IT Security Assessment Report for IT Security Specialist Training
VerifiedAdded on 2022/08/26
|10
|1587
|18
Report
AI Summary
This report serves as an IT Security Assessment, designed to educate junior staff on identifying and mitigating IT security risks. It begins by outlining the potential impacts of incorrect firewall configurations, such as unauthorized data breaches and network vulnerabilities. The report then explores improvements to network security through the implementation of Demilitarized Zones (DMZ), static IP addresses, and Network Address Translation (NAT), detailing how these techniques can defend against various network attacks. It further discusses the benefits of network monitoring systems in optimizing performance, minimizing risks, ensuring compliance, and generating reports. The concept of a trusted network as an integral part of an IT security solution is also examined, emphasizing its interoperability and ability to establish end-to-end trust. The report concludes by summarizing the key topics covered, including security risks, mitigation techniques, and the importance of a comprehensive approach to IT security. The report also discusses about the security risks with the organization and its types that can have a negative impact on the business process. The security issues can rise due to different reason such flaws in the network security configuration, lack of authentication and authorization, etc. The possible security mechanism techniques that can be applied for improving the security. A discussion is made on the firewall policy misconfiguration impact, improvement that can be made with the implementation of DMZ, NAT and static IP address. The integration of network monitoring system and the consideration of trusted network as the IT security solution is also discussed in the report.

Running head: SECURITY PRESENTATION AND GUIDEBOOK
IT Security Assessment report
Name of the Student
Name of the University
Author’s Note
IT Security Assessment report
Name of the Student
Name of the University
Author’s Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
SECURITY PRESENTATION AND GUIDEBOOK
Table of Contents
Introduction......................................................................................................................................2
Potential impact of incorrect firewall configuration on IT security................................................2
Improvement of Network security with the implementation of DMZ, Static IP and NAT.............3
Benefits of network monitoring systems.........................................................................................6
Trusted Network as a part of IT security solution...........................................................................7
Conclusion.......................................................................................................................................8
References........................................................................................................................................9
SECURITY PRESENTATION AND GUIDEBOOK
Table of Contents
Introduction......................................................................................................................................2
Potential impact of incorrect firewall configuration on IT security................................................2
Improvement of Network security with the implementation of DMZ, Static IP and NAT.............3
Benefits of network monitoring systems.........................................................................................6
Trusted Network as a part of IT security solution...........................................................................7
Conclusion.......................................................................................................................................8
References........................................................................................................................................9

2
SECURITY PRESENTATION AND GUIDEBOOK
Introduction
The security system are integrated with the computer networks for monitoring and
preventing the unauthorized access, modification and misuse of information. The security of a
network can be improved by analyzing the firewall configuration and reconfiguring it to restrict
the unauthorized user to access the network. DMZ zone can be implemented along with the use
of static IP and NAT such that different types of attacks such as DDOS can be restricted and the
performance of the network is not affected.
Potential impact of incorrect firewall configuration on IT security
Poor firewall configuration can have different negative outcomes such as unauthorized
data exfiltration and make the computers installed in the network vulnerable to port stabbing. It
can also cause the desired network traffic to be blocked to reach the intended destination. The
data packets can be routed to wrong address or it cannot be routed at all. There can be multiple
sites that uses different router configuration and if it does not matches the standard of
authentication the network is kept vulnerable to attack using the router since it is not aligned with
the centralized authentication mechanism (Perlman, Kaufman & Speciner, 2016). The incorrect
firewall configuration can also cause unexpected reduction of redundancy and increase difficulty
in troubleshooting the different parts of the network. The performance of the firewall can also be
affected if there is excessive rules and logging and it can go down leaving the network
vulnerable to be accessed by the unauthorized users.
SECURITY PRESENTATION AND GUIDEBOOK
Introduction
The security system are integrated with the computer networks for monitoring and
preventing the unauthorized access, modification and misuse of information. The security of a
network can be improved by analyzing the firewall configuration and reconfiguring it to restrict
the unauthorized user to access the network. DMZ zone can be implemented along with the use
of static IP and NAT such that different types of attacks such as DDOS can be restricted and the
performance of the network is not affected.
Potential impact of incorrect firewall configuration on IT security
Poor firewall configuration can have different negative outcomes such as unauthorized
data exfiltration and make the computers installed in the network vulnerable to port stabbing. It
can also cause the desired network traffic to be blocked to reach the intended destination. The
data packets can be routed to wrong address or it cannot be routed at all. There can be multiple
sites that uses different router configuration and if it does not matches the standard of
authentication the network is kept vulnerable to attack using the router since it is not aligned with
the centralized authentication mechanism (Perlman, Kaufman & Speciner, 2016). The incorrect
firewall configuration can also cause unexpected reduction of redundancy and increase difficulty
in troubleshooting the different parts of the network. The performance of the firewall can also be
affected if there is excessive rules and logging and it can go down leaving the network
vulnerable to be accessed by the unauthorized users.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
3
SECURITY PRESENTATION AND GUIDEBOOK
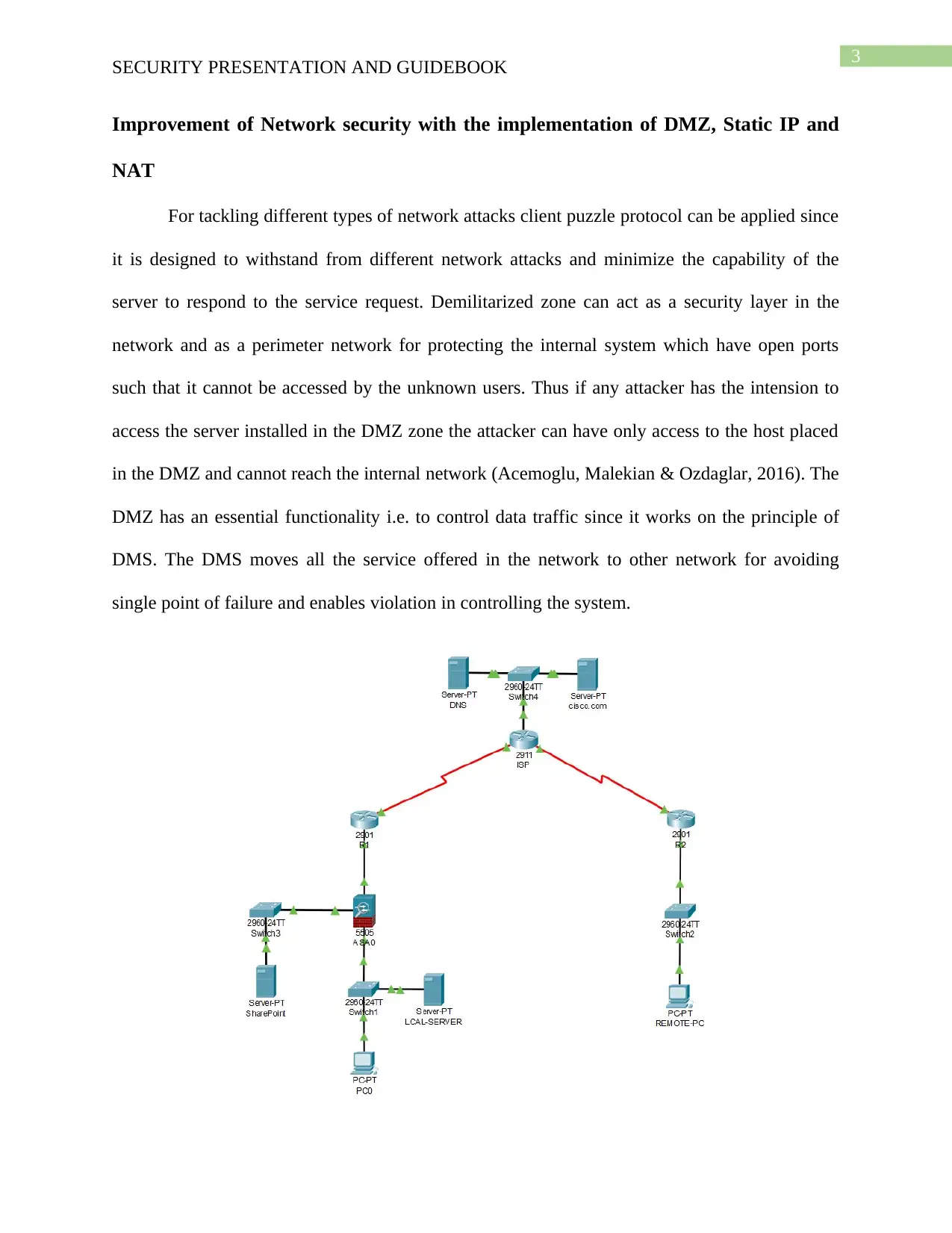
Improvement of Network security with the implementation of DMZ, Static IP and
NAT
For tackling different types of network attacks client puzzle protocol can be applied since
it is designed to withstand from different network attacks and minimize the capability of the
server to respond to the service request. Demilitarized zone can act as a security layer in the
network and as a perimeter network for protecting the internal system which have open ports
such that it cannot be accessed by the unknown users. Thus if any attacker has the intension to
access the server installed in the DMZ zone the attacker can have only access to the host placed
in the DMZ and cannot reach the internal network (Acemoglu, Malekian & Ozdaglar, 2016). The
DMZ has an essential functionality i.e. to control data traffic since it works on the principle of
DMS. The DMS moves all the service offered in the network to other network for avoiding
single point of failure and enables violation in controlling the system.
SECURITY PRESENTATION AND GUIDEBOOK
Improvement of Network security with the implementation of DMZ, Static IP and
NAT
For tackling different types of network attacks client puzzle protocol can be applied since
it is designed to withstand from different network attacks and minimize the capability of the
server to respond to the service request. Demilitarized zone can act as a security layer in the
network and as a perimeter network for protecting the internal system which have open ports
such that it cannot be accessed by the unknown users. Thus if any attacker has the intension to
access the server installed in the DMZ zone the attacker can have only access to the host placed
in the DMZ and cannot reach the internal network (Acemoglu, Malekian & Ozdaglar, 2016). The
DMZ has an essential functionality i.e. to control data traffic since it works on the principle of
DMS. The DMS moves all the service offered in the network to other network for avoiding
single point of failure and enables violation in controlling the system.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4
SECURITY PRESENTATION AND GUIDEBOOK
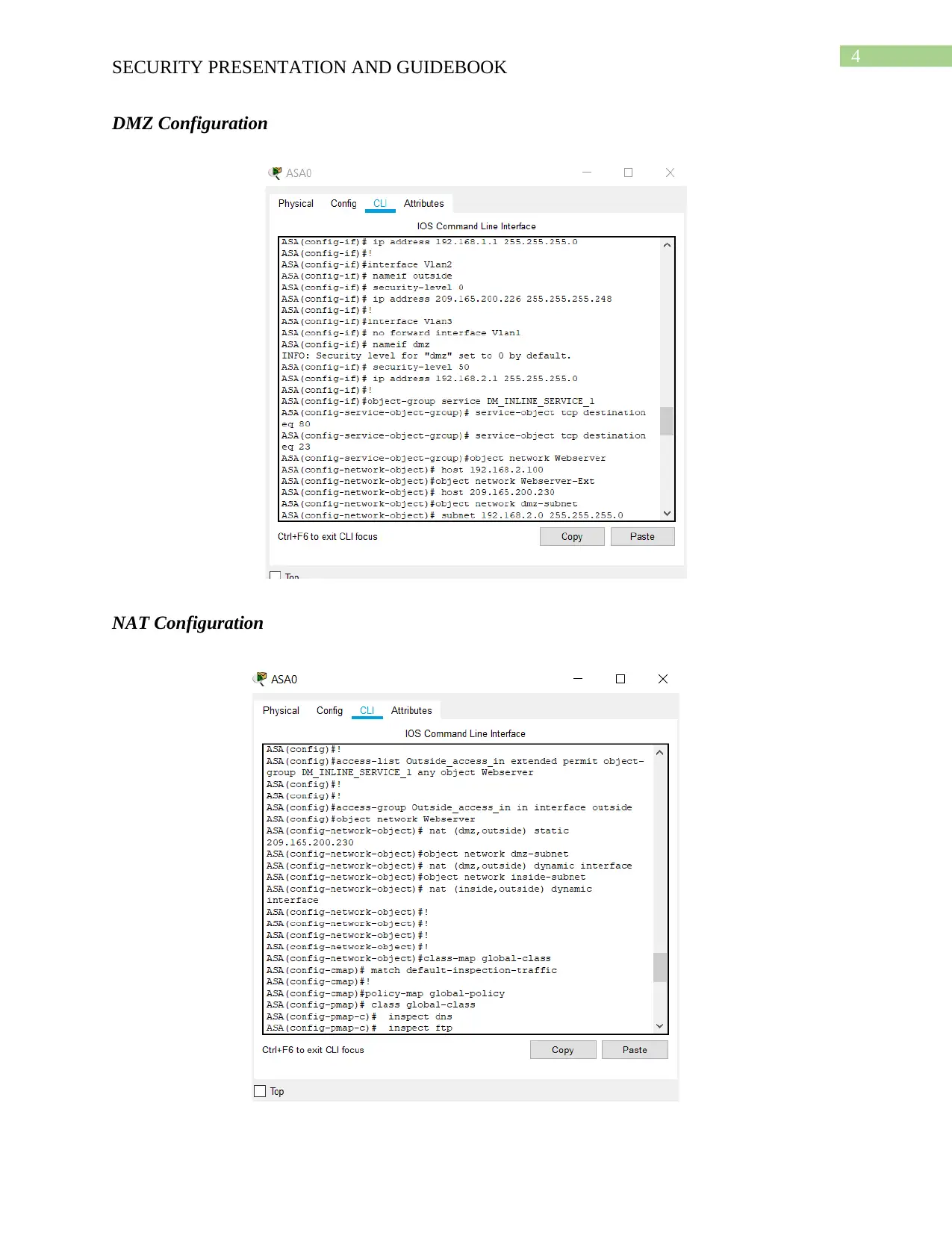
DMZ Configuration
NAT Configuration
SECURITY PRESENTATION AND GUIDEBOOK
DMZ Configuration
NAT Configuration
5
SECURITY PRESENTATION AND GUIDEBOOK
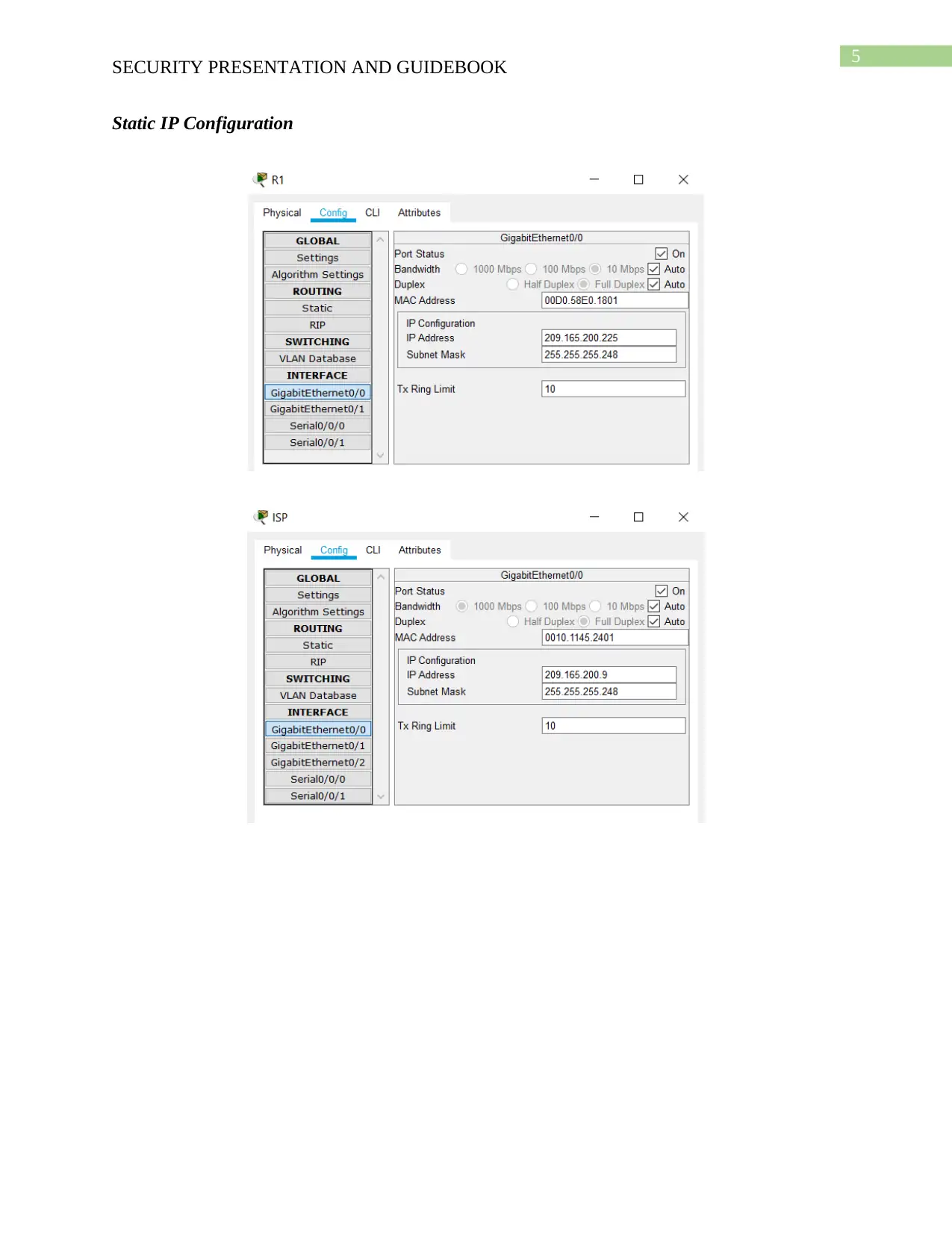
Static IP Configuration
SECURITY PRESENTATION AND GUIDEBOOK
Static IP Configuration
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6
SECURITY PRESENTATION AND GUIDEBOOK
The hosts installed in the DMZ is special that can be contacted directly from outside and
safe application is used in each of the host with the ability of monitoring and updating at a
regular time interval. The demilitarized zone is created based on the concept of NAT/ PAT and
IP addressing. The NAT is used for showing the real address of the packages from where it has
arrived and its destination in the internal network (Kang & Kang, 2016). The PAT shows the
specific port or the range of ports, IP address the data is coming to specific or range of port of
internal IP address and the access list that controls the data precisely to enter the internal
network. Static IP address is necessary to be used in the network since the change in IP address
can cause malfunctioning of the access list and allow the malicious data packet to enter the
internal network.
Benefits of network monitoring systems
Network monitoring is used for monitoring the current network bandwidth usage and
identify the current problems in the network. The network monitoring can help in eliminating the
risk of network slow down or failure of the different network components such as routers,
SECURITY PRESENTATION AND GUIDEBOOK
The hosts installed in the DMZ is special that can be contacted directly from outside and
safe application is used in each of the host with the ability of monitoring and updating at a
regular time interval. The demilitarized zone is created based on the concept of NAT/ PAT and
IP addressing. The NAT is used for showing the real address of the packages from where it has
arrived and its destination in the internal network (Kang & Kang, 2016). The PAT shows the
specific port or the range of ports, IP address the data is coming to specific or range of port of
internal IP address and the access list that controls the data precisely to enter the internal
network. Static IP address is necessary to be used in the network since the change in IP address
can cause malfunctioning of the access list and allow the malicious data packet to enter the
internal network.
Benefits of network monitoring systems
Network monitoring is used for monitoring the current network bandwidth usage and
identify the current problems in the network. The network monitoring can help in eliminating the
risk of network slow down or failure of the different network components such as routers,
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7
SECURITY PRESENTATION AND GUIDEBOOK
firewalls, client system and the servers (Stallings, 2016). The following are the benefits of the
network monitoring system:
Optimizing the performance – the slowdown and network problems can be identified
with the collection of performance data. The integration of network monitoring system can help
the network administrator to optimize the performance of the network and eliminate the
vulnerability such that the attacking problems can be eliminated and prevent from future attacks
(Rathore et al., 2017).
Minimizing the risk – The malicious threats and behavior in the network can be identified
with the help of network monitoring system and it can help in track the threats on the network.
Unauthorized access to the network resources and changes of password can be tracked such that
unusual behavior can be flagged and thus it is ensured that security breaches can be identified
and eliminated as soon as possible (Shin et al., 2016).
Compliance and maintenance – The monitoring system is needed to be complied with
the regulatory entities such as HIPPA, ISO 207001 and DSS PCI such that best practice is
carried out and security measure is integrated with the solution.
Network Reporting – The monitoring software can be used for generating report and
share the findings with the network administrator. Some of the network monitoring software can
also offer customization of report and automation such that the network administrator can be
alerted on finding unusual usage of the network (Beberlein et al., 2017).
Trusted Network as a part of IT security solution
Trusted network can be a part of the IT security solution since the network is developed
following set of standards and network security policy that makes it interoperable and establish
SECURITY PRESENTATION AND GUIDEBOOK
firewalls, client system and the servers (Stallings, 2016). The following are the benefits of the
network monitoring system:
Optimizing the performance – the slowdown and network problems can be identified
with the collection of performance data. The integration of network monitoring system can help
the network administrator to optimize the performance of the network and eliminate the
vulnerability such that the attacking problems can be eliminated and prevent from future attacks
(Rathore et al., 2017).
Minimizing the risk – The malicious threats and behavior in the network can be identified
with the help of network monitoring system and it can help in track the threats on the network.
Unauthorized access to the network resources and changes of password can be tracked such that
unusual behavior can be flagged and thus it is ensured that security breaches can be identified
and eliminated as soon as possible (Shin et al., 2016).
Compliance and maintenance – The monitoring system is needed to be complied with
the regulatory entities such as HIPPA, ISO 207001 and DSS PCI such that best practice is
carried out and security measure is integrated with the solution.
Network Reporting – The monitoring software can be used for generating report and
share the findings with the network administrator. Some of the network monitoring software can
also offer customization of report and automation such that the network administrator can be
alerted on finding unusual usage of the network (Beberlein et al., 2017).
Trusted Network as a part of IT security solution
Trusted network can be a part of the IT security solution since the network is developed
following set of standards and network security policy that makes it interoperable and establish

8
SECURITY PRESENTATION AND GUIDEBOOK
an end to end trust with multi user environment. It can also provide different network
technologies, policies and variety of end point to communicate with each other. The compliance
of the network can be evaluated with the help of intelligent decisions about policy, dynamic
enforcement of security and automation of security for the security systems and disparate
networks (Yang & Fung, 2016). The trusted network has multiple interoperable standards such
as visibility of endpoint and network, compliance with the endpoint, network enforcement for
blocking and managing access of the users. The information about the connected device, threats
and users can be shared at a real time and thus can be considered as a part of IT security solution.
Conclusion
The report discusses about the security risks with the organization and its types that can
have a negative impact on the business process. The security issues can rise due to different
reason such flaws in the network security configuration, lack of authentication and authorization,
etc. The possible security mechanism techniques that can be applied for improving the security.
A discussion is made on the firewall policy misconfiguration impact, improvement that can be
made with the implementation of DMZ, NAT and static IP address. The integration of network
monitoring system and the consideration of trusted network as the IT security solution is also
discussed in the report.
SECURITY PRESENTATION AND GUIDEBOOK
an end to end trust with multi user environment. It can also provide different network
technologies, policies and variety of end point to communicate with each other. The compliance
of the network can be evaluated with the help of intelligent decisions about policy, dynamic
enforcement of security and automation of security for the security systems and disparate
networks (Yang & Fung, 2016). The trusted network has multiple interoperable standards such
as visibility of endpoint and network, compliance with the endpoint, network enforcement for
blocking and managing access of the users. The information about the connected device, threats
and users can be shared at a real time and thus can be considered as a part of IT security solution.
Conclusion
The report discusses about the security risks with the organization and its types that can
have a negative impact on the business process. The security issues can rise due to different
reason such flaws in the network security configuration, lack of authentication and authorization,
etc. The possible security mechanism techniques that can be applied for improving the security.
A discussion is made on the firewall policy misconfiguration impact, improvement that can be
made with the implementation of DMZ, NAT and static IP address. The integration of network
monitoring system and the consideration of trusted network as the IT security solution is also
discussed in the report.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9
SECURITY PRESENTATION AND GUIDEBOOK
References
Acemoglu, D., Malekian, A., & Ozdaglar, A. (2016). Network security and contagion. Journal
of Economic Theory, 166, 536-585.
Beberlein, L. T., Dias, G., Levitt, K. N., Mukherjee, B., & Wood, J. (2017). Network attacks and
an Ethernet-based network security monitor.
Kang, M. J., & Kang, J. W. (2016). Intrusion detection system using deep neural network for in-
vehicle network security. PloS one, 11(6), e0155781.
Perlman, R., Kaufman, C., & Speciner, M. (2016). Network security: private communication in a
public world. Pearson Education India.
Rathore, S., Sharma, P. K., Loia, V., Jeong, Y. S., & Park, J. H. (2017). Social network security:
Issues, challenges, threats, and solutions. Information sciences, 421, 43-69.
Shin, S., Xu, L., Hong, S., & Gu, G. (2016, August). Enhancing network security through
software defined networking (SDN). In 2016 25th international conference on computer
communication and networks (ICCCN) (pp. 1-9). IEEE.
Stallings, W. (2016). Network security essentials: applications and standards. Pearson.
Yang, W., & Fung, C. (2016, June). A survey on security in network functions virtualization.
In 2016 IEEE NetSoft Conference and Workshops (NetSoft) (pp. 15-19). IEEE.
SECURITY PRESENTATION AND GUIDEBOOK
References
Acemoglu, D., Malekian, A., & Ozdaglar, A. (2016). Network security and contagion. Journal
of Economic Theory, 166, 536-585.
Beberlein, L. T., Dias, G., Levitt, K. N., Mukherjee, B., & Wood, J. (2017). Network attacks and
an Ethernet-based network security monitor.
Kang, M. J., & Kang, J. W. (2016). Intrusion detection system using deep neural network for in-
vehicle network security. PloS one, 11(6), e0155781.
Perlman, R., Kaufman, C., & Speciner, M. (2016). Network security: private communication in a
public world. Pearson Education India.
Rathore, S., Sharma, P. K., Loia, V., Jeong, Y. S., & Park, J. H. (2017). Social network security:
Issues, challenges, threats, and solutions. Information sciences, 421, 43-69.
Shin, S., Xu, L., Hong, S., & Gu, G. (2016, August). Enhancing network security through
software defined networking (SDN). In 2016 25th international conference on computer
communication and networks (ICCCN) (pp. 1-9). IEEE.
Stallings, W. (2016). Network security essentials: applications and standards. Pearson.
Yang, W., & Fung, C. (2016, June). A survey on security in network functions virtualization.
In 2016 IEEE NetSoft Conference and Workshops (NetSoft) (pp. 15-19). IEEE.
1 out of 10
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





