Comprehensive Report on IT Security Risk Assessment & Management
VerifiedAdded on 2024/06/03
|30
|4787
|183
Report
AI Summary
This report provides a comprehensive assessment of IT security risks within an organization, focusing on identifying various types of security threats such as ransomware, malware, viruses, spyware, and hackers. It details organizational security procedures, including data identification, documentation, configuration, password management, and security continuation. The report proposes a method to assess and treat IT security risks through risk assessment and management, emphasizing the importance of trusted networks and the potential impact of incorrect firewall configurations and third-party VPNs. Furthermore, it explores the implementation of DMZ, static IP, and NAT to enhance network security and discusses the benefits of network monitoring systems. The document reviews mechanisms to control organizational IT security, including risk assessment procedures, data protection processes, and regulations, summarizing the ISO 31000 risk management methodology and the possible impacts of IT security audits. Finally, it addresses the alignment of IT security with organizational policy, designs a security policy, lists the main components of a disaster recovery plan, discusses the roles of stakeholders, and evaluates the suitability of tools used in organizational policy. Desklib offers a variety of study tools and solved assignments for students.

SECURITY
1
1
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

TABLE OF CONTENT
Introduction......................................................................................................................................1
LO1 Assess risks to IT security.......................................................................................................2
P1 Identify types of security risks to organisation......................................................................2
P2 Describe organisational security procedures..........................................................................4
M1 Propose a method to assess and treat IT security risks.........................................................6
D1 Investigate how a ‘trusted network’ may be part of an IT security solution.........................7
LO2 Describe IT security solutions.................................................................................................9
P3 Identify the potential impact to IT security of incorrect configuration of firewall policies
and third-party VPNs...................................................................................................................9
P4 Show, using an example for each, how implementing a DMZ, static IP and NAT in a
network can improve Network Security....................................................................................11
M2 Discuss three benefits to implement network monitoring systems with supporting reasons
...................................................................................................................................................12
LO3 Review mechanisms to control organisational IT security...................................................13
P5 Discuss risk assessment procedures.....................................................................................13
P6 Explain data protection processes and regulations as applicable to an organisation...........15
M3 Summarize the ISO 31000 risk management methodology and its application in IT
security.......................................................................................................................................16
M4 Discuss possible impacts to organisational security resulting from an IT security audit.. .17
D2 Consider how IT security can be aligned with organisational policy, detailing the security
impact of any misalignment.......................................................................................................18
LO4 Manage organisational security.............................................................................................19
P7 Design and implement a security policy for an organisation...............................................19
P8 List the main components of an organisational disaster recovery plan, justifying the reasons
for inclusion...............................................................................................................................20
M5 Discuss the roles of stakeholders in the organisation to implement security audit
recommendations.......................................................................................................................21
D3 Evaluate the suitability of the tools used in an organisational policy..................................22
Conclusion.....................................................................................................................................23
References......................................................................................................................................24
2
Introduction......................................................................................................................................1
LO1 Assess risks to IT security.......................................................................................................2
P1 Identify types of security risks to organisation......................................................................2
P2 Describe organisational security procedures..........................................................................4
M1 Propose a method to assess and treat IT security risks.........................................................6
D1 Investigate how a ‘trusted network’ may be part of an IT security solution.........................7
LO2 Describe IT security solutions.................................................................................................9
P3 Identify the potential impact to IT security of incorrect configuration of firewall policies
and third-party VPNs...................................................................................................................9
P4 Show, using an example for each, how implementing a DMZ, static IP and NAT in a
network can improve Network Security....................................................................................11
M2 Discuss three benefits to implement network monitoring systems with supporting reasons
...................................................................................................................................................12
LO3 Review mechanisms to control organisational IT security...................................................13
P5 Discuss risk assessment procedures.....................................................................................13
P6 Explain data protection processes and regulations as applicable to an organisation...........15
M3 Summarize the ISO 31000 risk management methodology and its application in IT
security.......................................................................................................................................16
M4 Discuss possible impacts to organisational security resulting from an IT security audit.. .17
D2 Consider how IT security can be aligned with organisational policy, detailing the security
impact of any misalignment.......................................................................................................18
LO4 Manage organisational security.............................................................................................19
P7 Design and implement a security policy for an organisation...............................................19
P8 List the main components of an organisational disaster recovery plan, justifying the reasons
for inclusion...............................................................................................................................20
M5 Discuss the roles of stakeholders in the organisation to implement security audit
recommendations.......................................................................................................................21
D3 Evaluate the suitability of the tools used in an organisational policy..................................22
Conclusion.....................................................................................................................................23
References......................................................................................................................................24
2

LIST OF TABLES
Table 1: IT security aligned...........................................................................................................18
3
Table 1: IT security aligned...........................................................................................................18
3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

LIST OF FIGURES
Figure 1: Type of risk......................................................................................................................2
Figure 2: Risk procedure.................................................................................................................4
Figure 3: Type of networks..............................................................................................................7
Figure 4: Firewall............................................................................................................................9
Figure 5: VPNs functioning...........................................................................................................10
Figure 6: Benefit of the network monitoring.................................................................................12
Figure 7: Risk assessment procedure.............................................................................................13
Figure 8: Process View of the ISO 31000.....................................................................................16
4
Figure 1: Type of risk......................................................................................................................2
Figure 2: Risk procedure.................................................................................................................4
Figure 3: Type of networks..............................................................................................................7
Figure 4: Firewall............................................................................................................................9
Figure 5: VPNs functioning...........................................................................................................10
Figure 6: Benefit of the network monitoring.................................................................................12
Figure 7: Risk assessment procedure.............................................................................................13
Figure 8: Process View of the ISO 31000.....................................................................................16
4
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Introduction
The project is based on the security of the information technology in the organisation. As the
organisation face the lot of problems due to the lack of the security. The organisation is used in
the project is Maria for which the different type of network security has been described. Under
this project we have also explained the implementation of the DMZ, static IP and NAT for the
improvement of the network in the organisation. The network benefits and risk assessment has
also described in the project so that the risk can be manage and analysis in the proper way. The
data protection and regulation has also used in the project. The stakeholder audit is arranged by
the organisation for the recommendation of the project security. The stakeholder audit is one of
the best factors in the project as it will provide the proper measurement for the security of the
system.
1
The project is based on the security of the information technology in the organisation. As the
organisation face the lot of problems due to the lack of the security. The organisation is used in
the project is Maria for which the different type of network security has been described. Under
this project we have also explained the implementation of the DMZ, static IP and NAT for the
improvement of the network in the organisation. The network benefits and risk assessment has
also described in the project so that the risk can be manage and analysis in the proper way. The
data protection and regulation has also used in the project. The stakeholder audit is arranged by
the organisation for the recommendation of the project security. The stakeholder audit is one of
the best factors in the project as it will provide the proper measurement for the security of the
system.
1

LO1 Assess risks to IT security
P1 Identify types of security risks to organisation.
For the security of the organisation the proper inspection has to be done for the security of the
system. There are various type of risk arrive in the system that can cause the impact on the data
security and integrity.
Figure 1: Type of risk
(Source: Author)
Ransome and Malware Attack: The Ransome and malware attack can occur in the system while
accessing operation of the computer system. The attack usually corrupts the files and folder in
system after locking the machine that can damage the files hide and steal the information etc.
Viruses: The viruses can cause the effect on the operations of the system by slowing the speed
the computer operations, damaging the data, deleting the files etc.
2
IT Risk
Hackers
Ransom
e and
malware
attack
Viruses
Spaywa
re
P1 Identify types of security risks to organisation.
For the security of the organisation the proper inspection has to be done for the security of the
system. There are various type of risk arrive in the system that can cause the impact on the data
security and integrity.
Figure 1: Type of risk
(Source: Author)
Ransome and Malware Attack: The Ransome and malware attack can occur in the system while
accessing operation of the computer system. The attack usually corrupts the files and folder in
system after locking the machine that can damage the files hide and steal the information etc.
Viruses: The viruses can cause the effect on the operations of the system by slowing the speed
the computer operations, damaging the data, deleting the files etc.
2
IT Risk
Hackers
Ransom
e and
malware
attack
Viruses
Spaywa
re
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Spyware: This type of risk cause the information leak to the unauthorized person that is third
party. The spyware can cause the access to the third person that can software and steal the
important data from the computer (Perlman et.al 2016).
Hackers: The hackers are the third party person that accesses the computer operation by
performing the unauthorized functions in the system. The hacker can access on the important
files and folder even if the files are protected.
3
party. The spyware can cause the access to the third person that can software and steal the
important data from the computer (Perlman et.al 2016).
Hackers: The hackers are the third party person that accesses the computer operation by
performing the unauthorized functions in the system. The hacker can access on the important
files and folder even if the files are protected.
3
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
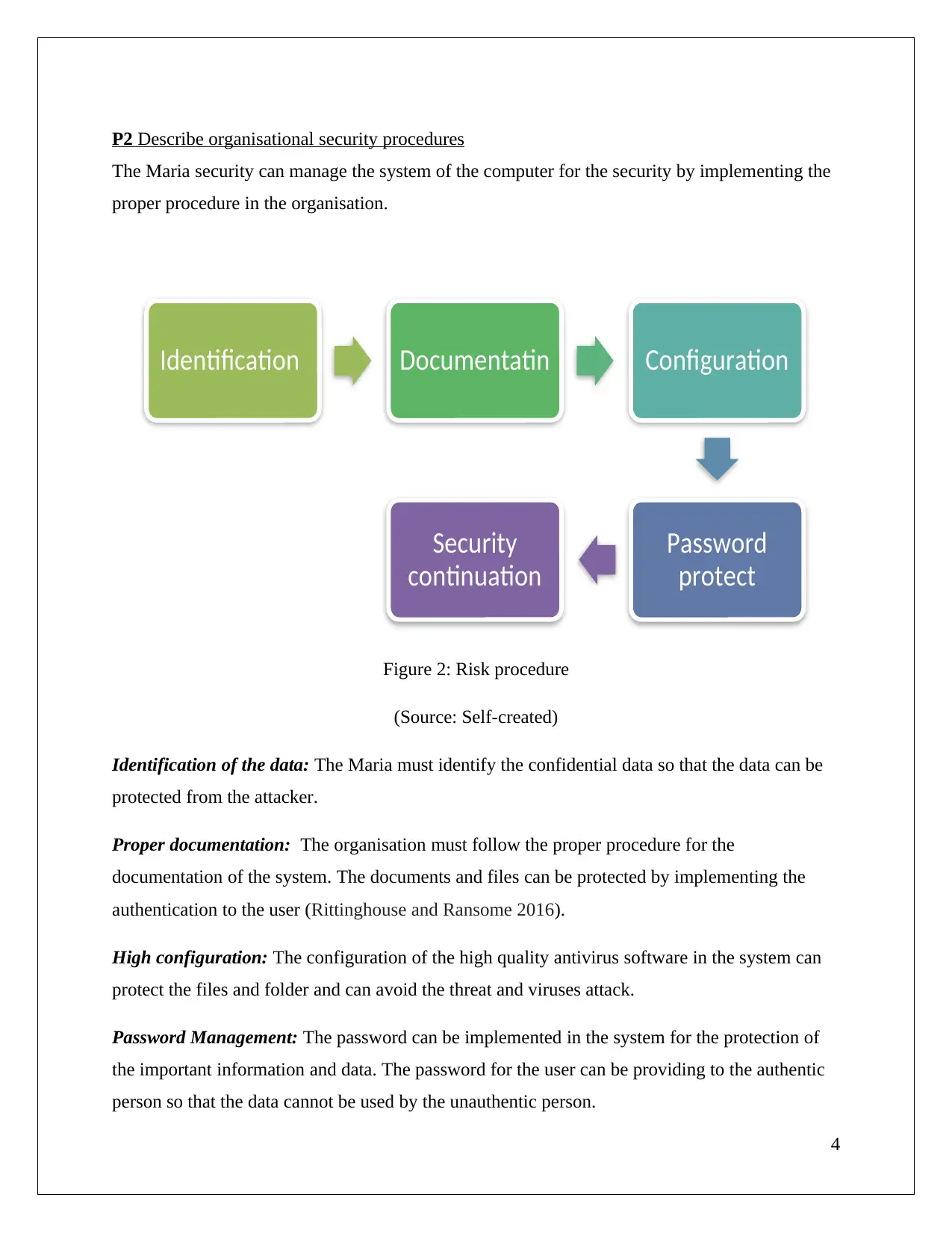
P2 Describe organisational security procedures
The Maria security can manage the system of the computer for the security by implementing the
proper procedure in the organisation.
Figure 2: Risk procedure
(Source: Self-created)
Identification of the data: The Maria must identify the confidential data so that the data can be
protected from the attacker.
Proper documentation: The organisation must follow the proper procedure for the
documentation of the system. The documents and files can be protected by implementing the
authentication to the user (Rittinghouse and Ransome 2016).
High configuration: The configuration of the high quality antivirus software in the system can
protect the files and folder and can avoid the threat and viruses attack.
Password Management: The password can be implemented in the system for the protection of
the important information and data. The password for the user can be providing to the authentic
person so that the data cannot be used by the unauthentic person.
4
Identification Documentatin Configuration
Password
protect
Security
continuation
The Maria security can manage the system of the computer for the security by implementing the
proper procedure in the organisation.
Figure 2: Risk procedure
(Source: Self-created)
Identification of the data: The Maria must identify the confidential data so that the data can be
protected from the attacker.
Proper documentation: The organisation must follow the proper procedure for the
documentation of the system. The documents and files can be protected by implementing the
authentication to the user (Rittinghouse and Ransome 2016).
High configuration: The configuration of the high quality antivirus software in the system can
protect the files and folder and can avoid the threat and viruses attack.
Password Management: The password can be implemented in the system for the protection of
the important information and data. The password for the user can be providing to the authentic
person so that the data cannot be used by the unauthentic person.
4
Identification Documentatin Configuration
Password
protect
Security
continuation

Security procedure continuation: The organisation must continue the process for the protection
of the system. The discontinuation of the procedure or lack of the security can make the system
corrupt and data loss.
These are the basic procedure that has to be followed by the organisation for the security of the
business by following this process the data and information can be kept protected.
5
of the system. The discontinuation of the procedure or lack of the security can make the system
corrupt and data loss.
These are the basic procedure that has to be followed by the organisation for the security of the
business by following this process the data and information can be kept protected.
5
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

M1 Propose a method to assess and treat IT security risks
The data can be protected using the risk assessment and risk management. It refers to the data
identification and evaluation so that the problem can be resolve. The risk can be arising in the
computer by the hackers and attacker. By relating the schedule for the security of the
organisation can reduce the risk of attacker and hacker in the system. The risk assessment can
help the organisation to find out the major cause of the unwanted data deletion and risk of leak of
information. The Maria can implement the risk assessment in the organisation for the
identification of the risk and its renovation of problem (Chang et.al 2016).
Risk management: The risk can be managed by using the risk management process under this
procedure the risk can be analyses and the risk approach can be implemented for the risk
management. The risk matrix is also used to identify the risk by using the risk assessment. The
risk matrix identified by categorizing into two types such as probabilities and likelihood. With
the help of the risk matrix the proper risk management can be prepare for the identification of the
risk.
6
The data can be protected using the risk assessment and risk management. It refers to the data
identification and evaluation so that the problem can be resolve. The risk can be arising in the
computer by the hackers and attacker. By relating the schedule for the security of the
organisation can reduce the risk of attacker and hacker in the system. The risk assessment can
help the organisation to find out the major cause of the unwanted data deletion and risk of leak of
information. The Maria can implement the risk assessment in the organisation for the
identification of the risk and its renovation of problem (Chang et.al 2016).
Risk management: The risk can be managed by using the risk management process under this
procedure the risk can be analyses and the risk approach can be implemented for the risk
management. The risk matrix is also used to identify the risk by using the risk assessment. The
risk matrix identified by categorizing into two types such as probabilities and likelihood. With
the help of the risk matrix the proper risk management can be prepare for the identification of the
risk.
6
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
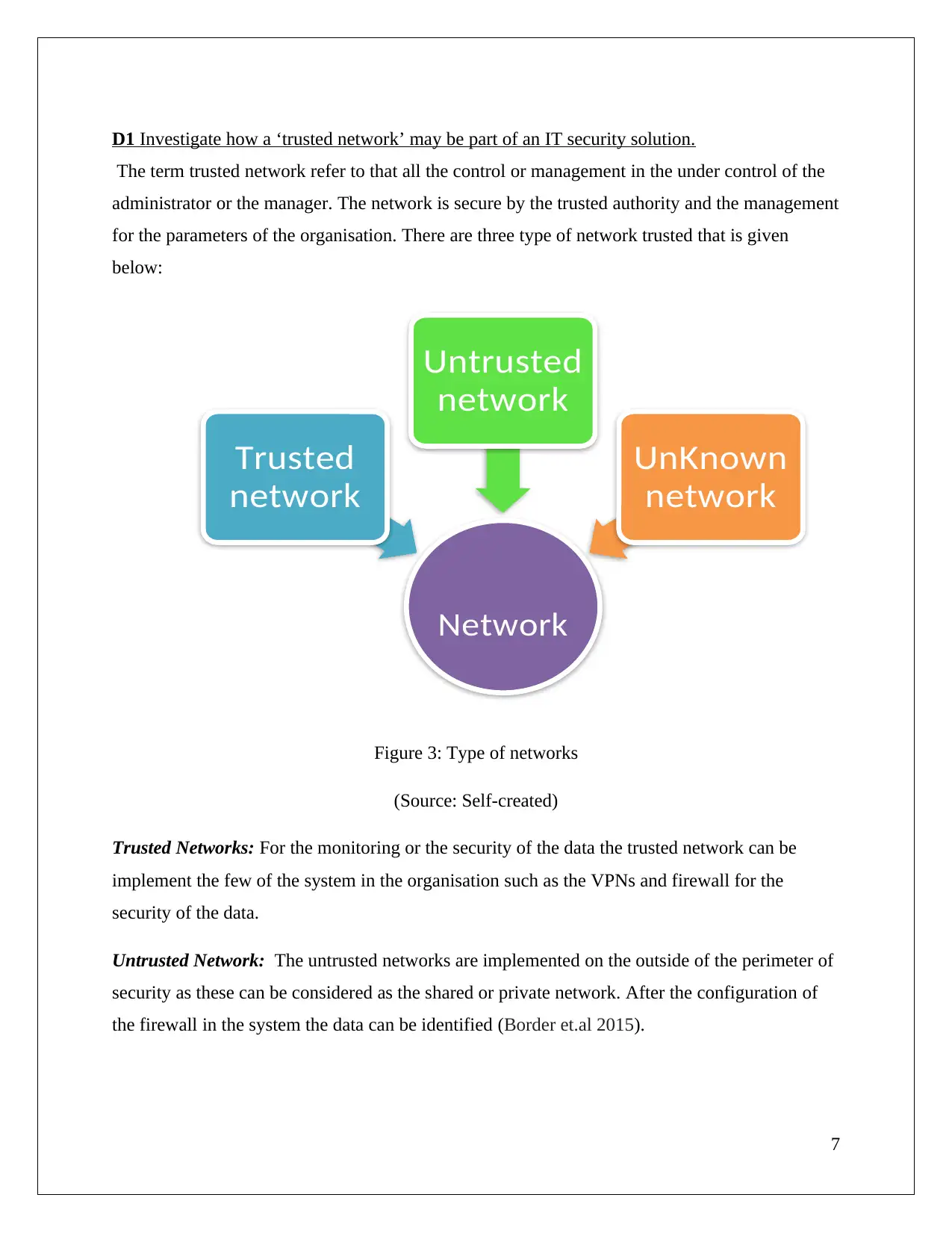
D1 Investigate how a ‘trusted network’ may be part of an IT security solution.
The term trusted network refer to that all the control or management in the under control of the
administrator or the manager. The network is secure by the trusted authority and the management
for the parameters of the organisation. There are three type of network trusted that is given
below:
Figure 3: Type of networks
(Source: Self-created)
Trusted Networks: For the monitoring or the security of the data the trusted network can be
implement the few of the system in the organisation such as the VPNs and firewall for the
security of the data.
Untrusted Network: The untrusted networks are implemented on the outside of the perimeter of
security as these can be considered as the shared or private network. After the configuration of
the firewall in the system the data can be identified (Border et.al 2015).
7
Network
Trusted
network
Untrusted
network
UnKnown
network
The term trusted network refer to that all the control or management in the under control of the
administrator or the manager. The network is secure by the trusted authority and the management
for the parameters of the organisation. There are three type of network trusted that is given
below:
Figure 3: Type of networks
(Source: Self-created)
Trusted Networks: For the monitoring or the security of the data the trusted network can be
implement the few of the system in the organisation such as the VPNs and firewall for the
security of the data.
Untrusted Network: The untrusted networks are implemented on the outside of the perimeter of
security as these can be considered as the shared or private network. After the configuration of
the firewall in the system the data can be identified (Border et.al 2015).
7
Network
Trusted
network
Untrusted
network
UnKnown
network

Unknown network: The network that is difficult to identify is known as neither the unknown
network as these are not the trusted nor the untrusted network. The networks which are not even
identified by the firewall also it can be unauthorized network those are not even identified.
These are the three different type of network used by the organisation for the identification of the
work process and data process.
8
network as these are not the trusted nor the untrusted network. The networks which are not even
identified by the firewall also it can be unauthorized network those are not even identified.
These are the three different type of network used by the organisation for the identification of the
work process and data process.
8
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 30
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.



