cause damage to the organization not only by using personal devices for work but
also by making personal use of the tool. This includes browsing unsafe websites. While it is not
appropriate for employees to view adult content on work devices, it is also very dangerous. Many
pornographic websites hide malicious content in their URLs, which means users can install malicious
software onto corporate networks by clicking on obscene links. Like most online users, employees
like to create their social media profile. But where they check in and what they post can pose a threat
to the organization. To illustrate, social media users often recognize shortened links. Companies used
URL shortening services to help track link click rates on social media. However, because shortened
URLs do not disclose information about their real purpose, attackers also use it to trick users into
visiting malicious websites. If the employee clicks a link while logged in to one of their accounts on
the work device, which can parse problems for the network of organizations. In addition, what
workers in social media can do is a threat to the organization. For example, if the employee displays
detailed information about their work on social media sites, attackers can use that information to
create bull phishing emails aimed at steal their corporate credentials. The employee may also post
pictures that inadvertently associate sensitive information about the organization, such as by
installing a selfie that includes parts of documents that contain organizational financial information.
SITI NORHADIAYTUL FITRI BINTI HAJI ABD RASHID 4
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

SECURITY / BTEC -L5C/FT/04/18 / KH58922
P2 Describe organisational security procedures:
Security procedures are detailed step-by-step instructions on how to implement, enable, or enforce
security controls as outlined in your organization's security policy. The purpose of the Security
procedures is to ensure consistency in the implementation of security controls or the implementation
of relevant security business processes. They must be followed every time the controls are
implemented or the business-related security process is followed. Below are the examples of
organizational security procedures:
General procedure
Anyone who attempts to enter the office area from the receipt must cross the first security check
point.
All employees must have an identity card and submit their identity card to the security guard for
verification. So, security guards must carefully check identification cards, employee photos,
employee names and card identification cards to ensure that they are a company employee.
The worker's face must be clear for safety checks and after the safety identity of the worker is
pure, they can move forward and scan the fingerprint to access the office.
If the employee's face is not identical to the identity card, the security guard must contact the
senior employee of the employee or the human resources department to obtain the confirmation.
So, if anyone who tries to enter the office from the reception cannot be confirmed as a pure
worker, they must be guided by the building by the security guard.
Virus Protection Procedure
Network:
IT will respond to any detected, likely or imminent attack to the organization as it sees
appropriate in accordance with the IT Security Policy.
If an attack is likely or imminent, IT may isolate the organization network from the rest of the
Internet if no other protection is available.
If the network has been infected, IT may isolate the contaminated portion of the organization
network from the rest of the organization.
Device:
A PC, laptop or other device that has been infected will be disconnected from the organization
network.
The infected device will need to be cleaned and cleared of any threat to the organization network.
The device may be required to be presented for inspection by IT before reconnection to the
organization network is permitted.
Members of the organization community are required to abide by the Desktop Virus Protection
Guidelines to reduce the risk of virus problems.
File:
If an infection to a file occurs, the following steps apply:
If a file can be cleaned, it is cleaned.
SITI NORHADIAYTUL FITRI BINTI HAJI ABD RASHID 5
P2 Describe organisational security procedures:
Security procedures are detailed step-by-step instructions on how to implement, enable, or enforce
security controls as outlined in your organization's security policy. The purpose of the Security
procedures is to ensure consistency in the implementation of security controls or the implementation
of relevant security business processes. They must be followed every time the controls are
implemented or the business-related security process is followed. Below are the examples of
organizational security procedures:
General procedure
Anyone who attempts to enter the office area from the receipt must cross the first security check
point.
All employees must have an identity card and submit their identity card to the security guard for
verification. So, security guards must carefully check identification cards, employee photos,
employee names and card identification cards to ensure that they are a company employee.
The worker's face must be clear for safety checks and after the safety identity of the worker is
pure, they can move forward and scan the fingerprint to access the office.
If the employee's face is not identical to the identity card, the security guard must contact the
senior employee of the employee or the human resources department to obtain the confirmation.
So, if anyone who tries to enter the office from the reception cannot be confirmed as a pure
worker, they must be guided by the building by the security guard.
Virus Protection Procedure
Network:
IT will respond to any detected, likely or imminent attack to the organization as it sees
appropriate in accordance with the IT Security Policy.
If an attack is likely or imminent, IT may isolate the organization network from the rest of the
Internet if no other protection is available.
If the network has been infected, IT may isolate the contaminated portion of the organization
network from the rest of the organization.
Device:
A PC, laptop or other device that has been infected will be disconnected from the organization
network.
The infected device will need to be cleaned and cleared of any threat to the organization network.
The device may be required to be presented for inspection by IT before reconnection to the
organization network is permitted.
Members of the organization community are required to abide by the Desktop Virus Protection
Guidelines to reduce the risk of virus problems.
File:
If an infection to a file occurs, the following steps apply:
If a file can be cleaned, it is cleaned.
SITI NORHADIAYTUL FITRI BINTI HAJI ABD RASHID 5

SECURITY / BTEC -L5C/FT/04/18 / KH58922
If it can't be cleaned, and the file is recoverable from backup, it is deleted.
If it can't be cleaned, and the file is not recoverable from backup, it is quarantined off the
network.
Router and Switch Security Procedure
1 Each router must meet the following configuration and operation standards
2 No local user accounts configured on the router.
3 Password that allows must be stored in secure encrypted form on all routers. The router must
have a password that allows the current production password setting.
4 Access rules should be added as business requirements arise.
5 All networks connected to the production network must be operated and managed by the
Infrastructure and Network Control Systems.
Accessing Building Time for Staff Procedures
No employee may enter the building unless they are responsible, they have obtained prior
permission from their line manager. If for any reason any access is required, the following
procedures need to be followed.
Get approval from your line manager
Speak to Parking Manager and Community Safety Managers to make sure they access the
company, and tell them you will be out of the clock.
Make sure your scratch card will allow you to have access to the building at the weekend.
You must enter the building through the back door.
You must complete the 'out of clock' sheet, by the alarm panel, downstairs. This must be
completed by the time you leave when you depart.
Check in with CCTV
The CCTV will call at the designated interval, to ensure staff safety, if no CCTV answers will
call the primary depositors who are investigating.
You must check with CCTV when you leave.
Safety of equipment and property procedure
No equipment such as laptops and projectors for example should be left unattended in a meeting
or space of the Committee. Those using the equipment are responsible for their safety and
security.
Individual wealth is an individual's responsibility and if staff, volunteers or visitors bring
valuable items to the office, they must ensure they are safely stored in a safe place. The Council
shall not be liable for lost property if there is no proof of delay.
Cash records will be stored in a locker / locked vault in the office, in compliance with financial
control policies.
Any theft or loss must be reported immediately to the Building Manager and to the Police if
appropriate.
Visitors are not allowed to allow others to enter unauthorized buildings from previous employees.
When leaving the office, all filing cabinets holding sensitive information / materials must be
locked and the keys are kept in a safe location. All internal doors need to be locked, windows
SITI NORHADIAYTUL FITRI BINTI HAJI ABD RASHID 6
If it can't be cleaned, and the file is recoverable from backup, it is deleted.
If it can't be cleaned, and the file is not recoverable from backup, it is quarantined off the
network.
Router and Switch Security Procedure
1 Each router must meet the following configuration and operation standards
2 No local user accounts configured on the router.
3 Password that allows must be stored in secure encrypted form on all routers. The router must
have a password that allows the current production password setting.
4 Access rules should be added as business requirements arise.
5 All networks connected to the production network must be operated and managed by the
Infrastructure and Network Control Systems.
Accessing Building Time for Staff Procedures
No employee may enter the building unless they are responsible, they have obtained prior
permission from their line manager. If for any reason any access is required, the following
procedures need to be followed.
Get approval from your line manager
Speak to Parking Manager and Community Safety Managers to make sure they access the
company, and tell them you will be out of the clock.
Make sure your scratch card will allow you to have access to the building at the weekend.
You must enter the building through the back door.
You must complete the 'out of clock' sheet, by the alarm panel, downstairs. This must be
completed by the time you leave when you depart.
Check in with CCTV
The CCTV will call at the designated interval, to ensure staff safety, if no CCTV answers will
call the primary depositors who are investigating.
You must check with CCTV when you leave.
Safety of equipment and property procedure
No equipment such as laptops and projectors for example should be left unattended in a meeting
or space of the Committee. Those using the equipment are responsible for their safety and
security.
Individual wealth is an individual's responsibility and if staff, volunteers or visitors bring
valuable items to the office, they must ensure they are safely stored in a safe place. The Council
shall not be liable for lost property if there is no proof of delay.
Cash records will be stored in a locker / locked vault in the office, in compliance with financial
control policies.
Any theft or loss must be reported immediately to the Building Manager and to the Police if
appropriate.
Visitors are not allowed to allow others to enter unauthorized buildings from previous employees.
When leaving the office, all filing cabinets holding sensitive information / materials must be
locked and the keys are kept in a safe location. All internal doors need to be locked, windows
SITI NORHADIAYTUL FITRI BINTI HAJI ABD RASHID 6
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

SECURITY / BTEC -L5C/FT/04/18 / KH58922
checked and when the main building departs, the alarm must be set. Failure to do so may lead to
the disciplinary procedures.
Use Safety Layered procedure
The employee should have a firewall that protects their Internet traffic, and then each server should
be protected by antivirus software and operating system firewalls as well.
Security Audit procedure
The employee should print the security log every week and analyse the activity. If you notice
repeated trials on security violations, strengthen the attacked area and report the Internet address
that strikes to the appropriate Internet service provider.
You should also track the websites your employees visit to see if anyone is accessing websites
that may contain viruses or other security risks.
Email Filter procedure
Place email filters on your server that check attachments and check for potentially harmful files.
Include a section in your employee's email that recommends that employees not open
attachments in emails from people they do not know.
SITI NORHADIAYTUL FITRI BINTI HAJI ABD RASHID 7
checked and when the main building departs, the alarm must be set. Failure to do so may lead to
the disciplinary procedures.
Use Safety Layered procedure
The employee should have a firewall that protects their Internet traffic, and then each server should
be protected by antivirus software and operating system firewalls as well.
Security Audit procedure
The employee should print the security log every week and analyse the activity. If you notice
repeated trials on security violations, strengthen the attacked area and report the Internet address
that strikes to the appropriate Internet service provider.
You should also track the websites your employees visit to see if anyone is accessing websites
that may contain viruses or other security risks.
Email Filter procedure
Place email filters on your server that check attachments and check for potentially harmful files.
Include a section in your employee's email that recommends that employees not open
attachments in emails from people they do not know.
SITI NORHADIAYTUL FITRI BINTI HAJI ABD RASHID 7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

SECURITY / BTEC -L5C/FT/04/18 / KH58922
M1 Propose a method to assess and treat IT security risks:
Methods to assess IT risks
By following well-defined steps, we can analyse the security risks in a computing system. The steps
on the below are described in detail in the following sections:
Identifying and prioritizing assets
Assets include servers, customer contact information, sensitive partner documents, trade secrets
and so on. Remember, what you think a technician is worth is probably not the most valuable one
for a business. Therefore, you need to work with business and management users to create a list
of all valuable assets. For each asset, gather the following information, as appropriate:
Software
Hardware
Data
Interface
IT Security Policy
IT security architecture
Network topology
Since most organizations have limited budgets for risk assessment, you may need to limit the
scope of the project to mission critical assets. Accordingly, you need to define the standard to
determine the importance of each asset. General criteria include the value of financial assets,
legal standing and organizational interests. Once the standards have been approved by
management and formally incorporated into the risk assessment security policy, use them to
classify each asset you identified as critical, primary or minor.
Identify threats
Threats are anything that can exploit vulnerabilities to violate security and cause harm to your
organization. While hackers and malware may jump into the mind, there are many other types of
threats:
System failure. Possibility of system failure depends on the quality of your computer. For
relatively new and high-quality equipment, the likelihood of system failure is low. But if the
equipment is old or from "no-name" vendors, the chances of failure are much higher.
Therefore, it is wise to buy high-quality equipment, or at least equipment with good support.
Malicious people. There are three types of malicious behaviour:
Interference is when someone causes damage to your business by deleting data,
engineering denial of service (DDOS) that is distributed against your site, physically steal
a computer or server, and so on.
Interception is a classic hacking, where they steal your data.
Impersonation is a misuse of others' entitlements, which are often obtained through social
engineering attacks or abusive attacks, or purchased on dark sites.
SITI NORHADIAYTUL FITRI BINTI HAJI ABD RASHID 8
M1 Propose a method to assess and treat IT security risks:
Methods to assess IT risks
By following well-defined steps, we can analyse the security risks in a computing system. The steps
on the below are described in detail in the following sections:
Identifying and prioritizing assets
Assets include servers, customer contact information, sensitive partner documents, trade secrets
and so on. Remember, what you think a technician is worth is probably not the most valuable one
for a business. Therefore, you need to work with business and management users to create a list
of all valuable assets. For each asset, gather the following information, as appropriate:
Software
Hardware
Data
Interface
IT Security Policy
IT security architecture
Network topology
Since most organizations have limited budgets for risk assessment, you may need to limit the
scope of the project to mission critical assets. Accordingly, you need to define the standard to
determine the importance of each asset. General criteria include the value of financial assets,
legal standing and organizational interests. Once the standards have been approved by
management and formally incorporated into the risk assessment security policy, use them to
classify each asset you identified as critical, primary or minor.
Identify threats
Threats are anything that can exploit vulnerabilities to violate security and cause harm to your
organization. While hackers and malware may jump into the mind, there are many other types of
threats:
System failure. Possibility of system failure depends on the quality of your computer. For
relatively new and high-quality equipment, the likelihood of system failure is low. But if the
equipment is old or from "no-name" vendors, the chances of failure are much higher.
Therefore, it is wise to buy high-quality equipment, or at least equipment with good support.
Malicious people. There are three types of malicious behaviour:
Interference is when someone causes damage to your business by deleting data,
engineering denial of service (DDOS) that is distributed against your site, physically steal
a computer or server, and so on.
Interception is a classic hacking, where they steal your data.
Impersonation is a misuse of others' entitlements, which are often obtained through social
engineering attacks or abusive attacks, or purchased on dark sites.
SITI NORHADIAYTUL FITRI BINTI HAJI ABD RASHID 8

SECURITY / BTEC -L5C/FT/04/18 / KH58922
Identify the vulnerability
Third, we need to see the weaknesses. The threats that can exploit violations and endanger your
organization. The vulnerabilities can be identified through the audit reports, vulnerability
analysis, vulnerability databases, vendor data, commercial computer incident response teams, and
system software security analysis. Testing the IT system is also an important tool in identifying
weaknesses. Testing can include the following:
Security Procedures and Assessment Procedures
Penetration test technique
Automatic weakness scanning tool
You can reduce your software-based weakness with proper patch management. But do not forget
about physical weaknesses. For example, transferring your server's room to the second floor of
the building will reduce your vulnerability to flooding.
Control analysis
Analysing controls that are either in place or in the planning stage to minimize or eliminate the
probability of the threat will exploit vulnerabilities in the system. The controls can be
implemented through the technical means, such as hardware or computer software, encryption,
intrusion detection mechanisms, and identification and authentication subsystems. Non-technical
controls include security policies, administrative measures, and physical and environmental
mechanisms. Both technical and non-technical controls can be classified as preventative or
detective controls. As the name suggests, preventive control attempts to anticipate and stop
attacks. Examples of preventative technical controls are encryption and authentication devices.
Detective controls are used to search for attacks or events through means such as audit trails and
intrusion detection systems.
Determine the likelihood of an incident
Assess the probability that the weaknesses may be really exploited, taking into account the types
of vulnerabilities, capabilities and motivation of the source of the threat, and the existence and
effectiveness of your control. From numerical scores, many organizations use high, medium and
low categories to assess possible attacks or other adverse events.
Assess impact a threat could have
Impression analysis should include the following factors:
System missions, including processes implemented by the system
System intelligence, determined by its value and value of data to the organization
System sensitivity and its data
The information needed to perform an impact analysis can be obtained from existing
organizational documentation, including business impact analysis (or BIA) (or misleading reports
of missions, as sometimes called). This document uses quantitative or qualitative ways to
SITI NORHADIAYTUL FITRI BINTI HAJI ABD RASHID 9
Identify the vulnerability
Third, we need to see the weaknesses. The threats that can exploit violations and endanger your
organization. The vulnerabilities can be identified through the audit reports, vulnerability
analysis, vulnerability databases, vendor data, commercial computer incident response teams, and
system software security analysis. Testing the IT system is also an important tool in identifying
weaknesses. Testing can include the following:
Security Procedures and Assessment Procedures
Penetration test technique
Automatic weakness scanning tool
You can reduce your software-based weakness with proper patch management. But do not forget
about physical weaknesses. For example, transferring your server's room to the second floor of
the building will reduce your vulnerability to flooding.
Control analysis
Analysing controls that are either in place or in the planning stage to minimize or eliminate the
probability of the threat will exploit vulnerabilities in the system. The controls can be
implemented through the technical means, such as hardware or computer software, encryption,
intrusion detection mechanisms, and identification and authentication subsystems. Non-technical
controls include security policies, administrative measures, and physical and environmental
mechanisms. Both technical and non-technical controls can be classified as preventative or
detective controls. As the name suggests, preventive control attempts to anticipate and stop
attacks. Examples of preventative technical controls are encryption and authentication devices.
Detective controls are used to search for attacks or events through means such as audit trails and
intrusion detection systems.
Determine the likelihood of an incident
Assess the probability that the weaknesses may be really exploited, taking into account the types
of vulnerabilities, capabilities and motivation of the source of the threat, and the existence and
effectiveness of your control. From numerical scores, many organizations use high, medium and
low categories to assess possible attacks or other adverse events.
Assess impact a threat could have
Impression analysis should include the following factors:
System missions, including processes implemented by the system
System intelligence, determined by its value and value of data to the organization
System sensitivity and its data
The information needed to perform an impact analysis can be obtained from existing
organizational documentation, including business impact analysis (or BIA) (or misleading reports
of missions, as sometimes called). This document uses quantitative or qualitative ways to
SITI NORHADIAYTUL FITRI BINTI HAJI ABD RASHID 9
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

SECURITY / BTEC -L5C/FT/04/18 / KH58922
determine the impact that will be caused by compromise or harm to an organization's information
assets. Attacks or adverse events may result in compromise or loss of confidentiality of
information systems, integrity and availability. Like the determination of abilities, the impact on
the system can be qualitatively assessed as high, medium or low. The following additional items
should be included in the impact analysis:
Frequency of expectation of exploitation of vulnerability threats each year
Estimated cost per occurrence
The weight factor is based on the relative impression of certain threats that exploit certain
weaknesses
Prioritizing the information security risk
For each pair of threats / weaknesses, determine the level of risk to the IT system, based on the
following:
Possible threats will exploit vulnerabilities
The threat of exploit successfully exploits weaknesses
Adequate adequacy of existing or planned information security controls to eliminate or
minimize risks
A useful tool for estimating risk in this way is the risk level matrix. Most likely the threat will be
rated 1.0; one simple possibility is rated at 0.5; and possibly the possibility of rating 0.1.
Likewise, the high impact level is given 100, the level of simple impact 50, and the low impact
level 10. The risk is calculated by multiplying the probable value of the threat by the impression
value, and risks categorized as high, medium or low based on the result.
Recommend controls
Using the level of risk as a basis, define actions that senior management and responsible
individuals need to take to reduce risk. Here are some general guidelines for each level of risk:
High - Plans for corrective measures should be developed as soon as possible.
Medium - The plan for corrective measures needs to be developed within a reasonable period
of time.
Low - The team must decide whether to accept the risk or perform corrective action.
When you consider the controls to reduce each risk, be sure to consider:
Organizational basis
Cost-benefit analysis
Effect of operation
Eligibility
Rules apply
The overall effectiveness of the recommended controls
Security and reliability
SITI NORHADIAYTUL FITRI BINTI HAJI ABD RASHID 10
determine the impact that will be caused by compromise or harm to an organization's information
assets. Attacks or adverse events may result in compromise or loss of confidentiality of
information systems, integrity and availability. Like the determination of abilities, the impact on
the system can be qualitatively assessed as high, medium or low. The following additional items
should be included in the impact analysis:
Frequency of expectation of exploitation of vulnerability threats each year
Estimated cost per occurrence
The weight factor is based on the relative impression of certain threats that exploit certain
weaknesses
Prioritizing the information security risk
For each pair of threats / weaknesses, determine the level of risk to the IT system, based on the
following:
Possible threats will exploit vulnerabilities
The threat of exploit successfully exploits weaknesses
Adequate adequacy of existing or planned information security controls to eliminate or
minimize risks
A useful tool for estimating risk in this way is the risk level matrix. Most likely the threat will be
rated 1.0; one simple possibility is rated at 0.5; and possibly the possibility of rating 0.1.
Likewise, the high impact level is given 100, the level of simple impact 50, and the low impact
level 10. The risk is calculated by multiplying the probable value of the threat by the impression
value, and risks categorized as high, medium or low based on the result.
Recommend controls
Using the level of risk as a basis, define actions that senior management and responsible
individuals need to take to reduce risk. Here are some general guidelines for each level of risk:
High - Plans for corrective measures should be developed as soon as possible.
Medium - The plan for corrective measures needs to be developed within a reasonable period
of time.
Low - The team must decide whether to accept the risk or perform corrective action.
When you consider the controls to reduce each risk, be sure to consider:
Organizational basis
Cost-benefit analysis
Effect of operation
Eligibility
Rules apply
The overall effectiveness of the recommended controls
Security and reliability
SITI NORHADIAYTUL FITRI BINTI HAJI ABD RASHID 10
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
SECURITY / BTEC -L5C/FT/04/18 / KH58922
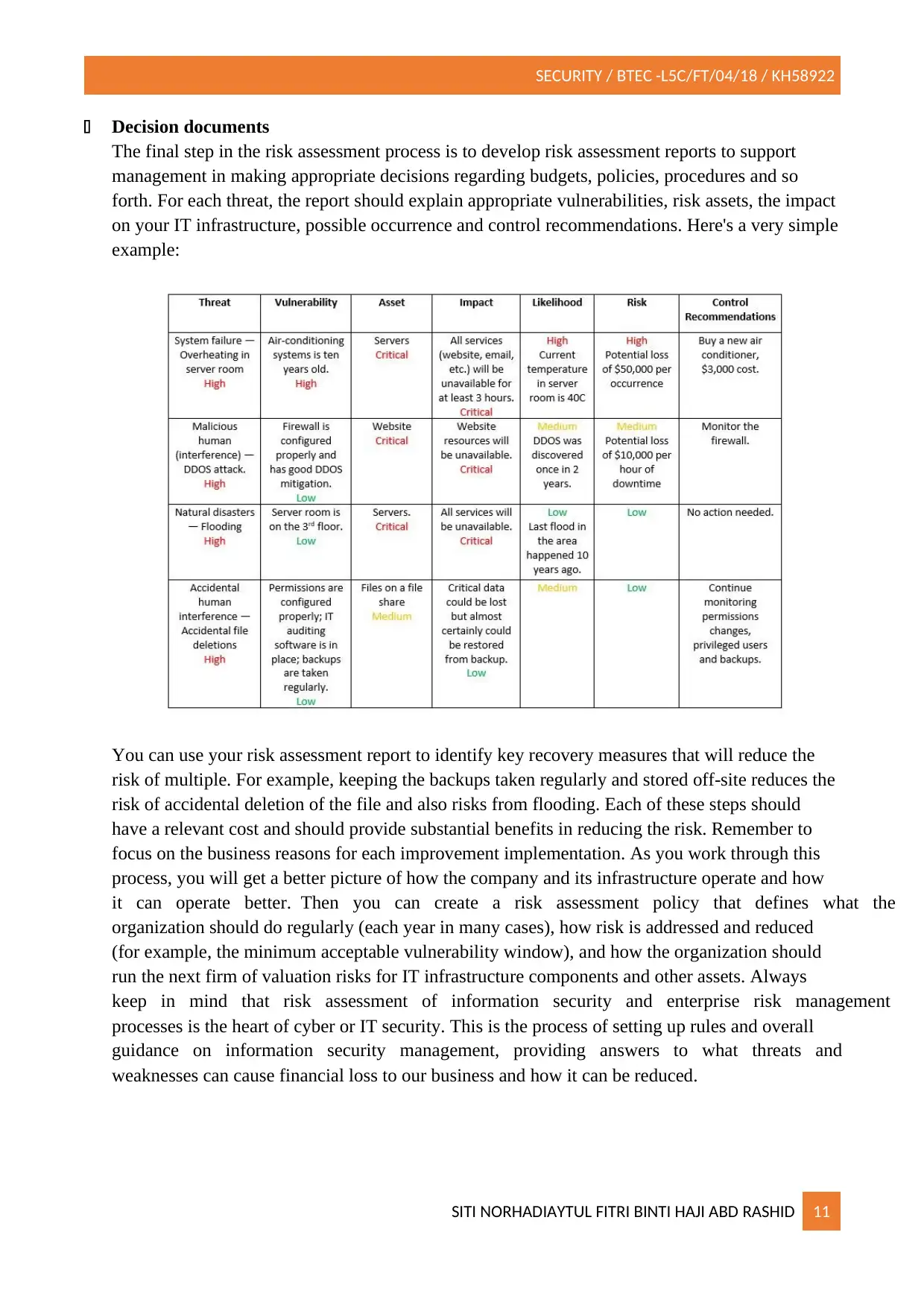
Decision documents
The final step in the risk assessment process is to develop risk assessment reports to support
management in making appropriate decisions regarding budgets, policies, procedures and so
forth. For each threat, the report should explain appropriate vulnerabilities, risk assets, the impact
on your IT infrastructure, possible occurrence and control recommendations. Here's a very simple
example:
You can use your risk assessment report to identify key recovery measures that will reduce the
risk of multiple. For example, keeping the backups taken regularly and stored off-site reduces the
risk of accidental deletion of the file and also risks from flooding. Each of these steps should
have a relevant cost and should provide substantial benefits in reducing the risk. Remember to
focus on the business reasons for each improvement implementation. As you work through this
process, you will get a better picture of how the company and its infrastructure operate and how
it can operate better. Then you can create a risk assessment policy that defines what the
organization should do regularly (each year in many cases), how risk is addressed and reduced
(for example, the minimum acceptable vulnerability window), and how the organization should
run the next firm of valuation risks for IT infrastructure components and other assets. Always
keep in mind that risk assessment of information security and enterprise risk management
processes is the heart of cyber or IT security. This is the process of setting up rules and overall
guidance on information security management, providing answers to what threats and
weaknesses can cause financial loss to our business and how it can be reduced.
SITI NORHADIAYTUL FITRI BINTI HAJI ABD RASHID 11
Decision documents
The final step in the risk assessment process is to develop risk assessment reports to support
management in making appropriate decisions regarding budgets, policies, procedures and so
forth. For each threat, the report should explain appropriate vulnerabilities, risk assets, the impact
on your IT infrastructure, possible occurrence and control recommendations. Here's a very simple
example:
You can use your risk assessment report to identify key recovery measures that will reduce the
risk of multiple. For example, keeping the backups taken regularly and stored off-site reduces the
risk of accidental deletion of the file and also risks from flooding. Each of these steps should
have a relevant cost and should provide substantial benefits in reducing the risk. Remember to
focus on the business reasons for each improvement implementation. As you work through this
process, you will get a better picture of how the company and its infrastructure operate and how
it can operate better. Then you can create a risk assessment policy that defines what the
organization should do regularly (each year in many cases), how risk is addressed and reduced
(for example, the minimum acceptable vulnerability window), and how the organization should
run the next firm of valuation risks for IT infrastructure components and other assets. Always
keep in mind that risk assessment of information security and enterprise risk management
processes is the heart of cyber or IT security. This is the process of setting up rules and overall
guidance on information security management, providing answers to what threats and
weaknesses can cause financial loss to our business and how it can be reduced.
SITI NORHADIAYTUL FITRI BINTI HAJI ABD RASHID 11

SECURITY / BTEC -L5C/FT/04/18 / KH58922
Methods to treat the IT risks
Risk treatment involves the development and implementation of strategies and action plans that are
cost-effective to increase benefits and reduce costs. Strategies and plans usually involve the
improvement of existing controls or the introduction of new controls to mitigate risks.
Risk avoidance:
Is the elimination of hazards, activities and disclosures that may adversely affect the
organization's assets within which IT assets are any information, system or hardware owned by
the company used during business activities? While risk management aims to control the damage
and financial consequences of threatening events, risk aversion is aimed at avoiding the event of
a complete sacrifice. While the complete elimination of risks is not possible, the risk aversion
strategy is designed to deflect as many possible threats to avoid costly consequences and disrupt
destructive events. The risk avoidance methodology attempts to minimize vulnerabilities that can
pose a threat. Avoidance and risk reduction can be achieved through policies and procedures,
training and implementation of education and technology.
Risk acceptance:
Is a risk assumption, usually because the risk profile is attractive and within your risk tolerance.
In general, it is impossible to make a profit in a business or life without risk. Therefore, risk
acceptance is a regular risk treatment.
Risk reduction:
Risk mitigation is a practice of mitigating the identified risk. Techniques to reduce risk depend on
the type of risk you want to decline. examples of IT Infrastructure such as computing, network
equipment and communications can be used to reduce business risks. IT infrastructure is the
hardware, software, network and basic facilities in which the organization's information
technology services are built. For example, tools designed to address security threats such as
denial of service attacks.
Risk transfer:
You may transfer all or some of the risks to a third party. The two main types of transfers are
insurance and outsourcing. For example, a company may choose to transfer a project risk
collection with project outsourcing.
Risk sharing:
Risk sharing is a risk distribution to various organizations or individuals. This is done for a
variety of reasons including insurance products and personal insurance strategies.
Risk control:
is the process, basis, practice, tool or structure used to manage the risks on a daily basis. For
example, in IT controls that include processes, policies, procedures and automation designed to
reduce risk. Controls are aspects of day-to-day information technology operations designed to
control risks and comply with industry laws, regulations, standards and best practices.
SITI NORHADIAYTUL FITRI BINTI HAJI ABD RASHID 12
Methods to treat the IT risks
Risk treatment involves the development and implementation of strategies and action plans that are
cost-effective to increase benefits and reduce costs. Strategies and plans usually involve the
improvement of existing controls or the introduction of new controls to mitigate risks.
Risk avoidance:
Is the elimination of hazards, activities and disclosures that may adversely affect the
organization's assets within which IT assets are any information, system or hardware owned by
the company used during business activities? While risk management aims to control the damage
and financial consequences of threatening events, risk aversion is aimed at avoiding the event of
a complete sacrifice. While the complete elimination of risks is not possible, the risk aversion
strategy is designed to deflect as many possible threats to avoid costly consequences and disrupt
destructive events. The risk avoidance methodology attempts to minimize vulnerabilities that can
pose a threat. Avoidance and risk reduction can be achieved through policies and procedures,
training and implementation of education and technology.
Risk acceptance:
Is a risk assumption, usually because the risk profile is attractive and within your risk tolerance.
In general, it is impossible to make a profit in a business or life without risk. Therefore, risk
acceptance is a regular risk treatment.
Risk reduction:
Risk mitigation is a practice of mitigating the identified risk. Techniques to reduce risk depend on
the type of risk you want to decline. examples of IT Infrastructure such as computing, network
equipment and communications can be used to reduce business risks. IT infrastructure is the
hardware, software, network and basic facilities in which the organization's information
technology services are built. For example, tools designed to address security threats such as
denial of service attacks.
Risk transfer:
You may transfer all or some of the risks to a third party. The two main types of transfers are
insurance and outsourcing. For example, a company may choose to transfer a project risk
collection with project outsourcing.
Risk sharing:
Risk sharing is a risk distribution to various organizations or individuals. This is done for a
variety of reasons including insurance products and personal insurance strategies.
Risk control:
is the process, basis, practice, tool or structure used to manage the risks on a daily basis. For
example, in IT controls that include processes, policies, procedures and automation designed to
reduce risk. Controls are aspects of day-to-day information technology operations designed to
control risks and comply with industry laws, regulations, standards and best practices.
SITI NORHADIAYTUL FITRI BINTI HAJI ABD RASHID 12
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 70
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




