Cyber Security: Academic Communication in Science Report - IT Field
VerifiedAdded on 2023/06/11
|8
|1647
|421
Report
AI Summary
This report provides an overview of cyber security, emphasizing its importance in modern companies and organizations compared to other IT fields. It highlights the increasing threat of cybercrime and the necessity of robust security measures. The report discusses key areas within cyber security, such as wireless security, data recovery, and access controls, and presents research data illustrating the prevalence of cybercrime versus other security issues like cyber warfare and hacktivism. It also addresses the limitations of studying cyber security, including usability challenges, higher costs, and the time-consuming nature of implementing security measures. The report concludes by suggesting areas for further research in cyber security, such as Internet of Things (IoT) security and cloud storage technology. Desklib provides access to this and other solved assignments for students.

Cyber Security 1
ACADEMIC COMMUNICATION IN SCIENCE
By
(Name)
(Course)
(Professor’s Name)
(Institution)
(State)
(Date)
ACADEMIC COMMUNICATION IN SCIENCE
By
(Name)
(Course)
(Professor’s Name)
(Institution)
(State)
(Date)
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Cyber Security 2
Abstract
Cyber security is important in modern companies and organization, hence Information
Technology (IT), computer science and any computer related students need to focus much on
cyber securing as compared to other disciplines such as programming and hardware. Data and
information regarding cyber security was collected using several methodologies, for example,
observation and interviewing. Participants included IT personnel from various organizations
such as International Organization for Standardization (ISO). The research revealed that cyber-
crime has increased greatly because of advancements in modern information technologies.
Introduction to Cyber Security
Cyber security is one of the major trends in computer technology. Many organizations
and companies have integrated computer systems into their day-to-day activities aiming at
simplifying most of the tasks that could have been done by human beings (Bulman and Fairlie
2016). Emerging trends in networking such as big data and Internet of Things (IoT) alongside
advancements in modern technology are some of the core factors that have influenced many
companies and organizations to incorporate computers into their operations. For instance,
computers are used in all fields ranging from manufacturing industries to medicine (Bulman and
Fairlie 2016). However, protecting computers against attacks and unauthorized access is a bit
tricky because of complexity in modern computer systems. Simply, computer security is
associated with some of the ways on which computers systems, wireless networks and internet at
large can be protected against attacks and unauthorized access (Von and Van 2013,97).
Information Technology (IT), computer science and any related computer technology students
need to concentrate much on cyber security, although there are other computer related disciplines
such as programming and networking. Therefore, students should focus on the following key
Abstract
Cyber security is important in modern companies and organization, hence Information
Technology (IT), computer science and any computer related students need to focus much on
cyber securing as compared to other disciplines such as programming and hardware. Data and
information regarding cyber security was collected using several methodologies, for example,
observation and interviewing. Participants included IT personnel from various organizations
such as International Organization for Standardization (ISO). The research revealed that cyber-
crime has increased greatly because of advancements in modern information technologies.
Introduction to Cyber Security
Cyber security is one of the major trends in computer technology. Many organizations
and companies have integrated computer systems into their day-to-day activities aiming at
simplifying most of the tasks that could have been done by human beings (Bulman and Fairlie
2016). Emerging trends in networking such as big data and Internet of Things (IoT) alongside
advancements in modern technology are some of the core factors that have influenced many
companies and organizations to incorporate computers into their operations. For instance,
computers are used in all fields ranging from manufacturing industries to medicine (Bulman and
Fairlie 2016). However, protecting computers against attacks and unauthorized access is a bit
tricky because of complexity in modern computer systems. Simply, computer security is
associated with some of the ways on which computers systems, wireless networks and internet at
large can be protected against attacks and unauthorized access (Von and Van 2013,97).
Information Technology (IT), computer science and any related computer technology students
need to concentrate much on cyber security, although there are other computer related disciplines
such as programming and networking. Therefore, students should focus on the following key

Cyber Security 3
areas in cyber security; wireless security, maintenance of computer systems and wireless
networks, email protection, access controls both physical and logical, data recovery and data
encryption (Von and Van 2013,97). The aim of writing this report is to show that cyber security
is very important as compared to other fields in the field of Information Technology (IT). Also,
the report has discussed explicitly about some of the challenges that are associated with studying
of cyber security.
Results of the Research
Cyber crime
59%
Cyber
Warfafe
23%
Cyber
Espionage
10%
Hackitivism
9%
Cyber Security
Analysis 2017
Cyber crime
Cyber Warfafe
Cyber Espionage
Hackitivism
Figure 1.0
The figure 1.0 above shows cyber security analysis that was recorded from the research.
From the figure, it’s evident that cyber security issues have increased greatly. The data from the
figure 1.0 above reveals that cyber-crime has the highest percentage compared to other security
issues such as hacktivism. For instance, cyber-crime has 58%, cyber warfare has 23%, followed
by cyber espionage with 10%, and lastly, hacktivism 9% (Prasad 2017).
Important Resources of Modern Companies
areas in cyber security; wireless security, maintenance of computer systems and wireless
networks, email protection, access controls both physical and logical, data recovery and data
encryption (Von and Van 2013,97). The aim of writing this report is to show that cyber security
is very important as compared to other fields in the field of Information Technology (IT). Also,
the report has discussed explicitly about some of the challenges that are associated with studying
of cyber security.
Results of the Research
Cyber crime
59%
Cyber
Warfafe
23%
Cyber
Espionage
10%
Hackitivism
9%
Cyber Security
Analysis 2017
Cyber crime
Cyber Warfafe
Cyber Espionage
Hackitivism
Figure 1.0
The figure 1.0 above shows cyber security analysis that was recorded from the research.
From the figure, it’s evident that cyber security issues have increased greatly. The data from the
figure 1.0 above reveals that cyber-crime has the highest percentage compared to other security
issues such as hacktivism. For instance, cyber-crime has 58%, cyber warfare has 23%, followed
by cyber espionage with 10%, and lastly, hacktivism 9% (Prasad 2017).
Important Resources of Modern Companies
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
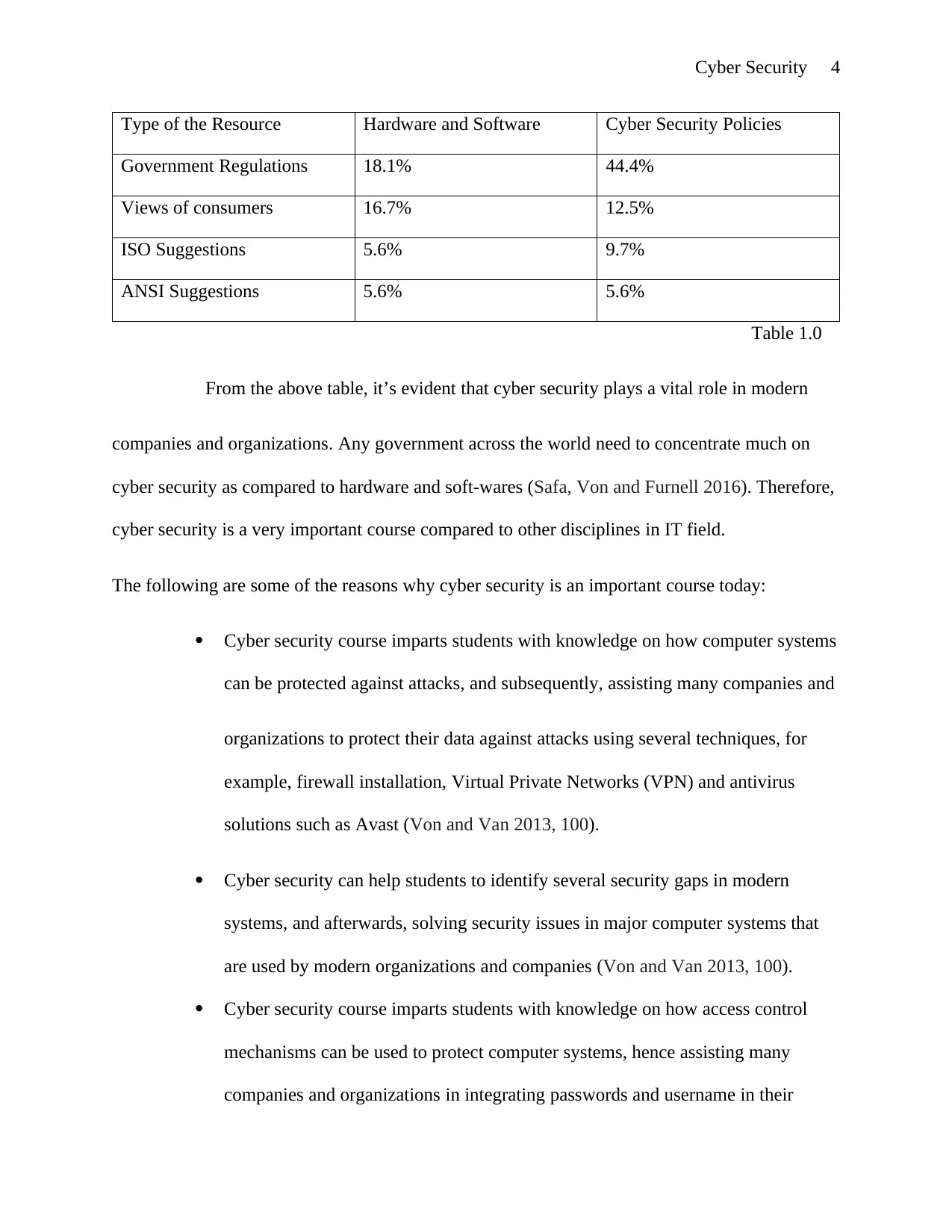
Cyber Security 4
Type of the Resource Hardware and Software Cyber Security Policies
Government Regulations 18.1% 44.4%
Views of consumers 16.7% 12.5%
ISO Suggestions 5.6% 9.7%
ANSI Suggestions 5.6% 5.6%
Table 1.0
From the above table, it’s evident that cyber security plays a vital role in modern
companies and organizations. Any government across the world need to concentrate much on
cyber security as compared to hardware and soft-wares (Safa, Von and Furnell 2016). Therefore,
cyber security is a very important course compared to other disciplines in IT field.
The following are some of the reasons why cyber security is an important course today:
Cyber security course imparts students with knowledge on how computer systems
can be protected against attacks, and subsequently, assisting many companies and
organizations to protect their data against attacks using several techniques, for
example, firewall installation, Virtual Private Networks (VPN) and antivirus
solutions such as Avast (Von and Van 2013, 100).
Cyber security can help students to identify several security gaps in modern
systems, and afterwards, solving security issues in major computer systems that
are used by modern organizations and companies (Von and Van 2013, 100).
Cyber security course imparts students with knowledge on how access control
mechanisms can be used to protect computer systems, hence assisting many
companies and organizations in integrating passwords and username in their
Type of the Resource Hardware and Software Cyber Security Policies
Government Regulations 18.1% 44.4%
Views of consumers 16.7% 12.5%
ISO Suggestions 5.6% 9.7%
ANSI Suggestions 5.6% 5.6%
Table 1.0
From the above table, it’s evident that cyber security plays a vital role in modern
companies and organizations. Any government across the world need to concentrate much on
cyber security as compared to hardware and soft-wares (Safa, Von and Furnell 2016). Therefore,
cyber security is a very important course compared to other disciplines in IT field.
The following are some of the reasons why cyber security is an important course today:
Cyber security course imparts students with knowledge on how computer systems
can be protected against attacks, and subsequently, assisting many companies and
organizations to protect their data against attacks using several techniques, for
example, firewall installation, Virtual Private Networks (VPN) and antivirus
solutions such as Avast (Von and Van 2013, 100).
Cyber security can help students to identify several security gaps in modern
systems, and afterwards, solving security issues in major computer systems that
are used by modern organizations and companies (Von and Van 2013, 100).
Cyber security course imparts students with knowledge on how access control
mechanisms can be used to protect computer systems, hence assisting many
companies and organizations in integrating passwords and username in their
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Cyber Security 5
systems, therefore, keeping computers systems secured against attacks that can
affect data availability and integrity (Von and Van 2013, 100).
Discussion
The figure 1.0 has revealed that security issues such as cyber-crime has increased greatly.
Cybercrime is associated with the process of jeopardizing operations of individuals,
organizations and companies using internet aiming at causing harm, for example, data loss. Also,
cybercrime can involve stealing one’s data and information, for example, bank account details
such as account number and passwords aiming at withdrawing money without user’s consent.
This has raised a lot of concern in many countries such as Australia. Common examples of
cyber-crime include the following; cyber-bullying and identity theft (Prasad 2017).
Apart from increase in cyber-crimes, the research also revealed that cyber security is
among one of the important necessities in modern companies and organizations as evidenced
from the table 1.0. For instance, according to the guidelines that are provided by American
National Standards Institutes (ANSI) it’s evident that companies and organizations need to put
more effort to secure their data and information against attacks. Therefore, cyber security course
is very important as compared to the other Information Technology (IT) disciplines such as
programming and hardware (Safa, Von and Furnell 2016).
Limitations of Studying Cyber Security
There are many challenges and disadvantages that are associated with studying cyber
security. The following are some of the challenges that may be encountered:
systems, therefore, keeping computers systems secured against attacks that can
affect data availability and integrity (Von and Van 2013, 100).
Discussion
The figure 1.0 has revealed that security issues such as cyber-crime has increased greatly.
Cybercrime is associated with the process of jeopardizing operations of individuals,
organizations and companies using internet aiming at causing harm, for example, data loss. Also,
cybercrime can involve stealing one’s data and information, for example, bank account details
such as account number and passwords aiming at withdrawing money without user’s consent.
This has raised a lot of concern in many countries such as Australia. Common examples of
cyber-crime include the following; cyber-bullying and identity theft (Prasad 2017).
Apart from increase in cyber-crimes, the research also revealed that cyber security is
among one of the important necessities in modern companies and organizations as evidenced
from the table 1.0. For instance, according to the guidelines that are provided by American
National Standards Institutes (ANSI) it’s evident that companies and organizations need to put
more effort to secure their data and information against attacks. Therefore, cyber security course
is very important as compared to the other Information Technology (IT) disciplines such as
programming and hardware (Safa, Von and Furnell 2016).
Limitations of Studying Cyber Security
There are many challenges and disadvantages that are associated with studying cyber
security. The following are some of the challenges that may be encountered:

Cyber Security 6
Usability of computer systems. Protecting computer systems and wireless networks
against attacks makes them more complicated, hence it becomes difficult for unskilled
employees to operate the systems (Safa, Von and Furnell 2016, 10).
Higher costs are incurred by companies and organizations. More secured systems can be
very expensive, hence many limiting most companies and organizations from adopting
such technologies.
Cyber security is time consuming. For instance, it takes much time for students to learn
and understand clearly how wireless security can be achieved (Safa, Von and Furnell
2016, 10).
Incorporation of human factors. The entire process of securing system requires
involvement of people especially relevant users of the systems; therefore, complicating
the entire process of securing wireless networks (Safa, Von and Furnell 2016,10).
Areas for Further Research in Cyber Security
The following are some of the areas for further research:
Internet of Things (IOT) security.
Data back-up and recovery.
Cloud storage technology.
Security of computer systems.
Security of wireless networks (Choras et al. 2015, 687).
Summary of Cyber Security Report
Cyber security is one of the emerging trends in the field of Information Technology (IT).
Cyber security is concerned with protection of wireless networks and internet at large against
attacks and unauthorize access. Also, cyber security is a very important subject as compared to
Usability of computer systems. Protecting computer systems and wireless networks
against attacks makes them more complicated, hence it becomes difficult for unskilled
employees to operate the systems (Safa, Von and Furnell 2016, 10).
Higher costs are incurred by companies and organizations. More secured systems can be
very expensive, hence many limiting most companies and organizations from adopting
such technologies.
Cyber security is time consuming. For instance, it takes much time for students to learn
and understand clearly how wireless security can be achieved (Safa, Von and Furnell
2016, 10).
Incorporation of human factors. The entire process of securing system requires
involvement of people especially relevant users of the systems; therefore, complicating
the entire process of securing wireless networks (Safa, Von and Furnell 2016,10).
Areas for Further Research in Cyber Security
The following are some of the areas for further research:
Internet of Things (IOT) security.
Data back-up and recovery.
Cloud storage technology.
Security of computer systems.
Security of wireless networks (Choras et al. 2015, 687).
Summary of Cyber Security Report
Cyber security is one of the emerging trends in the field of Information Technology (IT).
Cyber security is concerned with protection of wireless networks and internet at large against
attacks and unauthorize access. Also, cyber security is a very important subject as compared to
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Cyber Security 7
other IT disciplines such as programming as evidenced throughout the report. For instance, cyber
security imparts students with knowledge on how access control mechanisms can be used to
protect computer systems, hence assisting many companies and organizations in integrating
passwords and username in their systems, therefore, keeping computers systems secured against
attacks that can affect data availability and integrity. The following are some of the areas that
students need to focus in the field of cyber security; cloud computing security and data recovery.
other IT disciplines such as programming as evidenced throughout the report. For instance, cyber
security imparts students with knowledge on how access control mechanisms can be used to
protect computer systems, hence assisting many companies and organizations in integrating
passwords and username in their systems, therefore, keeping computers systems secured against
attacks that can affect data availability and integrity. The following are some of the areas that
students need to focus in the field of cyber security; cloud computing security and data recovery.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Cyber Security 8
References
Bulman, G. and Fairlie, R.W., 2016. Technology and education: Computers, software, and the
internet. In Handbook of the Economics of Education (Vol. 5, pp. 239-280). Elsevier.
Choras, M., Kozik, R., Bruna, M.P.T., Yautsiukhin, A., Churchill, A., Maciejewska, I., Eguinoa,
I. and Jomni, A., 2015, August. Comprehensive approach to increase cyber security and
resilience. In Availability, Reliability and Security (ARES), 2015 10th International Conference
on (pp. 686-692). IEEE.
Prasad, P., 2017. A Brief Introduction on Cyber Crime Cases under Information Technology
Act: Details & Analysis.
Safa, N.S., Von Solms, R. and Furnell, S., 2016. Information security policy compliance model
in organizations. Computers & Security, 56, pp.70-82.
Von Solms, R. and Van Niekerk, J., 2013. From information security to cyber
security. computers & security, 38, pp.97-102.
References
Bulman, G. and Fairlie, R.W., 2016. Technology and education: Computers, software, and the
internet. In Handbook of the Economics of Education (Vol. 5, pp. 239-280). Elsevier.
Choras, M., Kozik, R., Bruna, M.P.T., Yautsiukhin, A., Churchill, A., Maciejewska, I., Eguinoa,
I. and Jomni, A., 2015, August. Comprehensive approach to increase cyber security and
resilience. In Availability, Reliability and Security (ARES), 2015 10th International Conference
on (pp. 686-692). IEEE.
Prasad, P., 2017. A Brief Introduction on Cyber Crime Cases under Information Technology
Act: Details & Analysis.
Safa, N.S., Von Solms, R. and Furnell, S., 2016. Information security policy compliance model
in organizations. Computers & Security, 56, pp.70-82.
Von Solms, R. and Van Niekerk, J., 2013. From information security to cyber
security. computers & security, 38, pp.97-102.
1 out of 8
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





