Comprehensive IT Security Report: Audits, Risks, and Compliance
VerifiedAdded on 2020/02/05
|15
|5492
|94
Report
AI Summary
This report provides a comprehensive overview of IT security, encompassing security audits, risk assessments, and the legal and regulatory compliance requirements for companies. It differentiates between security audits and risk assessments, detailing their respective purposes and methodologies. The report also outlines the legal, regulatory, and compliance aspects crucial for IT security, including cyber laws, financial record confidentiality, and privacy. Furthermore, it delves into identifying network hosts, services, and peripheral devices to enhance security. The report discusses risk management strategies, including actions to resolve high-level risks, and highlights the importance of maintaining data confidentiality and security within IT systems. The content is structured to provide a clear understanding of IT security principles and practices, emphasizing the importance of proactive measures to mitigate risks and ensure data protection. The report also includes an illustration of a LAN infrastructure and references relevant sources.

IT Security
1
1
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
INTRODUCTION ...............................................................................................................................4
TASK 1.................................................................................................................................................4
Purpose and differences of security audits and risk assessments....................................................4
Legal, regulatory and compliance requirements for companies to carry out risk assessments.......6
Identify.............................................................................................................................................7
4. Description of above in its current state......................................................................................9
Strategies to manage and resolve the different levels of risk when conducting a risk assessment11
Actions that can be taken to resolve the high level risk items.......................................................12
CONCLUSION..................................................................................................................................13
References..........................................................................................................................................14
2
INTRODUCTION ...............................................................................................................................4
TASK 1.................................................................................................................................................4
Purpose and differences of security audits and risk assessments....................................................4
Legal, regulatory and compliance requirements for companies to carry out risk assessments.......6
Identify.............................................................................................................................................7
4. Description of above in its current state......................................................................................9
Strategies to manage and resolve the different levels of risk when conducting a risk assessment11
Actions that can be taken to resolve the high level risk items.......................................................12
CONCLUSION..................................................................................................................................13
References..........................................................................................................................................14
2

Illustration Index
Illustration 1: LAN Infrastructure........................................................................................................8
3
Illustration 1: LAN Infrastructure........................................................................................................8
3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

INTRODUCTION
IT security is also called as cyber security or computer security. Information security is
designed for protecting confidential, important and data in the computer system from the
unauthorised access. IT security helps in protection of the information system, hardware or software
from any kind of threat. This consists of controlling physical access to the hardware and protecting
data from harm through the network access or other means. With the creasing use of the computers
and other IT technologies, security regarding them is also increasing. It is essential to secure
computer systems from various threats which include computer crime, Trojans, malware, exploits,
viruses, denial of service, etc (Al-Aqrabi and et.al., 2012).
The present study includes purpose of security audits and risk assessment, legal, regulatory
and compliance requirement for the company. Along with this, the file consists of loss to the
organisation in the case of data hijack and weighting for indicating the level of risk.
TASK 1
Purpose and differences of security audits and risk assessments.
Security audit refers to the systematic measurable and technical evaluation of the system or
applications used by the company. IT firms conducts security audit of its system and other
applications time to time for checking their security status. It also conducts manual assessment by
asking the staff members, performs security vulnerability scans, check access controls related to
the operating system. System of the IT firms includes personal computer, servers, mainframes,
switches and network routers.
Purpose of the security audit:
The purpose of IT firms behind conducting security audit is to check the vulnerability of
network. With the help of audit only, company can identify issues or problems which lie in the
network or system. It is important for the firm to keep its information and data secure which is only
possible through the audit. Along with this, security audit protects information from common
security breaches and identifies loophole in the complete system. This evaluation helps the
company in improving weaknesses for making security stronger. In addition to it, this process is
cost effective so firm can conduct it whenever it feels the requirement (Baryshnikov, 2012).
Another purpose of IT firms is to determine the higher and lower risks for evaluating proper
solutions for resolving them accordingly. It is very difficult to detect vulnerability in the network or
application automatically so audit is organised by the firm. In favour to this, it also helps in testing
the ability and capacity of the network defenders to detect attacks or harms to the information or
4
IT security is also called as cyber security or computer security. Information security is
designed for protecting confidential, important and data in the computer system from the
unauthorised access. IT security helps in protection of the information system, hardware or software
from any kind of threat. This consists of controlling physical access to the hardware and protecting
data from harm through the network access or other means. With the creasing use of the computers
and other IT technologies, security regarding them is also increasing. It is essential to secure
computer systems from various threats which include computer crime, Trojans, malware, exploits,
viruses, denial of service, etc (Al-Aqrabi and et.al., 2012).
The present study includes purpose of security audits and risk assessment, legal, regulatory
and compliance requirement for the company. Along with this, the file consists of loss to the
organisation in the case of data hijack and weighting for indicating the level of risk.
TASK 1
Purpose and differences of security audits and risk assessments.
Security audit refers to the systematic measurable and technical evaluation of the system or
applications used by the company. IT firms conducts security audit of its system and other
applications time to time for checking their security status. It also conducts manual assessment by
asking the staff members, performs security vulnerability scans, check access controls related to
the operating system. System of the IT firms includes personal computer, servers, mainframes,
switches and network routers.
Purpose of the security audit:
The purpose of IT firms behind conducting security audit is to check the vulnerability of
network. With the help of audit only, company can identify issues or problems which lie in the
network or system. It is important for the firm to keep its information and data secure which is only
possible through the audit. Along with this, security audit protects information from common
security breaches and identifies loophole in the complete system. This evaluation helps the
company in improving weaknesses for making security stronger. In addition to it, this process is
cost effective so firm can conduct it whenever it feels the requirement (Baryshnikov, 2012).
Another purpose of IT firms is to determine the higher and lower risks for evaluating proper
solutions for resolving them accordingly. It is very difficult to detect vulnerability in the network or
application automatically so audit is organised by the firm. In favour to this, it also helps in testing
the ability and capacity of the network defenders to detect attacks or harms to the information or
4
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
systems. Security audit on timely basis provides evidences to support the increase in investments
regarding security of the personnel and technologies (Ackermann, 2012).
Purpose of risk assessment:
It refers to the process of determining the hazards and risks related to them so that
appropriate solutions can be identified to control them. The purpose of risk assessment is to prevent
employees from any kind of injury or risk. IT firms conducts assessment time to time for
identifying any kind of risk to the stored information and workers. The major purpose behind risk
assessment is to remove or reduce the level of risk due to hazards for creating safer working
environment. It helps the firm in recognising existing hazards and dangers in the company (Casey,
2011).
Along with above purpose, another aim is to aware employees about the risk so that they can keep
away themselves from it or handle it with care and safety. This awareness helps in reducing the
number of incidents within the organisation. Along with it, this process saves cost by being
proactive rather than reactive. It also helps in determining the type of training provided to the
workers so that they can handle the risky system or things with proper safety and security (Aloul,
2012).
Difference between security audit and risk assessment
Elements Security Audit Risk Assessment
Who can perform? It is conducted by an
independent and certified third
party. It is not possible to
conduct self-audit (Haimes,
2015).
It can be either conducted by
the company itself or by an
independent third party.
How deep it goes? It is a detailed and thorough
analysis of the technologies,
controls and policies. It also
includes testing of all the
system and other items.
It is a high level overview of
the company's technologies,
controls and policies. It does
not include any kind of testing
(Chernysheva, 2013).
Who requires what? Audit is conducted by the firm
to comply with different
Federal, state or industry
regulations (Wolf and
Gendrullis, 2011).
It is conducted for completing
IT risk assessment for cyber
security insurance requirement.
5
regarding security of the personnel and technologies (Ackermann, 2012).
Purpose of risk assessment:
It refers to the process of determining the hazards and risks related to them so that
appropriate solutions can be identified to control them. The purpose of risk assessment is to prevent
employees from any kind of injury or risk. IT firms conducts assessment time to time for
identifying any kind of risk to the stored information and workers. The major purpose behind risk
assessment is to remove or reduce the level of risk due to hazards for creating safer working
environment. It helps the firm in recognising existing hazards and dangers in the company (Casey,
2011).
Along with above purpose, another aim is to aware employees about the risk so that they can keep
away themselves from it or handle it with care and safety. This awareness helps in reducing the
number of incidents within the organisation. Along with it, this process saves cost by being
proactive rather than reactive. It also helps in determining the type of training provided to the
workers so that they can handle the risky system or things with proper safety and security (Aloul,
2012).
Difference between security audit and risk assessment
Elements Security Audit Risk Assessment
Who can perform? It is conducted by an
independent and certified third
party. It is not possible to
conduct self-audit (Haimes,
2015).
It can be either conducted by
the company itself or by an
independent third party.
How deep it goes? It is a detailed and thorough
analysis of the technologies,
controls and policies. It also
includes testing of all the
system and other items.
It is a high level overview of
the company's technologies,
controls and policies. It does
not include any kind of testing
(Chernysheva, 2013).
Who requires what? Audit is conducted by the firm
to comply with different
Federal, state or industry
regulations (Wolf and
Gendrullis, 2011).
It is conducted for completing
IT risk assessment for cyber
security insurance requirement.
5

How often they are completed? For completing this, there is
particular time-frame. It is
generally conducted on yearly
basis.
It is conducted on yearly basis
or whenever there is any
significant change in IT
environment. This consists of
addition or removal of any
software, application, system,
hardware, etc (Baier and
Breitinger, 2011).
Legal, regulatory and compliance requirements for companies to carry out risk assessments
Risk assessment is a process of determine the hazards so that appropriate actions can be take
to control the impact of risks. This process shows the probability of occurrence of a treat. From the
IT industry perspective, there are three major and important elements of risk: asset, threat and
vulnerability (Kim, Lee and Lee, 2012). Here, asset is an IT infrastructure part that has either
qualitative or quantitative value for the company. On the other hand, threat defines any kind of
incident that may be the reason of loss for IT asset. Similarly, vulnerability is a weakness of IT
component that can be used for destroy or damage IT asset.
For ensure the safety of the employees at the workplace, a complete and appropriate risk
assessment process is needed. If the organization is not aware about the workplace safety issues
than it has created the danger situation for employees, service users and the whole enterprise. So, it
is important to carry out the risk assessment process to eliminate the level of hazards and evolve the
new methods to resolve them. There are different reasons of conducting the risk assessment process
within the IT security companies (Scheid, 2013). The first cause of risk evaluation is ensure the
optimal productivity. Some times, employees have deal with defective system and tools and try to
fix things. It has wasted both time and money of IT companies and their workforce. So, with the
help of risk assessment process, organizations can create an ergonomic workplace and train the staff
to complete their work in safe manner (Whitman and Mattord, 2011). It has improved optimal
productivity of workers. Another reason of risk evaluation process is creating positive image in the
marketplace. If IT companies have done appropriate risk assessment method and show commitment
towards the safety than it will increase the success opportunities for the firms. Hence, from the
above stated causes, there are some more reasons to carried out risk assessment process in IT
companies (Khan, 2016).
During the process of risk assessment, IT organizations has needed to follow legal,
regulatory and compliance requirements. These all helps in define the scope of the risk evaluation
6
particular time-frame. It is
generally conducted on yearly
basis.
It is conducted on yearly basis
or whenever there is any
significant change in IT
environment. This consists of
addition or removal of any
software, application, system,
hardware, etc (Baier and
Breitinger, 2011).
Legal, regulatory and compliance requirements for companies to carry out risk assessments
Risk assessment is a process of determine the hazards so that appropriate actions can be take
to control the impact of risks. This process shows the probability of occurrence of a treat. From the
IT industry perspective, there are three major and important elements of risk: asset, threat and
vulnerability (Kim, Lee and Lee, 2012). Here, asset is an IT infrastructure part that has either
qualitative or quantitative value for the company. On the other hand, threat defines any kind of
incident that may be the reason of loss for IT asset. Similarly, vulnerability is a weakness of IT
component that can be used for destroy or damage IT asset.
For ensure the safety of the employees at the workplace, a complete and appropriate risk
assessment process is needed. If the organization is not aware about the workplace safety issues
than it has created the danger situation for employees, service users and the whole enterprise. So, it
is important to carry out the risk assessment process to eliminate the level of hazards and evolve the
new methods to resolve them. There are different reasons of conducting the risk assessment process
within the IT security companies (Scheid, 2013). The first cause of risk evaluation is ensure the
optimal productivity. Some times, employees have deal with defective system and tools and try to
fix things. It has wasted both time and money of IT companies and their workforce. So, with the
help of risk assessment process, organizations can create an ergonomic workplace and train the staff
to complete their work in safe manner (Whitman and Mattord, 2011). It has improved optimal
productivity of workers. Another reason of risk evaluation process is creating positive image in the
marketplace. If IT companies have done appropriate risk assessment method and show commitment
towards the safety than it will increase the success opportunities for the firms. Hence, from the
above stated causes, there are some more reasons to carried out risk assessment process in IT
companies (Khan, 2016).
During the process of risk assessment, IT organizations has needed to follow legal,
regulatory and compliance requirements. These all helps in define the scope of the risk evaluation
6
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

and vulnerability assessment for the given IT assets. It has ensured that IT companies are following
proper security, laws, regulations, guidelines and procedures at the workplace or not. The laws,
regulatory and compliance related to IT security has covered different areas such as cyber laws and
crimes, financial records confidentiality, privacy and corporate integrity (Cárdenas, Amin, Lin and
et.al., 2011). Explanation of require legal, regulatory and compliance for IT companies to carry out
risk assessment process is as follows.
IT system security level: With the use of legal, regulatory and compliance frameworks, it becomes
easy to determine the system security level. Due to this, the confidentiality, availability, integrity,
accountability and auditability of the IT system within the organizations. The potential level of
danger from IT security system has determined the weakness of the current system (Boyle and
Panko, 2014).
Determining risk phase: Various legal, regulatory and compliance frameworks helps the IT
companies during the risk assessment process in terms to identify the different risk phases. By
doing this, it becomes easy to calculate the level of many risks and the probability of occurrence as
well as their impact on IT system.
Identify threats and vulnerability: Various legal, regulatory and compliance frameworks helps in
identifying the those threats that can exploit system vulnerability. This is a part of risk assessment
process. With the help of this, the system connections, risks and their controls, risk of failure of the
system, errors can be determined in risk evaluation process (McManus, 2012.).
Rather than this, the different legal, regulatory and compliance frameworks helps the IT
companies in risk assessment process in terms of maintain the data confidentiality and security. It
has ensured that organizations are effectively implement the cyber laws or not (Asgari, Farahani and
Goh, 2013). During the risk assessment process, legal, regulatory and compliance regulations have
determine the potential risks of unauthorized access to devices and other unethical computer related
activities and their impacts. Another reason of need of the laws within the IT security companies is
assure that the organizations are protecting the individual personal information by maintain the
confidentiality or not (Modares, Salleh and Moravejosharieh, 2011). Therefore, from the above
stated statements has shown the different evidence to understand the needs and requirements of
legal, regulatory and compliance frameworks for IT companies during risk assessment process.
Identify
o The main hosts on your network.
o Services that are linked to the device that include credentials
o Peripheral devices that may contain data or network credentials
7
proper security, laws, regulations, guidelines and procedures at the workplace or not. The laws,
regulatory and compliance related to IT security has covered different areas such as cyber laws and
crimes, financial records confidentiality, privacy and corporate integrity (Cárdenas, Amin, Lin and
et.al., 2011). Explanation of require legal, regulatory and compliance for IT companies to carry out
risk assessment process is as follows.
IT system security level: With the use of legal, regulatory and compliance frameworks, it becomes
easy to determine the system security level. Due to this, the confidentiality, availability, integrity,
accountability and auditability of the IT system within the organizations. The potential level of
danger from IT security system has determined the weakness of the current system (Boyle and
Panko, 2014).
Determining risk phase: Various legal, regulatory and compliance frameworks helps the IT
companies during the risk assessment process in terms to identify the different risk phases. By
doing this, it becomes easy to calculate the level of many risks and the probability of occurrence as
well as their impact on IT system.
Identify threats and vulnerability: Various legal, regulatory and compliance frameworks helps in
identifying the those threats that can exploit system vulnerability. This is a part of risk assessment
process. With the help of this, the system connections, risks and their controls, risk of failure of the
system, errors can be determined in risk evaluation process (McManus, 2012.).
Rather than this, the different legal, regulatory and compliance frameworks helps the IT
companies in risk assessment process in terms of maintain the data confidentiality and security. It
has ensured that organizations are effectively implement the cyber laws or not (Asgari, Farahani and
Goh, 2013). During the risk assessment process, legal, regulatory and compliance regulations have
determine the potential risks of unauthorized access to devices and other unethical computer related
activities and their impacts. Another reason of need of the laws within the IT security companies is
assure that the organizations are protecting the individual personal information by maintain the
confidentiality or not (Modares, Salleh and Moravejosharieh, 2011). Therefore, from the above
stated statements has shown the different evidence to understand the needs and requirements of
legal, regulatory and compliance frameworks for IT companies during risk assessment process.
Identify
o The main hosts on your network.
o Services that are linked to the device that include credentials
o Peripheral devices that may contain data or network credentials
7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
o Software that may have credentials saved automatically
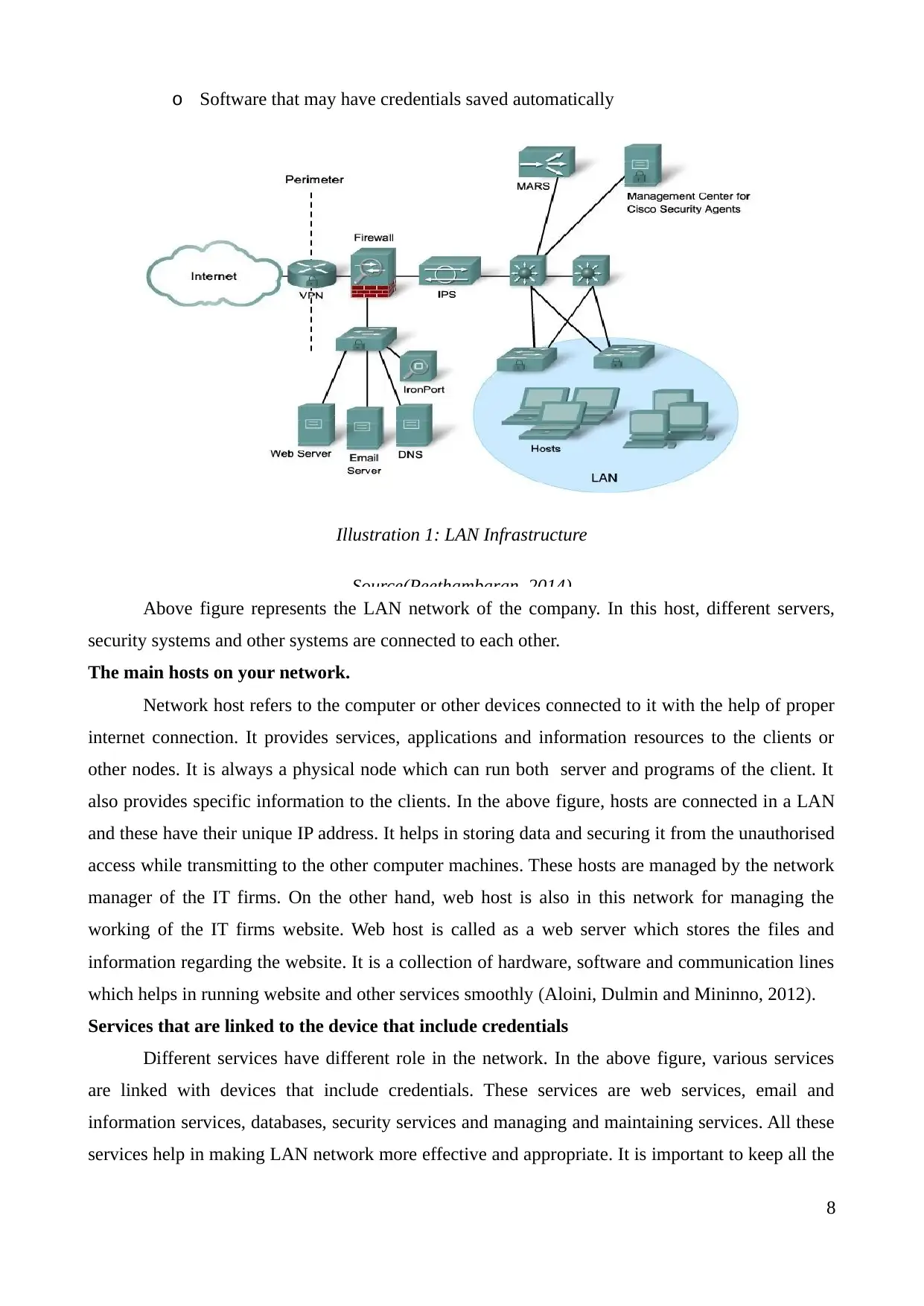
Above figure represents the LAN network of the company. In this host, different servers,
security systems and other systems are connected to each other.
The main hosts on your network.
Network host refers to the computer or other devices connected to it with the help of proper
internet connection. It provides services, applications and information resources to the clients or
other nodes. It is always a physical node which can run both server and programs of the client. It
also provides specific information to the clients. In the above figure, hosts are connected in a LAN
and these have their unique IP address. It helps in storing data and securing it from the unauthorised
access while transmitting to the other computer machines. These hosts are managed by the network
manager of the IT firms. On the other hand, web host is also in this network for managing the
working of the IT firms website. Web host is called as a web server which stores the files and
information regarding the website. It is a collection of hardware, software and communication lines
which helps in running website and other services smoothly (Aloini, Dulmin and Mininno, 2012).
Services that are linked to the device that include credentials
Different services have different role in the network. In the above figure, various services
are linked with devices that include credentials. These services are web services, email and
information services, databases, security services and managing and maintaining services. All these
services help in making LAN network more effective and appropriate. It is important to keep all the
8
Illustration 1: LAN Infrastructure
Source(Peethambaran, 2014)
Above figure represents the LAN network of the company. In this host, different servers,
security systems and other systems are connected to each other.
The main hosts on your network.
Network host refers to the computer or other devices connected to it with the help of proper
internet connection. It provides services, applications and information resources to the clients or
other nodes. It is always a physical node which can run both server and programs of the client. It
also provides specific information to the clients. In the above figure, hosts are connected in a LAN
and these have their unique IP address. It helps in storing data and securing it from the unauthorised
access while transmitting to the other computer machines. These hosts are managed by the network
manager of the IT firms. On the other hand, web host is also in this network for managing the
working of the IT firms website. Web host is called as a web server which stores the files and
information regarding the website. It is a collection of hardware, software and communication lines
which helps in running website and other services smoothly (Aloini, Dulmin and Mininno, 2012).
Services that are linked to the device that include credentials
Different services have different role in the network. In the above figure, various services
are linked with devices that include credentials. These services are web services, email and
information services, databases, security services and managing and maintaining services. All these
services help in making LAN network more effective and appropriate. It is important to keep all the
8
Illustration 1: LAN Infrastructure
Source(Peethambaran, 2014)

information safe and secure and for this it is essential to have proper security services in the
network so that third person cannot access any confidential information. Credentials help in keeping
devices safe and secure. Each device has its own unique credentials for keeping the access safe. The
feature of the credentials in the devices shows the status of each device which includes managed,
unmanaged and unreachable (Asgari, Farahani and Goh, 2013).
Peripheral devices that may contain data or network credentials
Pheripheral devices also called as auxillary devices which includes mouse, keyboard, image
scanner, tape drives, microphones, webcams and digital cameras. For proper access to the
information and other devices it is essential to have pheripheral devices. For proper managing the
netwrok IT firms uses various peripheral devices such as mouse, keyboard, printer, scanner and
webcams. With the help of these devices company makes its network more easy to run and execute
(Cárdenas and et.al., 2011).
Software that may have credentials saved automatically
Credentials plays essential role in providing security to the network. While connecting to a
remote computer with the help of emote desktop connection, system asked user to provide his/her
credentials. For this, there are some software which saves the credentials automatically into them so
that user can use them at the time of requirement. With the help of these saved credentials, user can
easily access their systems and can work properly. While looking for the credentials for a specific
host, this software query to the user and then stop after getting first answer. During saving the
credentials, software send username and password to all the helpers in the list and it depends upon
them what type of action they want to take (Boyle and Panko, 2014).
Description of above in its current state
A. Loss that would be incurred as a result of the item being taken physically or hijacked
In the present time, the risk or threat of harm, loss or compromise to an IT asset has
increased in IT companies. Form the perspective of IT industry the risk of loss of IT components
can affect the integrity, confidentiality and availability of the data in the terms of modifications,
information corrupt, disclosure etc. In the case of LAN IT system infrastructure, if any host or other
IT components has either physically harmed or hijacked by other party than loss of data can be
increase (Aloini, Dulmin and Mininno, 2012). Loss that would be incurred as a result of the item of
LAN being taken physically or hijacked are as follows.
Unauthorized access: In the situation of hijacked the IT asset by some one else has increased the
risk of unauthorized access of the data. With the help of different type of hacking method, the
hacker or attacker can gain the information about the ids and passwords of IT system of companies.
It leads to raise the risk of access the confidential information by unauthorized users (Kim, Lee and
9
network so that third person cannot access any confidential information. Credentials help in keeping
devices safe and secure. Each device has its own unique credentials for keeping the access safe. The
feature of the credentials in the devices shows the status of each device which includes managed,
unmanaged and unreachable (Asgari, Farahani and Goh, 2013).
Peripheral devices that may contain data or network credentials
Pheripheral devices also called as auxillary devices which includes mouse, keyboard, image
scanner, tape drives, microphones, webcams and digital cameras. For proper access to the
information and other devices it is essential to have pheripheral devices. For proper managing the
netwrok IT firms uses various peripheral devices such as mouse, keyboard, printer, scanner and
webcams. With the help of these devices company makes its network more easy to run and execute
(Cárdenas and et.al., 2011).
Software that may have credentials saved automatically
Credentials plays essential role in providing security to the network. While connecting to a
remote computer with the help of emote desktop connection, system asked user to provide his/her
credentials. For this, there are some software which saves the credentials automatically into them so
that user can use them at the time of requirement. With the help of these saved credentials, user can
easily access their systems and can work properly. While looking for the credentials for a specific
host, this software query to the user and then stop after getting first answer. During saving the
credentials, software send username and password to all the helpers in the list and it depends upon
them what type of action they want to take (Boyle and Panko, 2014).
Description of above in its current state
A. Loss that would be incurred as a result of the item being taken physically or hijacked
In the present time, the risk or threat of harm, loss or compromise to an IT asset has
increased in IT companies. Form the perspective of IT industry the risk of loss of IT components
can affect the integrity, confidentiality and availability of the data in the terms of modifications,
information corrupt, disclosure etc. In the case of LAN IT system infrastructure, if any host or other
IT components has either physically harmed or hijacked by other party than loss of data can be
increase (Aloini, Dulmin and Mininno, 2012). Loss that would be incurred as a result of the item of
LAN being taken physically or hijacked are as follows.
Unauthorized access: In the situation of hijacked the IT asset by some one else has increased the
risk of unauthorized access of the data. With the help of different type of hacking method, the
hacker or attacker can gain the information about the ids and passwords of IT system of companies.
It leads to raise the risk of access the confidential information by unauthorized users (Kim, Lee and
9
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Lee, 2012).
Lost of data: Due to the physical damage of IT component of LAN system, it is hard to recover or
modify the entire information. The potential damage of the system has influenced the organization
to made the compromise on the stage of loss of data.
Disclosure of important information: It is another loss that would be incurred as a result of the
LAN IT asset being taken physically or hijacked. The risk of disclosure of confidential data has
increased which leads to cause of loss of revenue, unable to take competitive advantages (Kim and
Gregg, 2005).
B. Level of risk/vulnerability
LAN structure system has consist the different types of risk and it has affected the working
of the system. The level of risk according to their weighting are showing in below table.
Type of risk Explanation Level of risk (10 to 1
i.e. high to low)
Attacks of hackers These are unauthorized people who attacks IT
security system with some personal benefits
4 (Lower)
Cyber terrorism Under this attack, the cyber terrorism has used
different kinds of system, software etc to
capture the important information of the firm.
3 (Low)
Malware and viruses It damages data that stores in IT system of
company. Along with this, it also stole the
information and create the replicate of one file
that can affect the entire data set of organization
(Whitman and Mattord, 2011).
10 (Highest)
Unauthorized access Under this risk, the unauthorized users can
easily access the IT system of the firm and get
the id and password. By doing this, they can
access the confidential information and data of
the company (Boyle and Panko, 2014).
6 (Higher)
Stolen or modification
in data
By not adopting the plan of backup of the data
or damaging of IT asset has raised the risk of
loss of information. Due to this, it has hard to
recover or modify the past data.
8 (High)
10
Lost of data: Due to the physical damage of IT component of LAN system, it is hard to recover or
modify the entire information. The potential damage of the system has influenced the organization
to made the compromise on the stage of loss of data.
Disclosure of important information: It is another loss that would be incurred as a result of the
LAN IT asset being taken physically or hijacked. The risk of disclosure of confidential data has
increased which leads to cause of loss of revenue, unable to take competitive advantages (Kim and
Gregg, 2005).
B. Level of risk/vulnerability
LAN structure system has consist the different types of risk and it has affected the working
of the system. The level of risk according to their weighting are showing in below table.
Type of risk Explanation Level of risk (10 to 1
i.e. high to low)
Attacks of hackers These are unauthorized people who attacks IT
security system with some personal benefits
4 (Lower)
Cyber terrorism Under this attack, the cyber terrorism has used
different kinds of system, software etc to
capture the important information of the firm.
3 (Low)
Malware and viruses It damages data that stores in IT system of
company. Along with this, it also stole the
information and create the replicate of one file
that can affect the entire data set of organization
(Whitman and Mattord, 2011).
10 (Highest)
Unauthorized access Under this risk, the unauthorized users can
easily access the IT system of the firm and get
the id and password. By doing this, they can
access the confidential information and data of
the company (Boyle and Panko, 2014).
6 (Higher)
Stolen or modification
in data
By not adopting the plan of backup of the data
or damaging of IT asset has raised the risk of
loss of information. Due to this, it has hard to
recover or modify the past data.
8 (High)
10
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Disclosure of
confidential
information
The loss of confidential data has increase
because of weakness of IT security system. It
has affected the performance level of the
organization as well as unable the firm to take
competitive advantages (McManus, 2012).
5 (Moderate)
Natural disaster The risk of damage or loss of data due to
occurrence of natural disaster may be raised.
Hurricanes, change in weather conditions,
floods, earthquakes etc has increased the risk of
damage or vulnerability of IT assets.
2 (Lowest)
Strategies to manage and resolve the different levels of risk when conducting a risk assessment
For managing the risks while conducting risk assessment, following four major categories
are being used by IT companies. Avoidance: It is one of the best way to manage the risks, firms invest more efforts for
identifying this option. It refers to redesigning the work or processes regarding the project
so that risky step no longer has to be taken. On the other hand, it also means to stop doing
particular task or project in the future (Kim, Lee and Lee, 2012). Transfer: This means making other party to accept the risk by transferring it to them under a
contract. Mitigation: In this, risk are treated by IT organisations for reducing its impact. Companies
accept that some risks are not good to avoid or transfer so it is better to handle them
properly.
Acceptance: In this, IT companies accept risk for achieving its goals or objectives.
Strategies to manage and resolve the different level of risks while conducting a risk
assessment are as follows.
Risk Mitigation Strategy: In this, company needs to create a plan for managing the risks. This
approach is used for reducing number impact of risk (McManus, 2012). A checklist is formed by the
risk handling manager. It contains the type of risks with their probability of occurrence or level.
Then as per the level, risks are being handled and controlled. The actions taken by the company for
resolving risks include the following steps. Establishing context of risk: In this, category or level of the risks being determined i.e.
either they are low level risk or high level.
11
confidential
information
The loss of confidential data has increase
because of weakness of IT security system. It
has affected the performance level of the
organization as well as unable the firm to take
competitive advantages (McManus, 2012).
5 (Moderate)
Natural disaster The risk of damage or loss of data due to
occurrence of natural disaster may be raised.
Hurricanes, change in weather conditions,
floods, earthquakes etc has increased the risk of
damage or vulnerability of IT assets.
2 (Lowest)
Strategies to manage and resolve the different levels of risk when conducting a risk assessment
For managing the risks while conducting risk assessment, following four major categories
are being used by IT companies. Avoidance: It is one of the best way to manage the risks, firms invest more efforts for
identifying this option. It refers to redesigning the work or processes regarding the project
so that risky step no longer has to be taken. On the other hand, it also means to stop doing
particular task or project in the future (Kim, Lee and Lee, 2012). Transfer: This means making other party to accept the risk by transferring it to them under a
contract. Mitigation: In this, risk are treated by IT organisations for reducing its impact. Companies
accept that some risks are not good to avoid or transfer so it is better to handle them
properly.
Acceptance: In this, IT companies accept risk for achieving its goals or objectives.
Strategies to manage and resolve the different level of risks while conducting a risk
assessment are as follows.
Risk Mitigation Strategy: In this, company needs to create a plan for managing the risks. This
approach is used for reducing number impact of risk (McManus, 2012). A checklist is formed by the
risk handling manager. It contains the type of risks with their probability of occurrence or level.
Then as per the level, risks are being handled and controlled. The actions taken by the company for
resolving risks include the following steps. Establishing context of risk: In this, category or level of the risks being determined i.e.
either they are low level risk or high level.
11

Identifying risk: In this, reasonable consequence and likelihood of the risks are identified by
the company during its risk assessment. Evaluating risk: This step includes analysis of risk tolerance and existing risk management
controls Treating risk: In this, company ensures that risks control tools and plans are relevant to the
risks and their consequences. If they are not then changes are being take place as per the
requirement for handling and controlling the risks (Modares, Salleh and Moravejosharieh,
2011.
Tracking and reporting to the risk plan: After the proper formation of risk plan, status
regarding the risks are being monitored and recorded by the company on monthly basis.
Risk management strategy: This strategy can be implemented for the low level and small projects
as well. It helps in identifying various risks at the time of risk assessment (Whitman and Mattord,
2011). With the help of this strategy, companies can effectively manage and control the risks.
Following stages are followed by IT firms for managing and resolving different level of risks. Identification of risks: In this, risks are being identified by the firm with their probability of
occurrence. It helps in understanding the type of risk and its connection with the working
processes or employees. Assessment: In this step, proper evaluation and estimation of the risk is take place by the IT
organisations. Loss to the profit, resources, cost, employees, projects, etc due to that risk are
being identified. Plan: As per the obtained results proper and effective action plan is formed by the company
for resolving each and every risk. Current risk handling tools and techniques are also
checked and tested by the organisation so that suitable changes can be made as per the
current situation and requirement (Al-Aqrabi and et.al., 2012).
Implementation: The developed plan is implemented in this step for resolving the risks.
Company monitor and handle the complete implemented plan time to time.
Actions that can be taken to resolve the high level risk items
As per the above mentioned table, it has been identified that there are different types of risk
related to LAN system. These have been rated from highest to lowest level. The hazards that comes
under the category between the lowest to low can be avoid. But the risk which are come under
highest to higher needed to be mitigate as soon as possible (Asgari, Farahani and Goh, 2013). By
doing this, the probability of occurrence of these risk can be minimized. Actions that can be taken to
resolve the high level risk activities are as follows:
12
the company during its risk assessment. Evaluating risk: This step includes analysis of risk tolerance and existing risk management
controls Treating risk: In this, company ensures that risks control tools and plans are relevant to the
risks and their consequences. If they are not then changes are being take place as per the
requirement for handling and controlling the risks (Modares, Salleh and Moravejosharieh,
2011.
Tracking and reporting to the risk plan: After the proper formation of risk plan, status
regarding the risks are being monitored and recorded by the company on monthly basis.
Risk management strategy: This strategy can be implemented for the low level and small projects
as well. It helps in identifying various risks at the time of risk assessment (Whitman and Mattord,
2011). With the help of this strategy, companies can effectively manage and control the risks.
Following stages are followed by IT firms for managing and resolving different level of risks. Identification of risks: In this, risks are being identified by the firm with their probability of
occurrence. It helps in understanding the type of risk and its connection with the working
processes or employees. Assessment: In this step, proper evaluation and estimation of the risk is take place by the IT
organisations. Loss to the profit, resources, cost, employees, projects, etc due to that risk are
being identified. Plan: As per the obtained results proper and effective action plan is formed by the company
for resolving each and every risk. Current risk handling tools and techniques are also
checked and tested by the organisation so that suitable changes can be made as per the
current situation and requirement (Al-Aqrabi and et.al., 2012).
Implementation: The developed plan is implemented in this step for resolving the risks.
Company monitor and handle the complete implemented plan time to time.
Actions that can be taken to resolve the high level risk items
As per the above mentioned table, it has been identified that there are different types of risk
related to LAN system. These have been rated from highest to lowest level. The hazards that comes
under the category between the lowest to low can be avoid. But the risk which are come under
highest to higher needed to be mitigate as soon as possible (Asgari, Farahani and Goh, 2013). By
doing this, the probability of occurrence of these risk can be minimized. Actions that can be taken to
resolve the high level risk activities are as follows:
12
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 15
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




